| URL: | https://www.7-zip.org/a/7z2201.exe |
| Full analysis: | https://app.any.run/tasks/2d107975-3bf9-4243-8091-503452074a93 |
| Verdict: | Malicious activity |
| Analysis date: | July 22, 2022, 11:29:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 0CDF816BD27453E845832A6F9AF2BD6E |
| SHA1: | D3C7A9B59F32AA3A527B356EAFF73F2E618E59F6 |
| SHA256: | 094F07F29745472CB522CA5B49002B7556FAD56B3CFA7EDE87F86C50117858F7 |
| SSDEEP: | 3:N8DSLohGACn:2OLoAACn |
MALICIOUS
Drops executable file immediately after starts
- iexplore.exe (PID: 912)
- iexplore.exe (PID: 1620)
- 7z2201.exe (PID: 3180)
Application was dropped or rewritten from another process
- 7z2201.exe (PID: 2568)
- 7z2201.exe (PID: 3180)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 912)
Drops a file with a compile date too recent
- iexplore.exe (PID: 1620)
- iexplore.exe (PID: 912)
- 7z2201.exe (PID: 3180)
Executable content was dropped or overwritten
- iexplore.exe (PID: 912)
- iexplore.exe (PID: 1620)
- 7z2201.exe (PID: 3180)
Checks supported languages
- 7z2201.exe (PID: 3180)
Creates/Modifies COM task schedule object
- 7z2201.exe (PID: 3180)
Creates a directory in Program Files
- 7z2201.exe (PID: 3180)
Reads the computer name
- 7z2201.exe (PID: 3180)
Creates a software uninstall entry
- 7z2201.exe (PID: 3180)
Creates files in the program directory
- 7z2201.exe (PID: 3180)
INFO
Checks supported languages
- iexplore.exe (PID: 1620)
- iexplore.exe (PID: 912)
Reads the computer name
- iexplore.exe (PID: 1620)
- iexplore.exe (PID: 912)
Changes internet zones settings
- iexplore.exe (PID: 1620)
Application launched itself
- iexplore.exe (PID: 1620)
Reads settings of System Certificates
- iexplore.exe (PID: 912)
- iexplore.exe (PID: 1620)
Reads the date of Windows installation
- iexplore.exe (PID: 1620)
Checks Windows Trust Settings
- iexplore.exe (PID: 912)
- iexplore.exe (PID: 1620)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 912 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1620 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1620 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.7-zip.org/a/7z2201.exe" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2568 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\7z2201.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\7z2201.exe | — | iexplore.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Installer Exit code: 3221226540 Version: 22.01 Modules
| |||||||||||||||
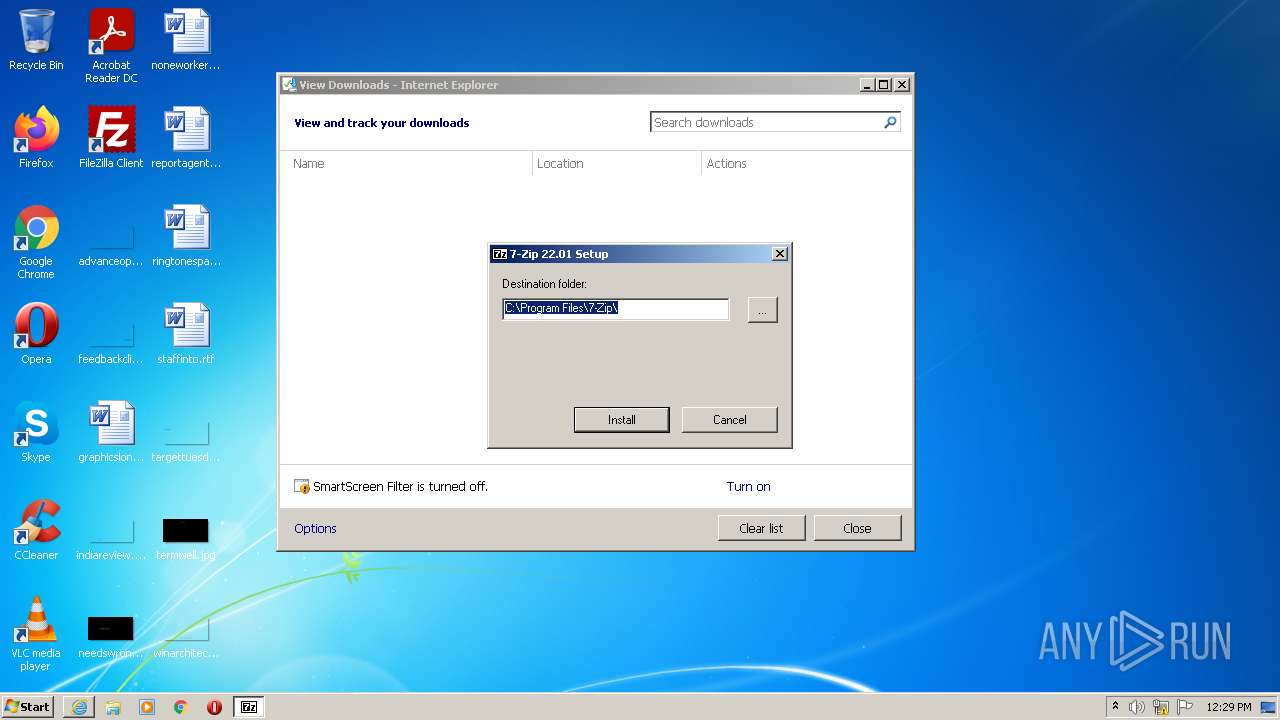
| 3180 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\7z2201.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\7z2201.exe | iexplore.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Installer Exit code: 0 Version: 22.01 Modules
| |||||||||||||||
Total events
18 581
Read events
18 473
Write events
107
Delete events
1
Modification events
| (PID) Process: | (1620) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1620) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1620) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30973374 | |||
| (PID) Process: | (1620) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1620) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30973374 | |||
| (PID) Process: | (1620) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1620) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1620) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1620) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1620) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
11
Suspicious files
13
Text files
98
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 912 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab95F8.tmp | compressed | |
MD5:— | SHA256:— | |||
| 912 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar95F9.tmp | cat | |
MD5:— | SHA256:— | |||
| 912 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 912 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 912 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar960B.tmp | cat | |
MD5:— | SHA256:— | |||
| 912 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 912 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6DDACEC779AEA0556D802C691D1E5E72 | der | |
MD5:— | SHA256:— | |||
| 912 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C9B5FA3AE0CBD04D11000E33964FCCF9 | der | |
MD5:— | SHA256:— | |||
| 912 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6DDACEC779AEA0556D802C691D1E5E72 | binary | |
MD5:— | SHA256:— | |||
| 912 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C9B5FA3AE0CBD04D11000E33964FCCF9 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
14
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
912 | iexplore.exe | GET | 200 | 2.16.2.75:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgOhcoaAv8eUa9ggqWrQxXmleg%3D%3D | unknown | der | 503 b | shared |
1620 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertGlobalRootCA.crl | US | der | 631 b | whitelisted |
912 | iexplore.exe | GET | 200 | 13.107.4.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4d408742b0a0eb98 | US | compressed | 4.70 Kb | whitelisted |
912 | iexplore.exe | GET | 200 | 96.16.145.230:80 | http://x1.c.lencr.org/ | US | der | 717 b | whitelisted |
912 | iexplore.exe | GET | 200 | 2.16.2.75:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgRGqY%2B0s0LJNEB2%2BVubTHMY%2Fw%3D%3D | unknown | der | 503 b | shared |
912 | iexplore.exe | GET | 200 | 13.107.4.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?c0f72bb8d2957e0c | US | compressed | 60.2 Kb | whitelisted |
912 | iexplore.exe | GET | 200 | 13.107.4.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fe9d7b17c2dae316 | US | compressed | 4.70 Kb | whitelisted |
912 | iexplore.exe | GET | 200 | 13.107.4.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?2f4b80df843e0acb | US | compressed | 60.2 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
912 | iexplore.exe | 159.65.89.65:443 | www.7-zip.org | — | US | suspicious |
912 | iexplore.exe | 13.107.4.50:80 | ctldl.windowsupdate.com | Microsoft Corporation | US | whitelisted |
912 | iexplore.exe | 96.16.145.230:80 | x1.c.lencr.org | Akamai Technologies, Inc. | US | suspicious |
1620 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
912 | iexplore.exe | 49.12.202.237:443 | d3.7-zip.org | — | IN | suspicious |
1620 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
912 | iexplore.exe | 2.16.2.75:80 | r3.o.lencr.org | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.7-zip.org |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
api.bing.com |
| whitelisted |
d3.7-zip.org |
| suspicious |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |