| File name: | 713-288-4192.doc |
| Full analysis: | https://app.any.run/tasks/642db971-2f6a-42b2-8fea-781396a09a12 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | March 20, 2019, 02:18:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: Admin, Template: Normal, Last Saved By: Admin, Revision Number: 2, Name of Creating Application: Microsoft Office Word, Total Editing Time: 02:00, Create Time/Date: Thu Jan 31 14:52:00 2019, Last Saved Time/Date: Tue Mar 19 19:47:00 2019, Number of Pages: 1, Number of Words: 4, Number of Characters: 23, Security: 0 |
| MD5: | 61F1A99292A199F867B168B76FC8CC74 |
| SHA1: | 967DA912065D014C275463917D236836967B27CA |
| SHA256: | 093D7065B58D12653ECD49A9C96DFA7A24B9C5224592F83EF4FA150EFCCC7A0B |
| SSDEEP: | 768:8L5oqYRuB2bu9CDFwWjkIP45860OLWqLaUctzS4xj5wnKHmWIl+1o9:c+qYRuBku9ABJP426VrLatNoKs+a9 |
MALICIOUS
Stops/Deletes Windows Defender service
- cmd.exe (PID: 2692)
- cmd.exe (PID: 2752)
- cmd.exe (PID: 3572)
- cmd.exe (PID: 564)
Application was dropped or rewritten from another process
- 36571.exe (PID: 2176)
- 36571.exe (PID: 3116)
Loads the Task Scheduler COM API
- 36571.exe (PID: 2176)
TRICKBOT was detected
- 36571.exe (PID: 2176)
- svchost.exe (PID: 1944)
Trickbot detected
- 36571.exe (PID: 2176)
Connects to CnC server
- 36571.exe (PID: 2176)
- svchost.exe (PID: 1944)
Uses SVCHOST.EXE for hidden code execution
- 36571.exe (PID: 2176)
Stealing of credential data
- svchost.exe (PID: 1944)
SQUIBLYDOO was detected
- cmstp.exe (PID: 3700)
SUSPICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 2824)
- cmd.exe (PID: 540)
Creates files in the user directory
- powershell.exe (PID: 2480)
- 36571.exe (PID: 2176)
- powershell.exe (PID: 3032)
- cmstp.exe (PID: 3700)
- cmd.exe (PID: 3188)
Connects to unusual port
- 36571.exe (PID: 2176)
- svchost.exe (PID: 1944)
Checks for external IP
- 36571.exe (PID: 2176)
Creates files in the program directory
- svchost.exe (PID: 3368)
Starts CMD.EXE for commands execution
- 36571.exe (PID: 3116)
- 36571.exe (PID: 2176)
Loads DLL from Mozilla Firefox
- svchost.exe (PID: 1944)
Executable content was dropped or overwritten
- cmstp.exe (PID: 3700)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2980)
- WINWORD.EXE (PID: 2536)
- WINWORD.EXE (PID: 2464)
Reads Internet Cache Settings
- iexplore.exe (PID: 4084)
- iexplore.exe (PID: 3760)
Creates files in the user directory
- WINWORD.EXE (PID: 2980)
- iexplore.exe (PID: 3760)
- WINWORD.EXE (PID: 2464)
- WINWORD.EXE (PID: 2536)
Reads internet explorer settings
- iexplore.exe (PID: 4084)
Changes internet zones settings
- iexplore.exe (PID: 3760)
Reads settings of System Certificates
- iexplore.exe (PID: 3760)
Changes settings of System certificates
- iexplore.exe (PID: 3760)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3760)
Application launched itself
- chrome.exe (PID: 2816)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | Admin |
| Keywords: | - |
| Comments: | - |
| Template: | Normal |
| LastModifiedBy: | Admin |
| RevisionNumber: | 2 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 2.0 minutes |
| CreateDate: | 2019:02:28 14:52:00 |
| ModifyDate: | 2019:03:19 19:47:00 |
| Pages: | 1 |
| Words: | 4 |
| Characters: | 23 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 26 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
77
Monitored processes
31
Malicious processes
5
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | /c powershell Set-MpPreference -DisableRealtimeMonitoring $true | C:\Windows\system32\cmd.exe | — | 36571.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 564 | /c sc stop WinDefend | C:\Windows\system32\cmd.exe | — | 36571.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 5 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1944 | svchost.exe | C:\Windows\system32\svchost.exe | 36571.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2056 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=884,7061862929669169408,8032342426195553922,131072 --enable-features=PasswordImport --service-pipe-token=7DA2ED20FB863A7A8BC731043C88A708 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7DA2ED20FB863A7A8BC731043C88A708 --renderer-client-id=5 --mojo-platform-channel-handle=1896 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2176 | "C:\Users\admin\AppData\Roaming\Microsoft\36571.exe" | C:\Users\admin\AppData\Roaming\Microsoft\36571.exe | cmstp.exe | ||||||||||||
User: admin Company: Runtime Library Integrity Level: MEDIUM Description: Runtime Library Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2292 | sc stop WinDefend | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2452 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\virtualclients.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2480 | powershell Set-MpPreference -DisableRealtimeMonitoring $true | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2536 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\downloadsbit.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
3 868
Read events
3 403
Write events
417
Delete events
48
Modification events
| (PID) Process: | (2980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 1+, |
Value: 312B2C00A40B0000010000000000000000000000 | |||
| (PID) Process: | (2980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2980) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1316225047 | |||
| (PID) Process: | (2980) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1316225168 | |||
| (PID) Process: | (2980) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1316225169 | |||
| (PID) Process: | (2980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: A40B0000B0A7B14BC3DED40100000000 | |||
| (PID) Process: | (2980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | +,, |
Value: 2B2C2C00A40B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | +,, |
Value: 2B2C2C00A40B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
1
Suspicious files
61
Text files
205
Unknown types
50
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE311.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF9CC6C95B37D012A6.TMP | — | |
MD5:— | SHA256:— | |||
| 2980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{822D647E-E416-4006-992F-C560E9589ABF}.tmp | — | |
MD5:— | SHA256:— | |||
| 2980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{9CF5976A-0CF7-4F52-A8F6-3C048ACF0366}.tmp | — | |
MD5:— | SHA256:— | |||
| 2480 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\F405CDDIVVI9OHTF3CUA.temp | — | |
MD5:— | SHA256:— | |||
| 3760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3760 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 4084 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab94AE.tmp | — | |
MD5:— | SHA256:— | |||
| 4084 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar94AF.tmp | — | |
MD5:— | SHA256:— | |||
| 4084 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab94DE.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
47
DNS requests
19
Threats
26
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
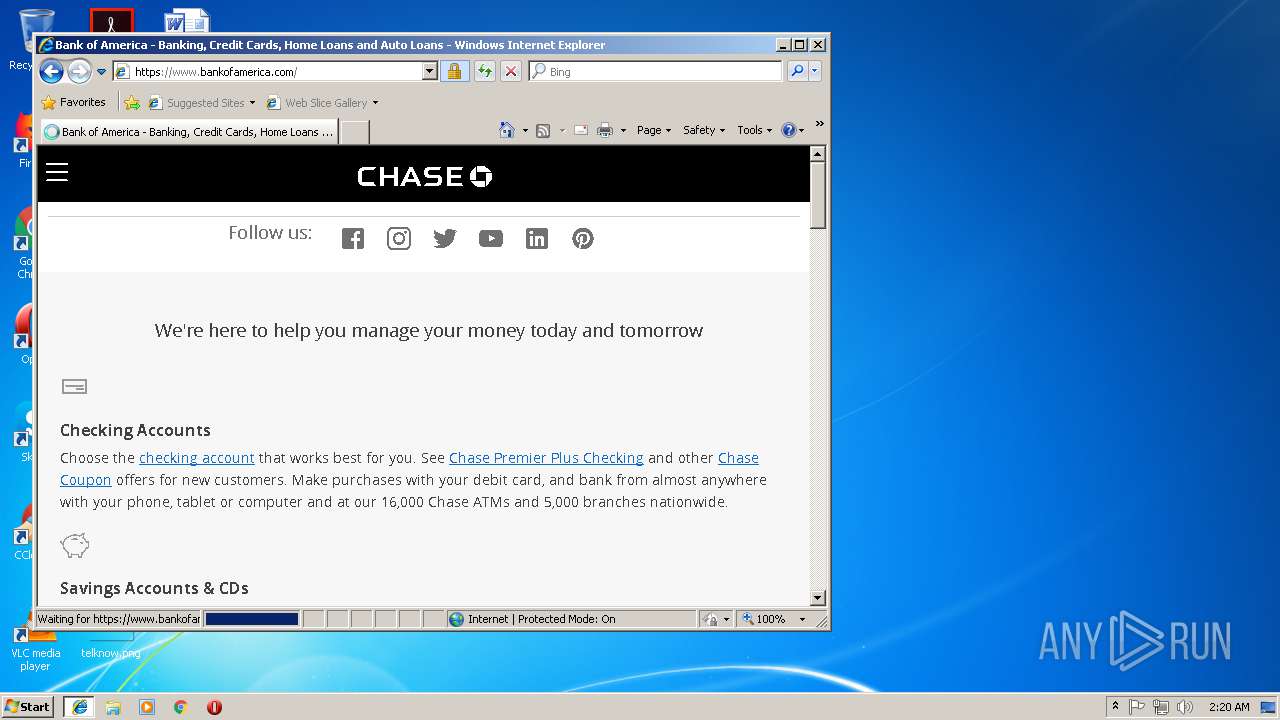
4084 | iexplore.exe | GET | 301 | 159.53.42.11:80 | http://chase.com/ | US | — | — | suspicious |
4084 | iexplore.exe | GET | 301 | 171.159.228.150:80 | http://bankofamerica.com/ | US | — | — | whitelisted |
3700 | cmstp.exe | GET | 200 | 104.20.208.21:80 | http://pastebin.com/raw/nQ4yJ47k | US | xml | 367 Kb | malicious |
2176 | 36571.exe | GET | 200 | 198.27.74.146:80 | http://wtfismyip.com/text | CA | text | 12 b | shared |
4084 | iexplore.exe | GET | 200 | 205.185.216.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.2 Kb | whitelisted |
3760 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
1944 | svchost.exe | POST | 200 | 103.119.144.250:8082 | http://103.119.144.250:8082/ser0319us/USER-PC_W617601.0D53D7D75B122B7976793726A57F35A1/81/ | unknown | text | 3 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3700 | cmstp.exe | 104.20.208.21:80 | pastebin.com | Cloudflare Inc | US | shared |
2176 | 36571.exe | 198.27.74.146:80 | wtfismyip.com | OVH SAS | CA | suspicious |
3760 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2176 | 36571.exe | 45.160.145.179:449 | — | — | — | malicious |
4084 | iexplore.exe | 159.53.42.11:80 | chase.com | JPMorgan Chase & Co. | US | suspicious |
4084 | iexplore.exe | 159.53.85.137:443 | chase.com | JPMorgan Chase & Co. | US | suspicious |
4084 | iexplore.exe | 159.53.43.185:443 | sites.chase.com | JPMorgan Chase & Co. | US | unknown |
4084 | iexplore.exe | 205.185.216.10:80 | www.download.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
4084 | iexplore.exe | 171.161.198.100:443 | www.bankofamerica.com | Bank of America | US | unknown |
3760 | iexplore.exe | 192.229.233.230:443 | www1.bac-assets.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
www.bing.com |
| whitelisted |
wtfismyip.com |
| shared |
chase.com |
| suspicious |
www.chase.com |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
sites.chase.com |
| unknown |
hvn7wsa62jjhkuyk.onion |
| unknown |
bankofamerica.com |
| whitelisted |
www.bankofamerica.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3700 | cmstp.exe | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |
3700 | cmstp.exe | A Network Trojan was detected | MALWARE [PTsecurity] Squiblydoo Scriptlet |
3700 | cmstp.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
2176 | 36571.exe | Potential Corporate Privacy Violation | ET POLICY IP Check wtfismyip.com |
2176 | 36571.exe | A Network Trojan was detected | MALWARE [PTsecurity] Blacklist Malicious SSL certificate detected (Trickbot) |
2176 | 36571.exe | A Network Trojan was detected | MALWARE [PTsecurity] Blacklist Malicious SSL certificate detected (Trickbot) |
2176 | 36571.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
2176 | 36571.exe | A Network Trojan was detected | MALWARE [PTsecurity] Dyre/Trickbot/Dridex SSL connection |
1052 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
2176 | 36571.exe | A Network Trojan was detected | MALWARE [PTsecurity] Blacklist Malicious SSL certificate detected (Trickbot) |
5 ETPRO signatures available at the full report