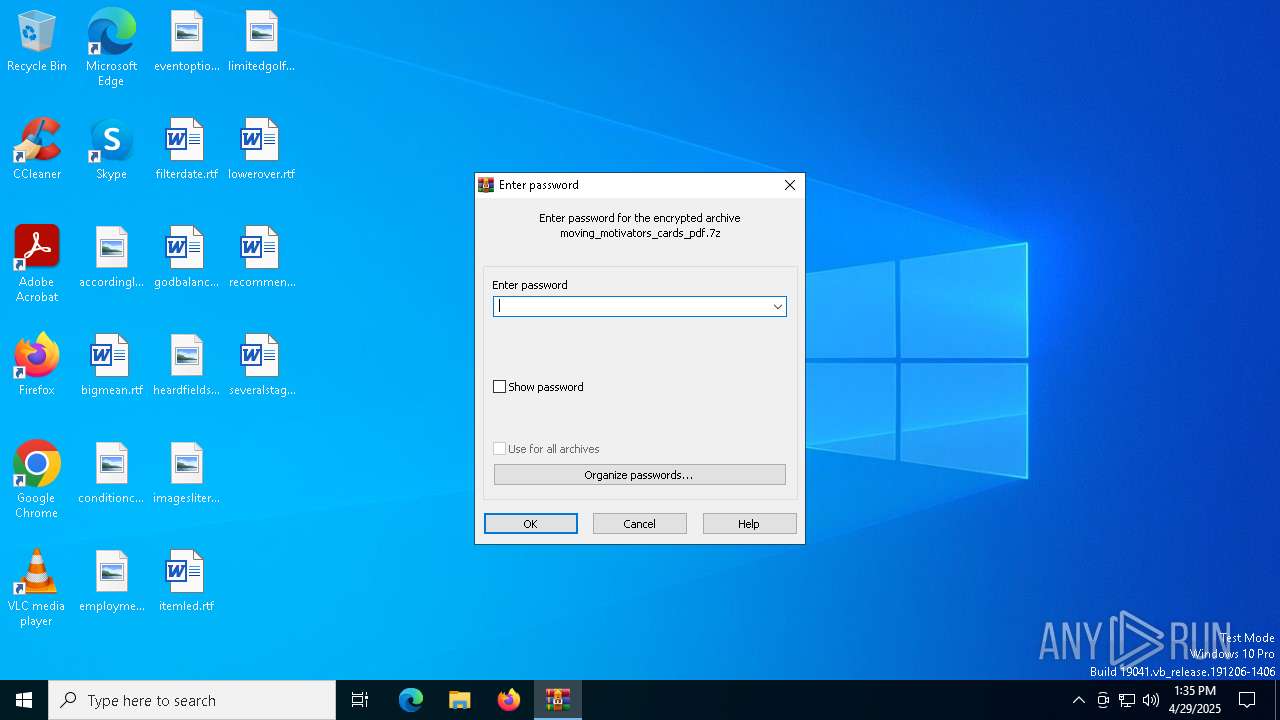
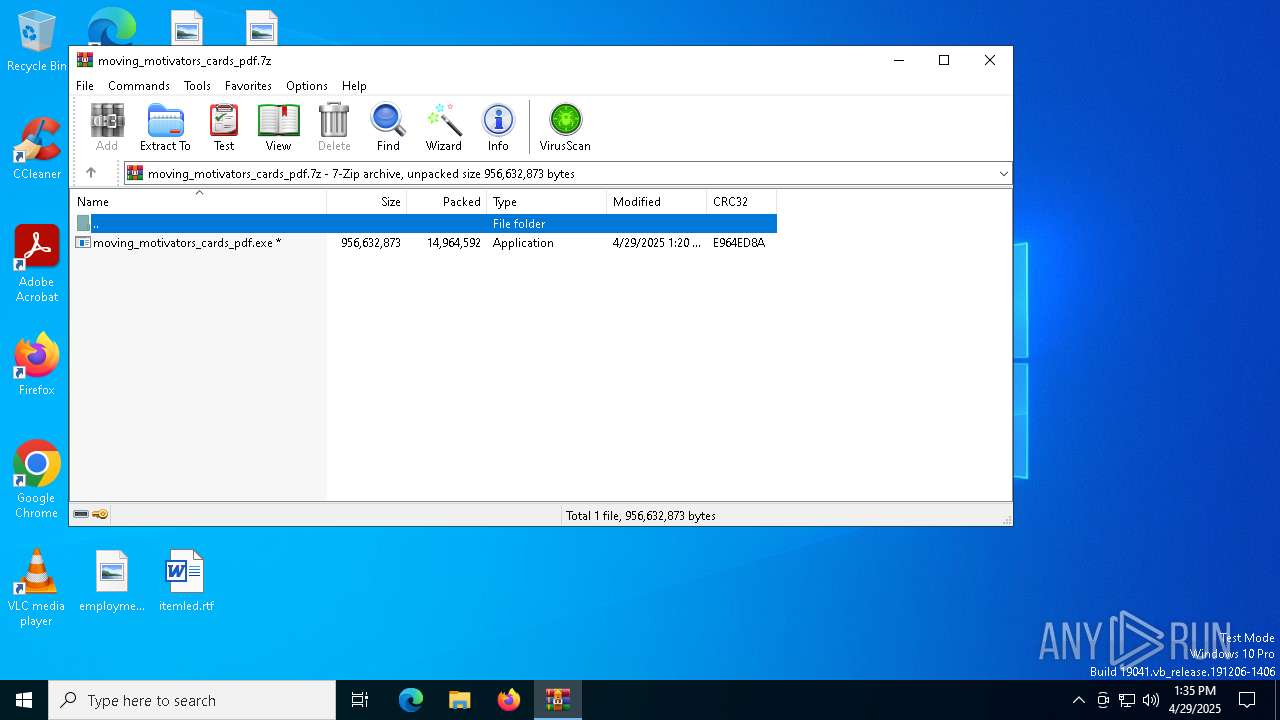
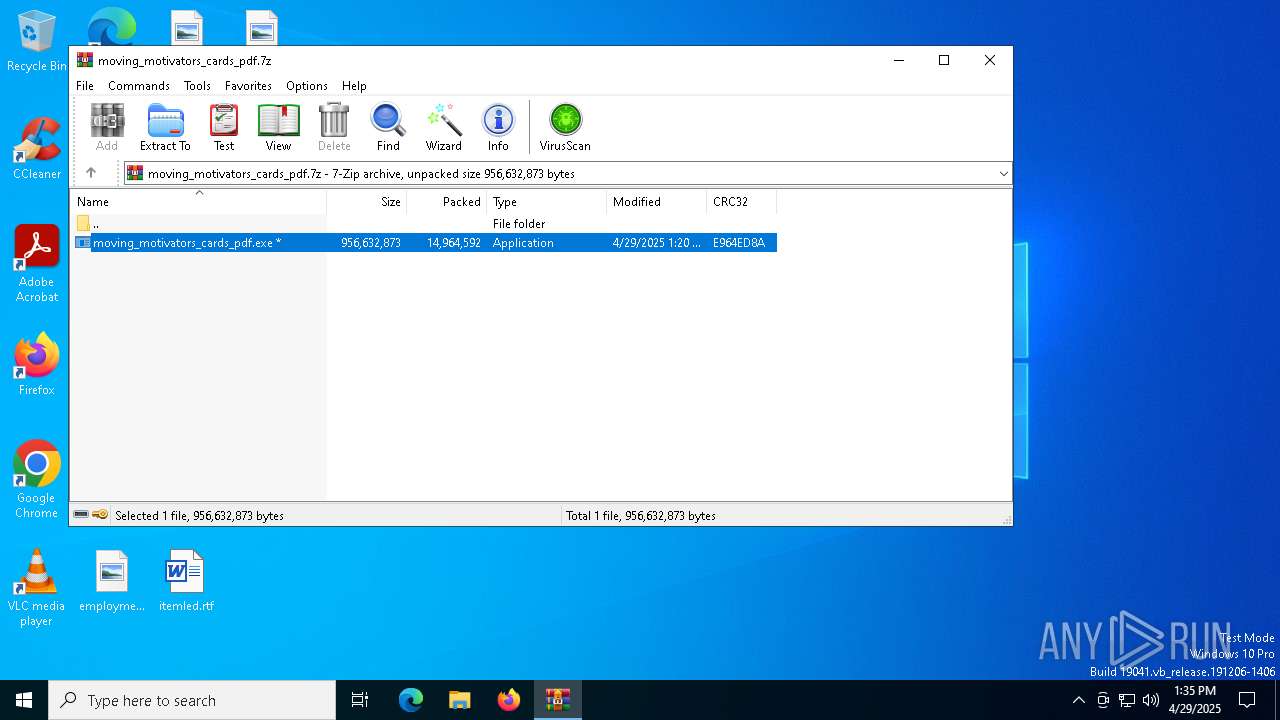
| File name: | moving_motivators_cards_pdf.7z |
| Full analysis: | https://app.any.run/tasks/79e252fb-efc3-4103-bec2-da5fb789c307 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 13:35:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 261D58563CA668433B630A26A1A818B8 |
| SHA1: | 17A7E59A384DD7C1DBB4DC784DFB75BDF0997EC9 |
| SHA256: | 093FB652F50DF707E7A26C65A09602C612C68680247B447CA0E53BFEA4FE201C |
| SSDEEP: | 98304:lPyev85rIT7v2MxFhdISIM698nqWX7t5iRYb7LVTlHQ3Eu3NVDhwVp0bk4Dg95WZ:vJRCx3EbfYLL2GHFGcc0MJts8CV |
MALICIOUS
AutoIt loader has been detected (YARA)
- Dispatched.com (PID: 8156)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5156)
- moving_motivators_cards_pdf.exe (PID: 7680)
Executing commands from a ".bat" file
- moving_motivators_cards_pdf.exe (PID: 7680)
Starts CMD.EXE for commands execution
- moving_motivators_cards_pdf.exe (PID: 7680)
- cmd.exe (PID: 7836)
Get information on the list of running processes
- cmd.exe (PID: 7836)
Application launched itself
- cmd.exe (PID: 7836)
Starts the AutoIt3 executable file
- cmd.exe (PID: 7836)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7836)
The executable file from the user directory is run by the CMD process
- Dispatched.com (PID: 8156)
Starts application with an unusual extension
- cmd.exe (PID: 7836)
There is functionality for taking screenshot (YARA)
- moving_motivators_cards_pdf.exe (PID: 7680)
- Dispatched.com (PID: 8156)
INFO
Reads the computer name
- moving_motivators_cards_pdf.exe (PID: 7680)
- extrac32.exe (PID: 8056)
- Dispatched.com (PID: 8156)
Checks supported languages
- moving_motivators_cards_pdf.exe (PID: 7680)
- extrac32.exe (PID: 8056)
- Dispatched.com (PID: 8156)
Create files in a temporary directory
- moving_motivators_cards_pdf.exe (PID: 7680)
- extrac32.exe (PID: 8056)
Process checks computer location settings
- moving_motivators_cards_pdf.exe (PID: 7680)
Creates a new folder
- cmd.exe (PID: 8036)
Reads mouse settings
- Dispatched.com (PID: 8156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
147
Monitored processes
17
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5156 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\moving_motivators_cards_pdf.7z | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7680 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb5156.5223\moving_motivators_cards_pdf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb5156.5223\moving_motivators_cards_pdf.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7836 | "C:\WINDOWS\System32\cmd.exe" /c copy Alabama.mid Alabama.mid.bat & Alabama.mid.bat | C:\Windows\SysWOW64\cmd.exe | — | moving_motivators_cards_pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7844 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7924 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7936 | findstr /I "opssvc wrsa" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7980 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7988 | findstr "SophosHealth bdservicehost AvastUI AVGUI nsWscSvc ekrn" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 357
Read events
3 348
Write events
9
Delete events
0
Modification events
| (PID) Process: | (5156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\moving_motivators_cards_pdf.7z | |||
| (PID) Process: | (5156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
17
Text files
4
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb5156.5223\moving_motivators_cards_pdf.exe | — | |
MD5:— | SHA256:— | |||
| 7680 | moving_motivators_cards_pdf.exe | C:\Users\admin\AppData\Local\Temp\Bundle.mid | binary | |
MD5:CB69A485D8461B5820BE6200E10702E9 | SHA256:153AB5578DD23BF88BF52CDFBB1089E10D112435C1435A7471A5F0C2409AA507 | |||
| 7680 | moving_motivators_cards_pdf.exe | C:\Users\admin\AppData\Local\Temp\Deal.mid | pgc | |
MD5:AE8A32725C76B5FC8B261753AA49A6C9 | SHA256:C9CFBEF9A56C3C1C2B9BD608C3C008C7824668139C056AD7AE68D8DC3992030E | |||
