| File name: | 666.exe malware.zip |
| Full analysis: | https://app.any.run/tasks/bd0c19ba-d913-44cd-a3ca-2ec887dfa0fc |
| Verdict: | Malicious activity |
| Analysis date: | March 16, 2024, 17:41:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 29FA9E769E966D235D50B905F7D86230 |
| SHA1: | C92929E61218173908925F5830B35FC41B56A7F9 |
| SHA256: | 09BC6605501BC38B05E60D21678CFADAD50473EAF0F39B24101A5CC6460BCC3B |
| SSDEEP: | 98304:klMOvSbvCemKja46x8RnKXbmDFw0yj5vgsqdiiAsgV4ZshrHExy4/KazcSp:aGZ |
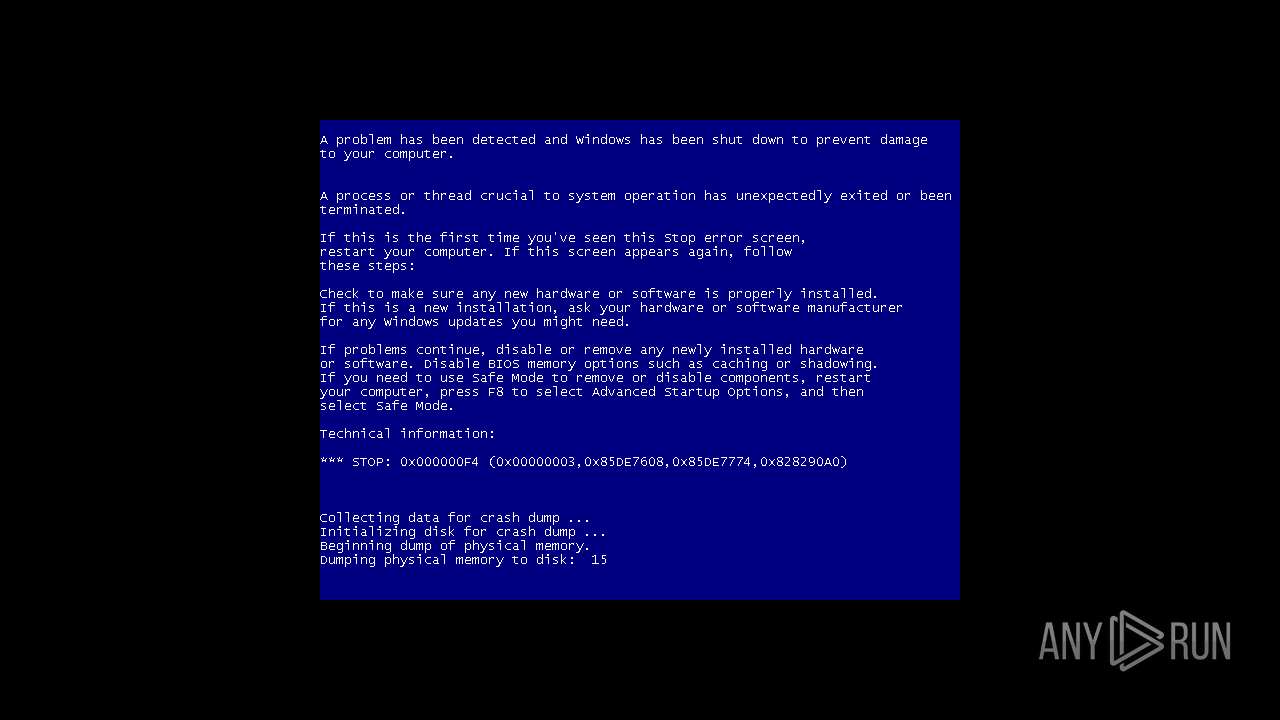
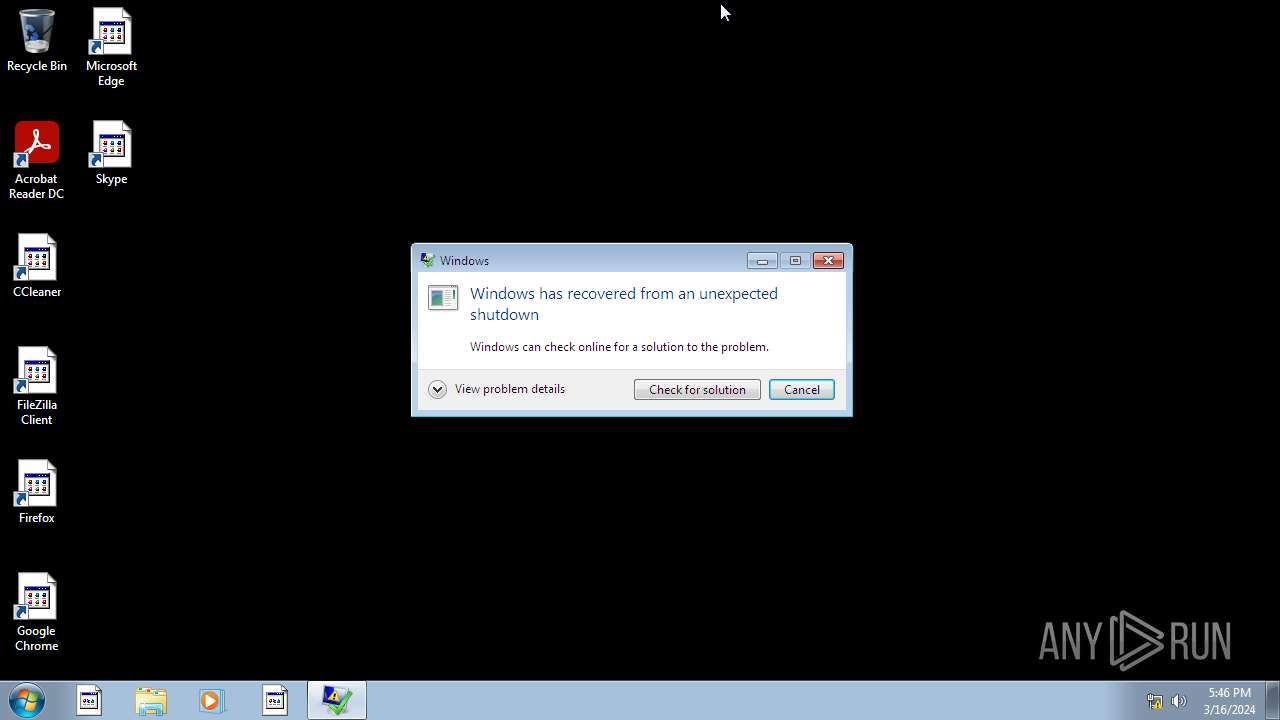
MALICIOUS
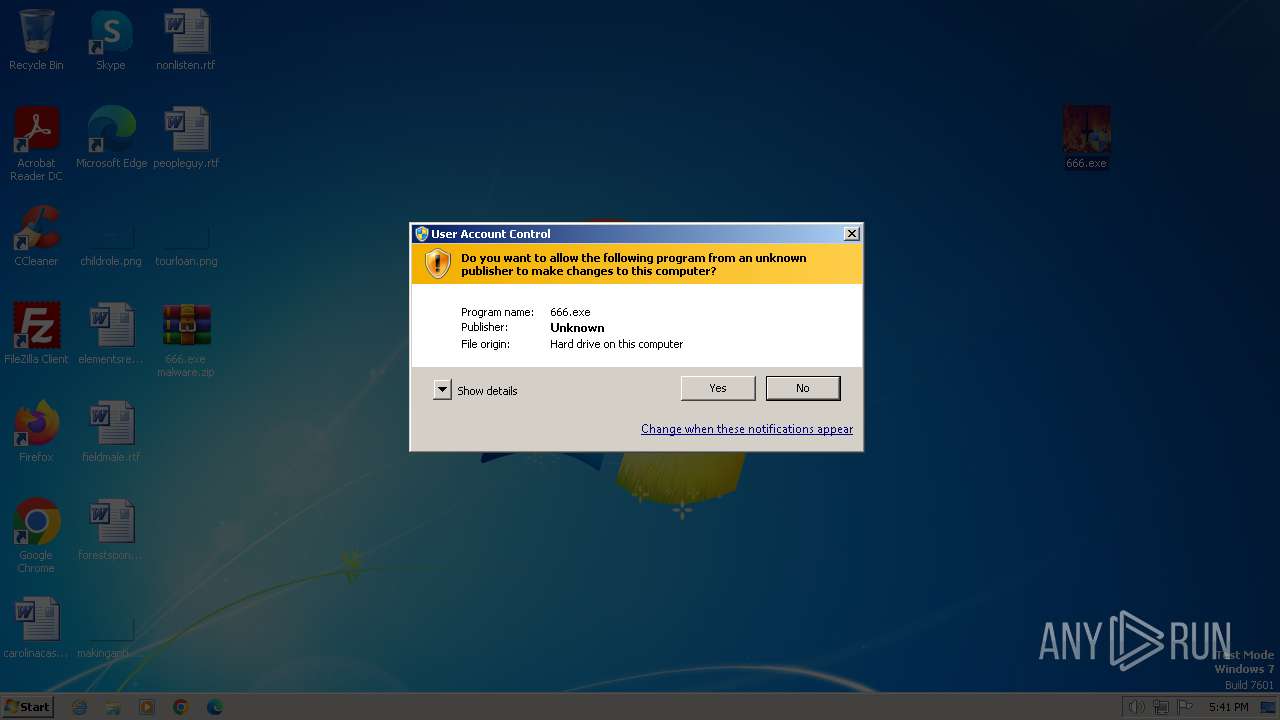
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2120)
- 666.exe (PID: 2596)
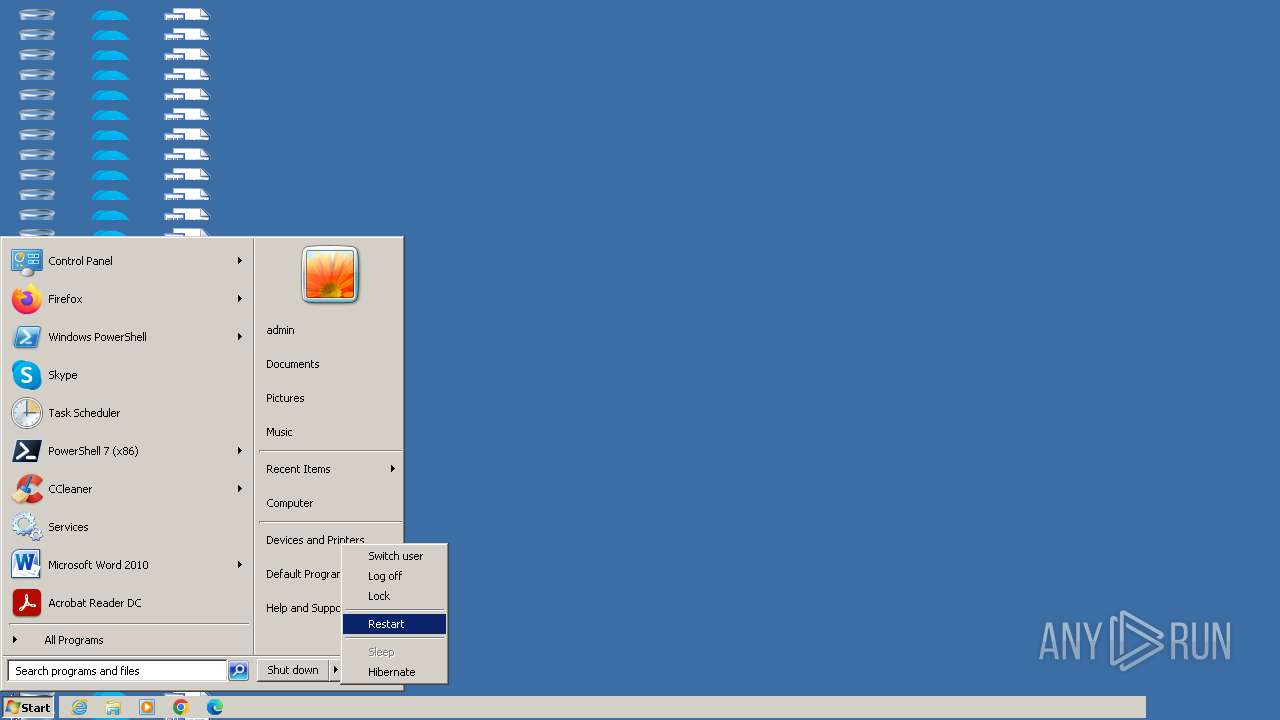
Disables the Shutdown in the Start menu
- 666.exe (PID: 2596)
Disables the Run the Start menu
- 666.exe (PID: 2596)
Changes the login/logoff helper path in the registry
- 666.exe (PID: 2596)
Changes image file execution options
- 666.exe (PID: 2596)
UAC/LUA settings modification
- 666.exe (PID: 2596)
Changes the autorun value in the registry
- unregmp2.exe (PID: 2240)
- regsvr32.exe (PID: 2312)
Create files in the Startup directory
- regsvr32.exe (PID: 2312)
Steals credentials from Web Browsers
- setup.exe (PID: 2640)
SUSPICIOUS
Executable content was dropped or overwritten
- 666.exe (PID: 2596)
Creates or modifies Windows services
- 666.exe (PID: 2596)
Changes the desktop background image
- 666.exe (PID: 2596)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1252)
- ctfmon.exe (PID: 1408)
- sipnotify.exe (PID: 1292)
Reads settings of System Certificates
- sipnotify.exe (PID: 1252)
- sipnotify.exe (PID: 1292)
Reads the Internet Settings
- sipnotify.exe (PID: 1252)
- runonce.exe (PID: 1600)
- ie4uinit.exe (PID: 2084)
- rundll32.exe (PID: 2132)
- rundll32.exe (PID: 2164)
- sipnotify.exe (PID: 1292)
- ie4uinit.exe (PID: 2220)
- ie4uinit.exe (PID: 2300)
Non-standard symbols in registry
- WerFault.exe (PID: 2052)
Application launched itself
- ie4uinit.exe (PID: 2084)
- rundll32.exe (PID: 2132)
- WerFault.exe (PID: 1412)
- setup.exe (PID: 2640)
Reads Internet Explorer settings
- ie4uinit.exe (PID: 2084)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 2084)
- rundll32.exe (PID: 2132)
Changes internet zones settings
- ie4uinit.exe (PID: 2084)
Reads Microsoft Outlook installation path
- ie4uinit.exe (PID: 2084)
Write to the desktop.ini file (may be used to cloak folders)
- ie4uinit.exe (PID: 2084)
- unregmp2.exe (PID: 2240)
- regsvr32.exe (PID: 2312)
Changes default file association
- unregmp2.exe (PID: 2240)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2120)
Checks supported languages
- 666.exe (PID: 2596)
- wmpnscfg.exe (PID: 2432)
- IMEKLMG.EXE (PID: 2168)
- wmpnscfg.exe (PID: 2452)
- IMEKLMG.EXE (PID: 2152)
- setup.exe (PID: 2652)
- setup.exe (PID: 2684)
- IMEKLMG.EXE (PID: 3156)
- IMEKLMG.EXE (PID: 3144)
- setup.exe (PID: 2640)
- IMKRMIG.EXE (PID: 3176)
- wmpnscfg.exe (PID: 3720)
- wmpnscfg.exe (PID: 3740)
Manual execution by a user
- 666.exe (PID: 2596)
- IMEKLMG.EXE (PID: 2152)
- IMEKLMG.EXE (PID: 2168)
- wmpnscfg.exe (PID: 2432)
- wmpnscfg.exe (PID: 2452)
- runonce.exe (PID: 1600)
- ie4uinit.exe (PID: 2084)
- unregmp2.exe (PID: 2240)
- regsvr32.exe (PID: 2312)
- ie4uinit.exe (PID: 2300)
- chrmstp.exe (PID: 2488)
- ie4uinit.exe (PID: 2220)
- setup.exe (PID: 2640)
- IMEKLMG.EXE (PID: 3144)
- IMEKLMG.EXE (PID: 3156)
- wmpnscfg.exe (PID: 3720)
- wmpnscfg.exe (PID: 3740)
Reads the computer name
- 666.exe (PID: 2596)
- IMEKLMG.EXE (PID: 2152)
- IMEKLMG.EXE (PID: 2168)
- wmpnscfg.exe (PID: 2432)
- wmpnscfg.exe (PID: 2452)
- setup.exe (PID: 2652)
- setup.exe (PID: 2684)
- IMEKLMG.EXE (PID: 3144)
- wmpnscfg.exe (PID: 3720)
- IMEKLMG.EXE (PID: 3156)
- wmpnscfg.exe (PID: 3740)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1252)
- ie4uinit.exe (PID: 2084)
- runonce.exe (PID: 1600)
- sipnotify.exe (PID: 1292)
Reads the software policy settings
- sipnotify.exe (PID: 1252)
- sipnotify.exe (PID: 1292)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2152)
- IMEKLMG.EXE (PID: 2168)
- IMEKLMG.EXE (PID: 3144)
- IMEKLMG.EXE (PID: 3156)
Reads the time zone
- runonce.exe (PID: 1600)
Creates files in the program directory
- ie4uinit.exe (PID: 2084)
- chrmstp.exe (PID: 2544)
- setup.exe (PID: 2652)
- setup.exe (PID: 2640)
- chrmstp.exe (PID: 2488)
- setup.exe (PID: 2684)
Checks proxy server information
- ie4uinit.exe (PID: 2084)
Application launched itself
- chrmstp.exe (PID: 2488)
- chrmstp.exe (PID: 2544)
- msedge.exe (PID: 2700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:07:28 19:19:06 |
| ZipCRC: | 0x298ee849 |
| ZipCompressedSize: | 1820904 |
| ZipUncompressedSize: | 4166144 |
| ZipFileName: | 666.exe |
Total processes
165
Monitored processes
39
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1252 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1292 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1408 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CTF Loader Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1412 | "C:\Windows\System32\WerFault.exe" -k -rq | C:\Windows\System32\WerFault.exe | — | runonce.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1600 | C:\Windows\system32\runonce.exe /Explorer | C:\Windows\System32\runonce.exe | — | explorer.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2052 | C:\Windows\System32\WerFault.exe -k -q | C:\Windows\System32\WerFault.exe | — | WerFault.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2084 | "C:\Windows\System32\ie4uinit.exe" -UserConfig | C:\Windows\System32\ie4uinit.exe | — | explorer.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2104 | C:\Windows\System32\ie4uinit.exe -ClearIconCache | C:\Windows\System32\ie4uinit.exe | — | ie4uinit.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2116 | C:\Windows\System32\rundll32 advpack.dll,LaunchINFSectionEx C:\Windows\system32\ieuinit.inf,Install,,36 | C:\Windows\System32\rundll32.exe | — | ie4uinit.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2120 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\666.exe malware.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
26 436
Read events
24 954
Write events
1 282
Delete events
200
Modification events
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\666.exe malware.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
8
Suspicious files
39
Text files
88
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2164 | rundll32.exe | C:\Users\Administrator\AppData\Local\Microsoft\Feeds Cache\AVO5ZJHP\fwlink[1] | — | |
MD5:— | SHA256:— | |||
| 2164 | rundll32.exe | C:\Users\Administrator\AppData\Local\Microsoft\Feeds Cache\I78Z4R0G\fwlink[1] | — | |
MD5:— | SHA256:— | |||
| 2164 | rundll32.exe | C:\Users\Administrator\AppData\Local\Microsoft\Feeds Cache\23SL9UQZ\fwlink[1] | — | |
MD5:— | SHA256:— | |||
| 2164 | rundll32.exe | C:\Users\Administrator\AppData\Local\Microsoft\Feeds Cache\F1FS46JA\fwlink[1] | — | |
MD5:— | SHA256:— | |||
| 2164 | rundll32.exe | C:\Users\Administrator\AppData\Local\Microsoft\Feeds Cache\AVO5ZJHP\fwlink[2] | — | |
MD5:— | SHA256:— | |||
| 2164 | rundll32.exe | C:\Users\Administrator\AppData\Local\Microsoft\Feeds Cache\I78Z4R0G\fwlink[2] | — | |
MD5:— | SHA256:— | |||
| 2596 | 666.exe | C:\Windows\first.exe | executable | |
MD5:4CB1F84904AF2DC04D8608AD00F8CA1E | SHA256:37F99309053D3B0ADCE6BAC240249F0390C6370A7B1F6D2099B7E838F6DF91B7 | |||
| 2596 | 666.exe | C:\Windows\death.exe | executable | |
MD5:F3346CEC01E6868EC4F593E7169DEC18 | SHA256:A29451E1B94AB7A4A4DE84BE214D39D3C6FF3343DC5DF041E627D1071B70201C | |||
| 1252 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\script.js | text | |
MD5:A2682382967C351F7ED21762F9E5DE9E | SHA256:36B1D26F1EC69685648C0528C2FCE95A3C2DBECF828CDFA4A8B4239A15B644A2 | |||
| 1252 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\styles.css | text | |
MD5:3383EEF350240253D7C2C2564381B3CB | SHA256:85443493D86D6D7FB0E07BC9705DFC9C858086FBA1B0E508092AB328D5F145E8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
14
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1252 | sipnotify.exe | HEAD | 200 | 88.221.61.151:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133550845300030000 | unknown | — | — | unknown |
1292 | sipnotify.exe | HEAD | 200 | 88.221.61.151:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133550846149480000 | unknown | — | — | unknown |
1292 | sipnotify.exe | GET | 200 | 88.221.61.151:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133550846149480000 | unknown | compressed | 78.4 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1100 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1252 | sipnotify.exe | 88.221.61.151:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | unknown |
1148 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1292 | sipnotify.exe | 88.221.61.151:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |