| File name: | rufus-4.8.exe |
| Full analysis: | https://app.any.run/tasks/15fbadf4-5b7b-43fe-a212-248ef3197e8c |
| Verdict: | Malicious activity |
| Analysis date: | June 15, 2025, 06:35:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 3 sections |
| MD5: | 96E7D9ACFF29770E15C8C2FA0BC92C5A |
| SHA1: | 51AFED81E9BD03F2DAEF4993DF94308615598B1E |
| SHA256: | 092B1C10C0240E4AE16F30989C3F06A8E784067A944E4AA3E8A11A75F803D71B |
| SSDEEP: | 98304:xGk1sDbzAkDIm/FJw0CX7G0yxyRAGkuRfj/Oc0r01rFiyWy4pu1o33yltYTBdSgD:Urtb/219C |
MALICIOUS
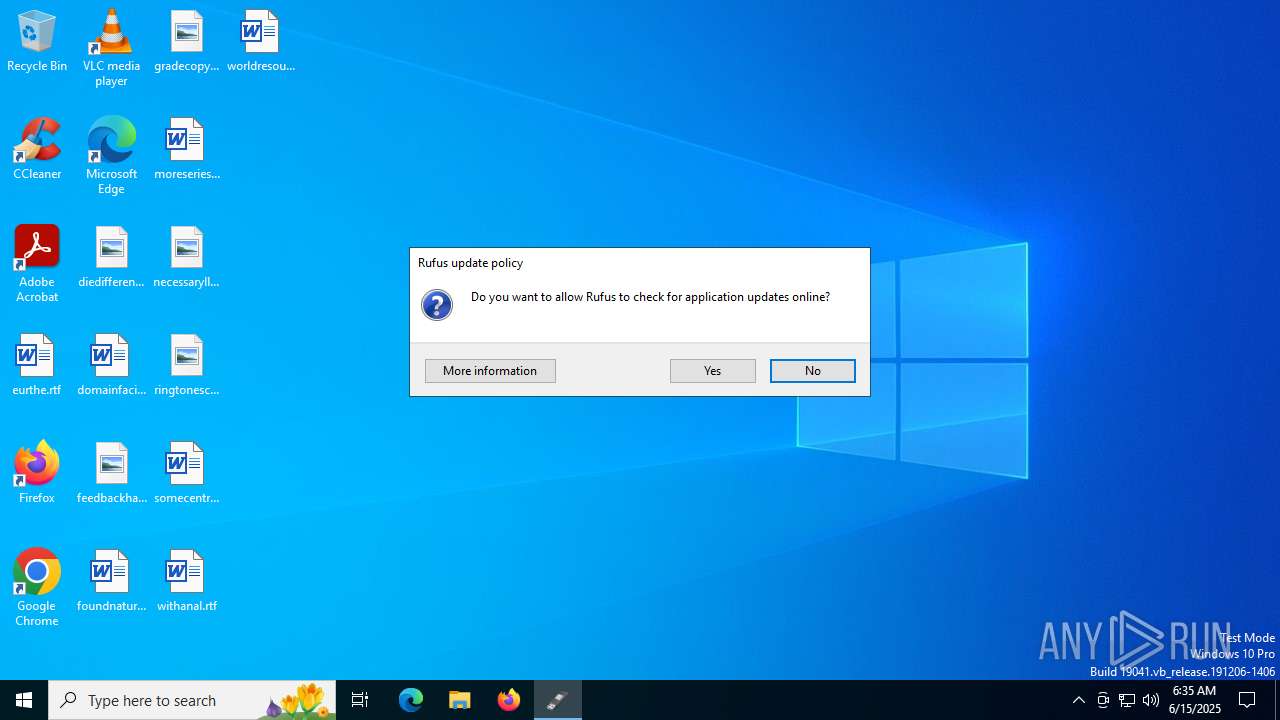
Changes the Windows auto-update feature
- rufus-4.8.exe (PID: 3388)
SUSPICIOUS
Executes as Windows Service
- vds.exe (PID: 984)
Reads security settings of Internet Explorer
- rufus-4.8.exe (PID: 3388)
Creates file in the systems drive root
- rufus-4.8.exe (PID: 3388)
The process executes via Task Scheduler
- default-browser-agent.exe (PID: 2764)
Loads DLL from Mozilla Firefox
- default-browser-agent.exe (PID: 2764)
INFO
Create files in a temporary directory
- rufus-4.8.exe (PID: 3388)
Checks supported languages
- rufus-4.8.exe (PID: 3388)
- default-browser-agent.exe (PID: 2764)
Reads the computer name
- rufus-4.8.exe (PID: 3388)
Reads the machine GUID from the registry
- rufus-4.8.exe (PID: 3388)
Process checks whether UAC notifications are on
- rufus-4.8.exe (PID: 3388)
UPX packer has been detected
- rufus-4.8.exe (PID: 3388)
Application launched itself
- firefox.exe (PID: 6160)
Checks proxy server information
- rufus-4.8.exe (PID: 3388)
- slui.exe (PID: 4580)
Creates files or folders in the user directory
- rufus-4.8.exe (PID: 3388)
Reads the software policy settings
- rufus-4.8.exe (PID: 3388)
- slui.exe (PID: 4580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (87.1) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.4) |
| .exe | | | DOS Executable Generic (6.4) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2073:05:01 17:13:54+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 2048000 |
| InitializedDataSize: | 45056 |
| UninitializedDataSize: | 4251648 |
| EntryPoint: | 0x602170 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.8.2253.0 |
| ProductVersionNumber: | 4.8.2253.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | https://rufus.ie |
| CompanyName: | Akeo Consulting |
| FileDescription: | Rufus |
| FileVersion: | 4.8.2253 |
| InternalName: | Rufus |
| LegalCopyright: | © 2011-2025 Pete Batard (GPL v3) |
| LegalTrademarks: | https://www.gnu.org/licenses/gpl-3.0.html |
| OriginalFileName: | rufus-4.8.exe |
| ProductName: | Rufus |
| ProductVersion: | 4.8.2253 |
Total processes
156
Monitored processes
8
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | C:\WINDOWS\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2044 | "C:\Users\admin\AppData\Local\Temp\rufus-4.8.exe" | C:\Users\admin\AppData\Local\Temp\rufus-4.8.exe | — | explorer.exe | |||||||||||
User: admin Company: Akeo Consulting Integrity Level: MEDIUM Description: Rufus Exit code: 3221226540 Version: 4.8.2253 Modules
| |||||||||||||||
| 2764 | "C:\Program Files\Mozilla Firefox\default-browser-agent.exe" do-task "308046B0AF4A39CB" | C:\Program Files\Mozilla Firefox\default-browser-agent.exe | — | svchost.exe | |||||||||||
User: admin Company: Mozilla Foundation Integrity Level: MEDIUM Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 2864 | "C:\Program Files\Mozilla Firefox\firefox.exe" --backgroundtask defaultagent do-task 308046B0AF4A39CB | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 3388 | "C:\Users\admin\AppData\Local\Temp\rufus-4.8.exe" | C:\Users\admin\AppData\Local\Temp\rufus-4.8.exe | explorer.exe | ||||||||||||
User: admin Company: Akeo Consulting Integrity Level: HIGH Description: Rufus Exit code: 0 Version: 4.8.2253 Modules
| |||||||||||||||
| 4580 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5496 | C:\WINDOWS\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6160 | "C:\Program Files\Mozilla Firefox\firefox.exe" --backgroundtask defaultagent do-task 308046B0AF4A39CB | C:\Program Files\Mozilla Firefox\firefox.exe | — | default-browser-agent.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
Total events
10 050
Read events
9 559
Write events
407
Delete events
84
Modification events
| (PID) Process: | (3388) rufus-4.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{497D50B5-6B03-4772-9F4E-D0AB6C2E0052}Machine\Software\Policies\Microsoft\AppHVSI |
| Operation: | write | Name: | AllowAppHVSI_ProviderSet |
Value: 0 | |||
| (PID) Process: | (3388) rufus-4.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{497D50B5-6B03-4772-9F4E-D0AB6C2E0052}Machine\Software\Policies\Microsoft\EdgeUpdate |
| Operation: | write | Name: | UpdateDefault |
Value: 0 | |||
| (PID) Process: | (3388) rufus-4.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{497D50B5-6B03-4772-9F4E-D0AB6C2E0052}Machine\Software\Policies\Microsoft\Windows\Network Connections |
| Operation: | write | Name: | NC_DoNotShowLocalOnlyIcon |
Value: 1 | |||
| (PID) Process: | (3388) rufus-4.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{497D50B5-6B03-4772-9F4E-D0AB6C2E0052}Machine\Software\Policies\Microsoft\Windows\Windows Feeds |
| Operation: | write | Name: | EnableFeeds |
Value: 0 | |||
| (PID) Process: | (3388) rufus-4.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{497D50B5-6B03-4772-9F4E-D0AB6C2E0052}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | WUServer |
Value: http://neverupdatewindows10.com | |||
| (PID) Process: | (3388) rufus-4.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{497D50B5-6B03-4772-9F4E-D0AB6C2E0052}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | WUStatusServer |
Value: http://neverupdatewindows10.com | |||
| (PID) Process: | (3388) rufus-4.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{497D50B5-6B03-4772-9F4E-D0AB6C2E0052}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | UpdateServiceUrlAlternate |
Value: http://neverupdatewindows10.com | |||
| (PID) Process: | (3388) rufus-4.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{497D50B5-6B03-4772-9F4E-D0AB6C2E0052}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | **del.FillEmptyContentUrls |
Value: | |||
| (PID) Process: | (3388) rufus-4.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{497D50B5-6B03-4772-9F4E-D0AB6C2E0052}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate\AU |
| Operation: | write | Name: | UseWUServer |
Value: 1 | |||
| (PID) Process: | (3388) rufus-4.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{497D50B5-6B03-4772-9F4E-D0AB6C2E0052}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate\AU |
| Operation: | write | Name: | NoAutoUpdate |
Value: 0 | |||
Executable files
3
Suspicious files
83
Text files
6
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Background Tasks Profiles\93u99co2.MozillaBackgroundTask-308046B0AF4A39CB-defaultagent\prefs.js | text | |
MD5:262A4081DD1F2DC19768C1DD5D0C082B | SHA256:AAD0AA4E748CF5FC5CB7B6B69D5A0E6E3F5BF69447469DDD6759292DC6D3A5C3 | |||
| 2864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Background Tasks Profiles\93u99co2.MozillaBackgroundTask-308046B0AF4A39CB-defaultagent\datareporting\glean\db\data.safe.bin | binary | |
MD5:0CC8D264FD1DB732E59AD15F897EB626 | SHA256:1F7E3AA6AC66450BD467F889806CC634683E5CB032E8440B8C56484FB4E7464C | |||
| 3388 | rufus-4.8.exe | C:\Users\admin\AppData\Local\Temp\Ruf5F56.tmp | text | |
MD5:E4AAF25313710D508B4AF46118E4B7D3 | SHA256:DB1D2C7C742887940C2E309164848118CFD56B45DC42DD173B25CE960F72E238 | |||
| 3388 | rufus-4.8.exe | C:\Windows\System32\GroupPolicy\gpt.ini | text | |
MD5:3D89F23265C9E30A0CF055C3EB4D637C | SHA256:806582F6221C79BD4C7EACDC4B63E937CE247EEE2BA159F55C545CDFB2B1C25B | |||
| 2864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Background Tasks Profiles\93u99co2.MozillaBackgroundTask-308046B0AF4A39CB-defaultagent\prefs-1.js | text | |
MD5:262A4081DD1F2DC19768C1DD5D0C082B | SHA256:AAD0AA4E748CF5FC5CB7B6B69D5A0E6E3F5BF69447469DDD6759292DC6D3A5C3 | |||
| 3388 | rufus-4.8.exe | C:\Windows\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:0C014C71A70DC7758BFDC822E974F1F3 | SHA256:8EBD915268E16B55A3ABDE6F612363576FAB5DF656F955D672CCE8889C5FF9CA | |||
| 2864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Background Tasks Profiles\93u99co2.MozillaBackgroundTask-308046B0AF4A39CB-defaultagent\datareporting\glean\db\data.safe.tmp | binary | |
MD5:0CC8D264FD1DB732E59AD15F897EB626 | SHA256:1F7E3AA6AC66450BD467F889806CC634683E5CB032E8440B8C56484FB4E7464C | |||
| 3388 | rufus-4.8.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:33C579E0DBBE7AA9BBE30465BD8317AF | SHA256:94BF467F3EA06555B042E7DD4788C541E6CBA862678D39DC10D58503FBB5A0ED | |||
| 3388 | rufus-4.8.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:CD8625A41E4531AE2A6D522EF32B2CF5 | SHA256:184DA636EA44975381859611AFCAA089B9C2DD0C8AB009FED9CD693E7477B8F6 | |||
| 3388 | rufus-4.8.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:8E0C480677EE4FC329CE07D2DA10503B | SHA256:2E2F03EF85A380C029528E732346D1C6C6B603266C109C1F19508C99CEB288F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
32
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6700 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6700 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6900 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3388 | rufus-4.8.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
3388 | rufus-4.8.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CECoW9cIBGAf3CpJj3Tw5qfI%3D | unknown | — | — | whitelisted |
3388 | rufus-4.8.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6876 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2200 | svchost.exe | 224.0.0.251:5353 | — | — | — | unknown |
2200 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
rufus-4.8.exe | *** Rufus init ***
|
rufus-4.8.exe | Usr dir: 'C:\Users\admin'
|
rufus-4.8.exe | Dat dir: 'C:\Users\admin\AppData\Local'
|
rufus-4.8.exe | App dir: 'C:\Users\admin\AppData\Local\Temp\'
|
rufus-4.8.exe | Tmp dir: 'C:\Users\admin\AppData\Local\Temp\'
|
rufus-4.8.exe | Sys dir: 'C:\WINDOWS\system32'
|
rufus-4.8.exe | Cur dir: 'C:\Users\admin\AppData\Local\Temp\'
|
rufus-4.8.exe | Binary executable is signed by 'Akeo Consulting'
|
rufus-4.8.exe | Will use settings from registry
|
rufus-4.8.exe | localization: extracted data to 'C:\Users\admin\AppData\Local\Temp\Ruf5F56.tmp'
|