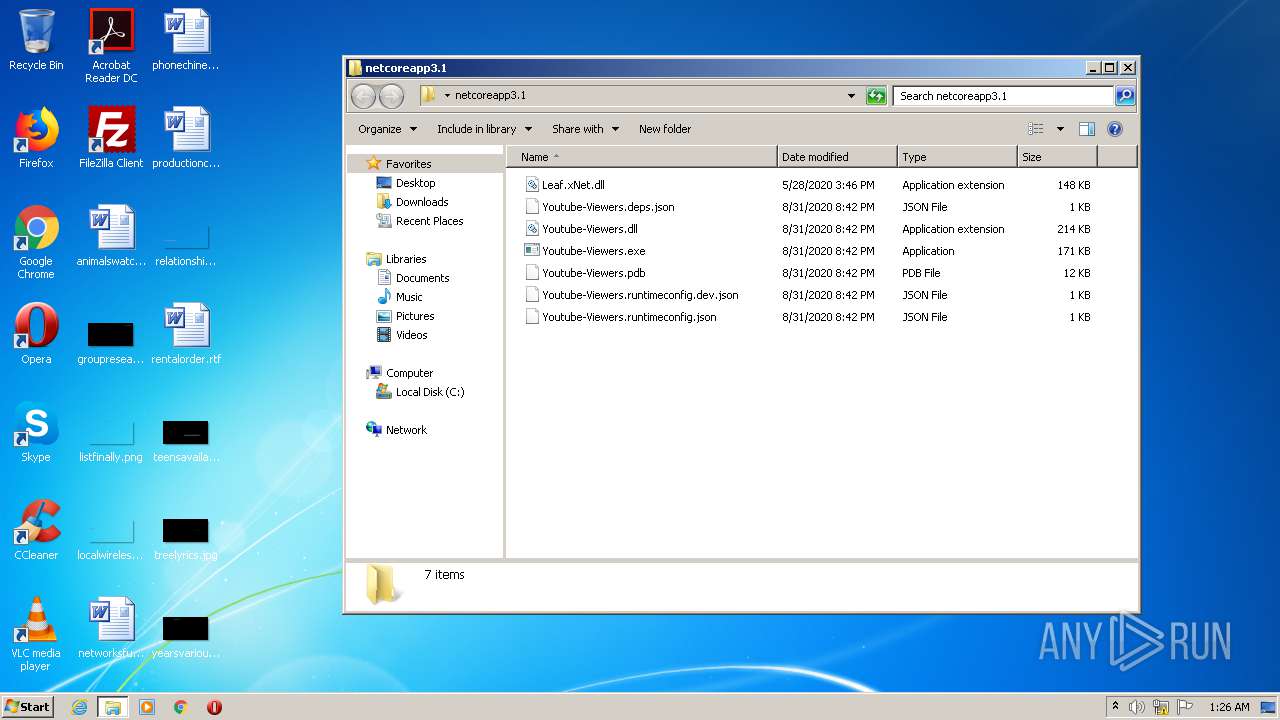
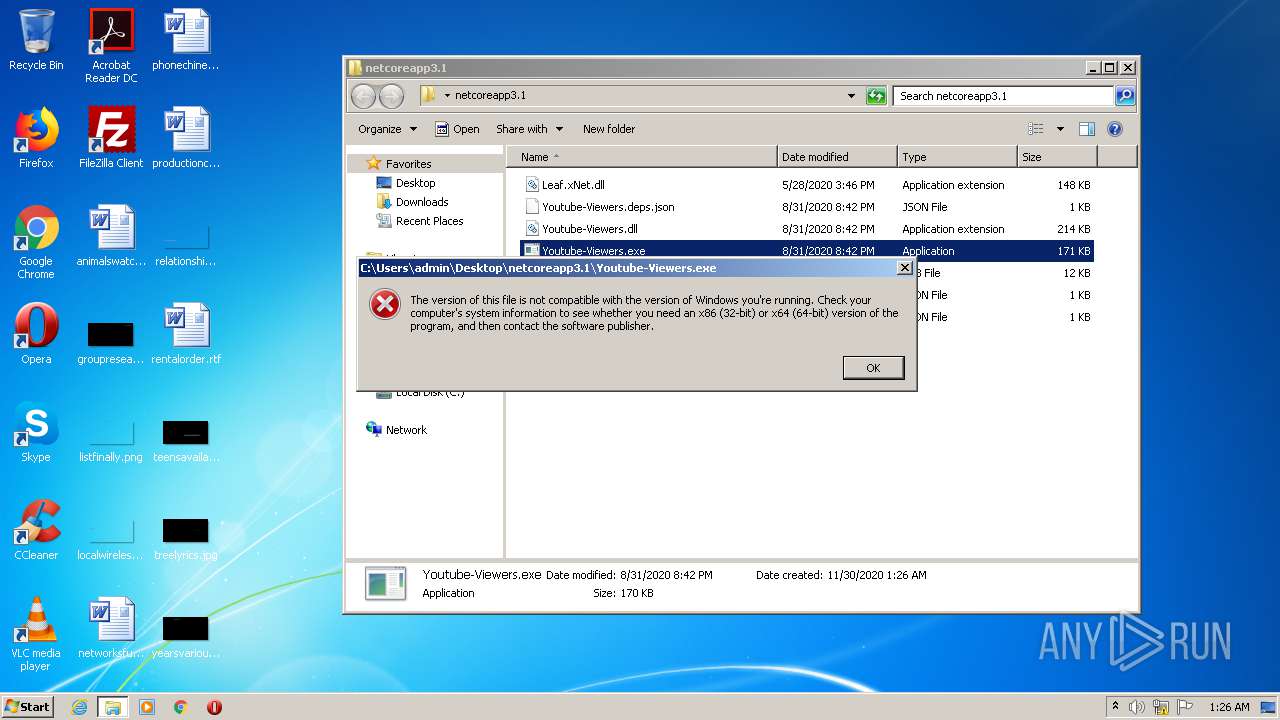
| File name: | netcoreapp3.1.7z |
| Full analysis: | https://app.any.run/tasks/66803406-23f5-4cb0-b75b-70d2c5a31afb |
| Verdict: | Malicious activity |
| Analysis date: | November 30, 2020, 01:25:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | C5CCD223B3CA304185E9656925AEA63E |
| SHA1: | 8B1F593F10EC2DC6B88450E75D6FCAE69343B7D1 |
| SHA256: | 0935EDFDB28894D24BDE2D06F0FED586C37A9238352C3EB59A90F5DAC1374BC9 |
| SSDEEP: | 3072:JRhvkQYaln/W1JLl9xnGaQ4x3grbD5e9cmX+XByCToBTJMVGBSR:JfFQX9RGIxqX5eCmXWBTTD4W |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3448)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2784)
Drops a file with too old compile date
- WinRAR.exe (PID: 2784)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2784)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
35
Monitored processes
2
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2784 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\netcoreapp3.1.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3448 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
782
Read events
763
Write events
19
Delete events
0
Modification events
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\netcoreapp3.1.7z | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
3
Suspicious files
1
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2784 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2784.39165\netcoreapp3.1\Youtube-Viewers.pdb | binary | |
MD5:— | SHA256:— | |||
| 2784 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2784.39165\netcoreapp3.1\Youtube-Viewers.runtimeconfig.dev.json | text | |
MD5:— | SHA256:— | |||
| 2784 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2784.39165\netcoreapp3.1\Youtube-Viewers.deps.json | text | |
MD5:— | SHA256:— | |||
| 2784 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2784.39165\netcoreapp3.1\Youtube-Viewers.exe | executable | |
MD5:— | SHA256:— | |||
| 2784 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2784.39165\netcoreapp3.1\Youtube-Viewers.dll | executable | |
MD5:— | SHA256:— | |||
| 2784 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2784.39165\netcoreapp3.1\Leaf.xNet.dll | executable | |
MD5:6F4784273E0E378ECF86ACC62A5E8005 | SHA256:2A5E234423CF8A275E0DC6127C94F53F0E3C6916704FCFF40D0ADA105AB13E8E | |||
| 2784 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2784.39165\netcoreapp3.1\Youtube-Viewers.runtimeconfig.json | text | |
MD5:42F40B6C1B9AB7F8F92B0AE5D8C5FDAB | SHA256:ED69FDC80437B2D0FD2B177D018A6E800517200E4FB6DD54705F5A62A908EC38 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report