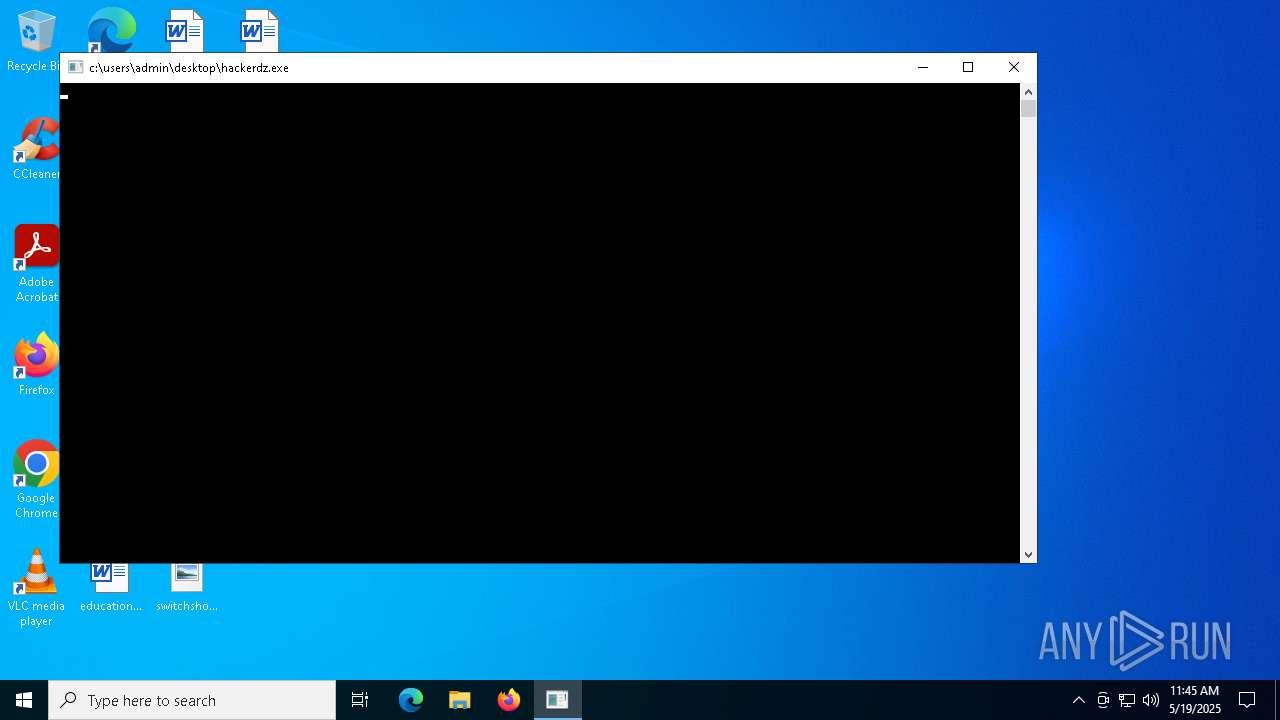
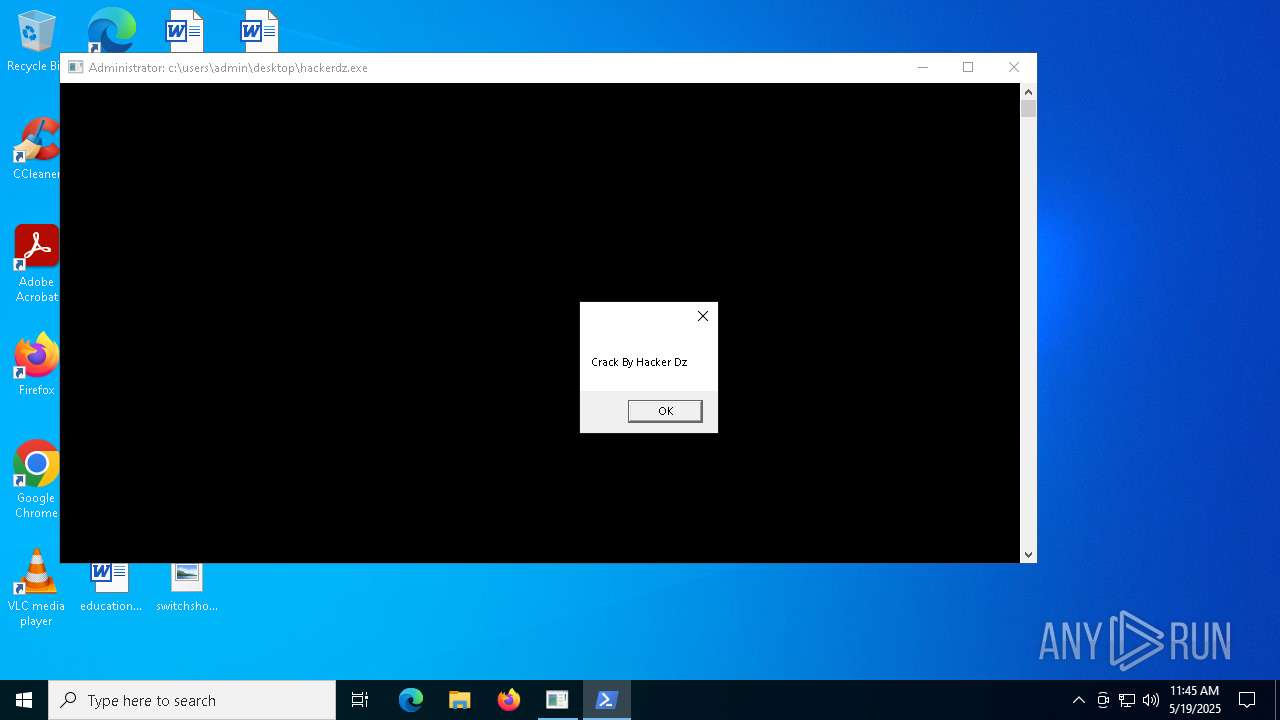
| File name: | HackerDz.exe |
| Full analysis: | https://app.any.run/tasks/6f5b4914-1071-4d7c-8c42-4fc1a81b90c9 |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 11:45:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | 9CD9B382CBFF666A39A1EC2BDE607891 |
| SHA1: | 49F6972C21C59F89284C2F0904FBEF9B30A6C800 |
| SHA256: | 08FE1D79059D1DEF2822C7C222BFA749C20B13137B8B82367FB8C42B123274AB |
| SSDEEP: | 6144:i0/1Thw5w4qjPRrf2VrRZHMrbLcPN7QLi8NiTbXA:5cPNCNiTLA |
MALICIOUS
JEEFO has been detected
- icsys.icn.exe (PID: 3240)
- HackerDz.exe (PID: 4408)
- explorer.exe (PID: 4980)
- svchost.exe (PID: 4220)
Changes the autorun value in the registry
- explorer.exe (PID: 4980)
- svchost.exe (PID: 4220)
SUSPICIOUS
Executable content was dropped or overwritten
- HackerDz.exe (PID: 4408)
- icsys.icn.exe (PID: 3240)
- explorer.exe (PID: 4980)
- spoolsv.exe (PID: 1276)
Starts itself from another location
- HackerDz.exe (PID: 4408)
- explorer.exe (PID: 4980)
- spoolsv.exe (PID: 1276)
- svchost.exe (PID: 4220)
- icsys.icn.exe (PID: 3240)
Starts application with an unusual extension
- HackerDz.exe (PID: 4408)
The process creates files with name similar to system file names
- icsys.icn.exe (PID: 3240)
- spoolsv.exe (PID: 1276)
Executing commands from a ".bat" file
- hackerdz.exe (PID: 920)
Starts CMD.EXE for commands execution
- hackerdz.exe (PID: 920)
Creates or modifies Windows services
- svchost.exe (PID: 4220)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4448)
INFO
Checks supported languages
- HackerDz.exe (PID: 4408)
- icsys.icn.exe (PID: 3240)
- hackerdz.exe (PID: 920)
- svchost.exe (PID: 4220)
- spoolsv.exe (PID: 1276)
- spoolsv.exe (PID: 4696)
- identity_helper.exe (PID: 5600)
- explorer.exe (PID: 4980)
Create files in a temporary directory
- HackerDz.exe (PID: 4408)
- icsys.icn.exe (PID: 3240)
- hackerdz.exe (PID: 920)
- explorer.exe (PID: 4980)
- spoolsv.exe (PID: 1276)
- svchost.exe (PID: 4220)
- spoolsv.exe (PID: 4696)
The sample compiled with english language support
- HackerDz.exe (PID: 4408)
Reads the computer name
- svchost.exe (PID: 4220)
- identity_helper.exe (PID: 5600)
Auto-launch of the file from Registry key
- svchost.exe (PID: 4220)
- explorer.exe (PID: 4980)
Reads security settings of Internet Explorer
- cmd.exe (PID: 4448)
Attempting to use instant messaging service
- msedge.exe (PID: 2516)
Manual execution by a user
- msedge.exe (PID: 5968)
- svchost.exe (PID: 7880)
- explorer.exe (PID: 7936)
- svchost.exe (PID: 7952)
- msedge.exe (PID: 4164)
Application launched itself
- msedge.exe (PID: 5968)
- msedge.exe (PID: 4920)
Reads Environment values
- identity_helper.exe (PID: 5600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:04:01 07:08:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 106496 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x290c |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Project1 |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | TJprojMain |
| OriginalFileName: | TJprojMain.exe |
Total processes
184
Monitored processes
57
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6592 --field-trial-handle=2380,i,16354387876830473594,14277515331972283930,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 920 | c:\users\admin\desktop\hackerdz.exe | C:\Users\admin\Desktop\hackerdz.exe | — | HackerDz.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1072 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x310,0x314,0x318,0x308,0x320,0x7ffc89dd5fd8,0x7ffc89dd5fe4,0x7ffc89dd5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1276 | c:\windows\resources\spoolsv.exe SE | C:\Windows\Resources\spoolsv.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1600 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=7376 --field-trial-handle=2380,i,16354387876830473594,14277515331972283930,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1628 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2564 --field-trial-handle=2380,i,16354387876830473594,14277515331972283930,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2584 --field-trial-handle=2400,i,5814528047996816622,12851423638111982961,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2516 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2556 --field-trial-handle=2380,i,16354387876830473594,14277515331972283930,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2800 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5744 --field-trial-handle=2380,i,16354387876830473594,14277515331972283930,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2908 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5972 --field-trial-handle=2380,i,16354387876830473594,14277515331972283930,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
13 642
Read events
13 593
Write events
45
Delete events
4
Modification events
| (PID) Process: | (4408) HackerDz.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (3240) icsys.icn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (4980) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (4980) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (4980) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (4980) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
| (PID) Process: | (4220) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (4220) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (4220) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (4220) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
Executable files
11
Suspicious files
261
Text files
34
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 920 | hackerdz.exe | C:\Users\admin\AppData\Local\Temp\C3DE.tmp\C3DF.tmp\C3E0.bat | text | |
MD5:040D7AAE1959776134A7469923D7B3AE | SHA256:D5666B9881D9027B109FC0BFF36DFB56A91F6E5561D3648A30293230A2F20D6B | |||
| 4408 | HackerDz.exe | C:\Users\admin\Desktop\hackerdz.exe | executable | |
MD5:26E601FA0FDD4E13EDAC588799400E41 | SHA256:DC9F5820E60DC7A99C4763D992381B45FE937AA254B77DDC99721D0304151F9D | |||
| 4696 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF7A633A60A1CF4C10.TMP | binary | |
MD5:7A959373C1D2452EFB1F77DB16CF12DF | SHA256:C3B8A67249927A9A4E4B8B93815BFE5821B77E75160F17EE208D9A5D16841EB0 | |||
| 3240 | icsys.icn.exe | C:\Windows\Resources\Themes\explorer.exe | executable | |
MD5:53682A0B64380F880767340C9E2C3478 | SHA256:039F9A456E3E0F3D6E938F2686046628190BC8F5EB028F926AFE46BBE7B20B71 | |||
| 4408 | HackerDz.exe | C:\Users\admin\AppData\Local\Temp\~DFA779CAF49460A80E.TMP | binary | |
MD5:88D61A489767370B7A18E35FFCB573FB | SHA256:5441563E43FF70A8AFC600A1A8F9AD9B2B1B086B95BB112A367487ECA74E8ABD | |||
| 4980 | explorer.exe | C:\Windows\Resources\spoolsv.exe | executable | |
MD5:85184D2C799CE48FCDE96F323BDF0F12 | SHA256:11E9005DCECED5D1CE94AF3F2405CD2D1F6BDC12D5B357D678FC7D0FFE69033E | |||
| 5968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10d999.TMP | — | |
MD5:— | SHA256:— | |||
| 5968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10d999.TMP | — | |
MD5:— | SHA256:— | |||
| 5968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1276 | spoolsv.exe | C:\Windows\Resources\svchost.exe | executable | |
MD5:3B18680CEEC3490116560597A8B7072F | SHA256:4B8C44F7AE31912299AB29FD33F837DF0C60260C288F60589303DE934B89D358 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
79
DNS requests
53
Threats
29
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5364 | svchost.exe | HEAD | 200 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1747700501&P2=404&P3=2&P4=n6oBNLHhID0kMwKunixrJ%2bjWxKpfB%2f8r32lmQpGZ5c8hEL3VlqrA%2bGsZB8ewiBn9BXQUaG0LRrCoSCsiDR3yeQ%3d%3d | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5364 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1747700501&P2=404&P3=2&P4=n6oBNLHhID0kMwKunixrJ%2bjWxKpfB%2f8r32lmQpGZ5c8hEL3VlqrA%2bGsZB8ewiBn9BXQUaG0LRrCoSCsiDR3yeQ%3d%3d | unknown | — | — | whitelisted |
5364 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1747700501&P2=404&P3=2&P4=n6oBNLHhID0kMwKunixrJ%2bjWxKpfB%2f8r32lmQpGZ5c8hEL3VlqrA%2bGsZB8ewiBn9BXQUaG0LRrCoSCsiDR3yeQ%3d%3d | unknown | — | — | whitelisted |
5364 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1747700501&P2=404&P3=2&P4=n6oBNLHhID0kMwKunixrJ%2bjWxKpfB%2f8r32lmQpGZ5c8hEL3VlqrA%2bGsZB8ewiBn9BXQUaG0LRrCoSCsiDR3yeQ%3d%3d | unknown | — | — | whitelisted |
5364 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1747700501&P2=404&P3=2&P4=n6oBNLHhID0kMwKunixrJ%2bjWxKpfB%2f8r32lmQpGZ5c8hEL3VlqrA%2bGsZB8ewiBn9BXQUaG0LRrCoSCsiDR3yeQ%3d%3d | unknown | — | — | whitelisted |
5364 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1747700501&P2=404&P3=2&P4=n6oBNLHhID0kMwKunixrJ%2bjWxKpfB%2f8r32lmQpGZ5c8hEL3VlqrA%2bGsZB8ewiBn9BXQUaG0LRrCoSCsiDR3yeQ%3d%3d | unknown | — | — | whitelisted |
5364 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1747700501&P2=404&P3=2&P4=n6oBNLHhID0kMwKunixrJ%2bjWxKpfB%2f8r32lmQpGZ5c8hEL3VlqrA%2bGsZB8ewiBn9BXQUaG0LRrCoSCsiDR3yeQ%3d%3d | unknown | — | — | whitelisted |
5364 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1747700501&P2=404&P3=2&P4=n6oBNLHhID0kMwKunixrJ%2bjWxKpfB%2f8r32lmQpGZ5c8hEL3VlqrA%2bGsZB8ewiBn9BXQUaG0LRrCoSCsiDR3yeQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5968 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2516 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2516 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
discord.gg |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
discord.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2516 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2516 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2516 | msedge.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
2516 | msedge.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
2516 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2516 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2516 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2516 | msedge.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
2516 | msedge.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
2516 | msedge.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |