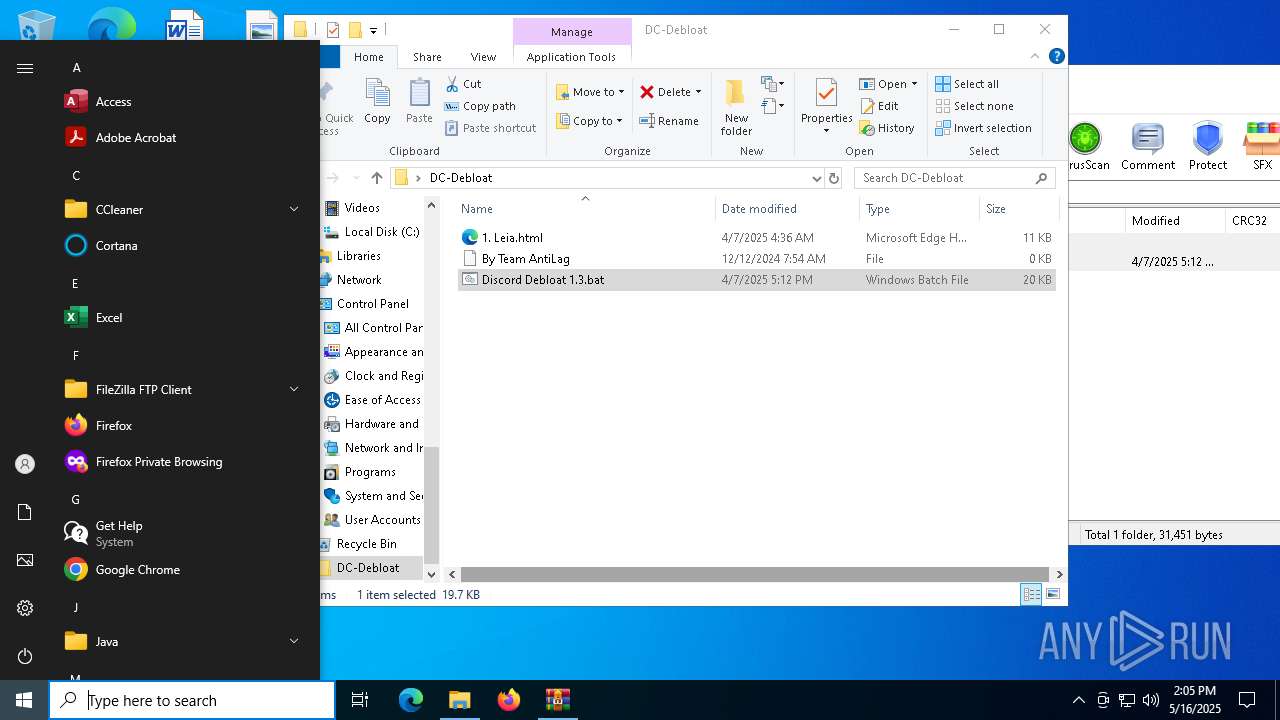
| File name: | DC-Debloat 1.3.rar |
| Full analysis: | https://app.any.run/tasks/c94efca9-6e67-4b33-b905-e637b1a1f6ca |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 14:03:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 953029A4958F9DBD8CE9CAC750F86501 |
| SHA1: | 99D970DE45E080D1EECB93F42730B0DAFB782E24 |
| SHA256: | 09070FC6202DB53FBCDA0FC75956DE9069FE504B0F94FA1661CEBDC3EB964D05 |
| SSDEEP: | 192:0/GYsueETb1o+3wEABB85NaDuOXGZa9twp7m8J79QSu0rUctIaD:a7T64ABGrafmpdJPlrUctD |
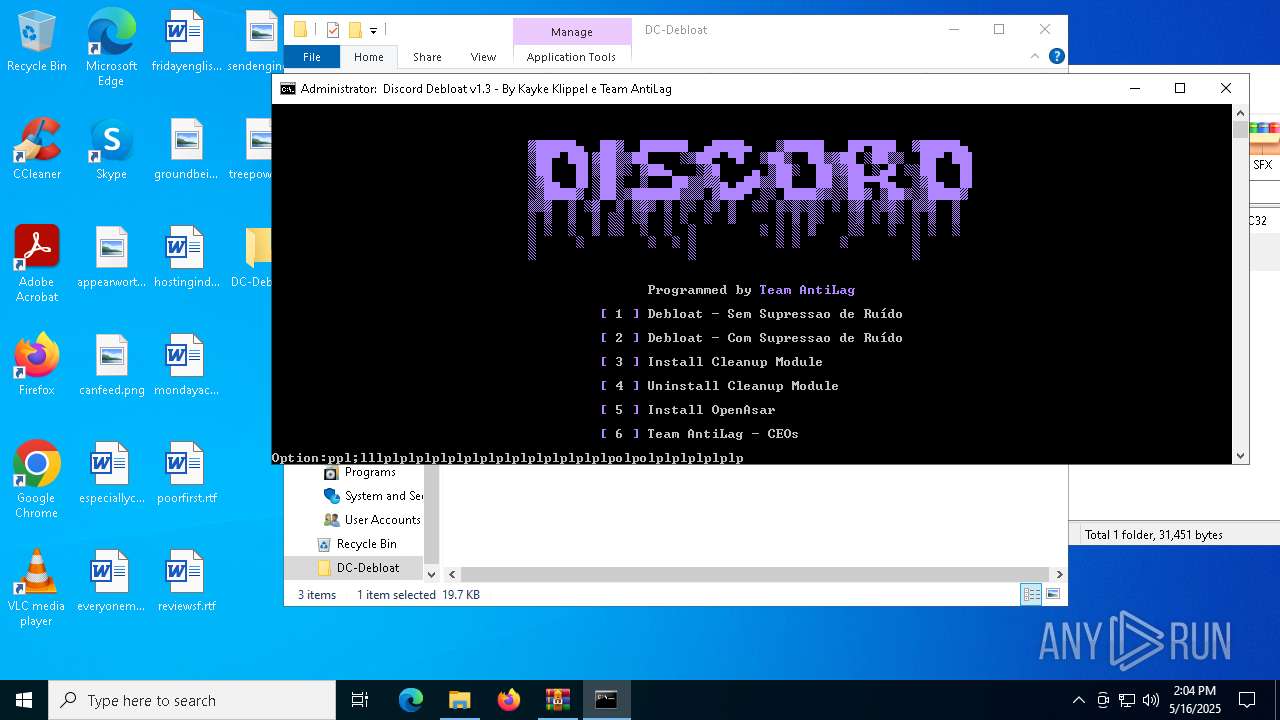
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1276)
SUSPICIOUS
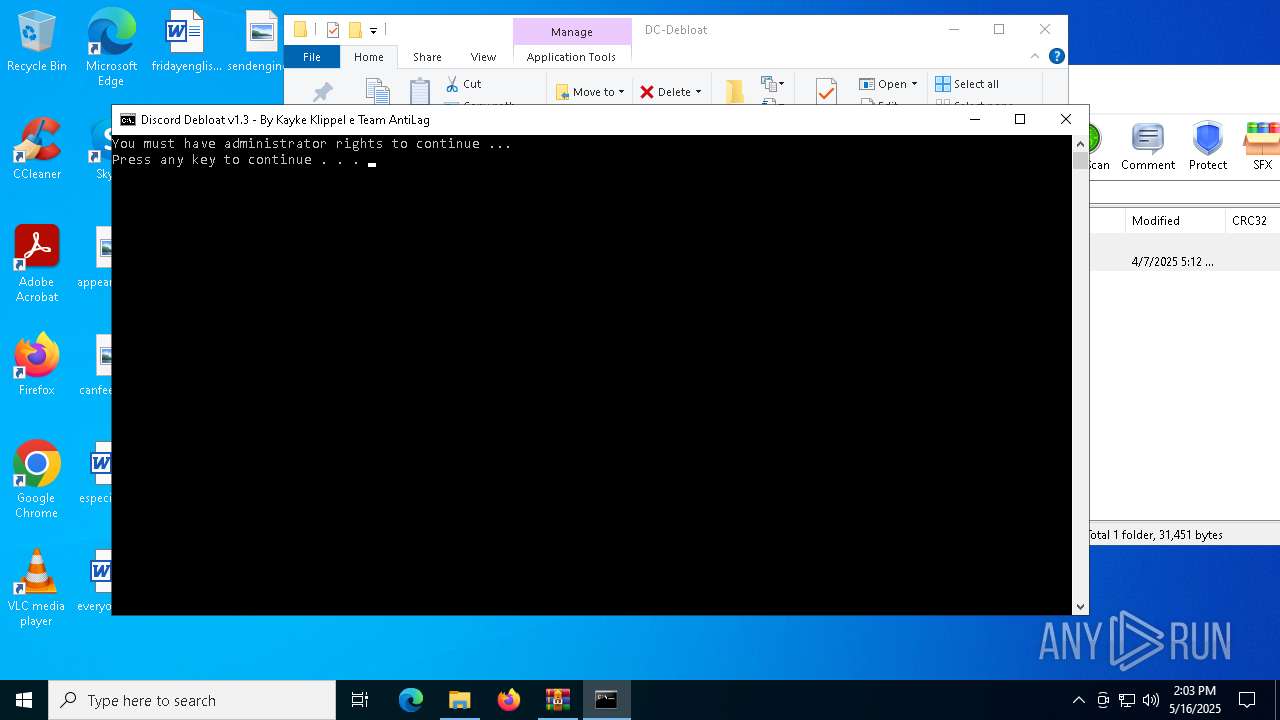
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4464)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4464)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4464)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4464)
Downloads file from URI via Powershell
- powershell.exe (PID: 4212)
- powershell.exe (PID: 6876)
- powershell.exe (PID: 6108)
- powershell.exe (PID: 4608)
- powershell.exe (PID: 5600)
- powershell.exe (PID: 6700)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4464)
Application launched itself
- cmd.exe (PID: 4464)
Starts application with an unusual extension
- cmd.exe (PID: 516)
- cmd.exe (PID: 4464)
INFO
Reads the software policy settings
- slui.exe (PID: 6712)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2092)
- powershell.exe (PID: 4212)
- powershell.exe (PID: 6108)
- powershell.exe (PID: 6876)
- powershell.exe (PID: 4608)
- powershell.exe (PID: 5600)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 6256)
Changes the display of characters in the console
- cmd.exe (PID: 4464)
- cmd.exe (PID: 516)
Manual execution by a user
- cmd.exe (PID: 4464)
- cmd.exe (PID: 516)
Checks supported languages
- chcp.com (PID: 4180)
- chcp.com (PID: 2692)
Checks proxy server information
- powershell.exe (PID: 4212)
- powershell.exe (PID: 6876)
- powershell.exe (PID: 6108)
- powershell.exe (PID: 4608)
- powershell.exe (PID: 6700)
Disables trace logs
- powershell.exe (PID: 6108)
- powershell.exe (PID: 6876)
- powershell.exe (PID: 4608)
- powershell.exe (PID: 5600)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 4212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 4204 |
| UncompressedSize: | 11256 |
| OperatingSystem: | Win32 |
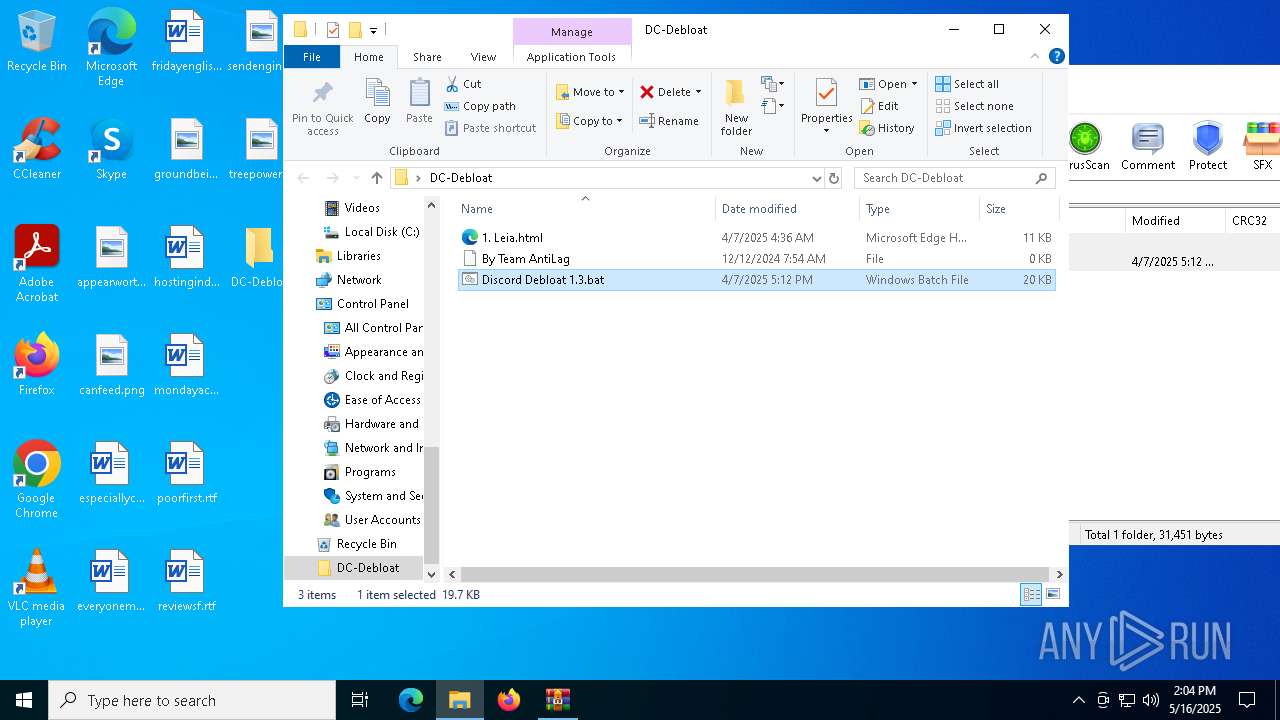
| ArchivedFileName: | DC-Debloat/1. Leia.html |
Total processes
170
Monitored processes
41
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | reg delete "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run" /v Discord /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
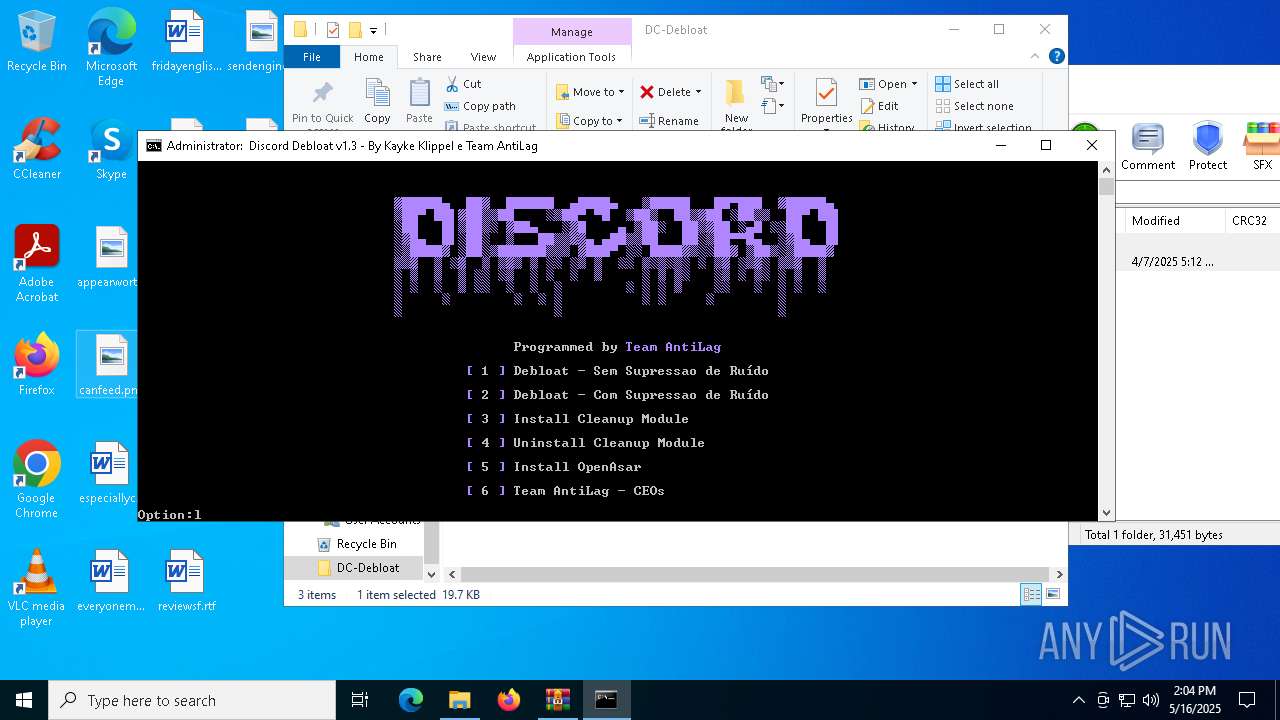
| 516 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\DC-Debloat\Discord Debloat 1.3.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | reg delete "HKEY_CURRENT_USER\SOFTWARE\Discord\Modules" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | taskkill /f /im Discord.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | reg delete "HKEY_CURRENT_USER\Software\Discord\ErrorReporting" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | reg delete "HKEY_CURRENT_USER\SOFTWARE\Discord\Update" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\DC-Debloat 1.3.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2064 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
40 121
Read events
40 112
Write events
8
Delete events
1
Modification events
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DC-Debloat 1.3.rar | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (300) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Discord |
Value: | |||
Executable files
0
Suspicious files
2
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.3047\DC-Debloat\Discord Debloat 1.3.bat | text | |
MD5:322A2473ACB16D90F9FE0B455199B1B2 | SHA256:3FE0B783AE3F04CCF13DB1FC744BCC3B2BB6AAF8A9C4528DD916F87DF7129AB3 | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.3047\DC-Debloat\1. Leia.html | binary | |
MD5:3B1ED3F2C0B376AE1D0A30ACA9C0C53F | SHA256:47BDEC06C0A7B40208917ABCCEDA7ABB7BDFA10B7FF73A21EA982868B0187560 | |||
| 2092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ad0t3mra.r3n.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ykkowtc1.r3e.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uencdu0t.olw.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ddwnct3o.wew.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6256 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3n4g5orq.gdy.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4608 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_axfkfrig.pip.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6876 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1y5mzlv5.j0i.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5600 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5hoql3do.rxw.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
45
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4040 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4040 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.36:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.36:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |