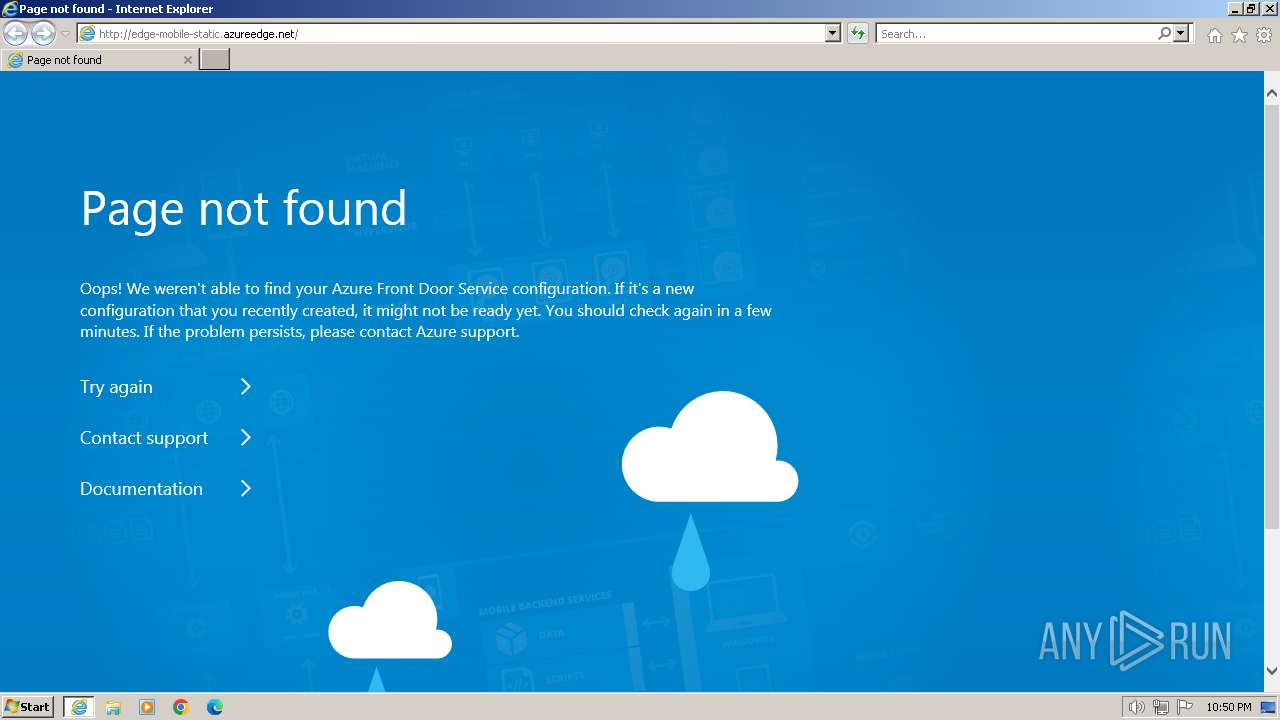
| URL: | edge-mobile-static.azureedge.net |
| Full analysis: | https://app.any.run/tasks/b8a5481b-0441-447c-abab-cdeb7ebd8a52 |
| Verdict: | Malicious activity |
| Analysis date: | February 28, 2024, 22:50:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 92F2B02D1A7D506281E4B8569F216E1A |
| SHA1: | EB56D1EBADCC90F9A5F7D4D9DC4C26B31A3A1C24 |
| SHA256: | 08FA79C81B4302E7F3544AAD1291912AE8906436D99BB5A03688FB0501BA7EF8 |
| SSDEEP: | 3:kD1KotWfcncn:kDAoTnc |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3672 | "C:\Program Files\Internet Explorer\iexplore.exe" "edge-mobile-static.azureedge.net" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3972 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3672 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
21 656
Read events
21 530
Write events
91
Delete events
35
Modification events
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31091352 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31091352 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
0
Suspicious files
3
Text files
10
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\UxFxErrorCss_8097D4DBB3B4874308CB3816C1762BED98637360[1].css | text | |
MD5:88E1336D359F8FC204863E2230FDB266 | SHA256:F702775B4C9ADC1E8FA61169A437B6F22556B44B9F2A975464E02432B547C13B | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:BF386101CCB01AD1C2AA35EF8677BEC3 | SHA256:8AC4C9EE597F2D889B9CBF6B785E3CF58A388FDFB8B4943CCEACEE7417B46D2E | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:488DA5E5066F15F3BF4F991CB3670C95 | SHA256:9BD3D879EB1EB38911429CFB4B333C910F77FCB3D224538AB3E142250DA75DBA | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\ErrorBackground[1].png | image | |
MD5:0F115D2C19D9C485EB8FF39AAC44AFE5 | SHA256:A6CBAA934A88444E751973109C0675982883A2768656FB17A292F2F557E5A96C | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\UxFxStableCssWesternEuropean_6724ABFCA058F28804A76FD40AD14C9D7A6031D9[1].css | text | |
MD5:B3FACF280AD7C12124415DFDC290BC96 | SHA256:FB384CDEB37D9E15FF825977806172D13F5FC9D5289D07DC81C5407C08B82F2B | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:1C0B4382F00F4500F3C8CBAEF1101D44 | SHA256:4E33E60DD3F51F48F71B6C8CFB25507833FFD5B1D2A7C842D7FCF0733731ECAA | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:5B6D81F77F891BE9EFA742BBD2509A2F | SHA256:6AE961632A3F8F4055909B466A1481CFA58F224A41F2D9941F51DC49B65379E9 | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\ver6D7A.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
24
DNS requests
16
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3972 | iexplore.exe | GET | 404 | 13.107.246.45:80 | http://edge-mobile-static.azureedge.net/ | unknown | html | 1.05 Kb | unknown |
3972 | iexplore.exe | GET | 304 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?86b4b67e50f1d6bf | unknown | — | — | unknown |
3972 | iexplore.exe | GET | 304 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?dfd57d13c28afd30 | unknown | — | — | unknown |
3972 | iexplore.exe | GET | 304 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?09a5b2e51d609355 | unknown | — | — | unknown |
3972 | iexplore.exe | GET | 304 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1c38e09e3428bf6c | unknown | — | — | unknown |
3972 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | binary | 471 b | unknown |
3672 | iexplore.exe | GET | 304 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?96c8eb5dfc595a04 | unknown | — | — | unknown |
3672 | iexplore.exe | GET | 304 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?70d85e3b0e586cab | unknown | — | — | unknown |
3672 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
3672 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3972 | iexplore.exe | 13.107.246.45:80 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3972 | iexplore.exe | 13.107.213.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3972 | iexplore.exe | 184.24.77.202:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3972 | iexplore.exe | 184.24.77.194:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3972 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3672 | iexplore.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3672 | iexplore.exe | 184.24.77.202:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
edge-mobile-static.azureedge.net |
| unknown |
azurefrontdoorpages.azureedge.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3972 | iexplore.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspicious message detected (saved from) |