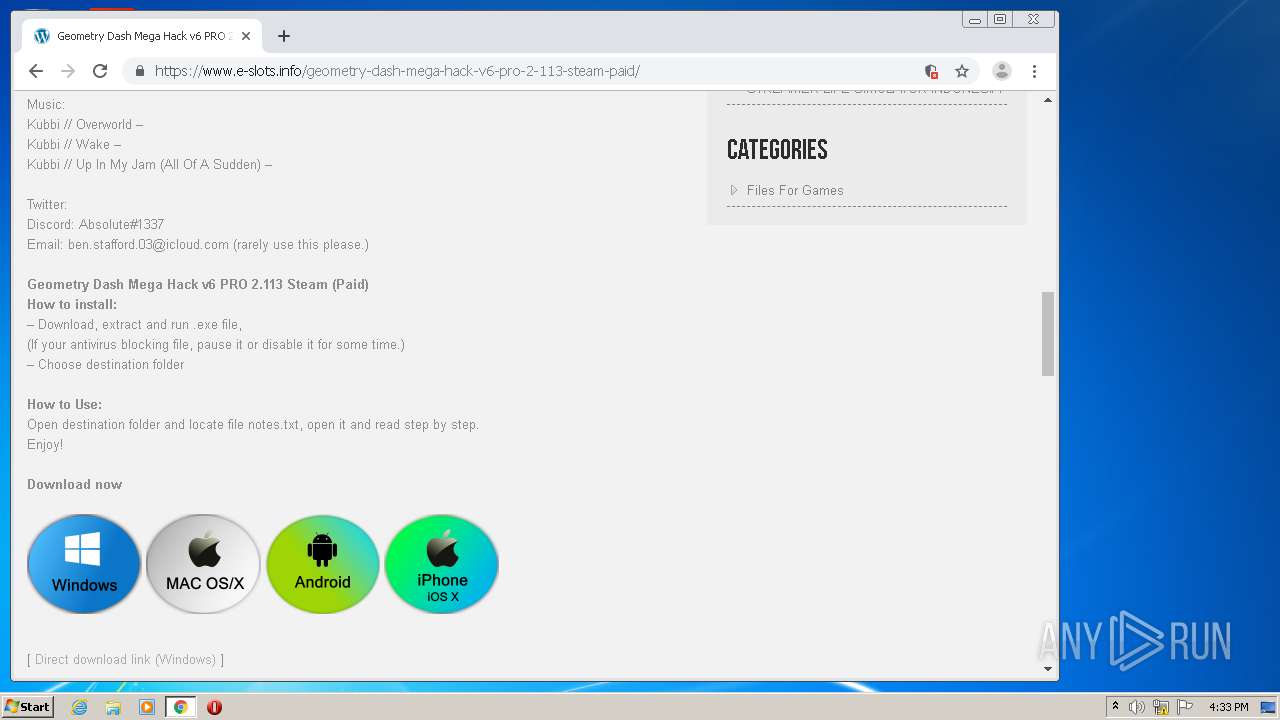
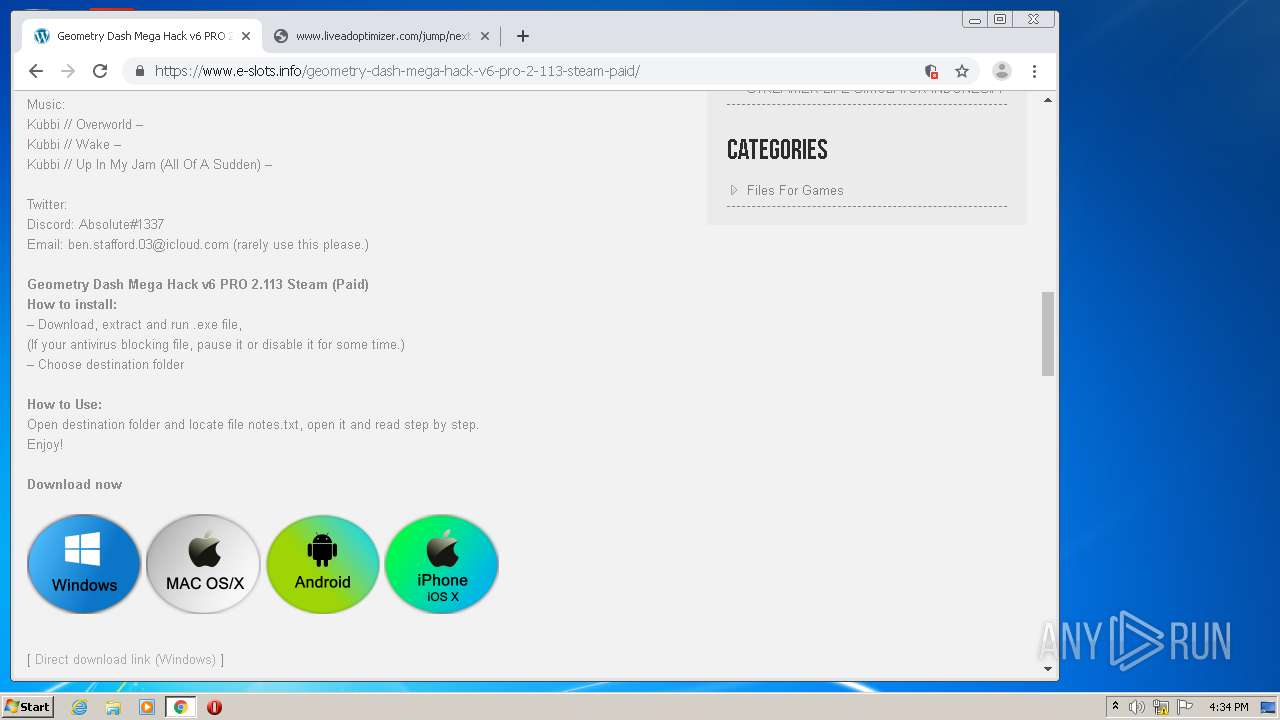
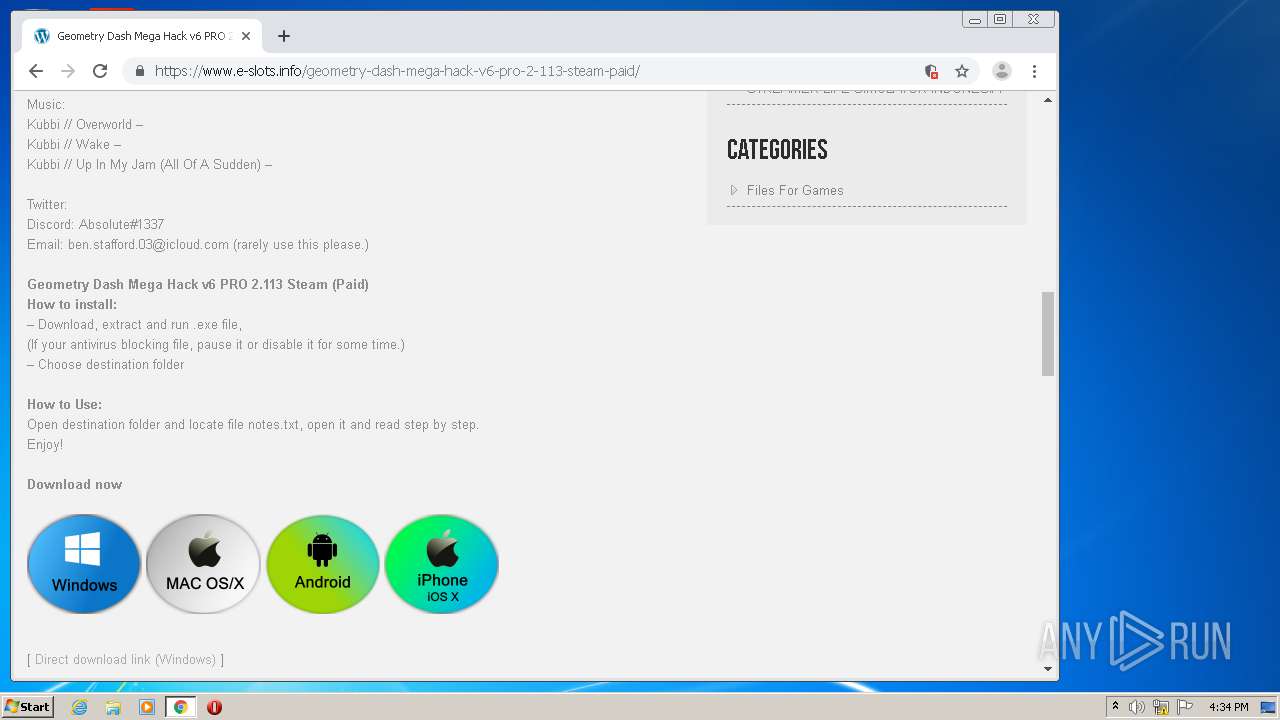
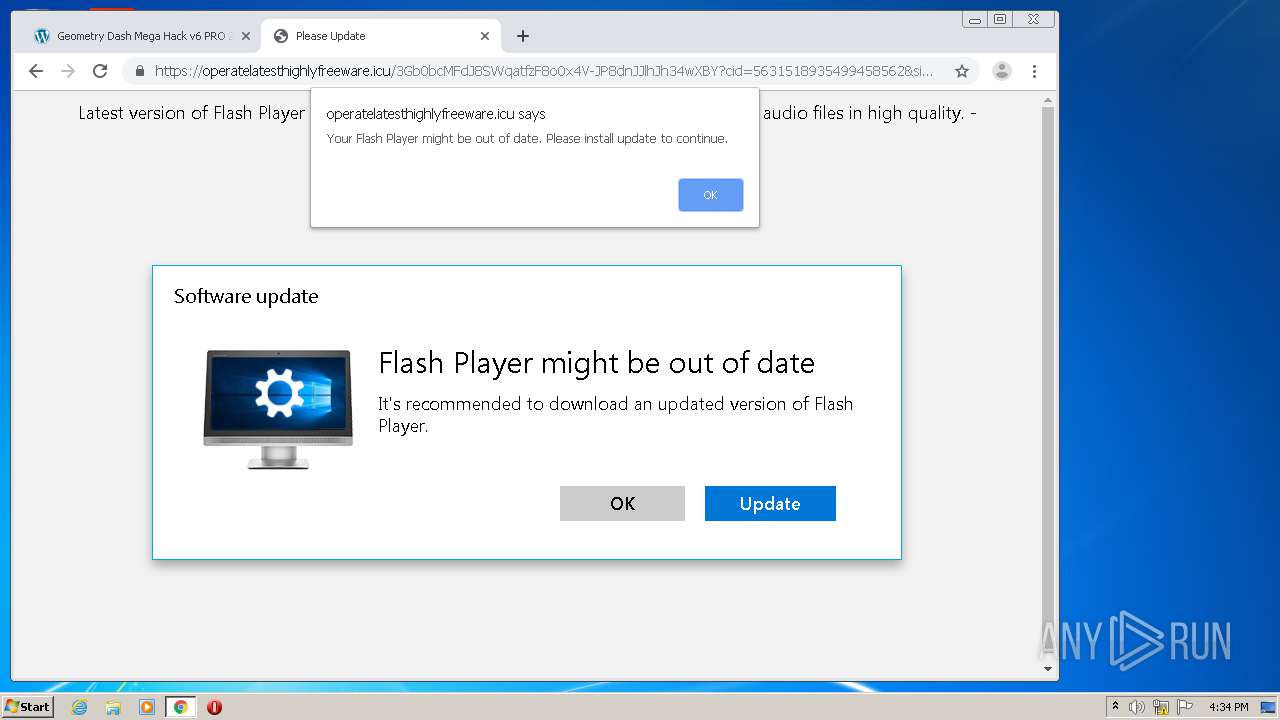
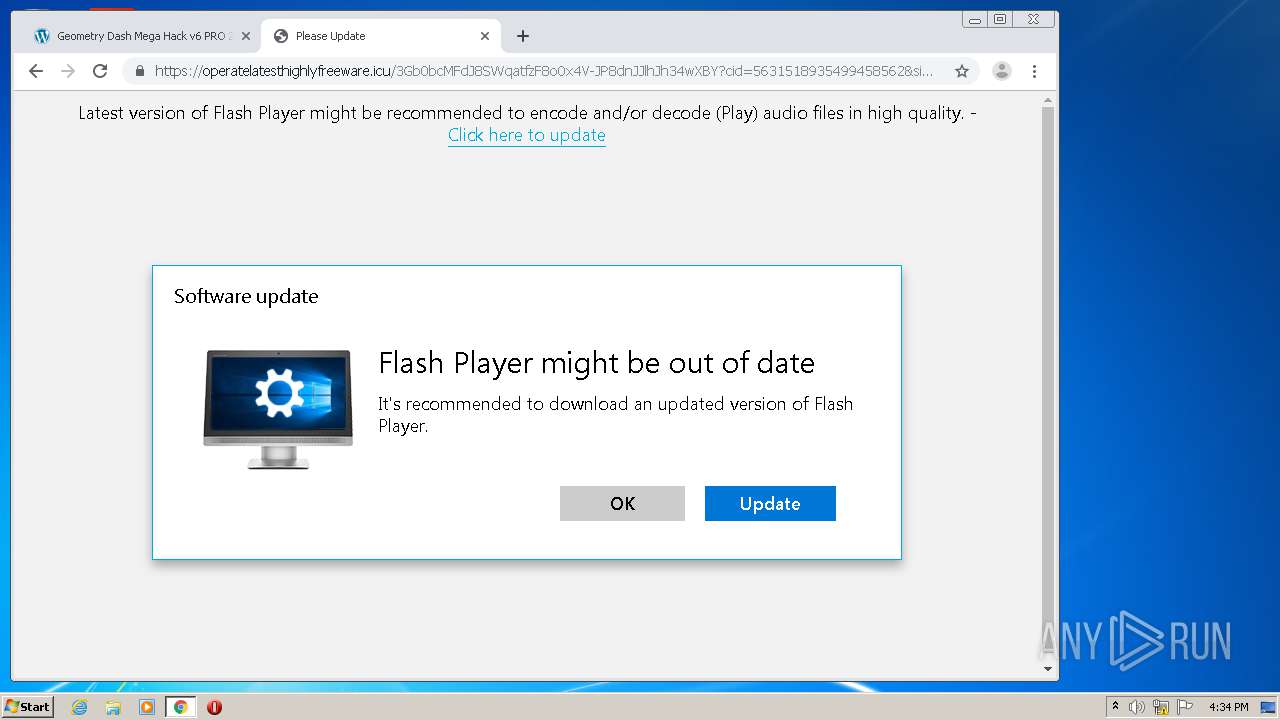
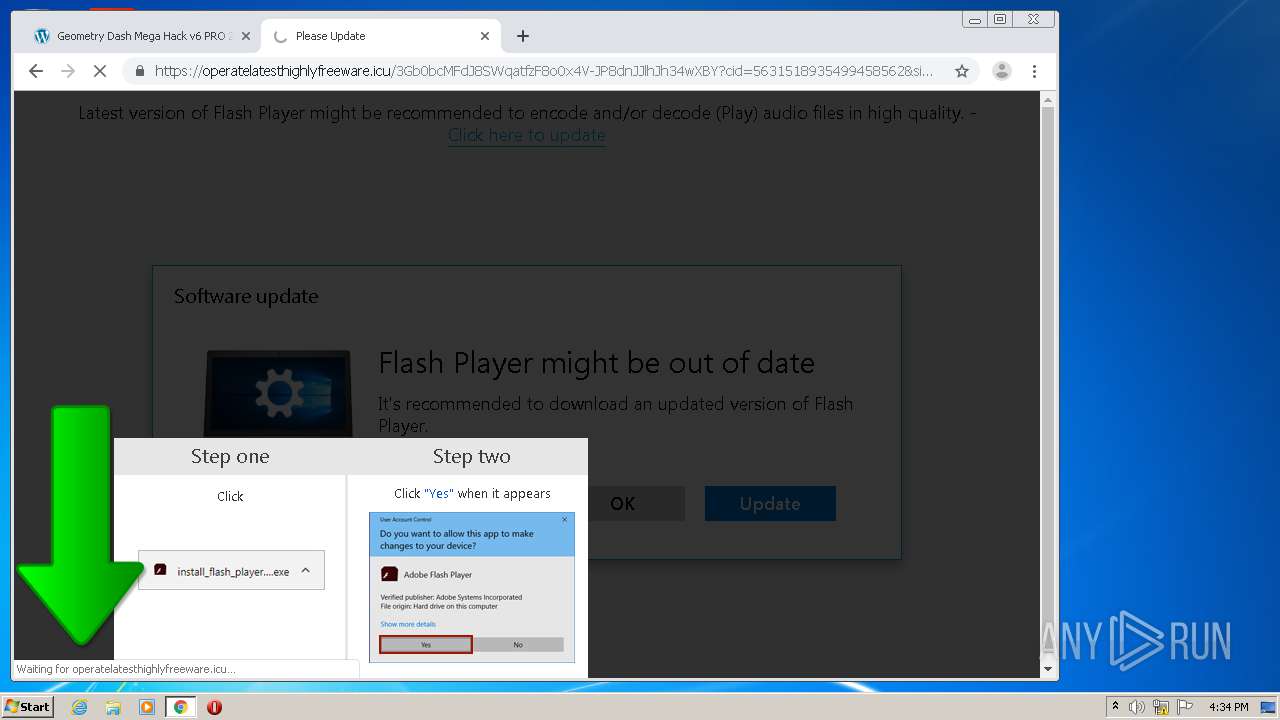
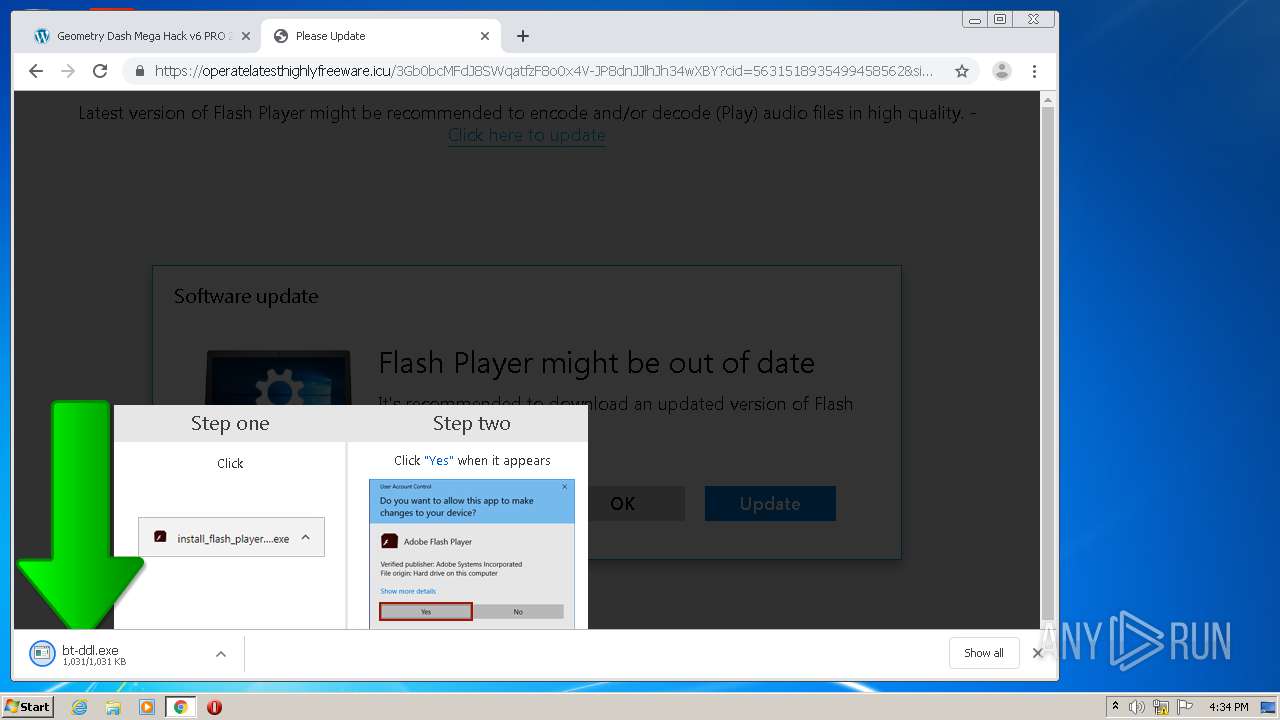
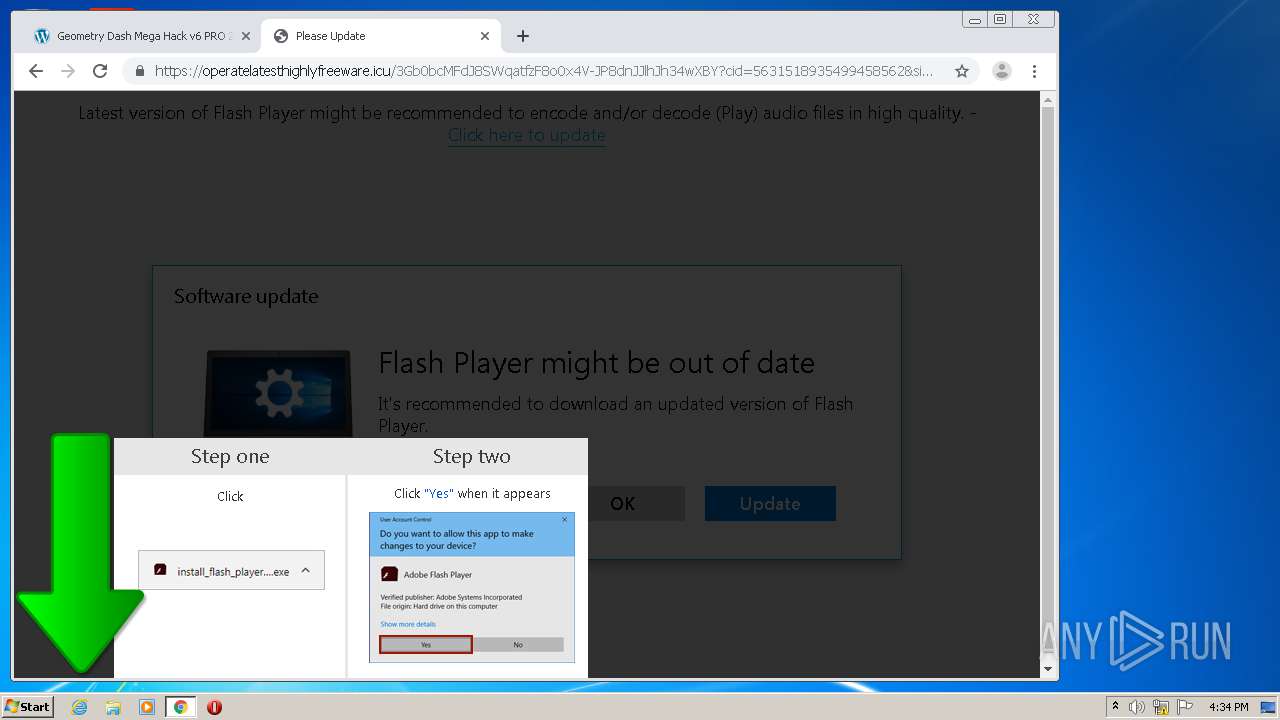
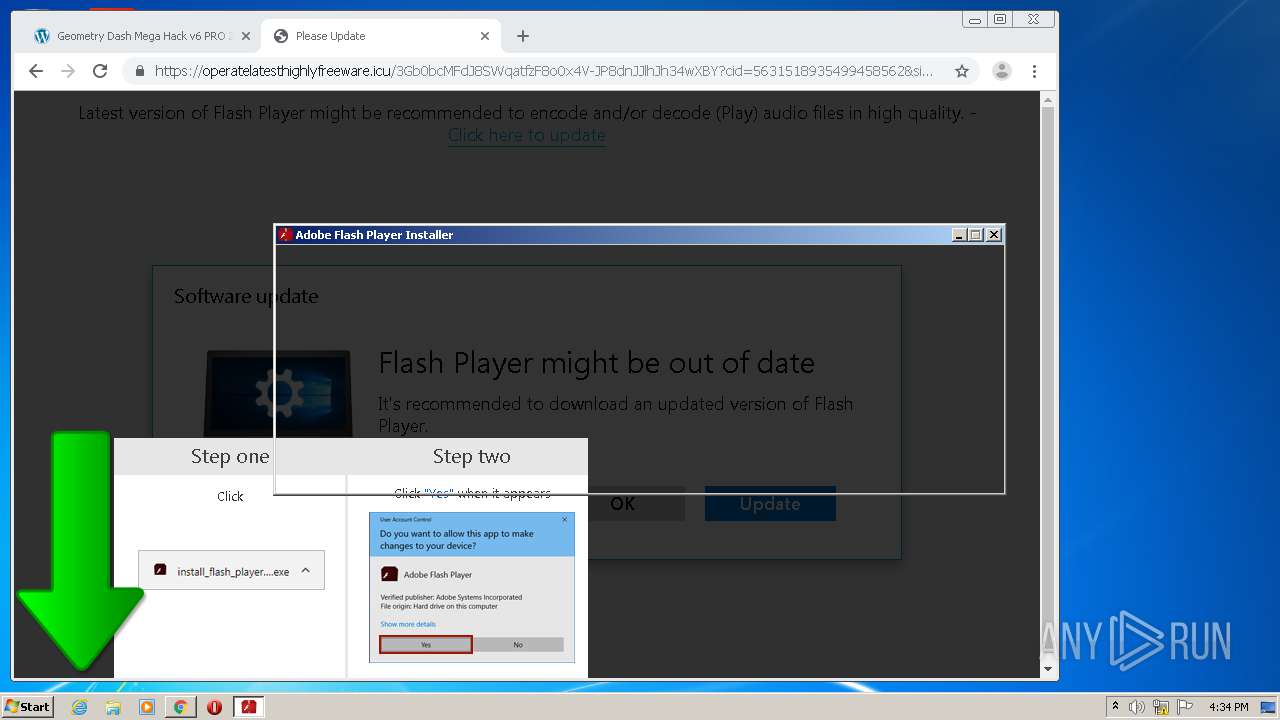
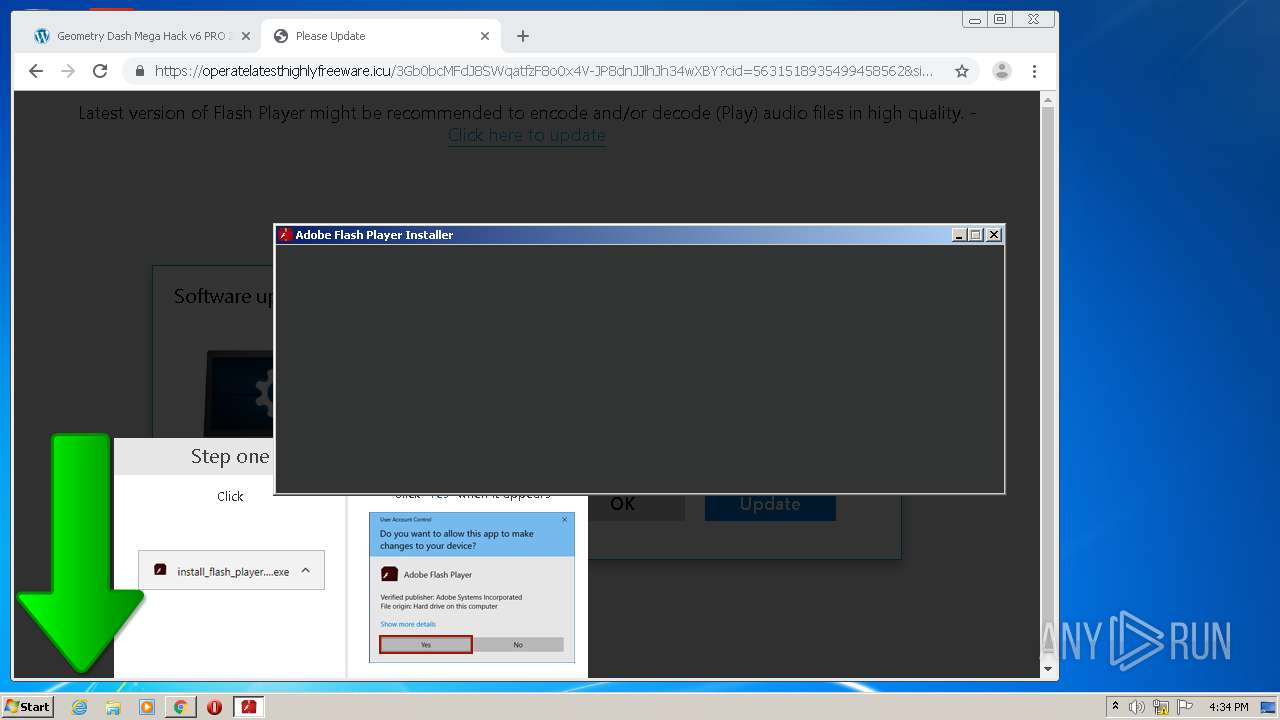
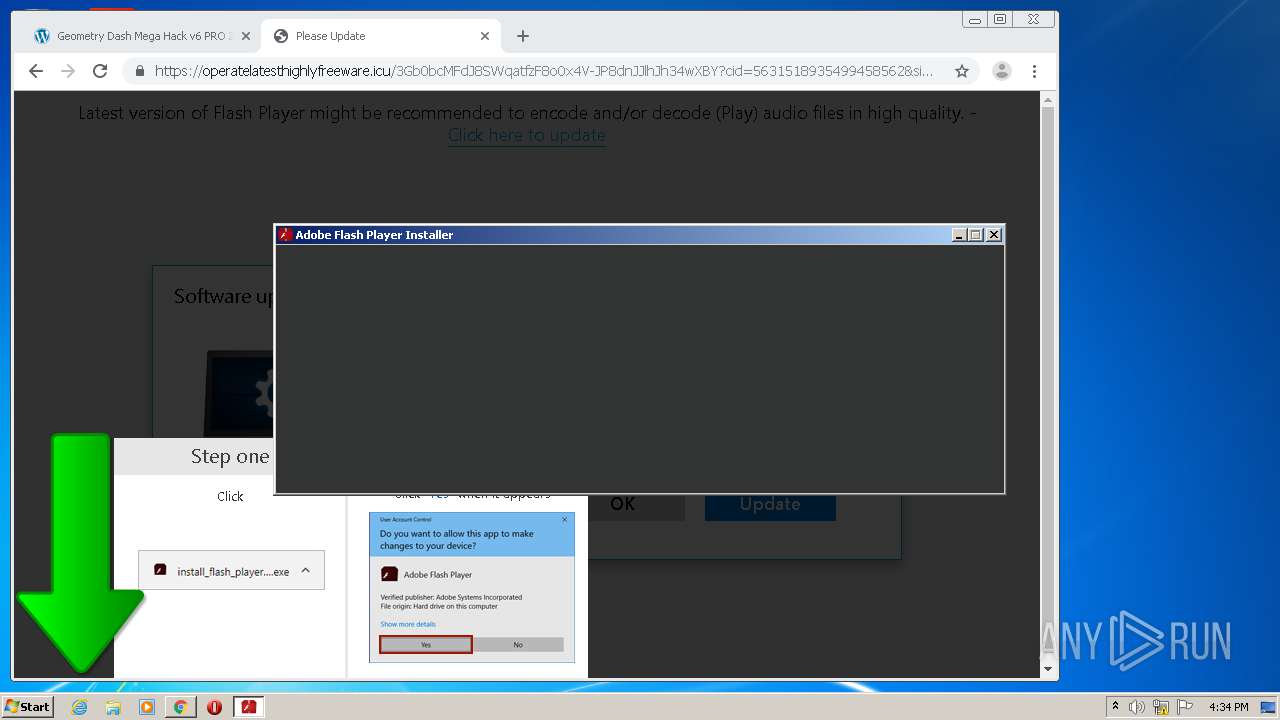
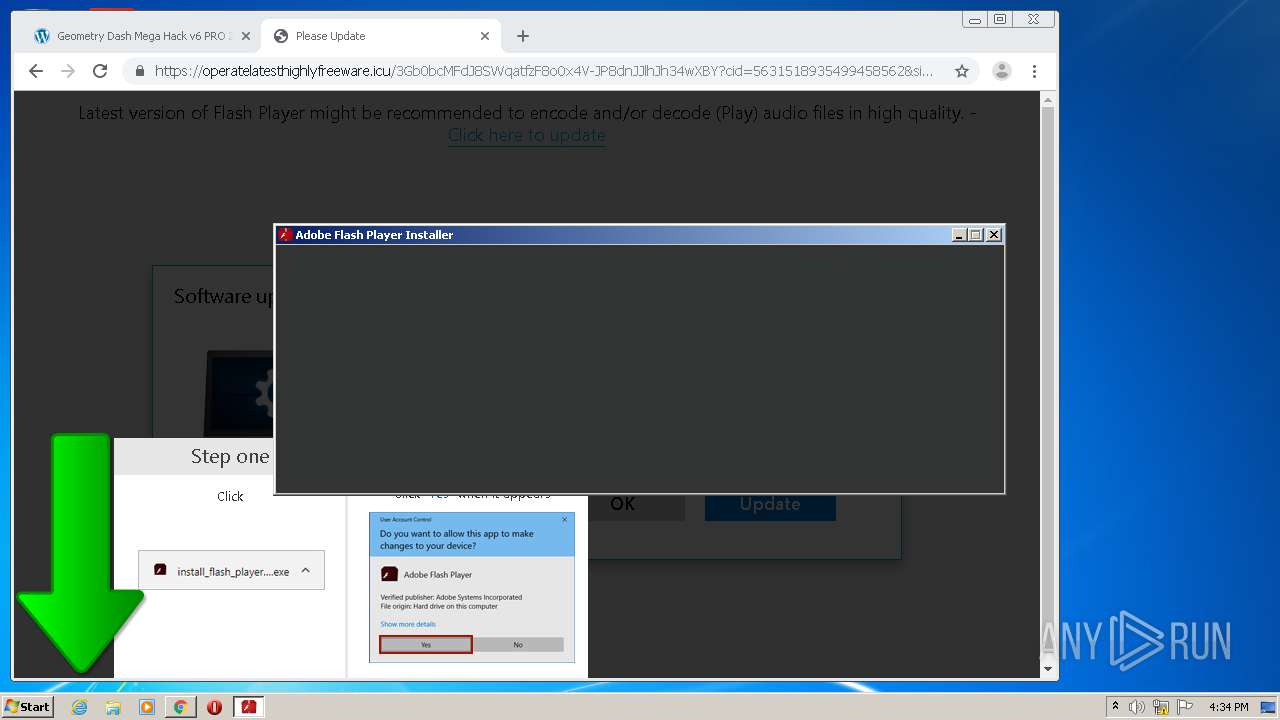
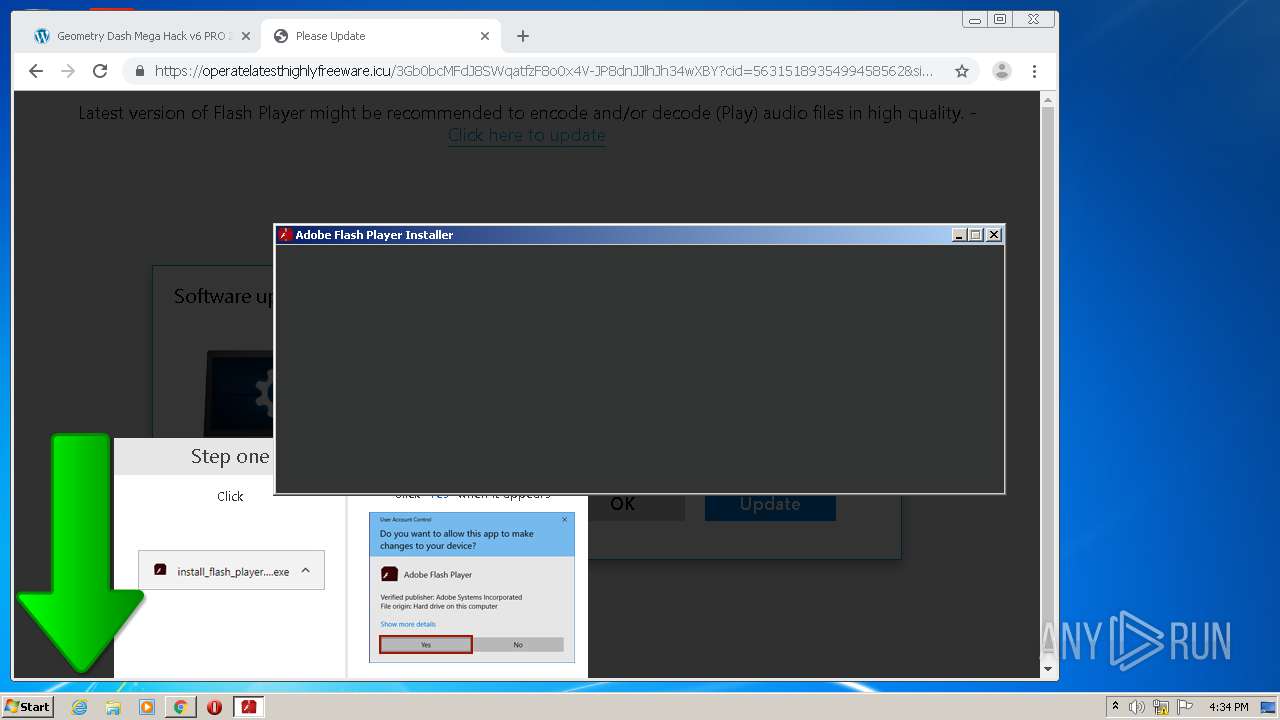
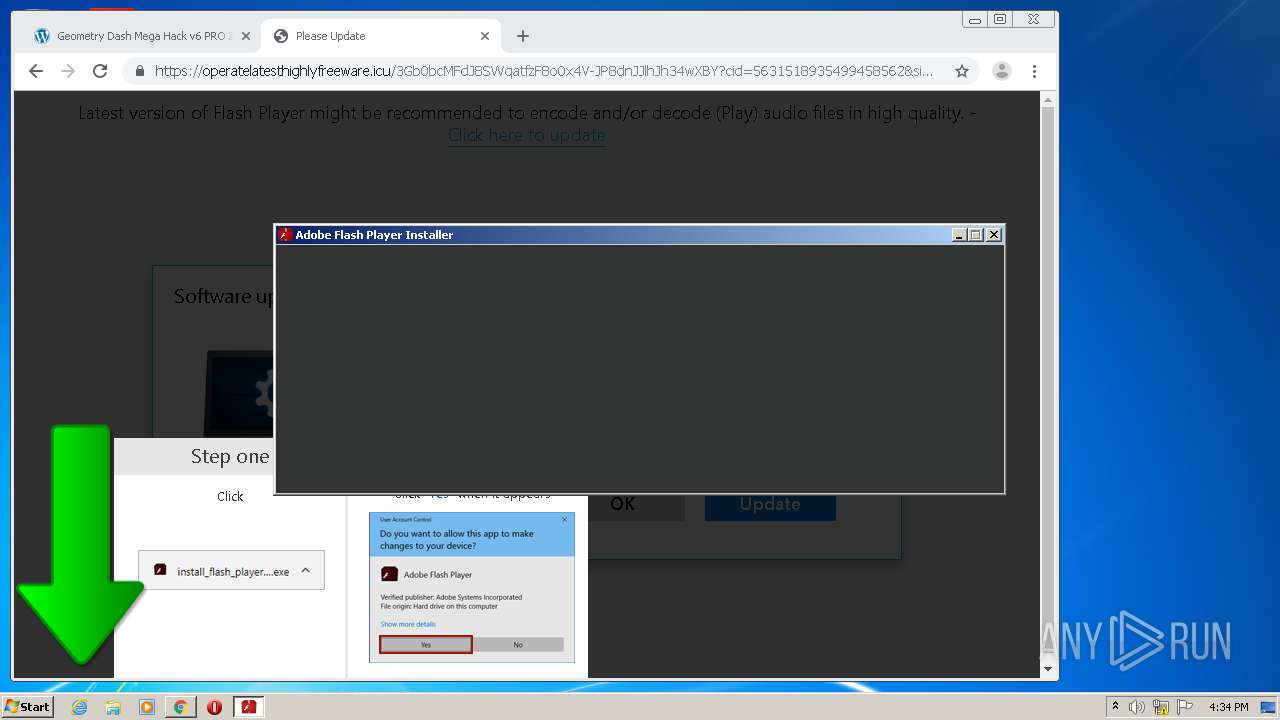
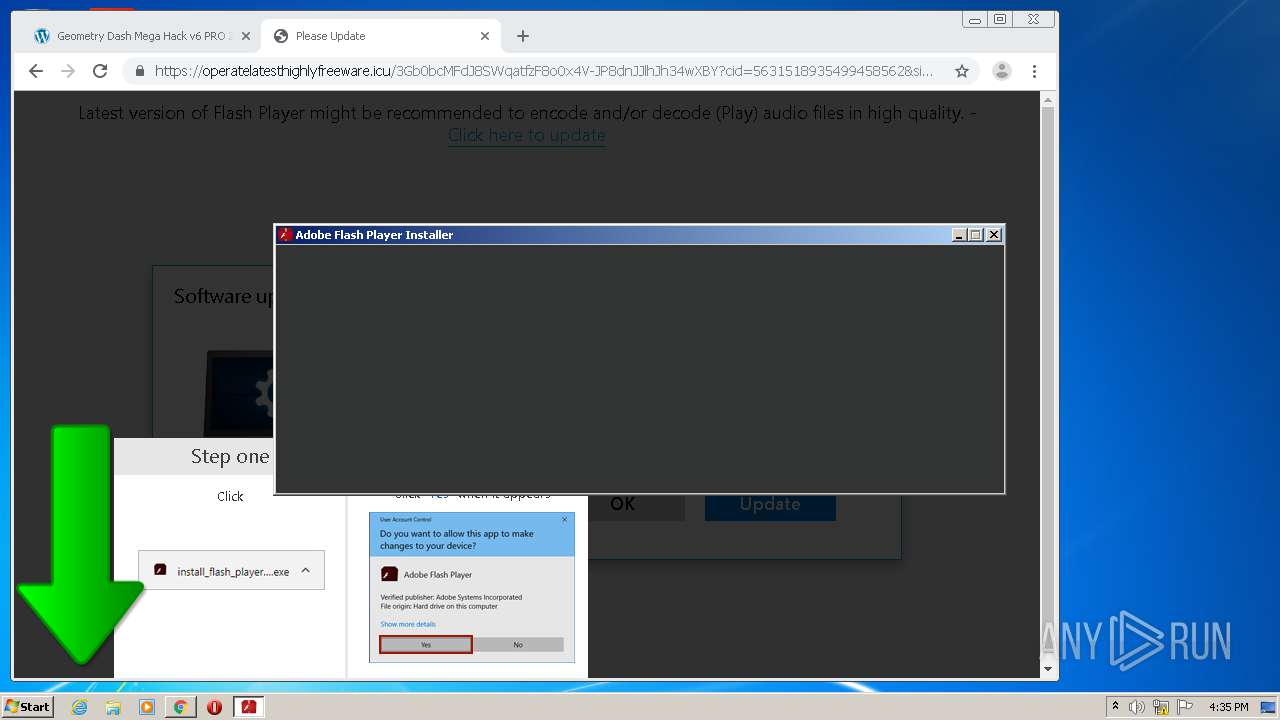
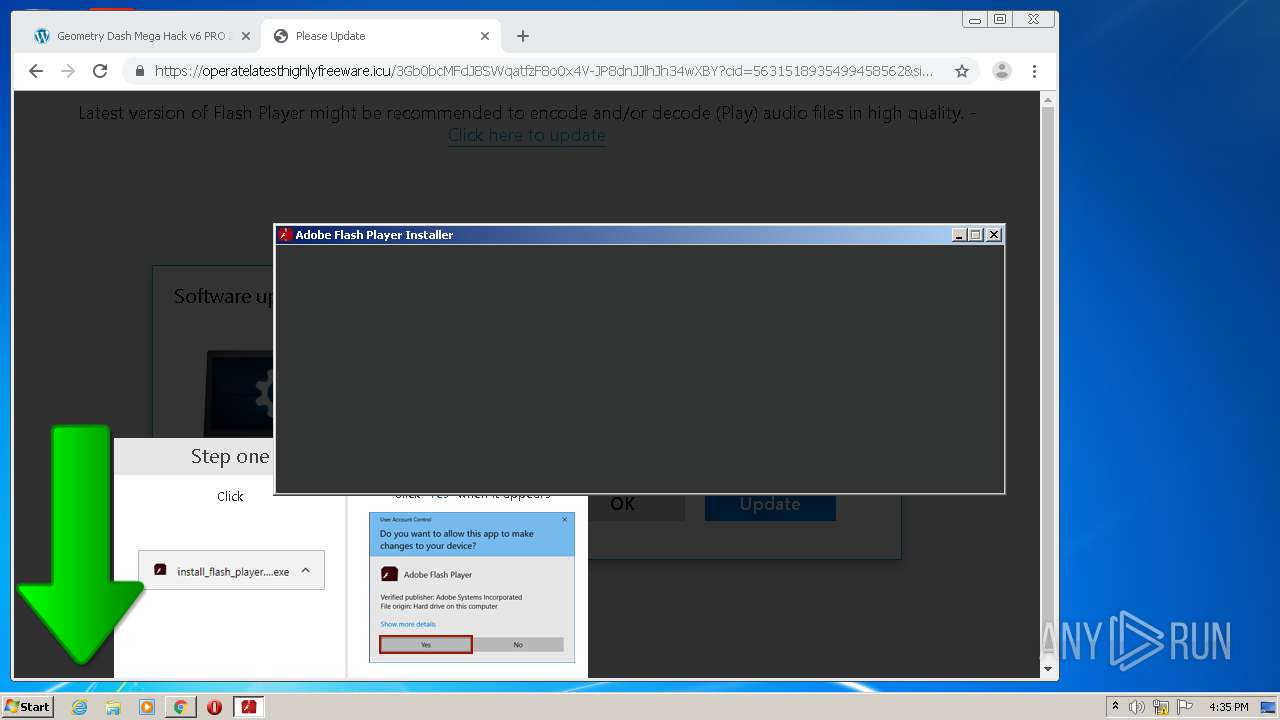
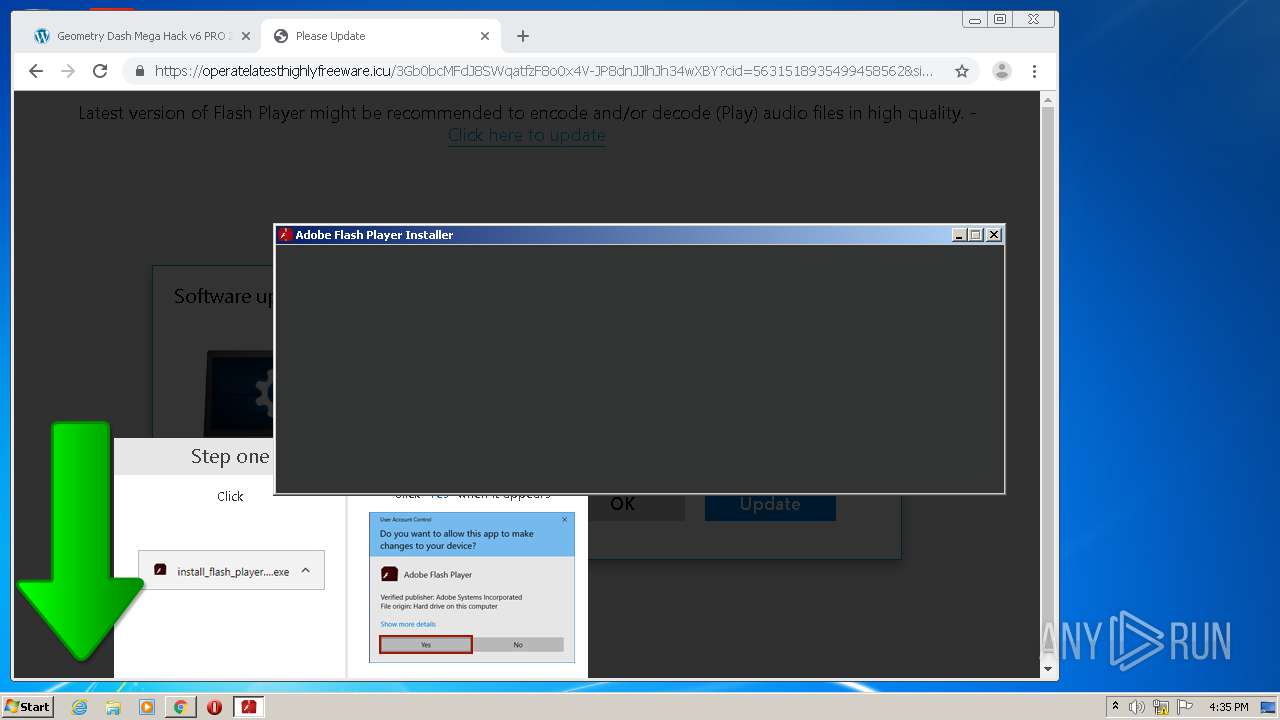
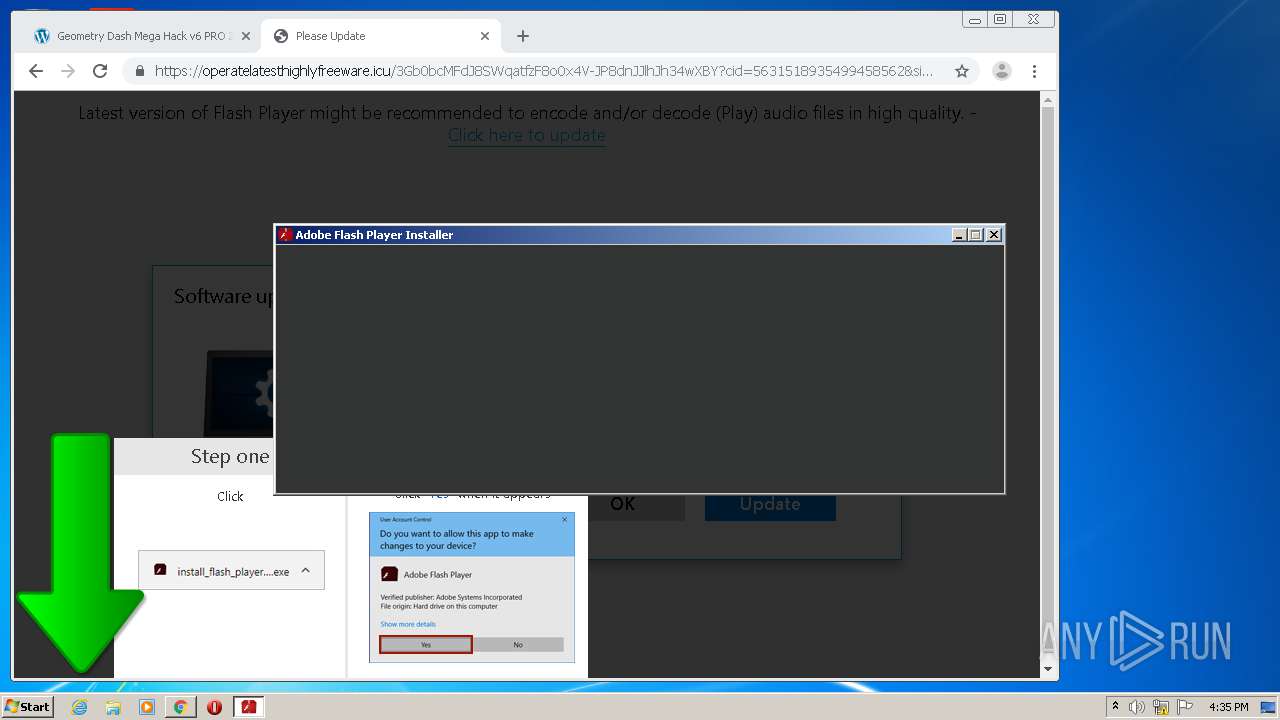
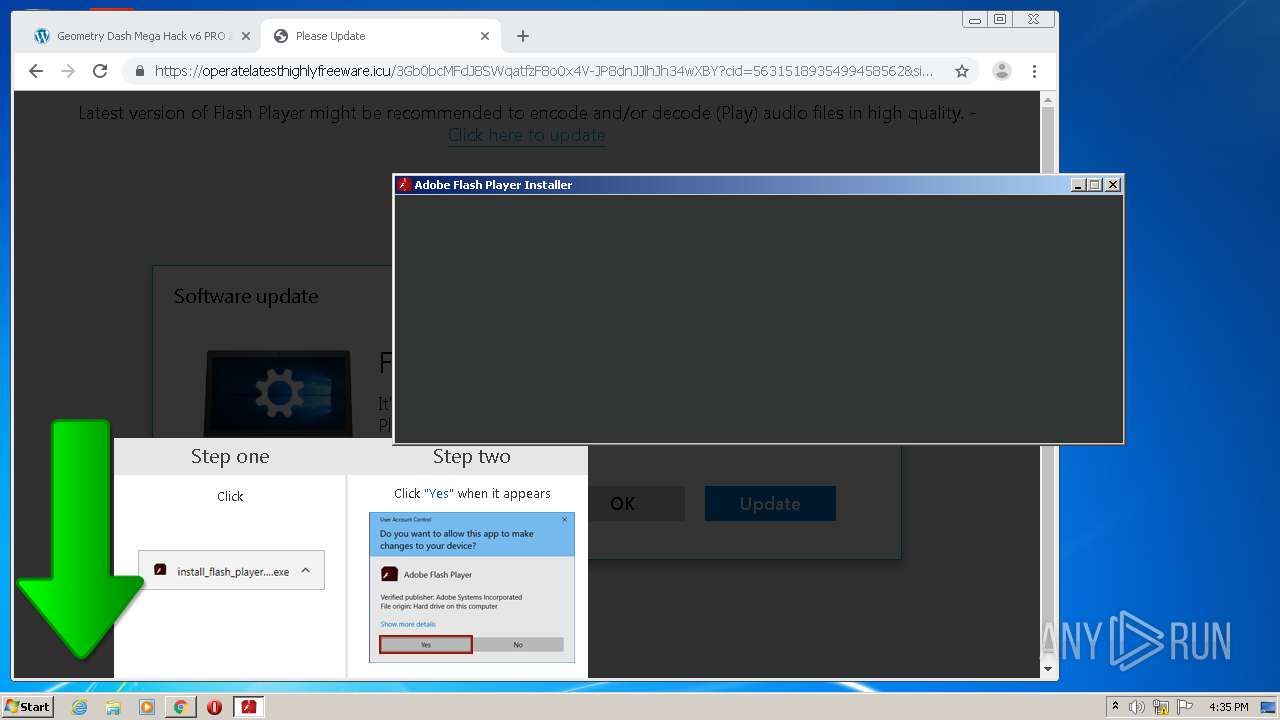
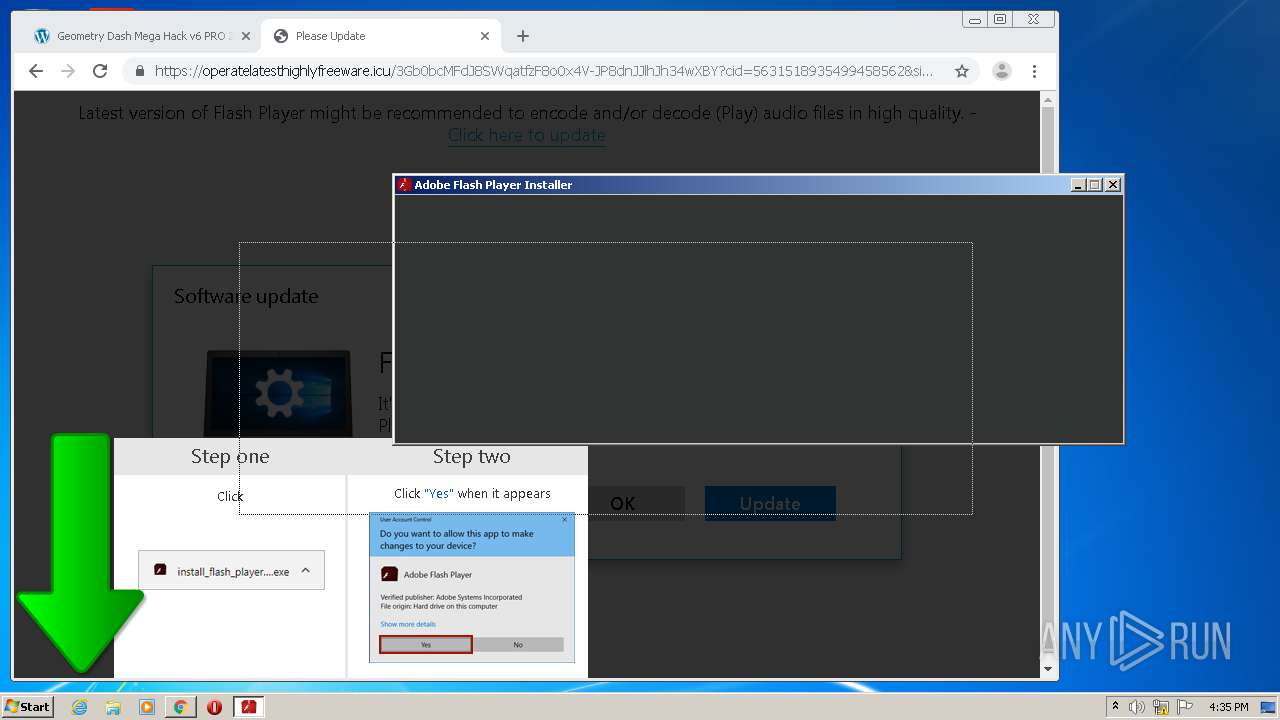
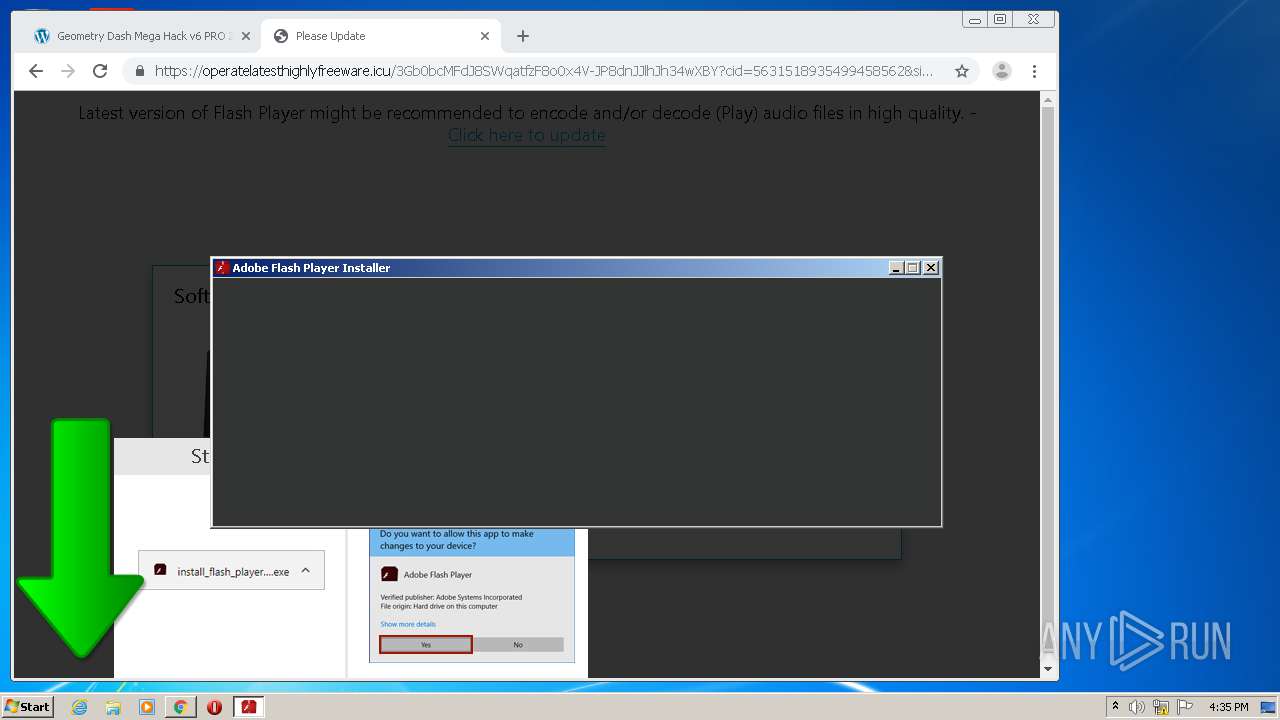
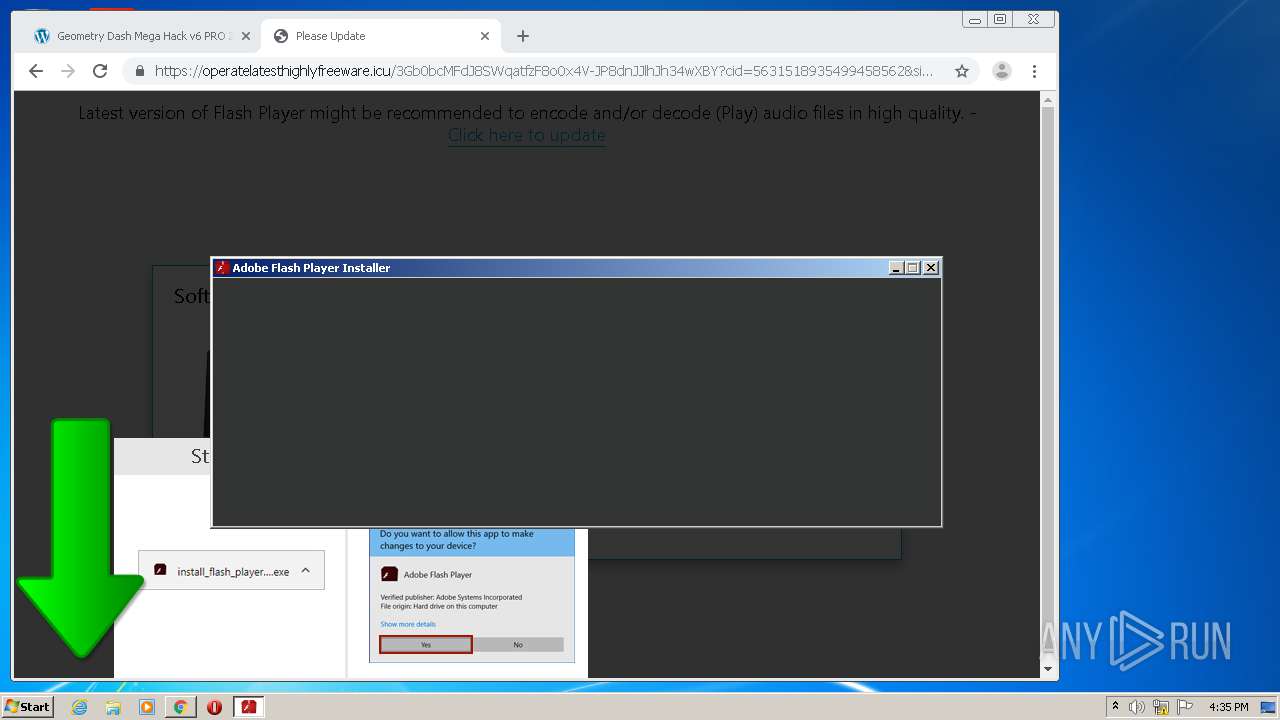
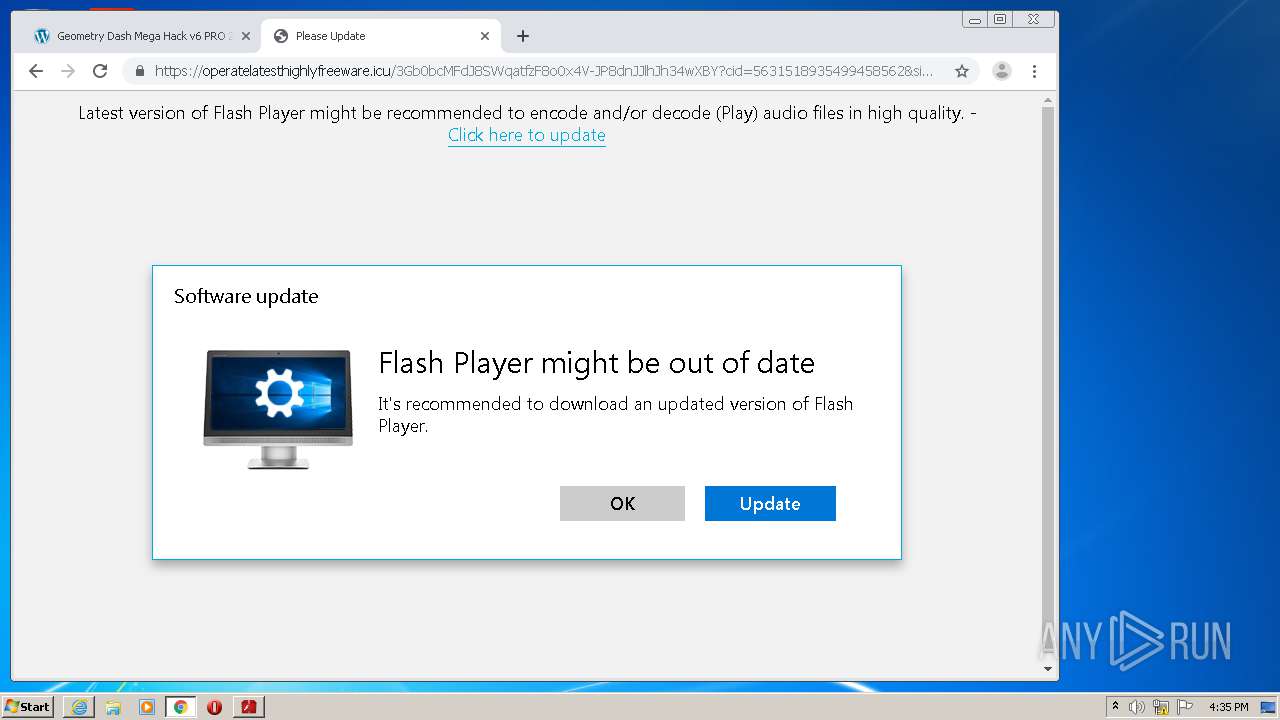
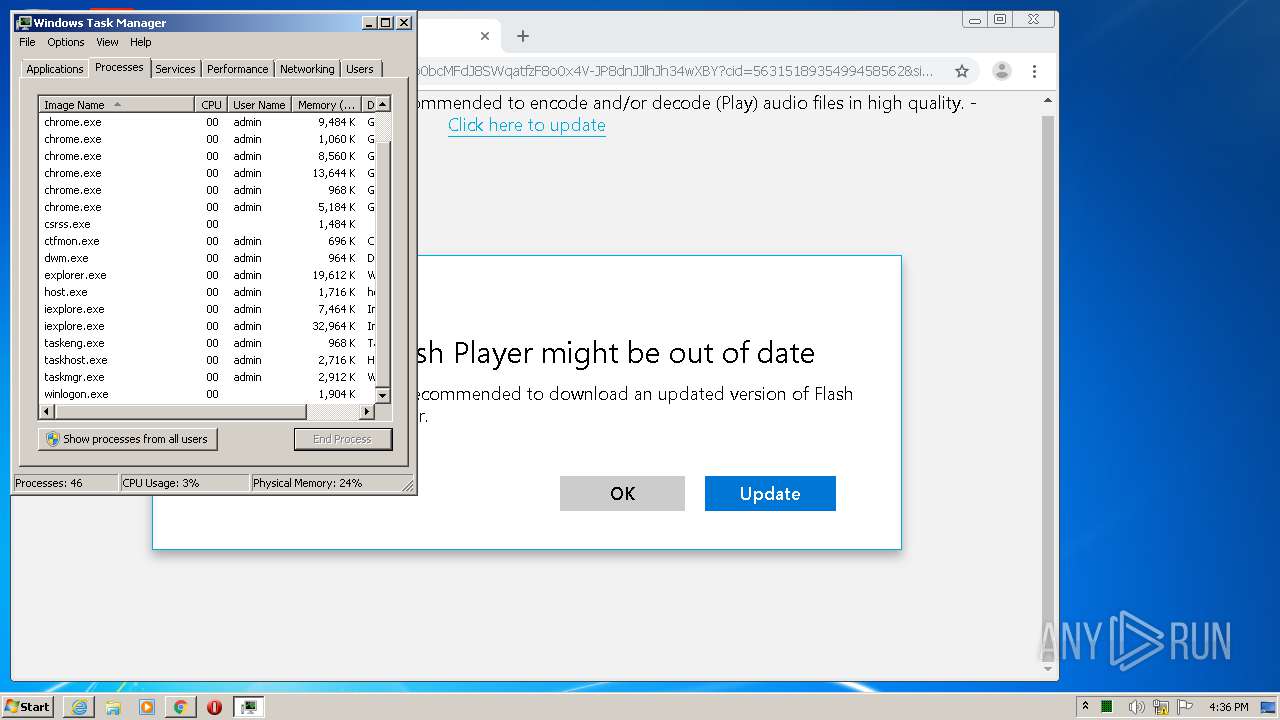
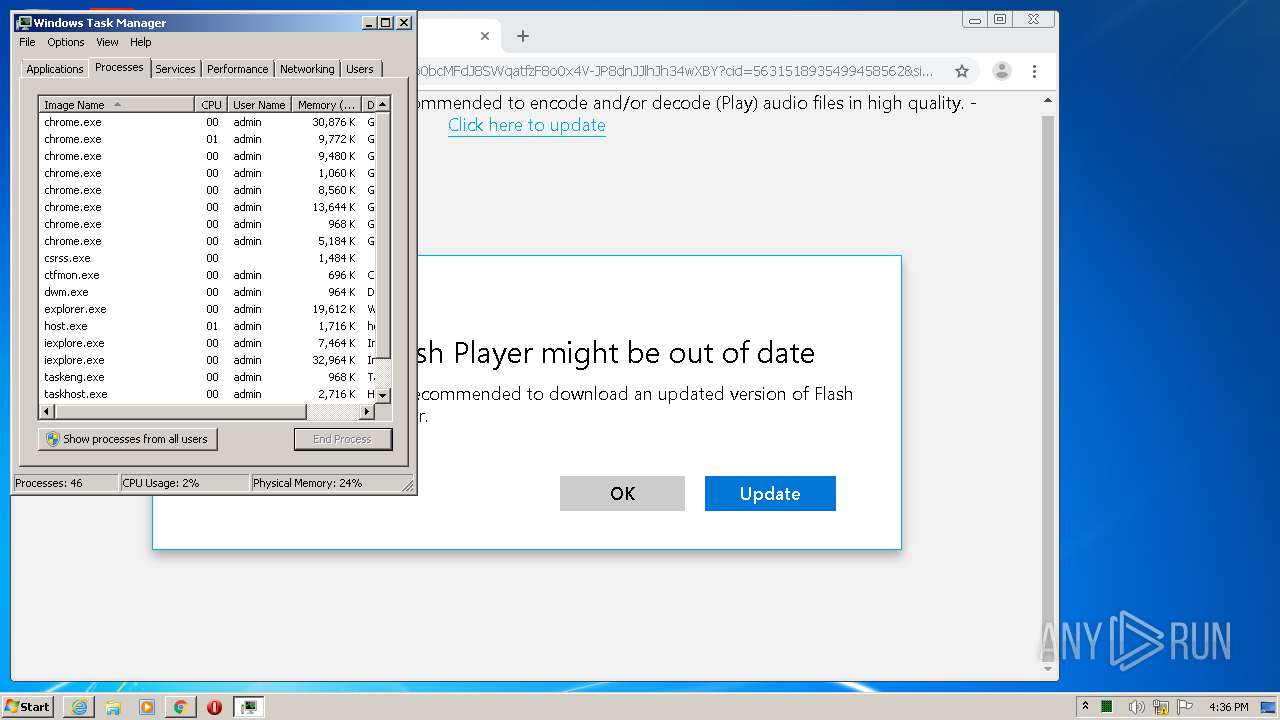
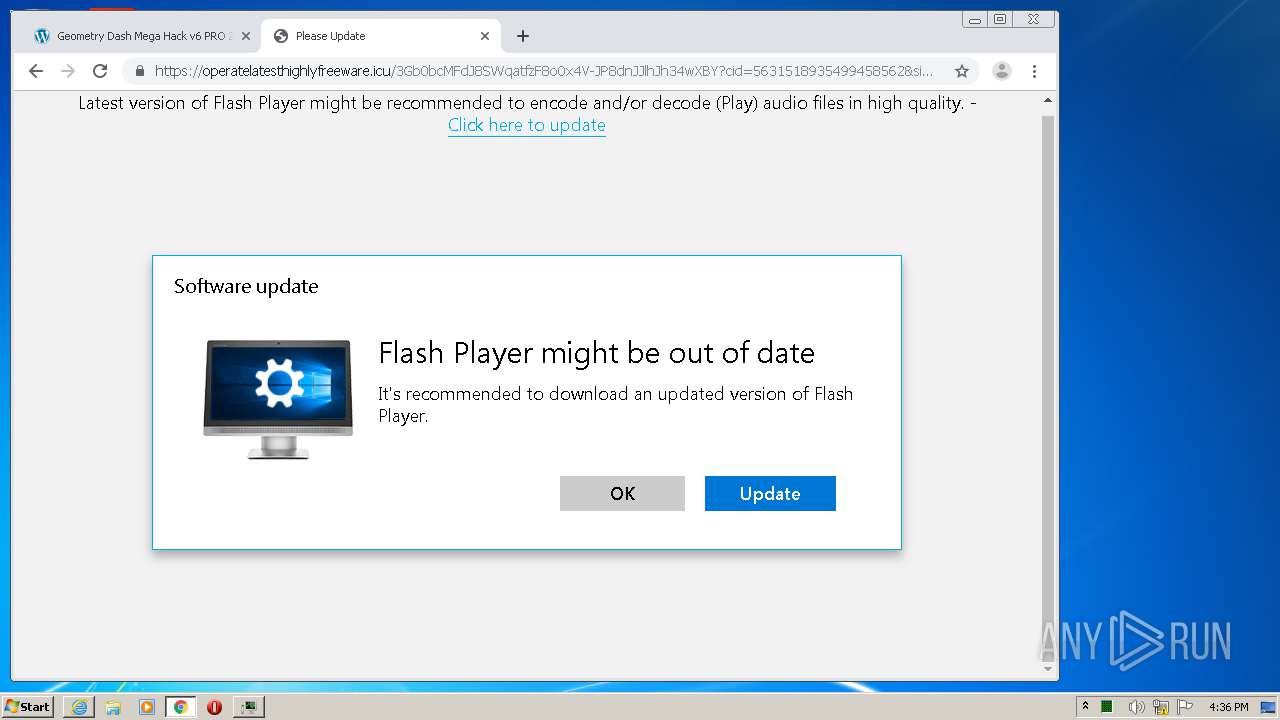
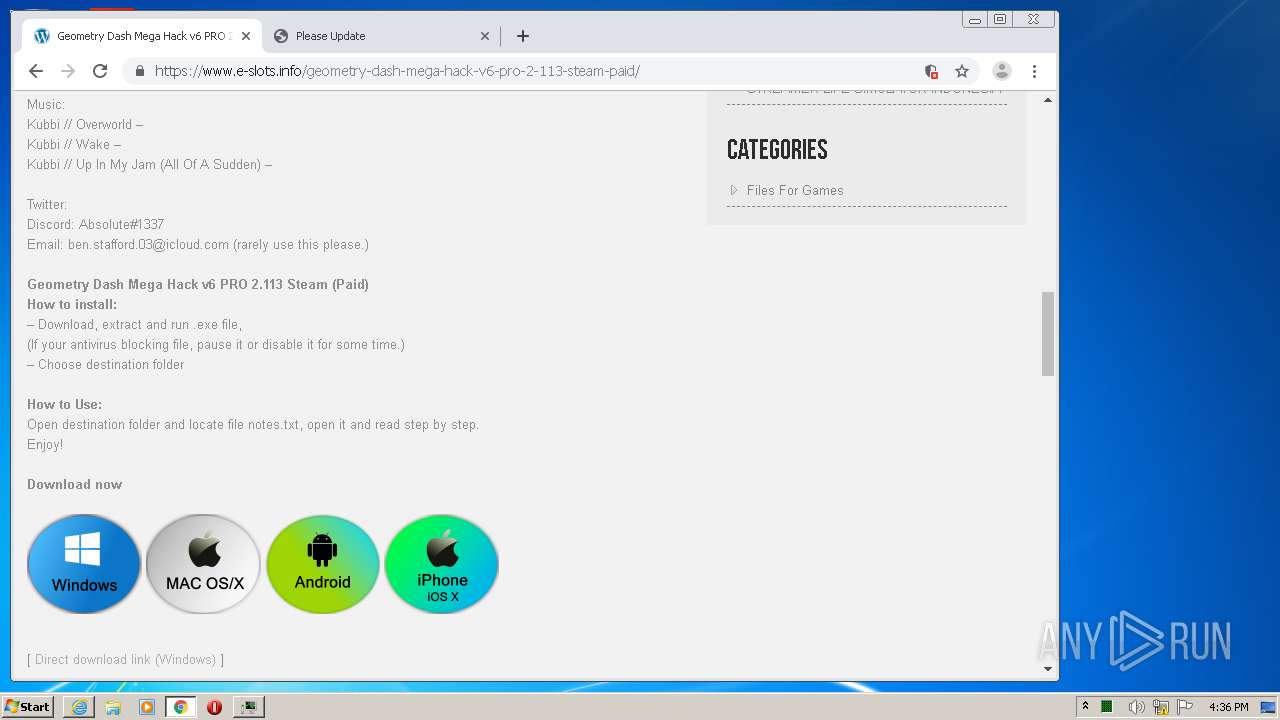
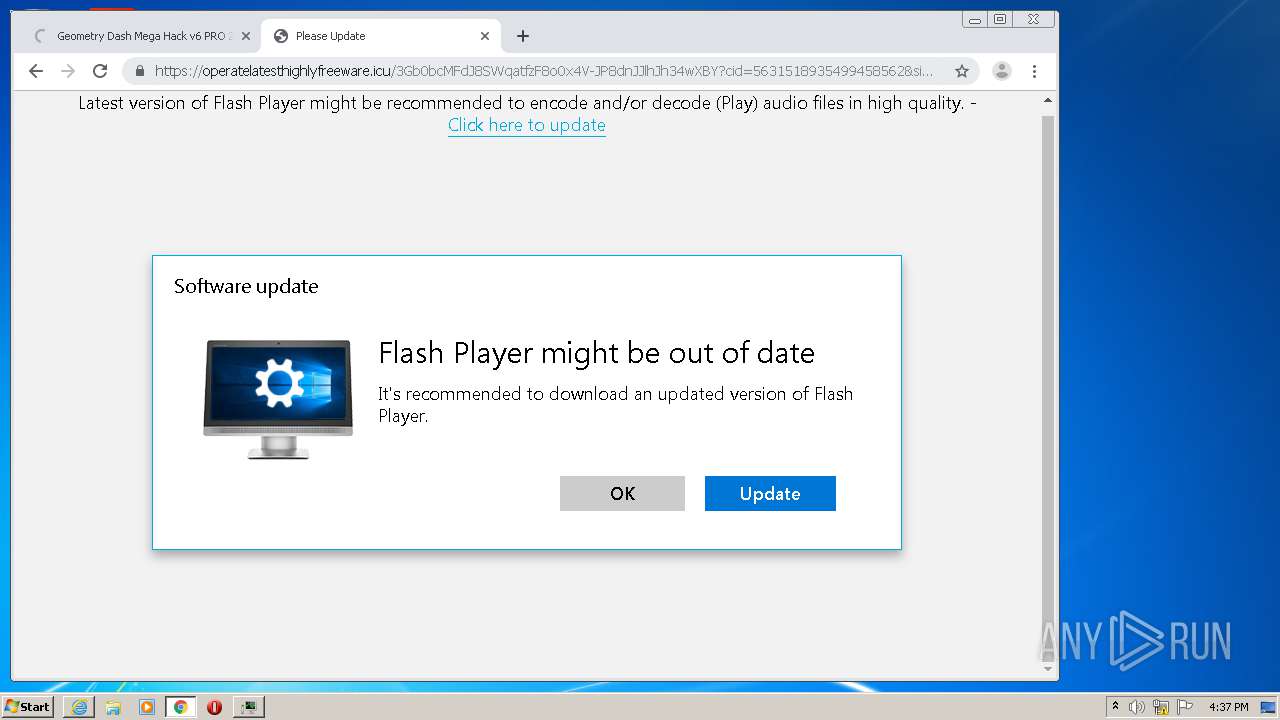
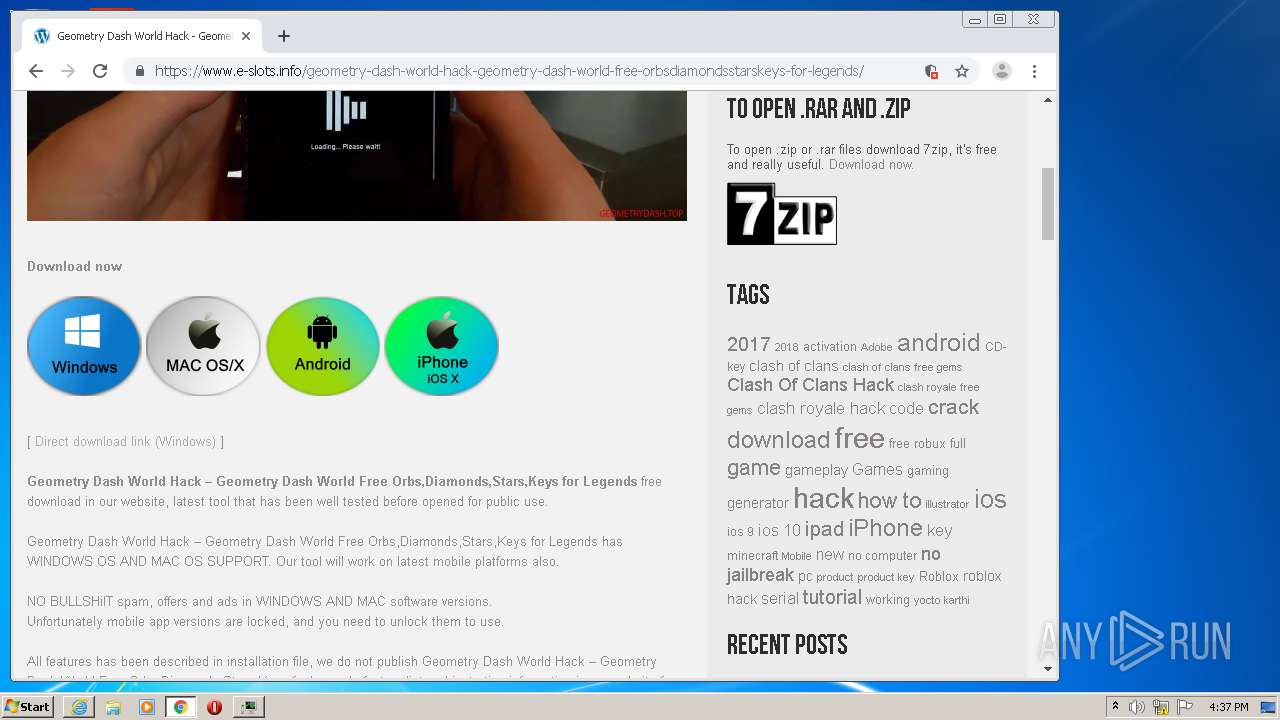
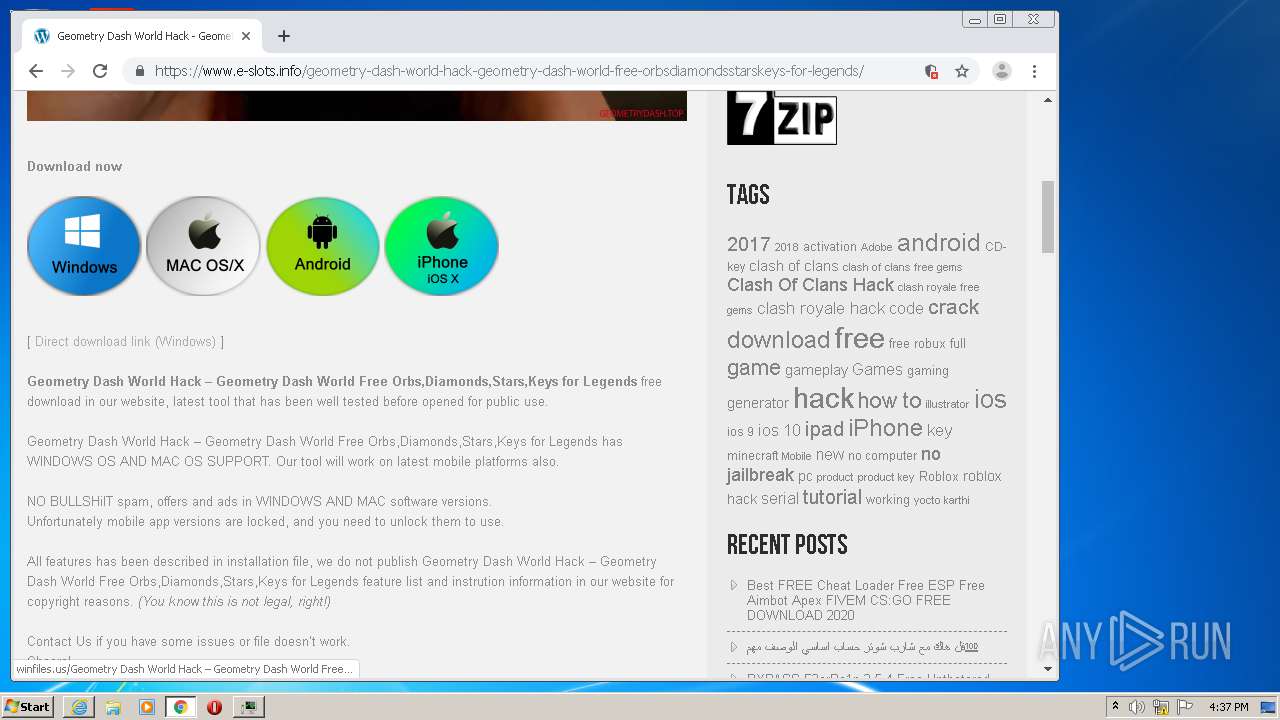
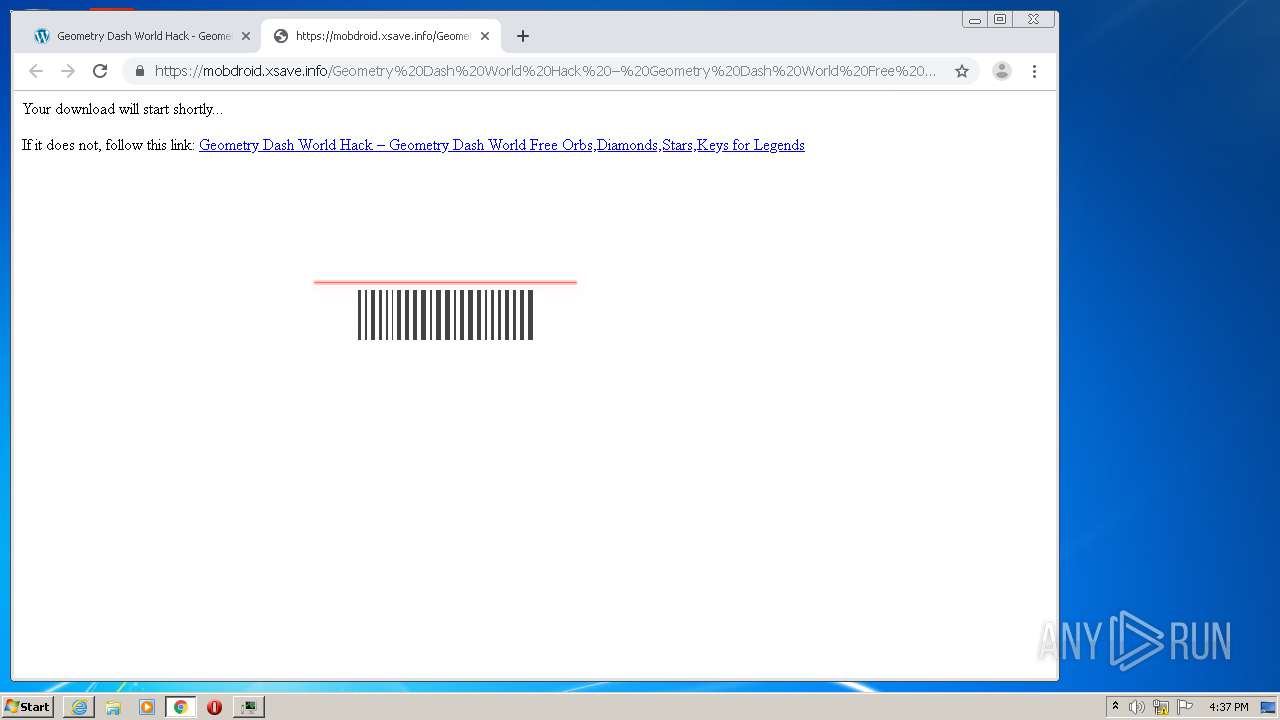
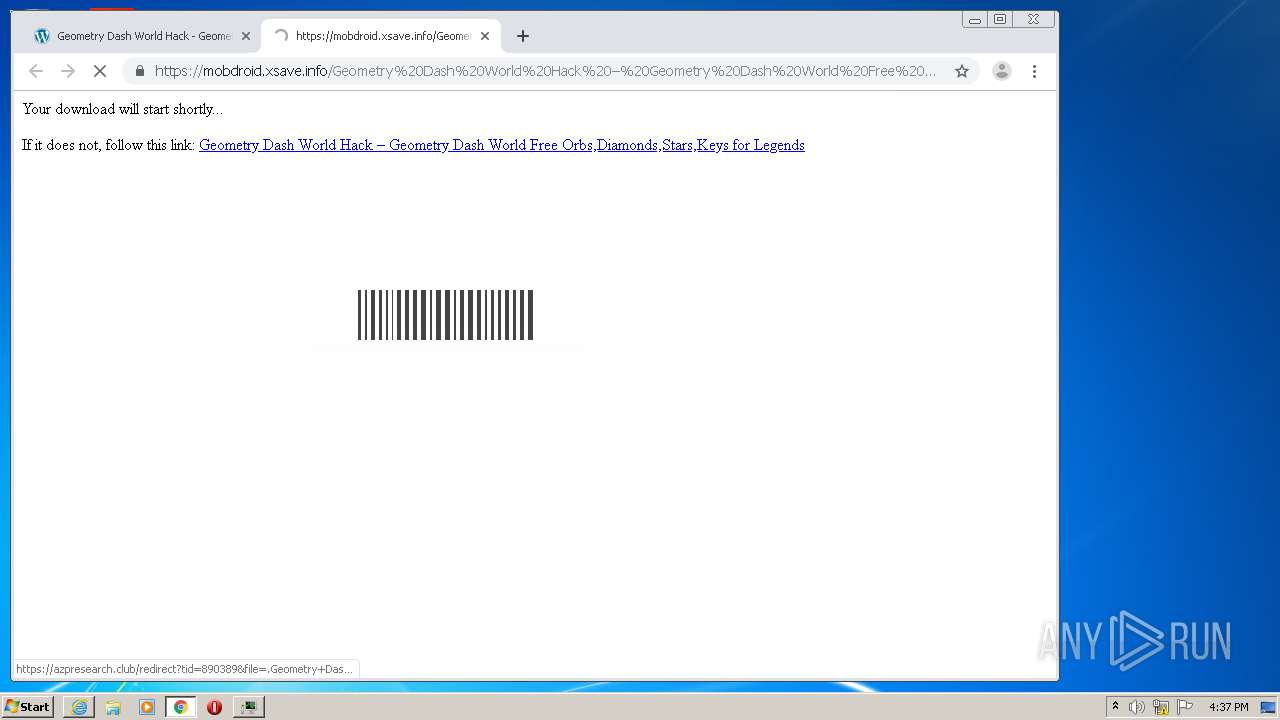
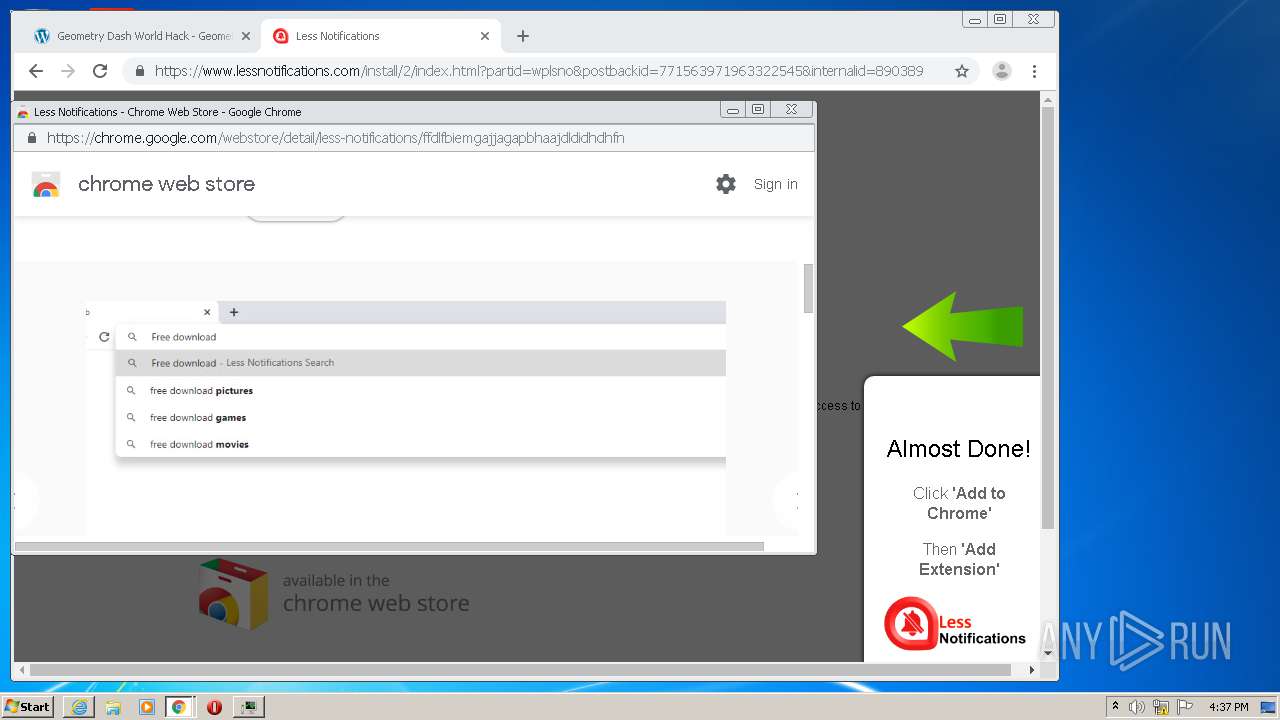
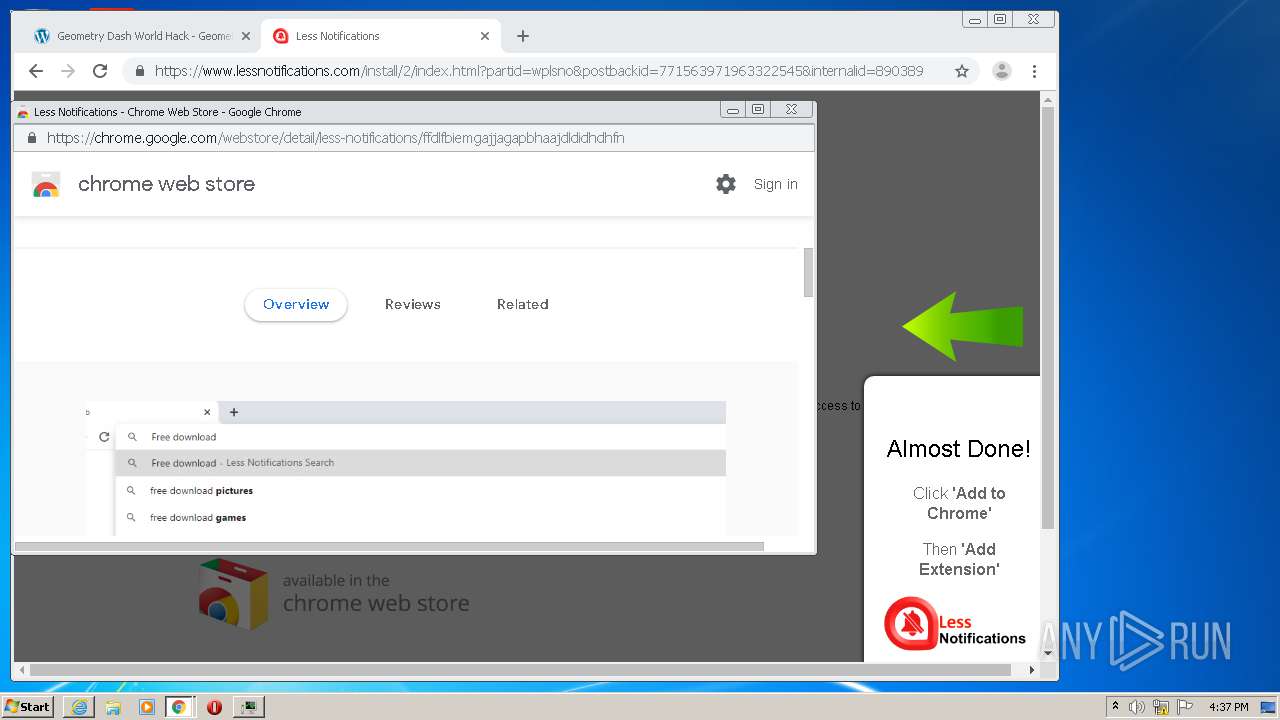
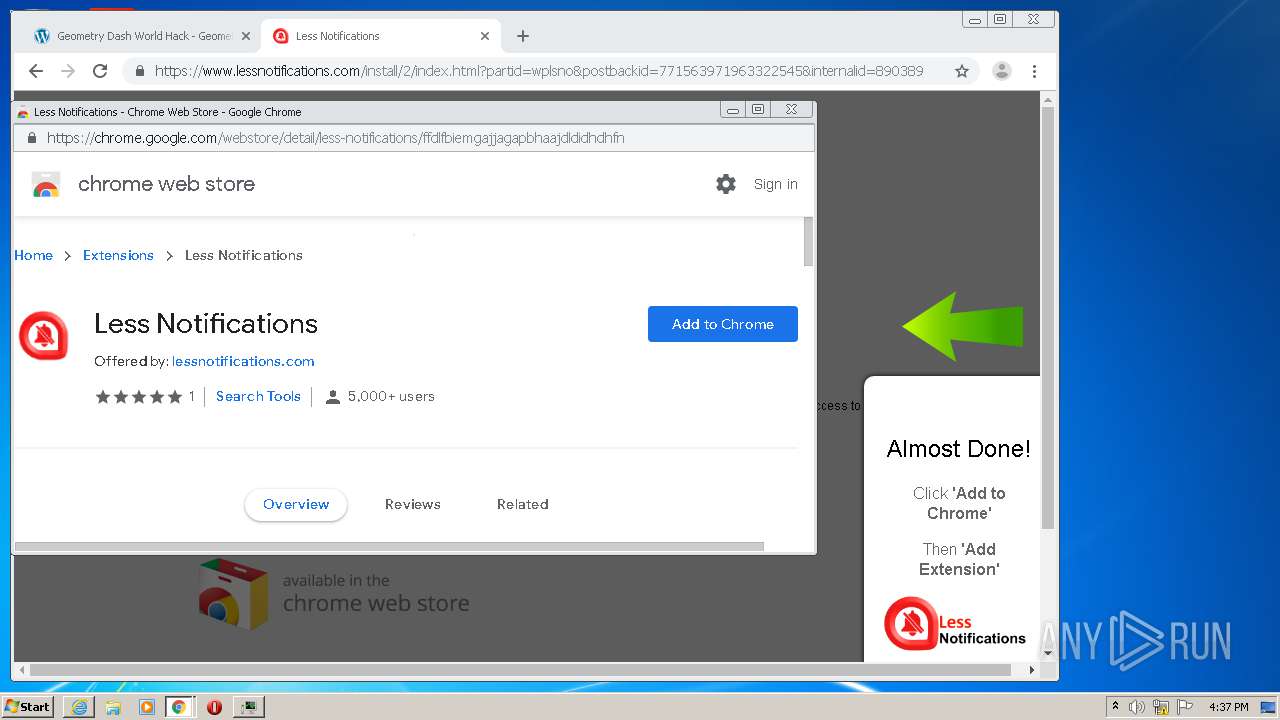
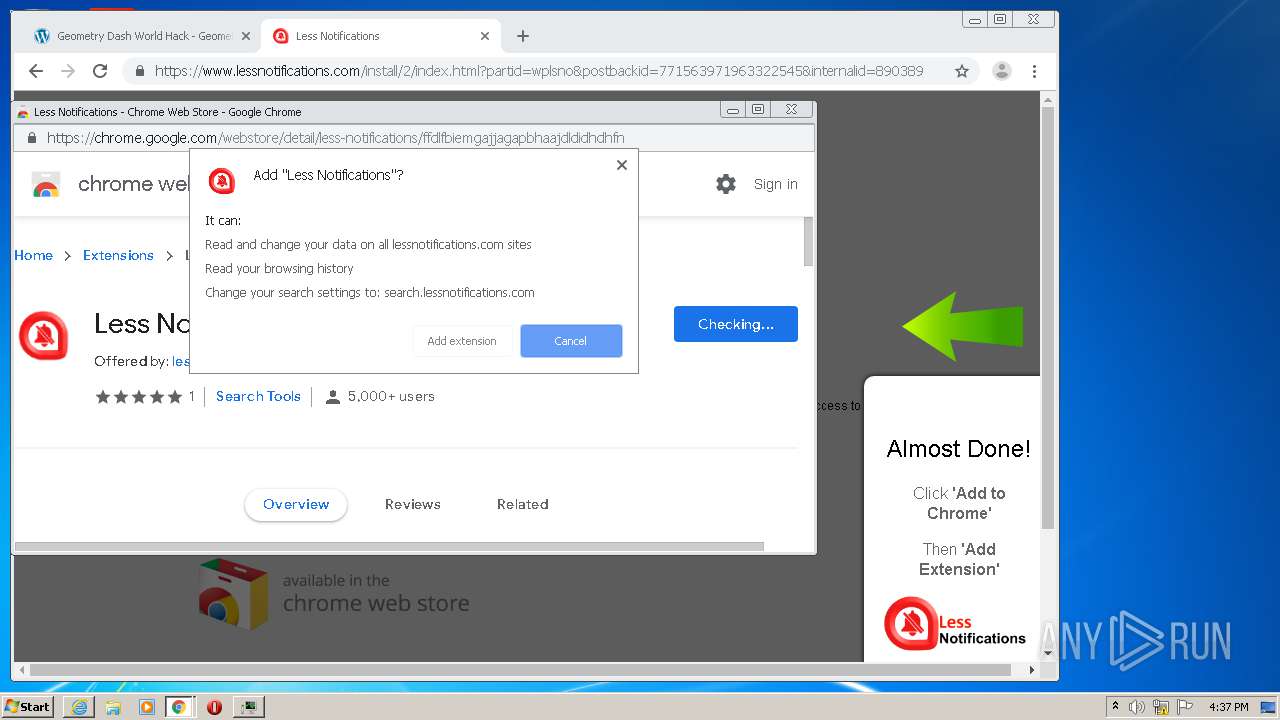
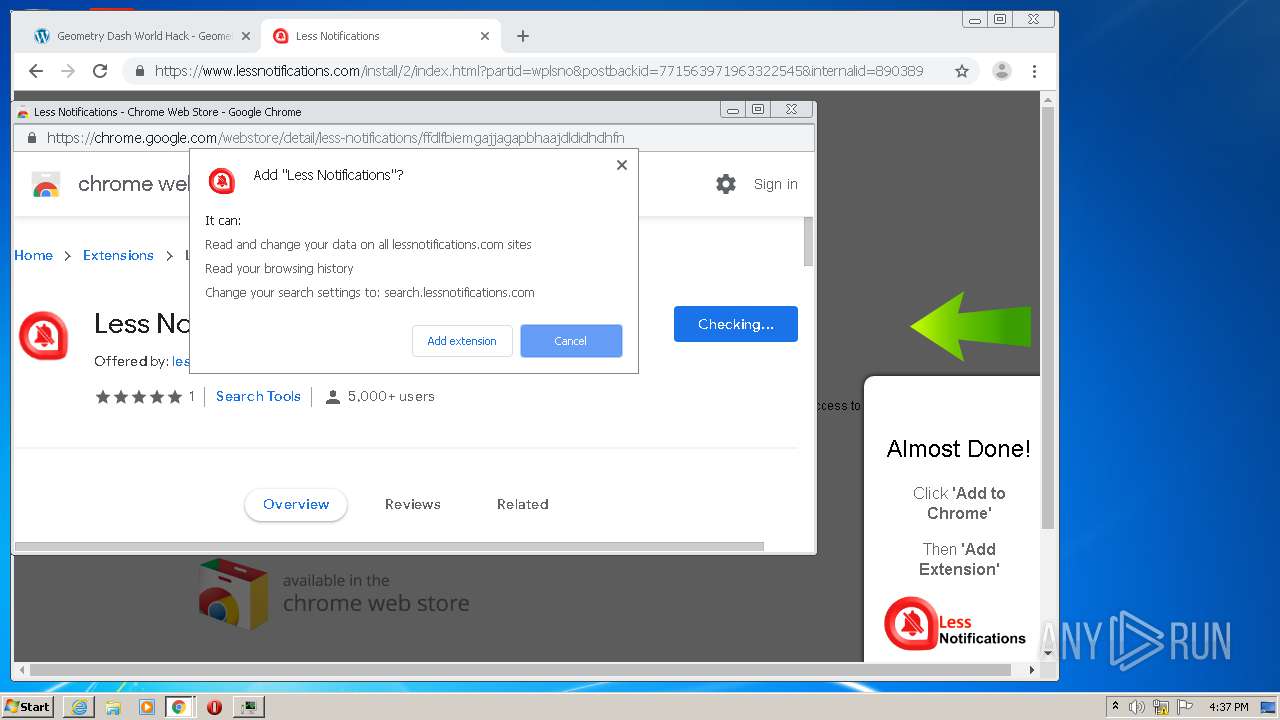
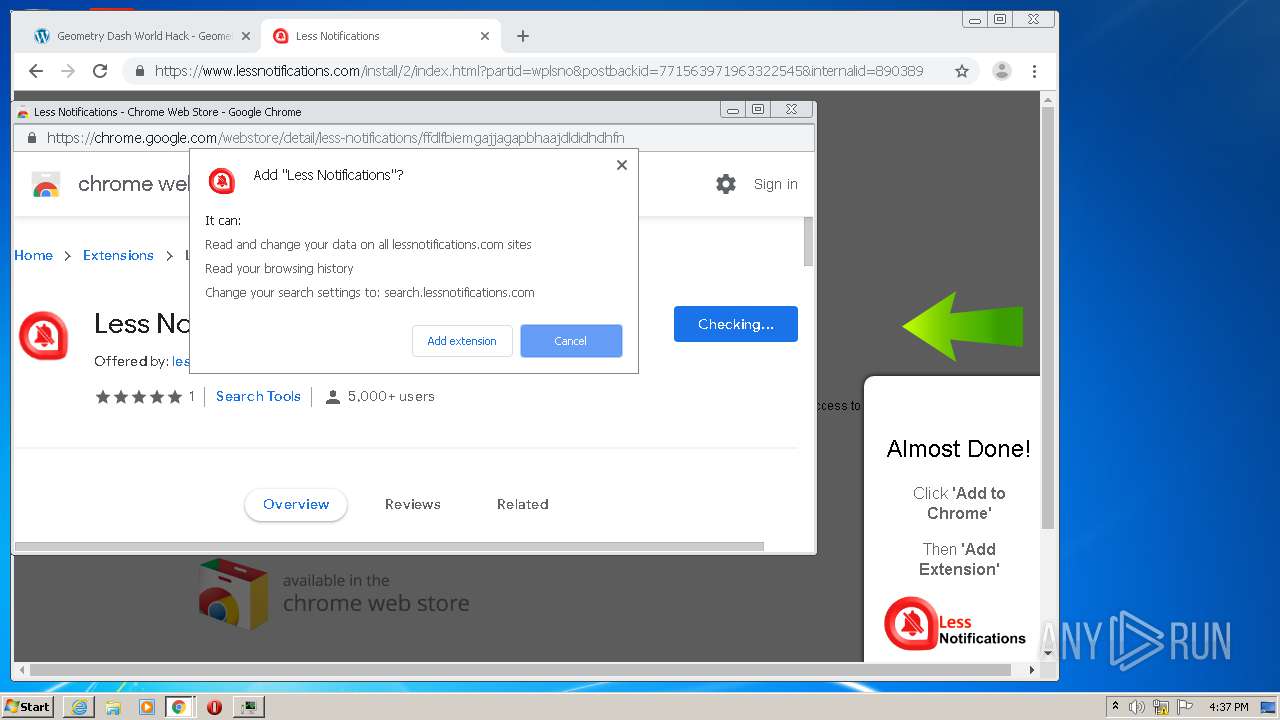
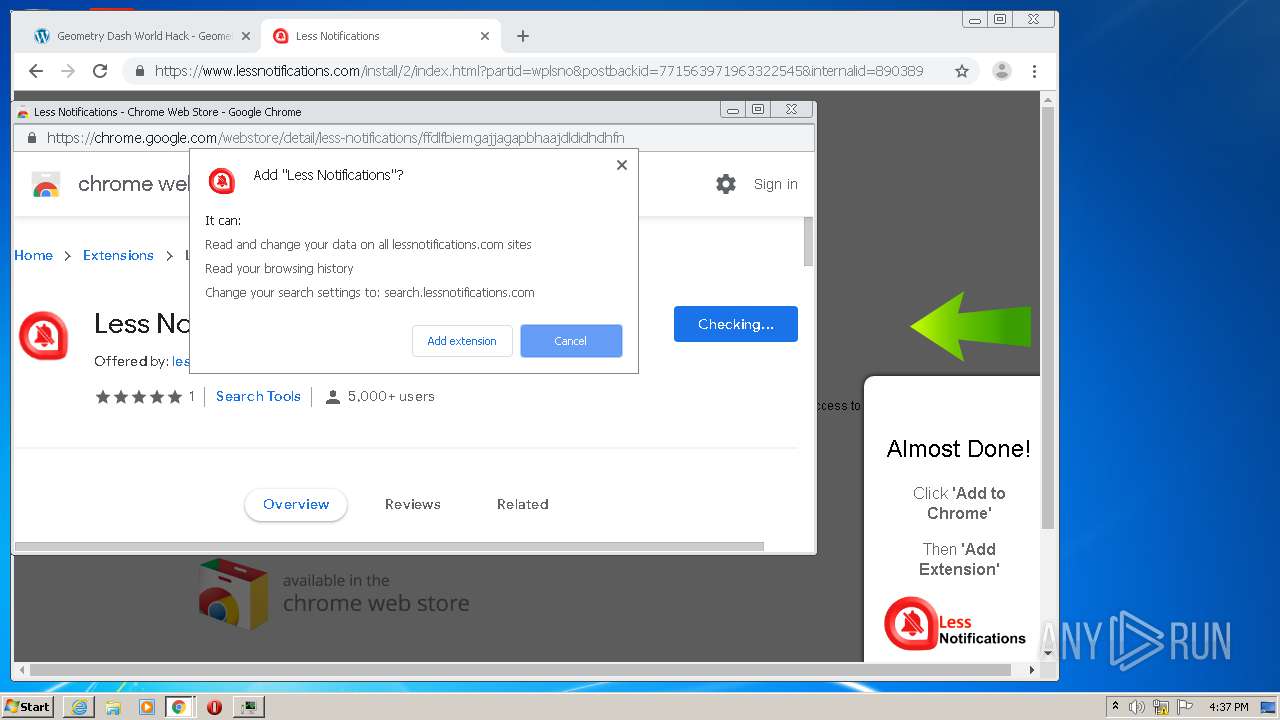
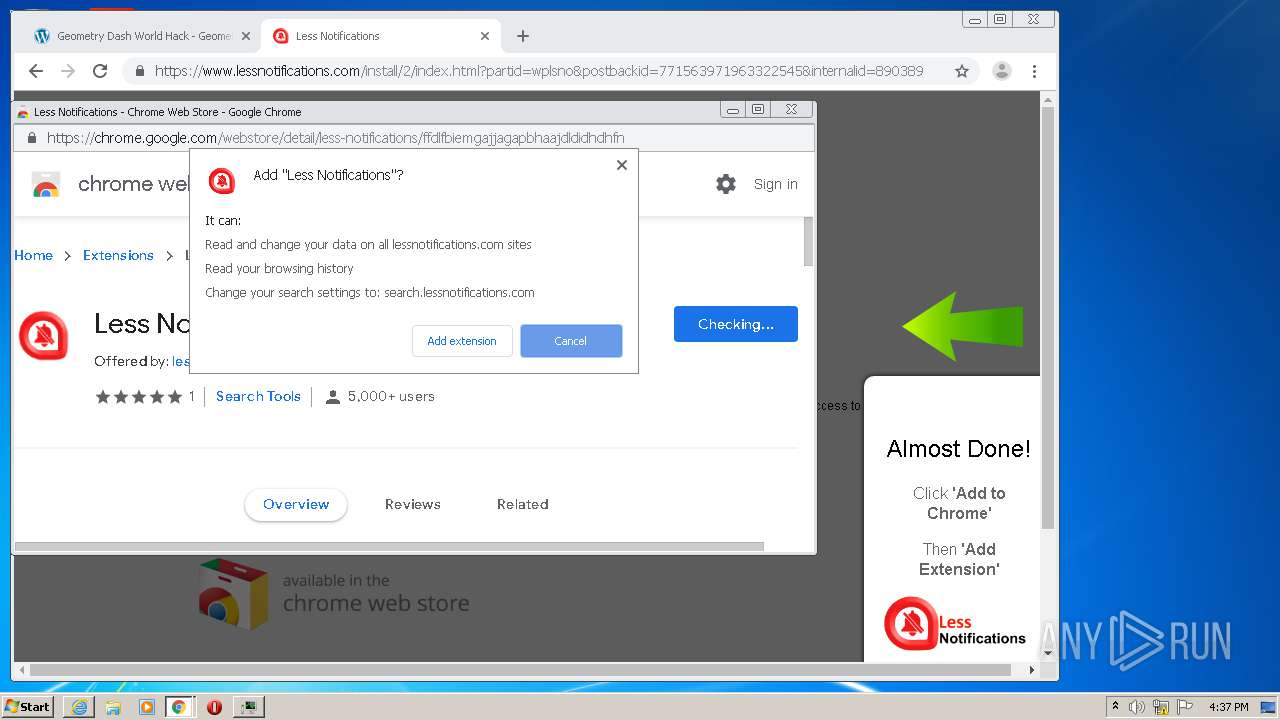
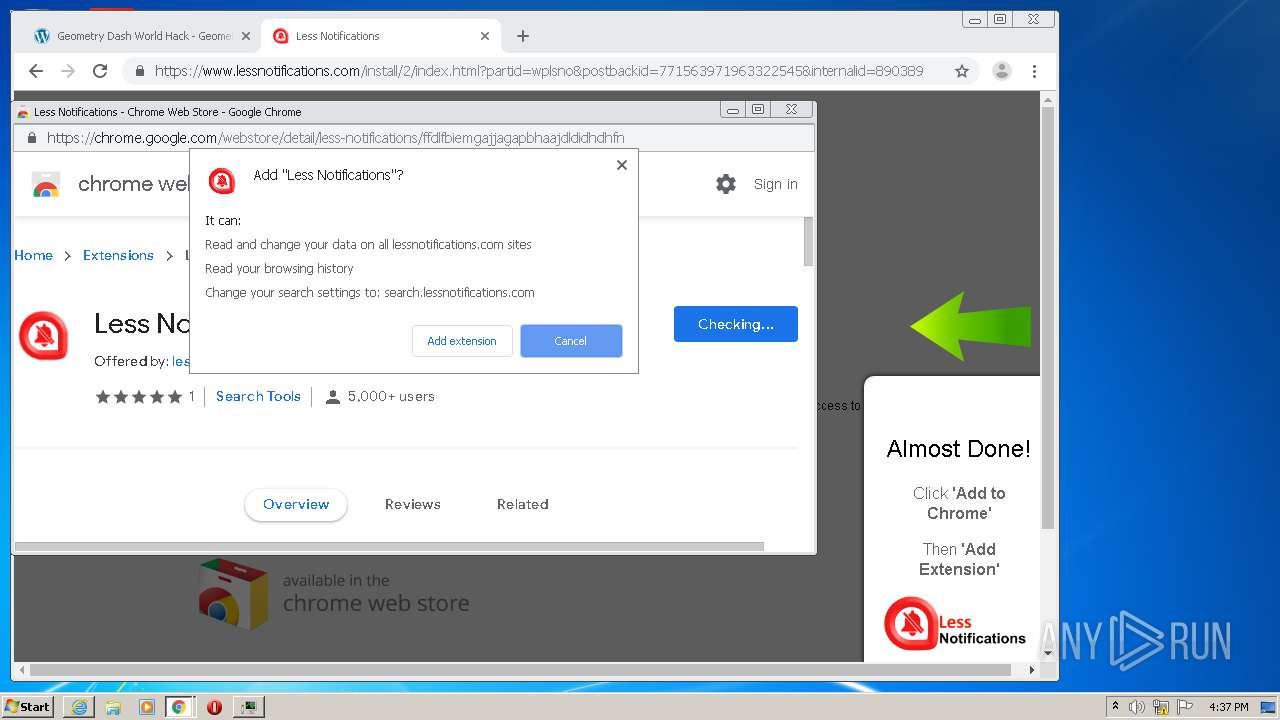
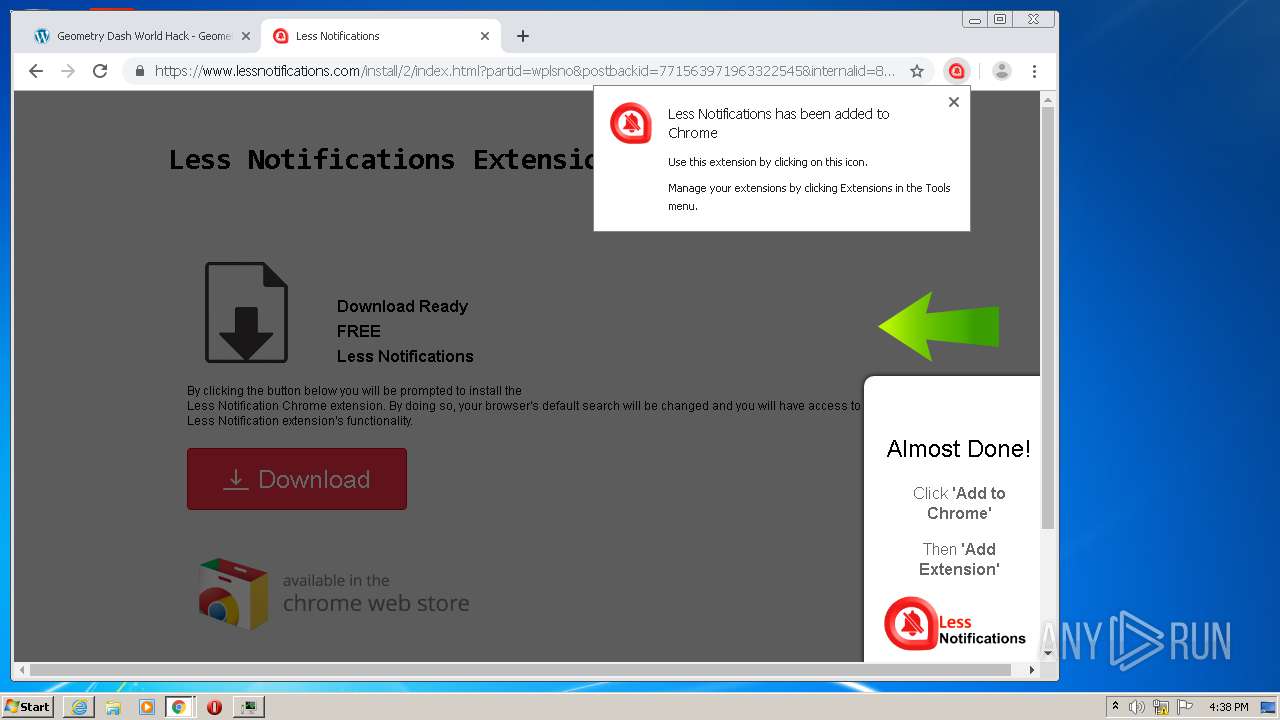
| URL: | https://www.e-slots.info/geometry-dash-mega-hack-v6-pro-2-113-steam-paid/ |
| Full analysis: | https://app.any.run/tasks/2876ea2a-ccaf-4968-9771-1ced7c8ec96c |
| Verdict: | Malicious activity |
| Analysis date: | September 04, 2020, 15:33:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E82CA865E239D98BDA0C58E9AF2B0CE7 |
| SHA1: | D007FC660E7A804D5035D186C0A23477C735051E |
| SHA256: | 095D3C918A13A5F17B5E5146045A8C815A57916F14751C3BF92CA913862893E5 |
| SSDEEP: | 3:N8DSLk4MYRPu/OudVW4AK:2OLk4Mci/v |
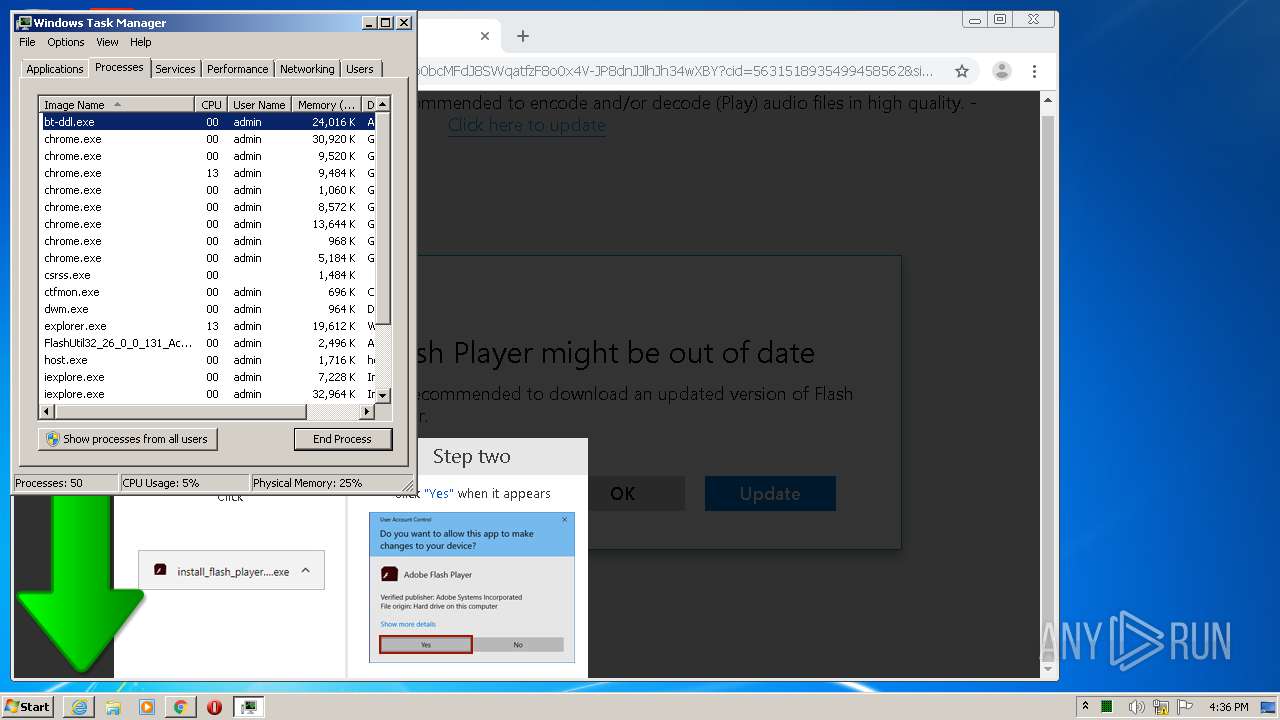
MALICIOUS
Application was dropped or rewritten from another process
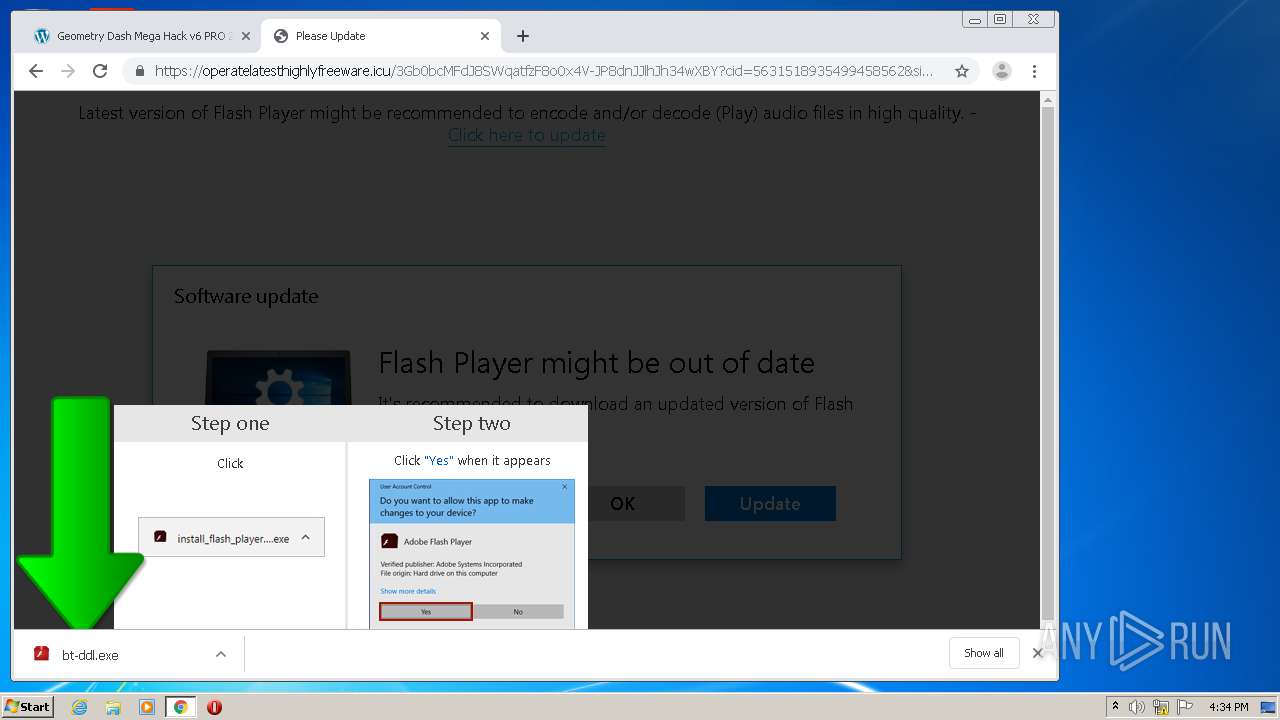
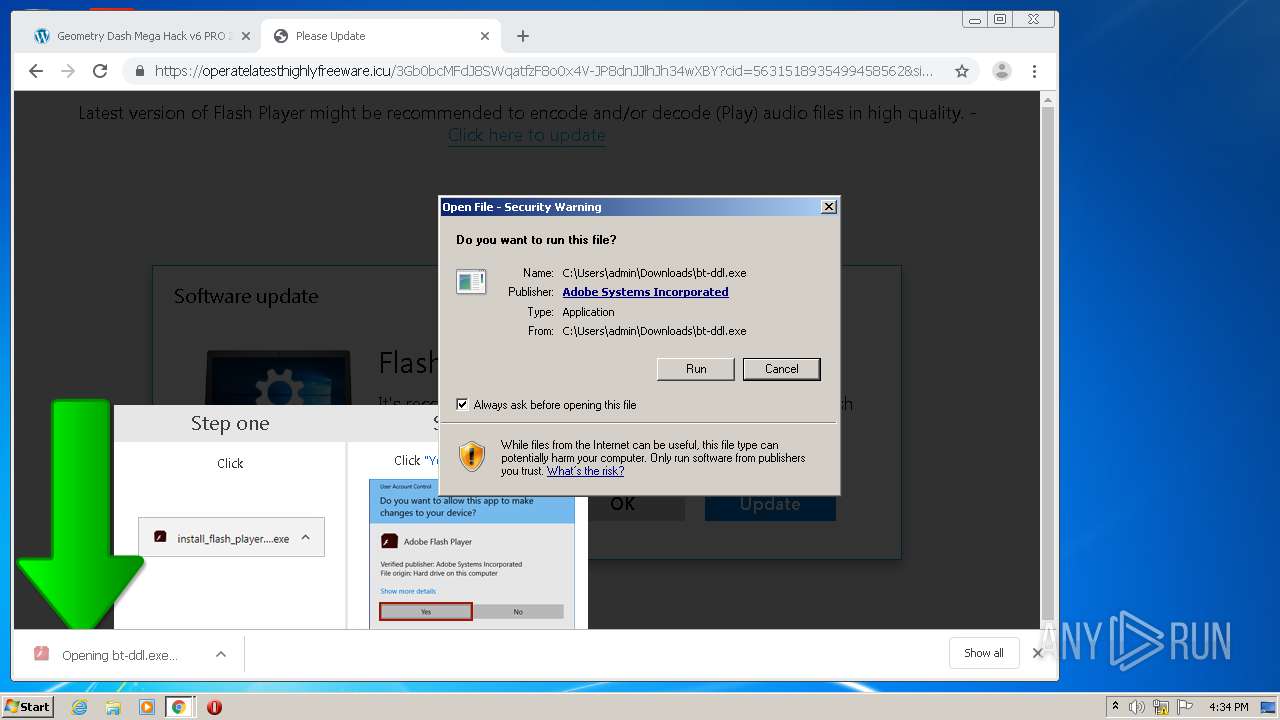
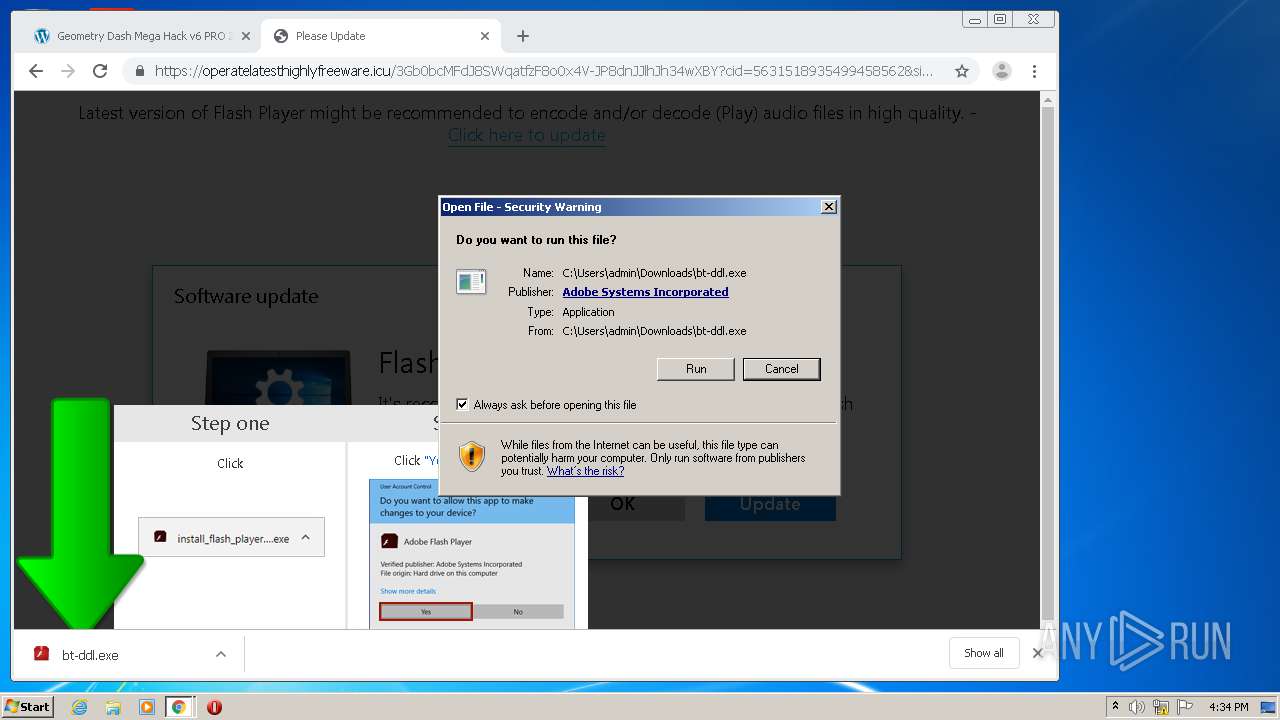
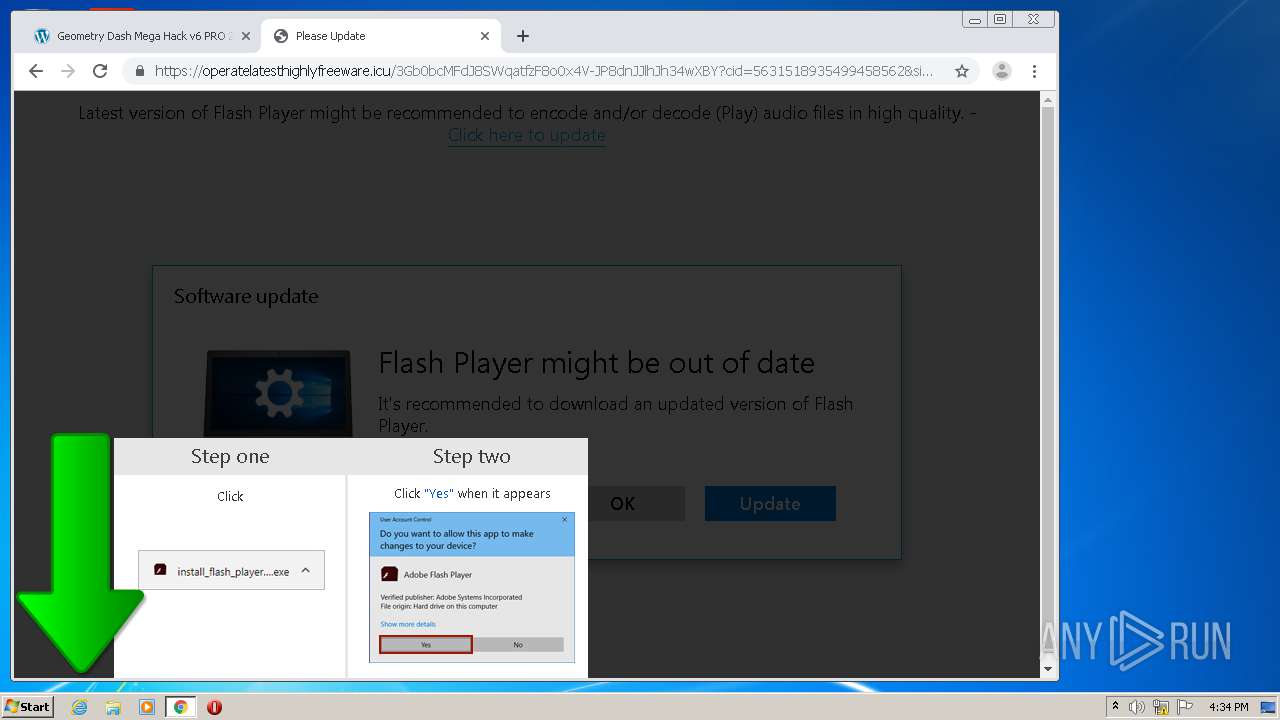
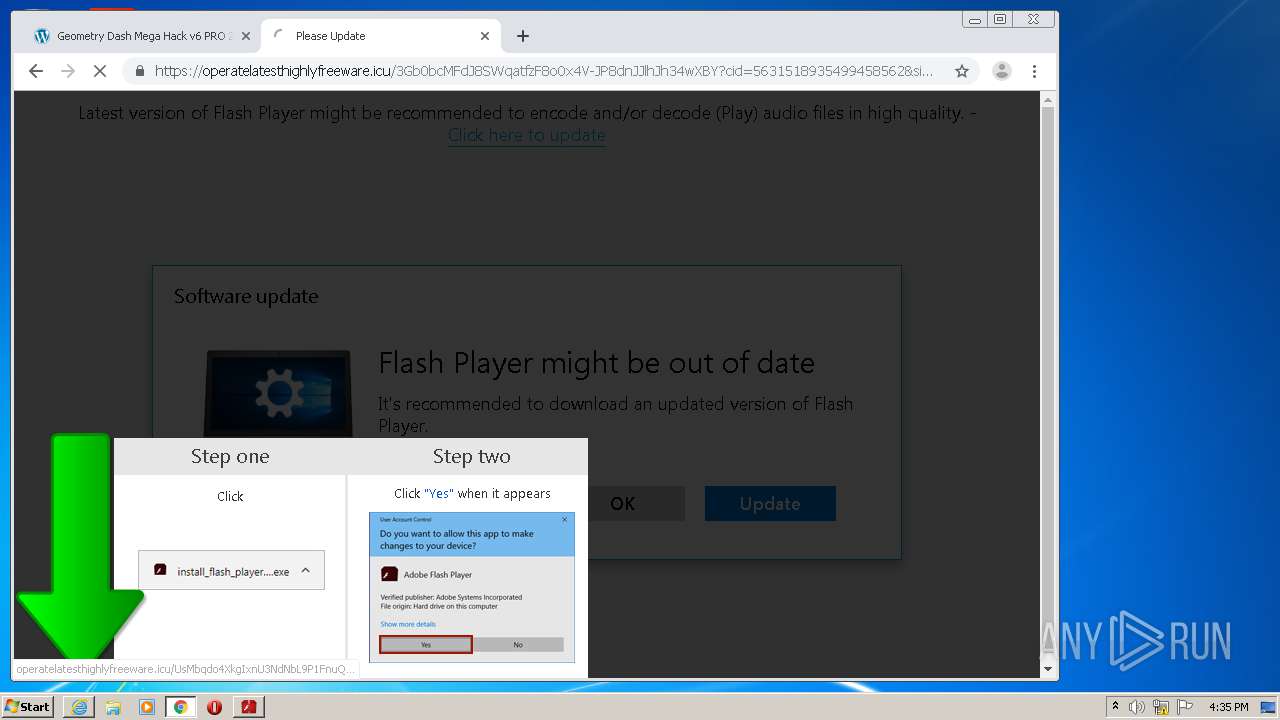
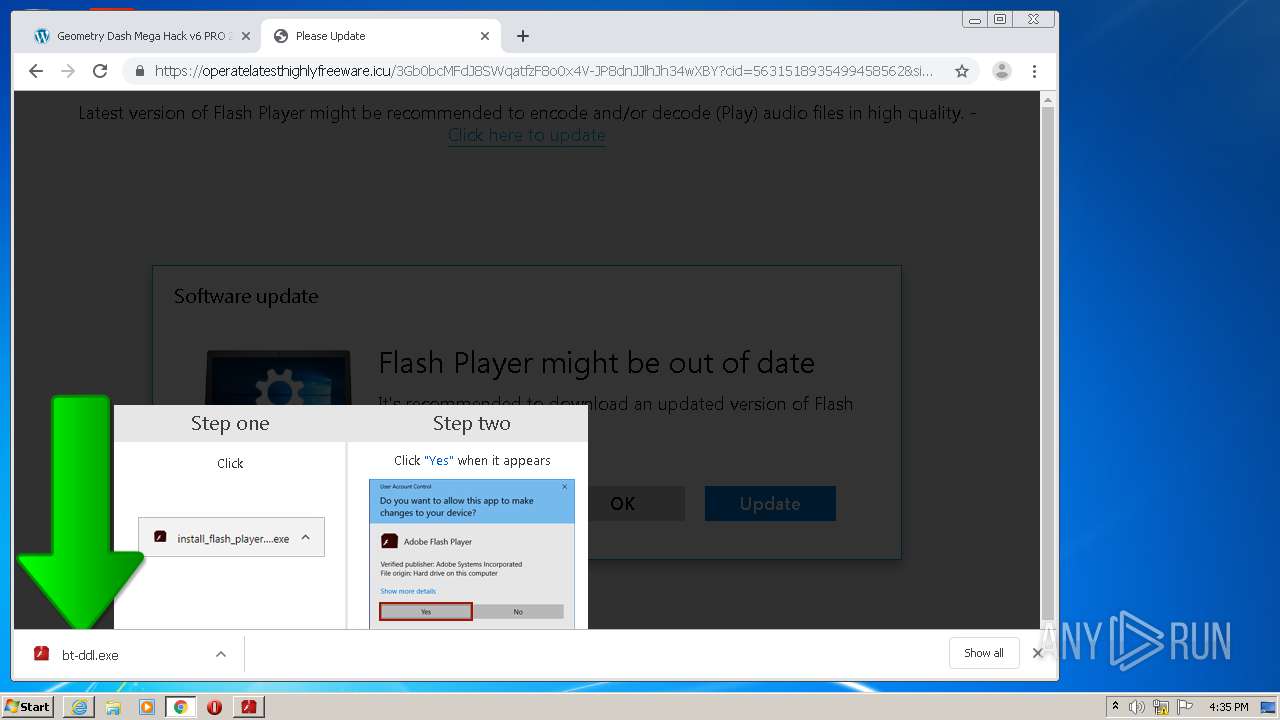
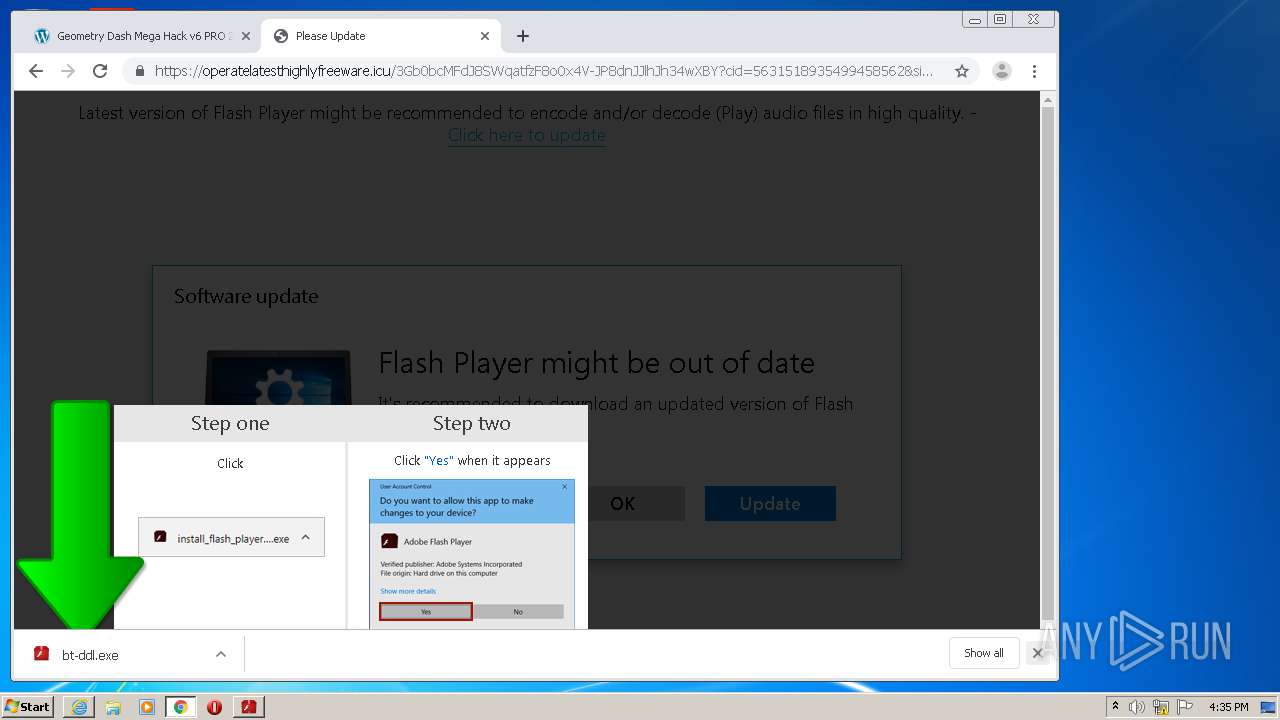
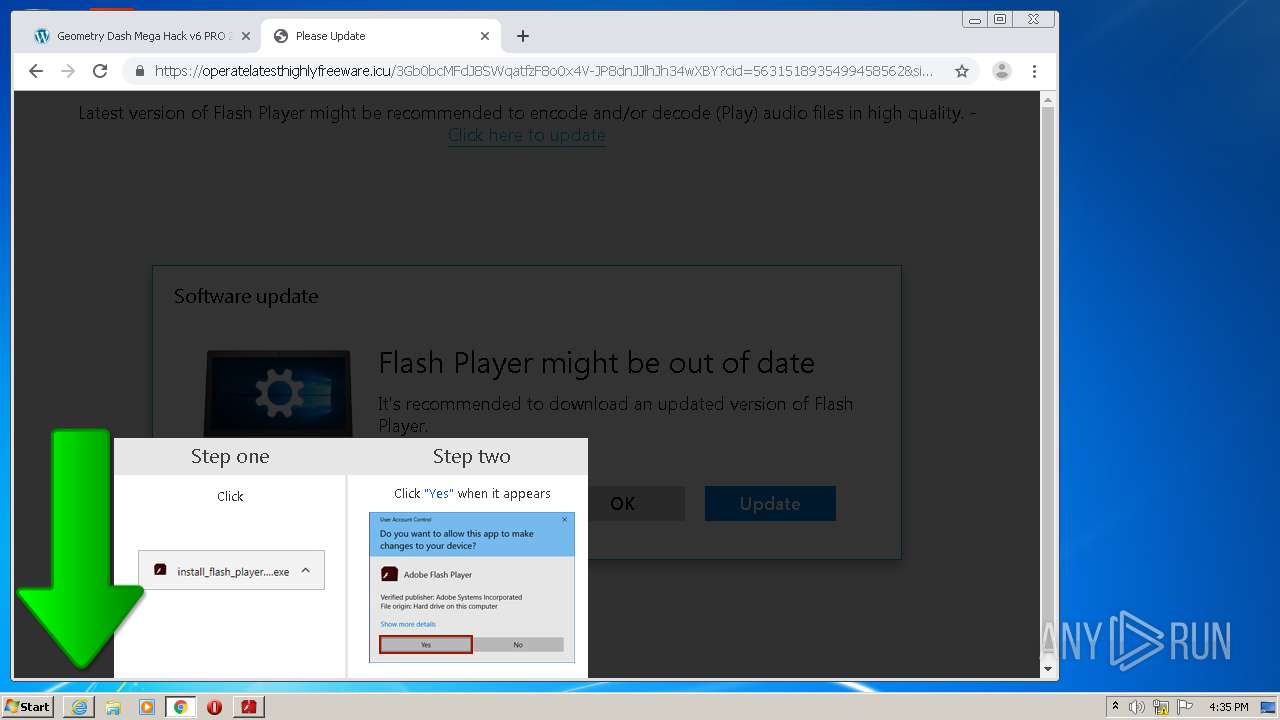
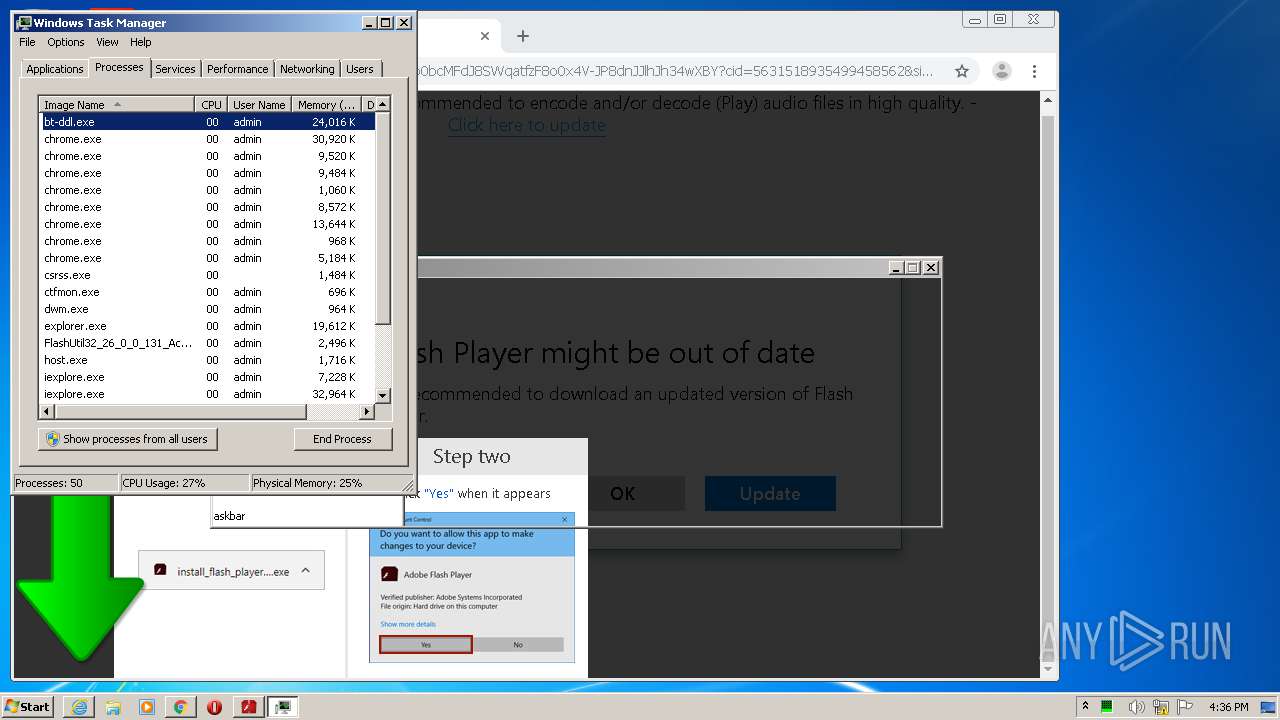
- bt-ddl.exe (PID: 1024)
- bt-ddl.exe (PID: 2768)
Changes settings of System certificates
- bt-ddl.exe (PID: 2768)
Loads dropped or rewritten executable
- bt-ddl.exe (PID: 2768)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 940)
- chrome.exe (PID: 2868)
- bt-ddl.exe (PID: 2768)
Application launched itself
- bt-ddl.exe (PID: 1024)
Reads Internet Cache Settings
- bt-ddl.exe (PID: 2768)
Creates files in the user directory
- bt-ddl.exe (PID: 2768)
Cleans NTFS data-stream (Zone Identifier)
- bt-ddl.exe (PID: 1024)
Adds / modifies Windows certificates
- bt-ddl.exe (PID: 2768)
Reads internet explorer settings
- bt-ddl.exe (PID: 2768)
Starts Internet Explorer
- bt-ddl.exe (PID: 2768)
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 1700)
Modifies files in Chrome extension folder
- chrome.exe (PID: 940)
INFO
Application launched itself
- iexplore.exe (PID: 2204)
- chrome.exe (PID: 940)
- iexplore.exe (PID: 1200)
Reads Internet Cache Settings
- iexplore.exe (PID: 2548)
- iexplore.exe (PID: 2204)
- chrome.exe (PID: 940)
- iexplore.exe (PID: 1200)
- iexplore.exe (PID: 1920)
Changes internet zones settings
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 1200)
Reads internet explorer settings
- iexplore.exe (PID: 2548)
- iexplore.exe (PID: 1920)
Reads settings of System Certificates
- iexplore.exe (PID: 2548)
- iexplore.exe (PID: 2204)
- chrome.exe (PID: 2868)
- chrome.exe (PID: 940)
- bt-ddl.exe (PID: 2768)
- iexplore.exe (PID: 1920)
- iexplore.exe (PID: 1200)
Creates files in the user directory
- iexplore.exe (PID: 2548)
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 1920)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 1700)
- iexplore.exe (PID: 1200)
- chrome.exe (PID: 940)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 1200)
Changes settings of System certificates
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 1200)
Reads the hosts file
- chrome.exe (PID: 940)
- chrome.exe (PID: 2868)
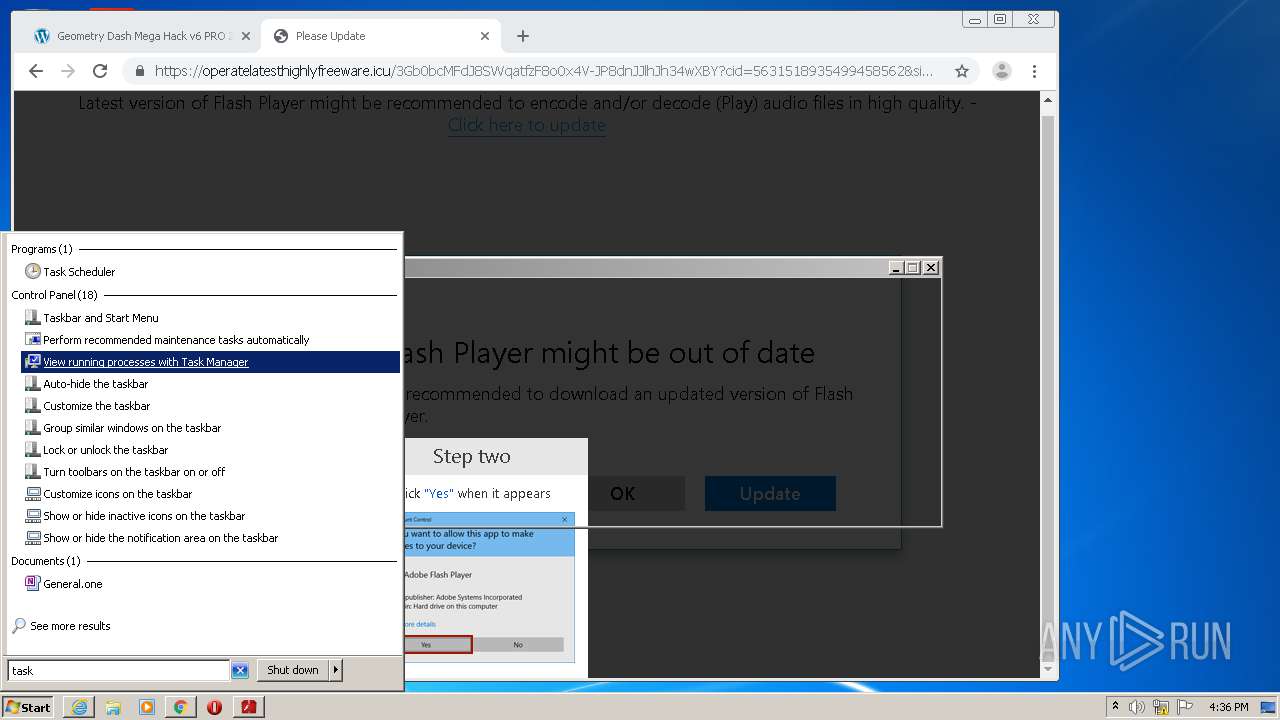
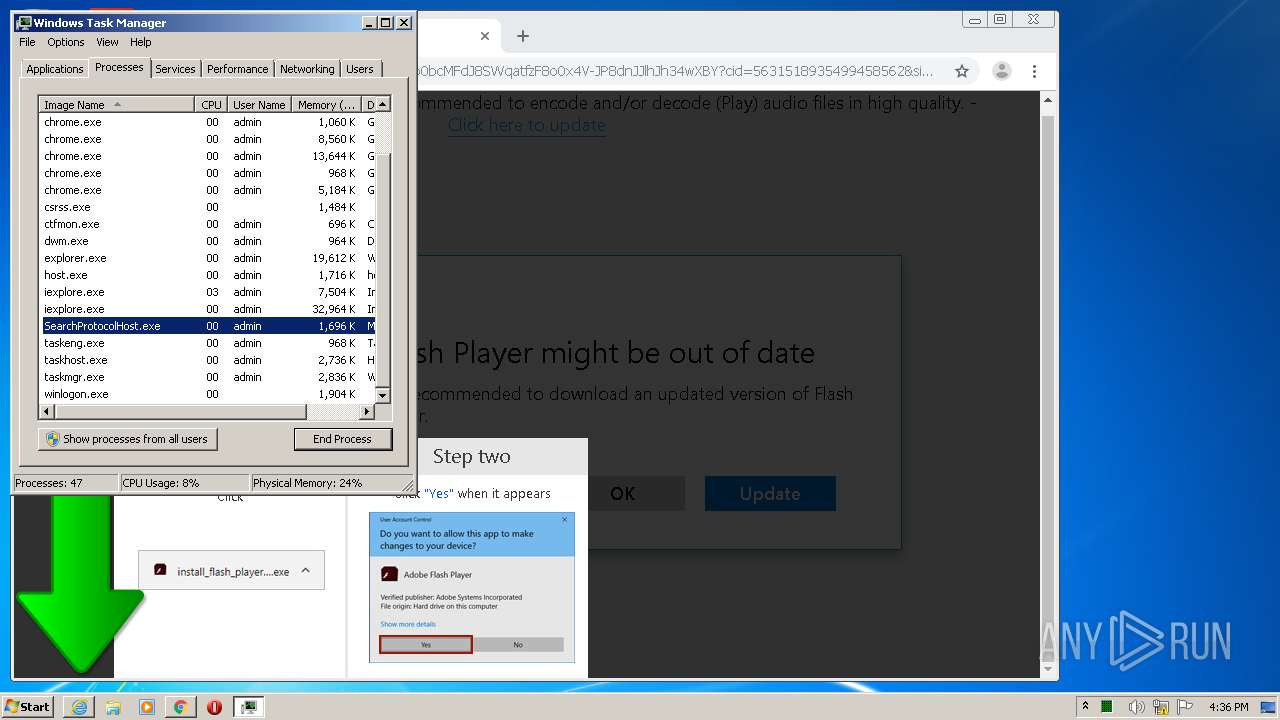
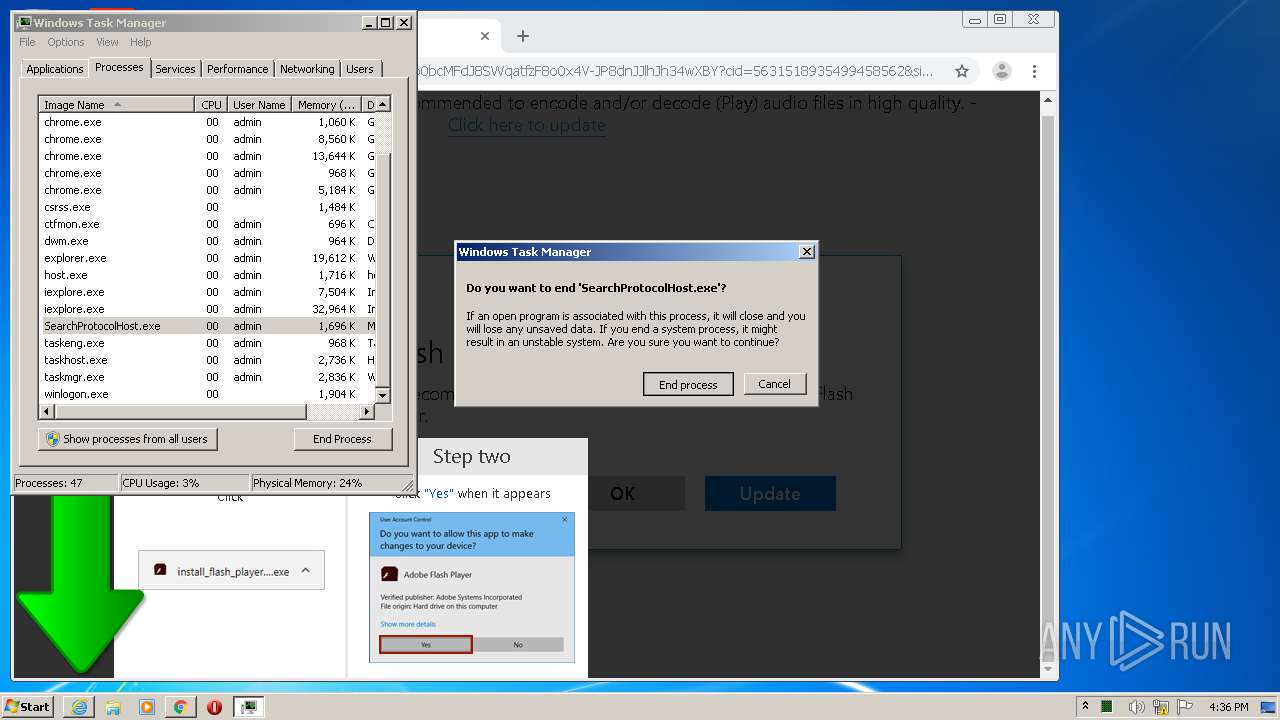
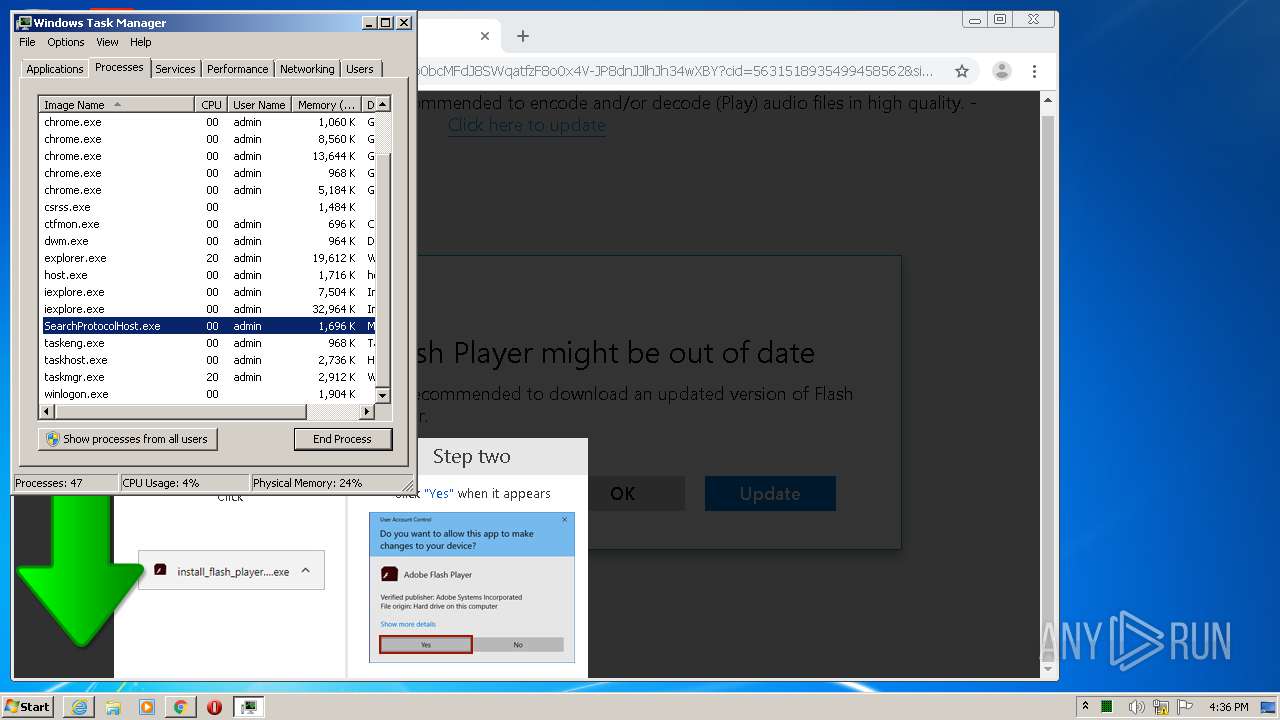
Manual execution by user
- chrome.exe (PID: 940)
- taskmgr.exe (PID: 2348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
104
Monitored processes
59
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1008,1596629583247729819,8227236031316374582,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=6069652004636858377 --mojo-platform-channel-handle=1292 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 624 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,1596629583247729819,8227236031316374582,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7480212627836033119 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2244 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 684 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,1596629583247729819,8227236031316374582,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12323597849255153139 --renderer-client-id=45 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4908 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 888 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,1596629583247729819,8227236031316374582,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17682852646379074091 --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2944 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 940 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1024 | "C:\Users\admin\Downloads\bt-ddl.exe" | C:\Users\admin\Downloads\bt-ddl.exe | — | chrome.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe Installation Helper Exit code: 0 Version: 3.5.4.26 Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,1596629583247729819,8227236031316374582,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13386420731729488157 --renderer-client-id=47 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5020 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
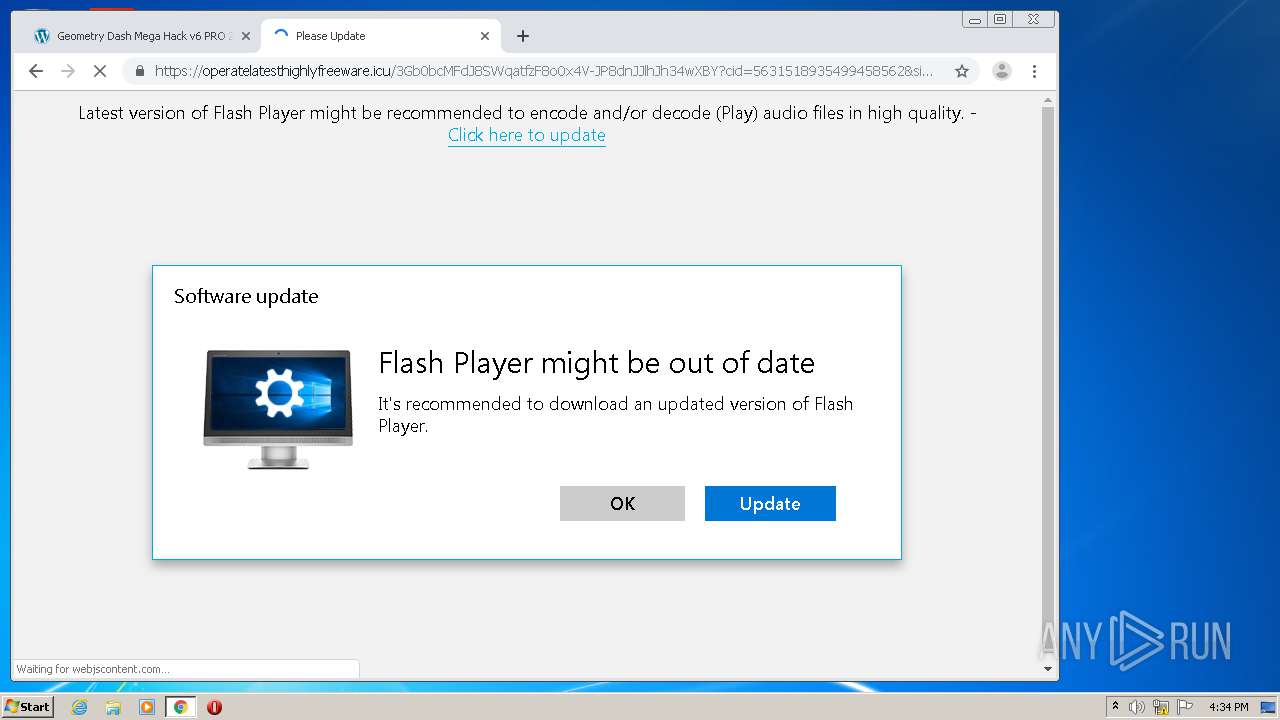
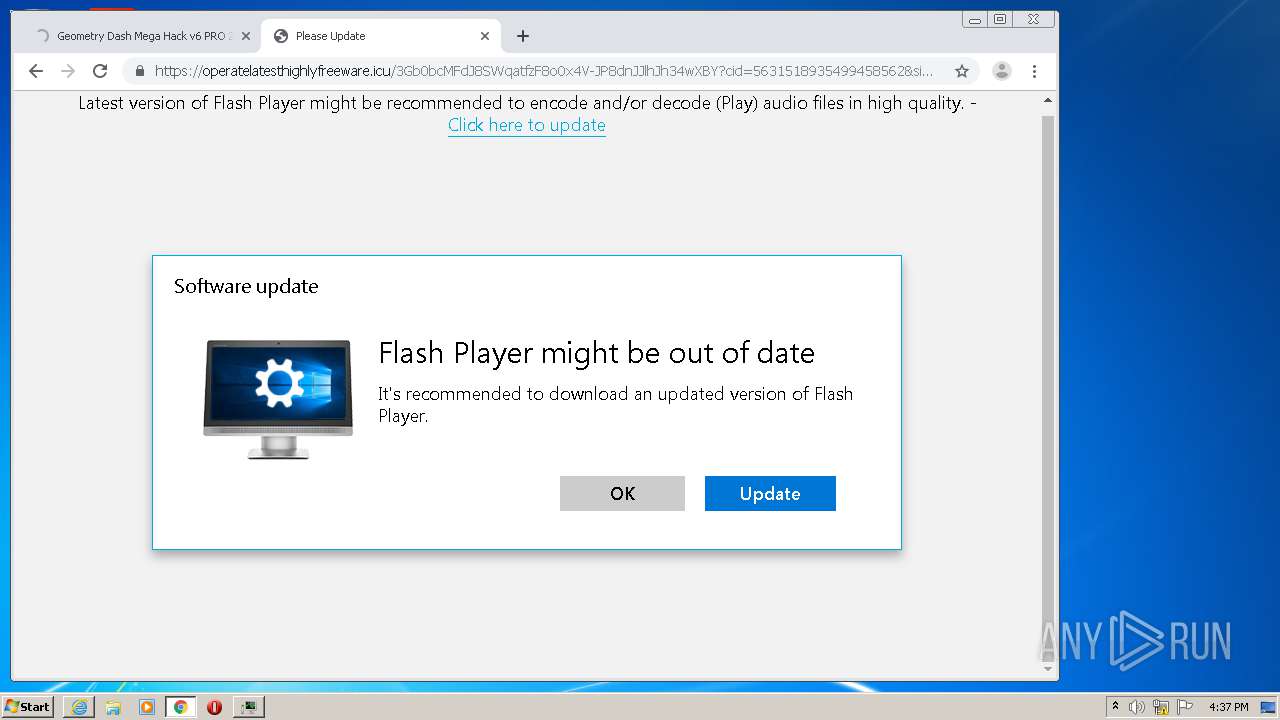
| 1200 | "C:\Program Files\Internet Explorer\iexplore.exe" https://get.adobe.com/flashplayer/completion/aih/?exitcode=-1 | C:\Program Files\Internet Explorer\iexplore.exe | bt-ddl.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,1596629583247729819,8227236031316374582,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6420085333203877733 --mojo-platform-channel-handle=2096 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,1596629583247729819,8227236031316374582,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12202796861257300973 --mojo-platform-channel-handle=4736 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
3 223
Read events
2 907
Write events
304
Delete events
12
Modification events
| (PID) Process: | (2204) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3482076982 | |||
| (PID) Process: | (2204) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30835408 | |||
| (PID) Process: | (2204) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2204) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2204) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2204) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2204) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2204) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A3000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2204) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2204) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
7
Suspicious files
164
Text files
280
Unknown types
38
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2548 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab822E.tmp | — | |
MD5:— | SHA256:— | |||
| 2548 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar822F.tmp | — | |
MD5:— | SHA256:— | |||
| 2548 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\WE14OUZQ.txt | text | |
MD5:— | SHA256:— | |||
| 2548 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\cb6f32c3d0907ab054b8f3e816eb2af5[1].js | text | |
MD5:— | SHA256:— | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].ico | image | |
MD5:9FB559A691078558E77D6848202F6541 | SHA256:6D8A01DC7647BC218D003B58FE04049E24A9359900B7E0CEBAE76EDF85B8B914 | |||
| 2548 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\82CB34DD3343FE727DF8890D352E0D8F | der | |
MD5:— | SHA256:— | |||
| 2548 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\82CB34DD3343FE727DF8890D352E0D8F | binary | |
MD5:— | SHA256:— | |||
| 2548 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | der | |
MD5:— | SHA256:— | |||
| 2548 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\geometry-dash-mega-hack-v6-pro-2-113-steam-paid[1].htm | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
150
DNS requests
113
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2768 | bt-ddl.exe | GET | 302 | 15.188.154.177:80 | http://stats.adobe.com/b/ss/adbacdcprod/1/H.25.4/s755090854031?AQB=1&ndh=1&t=4%2F8%2F2020%2016%3A34%3A54%205%20-60&fid=0C84A3AE3550DA30-228AFE70646DFD0C&ce=UTF-8&ns=adobecorp&pageName=acdc_fp_aih_launched&g=http%3A%2F%2F127.0.0.1%3A50519%2Fmainwindow.html&ch=acdc_flashplayer&events=event96%2Cevent19&products=%3Bflashplayer_aih&c1=aih&c2=acdc%20downloads&c3=get.adobe.com&c4=en&c5=en%3Aacdc_fp_aih_launched&v18=new&v22=friday%20-%209%3A30am&v73=acdc_flashplayer&s=1280x720&c=32&j=1.6&v=Y&k=Y&bw=728&bh=248&ct=lan&hp=N&AQE=1 | US | — | — | whitelisted |
2548 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
2548 | iexplore.exe | GET | 200 | 216.58.205.227:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEGPZqrycpduCCAAAAABUy10%3D | US | der | 471 b | whitelisted |
2548 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 5.42 Kb | whitelisted |
2548 | iexplore.exe | GET | 200 | 104.28.27.24:80 | http://www.e-slots.info/wp-content/themes/hannari/images/menuicon.png | US | image | 2.80 Kb | malicious |
2548 | iexplore.exe | GET | 200 | 216.58.205.227:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEET%2BoT01jxDcCAAAAABUygk%3D | US | der | 471 b | whitelisted |
2868 | chrome.exe | GET | 204 | 35.190.74.30:80 | http://www.liveadoptimizer.com/jump/next.php?stamat=m%7C%2CsIiPWo2arB1dQO0dEdHP3xP.615%2CS0kXXHXf2ck-DOZ9HRvwuM9aL_G46JdZU-2oa3bmXM_i4kFHSibmLHNC4QWHAlMovz0rFbFNdrsU8Hz9pH0cbg%2C%2C&cbrandom=0.3288744470320566&cbtitle=&cbiframe=0&cbWidth=1042&cbHeight=587&cbdescription=&cbkeywords=&cbref= | US | compressed | 2.55 Kb | suspicious |
2868 | chrome.exe | GET | 200 | 35.190.74.30:80 | http://www.liveadoptimizer.com/jump/next.php?r=335365&sub1=27526_99_16 | US | html | 2.55 Kb | suspicious |
2548 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgNPa1ZIp4hQ40WPhAJrhoMIOw%3D%3D | unknown | der | 527 b | whitelisted |
2868 | chrome.exe | GET | 200 | 35.190.74.30:80 | http://www.liveadoptimizer.com/jump/next.php?r=335365&sub1=27526_99_16 | US | html | 2.55 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2548 | iexplore.exe | 104.28.27.24:443 | www.e-slots.info | Cloudflare Inc | US | unknown |
2548 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2204 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2548 | iexplore.exe | 172.217.22.40:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
2548 | iexplore.exe | 104.28.21.198:443 | linkstate.info | Cloudflare Inc | US | unknown |
2548 | iexplore.exe | 159.65.89.65:443 | www.7-zip.org | — | US | suspicious |
2548 | iexplore.exe | 172.217.21.246:443 | i.ytimg.com | Google Inc. | US | whitelisted |
2548 | iexplore.exe | 2.16.186.11:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
2548 | iexplore.exe | 104.28.27.24:80 | www.e-slots.info | Cloudflare Inc | US | unknown |
2204 | iexplore.exe | 104.28.27.24:443 | www.e-slots.info | Cloudflare Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.e-slots.info |
| malicious |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
linkstate.info |
| suspicious |
www.7-zip.org |
| whitelisted |
i.ytimg.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
2868 | chrome.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.icu) in TLS SNI |
2868 | chrome.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.icu) |