| 7680 | moving_motivators_cards_pdf.exe | C:\Users\admin\AppData\Local\Temp\Provisions.mid | binary | |
MD5:B948F050C4B8B61A2ADA8FB36BD2EE7A | SHA256:B2BBCFEC2A025981F68939C4182D61E7DFEA80B606C28C9A0F8C211BAA823AF2 | |||
| 7836 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Alabama.mid.bat | text | |
MD5:BCAD756C329332DFFA34013E2A01A5E2 | SHA256:4DF80D34577FED23339298E9333D6339E6AEACB9B9AD939EFB115E527DB4635C | |||
| 8056 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Buyer | binary | |
MD5:6FCB5A396BC4A6CD58FFAB00E7A040F8 | SHA256:D10F327A43266029199373BB68B2704FFEC9A458B90A43966364B52CC589AA15 | |||
| 8056 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Fountain | binary | |
MD5:881E6ECCE9781394F12FD48D921BE963 | SHA256:2CED9A4DCB1BB023C970D30520A69AB20CB614A994EFA7CA9E70662A52B9FBAD | |||
| 7680 | moving_motivators_cards_pdf.exe | C:\Users\admin\AppData\Local\Temp\Benjamin.mid | compressed | |
MD5:94DE3DF17BDA146B666ABC31E9762535 | SHA256:349CF34664651609B2BBE6DCB2DC72C96ED75ECD406CBC53128BC79ACDC7E49D | |||
| 7680 | moving_motivators_cards_pdf.exe | C:\Users\admin\AppData\Local\Temp\Continuity.mid | binary | |
MD5:579C4E50DC657B923E5D8D9E9915EC6E | SHA256:3BA924D88D106B7A6C228ED8F5BA0C1801E41097C6C0F2222F8BE342CB73F8CD | |||
| 8056 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Exit | binary | |
MD5:3D1FE3DDD8B93D95888B922EBA87B3D1 | SHA256:1E1E78DF54BA727414DDD1D053A91800E9F697DB9BCCD10AA859B86950C470E0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
30
DNS requests
21
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.41:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7708 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7708 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.41:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.159.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7708 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
lcpYrDuoqTjy.lcpYrDuoqTjy |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |