| File name: | SetupFile_637708.exe |
| Full analysis: | https://app.any.run/tasks/e50072e2-8cf5-47bf-b5ea-8824242d2ea9 |
| Verdict: | Malicious activity |
| Analysis date: | August 20, 2024, 15:00:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 8477C4DAAFF92F6F602CB418912D3F06 |
| SHA1: | 19E0E759F147FCB9D23258D39CD878CC08B8F8E8 |
| SHA256: | 088AD56DECBED8C4783D415A1B4972AEBF1EDE8B846BA0100090A6F2085266FE |
| SSDEEP: | 49152:4sj5i3SBtbJGA4fm5mG/4m2N8Deis67uA+1DdJxpM5lSLmvjamdU9q8jjijv7+gP:VR9gI6B8EW |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- SetupFile_637708.exe (PID: 3356)
- SetupFile_637708.exe (PID: 7052)
Searches for installed software
- SetupFile_637708.exe (PID: 3356)
- SetupFile_637708.exe (PID: 7052)
Reads the date of Windows installation
- SetupFile_637708.exe (PID: 3356)
- SetupFile_637708.exe (PID: 7052)
Application launched itself
- SetupFile_637708.exe (PID: 3356)
Executable content was dropped or overwritten
- DivevUtility.exe (PID: 6048)
- SetupFile_637708.exe (PID: 7052)
Creates/Modifies COM task schedule object
- DivevUtility.exe (PID: 6048)
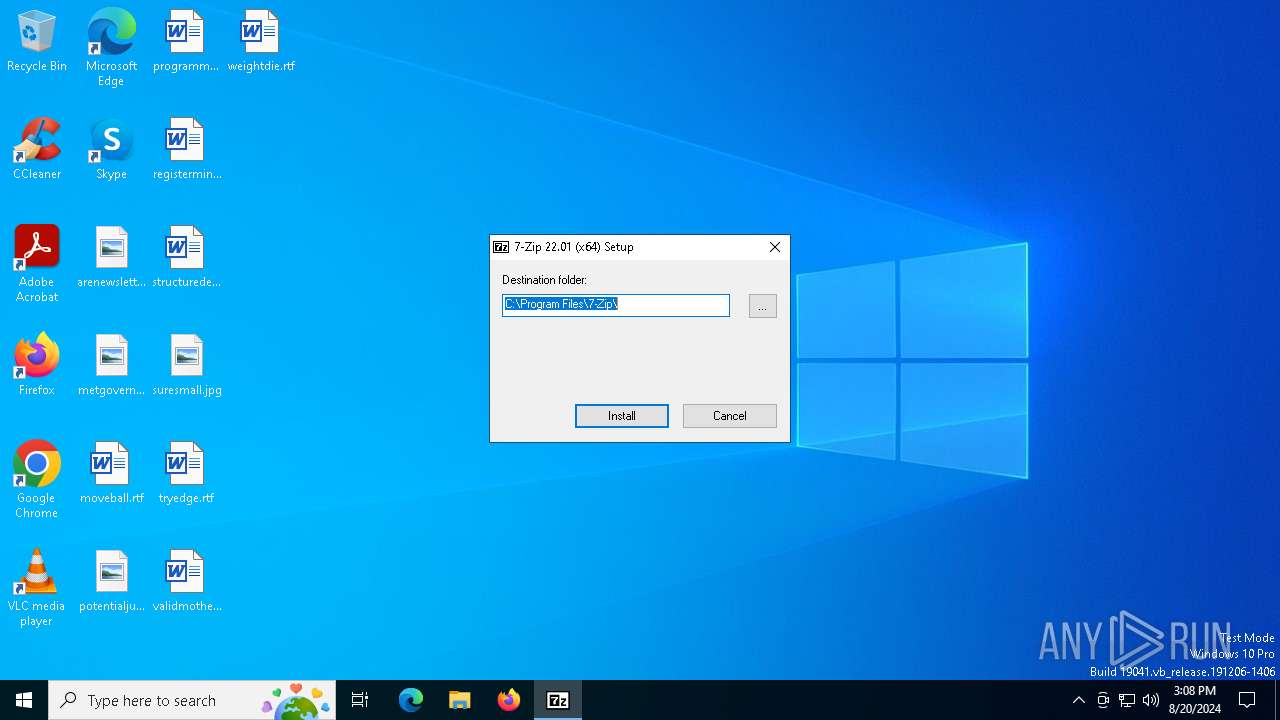
Drops 7-zip archiver for unpacking
- DivevUtility.exe (PID: 6048)
- SetupFile_637708.exe (PID: 7052)
Drops the executable file immediately after the start
- SetupFile_637708.exe (PID: 7052)
- DivevUtility.exe (PID: 6048)
Creates a software uninstall entry
- DivevUtility.exe (PID: 6048)
INFO
Reads the computer name
- SetupFile_637708.exe (PID: 3356)
- SetupFile_637708.exe (PID: 7052)
- DivevUtility.exe (PID: 6048)
Checks supported languages
- SetupFile_637708.exe (PID: 3356)
- SetupFile_637708.exe (PID: 7052)
- DivevUtility.exe (PID: 6048)
Process checks computer location settings
- SetupFile_637708.exe (PID: 3356)
- SetupFile_637708.exe (PID: 7052)
Creates files in the program directory
- SetupFile_637708.exe (PID: 7052)
- DivevUtility.exe (PID: 6048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:08:06 12:43:58+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 7758848 |
| InitializedDataSize: | 421888 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x74c100 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Dive Utility Company Solutions |
| FileDescription: | Dive Utility |
| InternalName: | DiveUtility.exe |
| LegalCopyright: | © 2024 |
| OriginalFileName: | DiveUtility.exe |
| ProductName: | Dive Utility |
| FileVersion: | 1.0.0.0 |
| ProductVersion: | 1.0.0.0 |
Total processes
111
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3356 | "C:\Users\admin\AppData\Local\Temp\SetupFile_637708.exe" | C:\Users\admin\AppData\Local\Temp\SetupFile_637708.exe | — | explorer.exe | |||||||||||
User: admin Company: Dive Utility Company Solutions Integrity Level: MEDIUM Description: Dive Utility Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6048 | "C:\Program Files (x86)\DiveCuriousirzUtility\DivevUtility.exe" | C:\Program Files (x86)\DiveCuriousirzUtility\DivevUtility.exe | SetupFile_637708.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Installer Exit code: 0 Version: 22.01 Modules
| |||||||||||||||
| 7052 | "C:\Users\admin\AppData\Local\Temp\SetupFile_637708.exe" --upd | C:\Users\admin\AppData\Local\Temp\SetupFile_637708.exe | SetupFile_637708.exe | ||||||||||||
User: admin Company: Dive Utility Company Solutions Integrity Level: HIGH Description: Dive Utility Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
6 038
Read events
6 001
Write events
37
Delete events
0
Modification events
| (PID) Process: | (3356) SetupFile_637708.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3356) SetupFile_637708.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3356) SetupFile_637708.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3356) SetupFile_637708.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7052) SetupFile_637708.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7052) SetupFile_637708.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (7052) SetupFile_637708.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (7052) SetupFile_637708.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6048) DivevUtility.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path64 |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (6048) DivevUtility.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip\ | |||
Executable files
10
Suspicious files
2
Text files
97
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6048 | DivevUtility.exe | C:\Program Files\7-Zip\Lang\an.txt | text | |
MD5:BF8564B2DAD5D2506887F87AEE169A0A | SHA256:0E8DD119DFA6C6C1B3ACA993715092CDF1560947871092876D309DBC1940A14A | |||
| 6048 | DivevUtility.exe | C:\Program Files\7-Zip\7-zip.chm | binary | |
MD5:34208890A28244903621CD32CC3FBDFC | SHA256:4B6939646570C9DDB5BFD39B8503EED99D8C64337E72F6DD4F9DDCFB4AC76703 | |||
| 6048 | DivevUtility.exe | C:\Program Files\7-Zip\History.txt | text | |
MD5:B1206A5ABF93BC64601A3CAA2DFF47D4 | SHA256:24A8A7C00F0BB8AC3096F58F53BD47FA392B8D220C1C43D372100BD692C68E5F | |||
| 6048 | DivevUtility.exe | C:\Program Files\7-Zip\Lang\bg.txt | text | |
MD5:833AFB4F88FDB5F48245C9B65577DC19 | SHA256:4DCABCC8AB8069DB79143E4C62B6B76D2CF42666A09389EACFC35074B61779E3 | |||
| 6048 | DivevUtility.exe | C:\Program Files\7-Zip\Lang\ba.txt | text | |
MD5:D83B65AC086DA0C94D6EB57BEE669C2B | SHA256:2901B54F7621C95429658CB4EDB28ABD0CB5B6E257C7D9A364FC468A8B86BAAE | |||
| 6048 | DivevUtility.exe | C:\Program Files\7-Zip\Lang\az.txt | text | |
MD5:81B732A8B4206FB747BFBFE524DDE192 | SHA256:CAEC460E73BD0403C2BCDE7E773459BEA9112D1BFACBE413D4F21E51A5762BA6 | |||
| 6048 | DivevUtility.exe | C:\Program Files\7-Zip\Lang\ca.txt | text | |
MD5:1657720023A267B5B625DE17BF292299 | SHA256:ED8748DA8FA99DB775FF621D3E801E2830E6C04DA42C0B701095580191A700A6 | |||
| 6048 | DivevUtility.exe | C:\Program Files\7-Zip\Lang\br.txt | text | |
MD5:C2EB67D788756BE5ECAA0A8CFB3D1E0B | SHA256:0F6BF6749C42C844980DB32EE56CADC987CE245EF650BC7D626D56468A7CBE6A | |||
| 6048 | DivevUtility.exe | C:\Program Files\7-Zip\Lang\be.txt | text | |
MD5:3C21135144AC7452E7DB66F0214F9D68 | SHA256:D095879B8BBC67A1C9875C5E9896942BACF730BD76155C06105544408068C59E | |||
| 6048 | DivevUtility.exe | C:\Program Files\7-Zip\Lang\bn.txt | text | |
MD5:D0E788F64268D15B4391F052B1F4B18A | SHA256:216CC780E371DC318C8B15B84DE8A5EC0E28F712B3109A991C8A09CDDAA2A81A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
65
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4876 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 52.165.165.26:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 13.85.23.206:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |