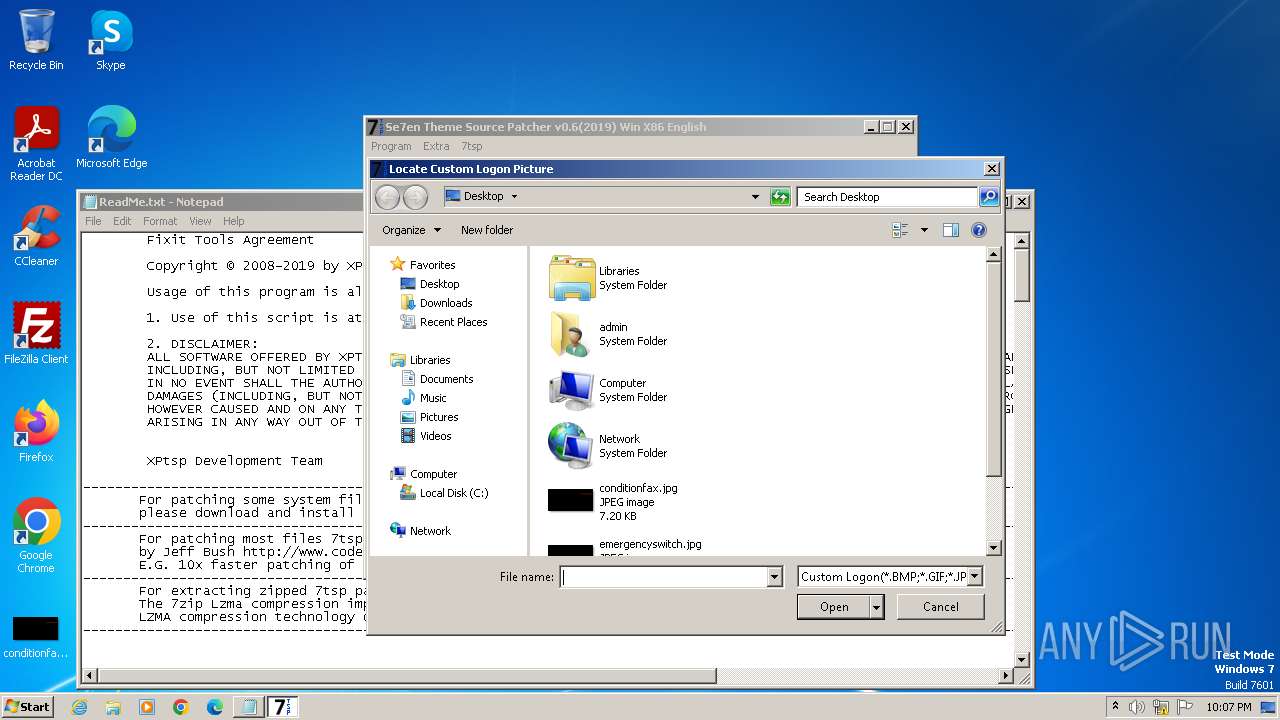
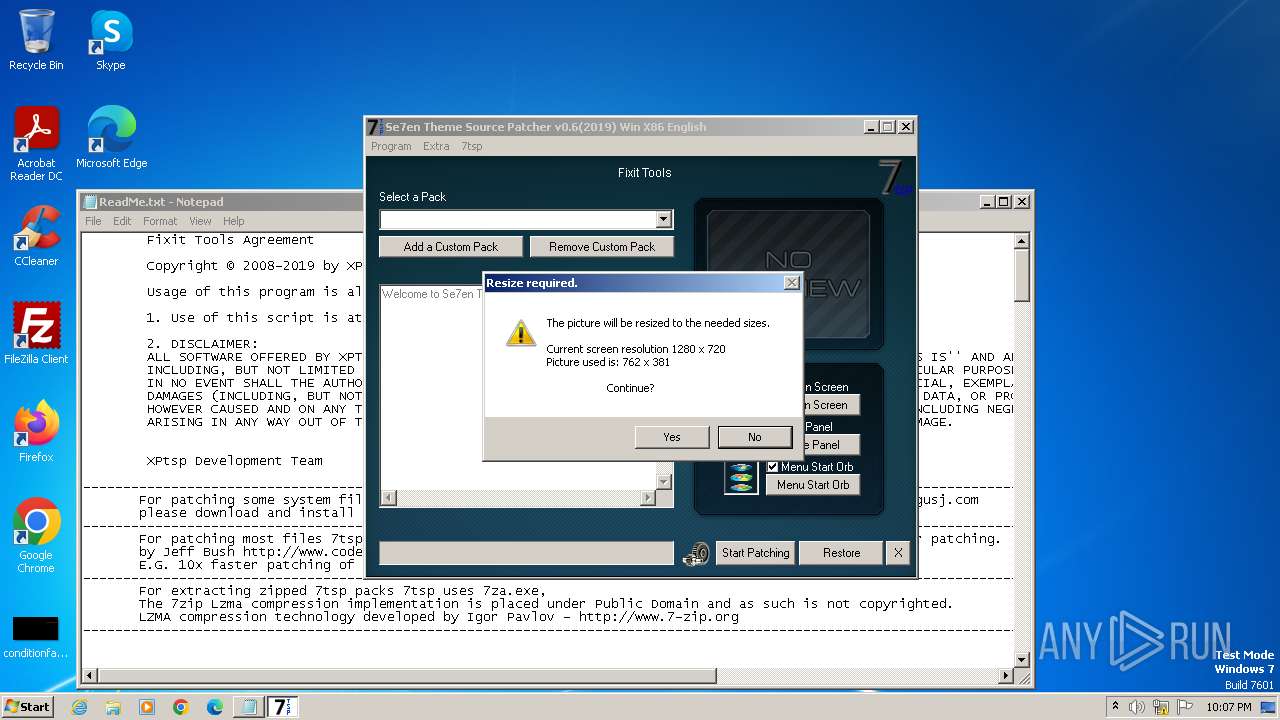
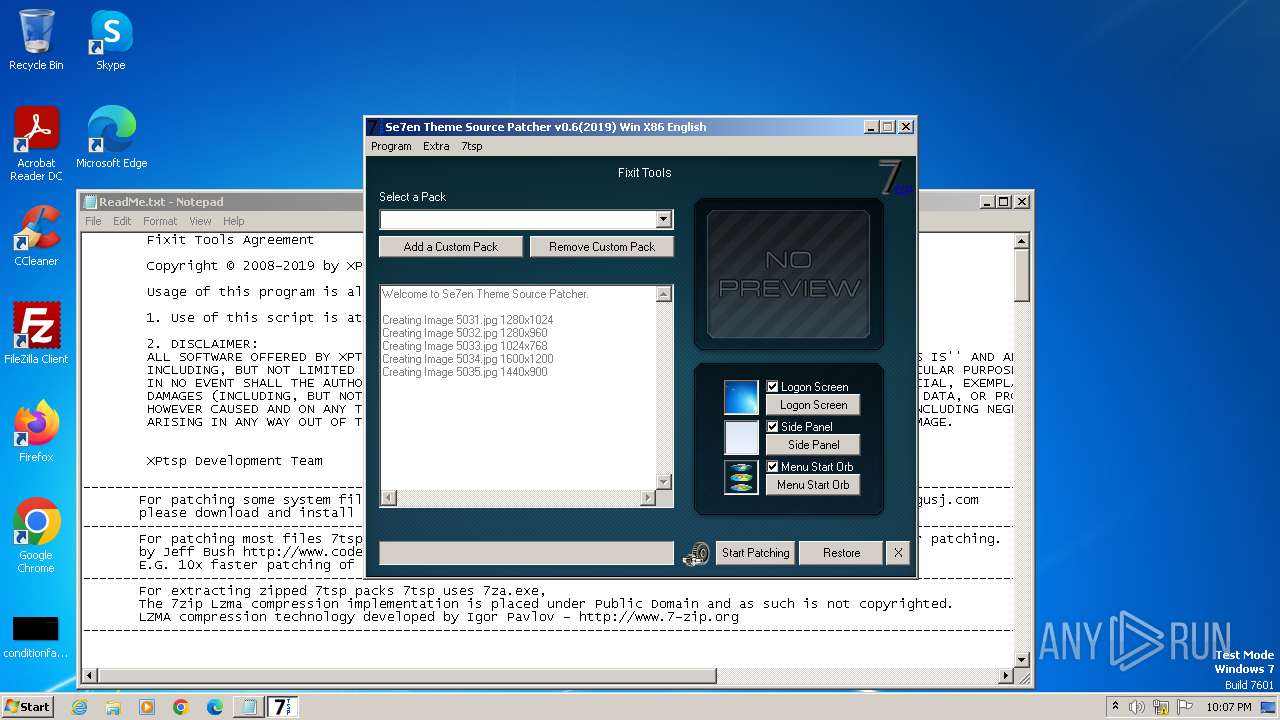
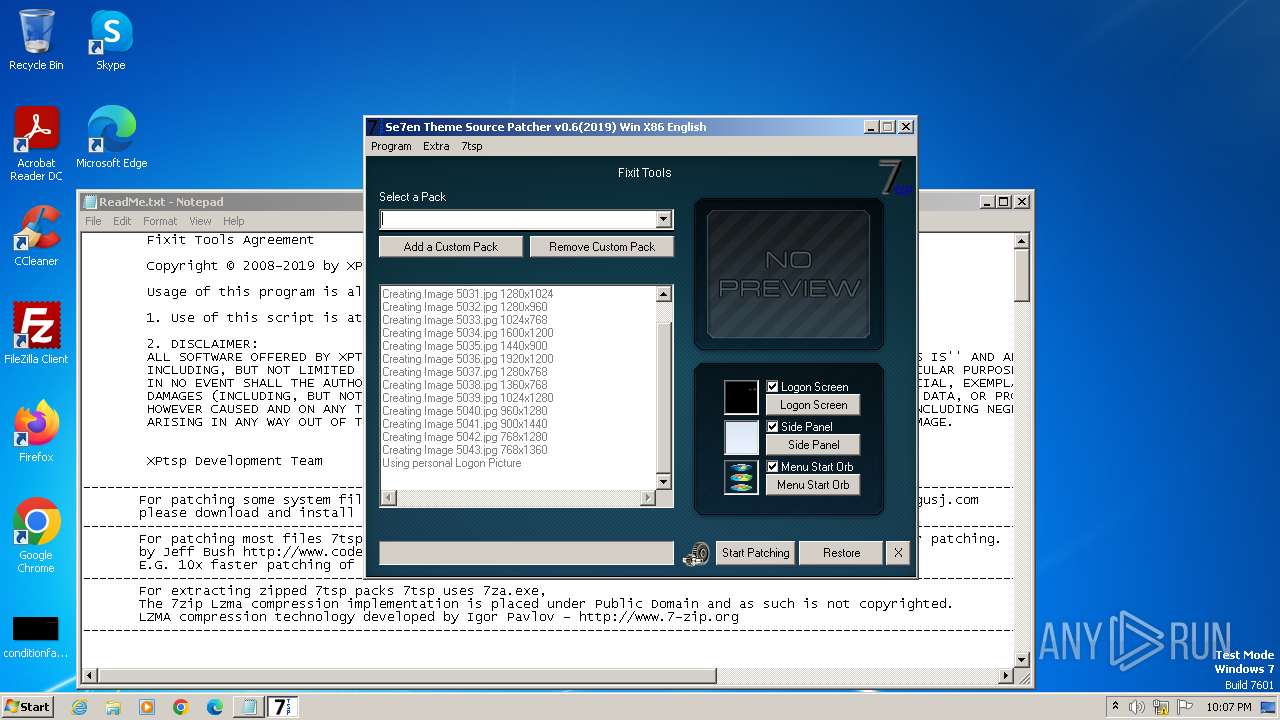
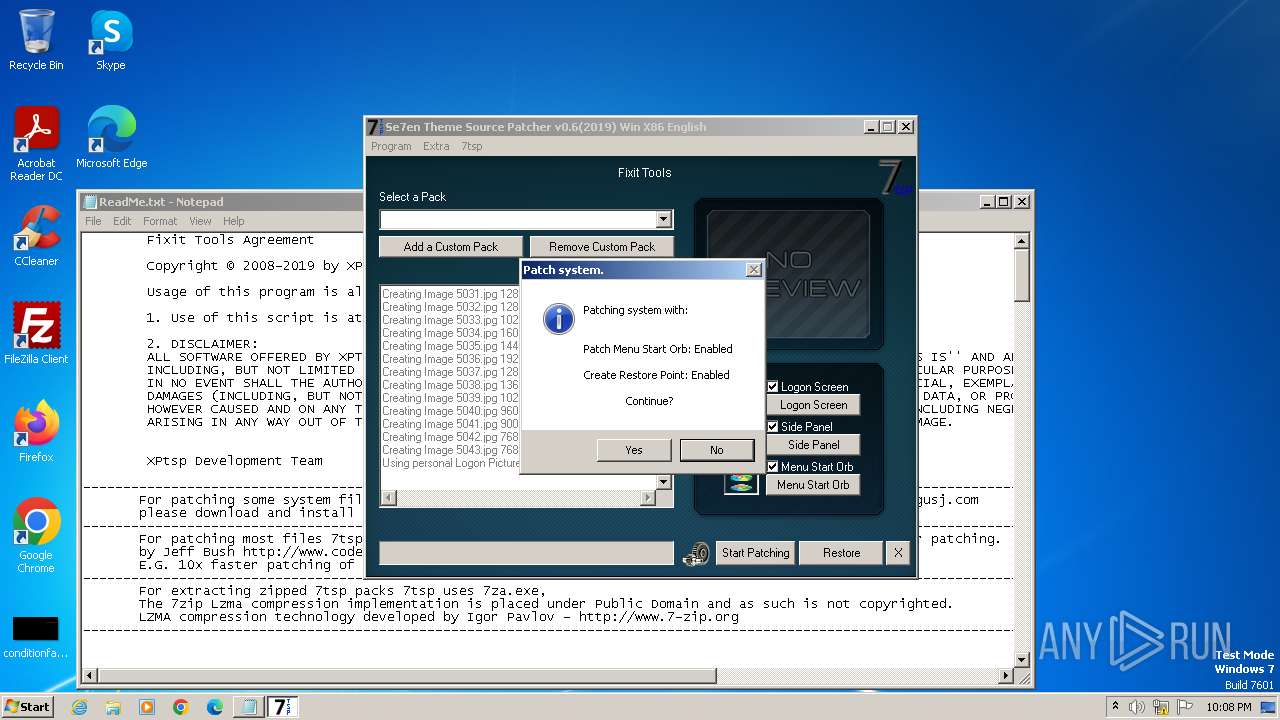
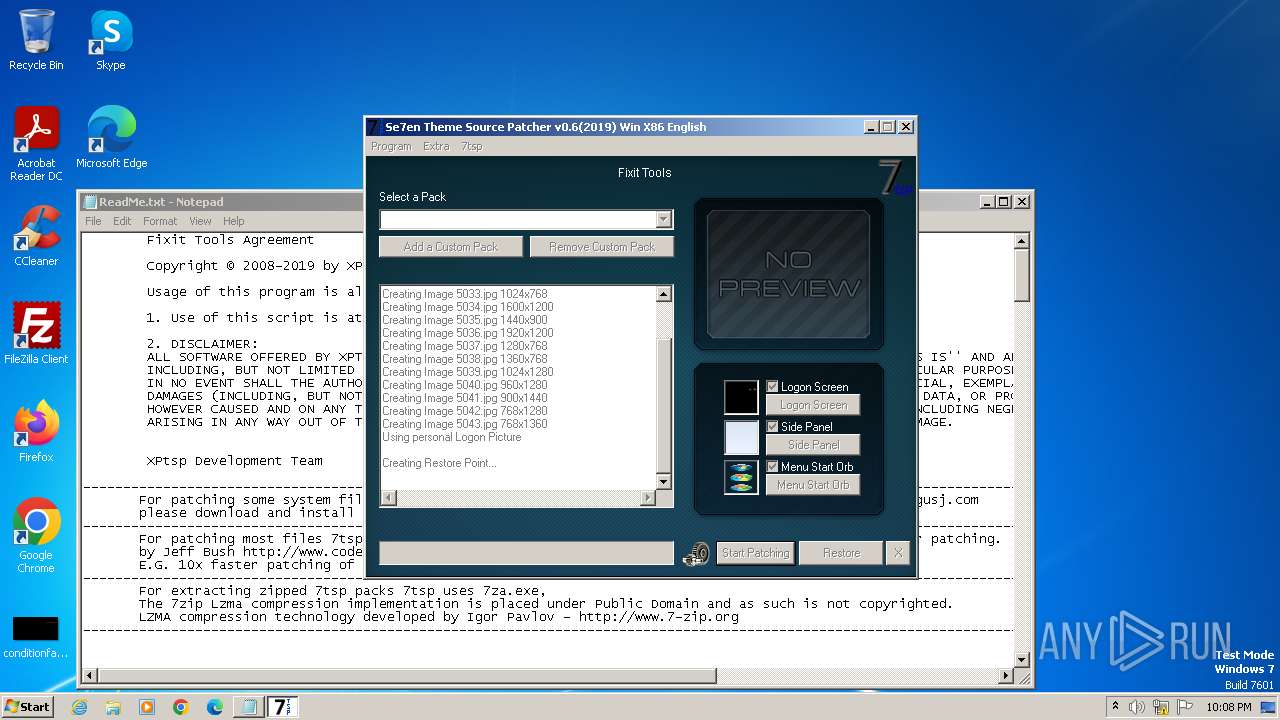
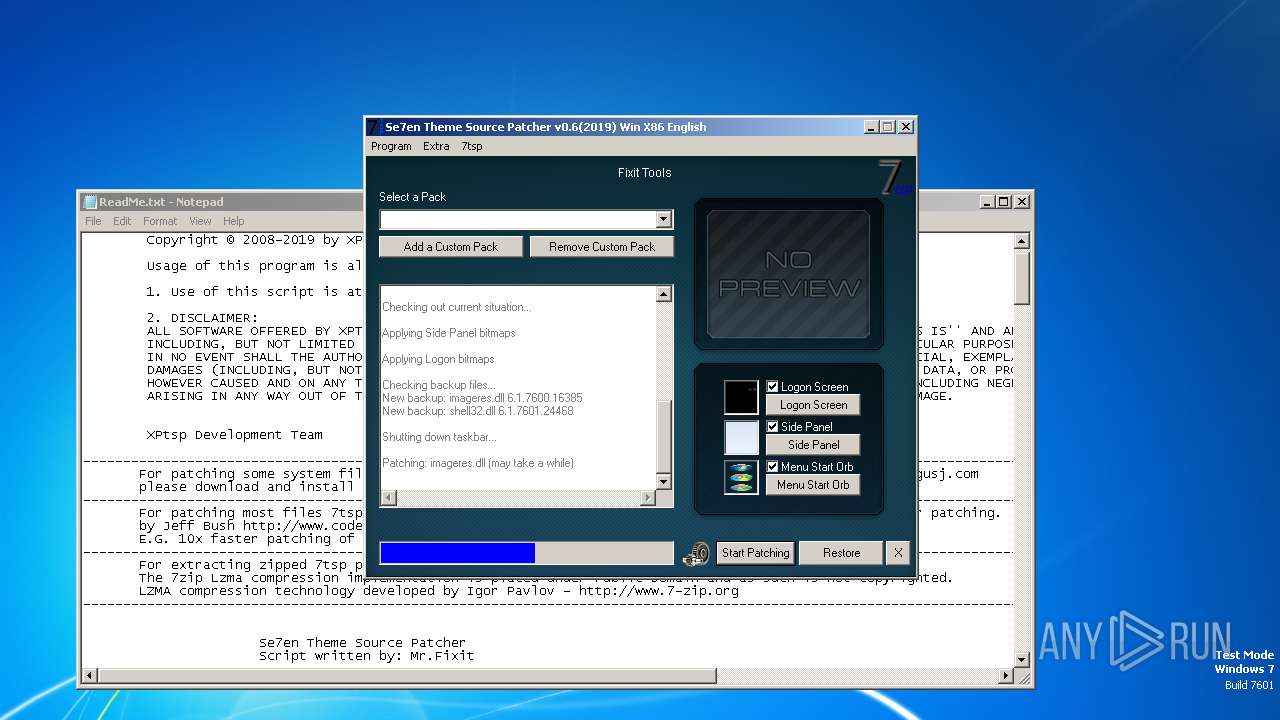
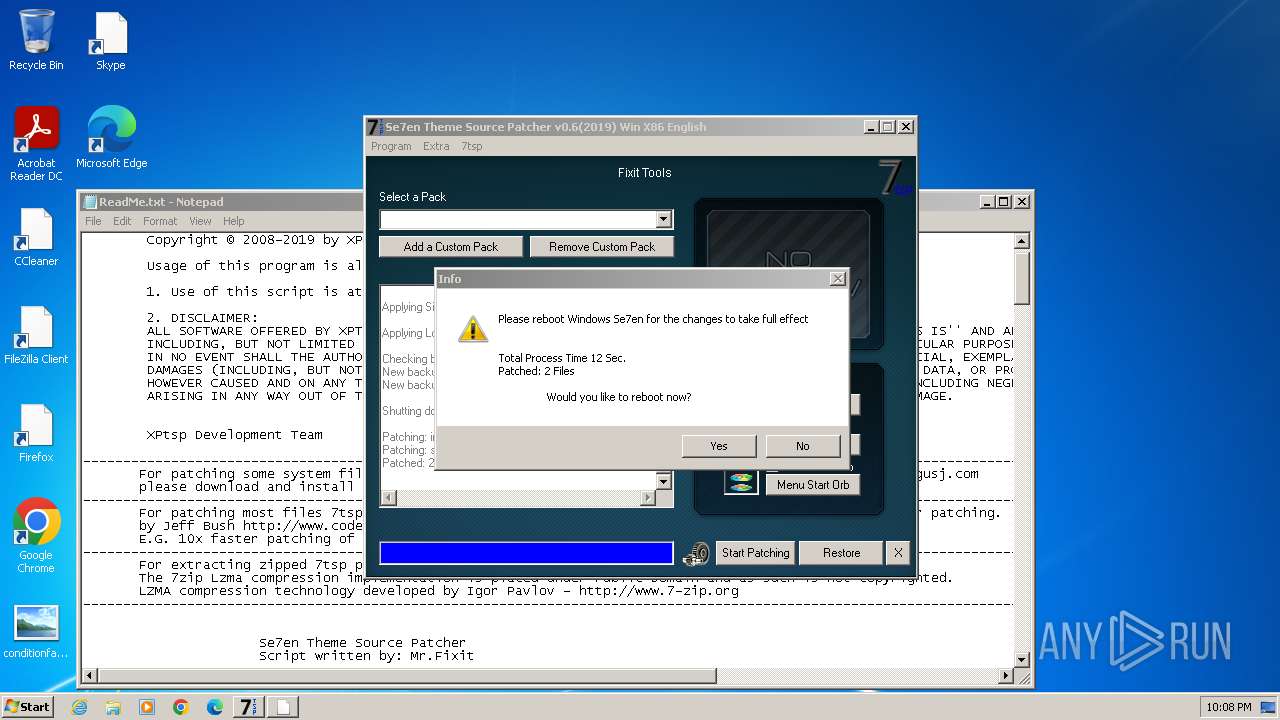
| File name: | 7tsp GUI v0.6(2019).exe |
| Full analysis: | https://app.any.run/tasks/81498521-075d-426f-bd15-2a561da1d25d |
| Verdict: | Malicious activity |
| Analysis date: | April 30, 2024, 21:06:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 0FC4B5592E3B58F1FC87D5EF81DE981A |
| SHA1: | F9408F54BE6540CCAF7CE0B9DBB80B81AFD83CA8 |
| SHA256: | 090C9E214599150F6ED241171BB2107E04D13BFA5E74927B094B139EAE280B65 |
| SSDEEP: | 98304:0kJXjsBN1FOVttlTfMO5bkjUBoUpQbo3r95HwTClvBAOMpWaQ0dy4ybVWT1rk/lv:0o31yYVBFX |
MALICIOUS
Drops the executable file immediately after the start
- 7tsp GUI v0.6(2019).exe (PID: 4068)
Starts NET.EXE for service management
- net.exe (PID: 1408)
- cmd.exe (PID: 1868)
- cmd.exe (PID: 1996)
- net.exe (PID: 2664)
Creates a writable file in the system directory
- 7tsp GUI v0.6(2019).exe (PID: 4068)
Changes the autorun value in the registry
- 7tsp GUI v0.6(2019).exe (PID: 4068)
SUSPICIOUS
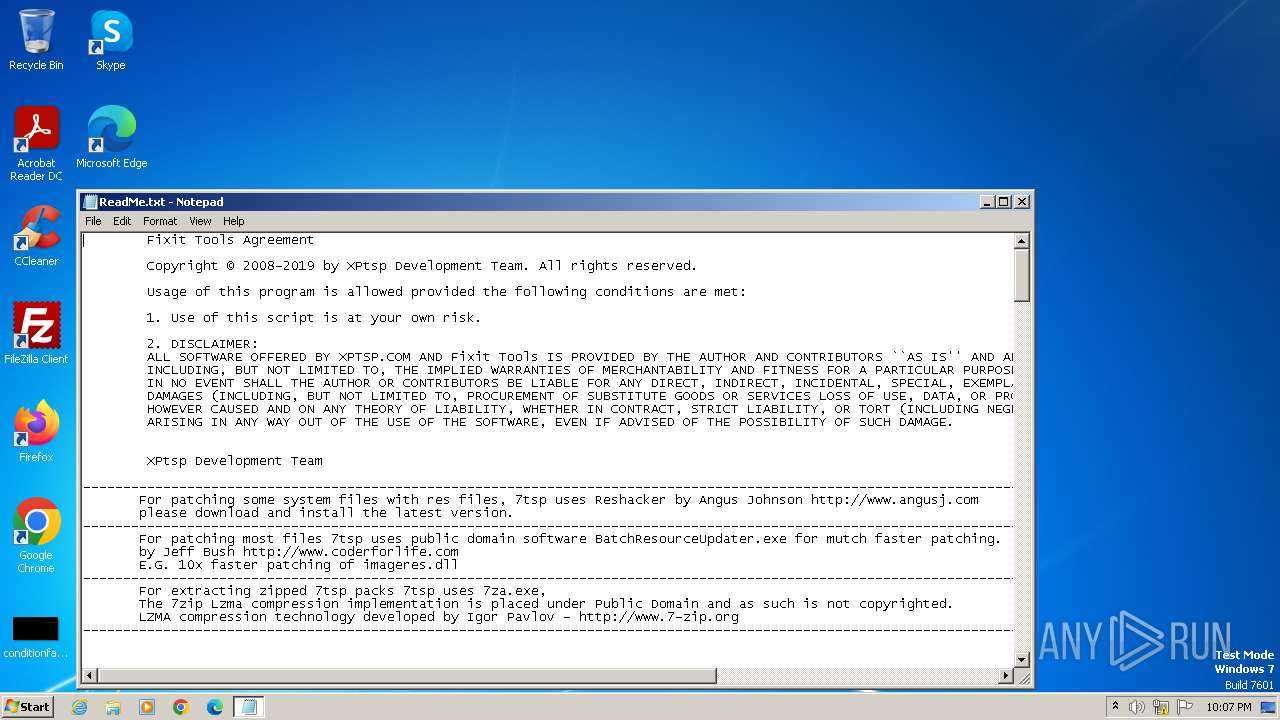
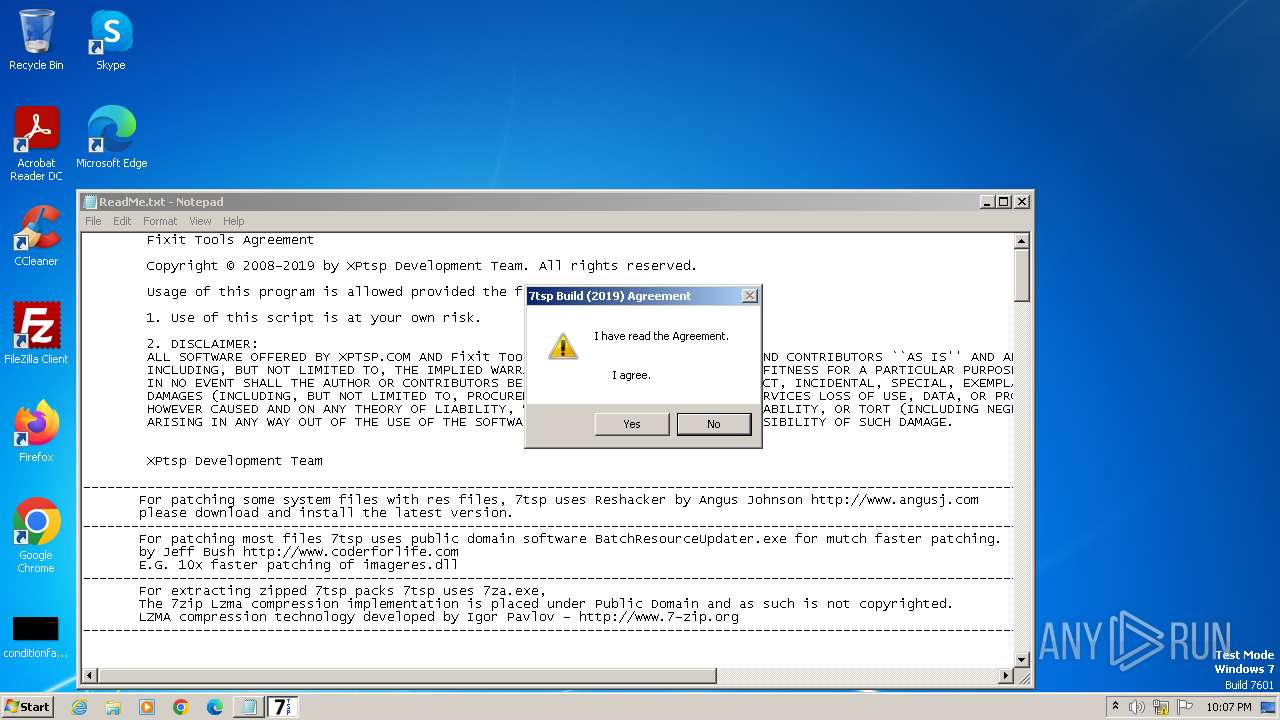
Start notepad (likely ransomware note)
- 7tsp GUI v0.6(2019).exe (PID: 4068)
Drops 7-zip archiver for unpacking
- 7tsp GUI v0.6(2019).exe (PID: 4068)
Executable content was dropped or overwritten
- 7tsp GUI v0.6(2019).exe (PID: 4068)
Starts CMD.EXE for commands execution
- 7tsp GUI v0.6(2019).exe (PID: 4068)
- c.i.c.exe (PID: 2092)
Searches for installed software
- 7tsp GUI v0.6(2019).exe (PID: 4068)
- dllhost.exe (PID: 2240)
Executes as Windows Service
- VSSVC.exe (PID: 2368)
Reads the Internet Settings
- 7tsp GUI v0.6(2019).exe (PID: 4068)
- sipnotify.exe (PID: 1816)
- runonce.exe (PID: 2068)
Process drops legitimate windows executable
- 7tsp GUI v0.6(2019).exe (PID: 4068)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 1020)
- cmd.exe (PID: 864)
- cmd.exe (PID: 764)
- cmd.exe (PID: 1800)
- cmd.exe (PID: 1144)
- cmd.exe (PID: 2272)
- cmd.exe (PID: 2560)
- cmd.exe (PID: 2548)
- cmd.exe (PID: 2572)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3916)
- cmd.exe (PID: 2112)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 3240)
- cmd.exe (PID: 2900)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1816)
- ctfmon.exe (PID: 1464)
Executing commands from a ".bat" file
- c.i.c.exe (PID: 2092)
INFO
Create files in a temporary directory
- 7tsp GUI v0.6(2019).exe (PID: 4068)
Checks supported languages
- 7tsp GUI v0.6(2019).exe (PID: 4068)
- ResHacker.exe (PID: 748)
- ResHacker.exe (PID: 116)
- ResHacker.exe (PID: 2204)
- ResHacker.exe (PID: 304)
- ResHacker.exe (PID: 2644)
- ResHacker.exe (PID: 2908)
- ResHacker.exe (PID: 2920)
- ResHacker.exe (PID: 2688)
- ResHacker.exe (PID: 1280)
- ResHacker.exe (PID: 2428)
- ResHacker.exe (PID: 2812)
- ResHacker.exe (PID: 2884)
- ResHacker.exe (PID: 3260)
- ResHacker.exe (PID: 3140)
- ResHacker.exe (PID: 3124)
- ResHacker.exe (PID: 3392)
- ResHacker.exe (PID: 3692)
- ResHacker.exe (PID: 2972)
- ResHacker.exe (PID: 3056)
- ResHacker.exe (PID: 2752)
- ResHacker.exe (PID: 3820)
- bru.exe (PID: 304)
- ResHacker.exe (PID: 2316)
- ResHacker.exe (PID: 3548)
- ResHacker.exe (PID: 3540)
- ResHacker.exe (PID: 1932)
- bru.exe (PID: 856)
- c.i.c.exe (PID: 2092)
- wmpnscfg.exe (PID: 2588)
- wmpnscfg.exe (PID: 2712)
Reads mouse settings
- 7tsp GUI v0.6(2019).exe (PID: 4068)
- c.i.c.exe (PID: 2092)
Checks Windows language
- 7tsp GUI v0.6(2019).exe (PID: 4068)
- c.i.c.exe (PID: 2092)
Reads the computer name
- 7tsp GUI v0.6(2019).exe (PID: 4068)
- ResHacker.exe (PID: 304)
- ResHacker.exe (PID: 748)
- ResHacker.exe (PID: 116)
- ResHacker.exe (PID: 2428)
- ResHacker.exe (PID: 2812)
- ResHacker.exe (PID: 2644)
- ResHacker.exe (PID: 2920)
- ResHacker.exe (PID: 2908)
- ResHacker.exe (PID: 2688)
- ResHacker.exe (PID: 1280)
- ResHacker.exe (PID: 3056)
- ResHacker.exe (PID: 2752)
- ResHacker.exe (PID: 3140)
- ResHacker.exe (PID: 3124)
- ResHacker.exe (PID: 3260)
- ResHacker.exe (PID: 3692)
- ResHacker.exe (PID: 3392)
- ResHacker.exe (PID: 2972)
- ResHacker.exe (PID: 3820)
- ResHacker.exe (PID: 2316)
- ResHacker.exe (PID: 3548)
- ResHacker.exe (PID: 3540)
- ResHacker.exe (PID: 1932)
- c.i.c.exe (PID: 2092)
- wmpnscfg.exe (PID: 2588)
- wmpnscfg.exe (PID: 2712)
Creates files in the program directory
- 7tsp GUI v0.6(2019).exe (PID: 4068)
- ResHacker.exe (PID: 304)
- ResHacker.exe (PID: 748)
- ResHacker.exe (PID: 116)
- ResHacker.exe (PID: 2644)
- icacls.exe (PID: 4040)
- ResHacker.exe (PID: 2316)
- ResHacker.exe (PID: 1932)
- icacls.exe (PID: 3332)
- c.i.c.exe (PID: 2092)
Reads the machine GUID from the registry
- 7tsp GUI v0.6(2019).exe (PID: 4068)
- bru.exe (PID: 304)
- bru.exe (PID: 856)
- c.i.c.exe (PID: 2092)
Creates files or folders in the user directory
- explorer.exe (PID: 2396)
- explorer.exe (PID: 2220)
Manual execution by a user
- runonce.exe (PID: 2068)
Reads the time zone
- runonce.exe (PID: 2068)
Reads security settings of Internet Explorer
- runonce.exe (PID: 2068)
Reads the Internet Settings
- explorer.exe (PID: 2220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:03:07 16:08:39+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 270336 |
| InitializedDataSize: | 151552 |
| UninitializedDataSize: | 602112 |
| EntryPoint: | 0xd5bc0 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.6.2.0 |
| ProductVersionNumber: | 3.3.6.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileVersion: | 0.6.2.0 |
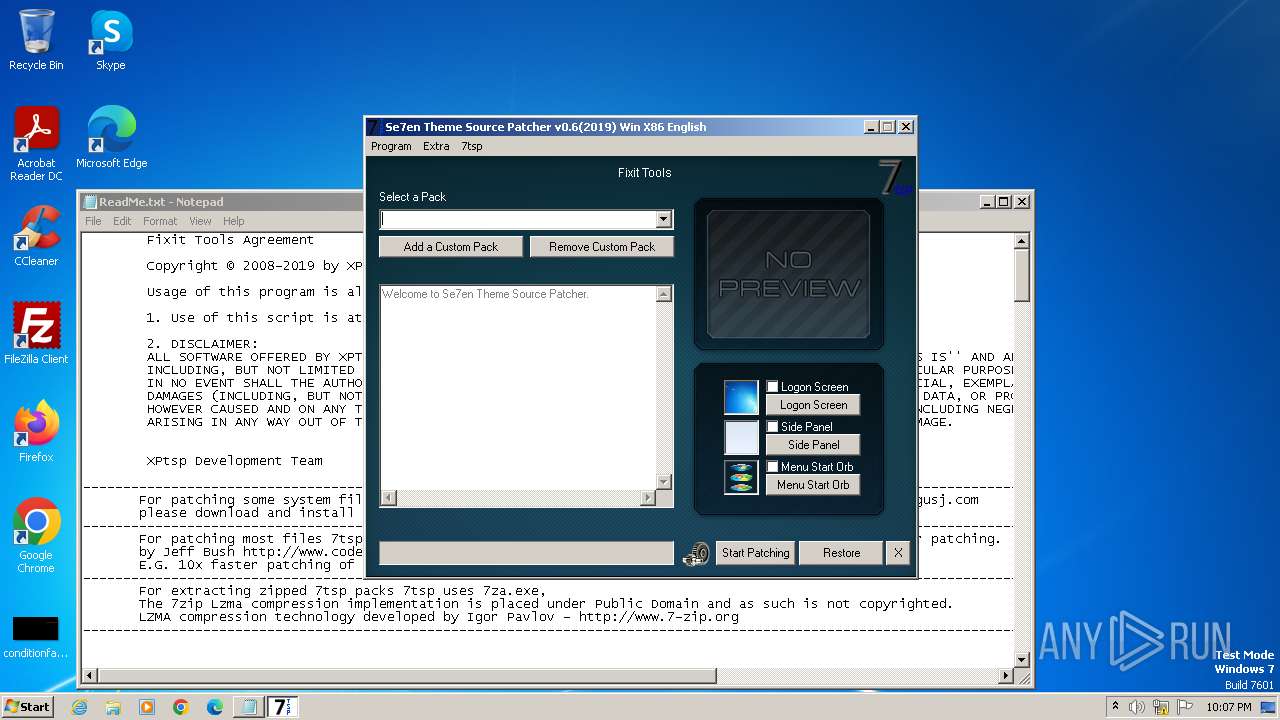
| Comments: | Se7en Theme Source Patcher v0.6.2019 Patches your Windows Se7en System Files with new Icons and Bitmaps |
| FileDescription: | Se7en Theme Source Patcher |
| LegalCopyright: | XPtsp Team -Program Written By Fixit- |
Total processes
235
Monitored processes
102
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | TAKEOWN /F "C:\Windows\system32\imageres.dll" /a | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 116 | "C:\ProgramData\local\temp\7tsp\Programs\reshacker.exe""" -extract "C:\Windows\system32\shell32.dll", "C:\ProgramData\local\temp\7tsp\Extra\shell32\633.bmp", BITMAP,633, | C:\ProgramData\local\temp\7tsp\programs\ResHacker.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Resource viewer, decompiler & recompiler. Exit code: 0 Version: 3.6.0.92 Modules
| |||||||||||||||
| 116 | icacls "C:\Windows\system32\imageres.dll" /grant *S-1-5-32-544:F | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 304 | "C:\ProgramData\local\temp\7tsp\Programs\reshacker.exe""" -extract "C:\Windows\explorer.exe", "C:\ProgramData\local\temp\7tsp\temp\orb.bmp", BITMAP,6801, | C:\ProgramData\local\temp\7tsp\programs\ResHacker.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Resource viewer, decompiler & recompiler. Exit code: 0 Version: 3.6.0.92 Modules
| |||||||||||||||
| 304 | "C:\ProgramData\local\temp\7tsp\programs\bru.exe""" "C:\ProgramData\local\temp\7tsp\imageres.dll.bru | C:\ProgramData\local\temp\7tsp\programs\bru.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 748 | "C:\ProgramData\local\temp\7tsp\Programs\reshacker.exe""" -extract "C:\Windows\system32\imageres.dll", "C:\ProgramData\local\temp\7tsp\Extra\logon\5033.jpg", IMAGE,5033, | C:\ProgramData\local\temp\7tsp\programs\ResHacker.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Resource viewer, decompiler & recompiler. Exit code: 0 Version: 3.6.0.92 Modules
| |||||||||||||||
| 764 | C:\Windows\system32\cmd.exe /c icacls "C:\Windows\system32\imageres.dll" /setowner *S-1-5-80-956008885-3418522649-1831038044-1853292631-2271478464 | C:\Windows\System32\cmd.exe | — | 7tsp GUI v0.6(2019).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 856 | "C:\ProgramData\local\temp\7tsp\programs\bru.exe""" "C:\ProgramData\local\temp\7tsp\shell32.dll.bru | C:\ProgramData\local\temp\7tsp\programs\bru.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 864 | C:\Windows\system32\cmd.exe /c icacls "C:\Windows\system32\imageres.dll" /grant *S-1-5-32-544:F | C:\Windows\System32\cmd.exe | — | 7tsp GUI v0.6(2019).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 948 | C:\Windows\system32\cmd.exe /c ""C:\ProgramData\local\temp\7tsp\Programs\reshacker.exe""" -extract "C:\ProgramData\local\temp\7tsp\resources\shell32.dll.res", "C:\ProgramData\local\temp\7tsp\recompile\recompile.rc ,,," | C:\Windows\System32\cmd.exe | — | 7tsp GUI v0.6(2019).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
32 607
Read events
32 090
Write events
498
Delete events
19
Modification events
| (PID) Process: | (4068) 7tsp GUI v0.6(2019).exe | Key: | HKEY_CURRENT_USER\Software\Fixit Tools\7tsp |
| Operation: | write | Name: | Agreement |
Value: (2019)Yes | |||
| (PID) Process: | (4068) 7tsp GUI v0.6(2019).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (4068) 7tsp GUI v0.6(2019).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | 0 |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00370074007300700020004700550049002000760030002E0036002800320030003100390029002E00650078006500000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070000000 | |||
| (PID) Process: | (4068) 7tsp GUI v0.6(2019).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (4068) 7tsp GUI v0.6(2019).exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (4068) 7tsp GUI v0.6(2019).exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000070000000200000006000000000000000B0000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (4068) 7tsp GUI v0.6(2019).exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4068) 7tsp GUI v0.6(2019).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | 4 |
Value: 370074007300700020004700550049002000760030002E0036002800320030003100390029002E0065007800650000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000006E0100009C000000EE0300007C020000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (4068) 7tsp GUI v0.6(2019).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | delete value | Name: | 4 |
Value: 7tsp GUI v0.6(2019).exe | |||
| (PID) Process: | (4068) 7tsp GUI v0.6(2019).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | 4 |
Value: 370074007300700020004700550049002000760030002E0036002800320030003100390029002E006500780065000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000006B010000730000009703000044020000000000000000000000000000000000006E0100009C000000EE0300007C020000000000000000000000000000000000000100000000000000 | |||
Executable files
17
Suspicious files
26
Text files
51
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4068 | 7tsp GUI v0.6(2019).exe | C:\ProgramData\local\temp\7tsp\Programs\logo.bmp | image | |
MD5:E0EF4516C9ECA05CCF55E3F6413B18FD | SHA256:FDE61D0757522A87E9D11A64A6FD08569BD7977E94ED9E9502F52843217B6D50 | |||
| 4068 | 7tsp GUI v0.6(2019).exe | C:\Users\admin\AppData\Local\Temp\aut85C1.tmp | binary | |
MD5:7281A8624942B0FD8D7707969122E6F2 | SHA256:F4D5025A7425C592EF3D1B4EAD6ED056A6B4DAAB57291957D7314216FC5C8E96 | |||
| 4068 | 7tsp GUI v0.6(2019).exe | C:\Users\admin\AppData\Local\Temp\aut5621.tmp | binary | |
MD5:50A46D26B330BCD5D0BAC4E14554953B | SHA256:0D7193BDB42674D17C242D8504DB31A2C5B6864BD1D372016E8CDC9EAA62D9E4 | |||
| 4068 | 7tsp GUI v0.6(2019).exe | C:\Users\admin\AppData\Local\Temp\aut868D.tmp | binary | |
MD5:EE15D23DEA27B37C972E58AFE27DC201 | SHA256:4536C7F61CD9A26411D159E91DFF12B43AC72AEBA9F6C252AF49F0E682D12E19 | |||
| 4068 | 7tsp GUI v0.6(2019).exe | C:\ProgramData\local\temp\7tsp\programs\lang.ini | text | |
MD5:DD3D7C4A542DBD24F254093762300901 | SHA256:38B48270CC628E4B60DDB354EE115E6C465740D0B93AA6FCAECC60D5C67D9B72 | |||
| 4068 | 7tsp GUI v0.6(2019).exe | C:\Users\admin\AppData\Local\Temp\aut85A1.tmp | binary | |
MD5:EE0184EA0040C539DF18EDC0C60E122D | SHA256:5D6D88804FF6C8E90C895625173422A0C94AF20D53B4A5AE66299CE9543FF09C | |||
| 4068 | 7tsp GUI v0.6(2019).exe | C:\ProgramData\local\temp\7tsp\programs\bru.exe | executable | |
MD5:6D93FA10C1C8C9DE200CF63F89A9092A | SHA256:163F17B8F6DB680DE43A71DCCA00101F9935AAF09B1E75DBF756DA16B9C80536 | |||
| 4068 | 7tsp GUI v0.6(2019).exe | C:\Users\admin\AppData\Local\Temp\aut8580.tmp | binary | |
MD5:24A69F380E798553D3057BB10E48D5D7 | SHA256:12A574B867BF5B93BFD50F0BE082BC34E8A081CF1D4632CC68F4EEE839B197C9 | |||
| 4068 | 7tsp GUI v0.6(2019).exe | C:\Users\admin\AppData\Local\Temp\aut8590.tmp | binary | |
MD5:27DA1566828714105C1ADBB661C76F7A | SHA256:2555C1E91E885ADBFE1F55617B1649DC926DF9AE3BC09B99D727C428B0D2AB17 | |||
| 4068 | 7tsp GUI v0.6(2019).exe | C:\ProgramData\local\temp\7tsp\programs\7za.exe | executable | |
MD5:C6D72642721E84D227DEFC3EC4AB12E6 | SHA256:0CC0DE83B51DAE55A4FCAE559DEFC87BEA8448010D064C316ABCFE9459ECE035 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
12
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1816 | sipnotify.exe | HEAD | — | 184.25.191.235:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133589885519530000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1472 | svchost.exe | 239.255.255.250:3702 | — | — | — | unknown |
1120 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1816 | sipnotify.exe | 184.25.191.235:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |