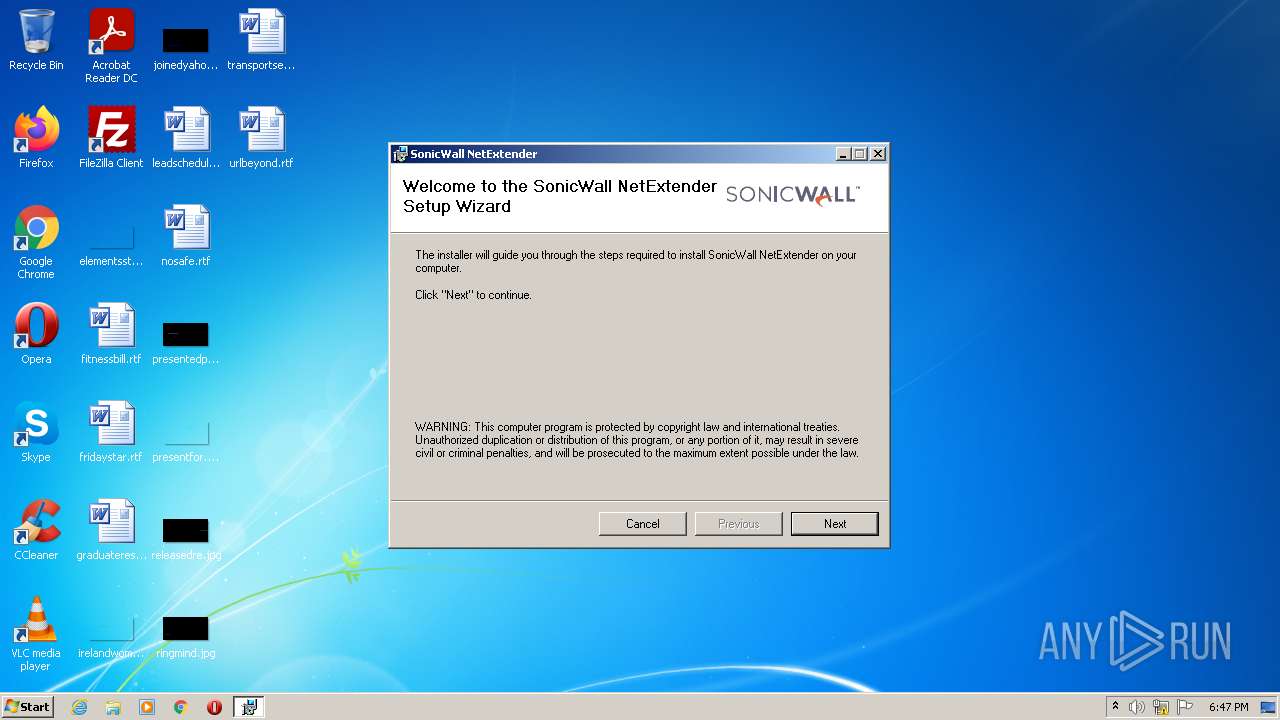
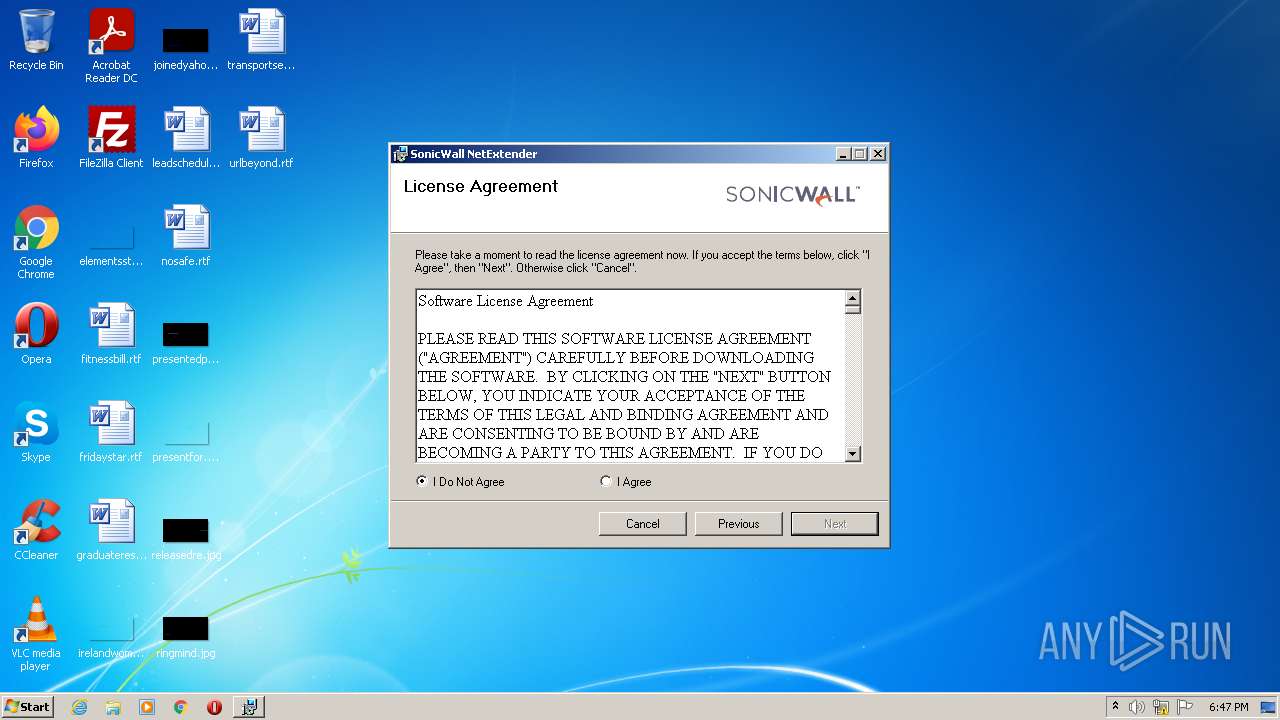
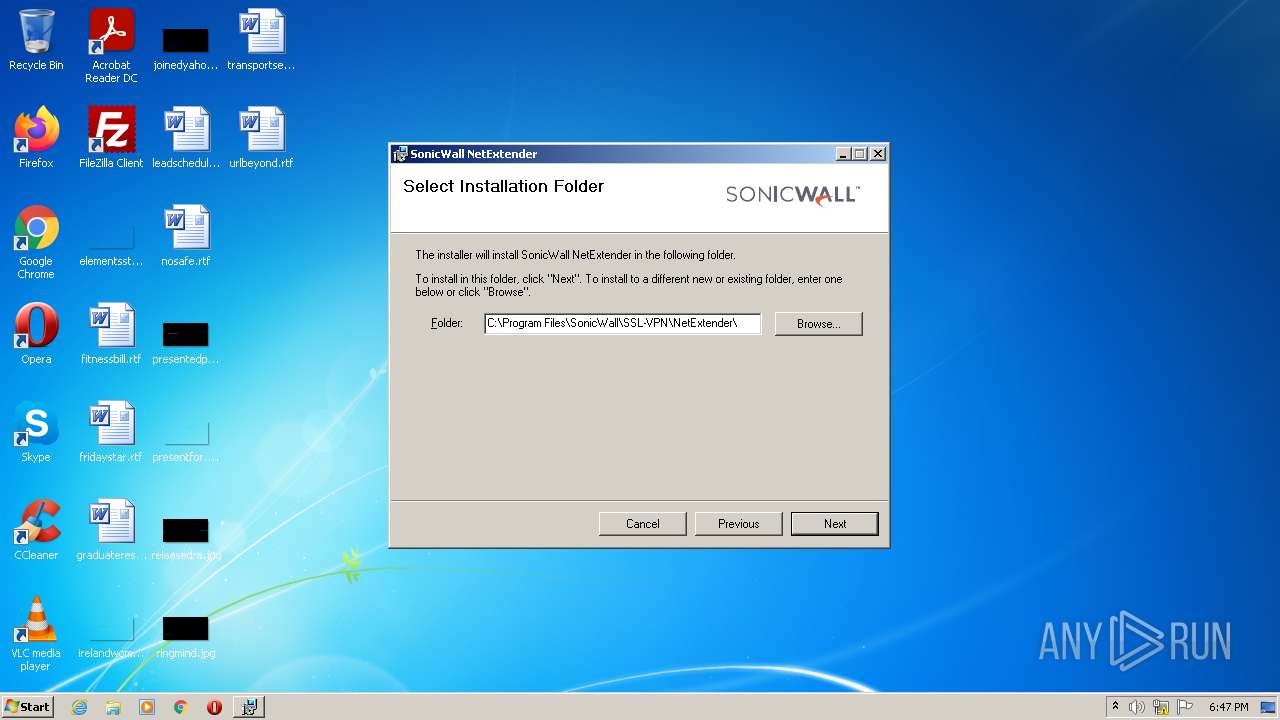
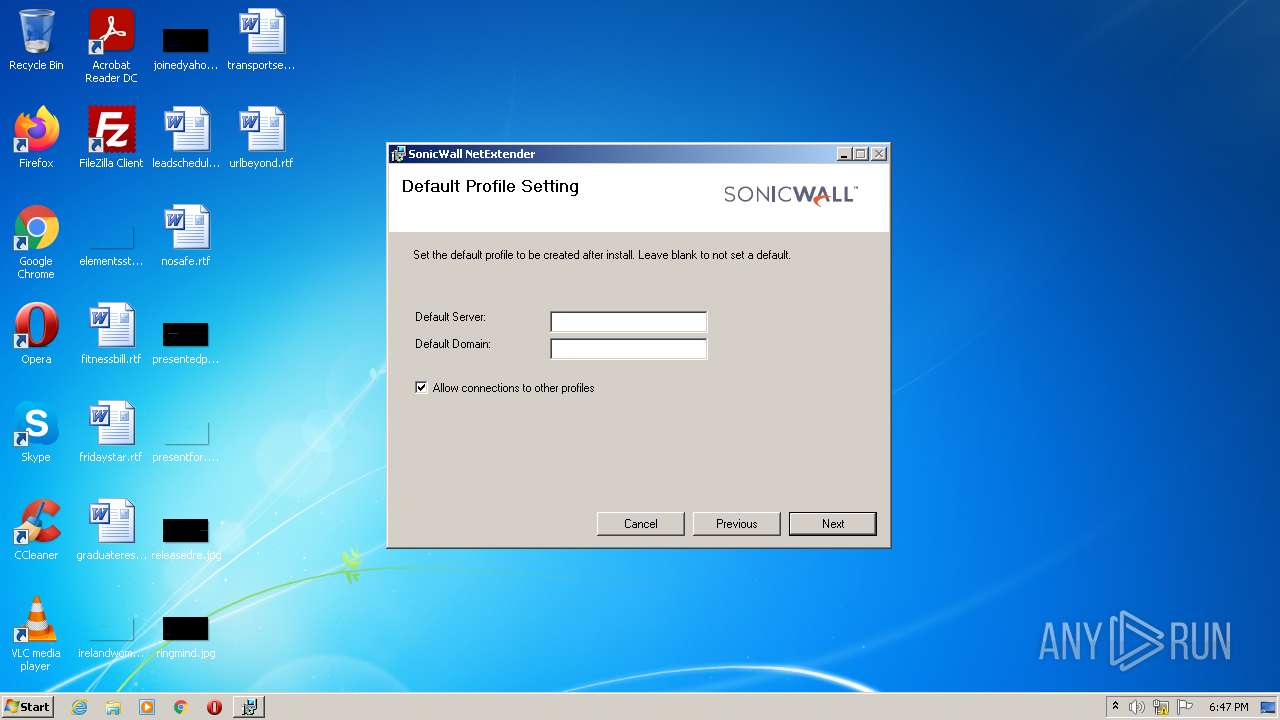
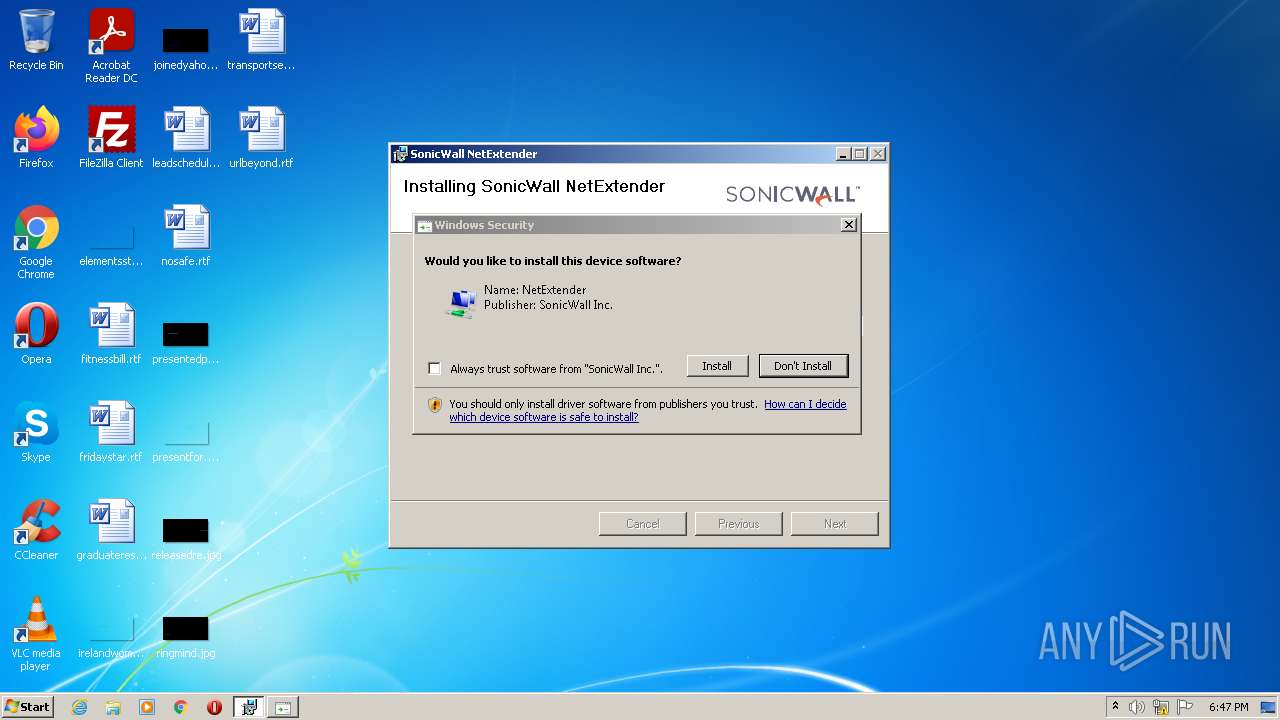
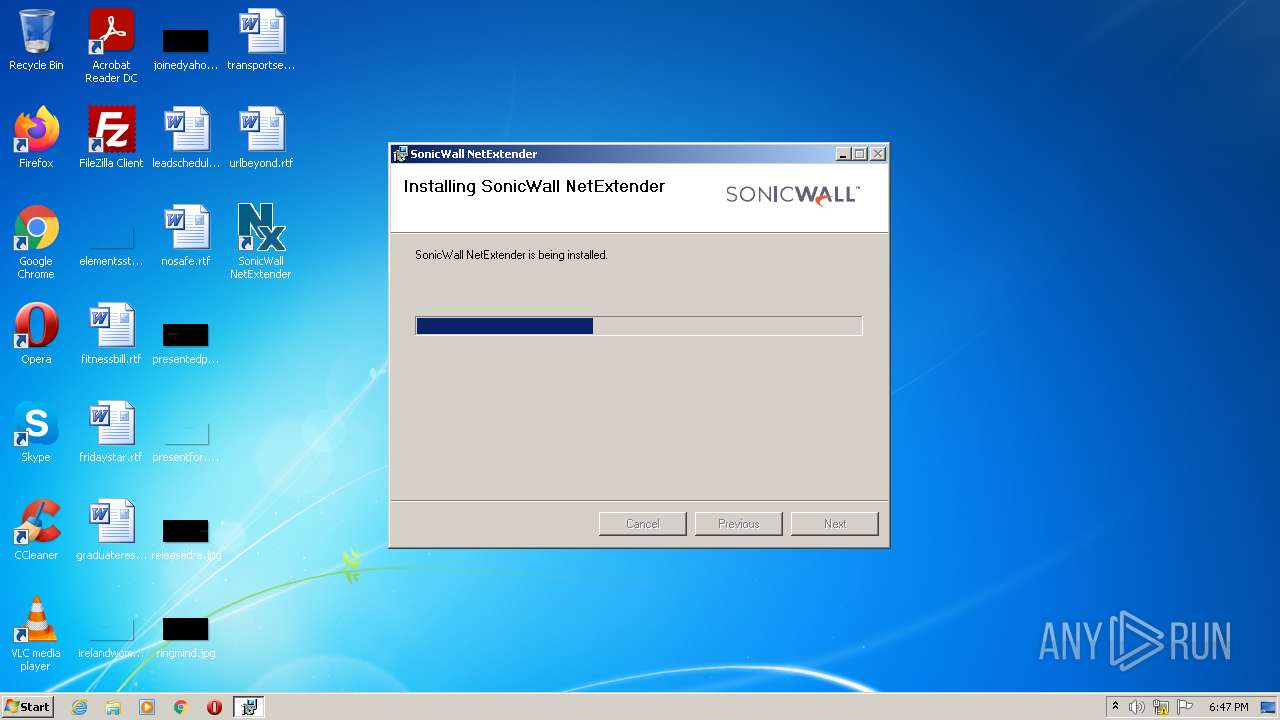
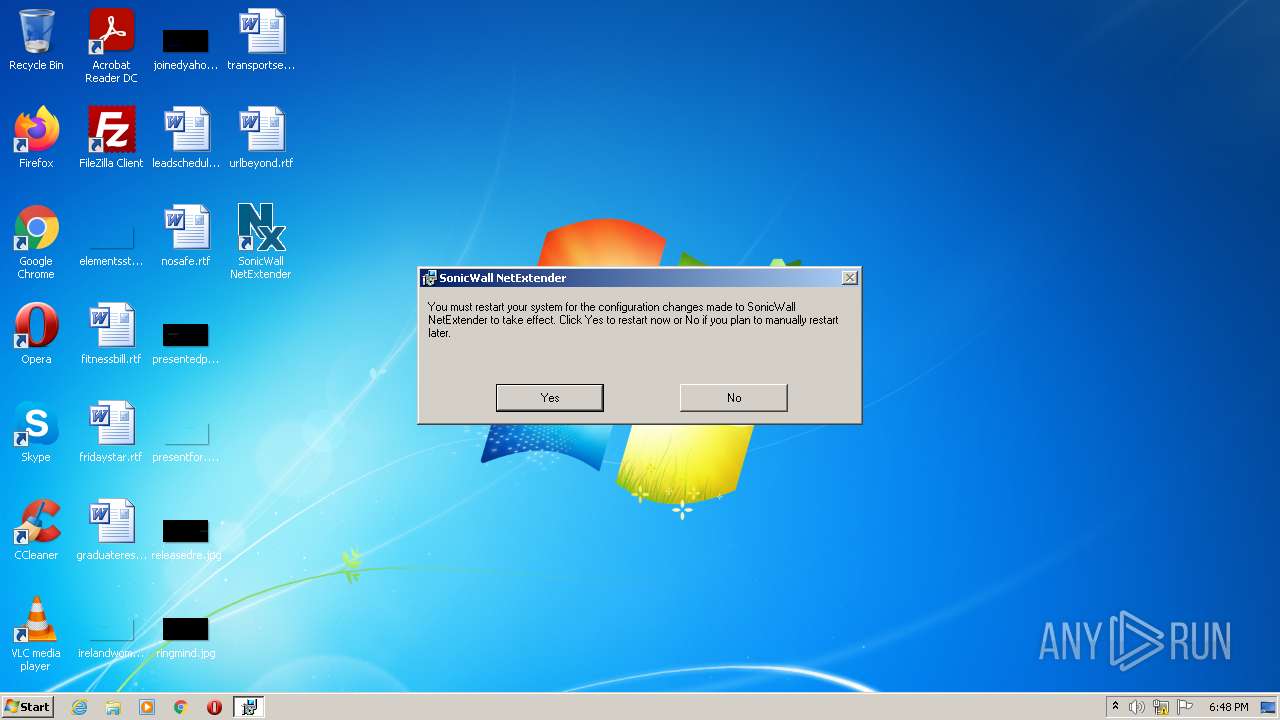
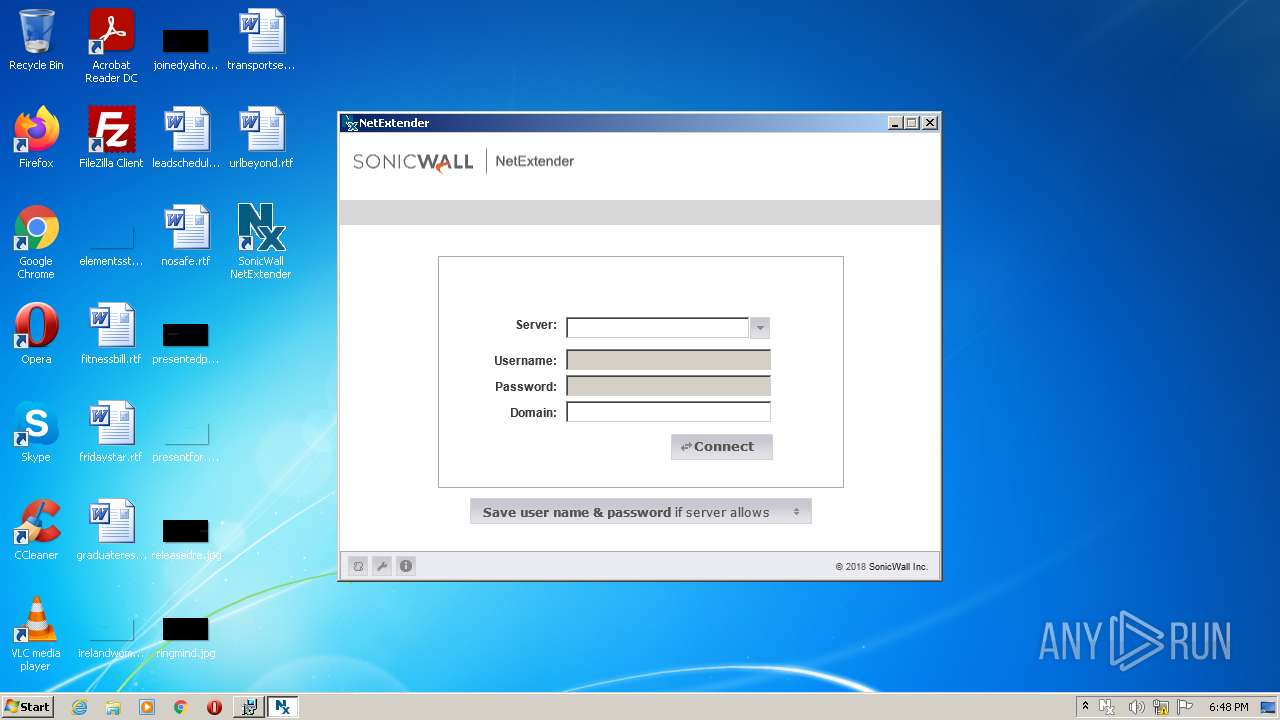
| File name: | NetExtender-9.0.0.274.MSI |
| Full analysis: | https://app.any.run/tasks/79f14235-515b-4ffa-881a-123ed9fb0715 |
| Verdict: | Malicious activity |
| Analysis date: | February 08, 2022, 18:46:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Code page: 1252, Title: Installation Database, Subject: SonicWall SSL-VPN NetExtender, Author: SonicWall Inc., Keywords: Installer, Comments: This installer database contains the logic and data required to install SonicWall NetExtender., Template: Intel;1033, Revision Number: {5EEE4895-1938-4874-83C0-E8BDDCF066D3}, Create Time/Date: Tue Jul 3 03:26:24 2018, Last Saved Time/Date: Tue Jul 3 03:26:24 2018, Number of Pages: 110, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.1.2318), Security: 0 |
| MD5: | AC7BBC59FB1B00C9E39EAC805A78DA61 |
| SHA1: | F256D541FAA5B28B1C3A5E0C727BCAD6D8A4BABE |
| SHA256: | 09B379C073D5D98B580AB1B36036DB109C0503FA793AC7CD87BD0064584A6793 |
| SSDEEP: | 196608:CXTaH2goR0dNb1Spnbwc3ZX+vDohFHn4K2jj8rBiCNto6SWpb+eCkPr:CDaRY5HhFnRiCNm6SWN+e |
MALICIOUS
Drops executable file immediately after starts
- MsiExec.exe (PID: 344)
- DrvInst.exe (PID: 2968)
- DrvInst.exe (PID: 3920)
- RUNDLL32.EXE (PID: 2916)
Changes the autorun value in the registry
- RUNDLL32.EXE (PID: 2916)
- msiexec.exe (PID: 2844)
SUSPICIOUS
Executed as Windows Service
- msiexec.exe (PID: 2844)
- vssvc.exe (PID: 592)
- NEService.exe (PID: 3832)
- SWClientProtectionService.exe (PID: 2968)
Reads Windows owner or organization settings
- msiexec.exe (PID: 4048)
- msiexec.exe (PID: 2844)
Reads the Windows organization settings
- msiexec.exe (PID: 4048)
- msiexec.exe (PID: 2844)
Drops a file that was compiled in debug mode
- msiexec.exe (PID: 4048)
- MsiExec.exe (PID: 344)
- msiexec.exe (PID: 2844)
- MsiExec.exe (PID: 3624)
- DrvInst.exe (PID: 2968)
- DrvInst.exe (PID: 3920)
- RUNDLL32.EXE (PID: 2916)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4048)
- msiexec.exe (PID: 2844)
- MsiExec.exe (PID: 344)
- MsiExec.exe (PID: 3624)
- DrvInst.exe (PID: 2968)
- DrvInst.exe (PID: 3920)
- RUNDLL32.EXE (PID: 2916)
Application launched itself
- msiexec.exe (PID: 2844)
Reads default file associations for system extensions
- MsiExec.exe (PID: 344)
Creates a directory in Program Files
- msiexec.exe (PID: 2844)
- MsiExec.exe (PID: 3624)
Creates files in the program directory
- msiexec.exe (PID: 2844)
- MsiExec.exe (PID: 3624)
- NEService.exe (PID: 3832)
- SWClientProtectionService.exe (PID: 2312)
Searches for installed software
- msiexec.exe (PID: 2844)
Reads Environment values
- vssvc.exe (PID: 592)
Checks supported languages
- DrvInst.exe (PID: 2968)
- DrvInst.exe (PID: 3920)
- NEService.exe (PID: 3832)
- SWClientProtectionService.exe (PID: 2312)
- SWClientProtectionService.exe (PID: 856)
- SWClientProtectionService.exe (PID: 2968)
- NEGui.exe (PID: 2816)
Removes files from Windows directory
- DrvInst.exe (PID: 2968)
- DrvInst.exe (PID: 3920)
- RUNDLL32.EXE (PID: 2916)
Reads the computer name
- DrvInst.exe (PID: 2968)
- DrvInst.exe (PID: 3920)
- NEService.exe (PID: 3832)
- SWClientProtectionService.exe (PID: 2312)
- SWClientProtectionService.exe (PID: 856)
- SWClientProtectionService.exe (PID: 2968)
- NEGui.exe (PID: 2816)
Creates files in the driver directory
- DrvInst.exe (PID: 2968)
- DrvInst.exe (PID: 3920)
- RUNDLL32.EXE (PID: 2916)
Creates files in the Windows directory
- DrvInst.exe (PID: 2968)
- DrvInst.exe (PID: 3920)
- RUNDLL32.EXE (PID: 2916)
Uses RUNDLL32.EXE to load library
- DrvInst.exe (PID: 2968)
- SWClientProtectionService.exe (PID: 2312)
Executed via COM
- DrvInst.exe (PID: 2968)
- DrvInst.exe (PID: 3920)
Creates or modifies windows services
- RUNDLL32.EXE (PID: 2916)
- SWClientProtectionService.exe (PID: 2312)
Creates files in the user directory
- msiexec.exe (PID: 2844)
Creates a software uninstall entry
- msiexec.exe (PID: 2844)
Reads the time zone
- runonce.exe (PID: 3056)
Drops a file with a compile date too recent
- SWClientProtectionService.exe (PID: 2968)
Reads Microsoft Outlook installation path
- NEGui.exe (PID: 2816)
INFO
Checks supported languages
- msiexec.exe (PID: 4048)
- msiexec.exe (PID: 2844)
- MsiExec.exe (PID: 2564)
- vssvc.exe (PID: 592)
- MsiExec.exe (PID: 344)
- MsiExec.exe (PID: 3624)
- rundll32.exe (PID: 888)
- RUNDLL32.EXE (PID: 2916)
- runonce.exe (PID: 3056)
- grpconv.exe (PID: 3204)
Reads the computer name
- msiexec.exe (PID: 4048)
- msiexec.exe (PID: 2844)
- MsiExec.exe (PID: 2564)
- vssvc.exe (PID: 592)
- MsiExec.exe (PID: 344)
- MsiExec.exe (PID: 3624)
- rundll32.exe (PID: 888)
- RUNDLL32.EXE (PID: 2916)
- runonce.exe (PID: 3056)
Reads settings of System Certificates
- msiexec.exe (PID: 4048)
- MsiExec.exe (PID: 3624)
- rundll32.exe (PID: 888)
- DrvInst.exe (PID: 3920)
- DrvInst.exe (PID: 2968)
- msiexec.exe (PID: 2844)
Checks Windows Trust Settings
- msiexec.exe (PID: 4048)
- msiexec.exe (PID: 2844)
- DrvInst.exe (PID: 2968)
- rundll32.exe (PID: 888)
- MsiExec.exe (PID: 3624)
- DrvInst.exe (PID: 3920)
Reads CPU info
- runonce.exe (PID: 3056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (95.3) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (3.2) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| Software: | Windows Installer XML Toolset (3.11.1.2318) |
| Words: | 2 |
| Pages: | 110 |
| ModifyDate: | 2018:07:03 02:26:24 |
| CreateDate: | 2018:07:03 02:26:24 |
| RevisionNumber: | {5EEE4895-1938-4874-83C0-E8BDDCF066D3} |
| Template: | Intel;1033 |
| Comments: | This installer database contains the logic and data required to install SonicWall NetExtender. |
| Keywords: | Installer |
| Author: | SonicWall Inc. |
| Subject: | SonicWall SSL-VPN NetExtender |
| Title: | Installation Database |
| CodePage: | Windows Latin 1 (Western European) |
Total processes
55
Monitored processes
17
Malicious processes
7
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 344 | C:\Windows\system32\MsiExec.exe -Embedding B646A850C00E7103B6813212C43CA6B2 | C:\Windows\system32\MsiExec.exe | msiexec.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) | ||||
| 592 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft� Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 856 | "C:\Program Files\SonicWall\Client Protection Service\SWClientProtectionService.exe" -i install | C:\Program Files\SonicWall\Client Protection Service\SWClientProtectionService.exe | — | MsiExec.exe |
User: SYSTEM Company: SonicWall Integrity Level: SYSTEM Description: Client Protection Service Exit code: 0 Version: 1.0.16.1 | ||||
| 888 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{38433b79-4075-37d0-5bfd-bf190b318c36} Global\{0eceab4c-bfec-6fe6-75f2-9a701b630707} C:\Windows\System32\DriverStore\Temp\{2d3727d8-2b0a-0445-2bc1-8c164ed5844d}\nxdrv.inf C:\Windows\System32\DriverStore\Temp\{2d3727d8-2b0a-0445-2bc1-8c164ed5844d}\NxDrv.cat | C:\Windows\system32\rundll32.exe | — | DrvInst.exe |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2312 | "C:\Program Files\SonicWall\Client Protection Service\SWClientProtectionService.exe" -i instdrv | C:\Program Files\SonicWall\Client Protection Service\SWClientProtectionService.exe | — | MsiExec.exe |
User: SYSTEM Company: SonicWall Integrity Level: SYSTEM Description: Client Protection Service Exit code: 0 Version: 1.0.16.1 | ||||
| 2564 | C:\Windows\system32\MsiExec.exe -Embedding A471A138422753C027D40356F5AAA316 C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) | ||||
| 2816 | "C:\Program Files\SonicWall\SSL-VPN\NetExtender\NEGui.exe" "" | C:\Program Files\SonicWall\SSL-VPN\NetExtender\NEGui.exe | — | msiexec.exe |
User: admin Company: SonicWall Integrity Level: MEDIUM Description: NetExtender GUI client Exit code: 0 Version: 9, 0, 274, 1 | ||||
| 2844 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) | ||||
| 2916 | RUNDLL32.EXE SETUPAPI.DLL,InstallHinfSection DefaultInstall 132 C:\PROGRA~1\SONICW~1\CLIENT~1\SFPMON~1.INF | C:\Windows\system32\RUNDLL32.EXE | SWClientProtectionService.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2968 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{49c760c9-a5fd-34cf-17e3-870e10b18203}\nxdrv.inf" "0" "6ed3b522b" "000004B8" "WinSta0\Default" "000004C8" "208" "c:\program files\sonicwall\ssl-vpn\netextender" | C:\Windows\system32\DrvInst.exe | svchost.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
40
Suspicious files
24
Text files
9
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2844 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2844 | msiexec.exe | C:\Windows\Installer\131531.msi | — | |
MD5:— | SHA256:— | |||
| 2844 | msiexec.exe | C:\Windows\Installer\MSI1BA9.tmp | — | |
MD5:— | SHA256:— | |||
| 4048 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIDE23.tmp | executable | |
MD5:— | SHA256:— | |||
| 2844 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:— | SHA256:— | |||
| 2844 | msiexec.exe | C:\Windows\Installer\MSI1BBA.tmp | executable | |
MD5:— | SHA256:— | |||
| 2844 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF7B4985C8ABD9CD74.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2844 | msiexec.exe | C:\Windows\Installer\131532.ipi | binary | |
MD5:— | SHA256:— | |||
| 2844 | msiexec.exe | C:\Windows\Installer\MSI1DC0.tmp | executable | |
MD5:— | SHA256:— | |||
| 344 | MsiExec.exe | C:\Users\admin\AppData\Local\Temp\SWClientProtectionService.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report