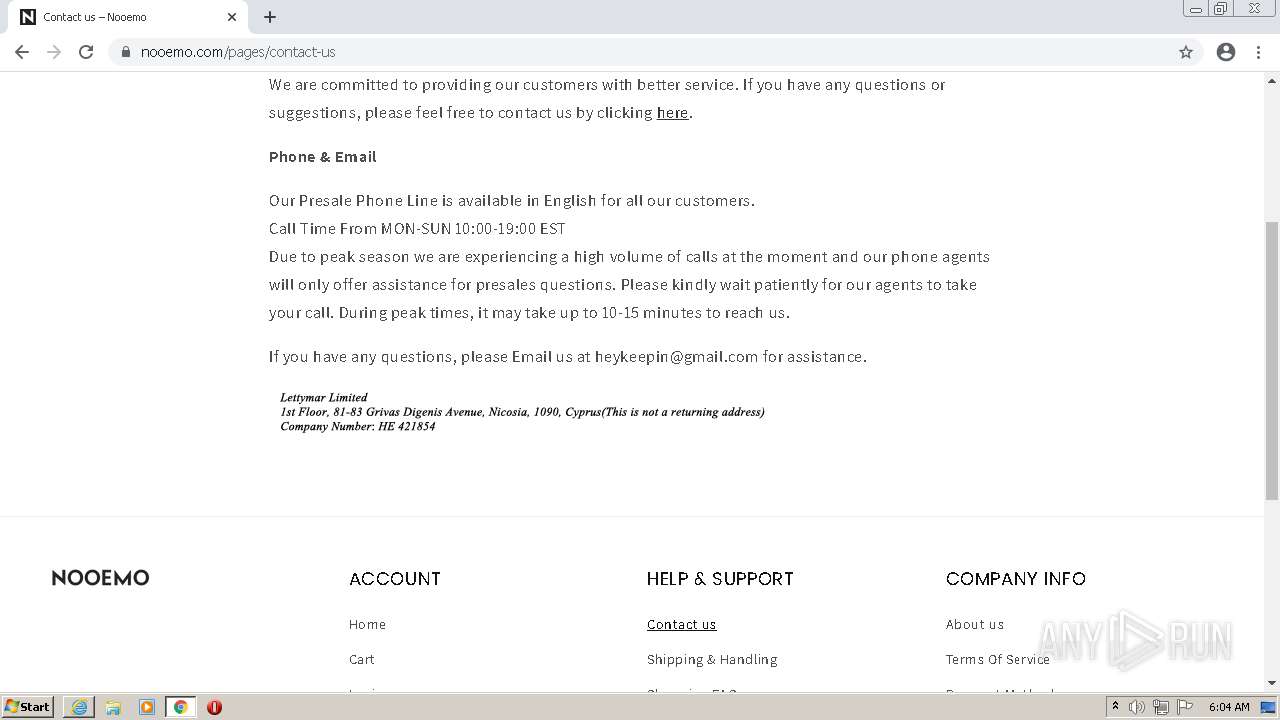
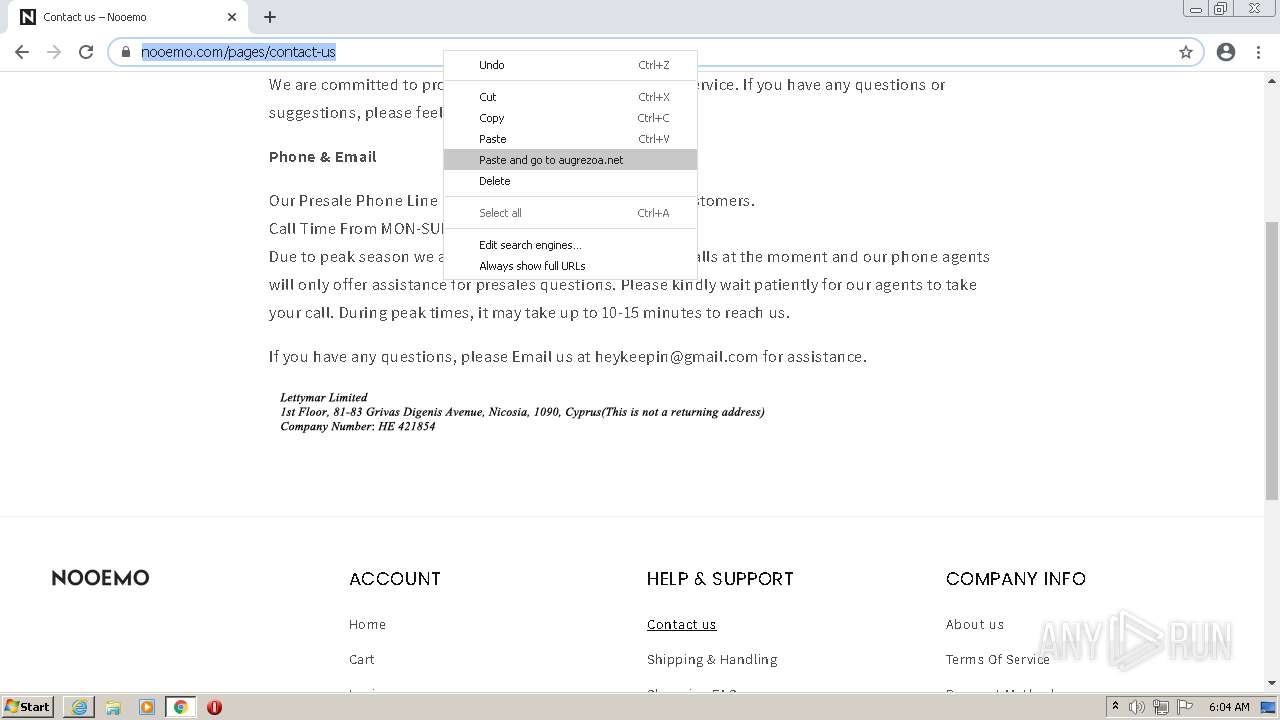
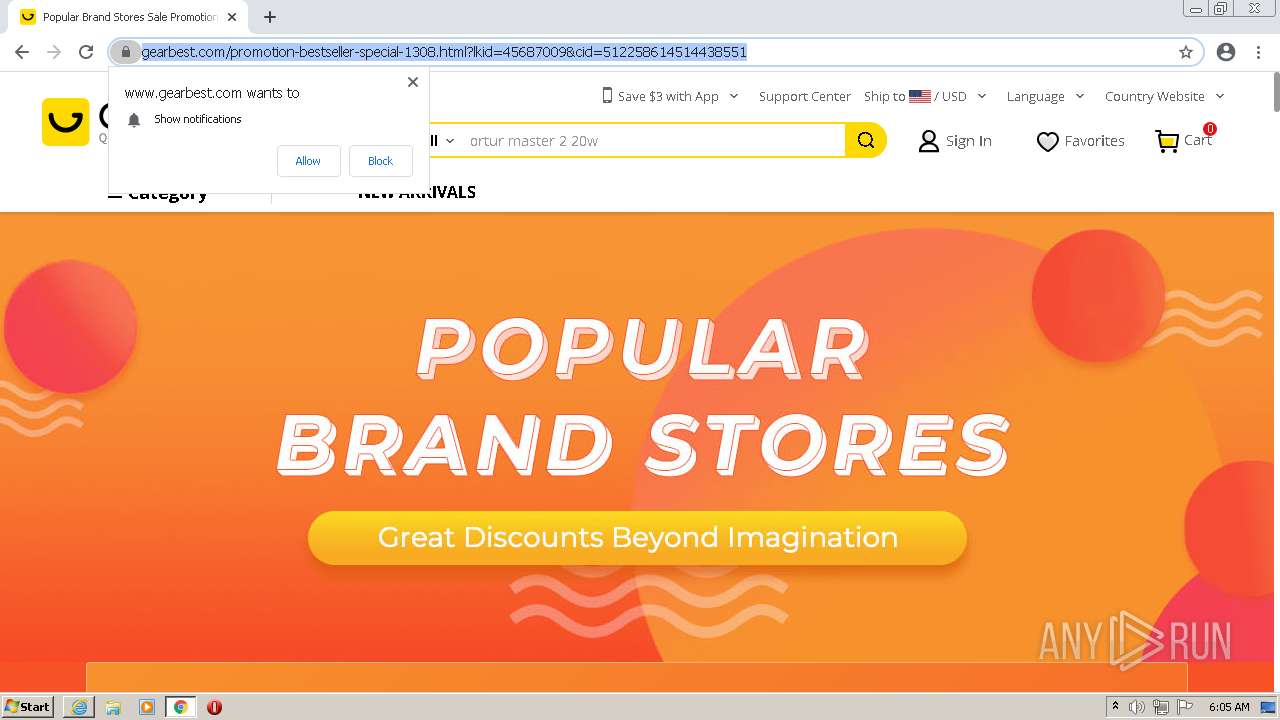
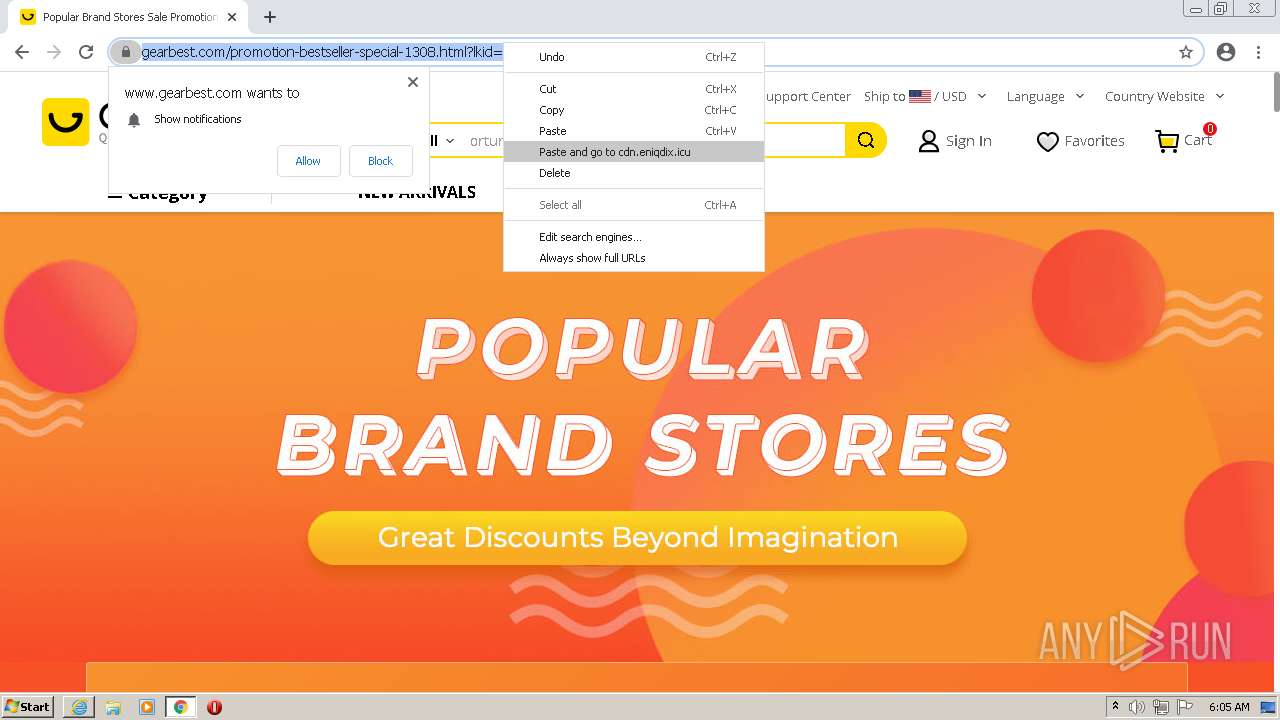
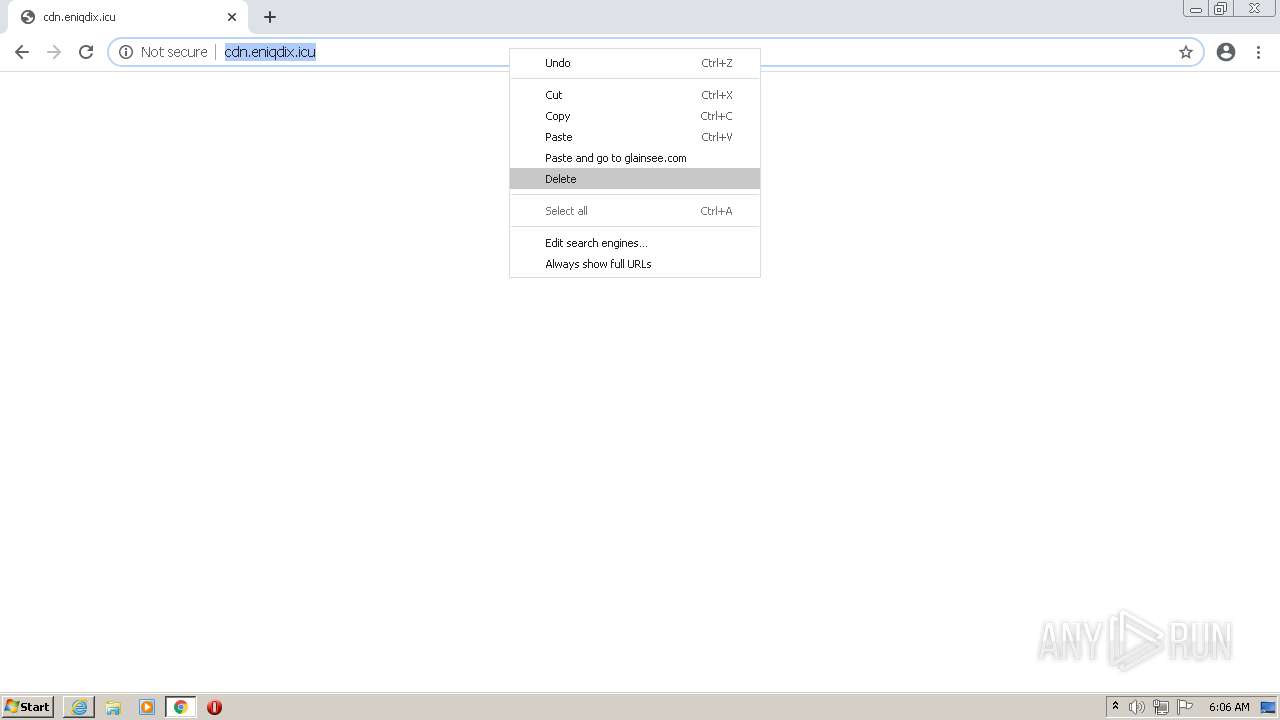
| URL: | http://www.nooemo.com/ |
| Full analysis: | https://app.any.run/tasks/b6cbd856-14d3-4e5c-bd08-8b414c67fbcc |
| Verdict: | Malicious activity |
| Analysis date: | February 01, 2022, 06:03:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4ED9DD7AD205156468799943BC20779E |
| SHA1: | 290A5844C3F529DC9BD7340F59F8C1ACCB2036CD |
| SHA256: | 0993725295BD667F253173A325F1BE310FACC36DEC98CB30BDE7404C6063665B |
| SSDEEP: | 3:N1KJS4+bJ3:Cc4+bd |
MALICIOUS
Connects to CnC server
- chrome.exe (PID: 2424)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3404)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3852)
INFO
Application launched itself
- iexplore.exe (PID: 2916)
- chrome.exe (PID: 3852)
Reads the computer name
- iexplore.exe (PID: 2916)
- iexplore.exe (PID: 3404)
- chrome.exe (PID: 3852)
- chrome.exe (PID: 2356)
- chrome.exe (PID: 2424)
- chrome.exe (PID: 2100)
- chrome.exe (PID: 3936)
- chrome.exe (PID: 1108)
- chrome.exe (PID: 3324)
- chrome.exe (PID: 316)
- chrome.exe (PID: 3840)
Checks supported languages
- iexplore.exe (PID: 2916)
- iexplore.exe (PID: 3404)
- chrome.exe (PID: 3852)
- chrome.exe (PID: 1128)
- chrome.exe (PID: 2356)
- chrome.exe (PID: 2424)
- chrome.exe (PID: 3020)
- chrome.exe (PID: 2896)
- chrome.exe (PID: 3928)
- chrome.exe (PID: 1276)
- chrome.exe (PID: 3644)
- chrome.exe (PID: 2100)
- chrome.exe (PID: 2832)
- chrome.exe (PID: 3668)
- chrome.exe (PID: 3444)
- chrome.exe (PID: 3936)
- chrome.exe (PID: 1952)
- chrome.exe (PID: 3644)
- chrome.exe (PID: 1044)
- chrome.exe (PID: 1108)
- chrome.exe (PID: 3324)
