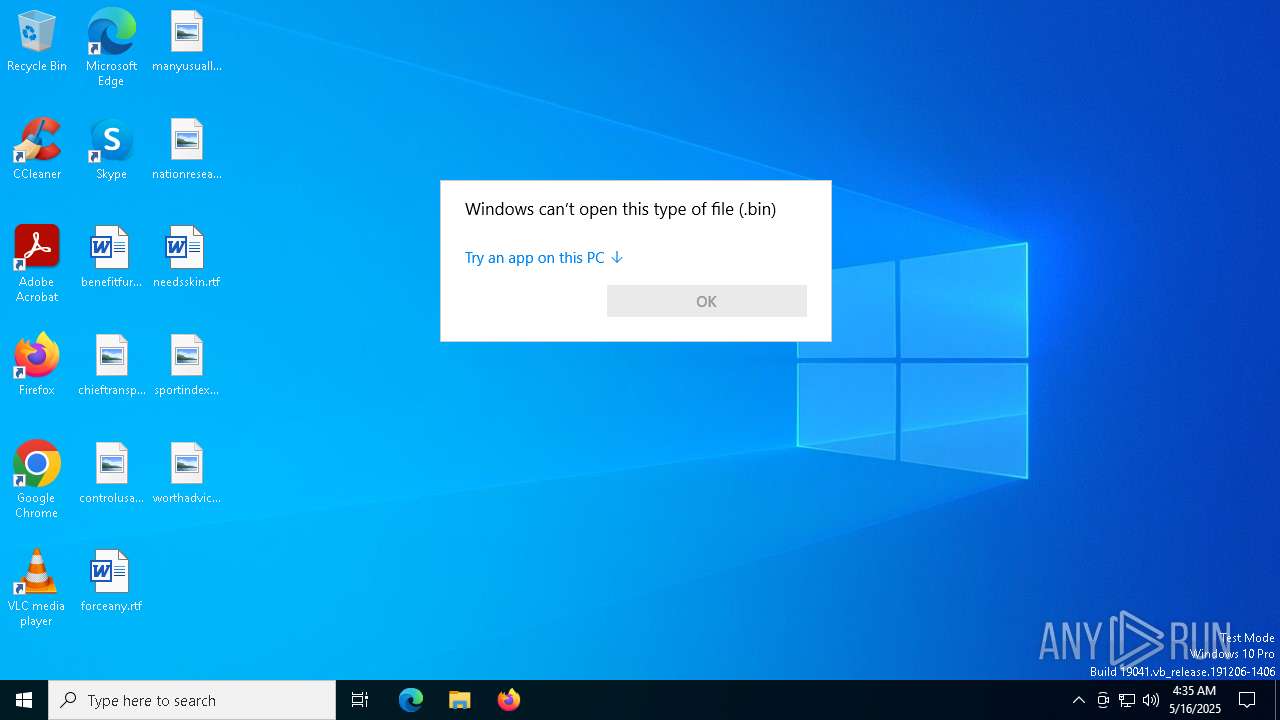
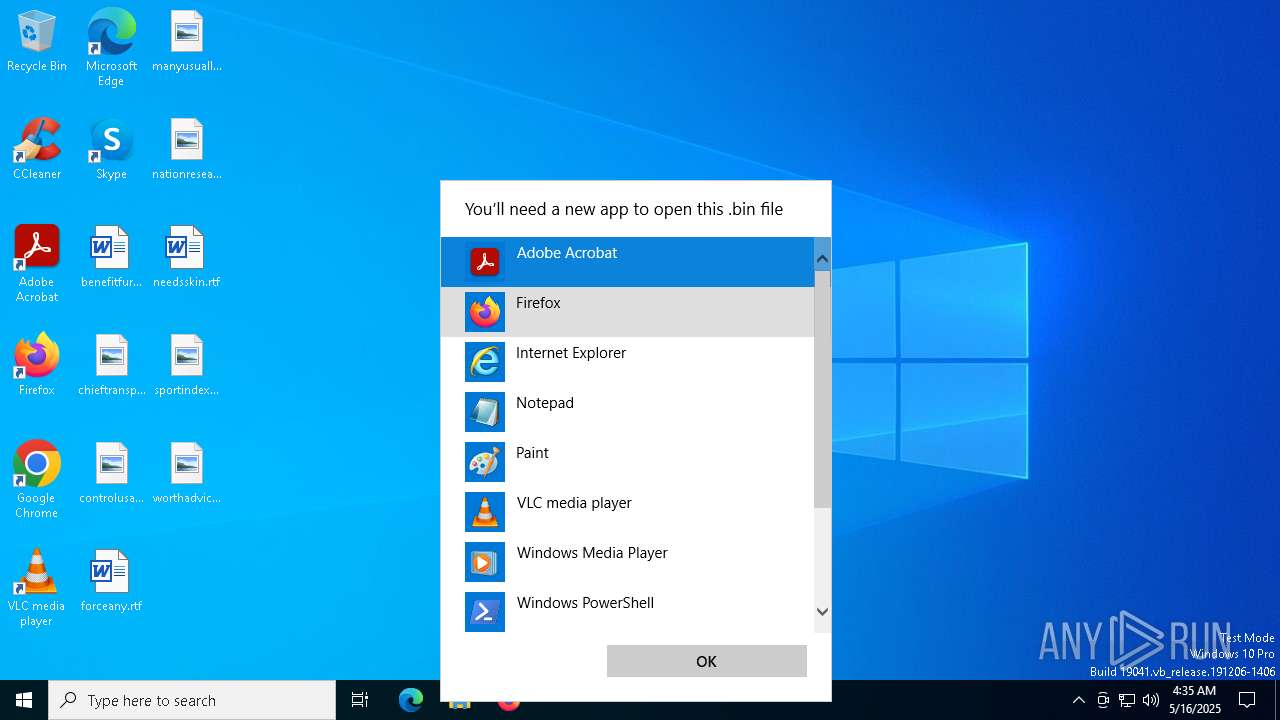
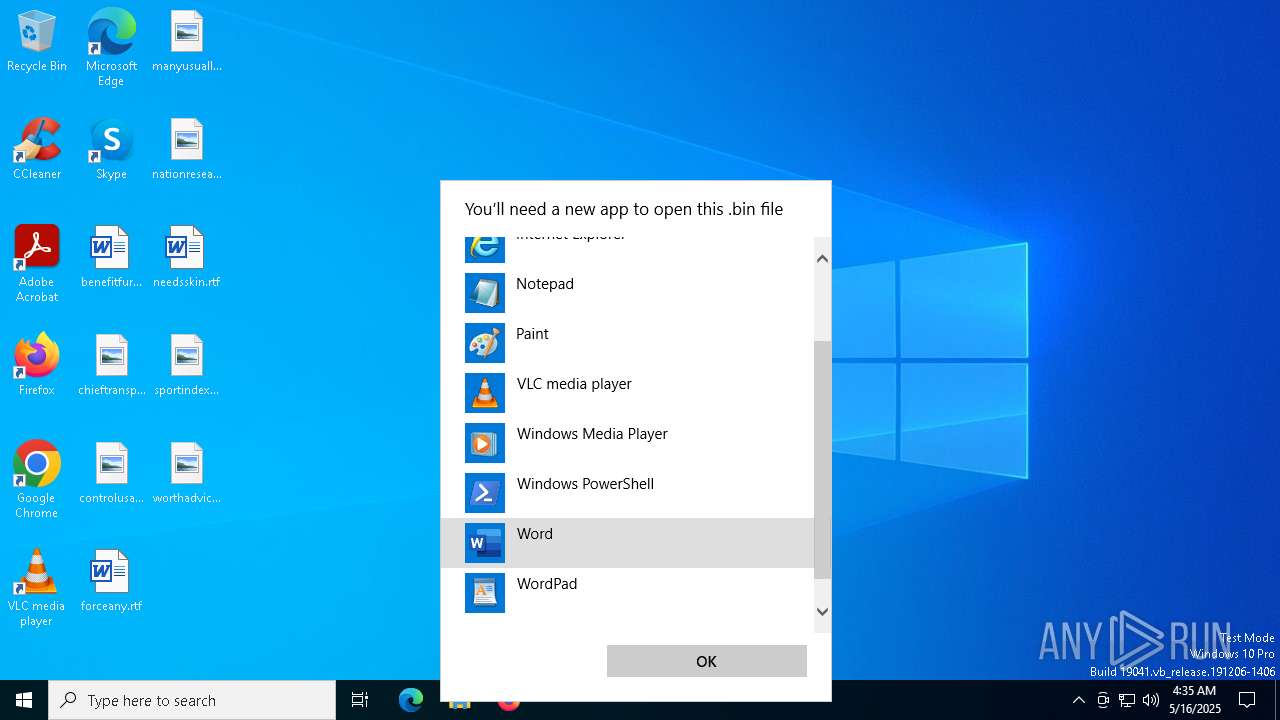
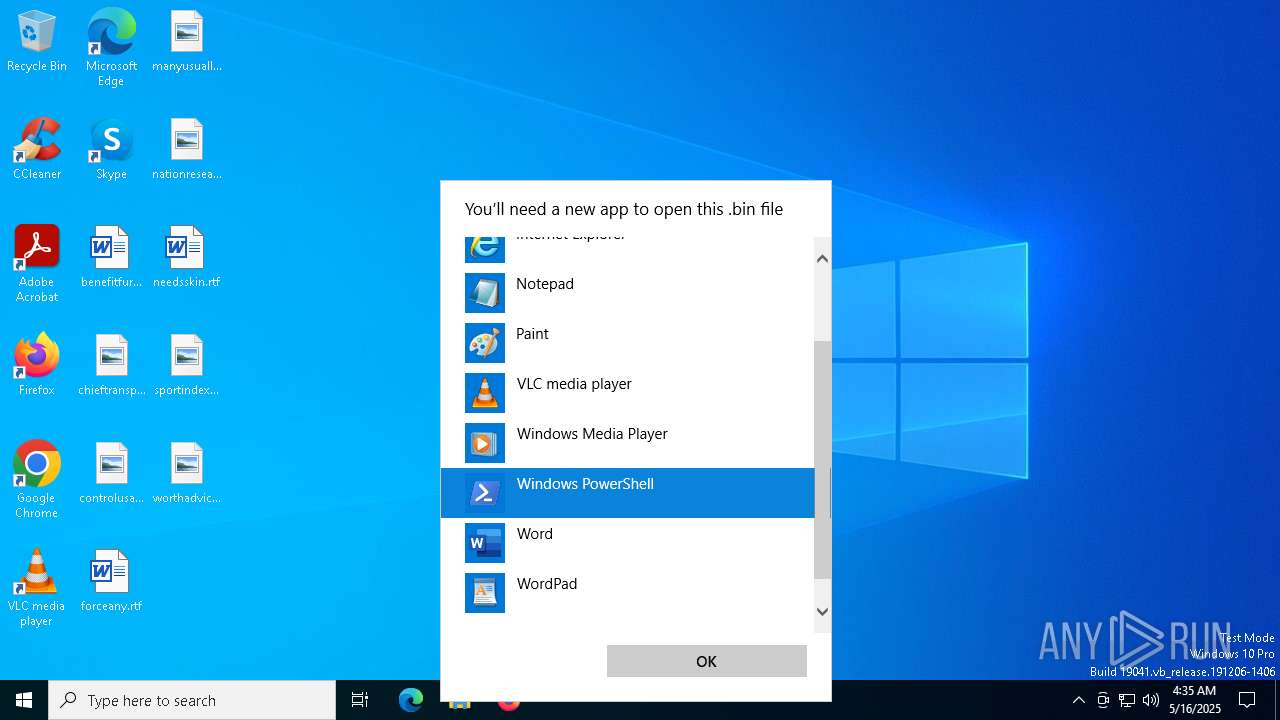
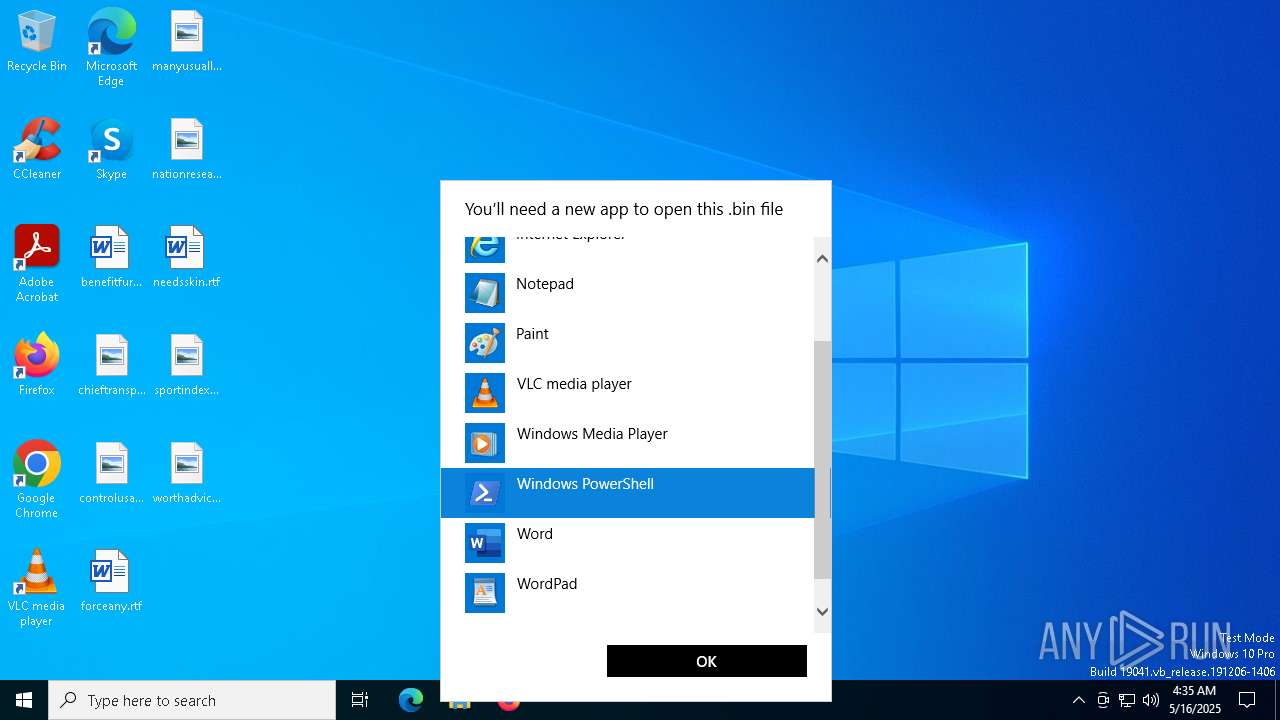
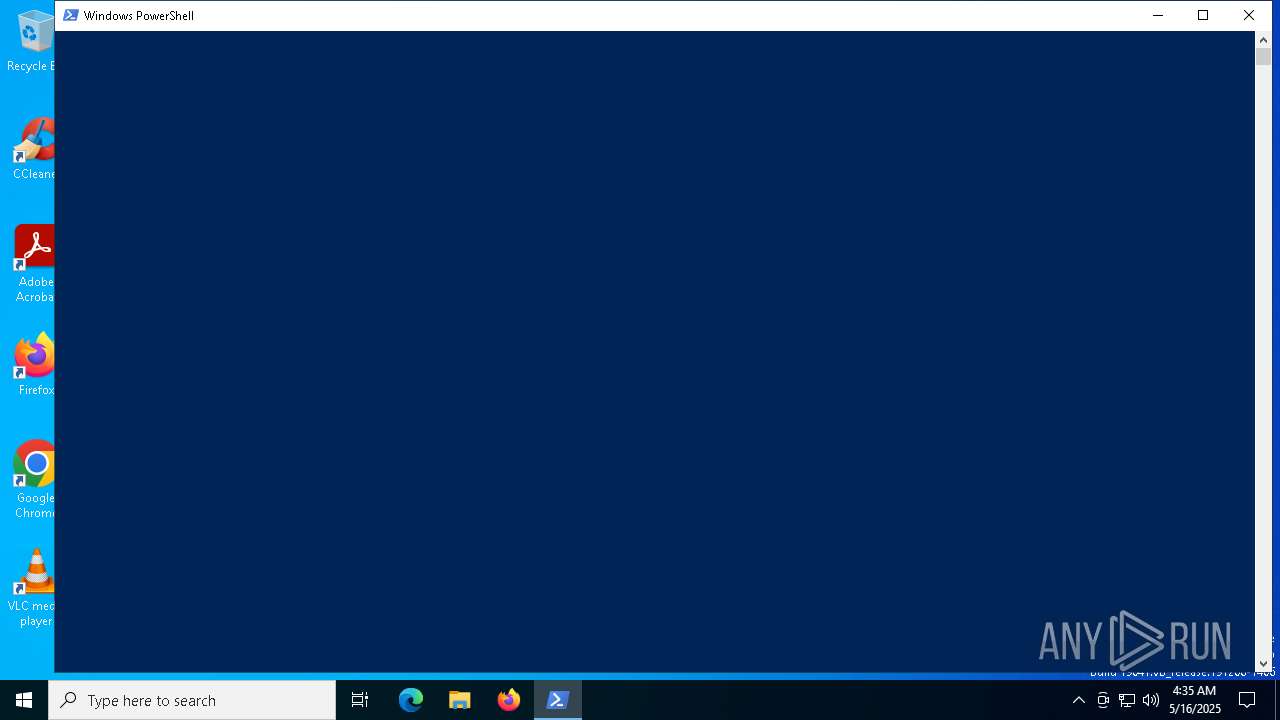
| File name: | prnjobs.data_84dee9df.bin |
| Full analysis: | https://app.any.run/tasks/88d74a27-aab3-4450-8153-ef8a981b4c60 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 04:35:35 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive, 4 sections |
| MD5: | 4C9615FC515731352196305888084331 |
| SHA1: | 7391499DB5E66108845AA9184E5590DC246AB9FD |
| SHA256: | 08986FD6CE64FC64905919E4D15E44A817FA9082911B1A54A354CF903F6566A2 |
| SSDEEP: | 12288:b8WWL6vPYy56IAjX2CSp/kbgFvyJYqgeVVVVVVuVV6VVVVVVuVV/CtXI0WCh4ptS:cop//PjCtY0WCiptQXizBv51YlN |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- OpenWith.exe (PID: 5048)
- OpenWith.exe (PID: 6816)
- powershell.exe (PID: 6040)
- powershell.exe (PID: 1348)
- powershell.exe (PID: 736)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 6816)
- powershell.exe (PID: 1040)
- powershell.exe (PID: 5228)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 3008)
- powershell.exe (PID: 4188)
- powershell.exe (PID: 780)
- powershell.exe (PID: 856)
- powershell.exe (PID: 6136)
- powershell.exe (PID: 2240)
- powershell.exe (PID: 976)
- powershell.exe (PID: 6972)
- powershell.exe (PID: 5136)
- powershell.exe (PID: 4220)
- powershell.exe (PID: 2092)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 6728)
- powershell.exe (PID: 6040)
- powershell.exe (PID: 960)
- powershell.exe (PID: 1096)
- powershell.exe (PID: 3176)
- powershell.exe (PID: 4336)
- powershell.exe (PID: 5508)
- powershell.exe (PID: 5008)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 6660)
- powershell.exe (PID: 2092)
- powershell.exe (PID: 6660)
- powershell.exe (PID: 6668)
- powershell.exe (PID: 644)
- powershell.exe (PID: 6156)
- powershell.exe (PID: 728)
- powershell.exe (PID: 5112)
- powershell.exe (PID: 6044)
- powershell.exe (PID: 1616)
- powershell.exe (PID: 3176)
- powershell.exe (PID: 6824)
- powershell.exe (PID: 3968)
- powershell.exe (PID: 1056)
- powershell.exe (PID: 6612)
- powershell.exe (PID: 3304)
- powershell.exe (PID: 5188)
- powershell.exe (PID: 1012)
- powershell.exe (PID: 4336)
- powershell.exe (PID: 3268)
- powershell.exe (PID: 6040)
- powershell.exe (PID: 5640)
- powershell.exe (PID: 4000)
- powershell.exe (PID: 6344)
- powershell.exe (PID: 6668)
- powershell.exe (PID: 2092)
- powershell.exe (PID: 6252)
- powershell.exe (PID: 4220)
- powershell.exe (PID: 1272)
- powershell.exe (PID: 5020)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 6488)
- powershell.exe (PID: 7000)
- powershell.exe (PID: 4776)
- powershell.exe (PID: 5400)
- powershell.exe (PID: 1040)
- powershell.exe (PID: 4376)
- powershell.exe (PID: 6564)
- powershell.exe (PID: 720)
- powershell.exe (PID: 3968)
- powershell.exe (PID: 6728)
- powershell.exe (PID: 6156)
- powershell.exe (PID: 3140)
- powershell.exe (PID: 4464)
- powershell.exe (PID: 2692)
- powershell.exe (PID: 3012)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 6668)
- powershell.exe (PID: 4692)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 6252)
- powershell.exe (PID: 4108)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 6244)
- powershell.exe (PID: 6208)
- powershell.exe (PID: 1300)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 5260)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 7144)
- powershell.exe (PID: 7144)
- powershell.exe (PID: 6576)
- powershell.exe (PID: 2780)
- powershell.exe (PID: 4276)
- powershell.exe (PID: 6080)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 5964)
- powershell.exe (PID: 5772)
- powershell.exe (PID: 920)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 5608)
- powershell.exe (PID: 4016)
- powershell.exe (PID: 5232)
- powershell.exe (PID: 5036)
- powershell.exe (PID: 5972)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 6436)
- powershell.exe (PID: 2416)
- powershell.exe (PID: 644)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 7036)
- powershell.exe (PID: 7000)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 2416)
- powershell.exe (PID: 4488)
- powershell.exe (PID: 644)
- powershell.exe (PID: 5744)
- powershell.exe (PID: 5812)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 4308)
- powershell.exe (PID: 4180)
- powershell.exe (PID: 2420)
- powershell.exe (PID: 5312)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 5548)
- powershell.exe (PID: 4284)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 720)
- powershell.exe (PID: 5404)
- powershell.exe (PID: 3016)
- powershell.exe (PID: 5344)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 6256)
- powershell.exe (PID: 2240)
- powershell.exe (PID: 4276)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 1244)
- powershell.exe (PID: 4944)
- powershell.exe (PID: 3884)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 5408)
- powershell.exe (PID: 1532)
- powershell.exe (PID: 3992)
- powershell.exe (PID: 5508)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 6044)
- powershell.exe (PID: 540)
- powershell.exe (PID: 7008)
- powershell.exe (PID: 5244)
- powershell.exe (PID: 5132)
- powershell.exe (PID: 2664)
- powershell.exe (PID: 5188)
- powershell.exe (PID: 5180)
- powershell.exe (PID: 5324)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 7036)
- powershell.exe (PID: 7020)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 6972)
- powershell.exe (PID: 6244)
- powershell.exe (PID: 7144)
- powershell.exe (PID: 1056)
- powershell.exe (PID: 3760)
- powershell.exe (PID: 6216)
- powershell.exe (PID: 4276)
- powershell.exe (PID: 732)
- powershell.exe (PID: 5720)
- powershell.exe (PID: 856)
- powershell.exe (PID: 4220)
- powershell.exe (PID: 5516)
- powershell.exe (PID: 2416)
- powershell.exe (PID: 1272)
- powershell.exe (PID: 5104)
- powershell.exe (PID: 5952)
- powershell.exe (PID: 3684)
- powershell.exe (PID: 5640)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 3016)
- powershell.exe (PID: 6564)
- powershell.exe (PID: 3008)
- powershell.exe (PID: 3012)
- powershell.exe (PID: 3884)
Application launched itself
- powershell.exe (PID: 1348)
- powershell.exe (PID: 736)
- powershell.exe (PID: 6040)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 6816)
- powershell.exe (PID: 1040)
- powershell.exe (PID: 5228)
- powershell.exe (PID: 4188)
- powershell.exe (PID: 3008)
- powershell.exe (PID: 6136)
- powershell.exe (PID: 780)
- powershell.exe (PID: 856)
- powershell.exe (PID: 2240)
- powershell.exe (PID: 976)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 6972)
- powershell.exe (PID: 4220)
- powershell.exe (PID: 6660)
- powershell.exe (PID: 6728)
- powershell.exe (PID: 2092)
- powershell.exe (PID: 6040)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 960)
- powershell.exe (PID: 1096)
- powershell.exe (PID: 5136)
- powershell.exe (PID: 6668)
- powershell.exe (PID: 4336)
- powershell.exe (PID: 3176)
- powershell.exe (PID: 5508)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 5008)
- powershell.exe (PID: 2092)
- powershell.exe (PID: 6824)
- powershell.exe (PID: 6660)
- powershell.exe (PID: 6156)
- powershell.exe (PID: 5112)
- powershell.exe (PID: 728)
- powershell.exe (PID: 6044)
- powershell.exe (PID: 3176)
- powershell.exe (PID: 1616)
- powershell.exe (PID: 3304)
- powershell.exe (PID: 3968)
- powershell.exe (PID: 644)
- powershell.exe (PID: 1056)
- powershell.exe (PID: 6612)
- powershell.exe (PID: 1012)
- powershell.exe (PID: 4336)
- powershell.exe (PID: 5188)
- powershell.exe (PID: 3268)
- powershell.exe (PID: 6040)
- powershell.exe (PID: 5640)
- powershell.exe (PID: 4000)
- powershell.exe (PID: 6344)
- powershell.exe (PID: 6668)
- powershell.exe (PID: 2092)
- powershell.exe (PID: 6252)
- powershell.exe (PID: 1272)
- powershell.exe (PID: 4220)
- powershell.exe (PID: 5020)
- powershell.exe (PID: 6488)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 7000)
- powershell.exe (PID: 4776)
- powershell.exe (PID: 5400)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 1040)
- powershell.exe (PID: 6564)
- powershell.exe (PID: 720)
- powershell.exe (PID: 6728)
- powershell.exe (PID: 3968)
- powershell.exe (PID: 6156)
- powershell.exe (PID: 3140)
- powershell.exe (PID: 4464)
- powershell.exe (PID: 2692)
- powershell.exe (PID: 3012)
- powershell.exe (PID: 4376)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 4692)
- powershell.exe (PID: 4108)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 6252)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 6668)
- powershell.exe (PID: 6244)
- powershell.exe (PID: 6576)
- powershell.exe (PID: 1300)
- powershell.exe (PID: 6208)
- powershell.exe (PID: 5260)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 7144)
- powershell.exe (PID: 2780)
- powershell.exe (PID: 4276)
- powershell.exe (PID: 5964)
- powershell.exe (PID: 5772)
- powershell.exe (PID: 920)
- powershell.exe (PID: 6080)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 5608)
- powershell.exe (PID: 7144)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 5232)
- powershell.exe (PID: 5036)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 5972)
- powershell.exe (PID: 6436)
- powershell.exe (PID: 644)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 4016)
- powershell.exe (PID: 2416)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 5812)
- powershell.exe (PID: 7000)
- powershell.exe (PID: 644)
- powershell.exe (PID: 7036)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 2416)
- powershell.exe (PID: 4488)
- powershell.exe (PID: 5744)
- powershell.exe (PID: 5548)
- powershell.exe (PID: 4308)
- powershell.exe (PID: 2420)
- powershell.exe (PID: 5312)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 4180)
- powershell.exe (PID: 4284)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 3016)
- powershell.exe (PID: 5404)
- powershell.exe (PID: 720)
- powershell.exe (PID: 5344)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 6256)
- powershell.exe (PID: 2240)
- powershell.exe (PID: 4276)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 1244)
- powershell.exe (PID: 3884)
- powershell.exe (PID: 4944)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 5408)
- powershell.exe (PID: 1532)
- powershell.exe (PID: 5188)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 5508)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 540)
- powershell.exe (PID: 6044)
- powershell.exe (PID: 5244)
- powershell.exe (PID: 2664)
- powershell.exe (PID: 5132)
- powershell.exe (PID: 5180)
- powershell.exe (PID: 3992)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 7008)
- powershell.exe (PID: 7036)
- powershell.exe (PID: 7020)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 7144)
- powershell.exe (PID: 6972)
- powershell.exe (PID: 6244)
- powershell.exe (PID: 5324)
- powershell.exe (PID: 5516)
- powershell.exe (PID: 1056)
- powershell.exe (PID: 6216)
- powershell.exe (PID: 4276)
- powershell.exe (PID: 732)
- powershell.exe (PID: 856)
- powershell.exe (PID: 3016)
- powershell.exe (PID: 4220)
- powershell.exe (PID: 3760)
- powershell.exe (PID: 5720)
- powershell.exe (PID: 2416)
- powershell.exe (PID: 1272)
- powershell.exe (PID: 5952)
- powershell.exe (PID: 3684)
- powershell.exe (PID: 5640)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 3012)
- powershell.exe (PID: 5104)
- powershell.exe (PID: 6564)
- powershell.exe (PID: 3884)
- powershell.exe (PID: 3008)
INFO
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 5048)
- OpenWith.exe (PID: 6816)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5048)
- OpenWith.exe (PID: 6816)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:12:02 10:07:30+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 165376 |
| InitializedDataSize: | 175104 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d5db |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
514
Monitored processes
385
Malicious processes
5
Suspicious processes
61
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\prnjobs.data_84dee9df.bin" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\prnjobs.data_84dee9df.bin" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\prnjobs.data_84dee9df.bin" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\prnjobs.data_84dee9df.bin" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
889 339
Read events
889 144
Write events
195
Delete events
0
Modification events
| (PID) Process: | (6816) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\UserChoice |
| Operation: | write | Name: | ProgId |
Value: Applications\powershell.exe | |||
| (PID) Process: | (6816) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\UserChoice |
| Operation: | write | Name: | Hash |
Value: tTg/bC2t83M= | |||
| (PID) Process: | (6816) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (6816) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (6816) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 114 | |||
| (PID) Process: | (1348) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (6040) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (736) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (4980) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (6816) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
Executable files
0
Suspicious files
571
Text files
380
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5508 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\M7VLWLS53JNW4TGCLD6W.temp | binary | |
MD5:1B551B2543ED2F7308EDE68AA07E67CA | SHA256:9C4C78814C7B9D59C377FB8B257F306F643B1E25B469CB4994CF8F8E947EFA1D | |||
| 1348 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:2159E0F1A1733C2B340A8AF8F9E09B4F | SHA256:CACF76857F3643C01A1E352CD4249A4C035A7EC5056652B2AC2C80106F5F3DC0 | |||
| 1348 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_iaswsrct.ye4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5508 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gvtdcv1w.cvd.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5508 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:1B551B2543ED2F7308EDE68AA07E67CA | SHA256:9C4C78814C7B9D59C377FB8B257F306F643B1E25B469CB4994CF8F8E947EFA1D | |||
| 5508 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF10e36c.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 5508 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tp5bmuzq.ihp.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1348 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF10fbc7.TMP | binary | |
MD5:1B551B2543ED2F7308EDE68AA07E67CA | SHA256:9C4C78814C7B9D59C377FB8B257F306F643B1E25B469CB4994CF8F8E947EFA1D | |||
| 1348 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\Y1ULVHYLZ018F9OPLDZB.temp | binary | |
MD5:2159E0F1A1733C2B340A8AF8F9E09B4F | SHA256:CACF76857F3643C01A1E352CD4249A4C035A7EC5056652B2AC2C80106F5F3DC0 | |||
| 5508 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:21FF332A5F22530645B5DB76B9244D4E | SHA256:5959A93506196360AB647DB385E048EEB515590E2652F68F365BC9FF39B095EF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
45
DNS requests
15
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2320 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2320 | SIHClient.exe | 13.95.31.18:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6456 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
18.31.95.13.in-addr.arpa |
| unknown |
4.8.2.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.0.0.2.0.c.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |