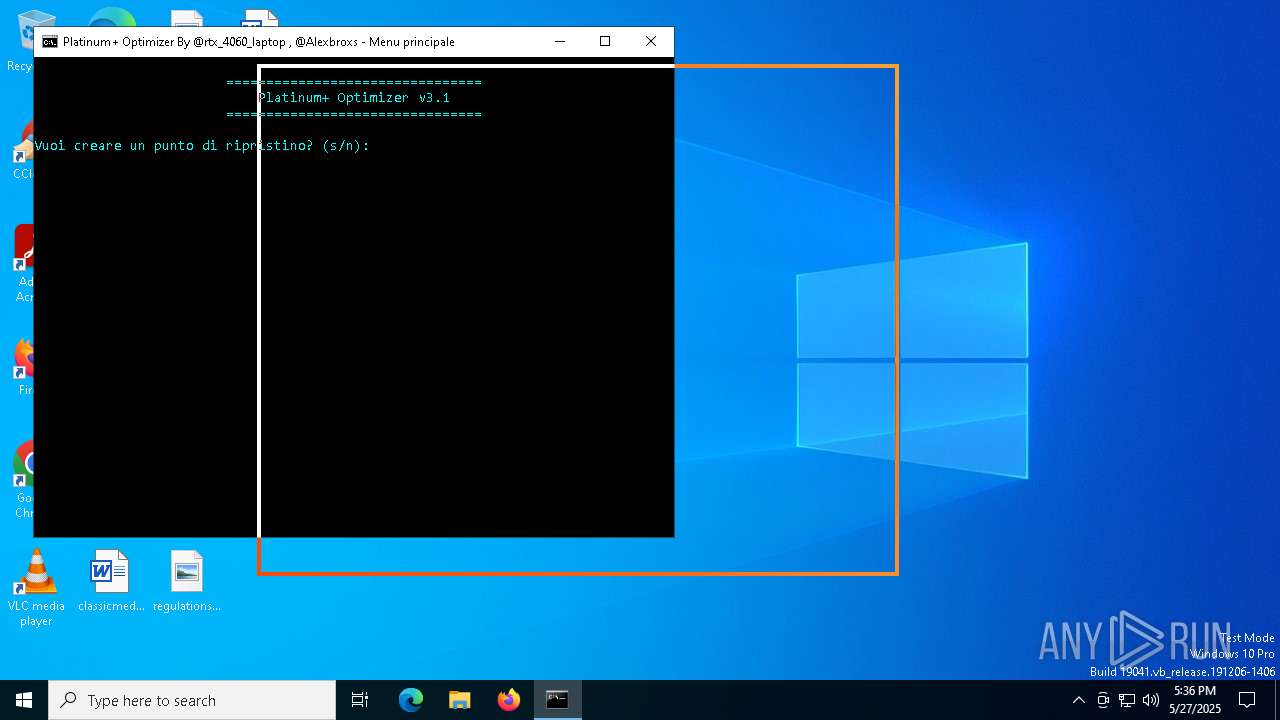
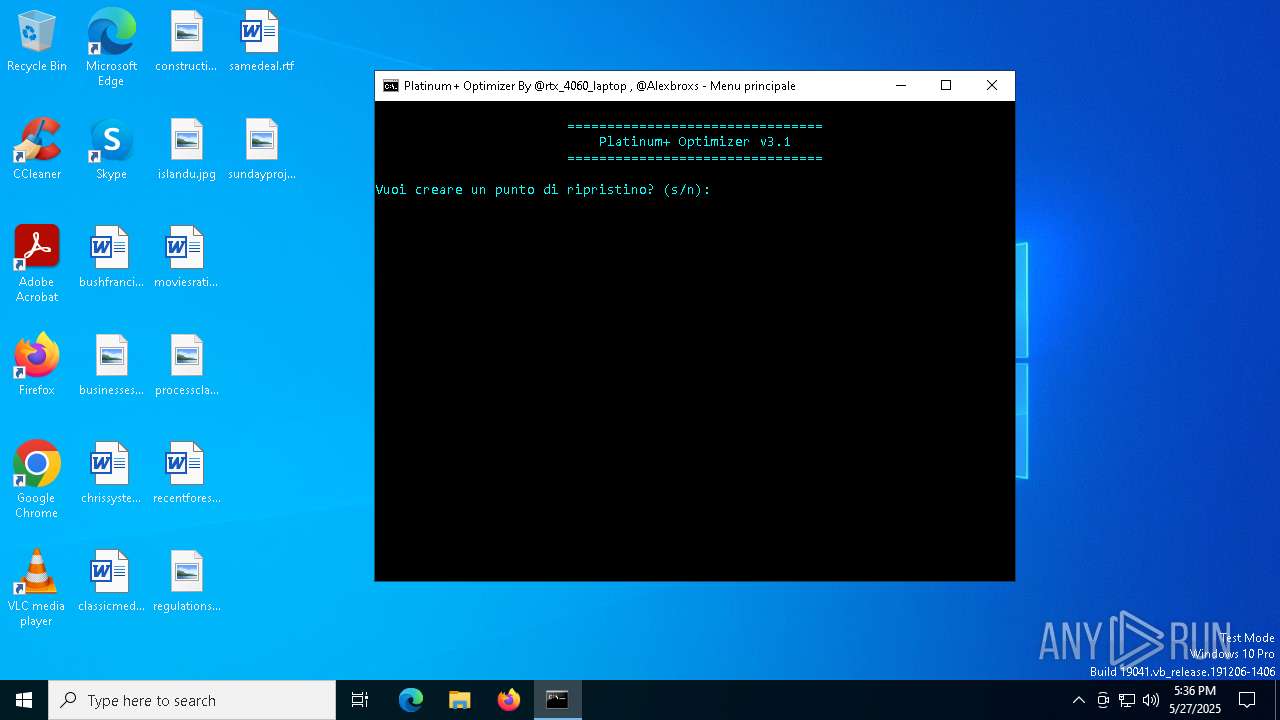
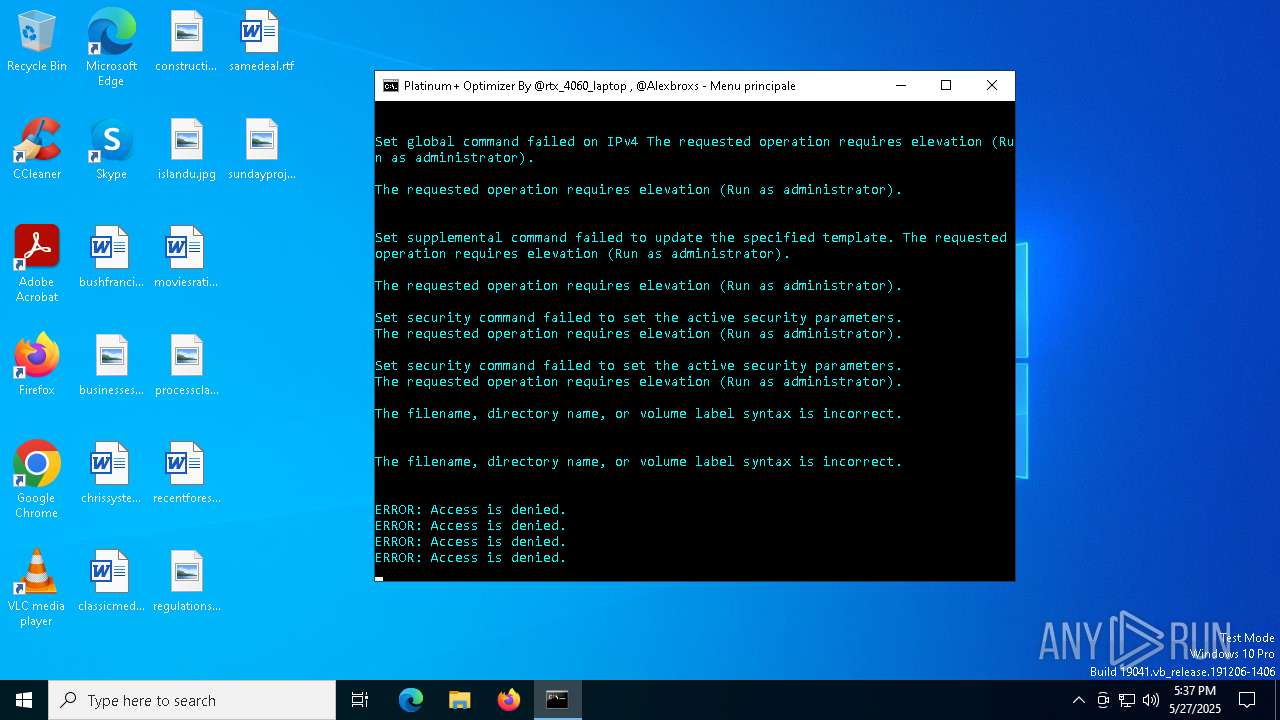
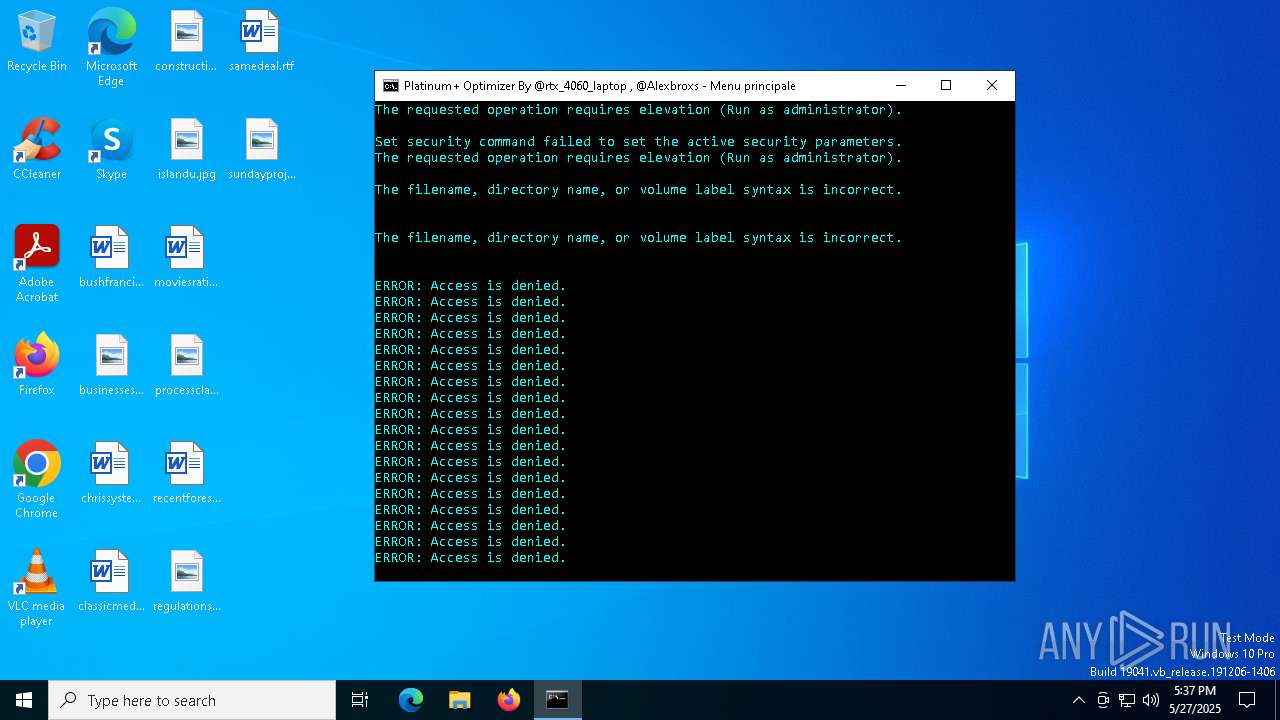
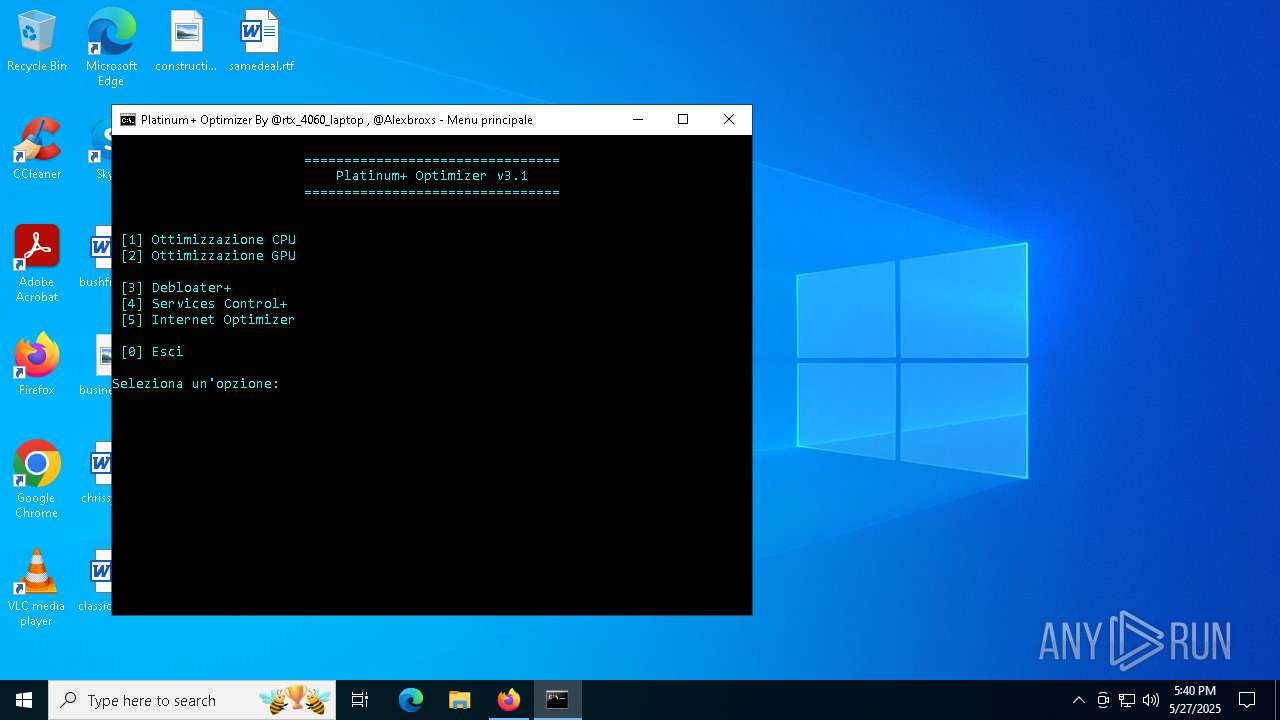
| File name: | Platinum+ Optimizer v3.1.bat |
| Full analysis: | https://app.any.run/tasks/69fa9955-552b-4b4f-90db-b150a8c588b3 |
| Verdict: | Malicious activity |
| Analysis date: | May 27, 2025, 17:36:37 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-16, little-endian text, with very long lines (32767), with no line terminators |
| MD5: | BE2374AD3006DF2031908DA1F725019E |
| SHA1: | F829248202A26D29F1B76FE2E9548638820D7AF8 |
| SHA256: | 08C019D8D0BEA8E26B000DF3EE7FC0A8E032E39C04BF61DA4ED2CDB08B097102 |
| SSDEEP: | 3072:sAXFuXJFRiEpsw/5RwymPBFcB45IKtKcHBzO:twsO0FyohzO |
MALICIOUS
No malicious indicators.SUSPICIOUS
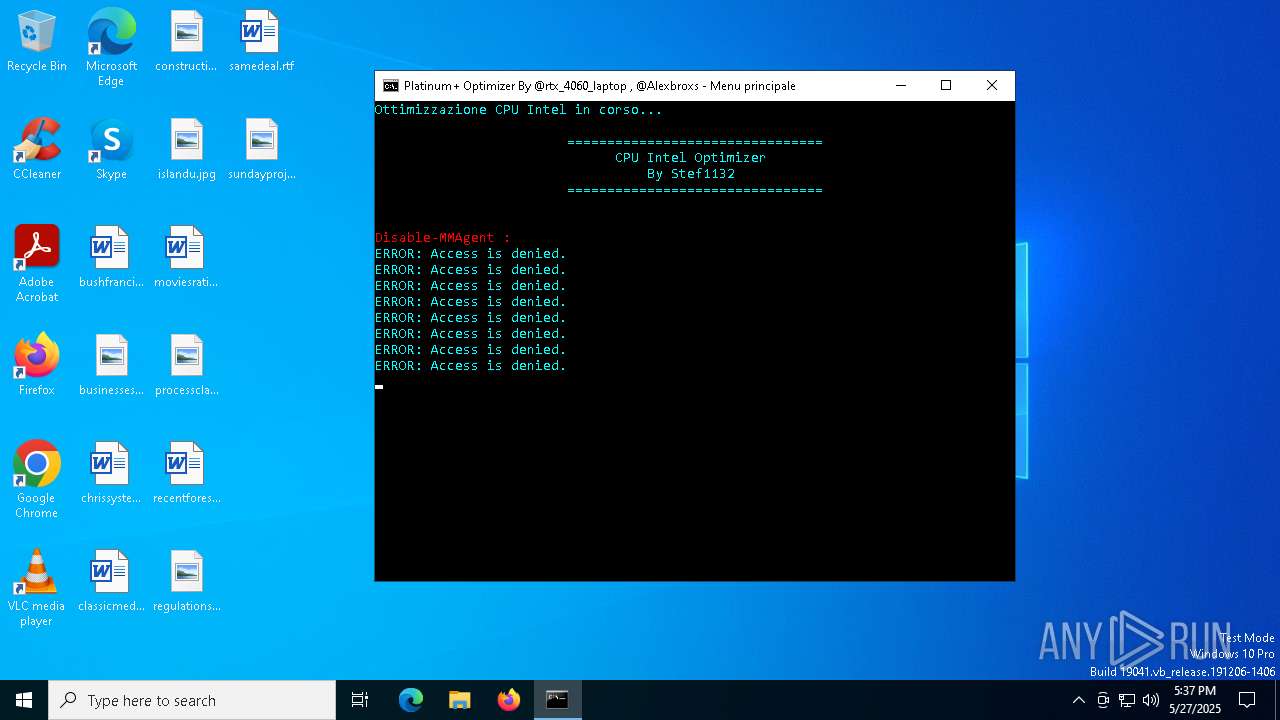
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4880)
- cmd.exe (PID: 3892)
- cmd.exe (PID: 5188)
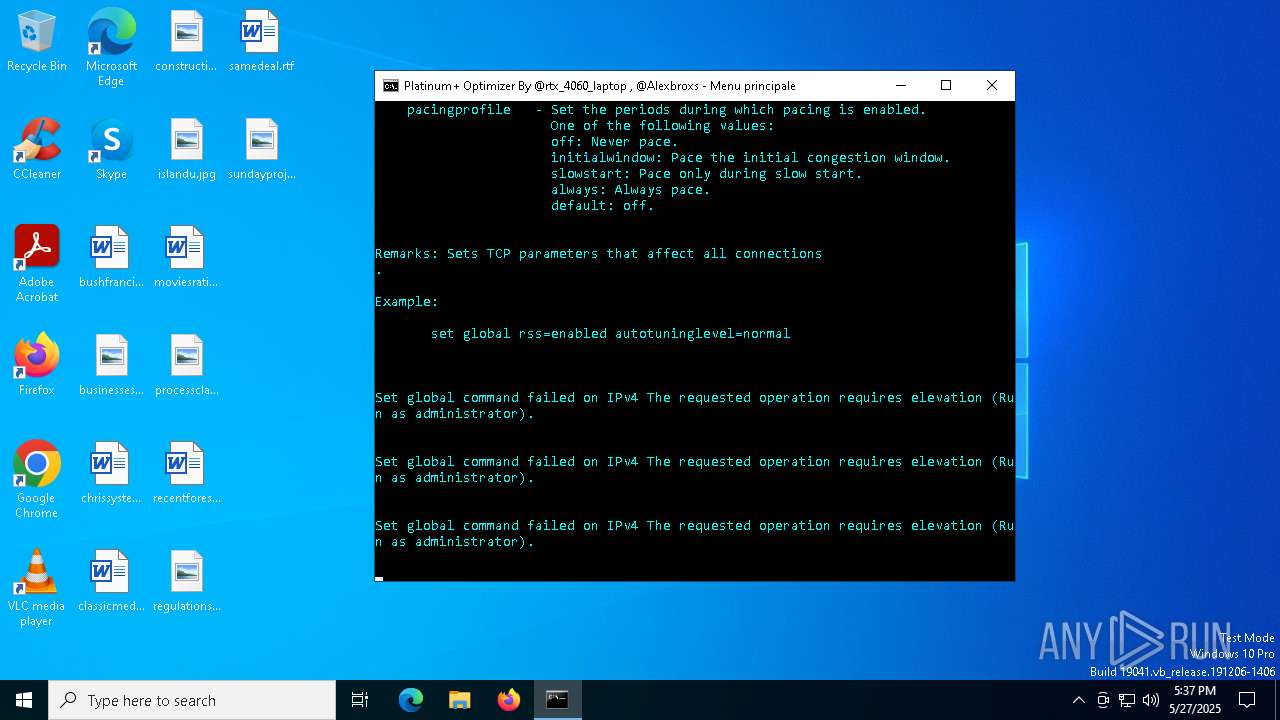
Suspicious use of NETSH.EXE
- cmd.exe (PID: 4880)
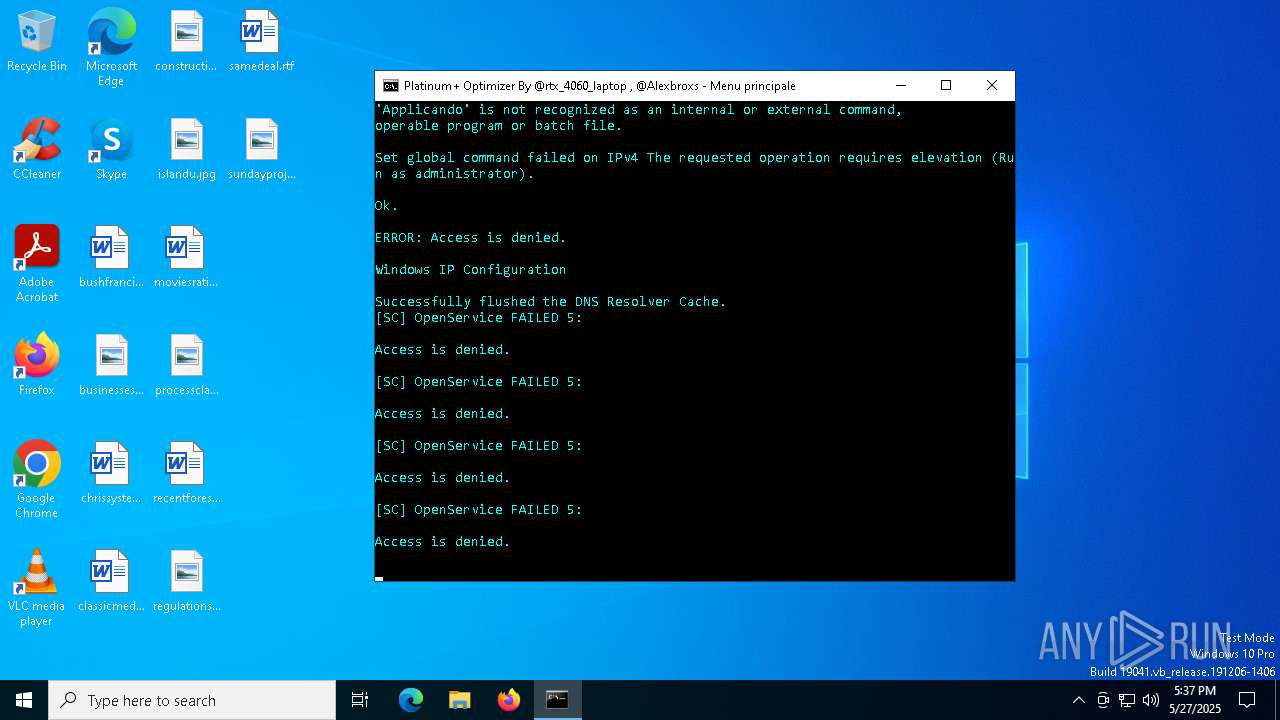
Starts SC.EXE for service management
- cmd.exe (PID: 4880)
- cmd.exe (PID: 3892)
- cmd.exe (PID: 5188)
Stops a currently running service
- sc.exe (PID: 7180)
- sc.exe (PID: 7272)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 4880)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 4880)
Windows service management via SC.EXE
- sc.exe (PID: 7212)
- sc.exe (PID: 7196)
- sc.exe (PID: 5632)
- sc.exe (PID: 7096)
- sc.exe (PID: 6764)
- sc.exe (PID: 3052)
- sc.exe (PID: 1188)
- sc.exe (PID: 6640)
- sc.exe (PID: 1668)
- sc.exe (PID: 2616)
- sc.exe (PID: 2196)
- sc.exe (PID: 7036)
- sc.exe (PID: 3952)
- sc.exe (PID: 876)
- sc.exe (PID: 7076)
- sc.exe (PID: 4444)
- sc.exe (PID: 2312)
- sc.exe (PID: 6556)
- sc.exe (PID: 6568)
- sc.exe (PID: 1876)
- sc.exe (PID: 4488)
- sc.exe (PID: 4940)
- sc.exe (PID: 6976)
- sc.exe (PID: 4340)
- sc.exe (PID: 5688)
- sc.exe (PID: 6612)
- sc.exe (PID: 6364)
- sc.exe (PID: 5360)
- sc.exe (PID: 6356)
- sc.exe (PID: 6100)
- sc.exe (PID: 7096)
- sc.exe (PID: 5632)
- sc.exe (PID: 6568)
- sc.exe (PID: 4236)
- sc.exe (PID: 3028)
- sc.exe (PID: 1540)
- sc.exe (PID: 6764)
- sc.exe (PID: 3052)
- sc.exe (PID: 7676)
- sc.exe (PID: 1876)
- sc.exe (PID: 3824)
- sc.exe (PID: 7696)
- sc.exe (PID: 7716)
- sc.exe (PID: 7736)
- sc.exe (PID: 7756)
- sc.exe (PID: 7776)
- sc.exe (PID: 7796)
- sc.exe (PID: 7936)
- sc.exe (PID: 7916)
- sc.exe (PID: 7956)
- sc.exe (PID: 8136)
- sc.exe (PID: 7976)
- sc.exe (PID: 8016)
- sc.exe (PID: 8096)
- sc.exe (PID: 7996)
- sc.exe (PID: 8056)
- sc.exe (PID: 8036)
- sc.exe (PID: 8076)
- sc.exe (PID: 8116)
- sc.exe (PID: 8160)
- sc.exe (PID: 7816)
- sc.exe (PID: 7836)
- sc.exe (PID: 7876)
- sc.exe (PID: 7856)
- sc.exe (PID: 7896)
- sc.exe (PID: 7380)
- sc.exe (PID: 7244)
- sc.exe (PID: 6224)
- sc.exe (PID: 6076)
- sc.exe (PID: 3008)
- sc.exe (PID: 7172)
- sc.exe (PID: 2484)
- sc.exe (PID: 7444)
- sc.exe (PID: 7556)
- sc.exe (PID: 8180)
- sc.exe (PID: 7316)
- sc.exe (PID: 1644)
- sc.exe (PID: 7264)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4880)
- cmd.exe (PID: 8092)
- cmd.exe (PID: 7780)
- cmd.exe (PID: 3892)
- cmd.exe (PID: 5188)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4880)
Application launched itself
- cmd.exe (PID: 4880)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 8092)
- cmd.exe (PID: 7780)
The process checks if it is being run in the virtual environment
- reg.exe (PID: 2340)
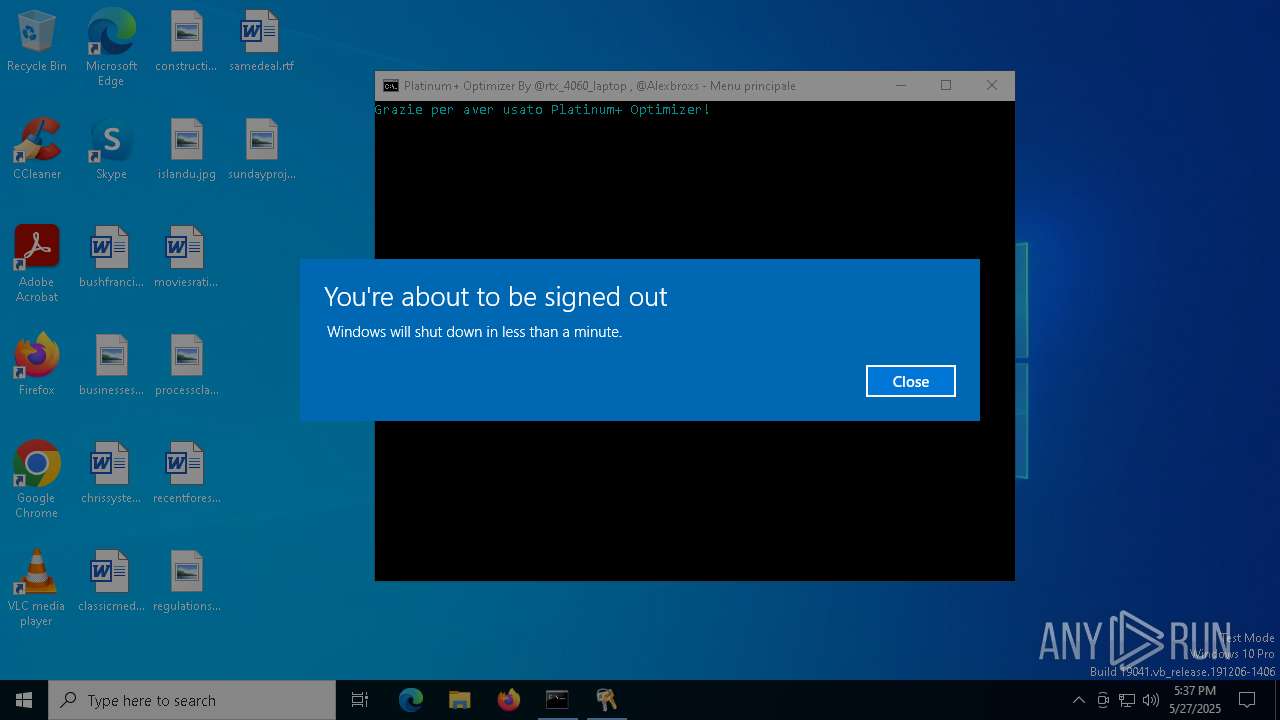
The system shut down or reboot
- cmd.exe (PID: 4880)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4116)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4880)
INFO
Starts MODE.COM to configure console settings
- mode.com (PID: 6184)
- mode.com (PID: 1476)
- mode.com (PID: 4176)
- mode.com (PID: 7788)
- mode.com (PID: 5180)
- mode.com (PID: 920)
Checks supported languages
- mode.com (PID: 6184)
- mode.com (PID: 7788)
Disables trace logs
- netsh.exe (PID: 1056)
- netsh.exe (PID: 5008)
- netsh.exe (PID: 6048)
- netsh.exe (PID: 7260)
- netsh.exe (PID: 7568)
- netsh.exe (PID: 7696)
- netsh.exe (PID: 7692)
- netsh.exe (PID: 7712)
- netsh.exe (PID: 3956)
- netsh.exe (PID: 7532)
- netsh.exe (PID: 7472)
- netsh.exe (PID: 7768)
- netsh.exe (PID: 7600)
- netsh.exe (PID: 7776)
- netsh.exe (PID: 7800)
- netsh.exe (PID: 2908)
- netsh.exe (PID: 2420)
- netsh.exe (PID: 736)
- netsh.exe (PID: 2800)
- netsh.exe (PID: 644)
- netsh.exe (PID: 5384)
- netsh.exe (PID: 7920)
- netsh.exe (PID: 8052)
- netsh.exe (PID: 7904)
- netsh.exe (PID: 1012)
Reads security settings of Internet Explorer
- netsh.exe (PID: 4920)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7868)
Manual execution by a user
- firefox.exe (PID: 6564)
- cmd.exe (PID: 3892)
- cmd.exe (PID: 5188)
Reads the computer name
- PLUGScheduler.exe (PID: 4116)
Creates files in the program directory
- PLUGScheduler.exe (PID: 4116)
Application launched itself
- firefox.exe (PID: 6564)
- firefox.exe (PID: 6676)
Attempting to use instant messaging service
- firefox.exe (PID: 6676)
Reads the software policy settings
- slui.exe (PID: 7324)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
463
Monitored processes
192
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | netsh int tcp set security mpp=disabled | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | netsh int tcp set supplemental template=custom icw=10 | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | reg.exe add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{d950ca8d-448e-4ca2-89de-a65a1ac2b2a6} /v "TcpAckFrequency" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | SC CONFIG WdiServiceHost start= disabled | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | mode con: cols=80 lines=30 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | reg.exe add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{9622632d-f513-40c5-85d0-96380709710f} /v "TCPNoDelay" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 976 | reg.exe add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{d950ca8d-448e-4ca2-89de-a65a1ac2b2a6} /v "TcpDelAckTicks" /t REG_DWORD /d "0" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | netsh int udp set global uro=enabled | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | netsh int tcp set global rss=disabled | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | SC CONFIG EFS start= disabled | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 561
Read events
30 559
Write events
2
Delete events
0
Modification events
| (PID) Process: | (6676) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6292) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore |
| Operation: | write | Name: | SystemRestorePointCreationFrequency |
Value: 0 | |||
Executable files
0
Suspicious files
134
Text files
23
Unknown types
68
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7868 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:CECB1929E8A154B90CC6B99403843D76 | SHA256:0ACA82F51575C5C5A8B7599D825ECC9865A95B961518EFFC6EF901A084BA60CA | |||
| 4116 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.042.etl | etl | |
MD5:C1F87CF12DD702D2185E703BA004D216 | SHA256:9D993487866C9538DC19F281A6346E1796E7478C7C164D61437AF6E698C66125 | |||
| 4116 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.049.etl | etl | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
| 4116 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.036.etl | etl | |
MD5:A477FE56C25FCDB850EA1AAB8D01B5C2 | SHA256:5C85DC2B41C2D076D6B2653C0BA5F5681ADABFEBDA8883C704E625EB9338F505 | |||
| 4116 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.047.etl | etl | |
MD5:FED961067F664B5381B65A534B7AB728 | SHA256:652F31A8284AE812D1D9D24192BC800976BF74C240591C6AC443A28C4709FB7C | |||
| 4116 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.041.etl | etl | |
MD5:09359EE89B0634478ADFF73CDA7BFB12 | SHA256:4D800AC7C55960B107C9D3E40F63130407835E69DF4F5C558C500FC0BD20D8ED | |||
| 4116 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.044.etl | etl | |
MD5:B53B2070E686FFB1FBC8B06994E7C8D7 | SHA256:A3ABD06F4E40CB700B1908AB6BCD2E27455E13EF076E0BF2345BB2FA369EF802 | |||
| 7868 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ffjlht50.fbc.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4116 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.048.etl | etl | |
MD5:A23907B6FDD47DCABFDFD7CF2FCD7671 | SHA256:0C9C33FE9E984A2E5A70EBA51F36B9929A86199E424AF2F8080E1267B87DC970 | |||
| 4116 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.050.etl | etl | |
MD5:C8834D365FAE073DEDE1F1620454CE71 | SHA256:C6DD793EEE1D5551CA507A3C5BFFECA82DD3E29C63C2C6DD218A7D4BFB37046B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
115
DNS requests
135
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1196 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1196 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5340 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6676 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6676 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6404 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6676 | firefox.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
6676 | firefox.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |