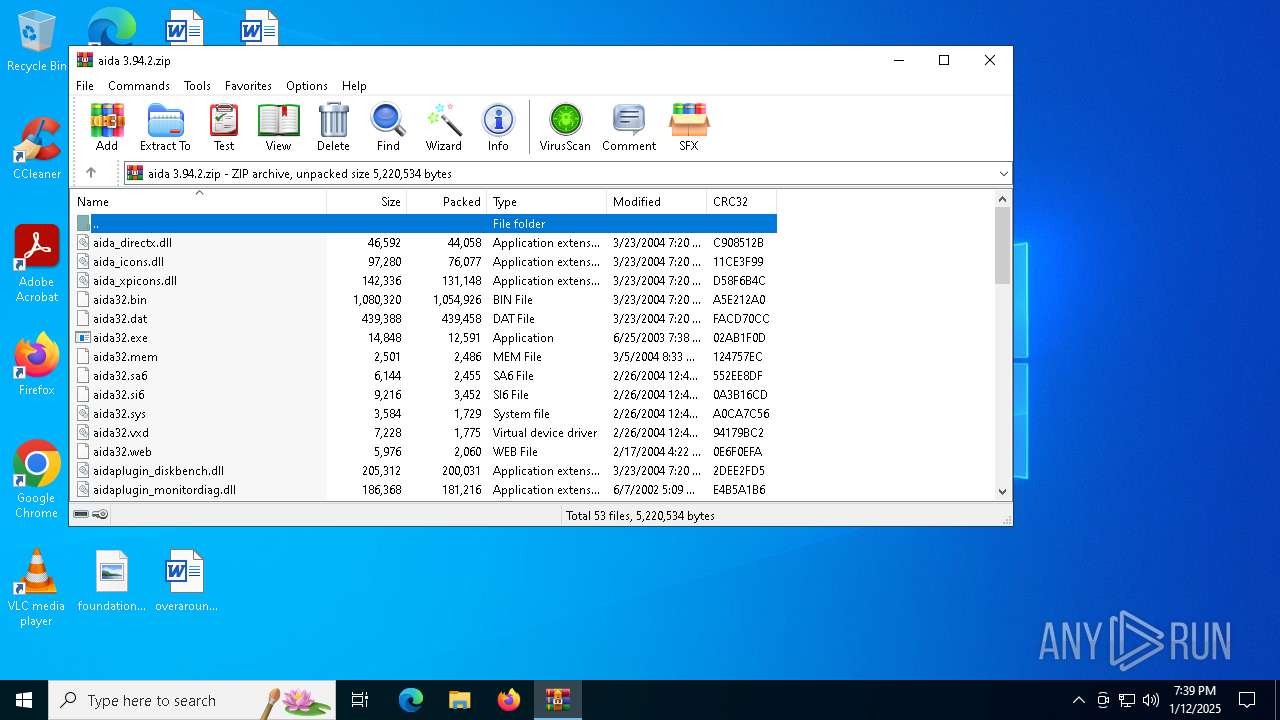
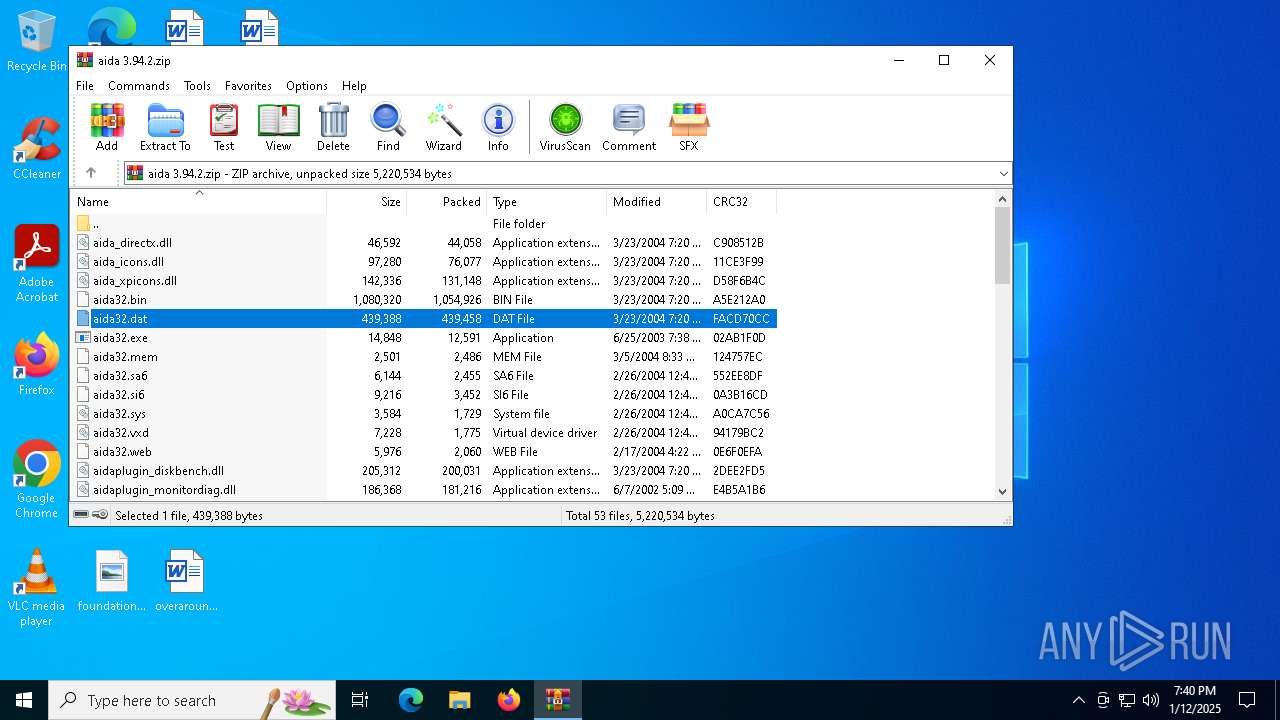
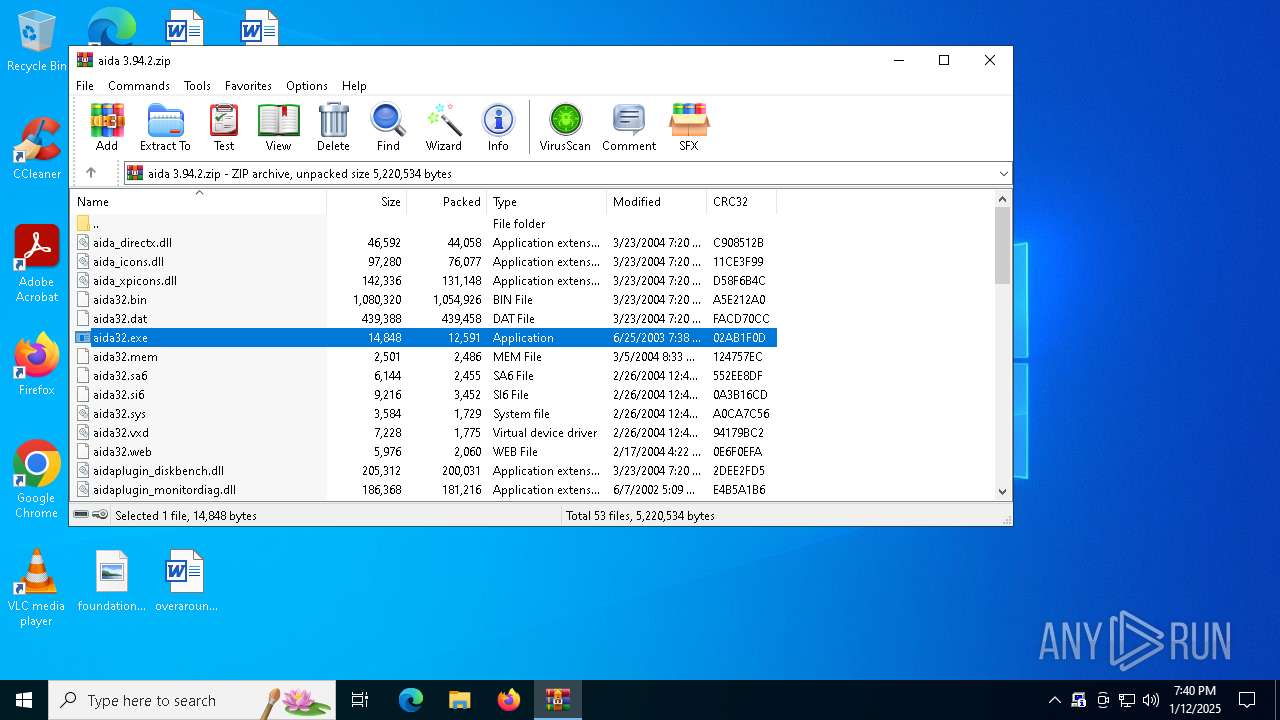
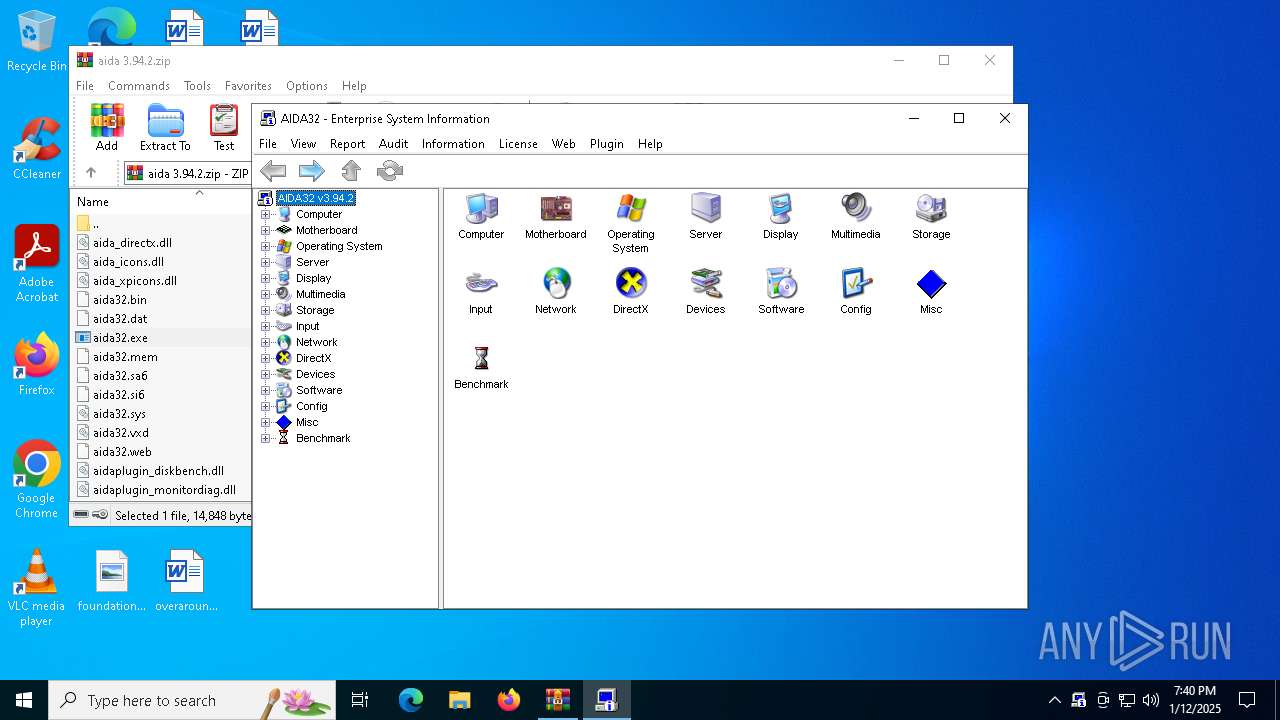
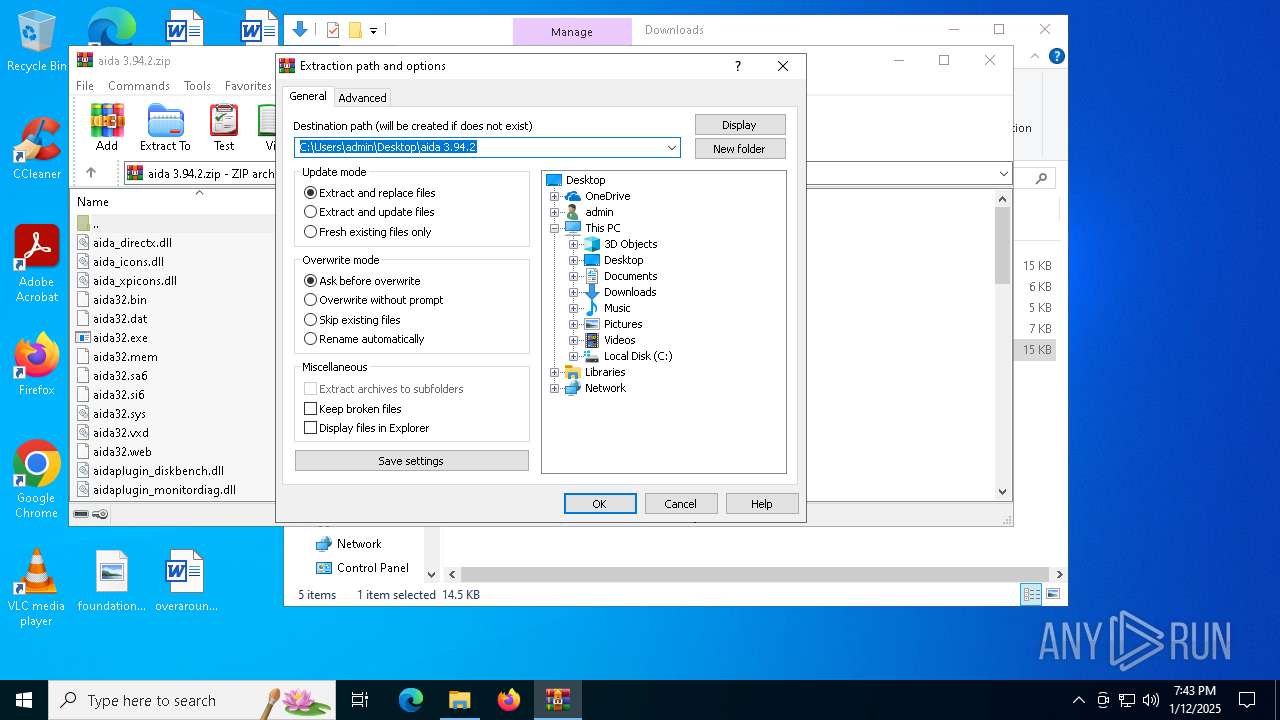
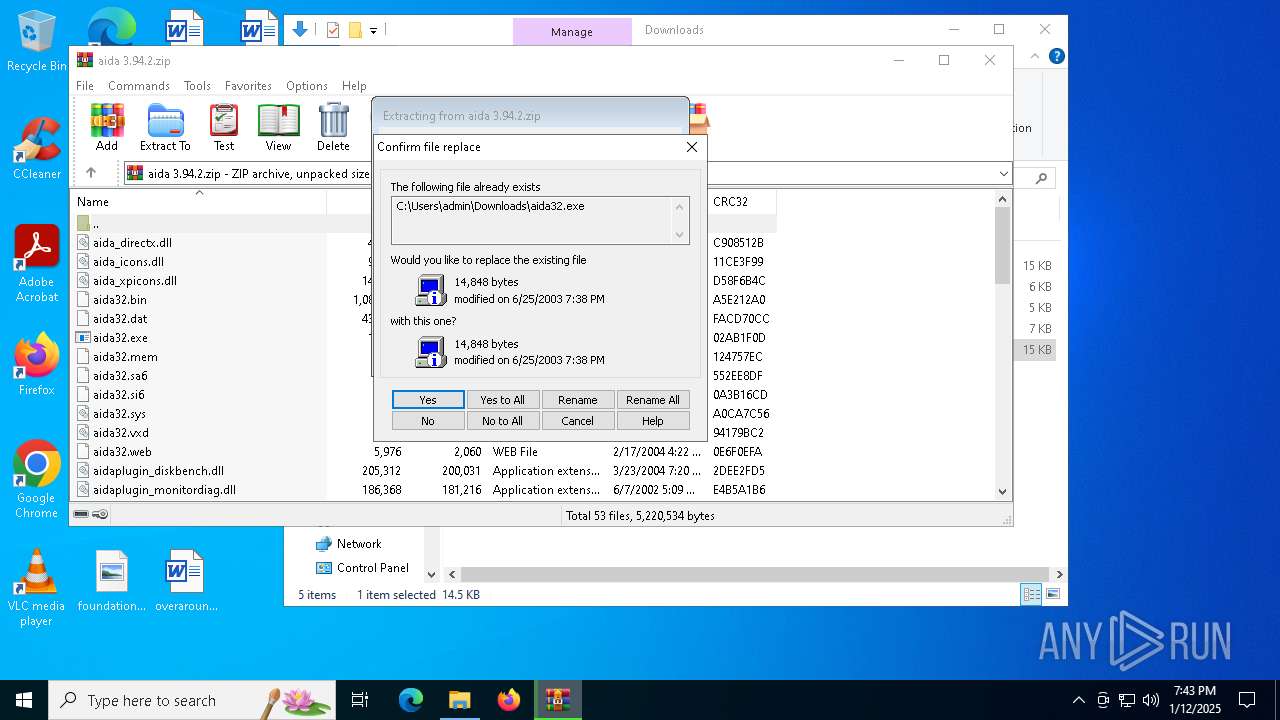
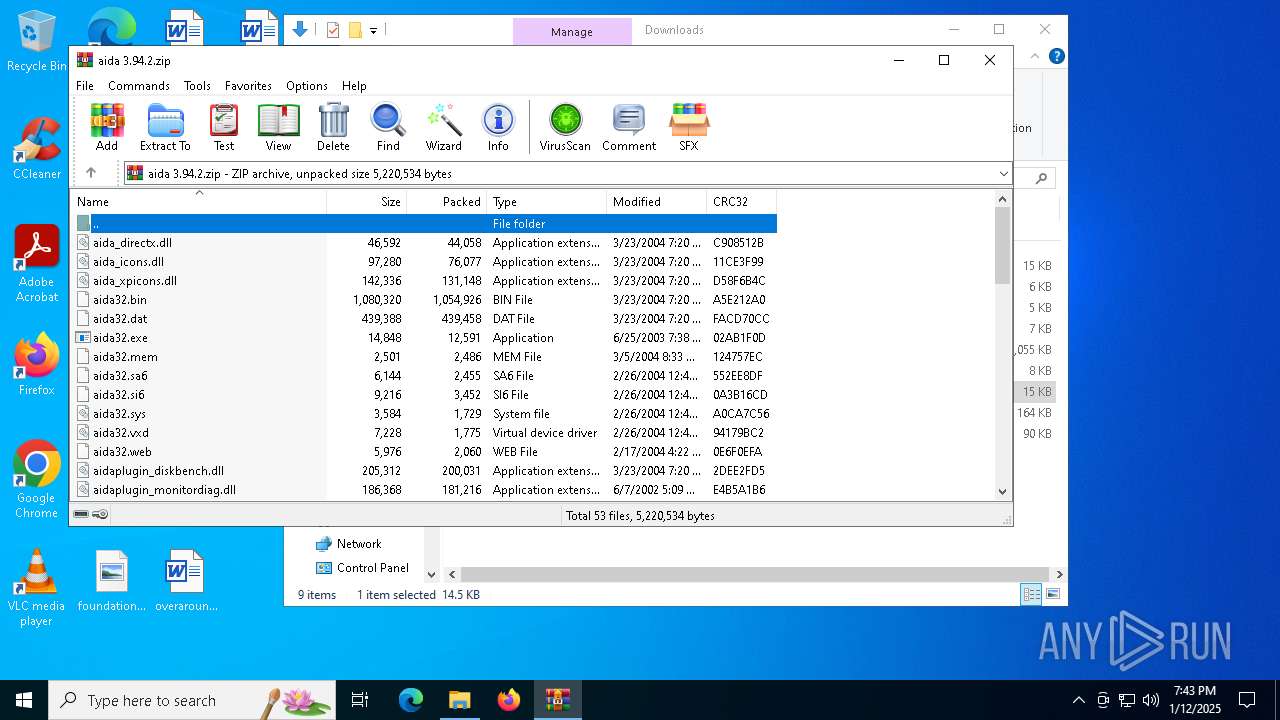
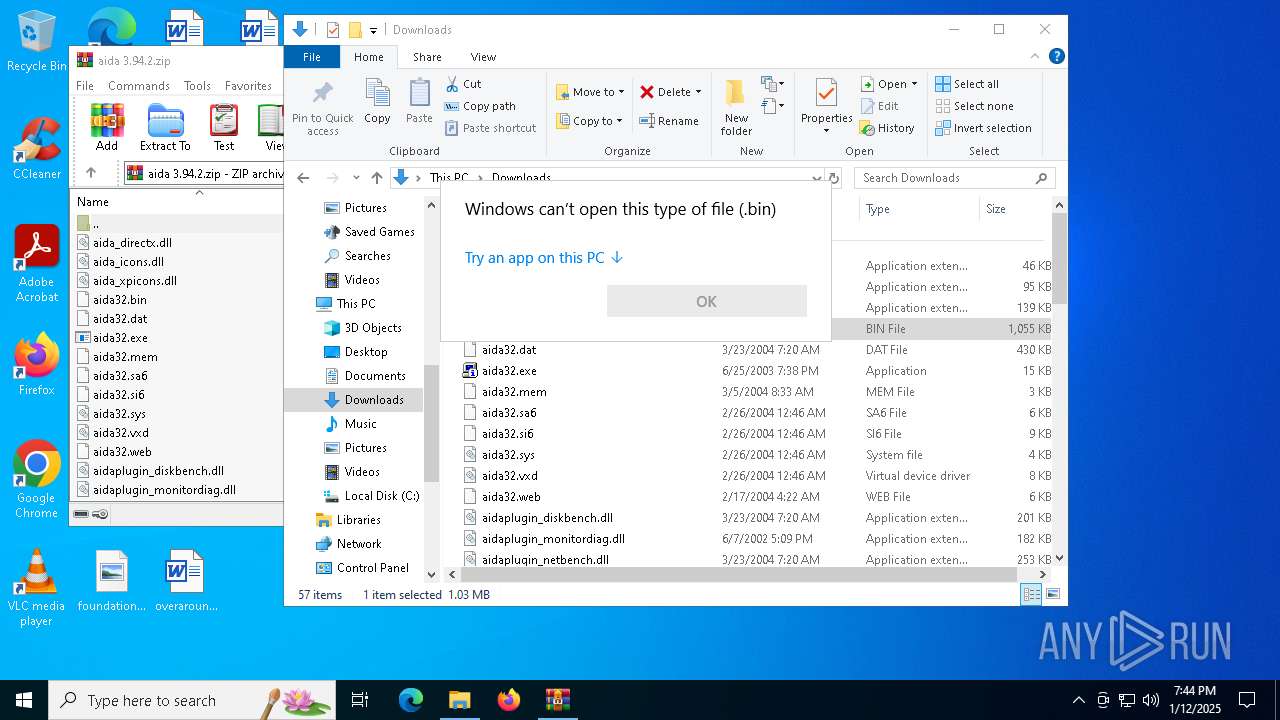
| File name: | aida 3.94.2.zip |
| Full analysis: | https://app.any.run/tasks/21bd44c8-743c-4abb-8b2c-d687c658d7e6 |
| Verdict: | Malicious activity |
| Analysis date: | January 12, 2025, 19:39:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6D5A81B16FE1A15BD72547AD986EEE67 |
| SHA1: | 17BC06C4A880C9B0F3507B5B60F0278E91AE039D |
| SHA256: | 08E5880862F74D45D03DBB598629893C40C4498DE4BD23502F7DAC1D4F9FA9F9 |
| SSDEEP: | 98304:wpEicu2svXUj0r5luFlN0xj/P3rYcOzuR815I1/uFH5ZNmWOC5fpPLRgjlhy3Yj+:1YWWI |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5400)
Executable content was dropped or overwritten
- aida32.bin (PID: 6712)
- aida32.bin (PID: 5000)
Starts application with an unusual extension
- aida32.exe (PID: 6696)
- aida32.exe (PID: 936)
There is functionality for VM detection VirtualBox (YARA)
- aida32.bin (PID: 6712)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 5400)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 5400)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6572)
- OpenWith.exe (PID: 7128)
- OpenWith.exe (PID: 4716)
The sample compiled with english language support
- WinRAR.exe (PID: 5400)
Checks supported languages
- aida32.bin (PID: 6712)
- aida32.exe (PID: 6696)
- aida32.exe (PID: 7048)
- aida32.exe (PID: 7016)
- aida32.bin (PID: 5000)
- aida32.exe (PID: 936)
Reads the computer name
- aida32.bin (PID: 6712)
- aida32.bin (PID: 5000)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5400)
Create files in a temporary directory
- aida32.bin (PID: 6712)
- aida32.bin (PID: 5000)
Reads CPU info
- aida32.bin (PID: 6712)
- aida32.bin (PID: 5000)
UPX packer has been detected
- aida32.bin (PID: 6712)
Manual execution by a user
- aida32.exe (PID: 7016)
- aida32.exe (PID: 7048)
- aida32.exe (PID: 936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2003:03:28 00:00:00 |
| ZipCRC: | 0x2ee9a436 |
| ZipCompressedSize: | 13353 |
| ZipUncompressedSize: | 167936 |
| ZipFileName: | DB - Access.mdb |
Total processes
136
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 936 | "C:\Users\admin\Downloads\aida32.exe" | C:\Users\admin\Downloads\aida32.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4716 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5000 | "C:\Users\admin\Downloads\aida32.exe" | C:\Users\admin\Downloads\aida32.bin | aida32.exe | ||||||||||||
User: admin Company: Tamas Miklos Integrity Level: MEDIUM Description: AIDA32 - Worldwide SysInfo Tool Version: 3.94.2 Modules
| |||||||||||||||
| 5400 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\aida 3.94.2.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6572 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6696 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5400.12136\aida32.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5400.12136\aida32.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6712 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5400.12136\aida32.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5400.12136\aida32.bin | aida32.exe | ||||||||||||
User: admin Company: Tamas Miklos Integrity Level: MEDIUM Description: AIDA32 - Worldwide SysInfo Tool Exit code: 0 Version: 3.94.2 Modules
| |||||||||||||||
| 6972 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7016 | "C:\Users\admin\Downloads\aida32.exe" | C:\Users\admin\Downloads\aida32.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7048 | "C:\Users\admin\Downloads\aida32.exe" | C:\Users\admin\Downloads\aida32.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
4 779
Read events
4 753
Write events
13
Delete events
13
Modification events
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\aida 3.94.2.zip | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
29
Suspicious files
8
Text files
73
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5400.12136\aida32.bin | executable | |
MD5:650D7EC24F7B687AF36331AE5DAAB794 | SHA256:6CAA021FA8DBFBAFC2D51889B3401E26CE3FE53C1E11C687FD8295742857349D | |||
| 5400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5400.12136\DB - Access.mdb | mdb | |
MD5:F86C5C3A95FEE8CEAA65CBE71193D7B8 | SHA256:A240F4F0BAEEE1570AD938891B728E264D5DB0DDEA67EC1B21C0F61A5728DED7 | |||
| 5400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5400.12136\DB - Access97.mdb | mdb | |
MD5:779E0F70E9A81199282F16DC768559B1 | SHA256:448016664220F30B110EE29252A14C30CD5103FFBC77D1BEFD08CD633DA44FD2 | |||
| 5400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5400.12136\aida32.vxd | executable | |
MD5:9AD3F735DC0B9BEA26849D2F7D93573D | SHA256:5C9EBA34CC2E4D9EB5089F790C225ADE1354E18E3E8C3C213D642ADE9044685F | |||
| 5400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa5400.11177\aida32.dat | binary | |
MD5:5A65FA16CE2AE05A6F5FF62FD423010B | SHA256:5D1D50BD4CCB4F9B493BE56A43078D05871862E370981C30B82001D258BF0FC6 | |||
| 5400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5400.12136\aidaplugin_monitordiag.dll | executable | |
MD5:7ED837C18362B0BA1390158A11CFEBDC | SHA256:07B8BD6B5A091F8F90B4A5EF641E4011CBCE40E916FF068B90C5106E0130926B | |||
| 5400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5400.12136\aidaplugin_diskbench.dll | executable | |
MD5:AA4ACD952F75346D51D86A7410A7DE8C | SHA256:169505E1914DF8A7335B794E28F6AA893C8DAAD3B62E7CA63AEA9753B114853D | |||
| 5400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5400.12136\aida32.dat | binary | |
MD5:5A65FA16CE2AE05A6F5FF62FD423010B | SHA256:5D1D50BD4CCB4F9B493BE56A43078D05871862E370981C30B82001D258BF0FC6 | |||
| 5400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5400.12136\aida_directx.dll | executable | |
MD5:BCBD7B004BA994CB8395605B53D3D10C | SHA256:3E74FFBFA8773DC316A0C80AA5AF589A0F687268455E56803CA698E95DCE7FE4 | |||
| 5400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5400.12136\aida32.sys | executable | |
MD5:8E8D4D4A94495CB2DEDA843F60534E98 | SHA256:B17FC6D38BEFCCB5DFE9D921679E89C9C8DA94D49394CD37563EADEF62EDEA14 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
50
DNS requests
13
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.176:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 104.126.37.178:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.153:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
3976 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3884 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4684 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4684 | SIHClient.exe | 20.242.39.171:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
171.39.242.20.in-addr.arpa |
| unknown |
d.8.0.a.e.e.f.b.0.0.0.0.0.0.0.0.5.0.0.0.0.0.8.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |
login.live.com |
| whitelisted |