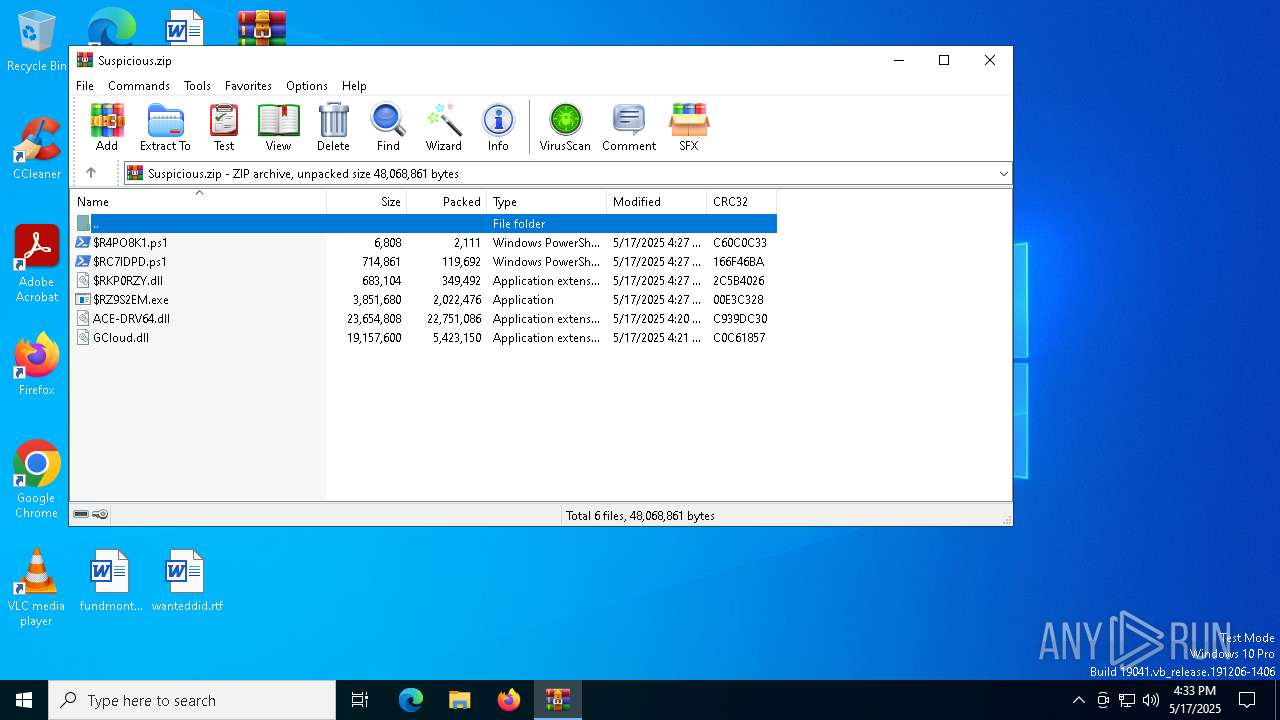
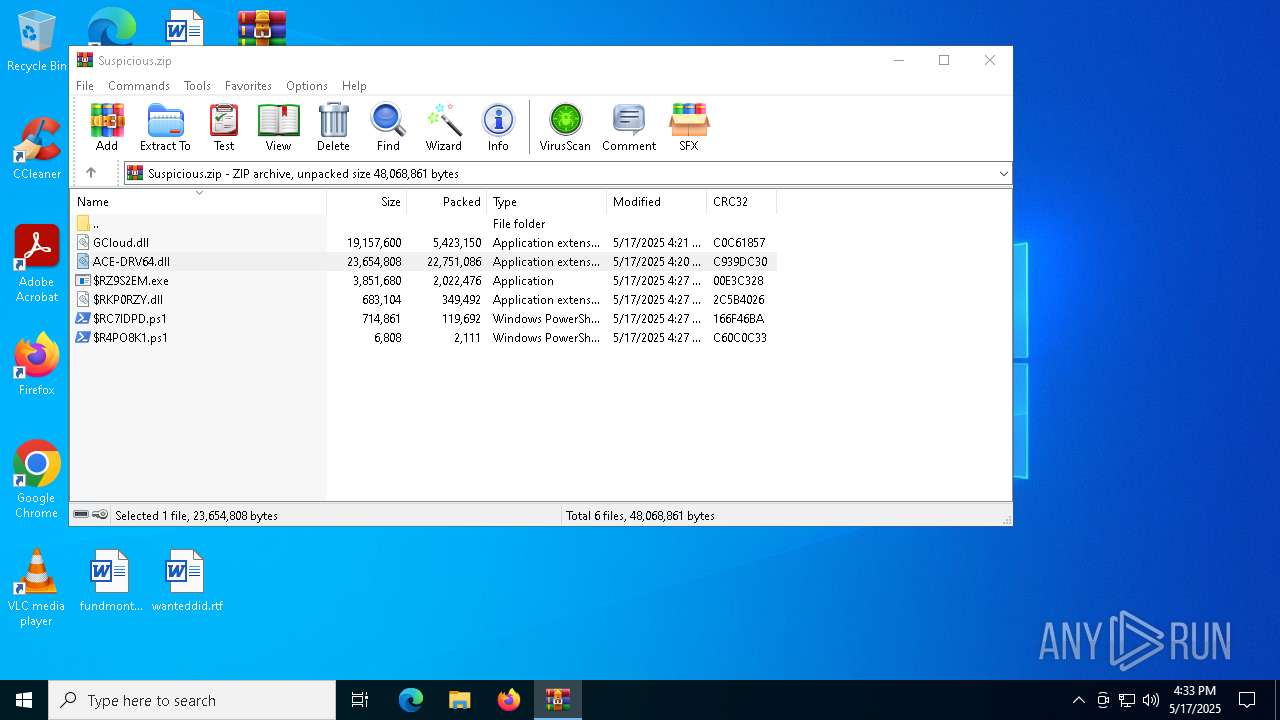
| File name: | Suspicious.zip |
| Full analysis: | https://app.any.run/tasks/141e69e6-00bb-4493-a51d-fd90c9aa4686 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 16:33:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6A6264E4B645CA22735B8C410DBE1AE3 |
| SHA1: | BD5F63C54AF7A17EF25C282E6CA1B53887025D0A |
| SHA256: | 088E1730D40DCEB45F8F42771FB6CC5FBC66A7DCC0694DB950AEE989479A9B2D |
| SSDEEP: | 196608:SID54KIN4+WRz9vnX6C1nrgxKLWjWXula92o+4LKhGXObAC:SIyK7+49PKCCgyjSlw4LKsmAC |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 7668)
- powershell.exe (PID: 7532)
SUSPICIOUS
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 7668)
Checks whether the computer is part of a domain (POWERSHELL)
- powershell.exe (PID: 7668)
INFO
Checks supported languages
- $RZ9S2EM.exe (PID: 7492)
The sample compiled with english language support
- WinRAR.exe (PID: 7300)
Manual execution by a user
- $RZ9S2EM.exe (PID: 7492)
- powershell.exe (PID: 7532)
- powershell.exe (PID: 7668)
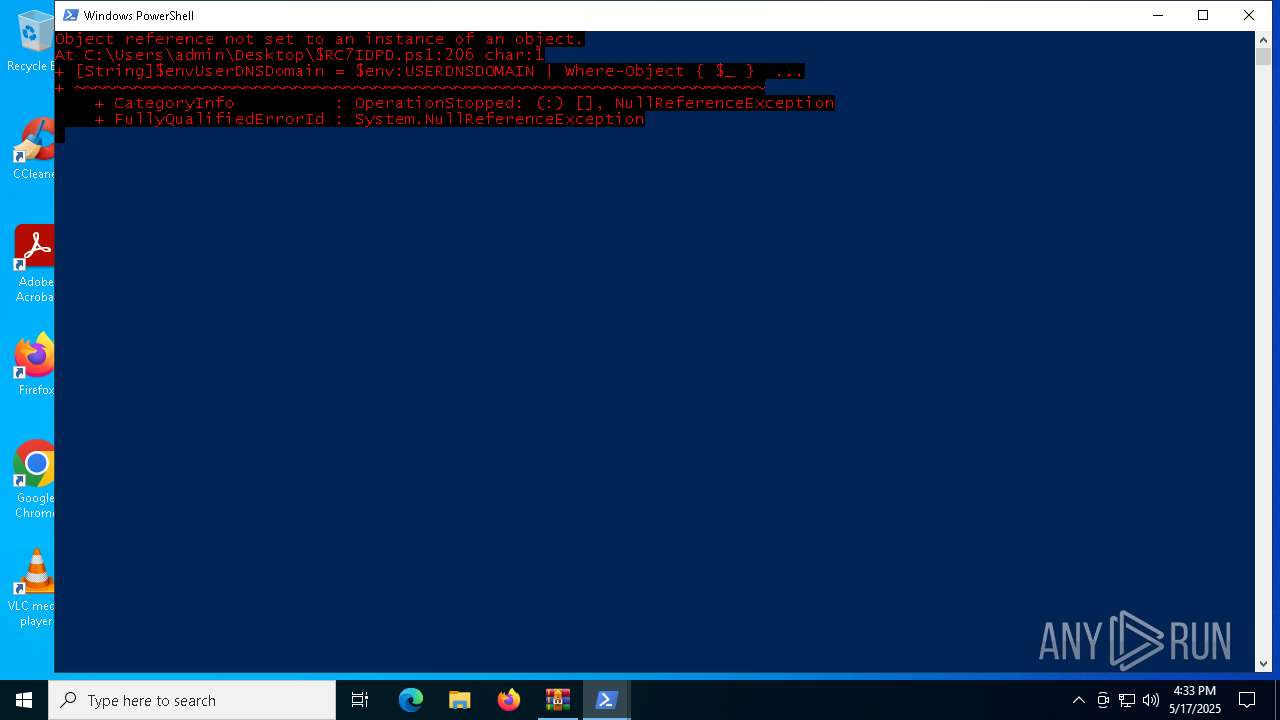
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7532)
- powershell.exe (PID: 7668)
Reads Windows Product ID
- powershell.exe (PID: 7668)
Checks proxy server information
- slui.exe (PID: 8108)
Reads the software policy settings
- slui.exe (PID: 8108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:17 11:27:40 |
| ZipCRC: | 0xc60c0c33 |
| ZipCompressedSize: | 2111 |
| ZipUncompressedSize: | 6808 |
| ZipFileName: | $R4PO8K1.ps1 |
Total processes
126
Monitored processes
7
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7300 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Suspicious.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7492 | "C:\Users\admin\Desktop\$RZ9S2EM.exe" | C:\Users\admin\Desktop\$RZ9S2EM.exe | — | explorer.exe | |||||||||||
User: admin Company: ANTICHEATEXPERT.COM Integrity Level: MEDIUM Description: ACE-Helper Exit code: 0 Version: 1.0.2112.1010 Modules
| |||||||||||||||
| 7532 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\$R4PO8K1.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7668 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\$RC7IDPD.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7676 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8108 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 593
Read events
16 584
Write events
9
Delete events
0
Modification events
| (PID) Process: | (7300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Suspicious.zip | |||
| (PID) Process: | (7300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
Executable files
0
Suspicious files
8
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7532 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF110bd4.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 7532 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_12lw2npi.u43.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7532 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\0TPZLY7MG9MBKIYEZ3GU.temp | binary | |
MD5:27BDD46AB25A4AFAEA033C84BFC7E7F0 | SHA256:1478C5F24203C03F70F6C0F673AAC0DFF8C8ACA08FF67996791A7788B0A8C08A | |||
| 7668 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:55F1F4A84234FD7F7B67FF82D2D56DDF | SHA256:0B6E6AD01A7878A95E58901FDA7CF9F30C1AA54FA84F3C41DB2689B7C5171B10 | |||
| 7532 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2mm3hwi1.3j3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7532 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:27BDD46AB25A4AFAEA033C84BFC7E7F0 | SHA256:1478C5F24203C03F70F6C0F673AAC0DFF8C8ACA08FF67996791A7788B0A8C08A | |||
| 7668 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF110fad.TMP | binary | |
MD5:27BDD46AB25A4AFAEA033C84BFC7E7F0 | SHA256:1478C5F24203C03F70F6C0F673AAC0DFF8C8ACA08FF67996791A7788B0A8C08A | |||
| 7532 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:3F95A05381C6D14195F6A1538F5FBADE | SHA256:0E753E9AD3EDE811C17D076B462F85321B8F559C2E462AF0990A1653573A525F | |||
| 7668 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_42ji0g4f.j1r.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7532 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_c2znbawc.eli.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
22
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6540 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8108 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |