| File name: | 998890-0996544scan.doc |
| Full analysis: | https://app.any.run/tasks/69aa58dc-d0ba-405d-b0b9-c43322bbe79b |
| Verdict: | Malicious activity |
| Analysis date: | January 23, 2019, 00:38:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1, unknown character set |
| MD5: | 837170A5B5D85B20D3E4C01228F5D74B |
| SHA1: | 578E3AC7888126144E4E6080CEC0981D3281F664 |
| SHA256: | 09BC978EBDC88D4F2CD380F14A33D8181F99F5D42DFDA3D4E48CCE6447A6E8F9 |
| SSDEEP: | 24576:wfdvUZaOtZTmZhm4L1LNDHGNEzUFLoHLim7GKELfL8fnIC:u |
MALICIOUS
Runs app for hidden code execution
- cmd.exe (PID: 3864)
- cmd.exe (PID: 2436)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2856)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2856)
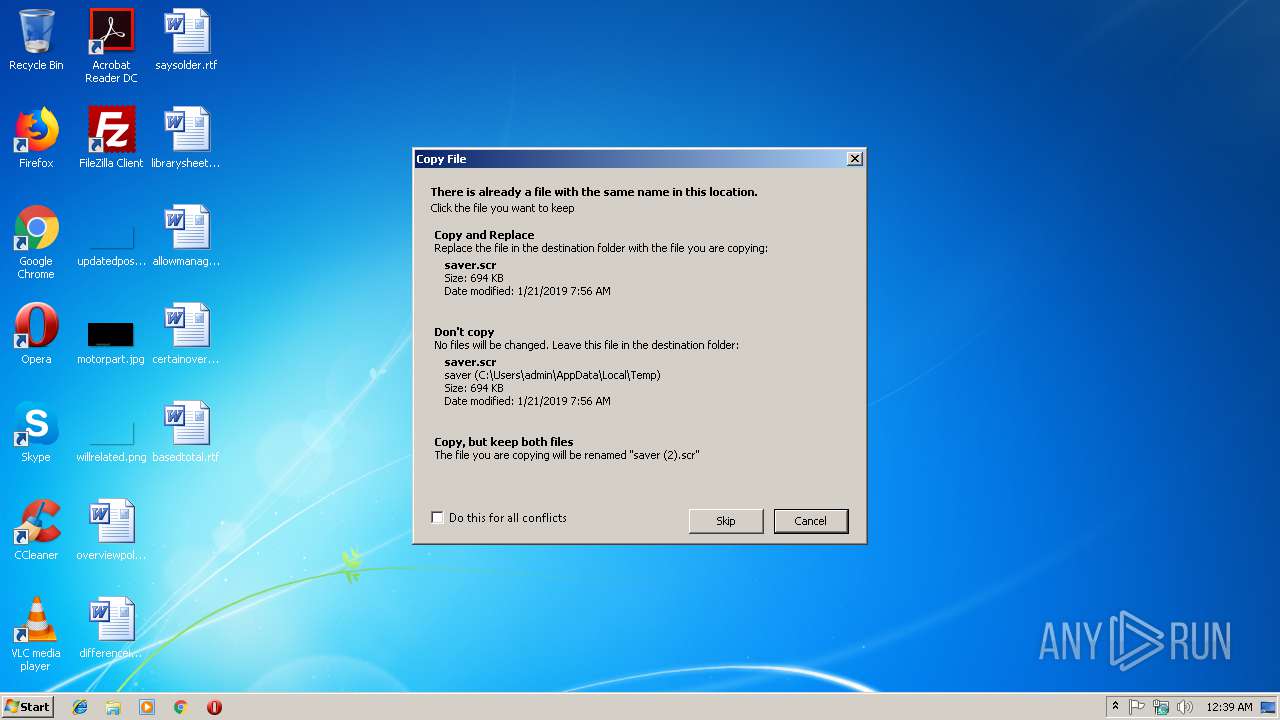
Application was dropped or rewritten from another process
- saver.scr (PID: 3612)
SUSPICIOUS
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3900)
- cmd.exe (PID: 3972)
- cmd.exe (PID: 3780)
- cmd.exe (PID: 3576)
- cmd.exe (PID: 2984)
- cmd.exe (PID: 2512)
- cmd.exe (PID: 2960)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2436)
- cmd.exe (PID: 2256)
- cmd.exe (PID: 3864)
- cmd.exe (PID: 2512)
Executable content was dropped or overwritten
- cscript.exe (PID: 4092)
Executes scripts
- cmd.exe (PID: 2512)
Uses TASKKILL.EXE to kill Office Apps
- cmd.exe (PID: 2512)
Application launched itself
- cmd.exe (PID: 2512)
Starts application with an unusual extension
- cmd.exe (PID: 2512)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2856)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
Total processes
68
Monitored processes
37
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1748 | REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\13.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1920 | REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\11.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2244 | REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\14.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2256 | CmD | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2368 | TIMEOUT /T 1 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2396 | REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2436 | "C:\Windows\System32\cmd.exe" /C CmD < "C:\Users\admin\AppData\Local\Temp\ufFm.cMD" | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2440 | REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\15.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2512 | C:\Windows\system32\cmd.exe /K itnqknf5.CMD | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2540 | TIMEOUT /T 1 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 480
Read events
1 448
Write events
29
Delete events
3
Modification events
| (PID) Process: | (2856) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | {g$ |
Value: 7B672400280B0000010000000000000000000000 | |||
| (PID) Process: | (2856) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2856) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2856) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1312227358 | |||
| (PID) Process: | (2856) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1312227472 | |||
| (PID) Process: | (2856) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1312227473 | |||
| (PID) Process: | (2856) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 280B0000D8708A08B4B2D40100000000 | |||
| (PID) Process: | (2856) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | rh$ |
Value: 72682400280B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2856) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | rh$ |
Value: 72682400280B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2856) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
1
Suspicious files
3
Text files
14
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9B5B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\uffm.cmd | text | |
MD5:— | SHA256:— | |||
| 2856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\itnqknf5.cmd | text | |
MD5:— | SHA256:— | |||
| 2512 | cmd.exe | C:\Users\admin\AppData\Local\Temp\_.vbs | text | |
MD5:— | SHA256:— | |||
| 2856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\a.ScT | xml | |
MD5:— | SHA256:— | |||
| 2856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\itn.zip | compressed | |
MD5:— | SHA256:— | |||
| 4092 | cscript.exe | C:\Users\admin\AppData\Local\Temp\gondi.doc | text | |
MD5:— | SHA256:— | |||
| 2856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{C4F4EA2F-6E1E-4465-BA69-1AB66986526F}.tmp | binary | |
MD5:— | SHA256:— | |||
| 2856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{660E7199-018B-4581-B782-AD8AB228E4DC}.tmp | binary | |
MD5:— | SHA256:— | |||
| 4092 | cscript.exe | C:\Users\admin\AppData\Local\Temp\saver.scr | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report