- chrome.exe (PID: 316)
- chrome.exe (PID: 3936)
- chrome.exe (PID: 3840)
- chrome.exe (PID: 316)
- chrome.exe (PID: 1780)
- chrome.exe (PID: 2312)
- chrome.exe (PID: 2792)
- chrome.exe (PID: 2276)
- chrome.exe (PID: 3240)
- chrome.exe (PID: 3012)
- chrome.exe (PID: 3208)
- chrome.exe (PID: 3112)
- chrome.exe (PID: 2076)
- chrome.exe (PID: 3480)
- chrome.exe (PID: 2464)
- chrome.exe (PID: 3200)
- chrome.exe (PID: 2024)
- chrome.exe (PID: 344)
- chrome.exe (PID: 496)
Changes internet zones settings
- iexplore.exe (PID: 2916)
Reads settings of System Certificates
- iexplore.exe (PID: 3404)
- iexplore.exe (PID: 2916)
- chrome.exe (PID: 2424)
Reads internet explorer settings
- iexplore.exe (PID: 3404)
Checks Windows Trust Settings
- iexplore.exe (PID: 3404)
- iexplore.exe (PID: 2916)
Creates files in the user directory
- iexplore.exe (PID: 3404)
- iexplore.exe (PID: 2916)
Manual execution by user
- chrome.exe (PID: 3852)
Reads the hosts file
- chrome.exe (PID: 3852)
- chrome.exe (PID: 2424)
Changes settings of System certificates
- iexplore.exe (PID: 2916)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2916)
Reads the date of Windows installation
- chrome.exe (PID: 3324)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 3852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
77
Monitored processes
40
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1032,6764775606734486744,5716473034717898300,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1696 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1032,6764775606734486744,5716473034717898300,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1844 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 344 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,6764775606734486744,5716473034717898300,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=35 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1500 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,6764775606734486744,5716473034717898300,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=36 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3560 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1044 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,6764775606734486744,5716473034717898300,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3296 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1108 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1032,6764775606734486744,5716473034717898300,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2532 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6b0ed988,0x6b0ed998,0x6b0ed9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1032,6764775606734486744,5716473034717898300,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2960 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,6764775606734486744,5716473034717898300,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3472 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,6764775606734486744,5716473034717898300,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3536 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
27 239
Read events
26 949
Write events
278
Delete events
12
Modification events
| (PID) Process: | (2916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30938929 | |||
| (PID) Process: | (2916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30938929 | |||
| (PID) Process: | (2916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
286
Text files
278
Unknown types
27
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3404 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3404 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3404 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 3404 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\3IHJHQLL.txt | text | |
MD5:— | SHA256:— | |||
| 3404 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F09491AFC5F9532D452145232E8C87DB | binary | |
MD5:— | SHA256:— | |||
| 3404 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 3404 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\J4G4QLE8.txt | text | |
MD5:— | SHA256:— | |||
| 3404 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\7WIH3YVN.txt | text | |
MD5:— | SHA256:— | |||
| 3404 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\OIJVQL66.htm | html | |
MD5:— | SHA256:— | |||
| 3404 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F09491AFC5F9532D452145232E8C87DB | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
57
TCP/UDP connections
154
DNS requests
111
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
884 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3 | US | — | — | whitelisted |
3404 | iexplore.exe | GET | — | 142.250.185.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | — | — | whitelisted |
3404 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGCDPAjbzpoUYuu%2B39wE%3D | US | der | 1.40 Kb | whitelisted |
3404 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3404 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
3404 | iexplore.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
3404 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/ca/gsatlasr3dvtlsca2020/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQT6XbZiiF%2BR%2FUEno7LSD4H4YmN6gQUQm1XLU8fJnd0pidk9oD6j0ho%2FnwCEAGrku%2BpBhGd5lfvJANOlbM%3D | US | der | 1.42 Kb | whitelisted |
3404 | iexplore.exe | GET | 200 | 95.101.89.24:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgTeCRHvtod4uXVxWEN8sZ3Jpg%3D%3D | unknown | der | 503 b | shared |
3404 | iexplore.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEEFKxQHtEPcBCgAAAAErfHU%3D | US | der | 471 b | whitelisted |
2916 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.68 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3404 | iexplore.exe | 23.227.38.74:80 | www.nooemo.com | Shopify, Inc. | CA | malicious |
3404 | iexplore.exe | 23.227.38.74:443 | www.nooemo.com | Shopify, Inc. | CA | malicious |
3404 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3404 | iexplore.exe | 104.89.32.83:80 | x1.c.lencr.org | Akamai Technologies, Inc. | NL | suspicious |
2916 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3404 | iexplore.exe | 95.101.89.24:80 | r3.o.lencr.org | Akamai International B.V. | — | unknown |
2916 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3404 | iexplore.exe | 104.18.20.226:80 | ocsp2.globalsign.com | Cloudflare Inc | US | shared |
3404 | iexplore.exe | 151.101.129.12:443 | cdn.shopify.com | Fastly | US | unknown |
3404 | iexplore.exe | 104.18.21.226:80 | ocsp2.globalsign.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.nooemo.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
ocsp.digicert.com |
| whitelisted |
cdn.shopify.com |
| whitelisted |
monorail-edge.shopifysvc.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2424 | chrome.exe | A Network Trojan was detected | ET MALWARE Win32/Adware.Agent.NSU CnC Activity M2 |
— | — | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
2424 | chrome.exe | A Network Trojan was detected | ET MALWARE Win32/Adware.Agent.NSU CnC Activity M2 |