| download: | survey-2020-early.jpag |
| Full analysis: | https://app.any.run/tasks/4bb57549-2ef6-4bd5-880b-fa22781aaefe |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 07:46:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | image/jpeg |
| File info: | JPEG image data, Exif standard: [TIFF image data, big-endian, direntries=12, height=289, bps=0, PhotometricIntepretation=RGB, orientation=upper-left, width=400], progressive, precision 8, 400x353, components 3 |
| MD5: | C14110BF7867EB0AEA11ABAD6FBD1262 |
| SHA1: | 0577561C01E48356E1A3ED2CA8569C9D4589C353 |
| SHA256: | 096987E7EF0DC00A8555DBDD33F1972ACF7B61083EFA522BCAB73FE6ABE55BB7 |
| SSDEEP: | 3072:fm/A8Jm/A8tXs+RsVJAs4UhWGHjx/NojBV4kjAkeP6:oOtXslAs4UnHjx/Nor4kZ |
MALICIOUS
The DLL Hijacking
- DllHost.exe (PID: 2440)
- rundll32.exe (PID: 3440)
SUSPICIOUS
No suspicious indicators.INFO
Reads the machine GUID from the registry
- DllHost.exe (PID: 2440)
Creates files in the user directory
- DllHost.exe (PID: 2440)
Manual execution by user
- rundll32.exe (PID: 2684)
- NOTEPAD.EXE (PID: 3644)
- ntvdm.exe (PID: 1280)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jpg | | | JFIF-EXIF JPEG Bitmap (43.4) |
|---|---|---|
| .jpg | | | JPEG bitmap (26) |
| .mp3 | | | MP3 audio (ID3 v1.x tag) (21.7) |
| .mp3 | | | MP3 audio (8.6) |
Total processes
41
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1280 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\system32\ntvdm.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2440 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
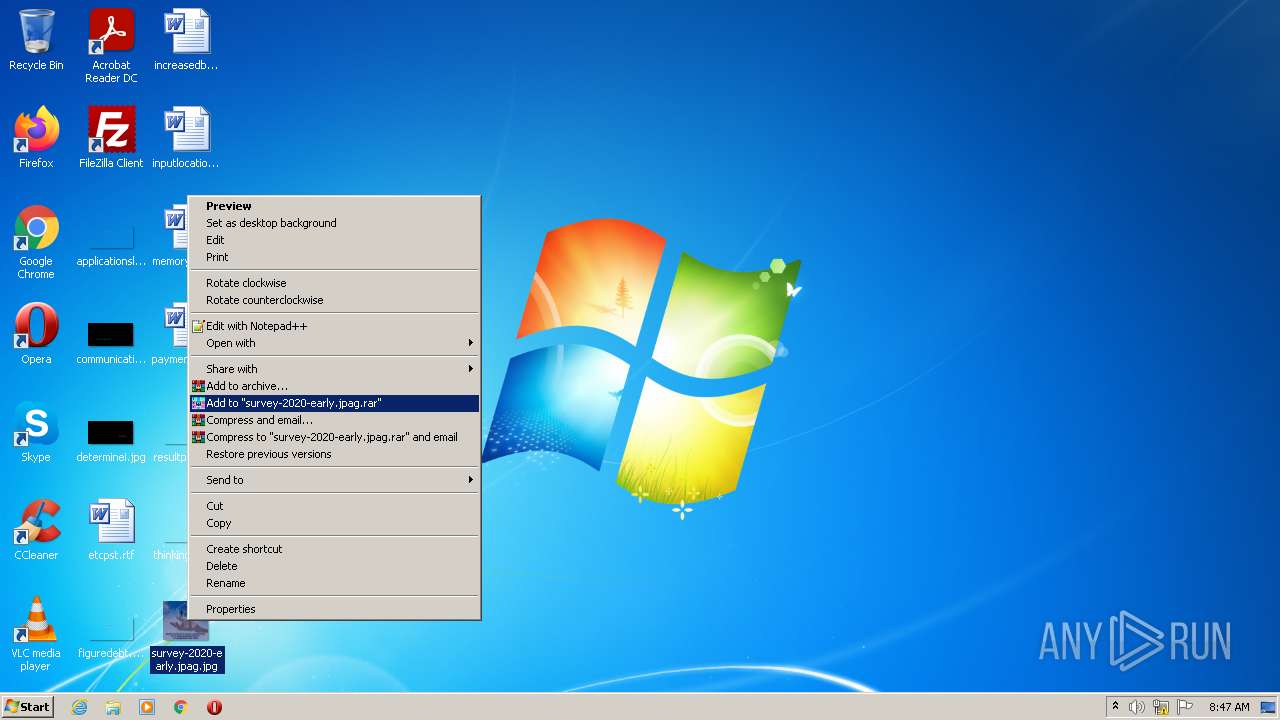
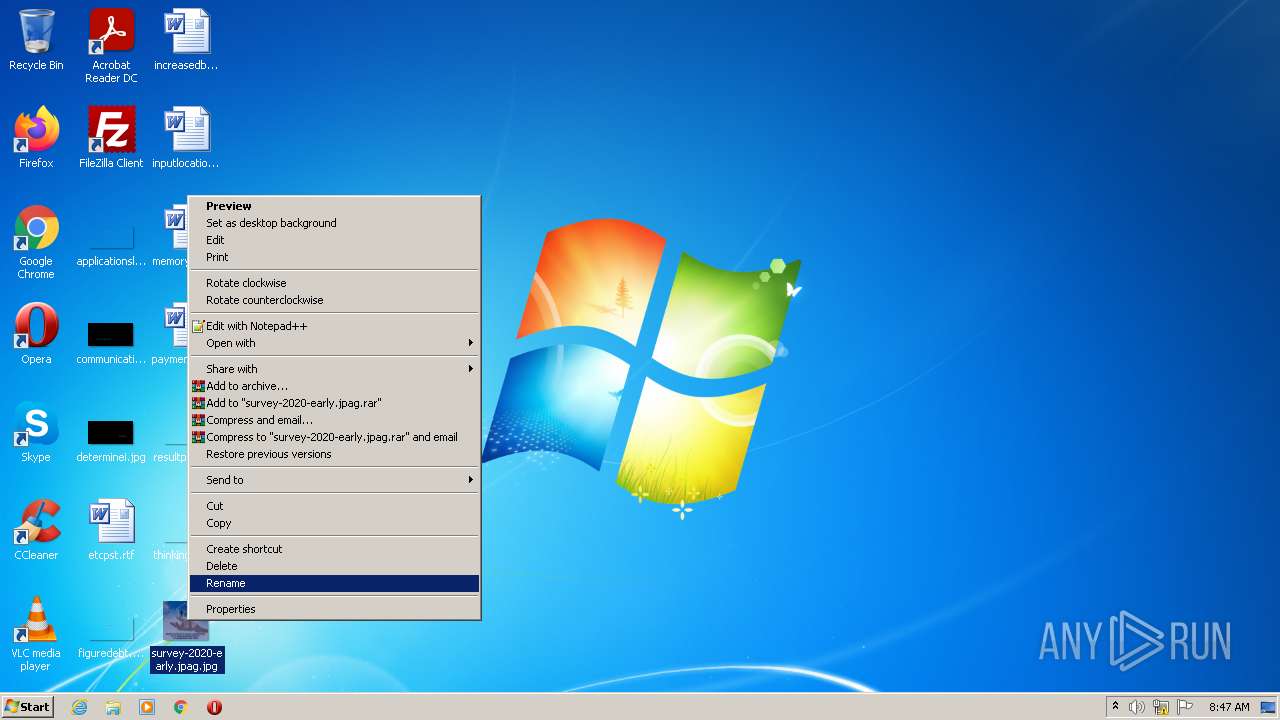
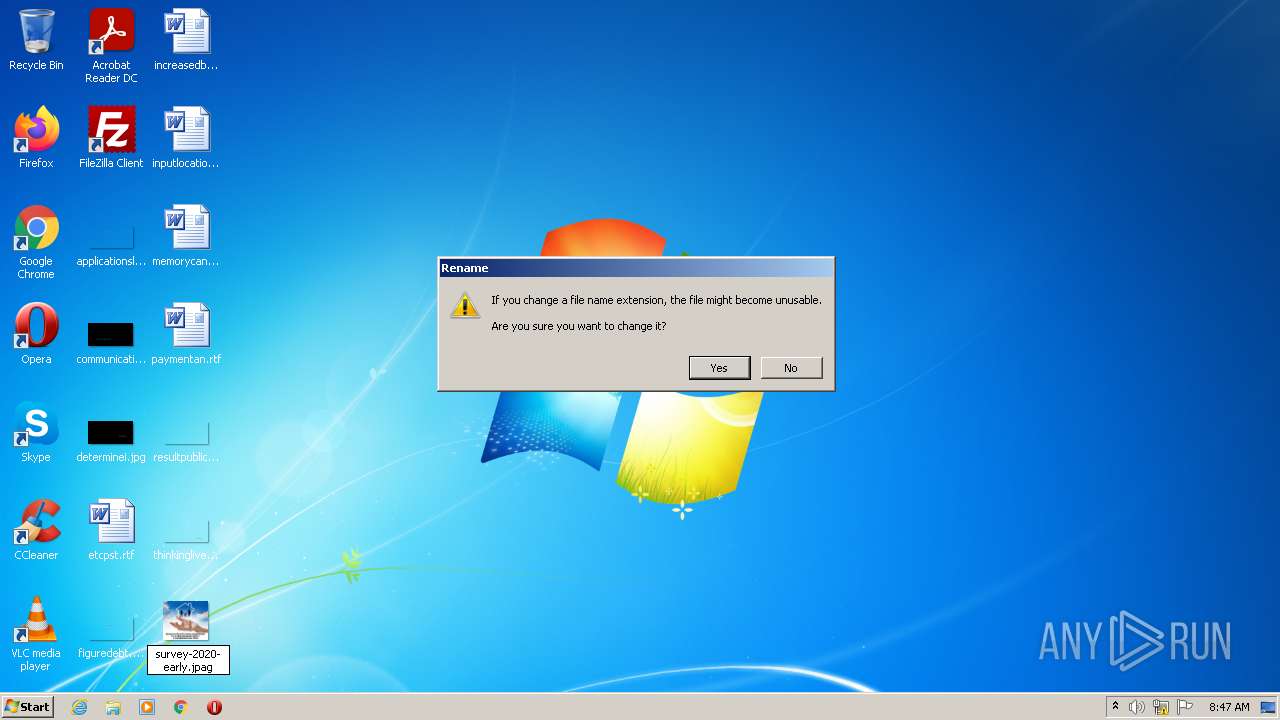
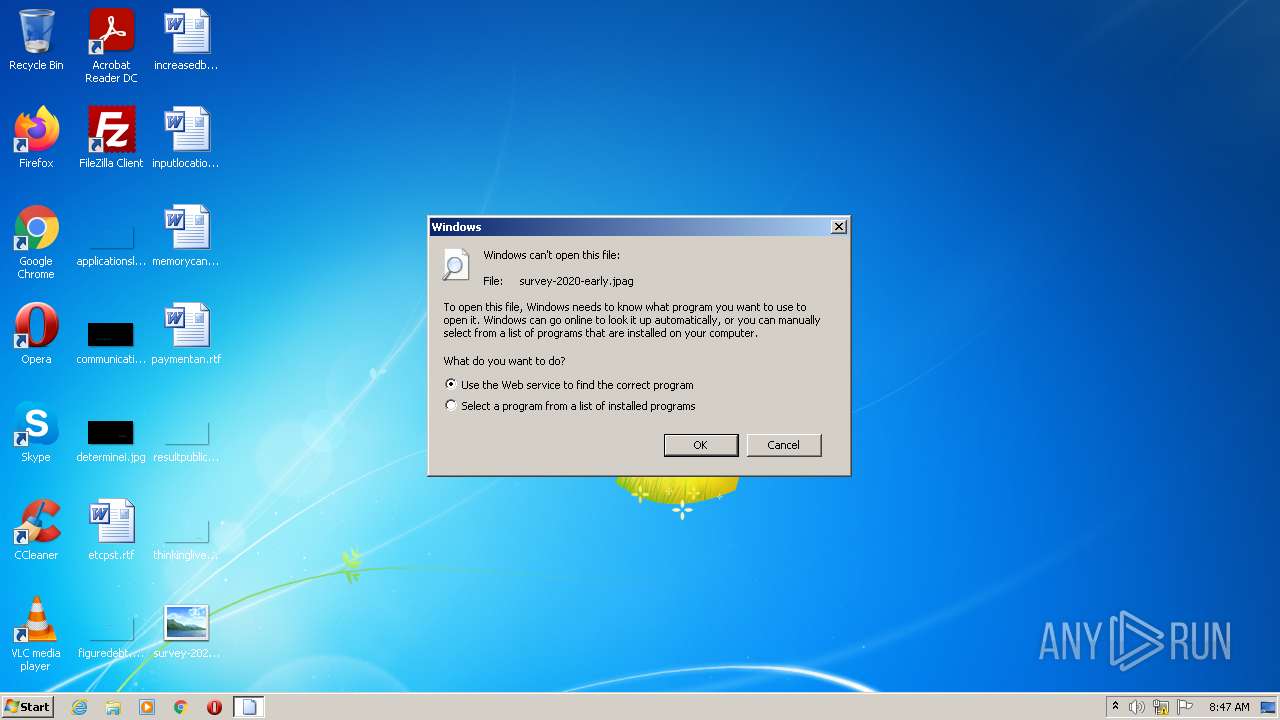
| 2684 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\survey-2020-early.jpag | C:\Windows\system32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3440 | "C:\Windows\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen "C:\Users\admin\Desktop\survey-2020-early.jpag.jpg" | C:\Windows\System32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3644 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\survey-2020-early.txt | C:\Windows\system32\NOTEPAD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
276
Read events
273
Write events
3
Delete events
0
Modification events
| (PID) Process: | (3440) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: rundll32.exe | |||
| (PID) Process: | (2440) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: DllHost.exe | |||
| (PID) Process: | (2440) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Photo Viewer\Viewer |
| Operation: | write | Name: | MainWndPos |
Value: 6000000034000000A00400008002000000000000 | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1280 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsDA35.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 1280 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsDA34.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report