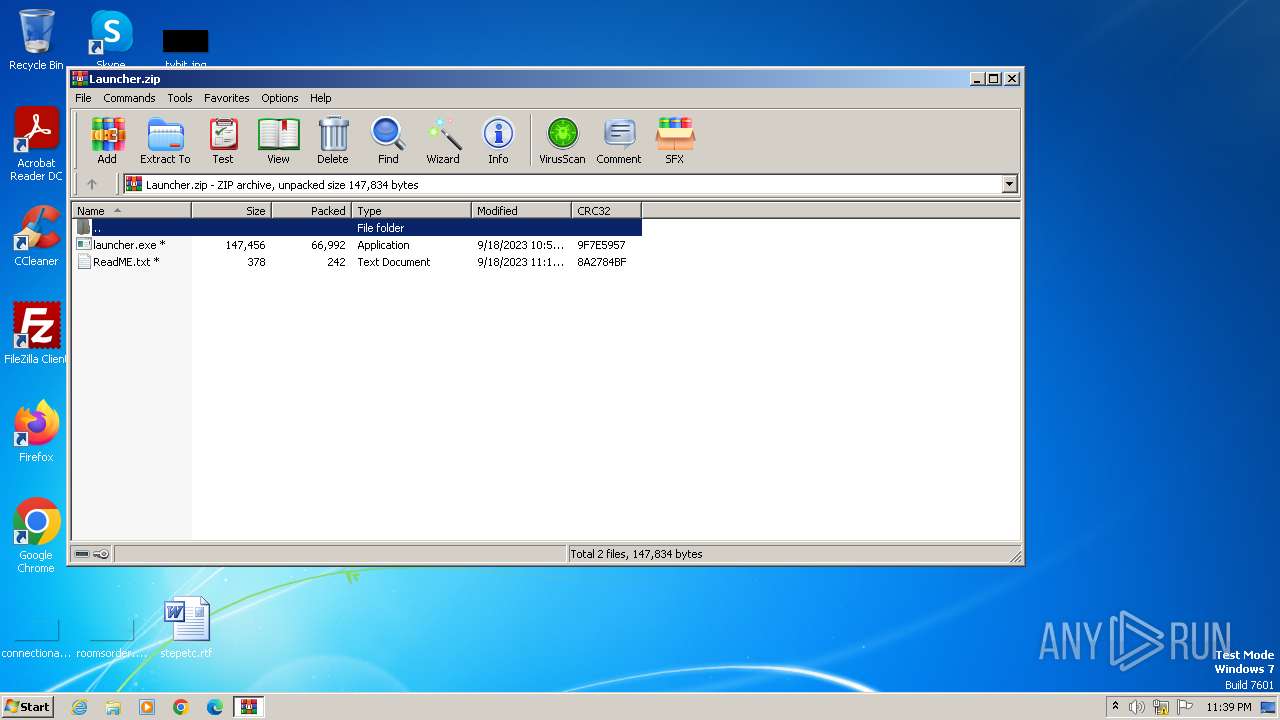
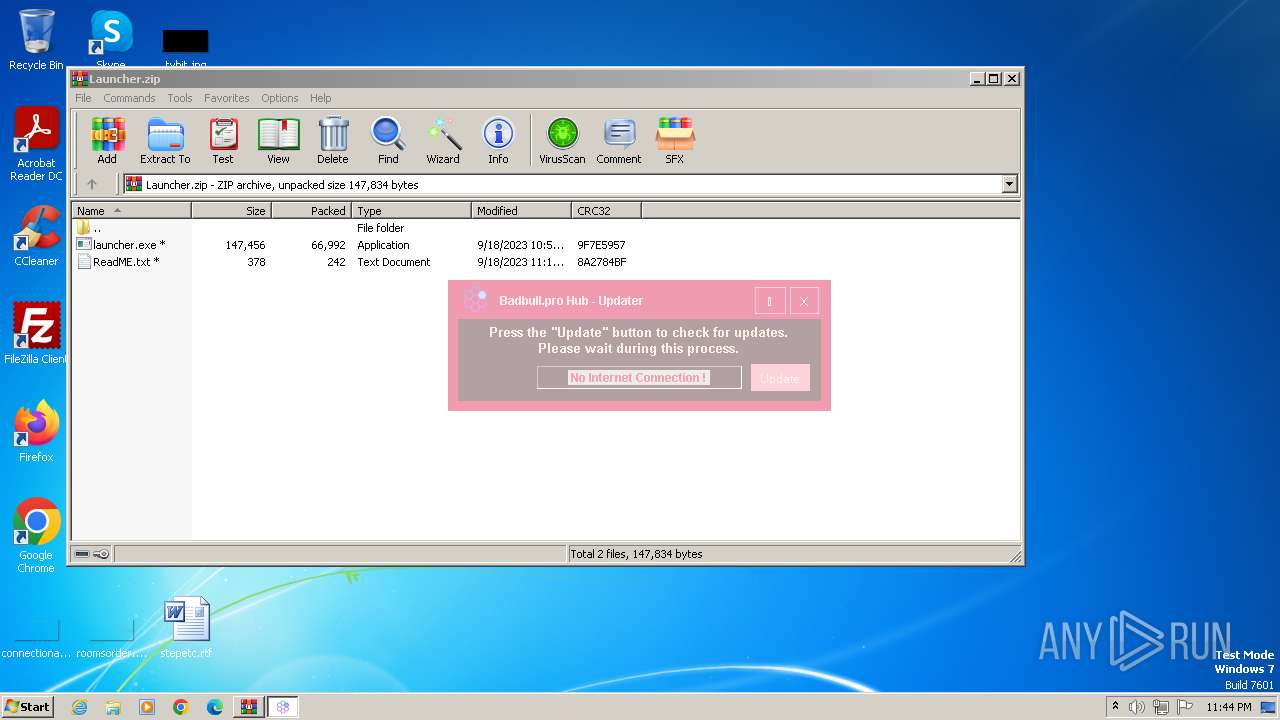
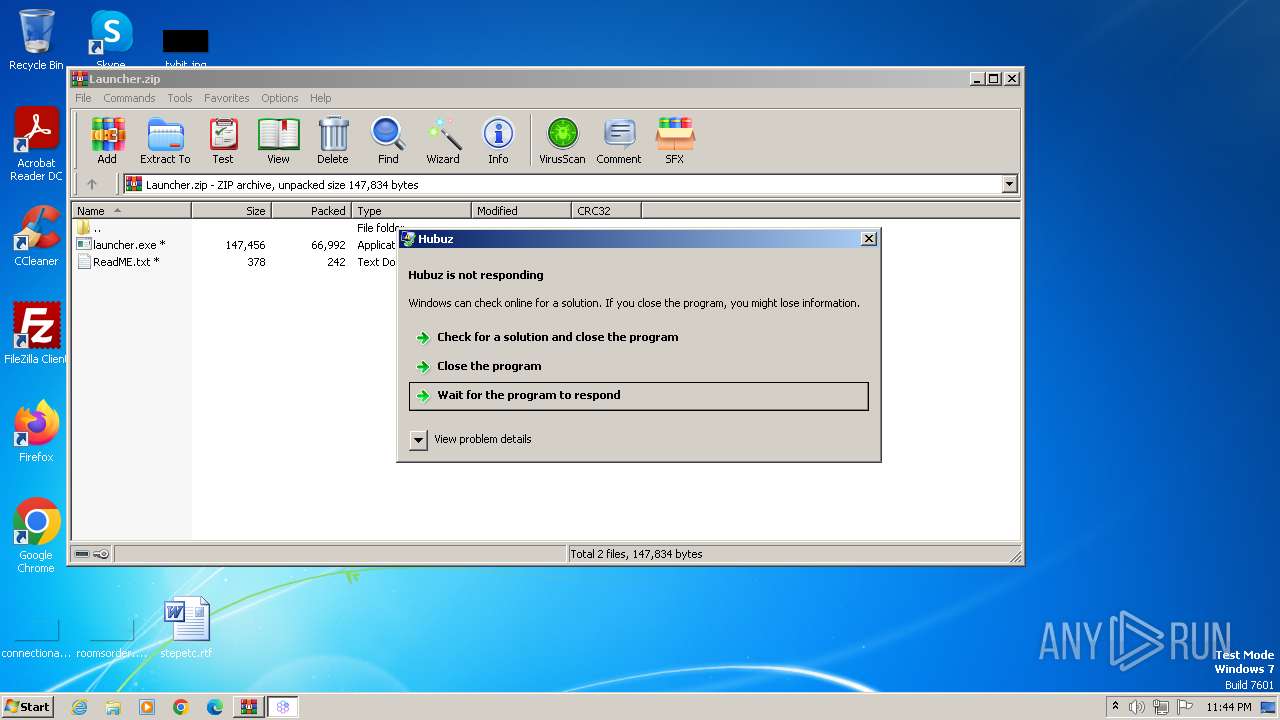
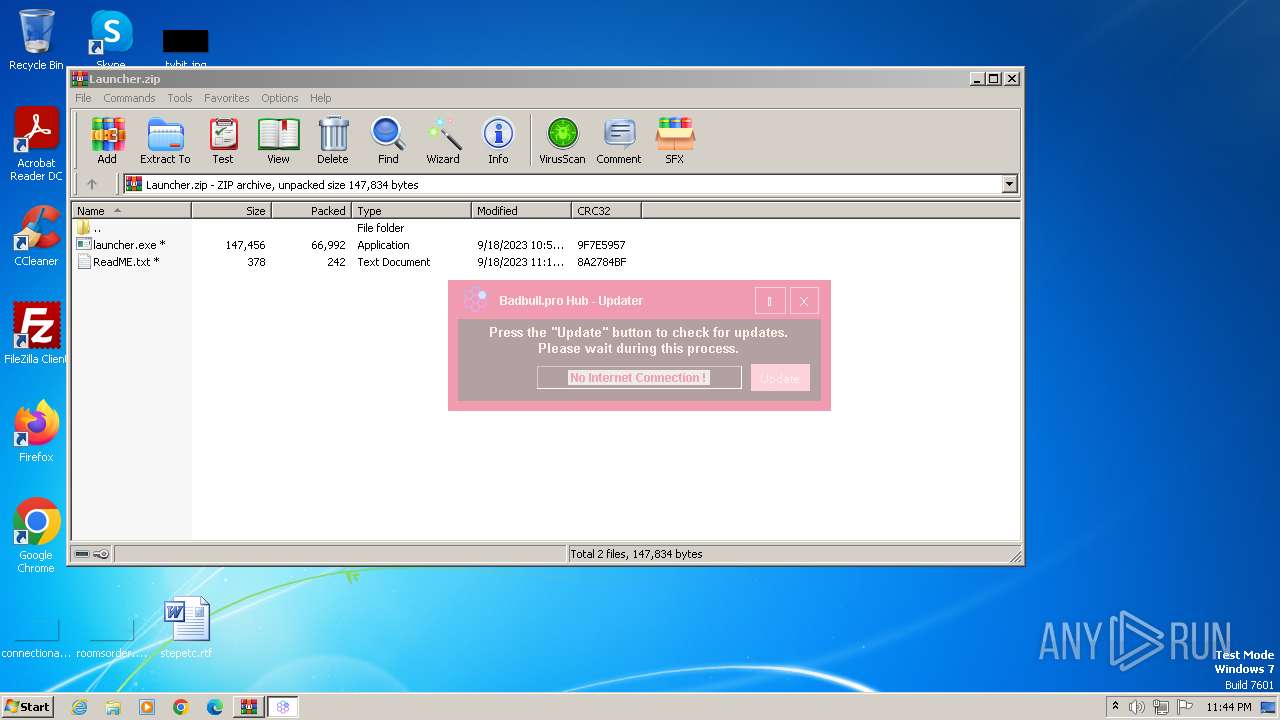
| File name: | Launcher.zip |
| Full analysis: | https://app.any.run/tasks/d6823d8e-c52a-4b49-ad6a-410f6e27c22f |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 23:39:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | C09BCDB9D13C5547503B43F3AAAF505F |
| SHA1: | 07A13FE544651BC4353D8DB7B8A609732FD09C8C |
| SHA256: | 088EE068D6B500D090031B5FF2D50AE7031DEFDDD1B0321EDEE6817B14B10286 |
| SSDEEP: | 1536:/1T/Se9cCWwLYHMzBj/1oLYyu2vZyb9bm84gf6XIaxo9w2CC:/1Vc7PHstduYWvZWmuf6XoB |
MALICIOUS
No malicious indicators.SUSPICIOUS
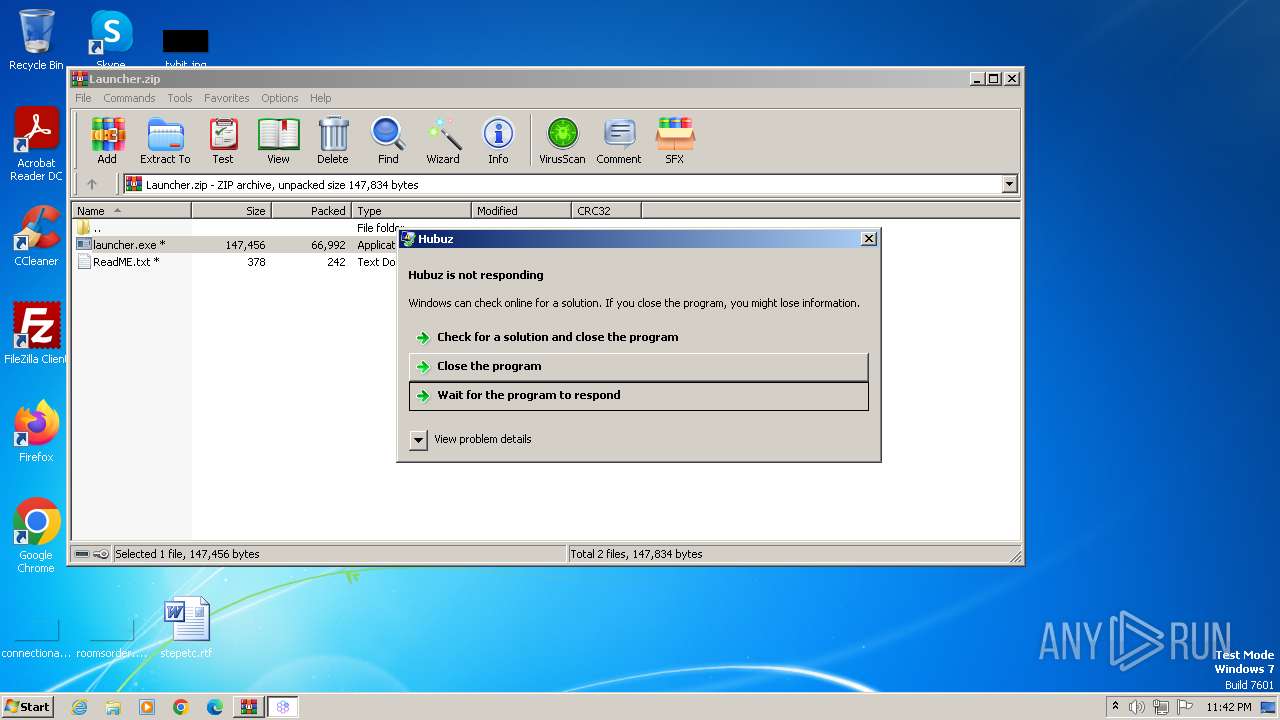
Starts POWERSHELL.EXE for commands execution
- launcher.exe (PID: 2184)
Powershell version downgrade attack
- powershell.exe (PID: 2668)
Reads the Internet Settings
- launcher.exe (PID: 2184)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3872)
- explorer.exe (PID: 3936)
- WINWORD.EXE (PID: 1244)
Reads the computer name
- wmpnscfg.exe (PID: 3872)
- launcher.exe (PID: 2184)
Checks supported languages
- wmpnscfg.exe (PID: 3872)
- launcher.exe (PID: 2184)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 564)
Reads the machine GUID from the registry
- launcher.exe (PID: 2184)
Reads Environment values
- launcher.exe (PID: 2184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2023:09:19 01:18:20 |
| ZipCRC: | 0x8a2784bf |
| ZipCompressedSize: | 242 |
| ZipUncompressedSize: | 378 |
| ZipFileName: | ReadME.txt |
Total processes
58
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 564 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Launcher.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1244 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Documents\develophardware.rtf" | C:\Program Files\microsoft office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2184 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb564.40991\launcher.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb564.40991\launcher.exe | WinRAR.exe | ||||||||||||
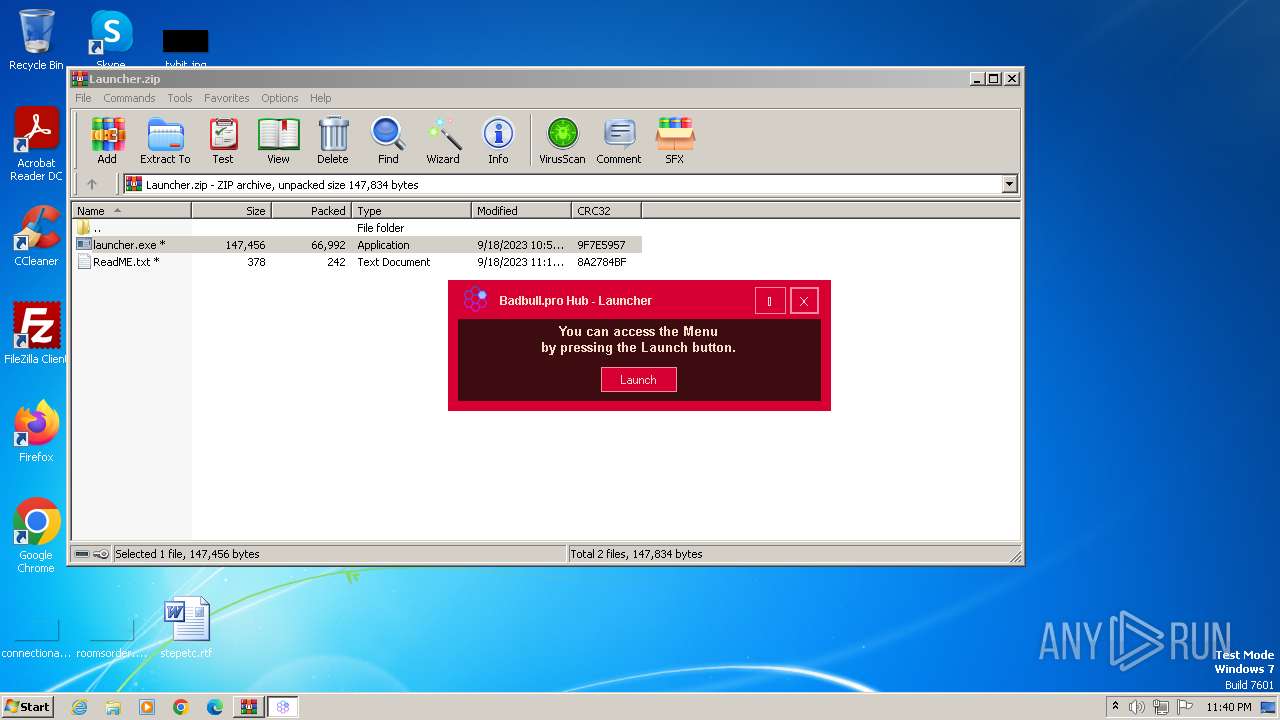
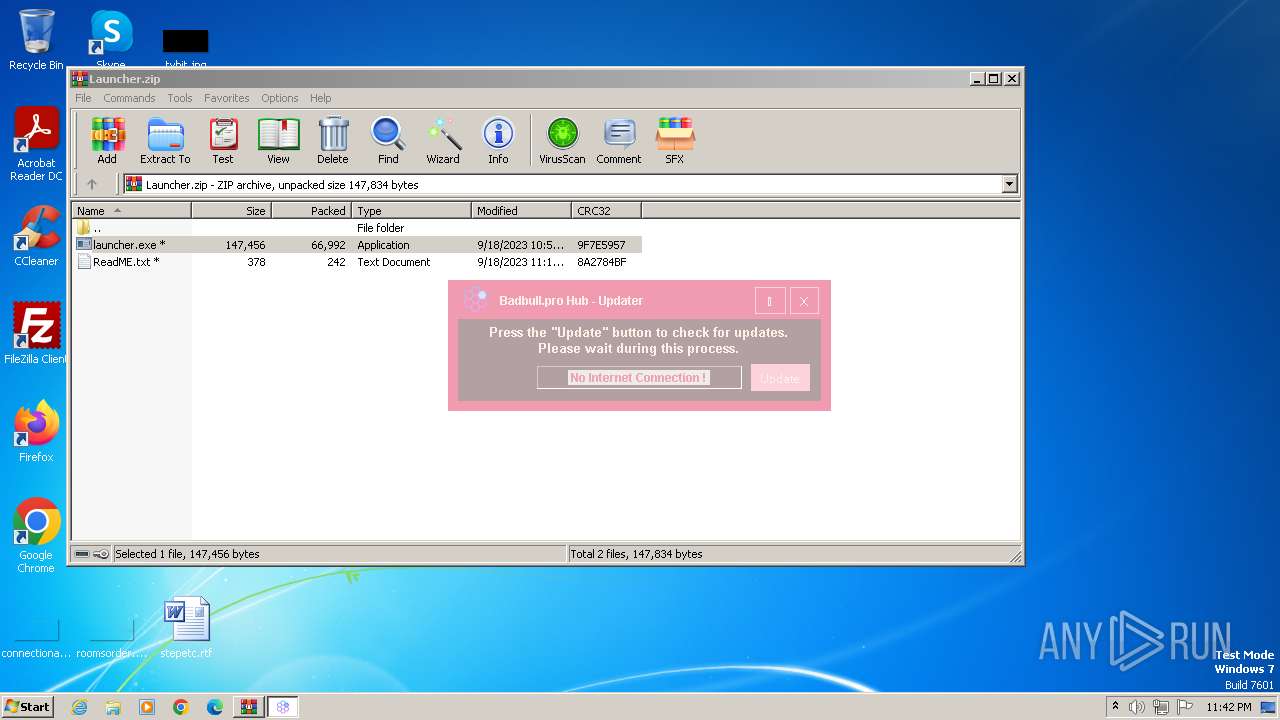
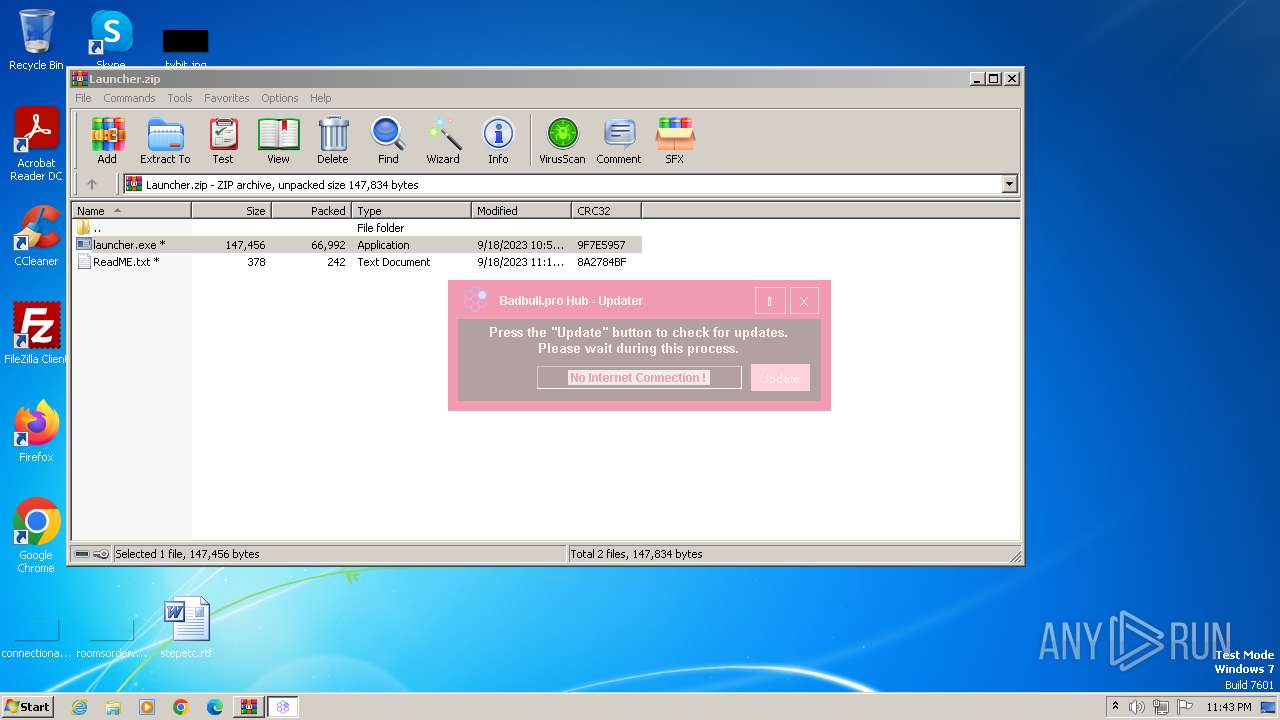
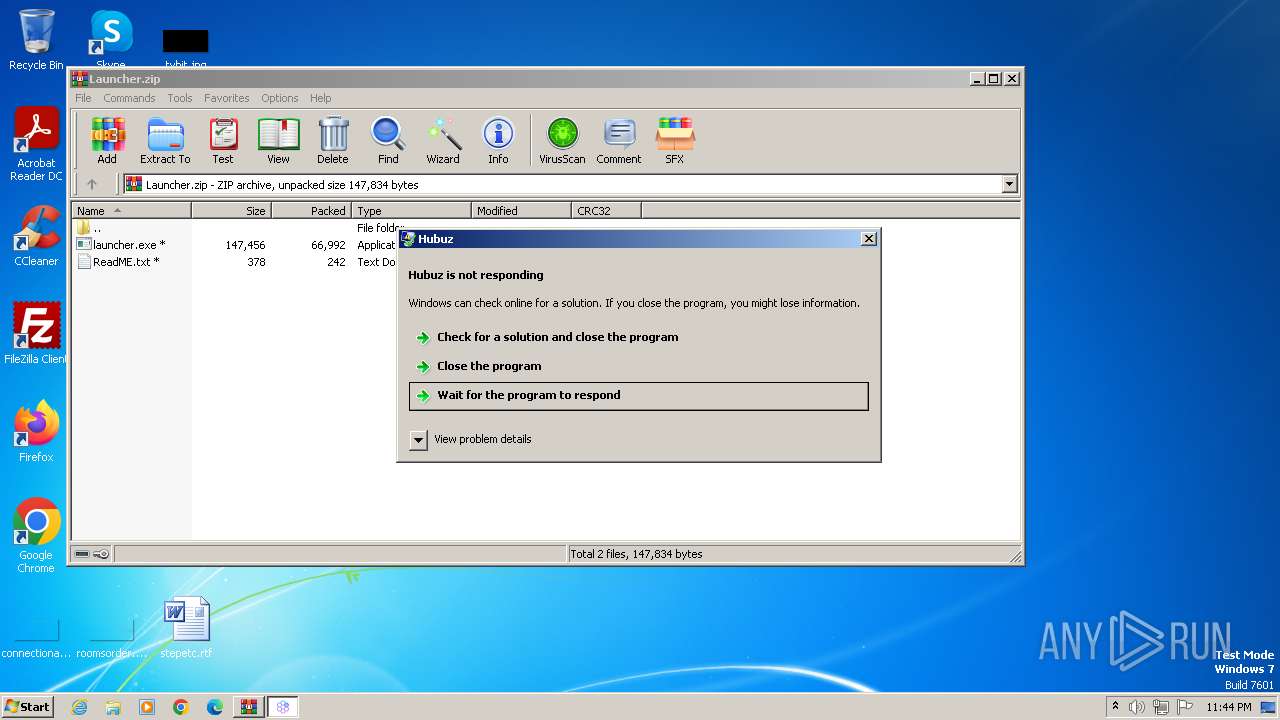
User: admin Integrity Level: HIGH Description: Hubuz Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2628 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb564.40991\launcher.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb564.40991\launcher.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Hubuz Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2668 | "powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3504 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3872 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3936 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 032
Read events
5 776
Write events
107
Delete events
149
Modification events
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
2
Suspicious files
9
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRC719.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1244 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\develophardware.rtf.LNK | binary | |
MD5:E23716DBECD91D15CD6D4E5EF4E93B26 | SHA256:1E2F112F3FDB7A2F4FF6BCD521A0C8CE59AED7BAC4D710273CAD44C2AA9F1CF2 | |||
| 1244 | WINWORD.EXE | C:\Users\admin\Documents\~$velophardware.rtf | binary | |
MD5:BA02BB2D08E544089F5DE5636B22C534 | SHA256:73065CC2AC2B8C5D16B60DCDFA2B9E8FCD223572A02A0016B64BBAF21817A8A3 | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb564.40991\ReadME.txt | text | |
MD5:663821C7A274E6DF340D8D044B953FCE | SHA256:B954E44EBCB1D6FC83CFF6A4E7002AC464147AAD237D2CE809EE6189B491C9A3 | |||
| 2668 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 1244 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:FCDA4E4D362D21B9D981E1D871C434AA | SHA256:3E6959B627C60E1288C71F2FE48E9EC8A2ABBDF646DCB15A55249C5C32EC1A3A | |||
| 2668 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\QRU0LBG7XRC33L1W5EF3.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb564.40991\launcher.exe | executable | |
MD5:B51C8E2023188114A3AFB85DF73B886F | SHA256:62D183E9BFA8EEDFCB7F2AD75C419F38088E8A600DDE6286F122BD7B567144F5 | |||
| 1244 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{3A3473E4-BB50-49AB-AEDE-0E595D293E5C}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 1244 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:BDF576729187A8C4A12C9B76CFABD058 | SHA256:315385B9EB831B8D80E593FEE7104D7E0F47C340D8D127696A56374B9BD3EA56 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 95.101.148.135:80 | armmf.adobe.com | Akamai International B.V. | NL | unknown |
2184 | launcher.exe | 142.250.185.132:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |
www.google.com |
| whitelisted |
dns.msftncsi.com |
| shared |