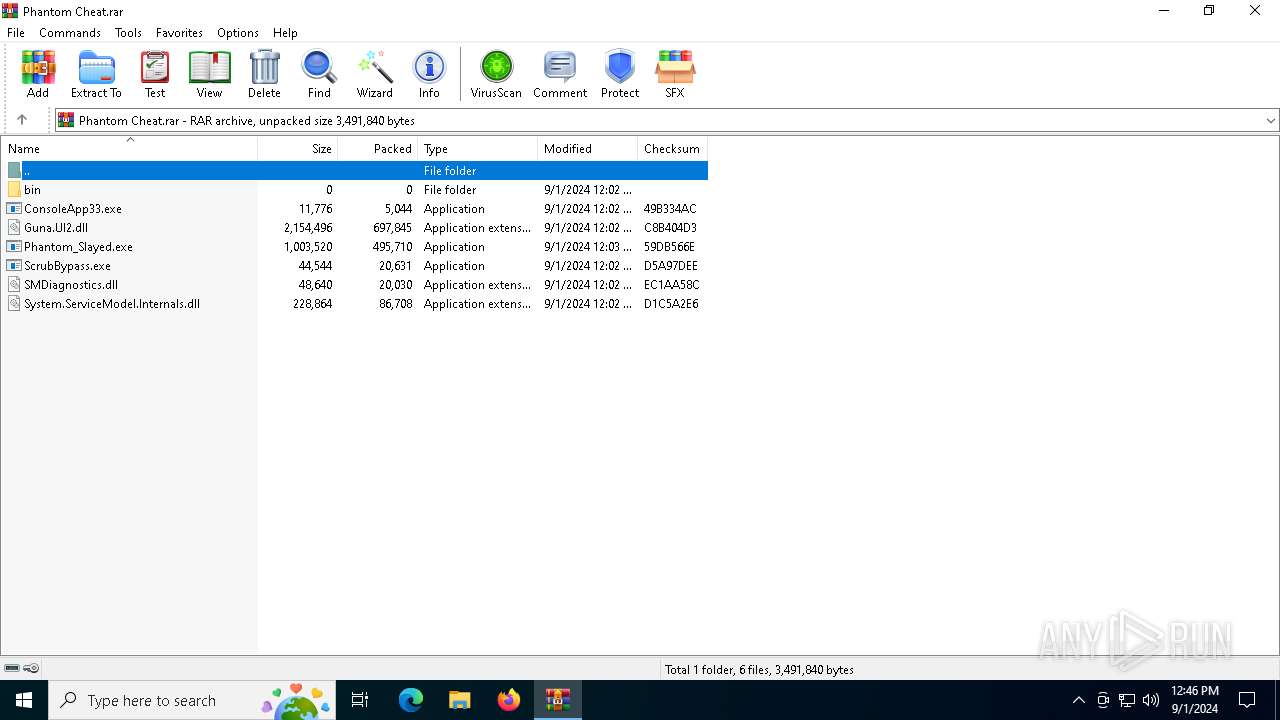
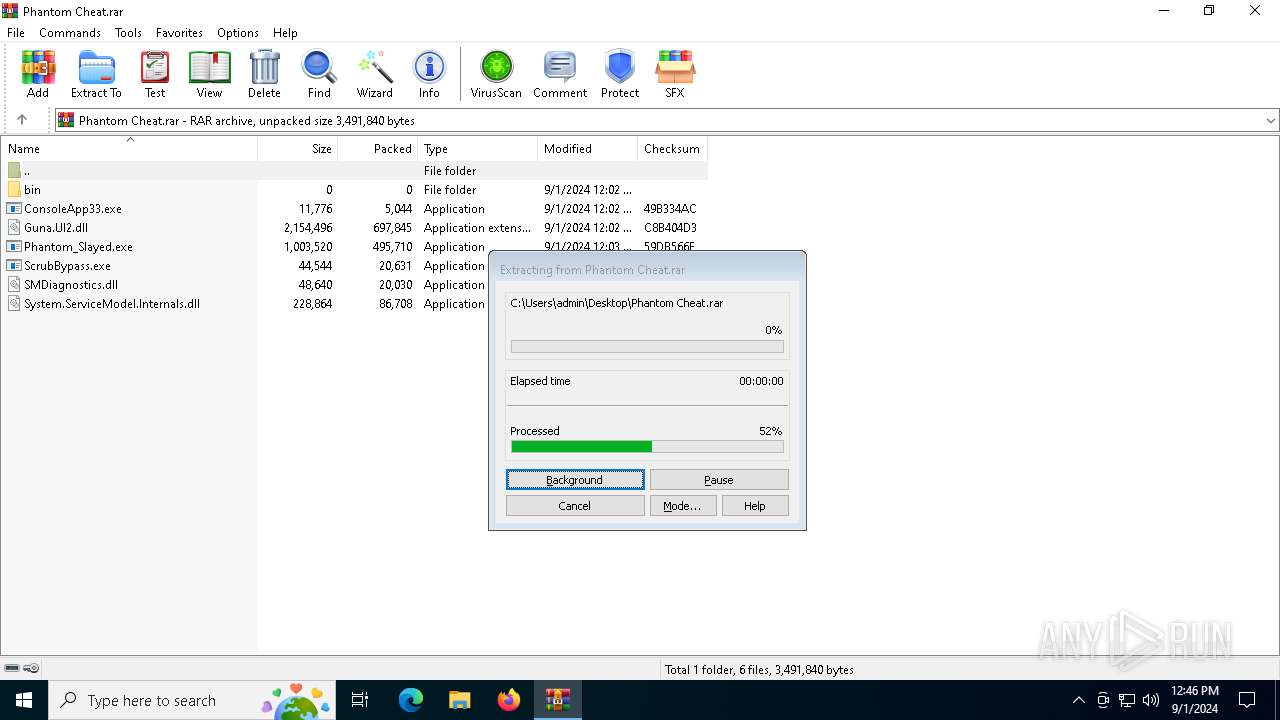
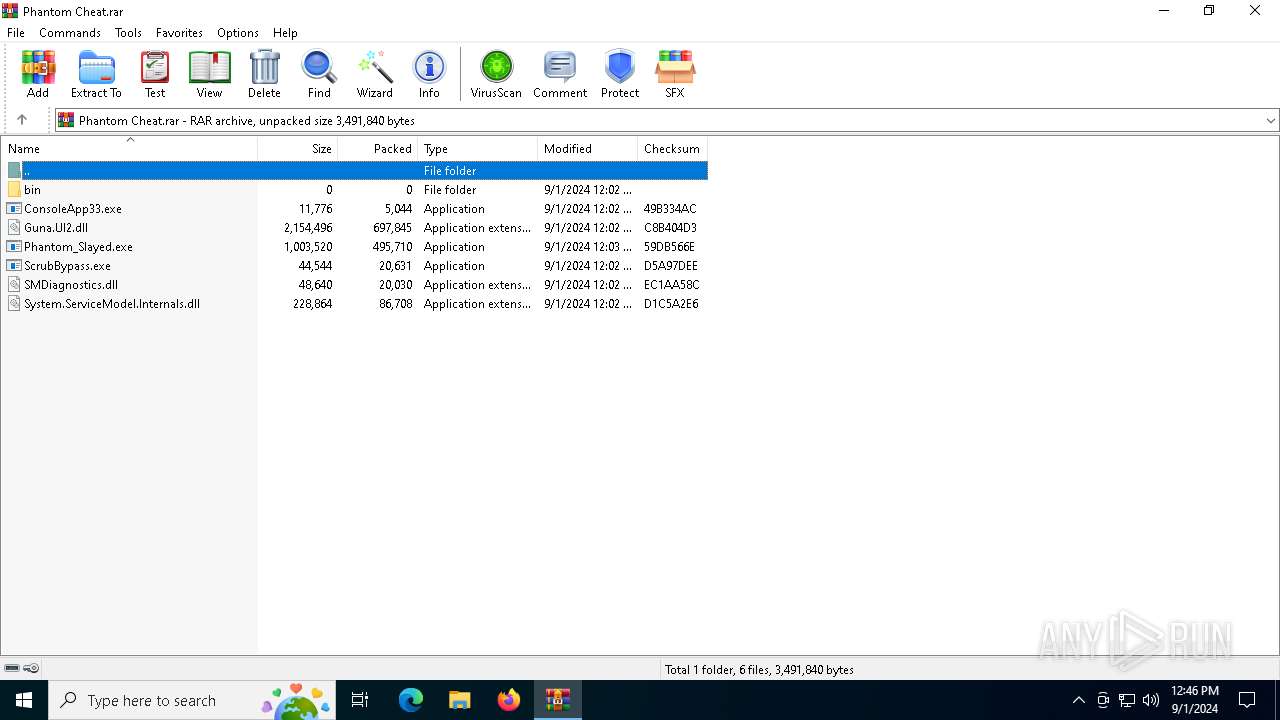
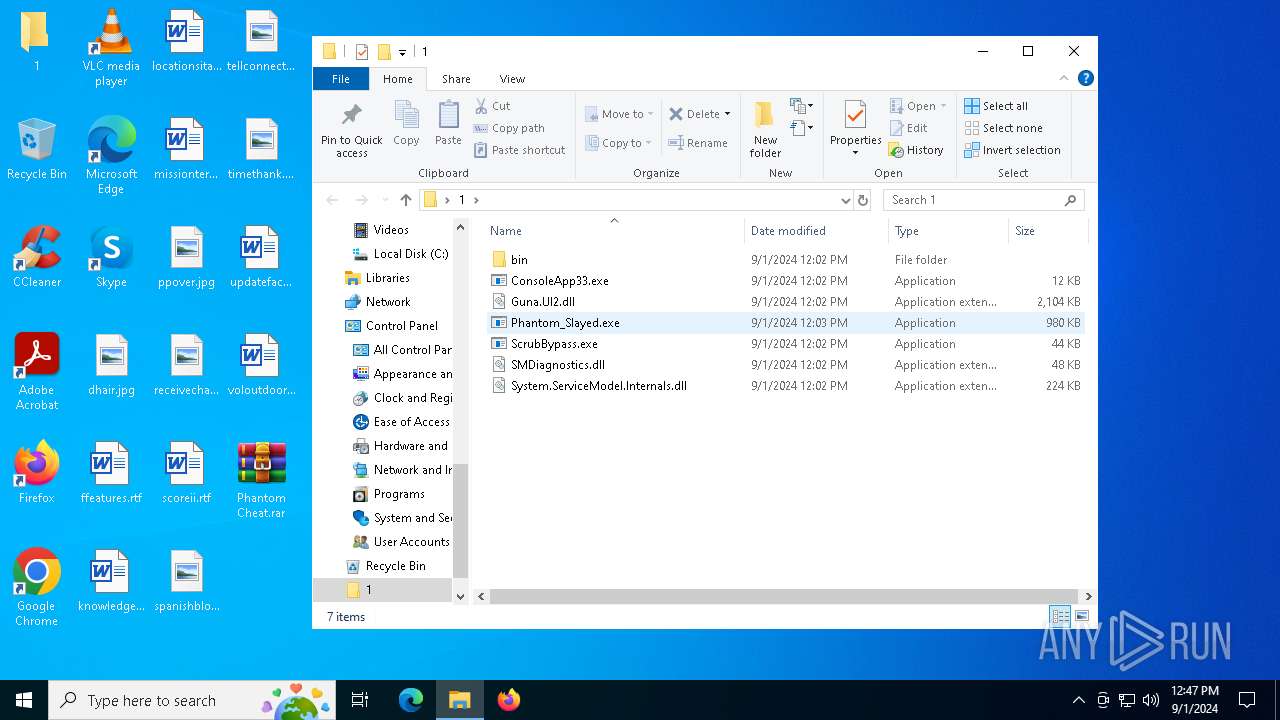
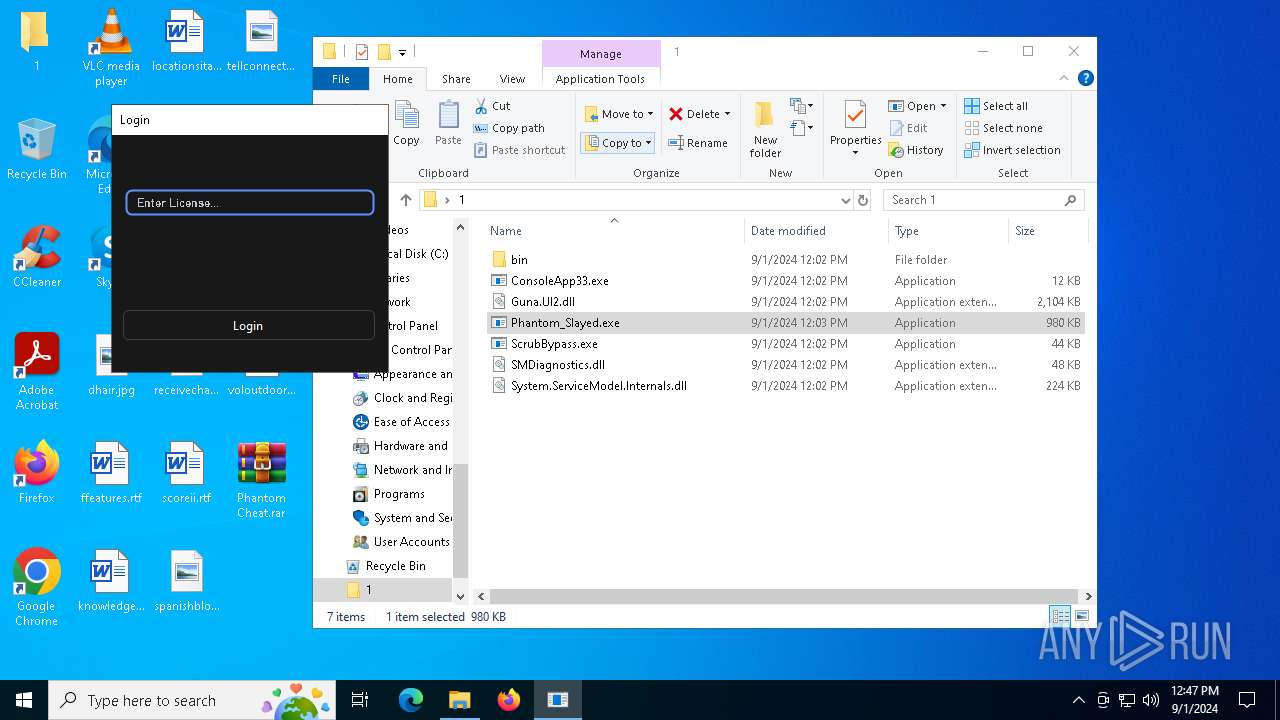
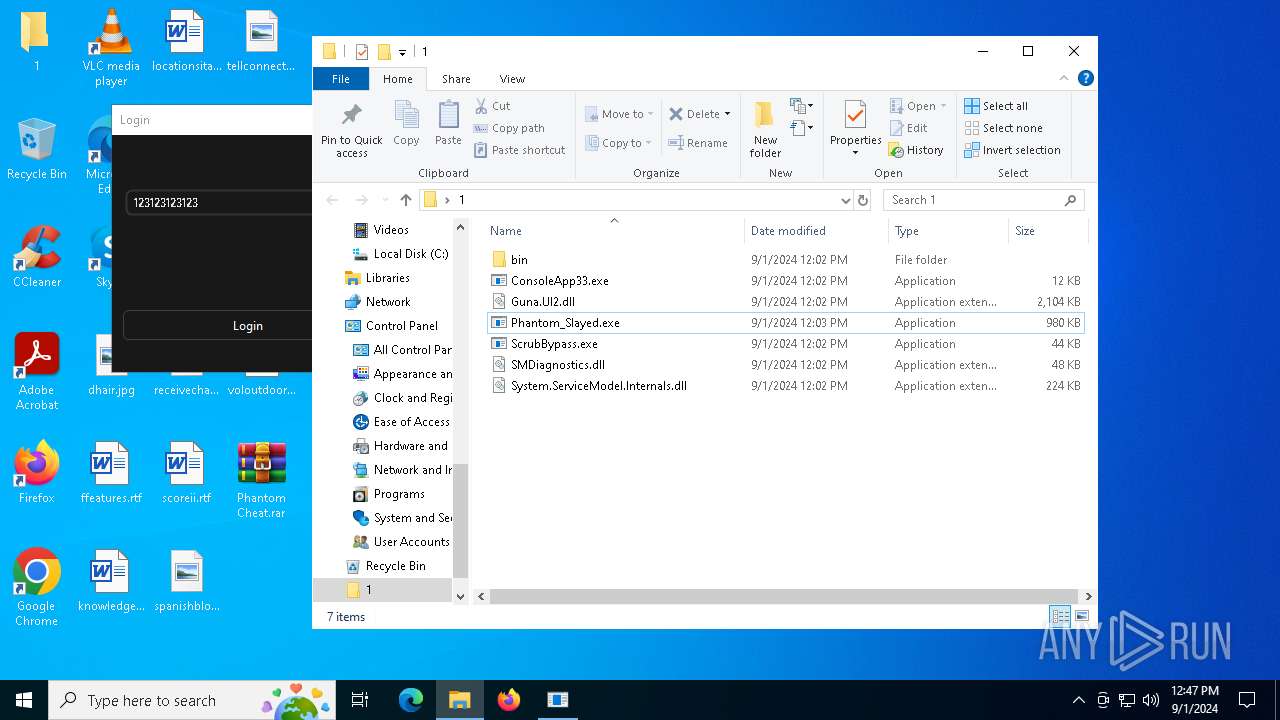
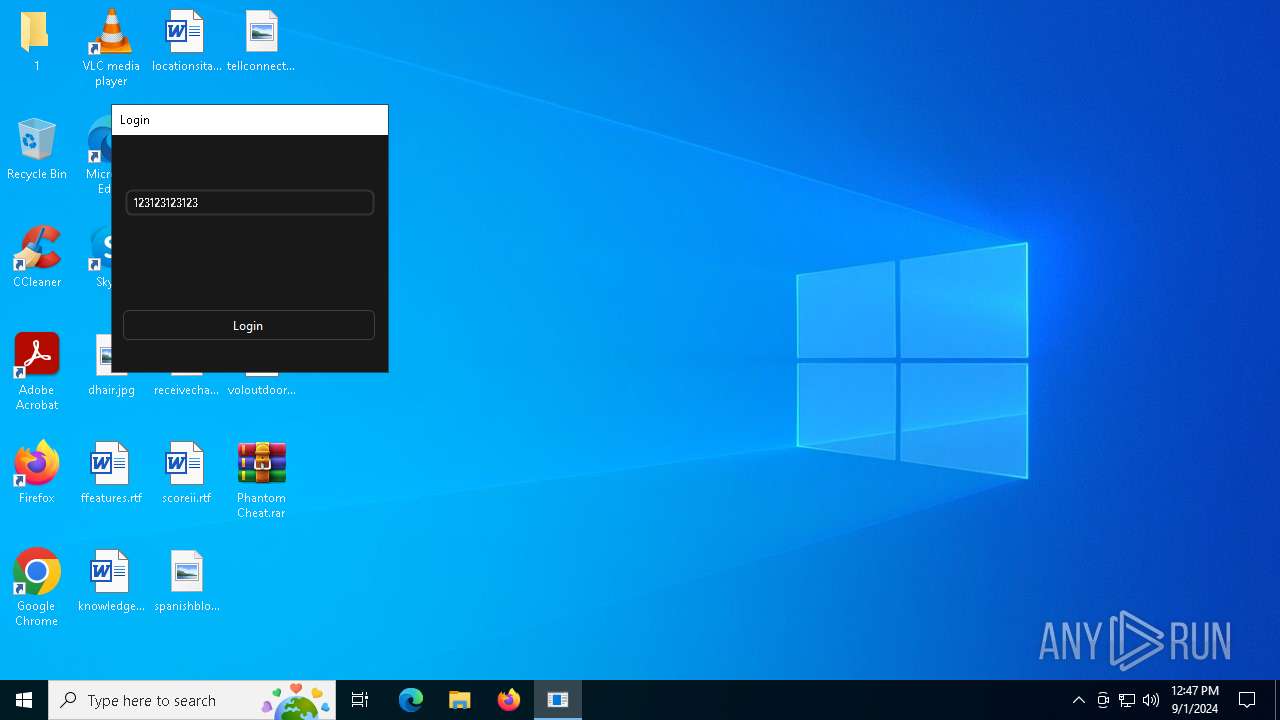
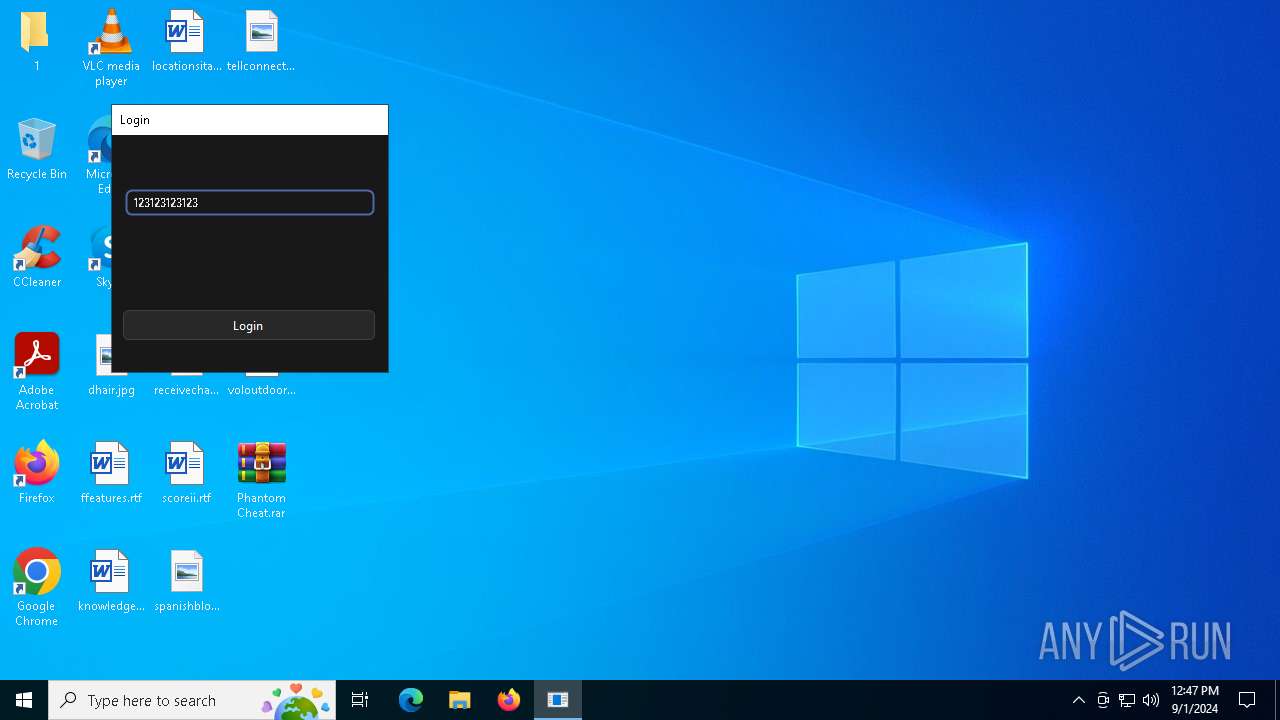
| File name: | Phantom Cheat.rar |
| Full analysis: | https://app.any.run/tasks/17cb3a22-3f32-4015-b41e-45c6776fb3a9 |
| Verdict: | Malicious activity |
| Analysis date: | September 01, 2024, 12:46:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | EA34933ECF5B0133632C958EF66EDE25 |
| SHA1: | 42151B52B72DB04EB55CFAAAB09855926148957E |
| SHA256: | 08A74FC894A3CD3BD631C533CCAE45093330CD4942ACC53831595756BED7128A |
| SSDEEP: | 49152:MjwSi5JCj+lt2sepgvDEfYFHPTsgx7iFKOZLuttjq2ABG/guePk5aAySQ18acTlK:pSiXCQ5v6YFHrsgRiEOZCttjq9B+eM5e |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 780)
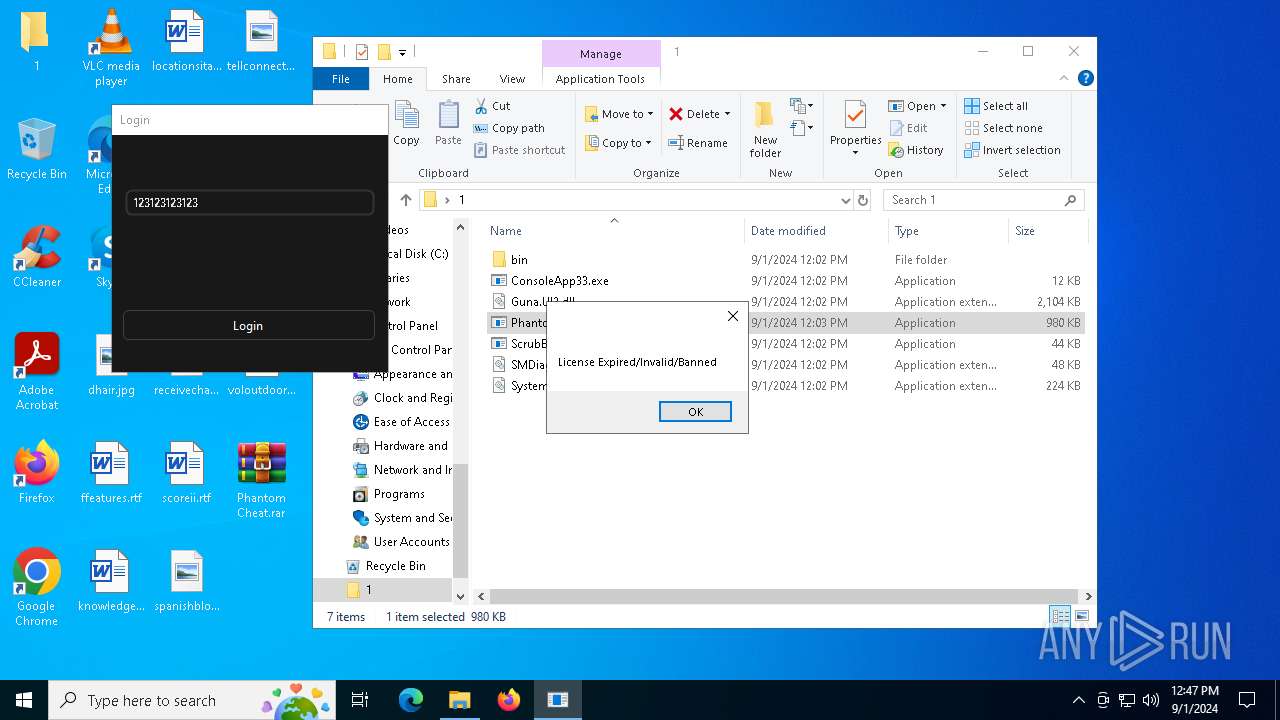
There is functionality for taking screenshot (YARA)
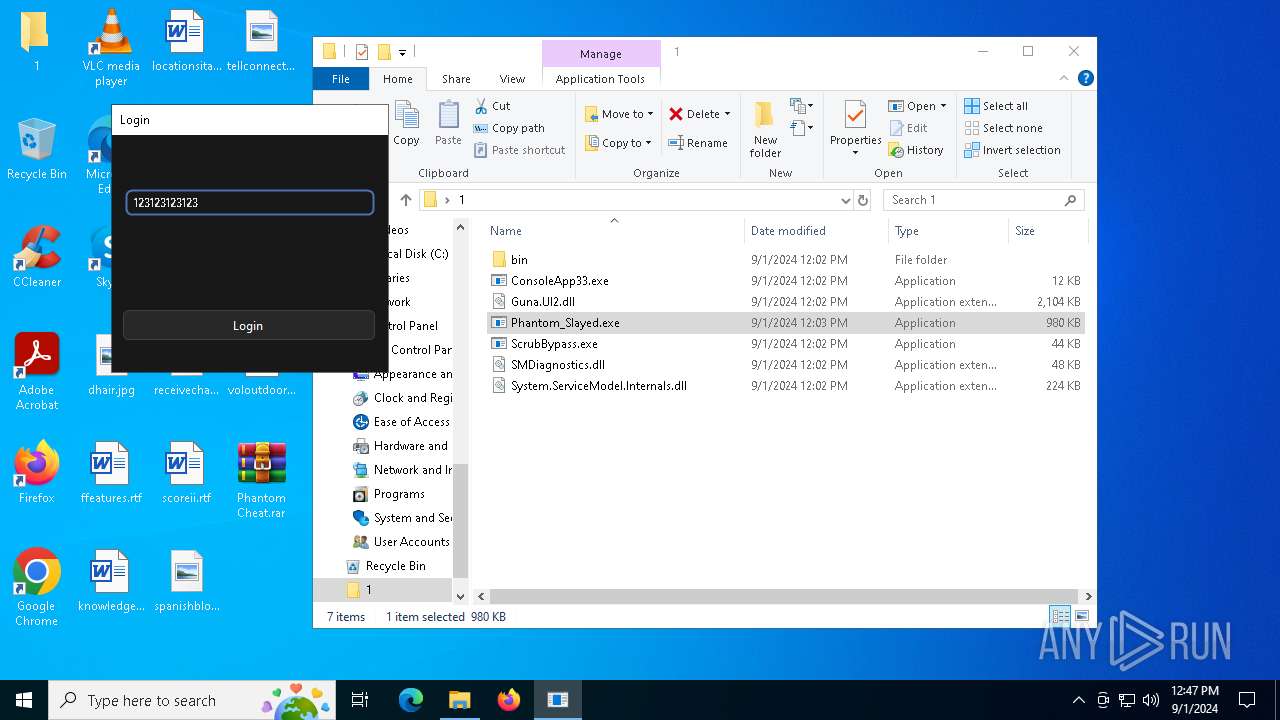
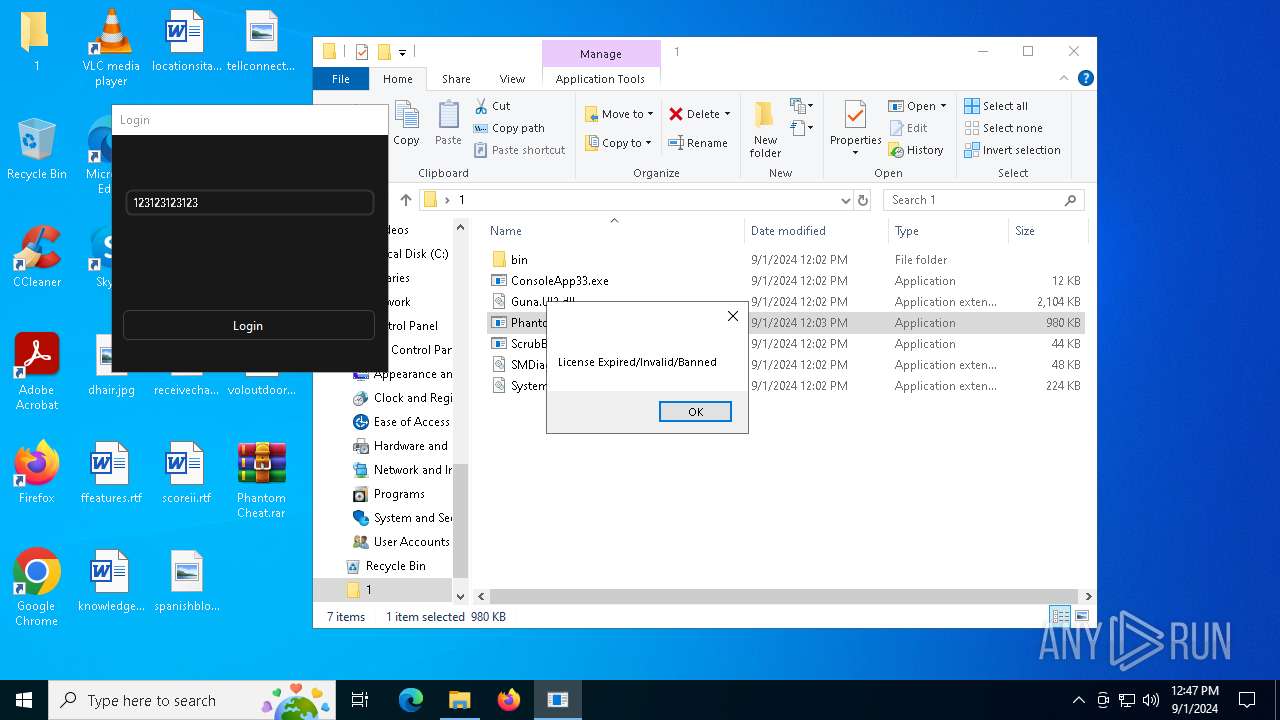
- Phantom_Slayed.exe (PID: 236)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 780)
Manual execution by a user
- Phantom_Slayed.exe (PID: 236)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 780)
Disables trace logs
- Phantom_Slayed.exe (PID: 236)
Reads Environment values
- Phantom_Slayed.exe (PID: 236)
Checks proxy server information
- Phantom_Slayed.exe (PID: 236)
Reads the machine GUID from the registry
- Phantom_Slayed.exe (PID: 236)
Checks supported languages
- Phantom_Slayed.exe (PID: 236)
Reads the computer name
- Phantom_Slayed.exe (PID: 236)
Reads the software policy settings
- Phantom_Slayed.exe (PID: 236)
Creates files in the program directory
- Phantom_Slayed.exe (PID: 236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
126
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Users\admin\Desktop\1\Phantom_Slayed.exe" | C:\Users\admin\Desktop\1\Phantom_Slayed.exe | explorer.exe | ||||||||||||
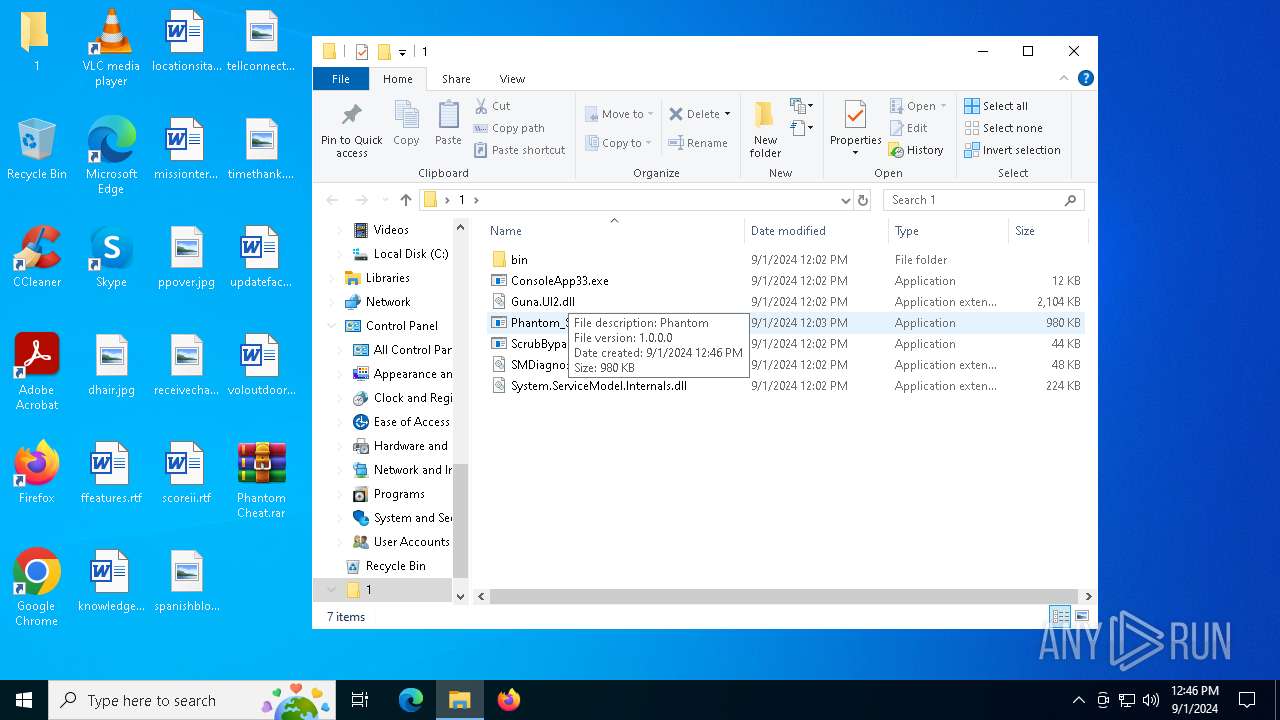
User: admin Integrity Level: MEDIUM Description: Phantom Version: 1.0.0.0 Modules
| |||||||||||||||
| 780 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Phantom Cheat.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1184 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 133
Read events
6 098
Write events
35
Delete events
0
Modification events
| (PID) Process: | (780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Phantom Cheat.rar | |||
| (PID) Process: | (780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\1 | |||
| (PID) Process: | (780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
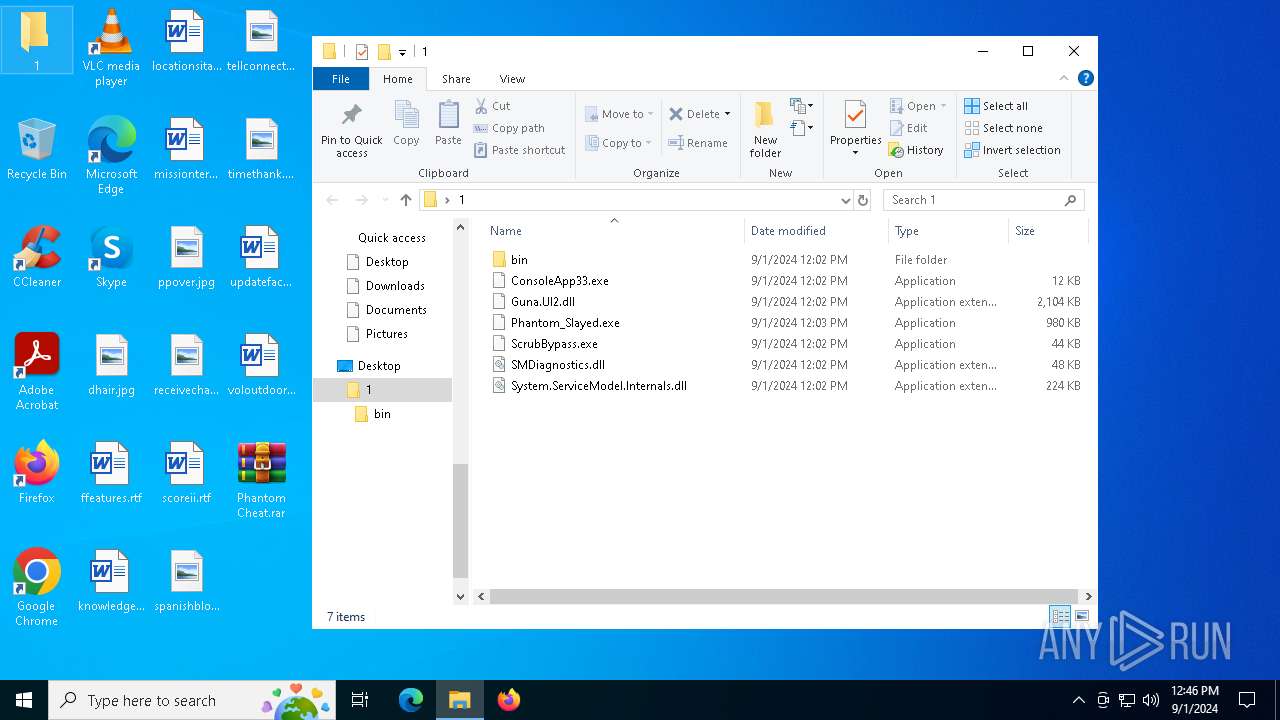
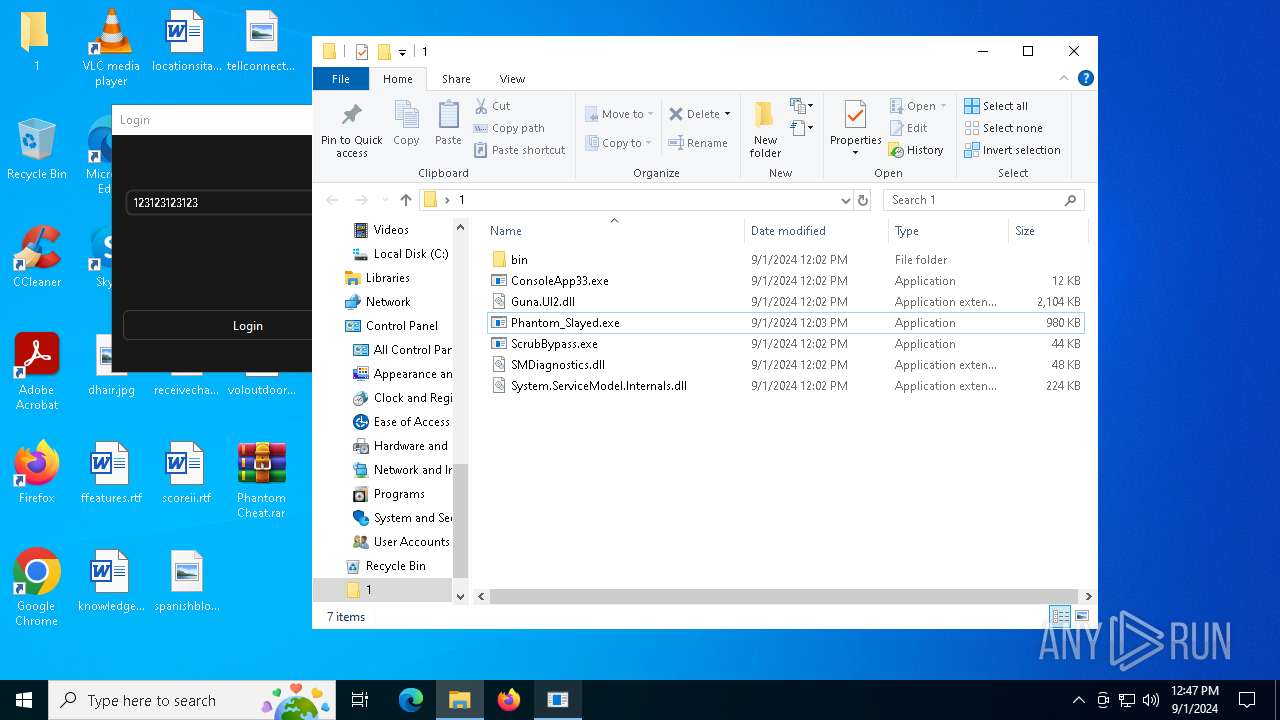
Executable files
6
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 780 | WinRAR.exe | C:\Users\admin\Desktop\1\Guna.UI2.dll | executable | |
MD5:AAB932E4AADEC1AAE199395CAC9DDD45 | SHA256:0B195733E4614A216A9EBD2F39B8AB4F53FE3EF85D71FB92155821E523121E3B | |||
| 236 | Phantom_Slayed.exe | C:\ProgramData\KeyAuth\debug\Phantom_Slayed\Sep_01_2024_logs.txt | text | |
MD5:6D5BE3E4E05121B62A8FA2326C5E5E07 | SHA256:4A68048AC1A76168C0E726D3E9ED1B72AB10A3B709849E1FAEA5B89CF53ABACD | |||
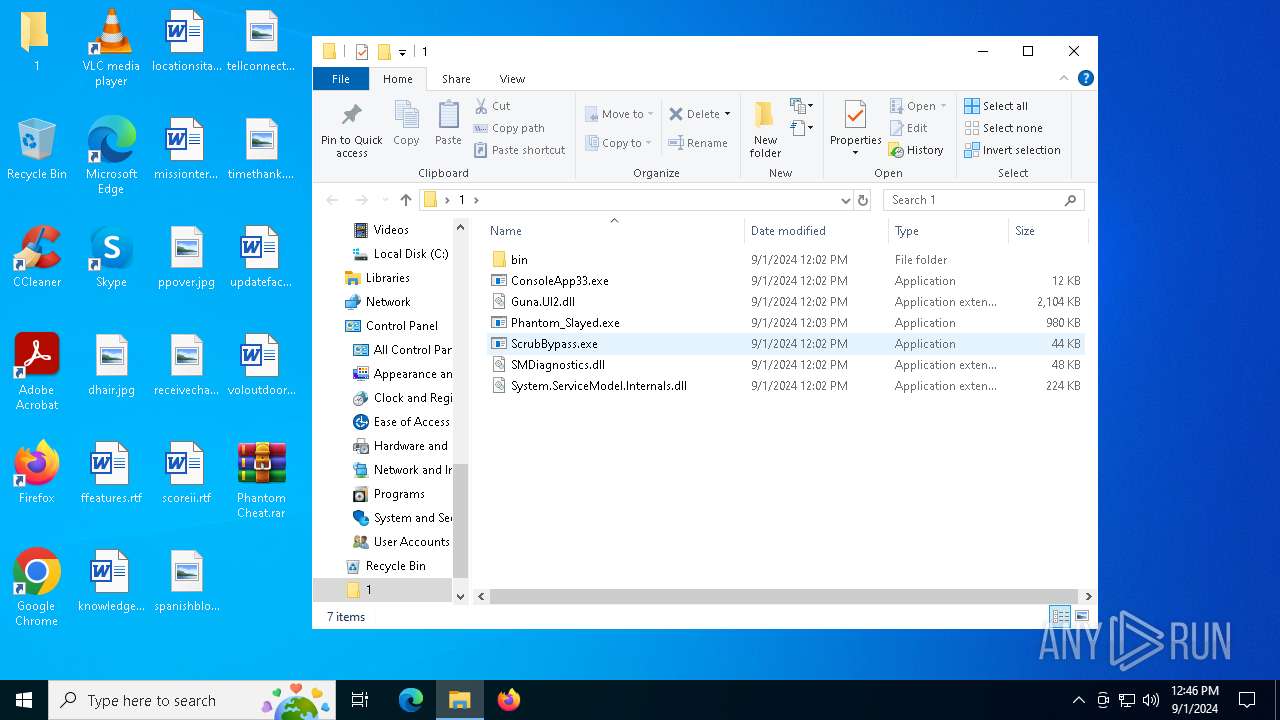
| 780 | WinRAR.exe | C:\Users\admin\Desktop\1\ScrubBypass.exe | executable | |
MD5:9EC9948C02E69907839FAD6931D75CA5 | SHA256:A9F561BF0717A2E090468FA0F61E8E34D307C371670CA61DD63E553495C72C3C | |||
| 780 | WinRAR.exe | C:\Users\admin\Desktop\1\SMDiagnostics.dll | executable | |
MD5:564CC2D134E3B360DB4AB234CCCB7075 | SHA256:72E748202E32FA20CC7C7CF2015E94E2562DD036EDBF89993AB904F666D31ABB | |||
| 780 | WinRAR.exe | C:\Users\admin\Desktop\1\Phantom_Slayed.exe | executable | |
MD5:D028111B39959D5319581C9E3AAA5CDF | SHA256:B13E04D107E3346A237F5505614CA94E463A146AF9205C523B20DA999235C350 | |||
| 780 | WinRAR.exe | C:\Users\admin\Desktop\1\ConsoleApp33.exe | executable | |
MD5:D1F143743ADAE88C81E7D33D7547EA45 | SHA256:C9BF1A2BDB62FC92976EE40C26ACD924B4B4A37A61C49F17FD16F439F36EFAC2 | |||
| 780 | WinRAR.exe | C:\Users\admin\Desktop\1\System.ServiceModel.Internals.dll | executable | |
MD5:6DB02F89DB687F6D33CCB283377EDB26 | SHA256:5055C7059E6C4B29D08C2EF0BD11E01F88ED297A4B4B321D4AE805AC80FA8ABA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
23
DNS requests
13
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1780 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2824 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2824 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6192 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6380 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1780 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1780 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
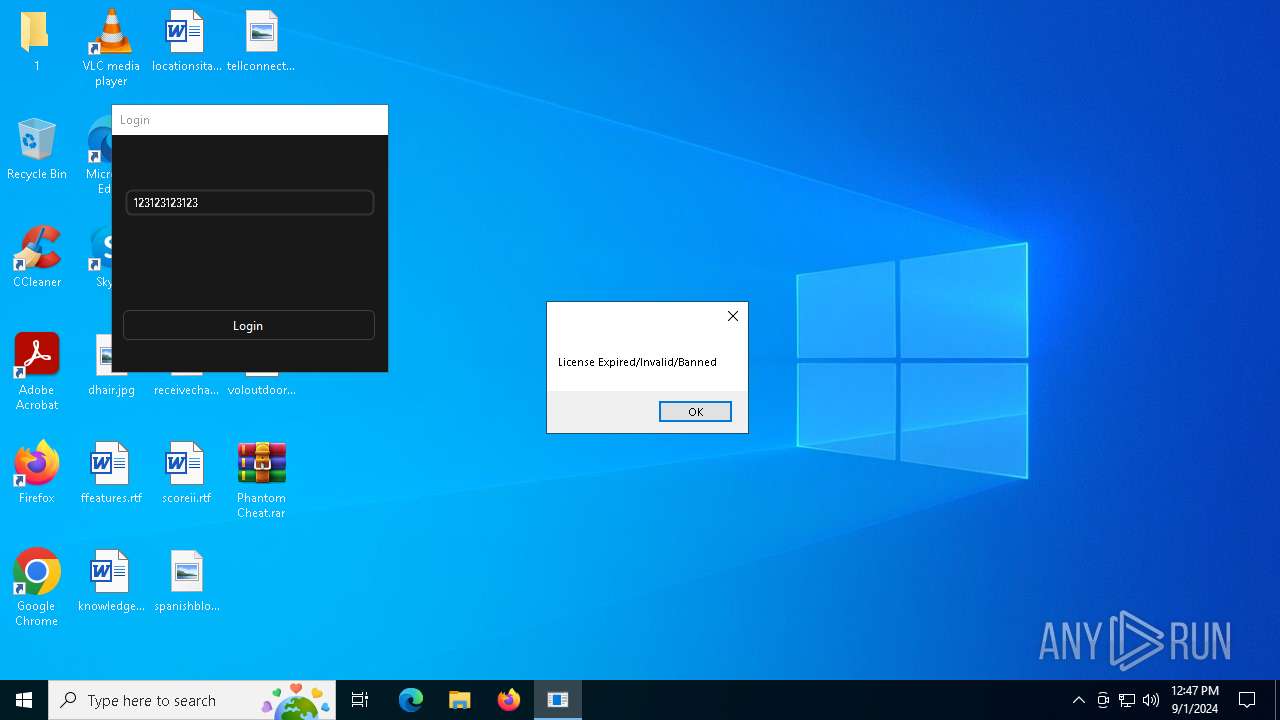
keyauth.win |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET INFO Fake Game Cheat Related Domain in DNS Lookup (keyauth .win) |
236 | Phantom_Slayed.exe | Potentially Bad Traffic | ET INFO Fake Game Cheat Related Domain (keyauth .win) in TLS SNI |