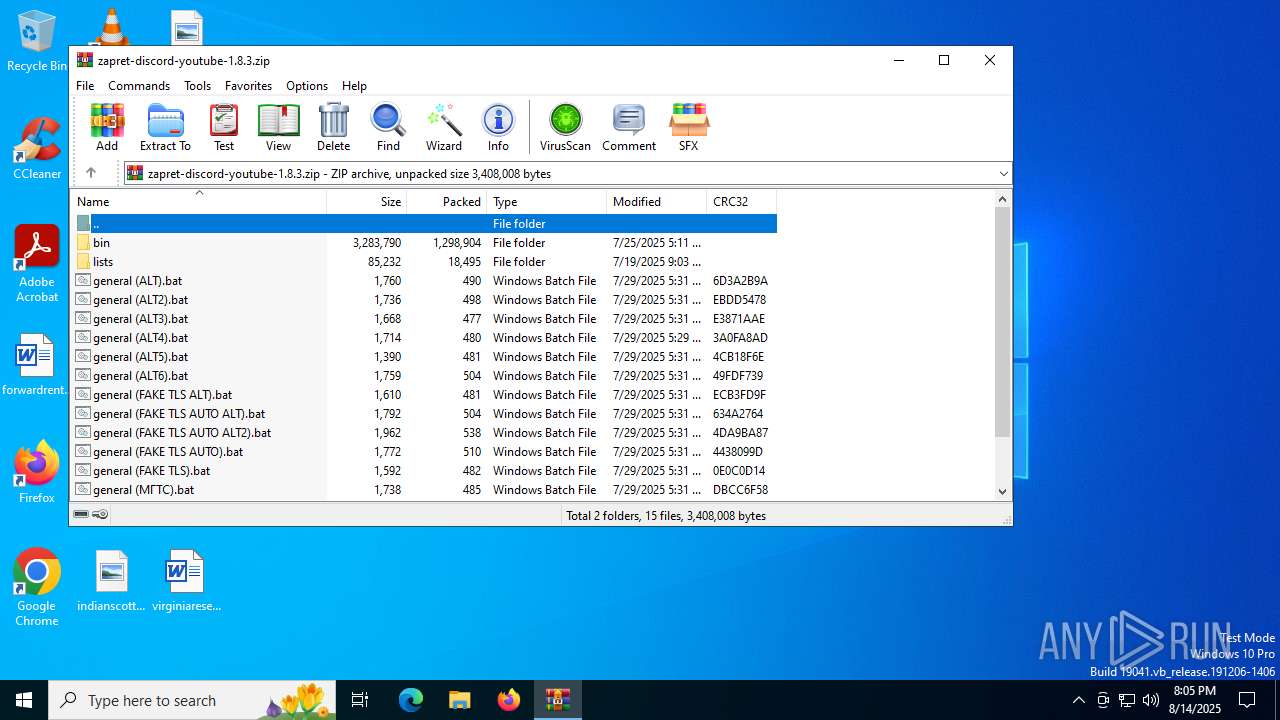
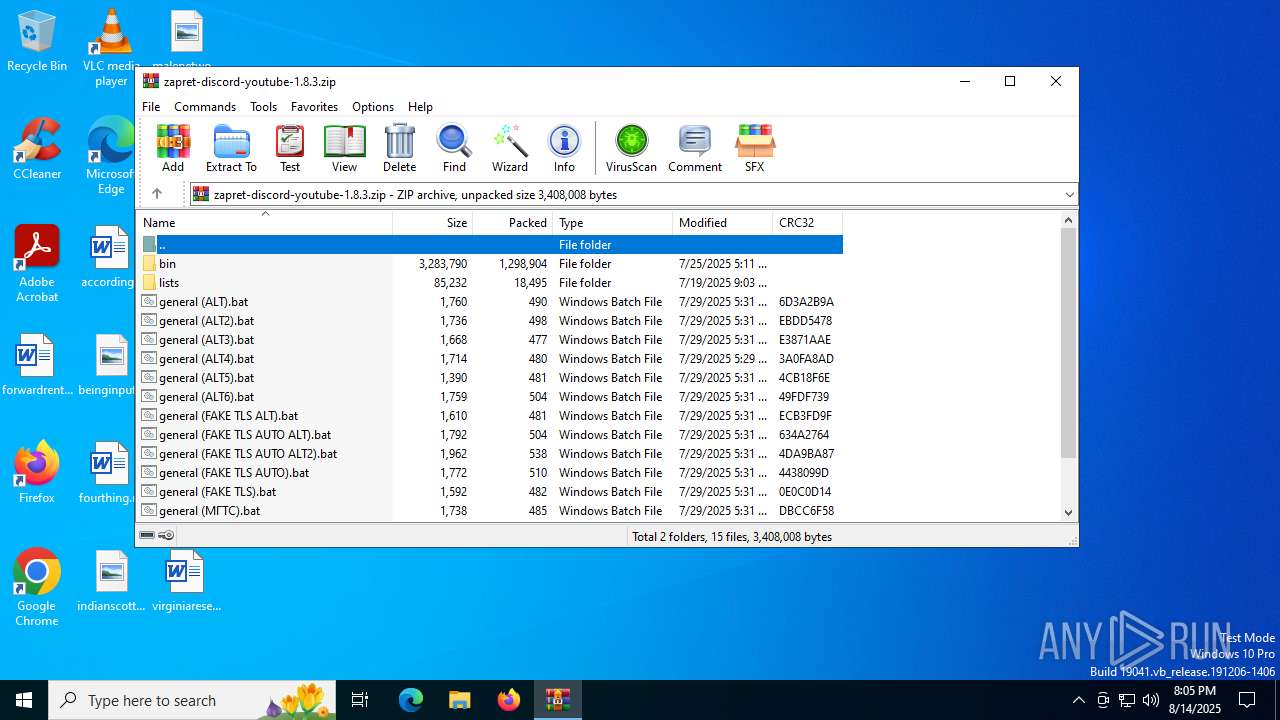
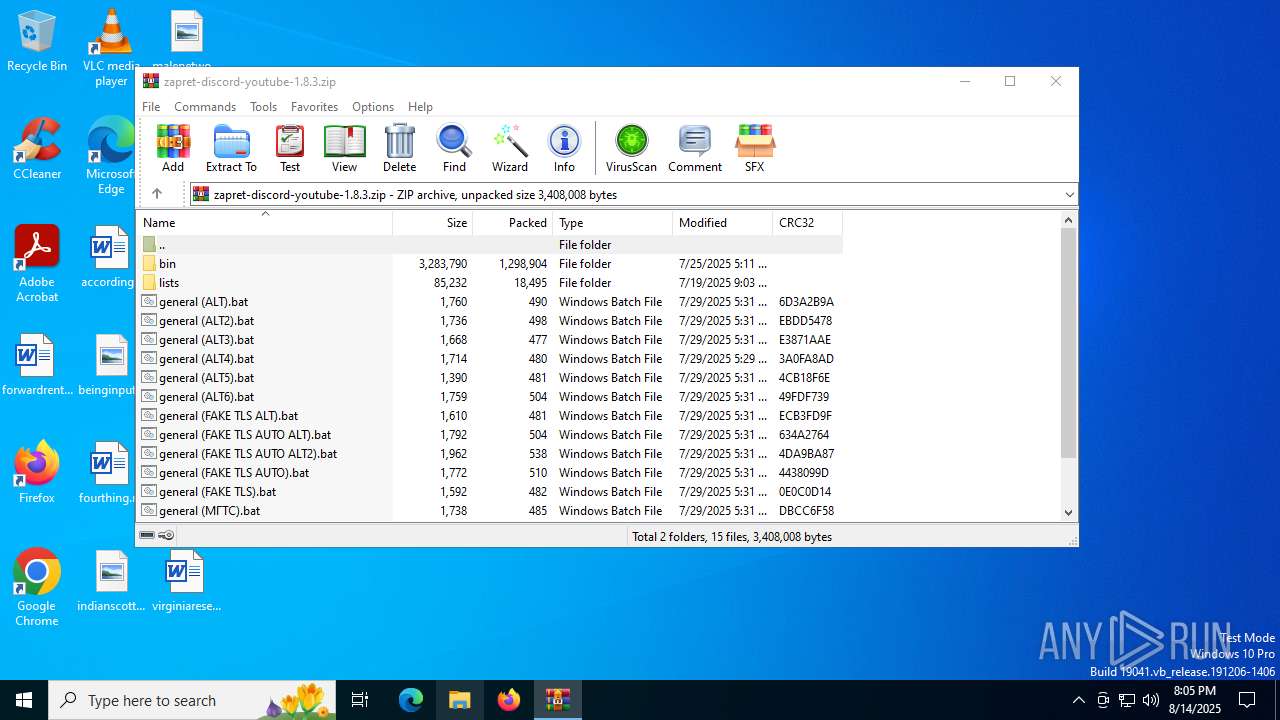
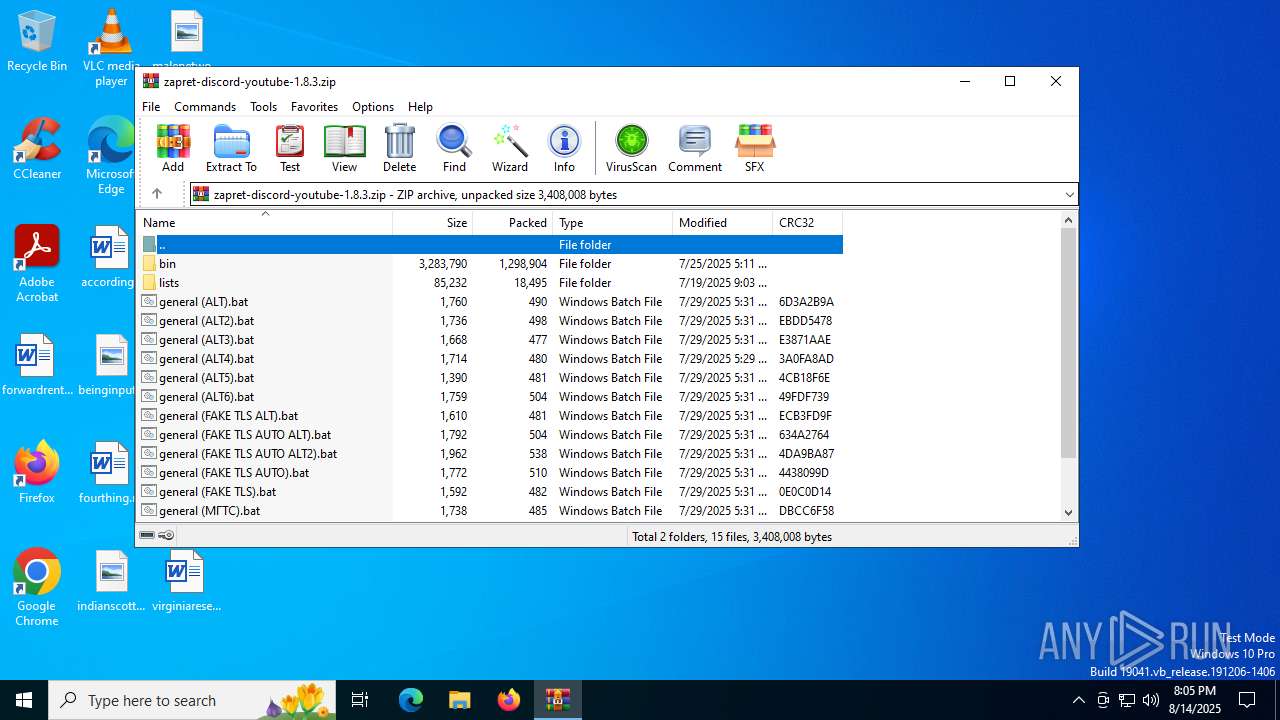
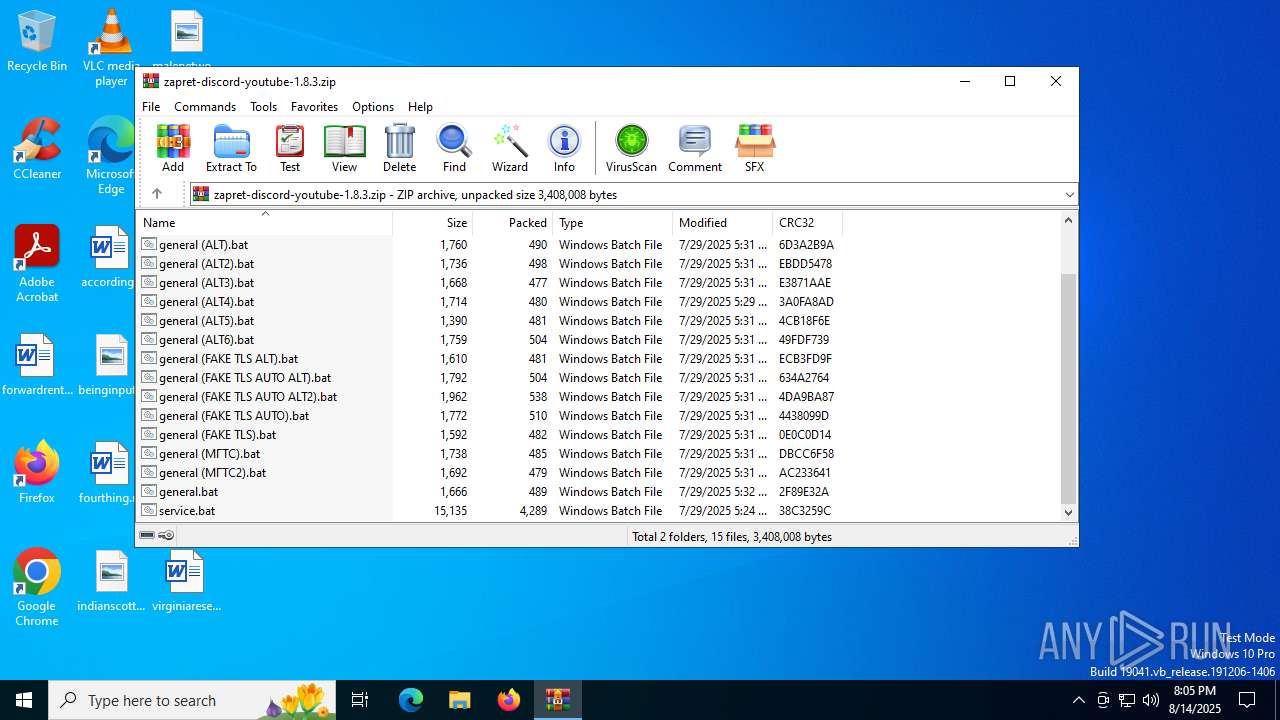
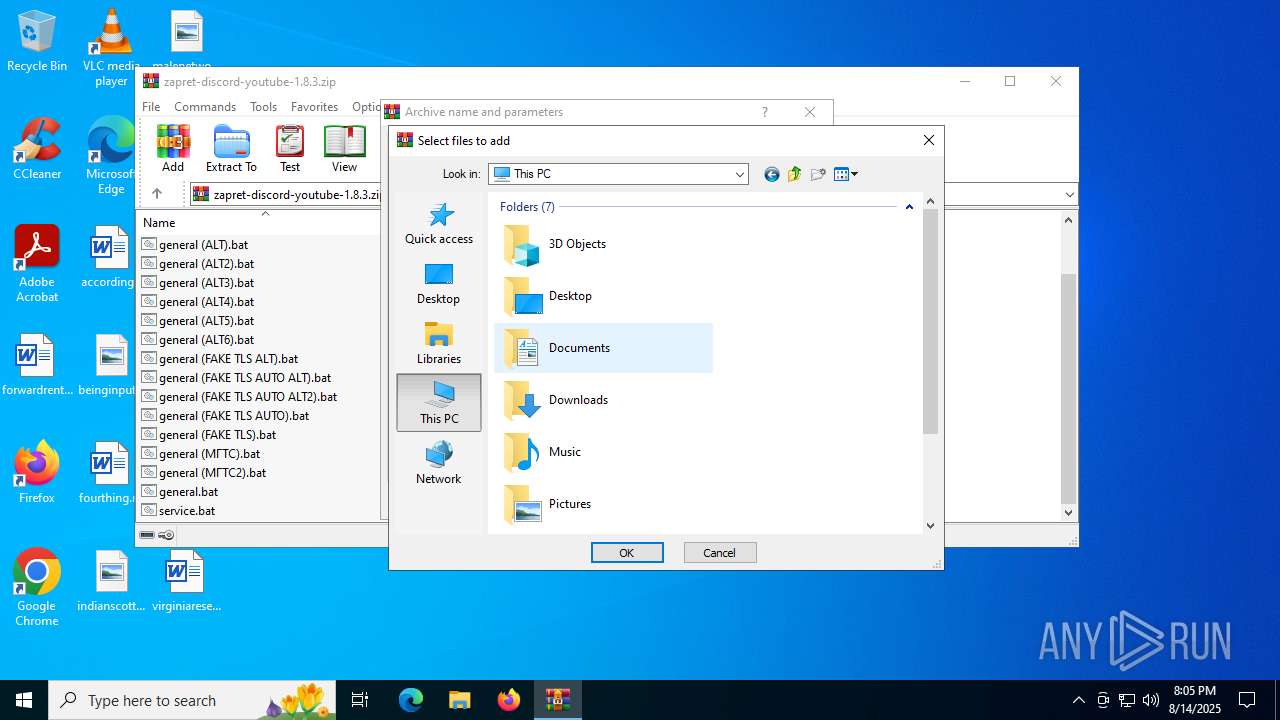
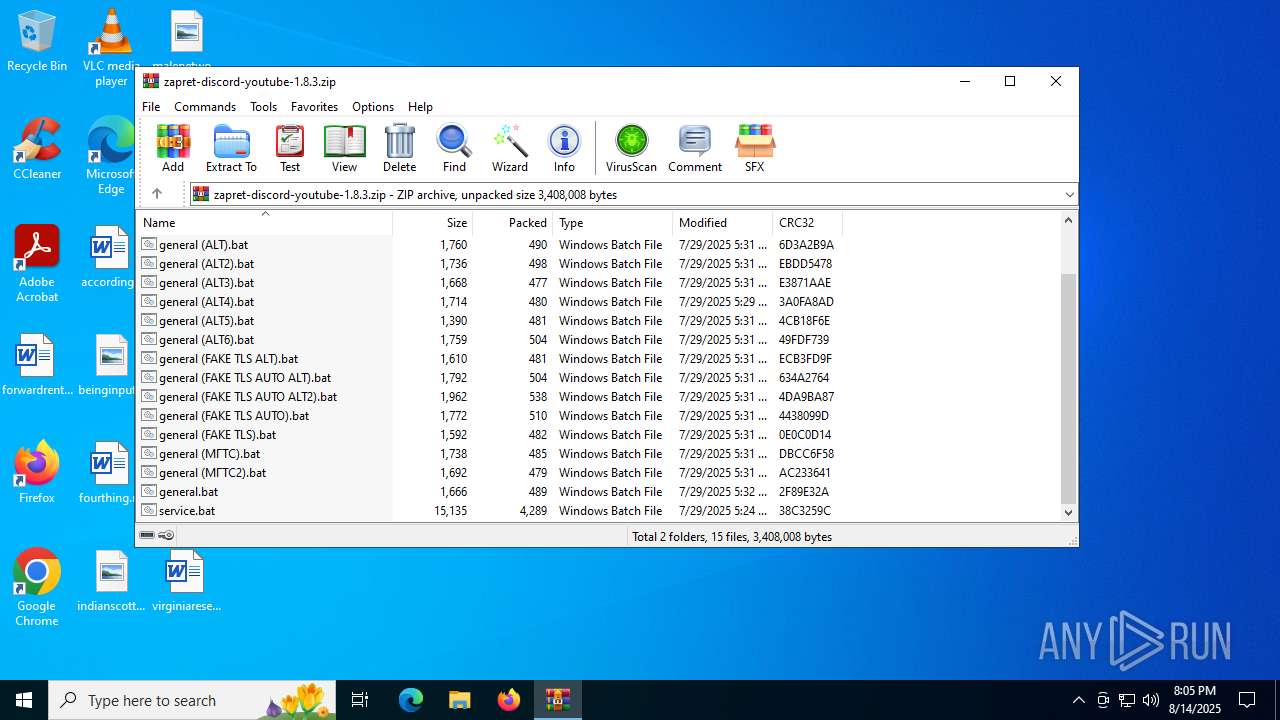
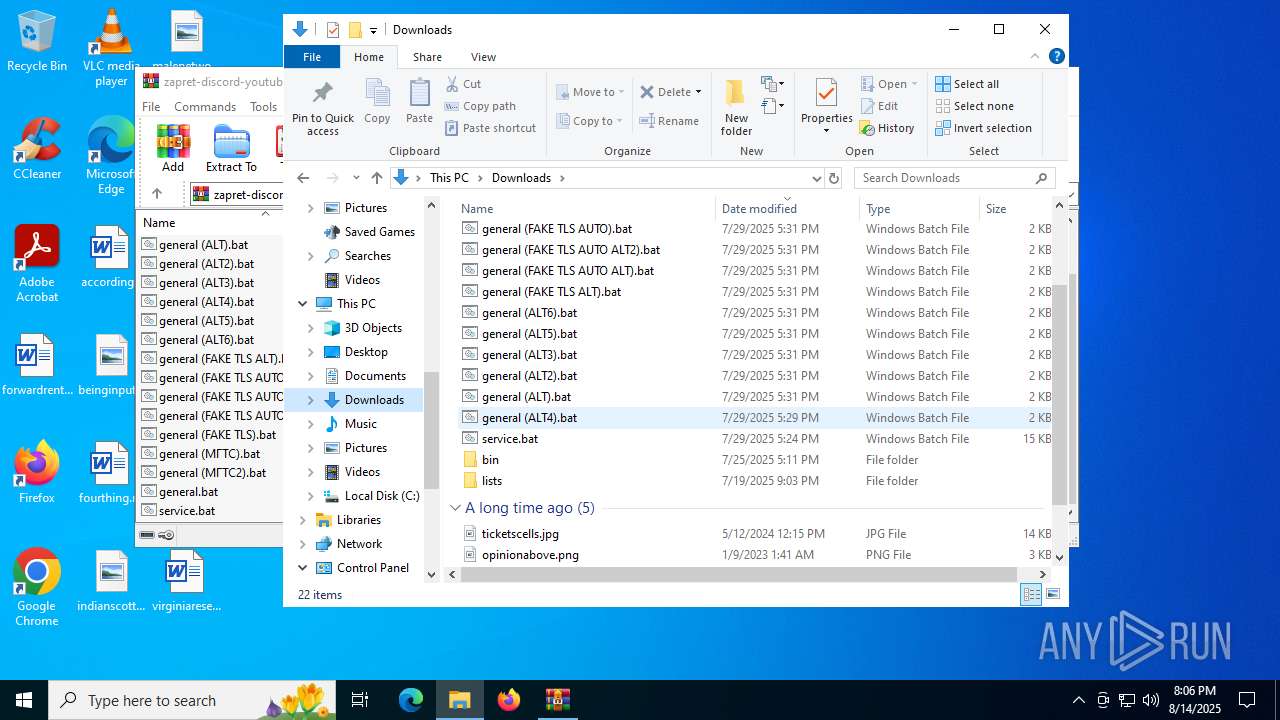
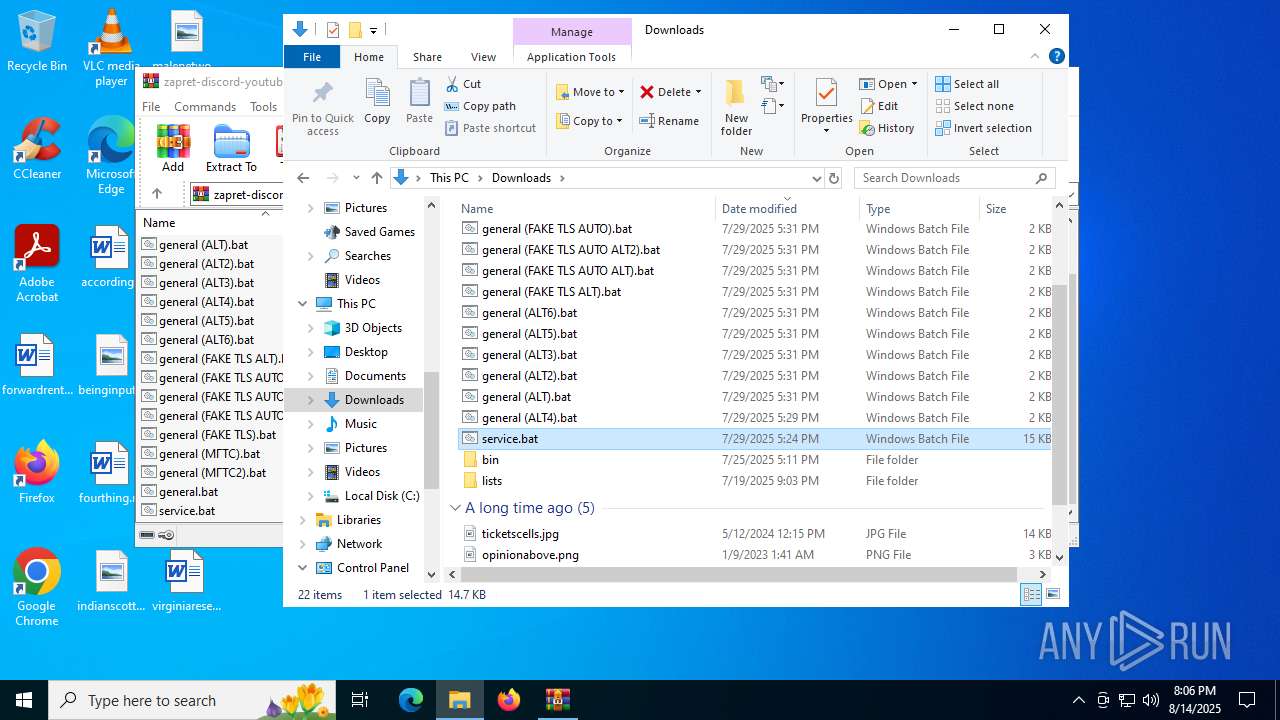
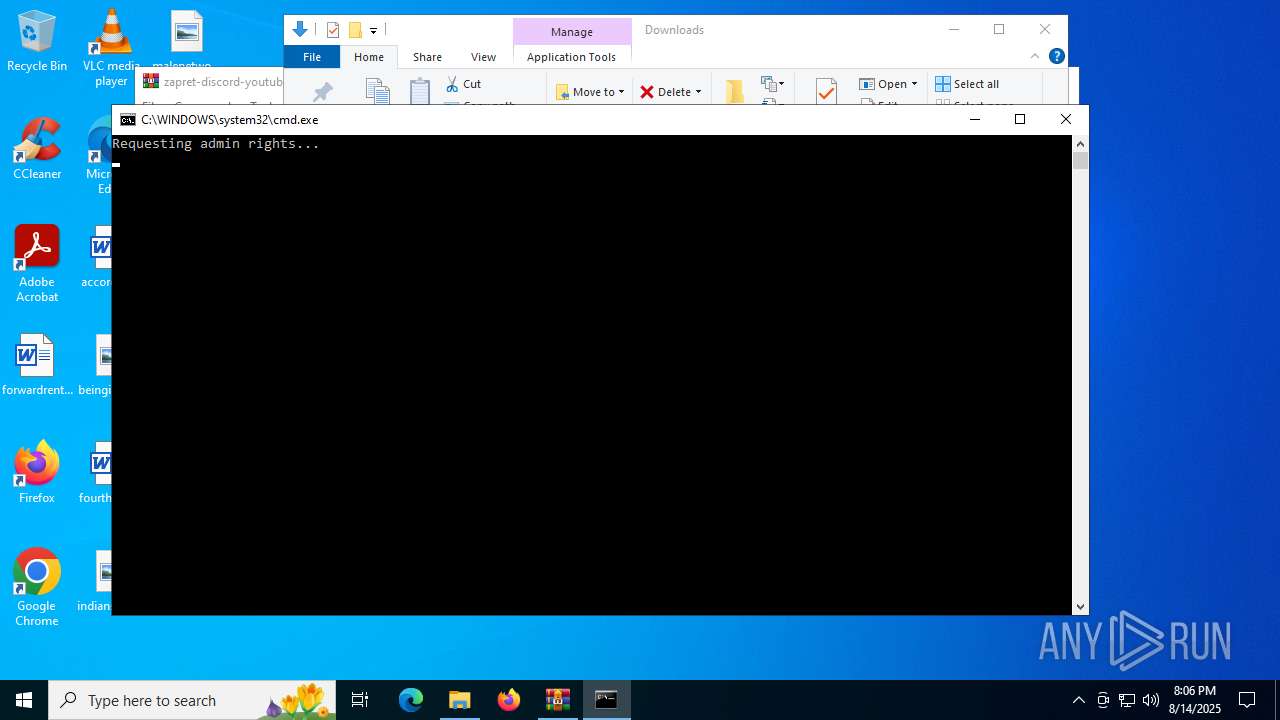
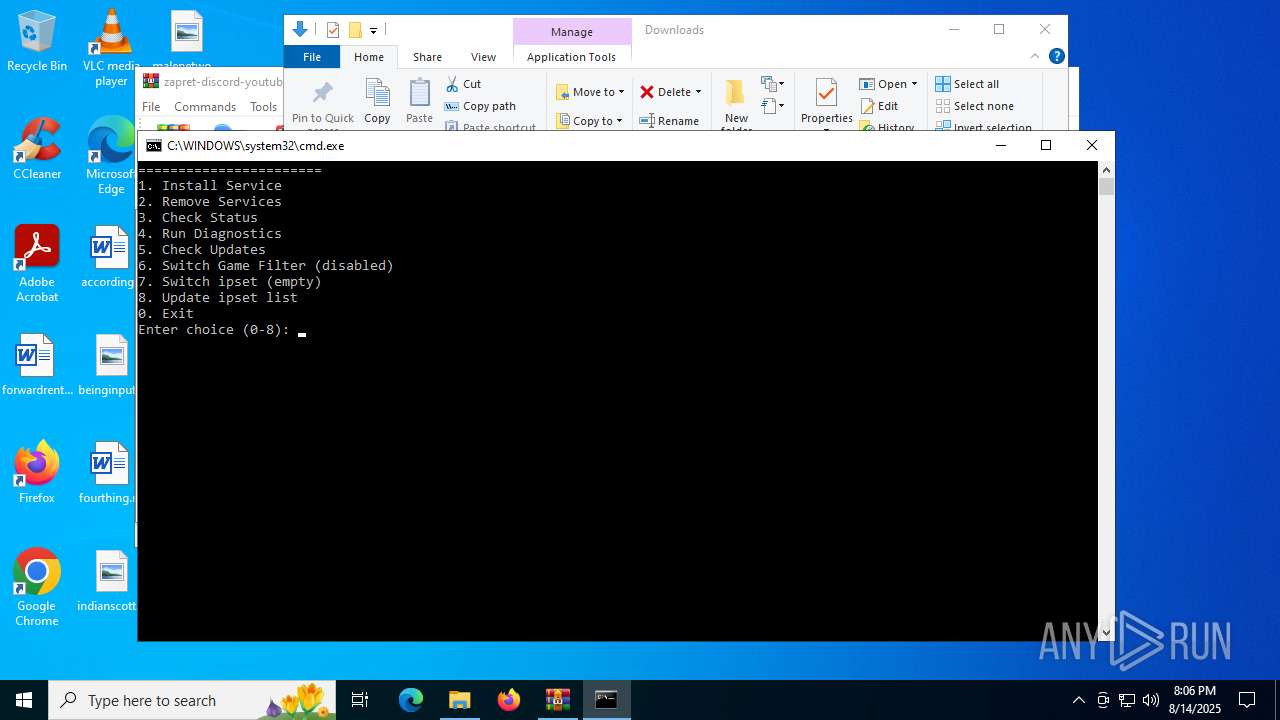
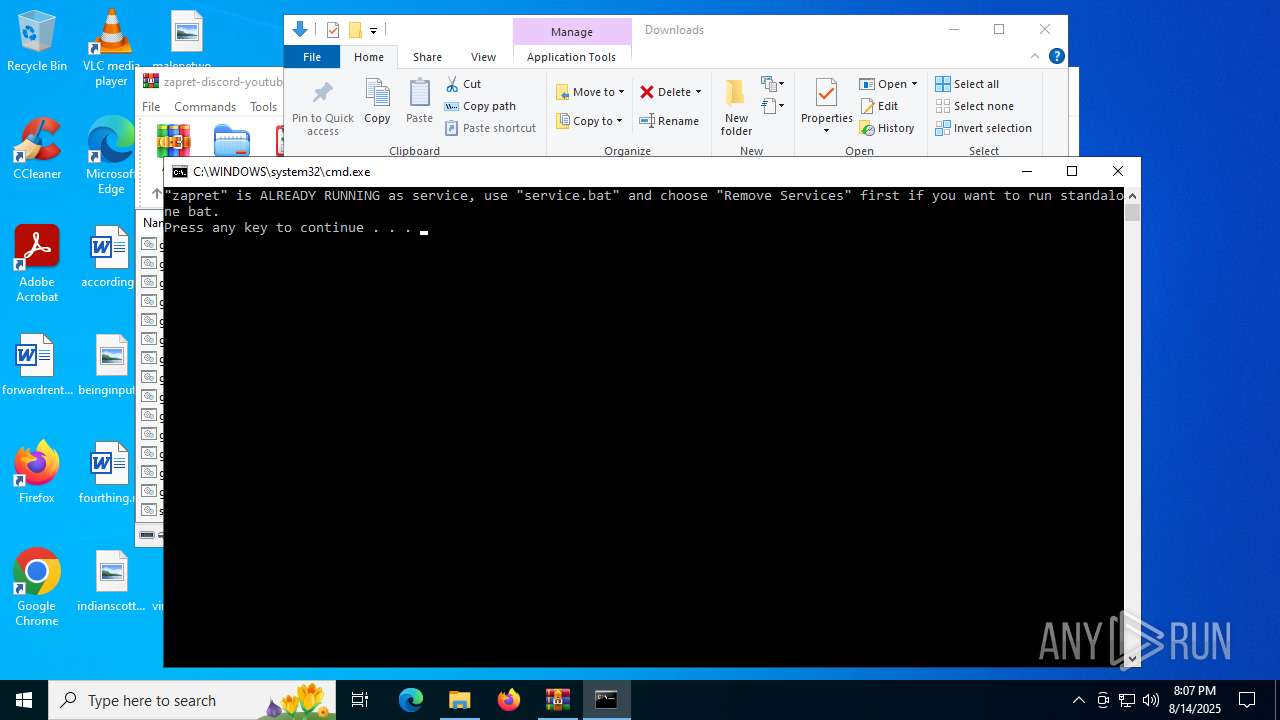
| File name: | zapret-discord-youtube-1.8.3.zip |
| Full analysis: | https://app.any.run/tasks/28027020-cdf0-4394-a0d2-b88d1da19cae |
| Verdict: | Malicious activity |
| Analysis date: | August 14, 2025, 20:05:01 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | A6D631D221D3F2FE835B4E7B937FDD68 |
| SHA1: | 387D31F71DE13382BF48906484E87A01DF8D25AE |
| SHA256: | 0983566889F26AB9C0741ED2B549CC793EB922B99D6B993640FA8F6E7B84E922 |
| SSDEEP: | 49152:wvw/Cv8X9eQS0s7eWvRlefNYLw1yD1LE6tVz64qEu1KufrHNW3FzmUS74G6+hefM:N/e8teQzUJRlSNYLeyD1DhdqCirtW3FK |
MALICIOUS
Detects Cygwin installation
- WinRAR.exe (PID: 4320)
Starts NET.EXE for service management
- cmd.exe (PID: 3940)
- net.exe (PID: 1204)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5744)
- cmd.exe (PID: 4788)
Starts process via Powershell
- powershell.exe (PID: 5684)
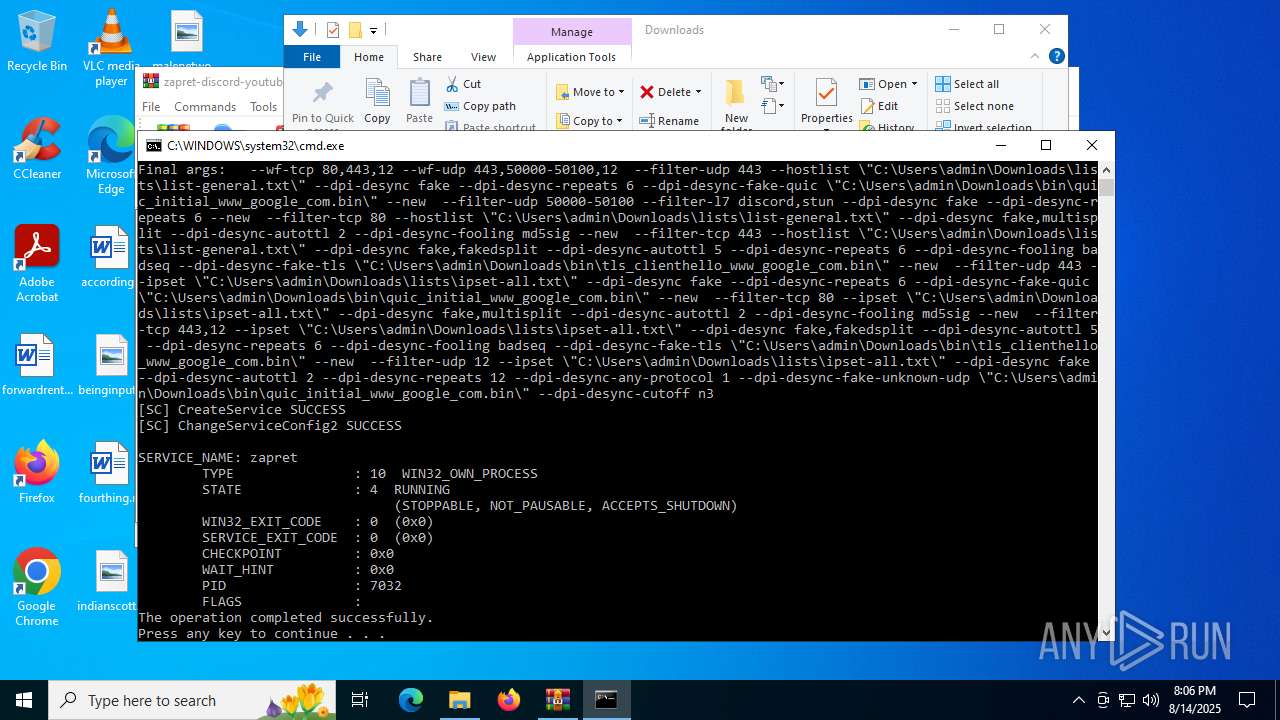
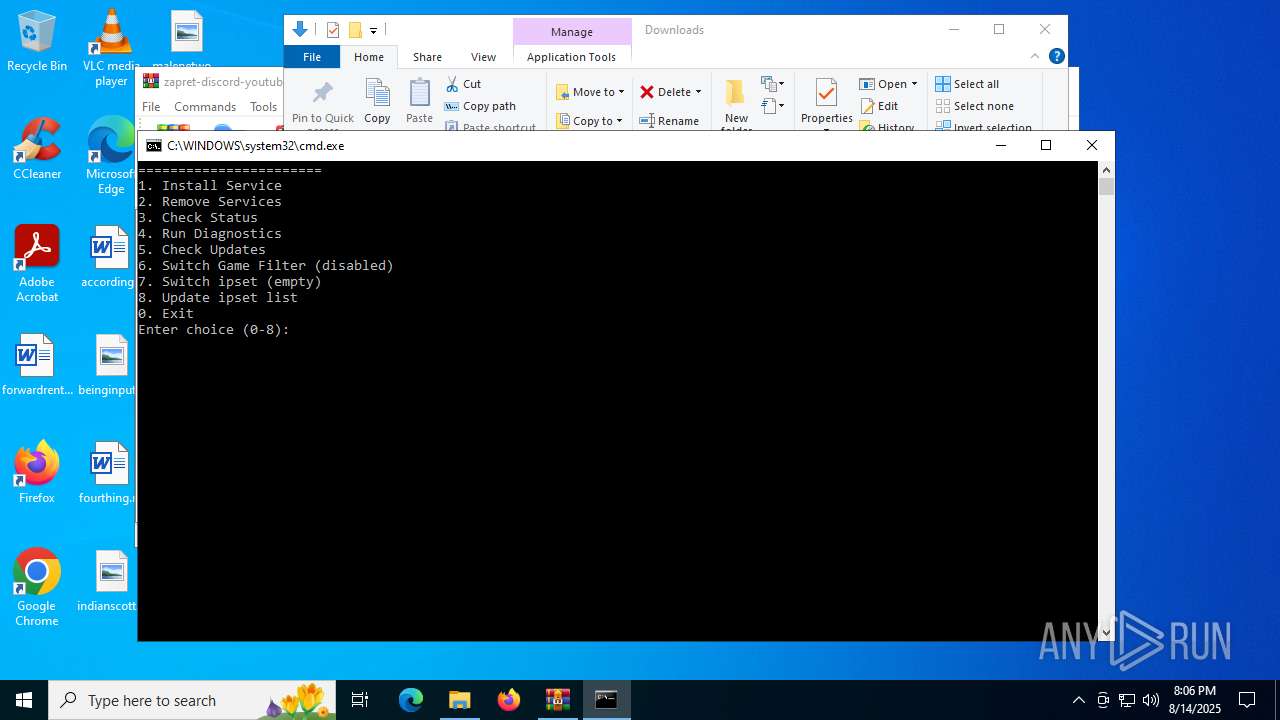
Executing commands from a ".bat" file
- powershell.exe (PID: 5684)
- cmd.exe (PID: 3940)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 4320)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 5684)
- cmd.exe (PID: 3940)
- cmd.exe (PID: 2804)
- cmd.exe (PID: 2128)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3940)
- cmd.exe (PID: 6240)
Application launched itself
- cmd.exe (PID: 3940)
- cmd.exe (PID: 2128)
- cmd.exe (PID: 2804)
Starts application with an unusual extension
- cmd.exe (PID: 3940)
- cmd.exe (PID: 2128)
- cmd.exe (PID: 2804)
Hides command output
- cmd.exe (PID: 2356)
- cmd.exe (PID: 4788)
Windows service management via SC.EXE
- sc.exe (PID: 3840)
- sc.exe (PID: 6228)
- sc.exe (PID: 3896)
- sc.exe (PID: 620)
Starts SC.EXE for service management
- cmd.exe (PID: 3940)
- cmd.exe (PID: 6240)
Creates a new Windows service
- sc.exe (PID: 3740)
Executes as Windows Service
- winws.exe (PID: 7032)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3940)
Creates or modifies Windows services
- reg.exe (PID: 2040)
INFO
Manual execution by a user
- cmd.exe (PID: 5744)
- cmd.exe (PID: 2804)
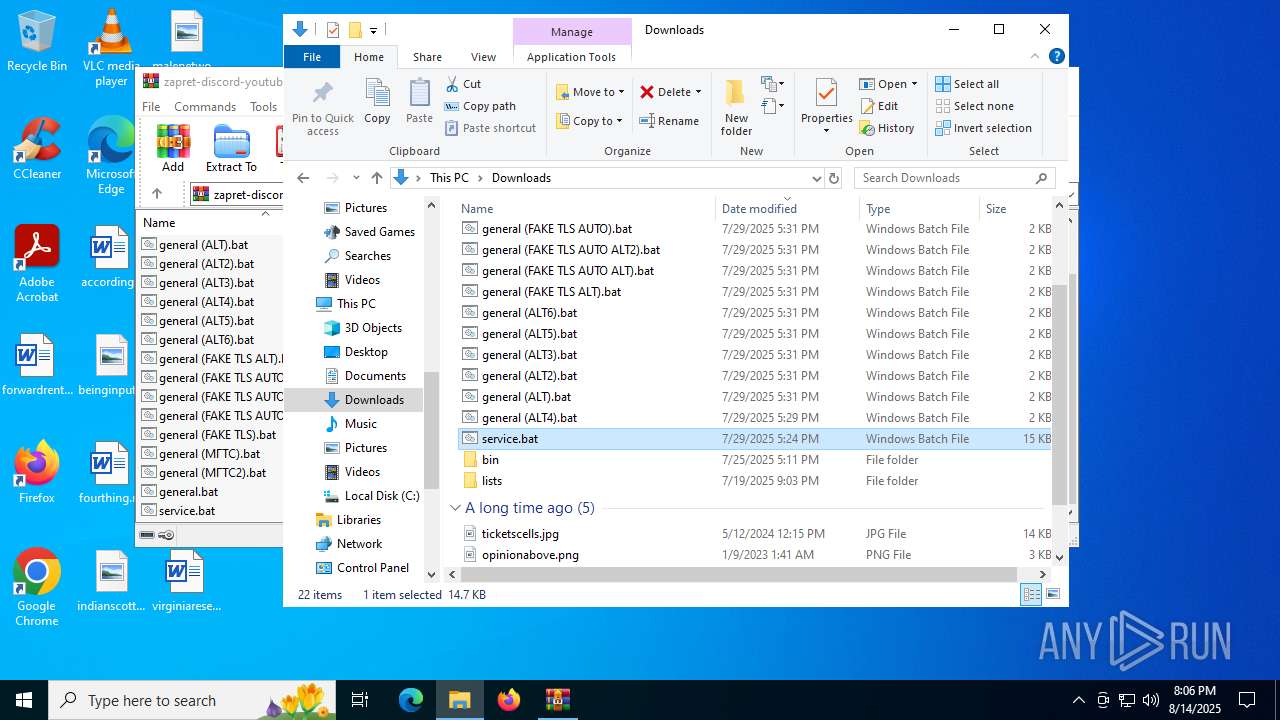
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4320)
The sample compiled with english language support
- WinRAR.exe (PID: 4320)
Checks supported languages
- chcp.com (PID: 4512)
- chcp.com (PID: 984)
- chcp.com (PID: 5436)
- winws.exe (PID: 7032)
- chcp.com (PID: 3876)
- chcp.com (PID: 6236)
- chcp.com (PID: 4456)
- chcp.com (PID: 7052)
- winws.exe (PID: 3584)
- chcp.com (PID: 2216)
Changes the display of characters in the console
- cmd.exe (PID: 3940)
- cmd.exe (PID: 2128)
- cmd.exe (PID: 2804)
Reads the software policy settings
- slui.exe (PID: 7140)
Checks proxy server information
- slui.exe (PID: 7140)
- powershell.exe (PID: 2728)
Reads the computer name
- winws.exe (PID: 7032)
- winws.exe (PID: 3584)
Disables trace logs
- powershell.exe (PID: 2728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:07:25 20:11:04 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
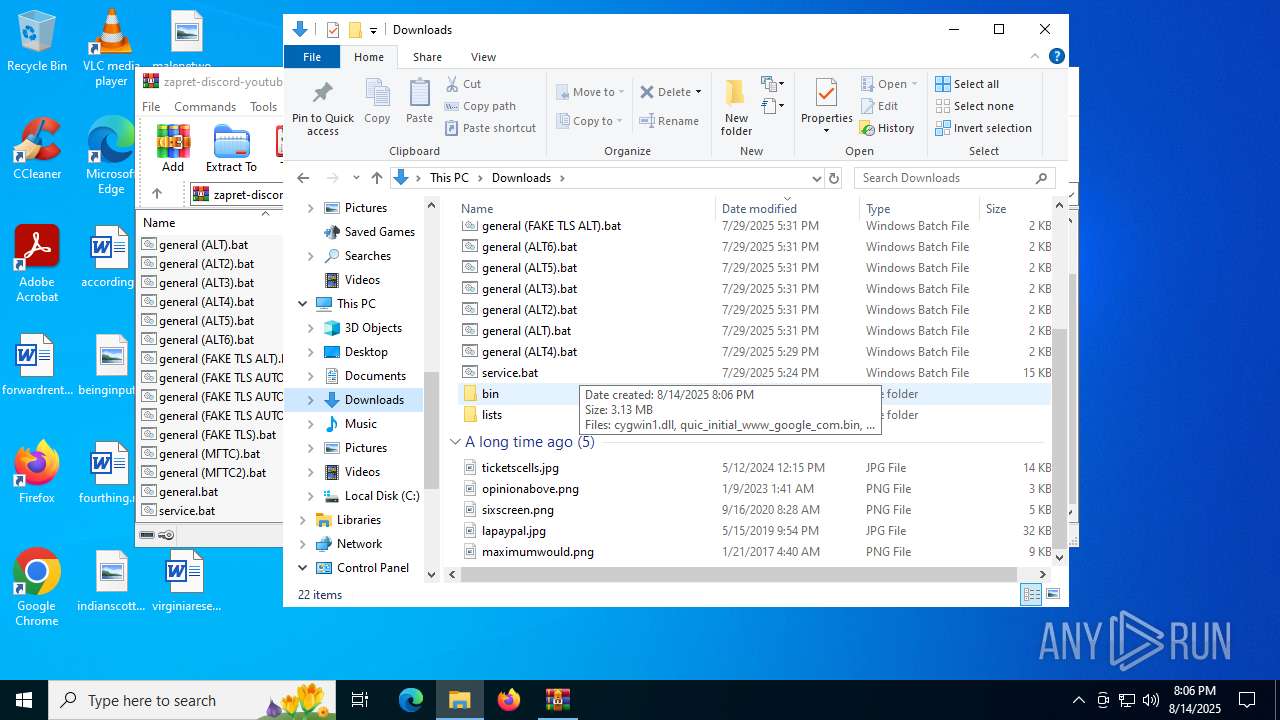
| ZipFileName: | bin/ |
Total processes
248
Monitored processes
103
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 72 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo %BIN%quic_initial_www_google_com.bin " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo %LISTS%ipset-all.txt " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 304 | findstr ":" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 620 | sc query "zapret" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | findstr ":" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo --filter-udp=443 --hostlist="%LISTS%list-general.txt" --dpi-desync=fake --dpi-desync-repeats=6 --dpi-desync-fake-quic="%BIN%quic_initial_www_google_com.bin" --new ^ " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | findstr /i "winws.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 984 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 984 | findstr ":" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1028 | findstr ":" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 846
Read events
16 691
Write events
123
Delete events
32
Modification events
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\zapret-discord-youtube-1.8.3.zip | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0E00000004000000030000000000000011000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
Executable files
4
Suspicious files
3
Text files
22
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4320 | WinRAR.exe | C:\Users\admin\Downloads\bin\quic_initial_www_google_com.bin | binary | |
MD5:312526D39958D89B1F8AB67789AB985F | SHA256:F4589C57749F956BB30538197A521D7005F8B0A8723B4707E72405E51DDAC50A | |||
| 4320 | WinRAR.exe | C:\Users\admin\Downloads\bin\cygwin1.dll | executable | |
MD5:A1C82ED072DC079DD7851F82D9AA7678 | SHA256:103104A52E5293CE418944725DF19E2BF81AD9269B9A120D71D39028E821499B | |||
| 4320 | WinRAR.exe | C:\Users\admin\Downloads\bin\tls_clienthello_www_google_com.bin | binary | |
MD5:41E47557F16690DF1781F67C8712714E | SHA256:F966351AE376963DFFBCB5B94256872649B9CDAAB8C5175025936FA50E07DC19 | |||
| 4320 | WinRAR.exe | C:\Users\admin\Downloads\general (ALT2).bat | text | |
MD5:779EB1CC5877DD178ED4E05C96870039 | SHA256:76BD39660FC381E4D503CD3E58E2E4450C835F5A2937D2265D7E2981FCB0336E | |||
| 4320 | WinRAR.exe | C:\Users\admin\Downloads\general (ALT).bat | text | |
MD5:CE07E7D887AA3436333DDE1F829BDC0A | SHA256:7429D33CC50966FBB81FB73F6EF04D19E33C2ED6A79F27CAEA1F20FC35236BD8 | |||
| 4320 | WinRAR.exe | C:\Users\admin\Downloads\bin\WinDivert.dll | executable | |
MD5:B2014D33EE645112D5DC16FE9D9FCBFF | SHA256:C1E060EE19444A259B2162F8AF0F3FE8C4428A1C6F694DCE20DE194AC8D7D9A2 | |||
| 4320 | WinRAR.exe | C:\Users\admin\Downloads\general (МГТС).bat | text | |
MD5:E2BAF0CCAF077C25B9FBBD038CDD1EF7 | SHA256:24F39838BFE6A63D11518E4D702BB721D785D2A2AB901CFBC94B420A1DF791F2 | |||
| 4320 | WinRAR.exe | C:\Users\admin\Downloads\general (FAKE TLS AUTO).bat | text | |
MD5:84F88648F6B2D68B88E0325FD40F8429 | SHA256:08A95CB237E4D4A5C753E7F8D21AEFDBBC79976F242533D3E18272E763AC3ECF | |||
| 4320 | WinRAR.exe | C:\Users\admin\Downloads\general (МГТС2).bat | text | |
MD5:BCB1EF8E77620113ECFAE2424190BDE8 | SHA256:F9D873FC09F0852245E7ED67B0213FA2E08F21AF29C8F158064C04AB85F90062 | |||
| 4320 | WinRAR.exe | C:\Users\admin\Downloads\general (FAKE TLS).bat | text | |
MD5:DCA4E32491E58815FBC3A0D4C0C1C349 | SHA256:3E0FD76E3BB65F65A692A3E40DEF8ED2E89437BF63E0FB1BD8A075213A5702C2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
25
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
504 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3840 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3840 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 104.76.201.34:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
3976 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6900 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.55.110.211:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
504 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
504 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |