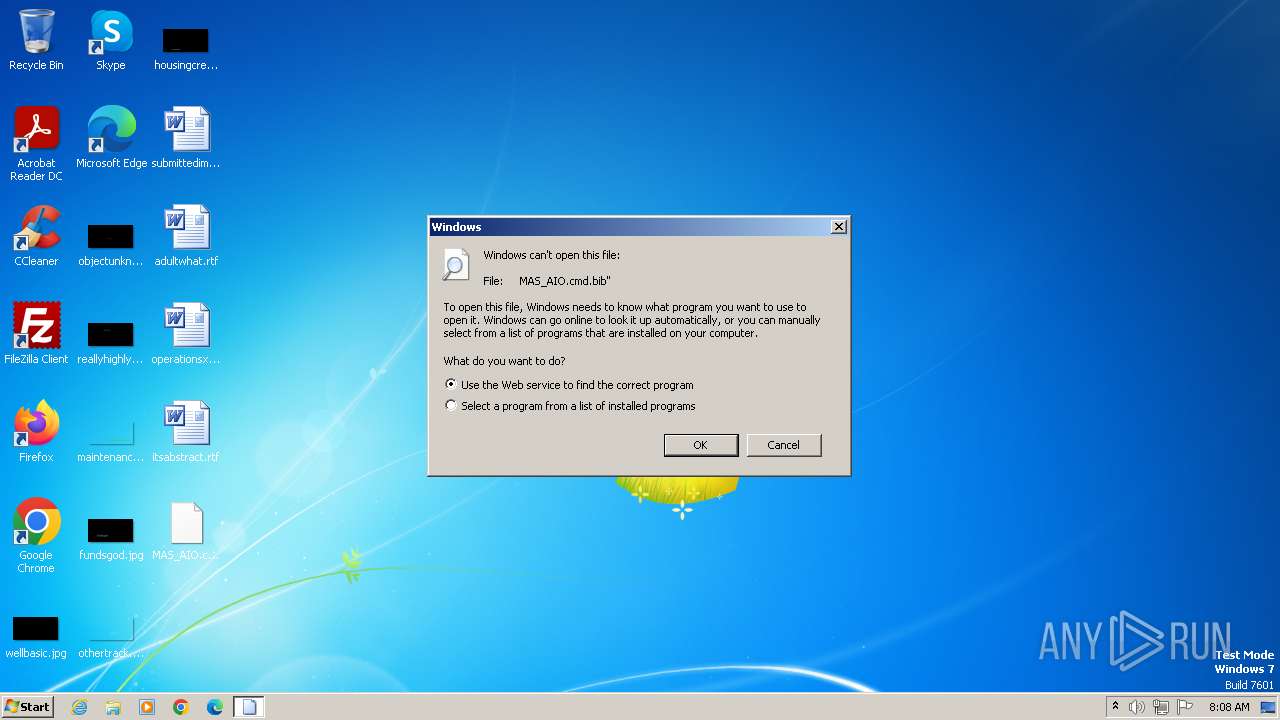
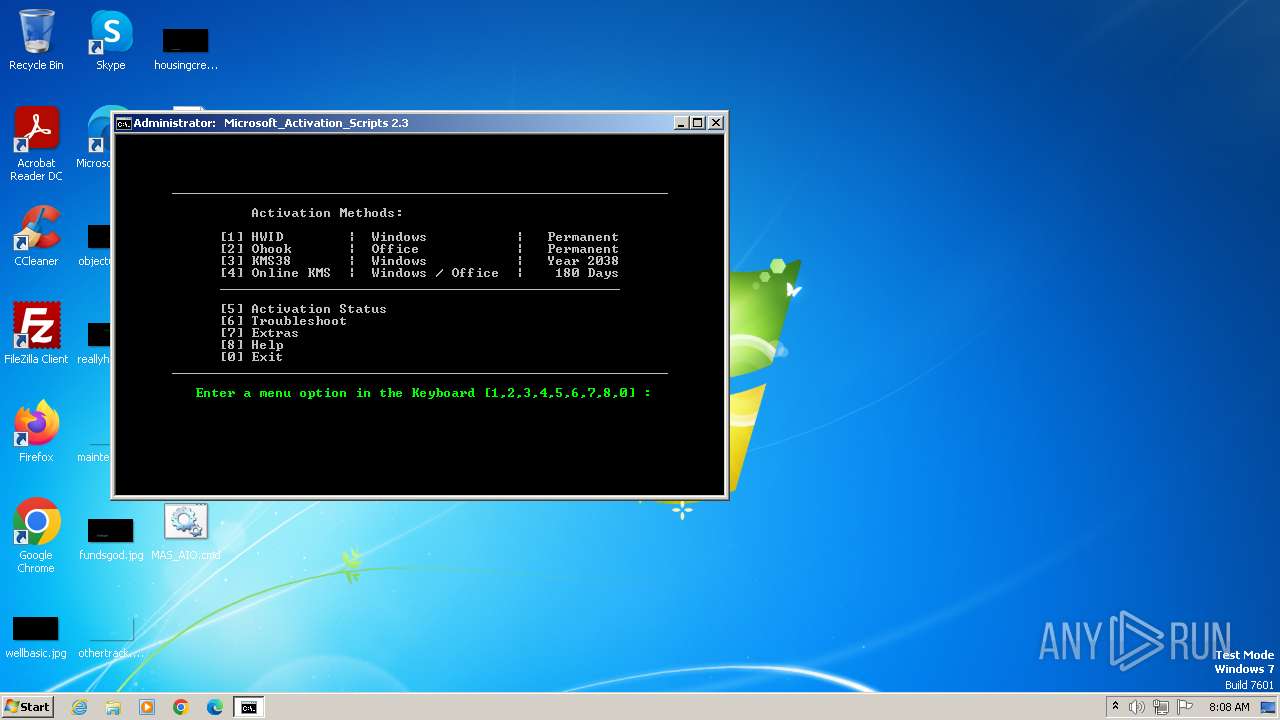
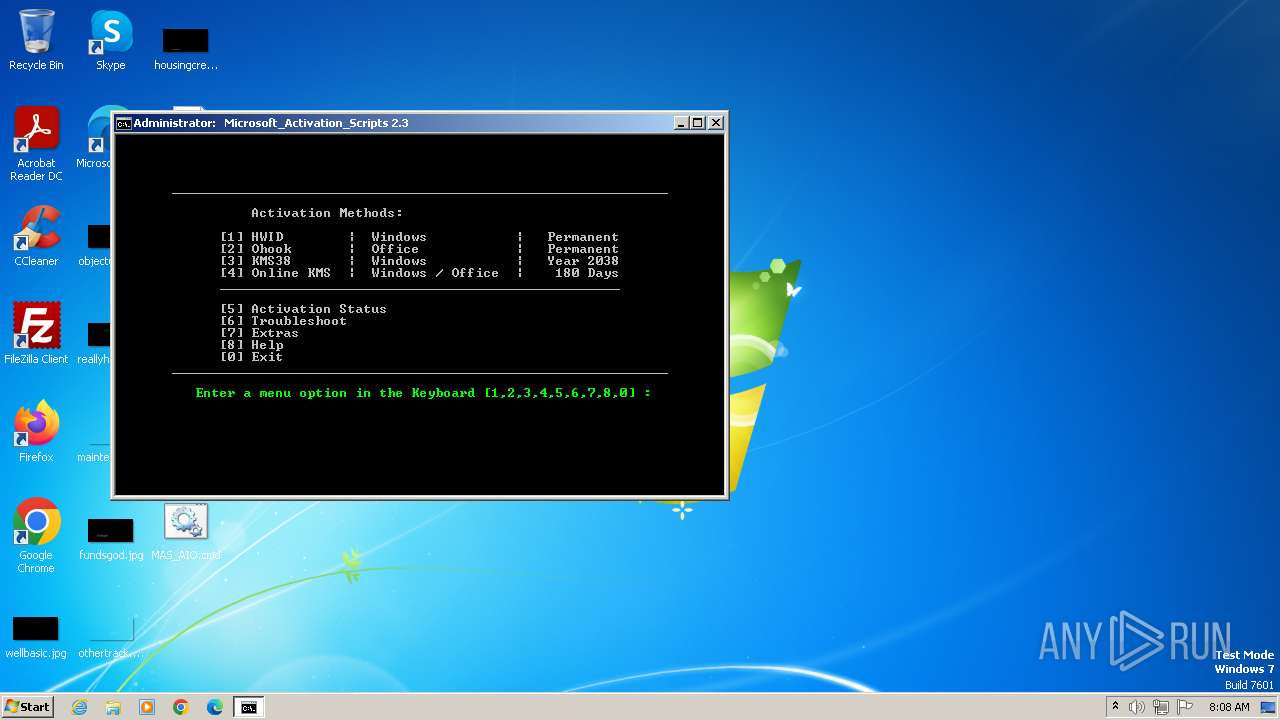
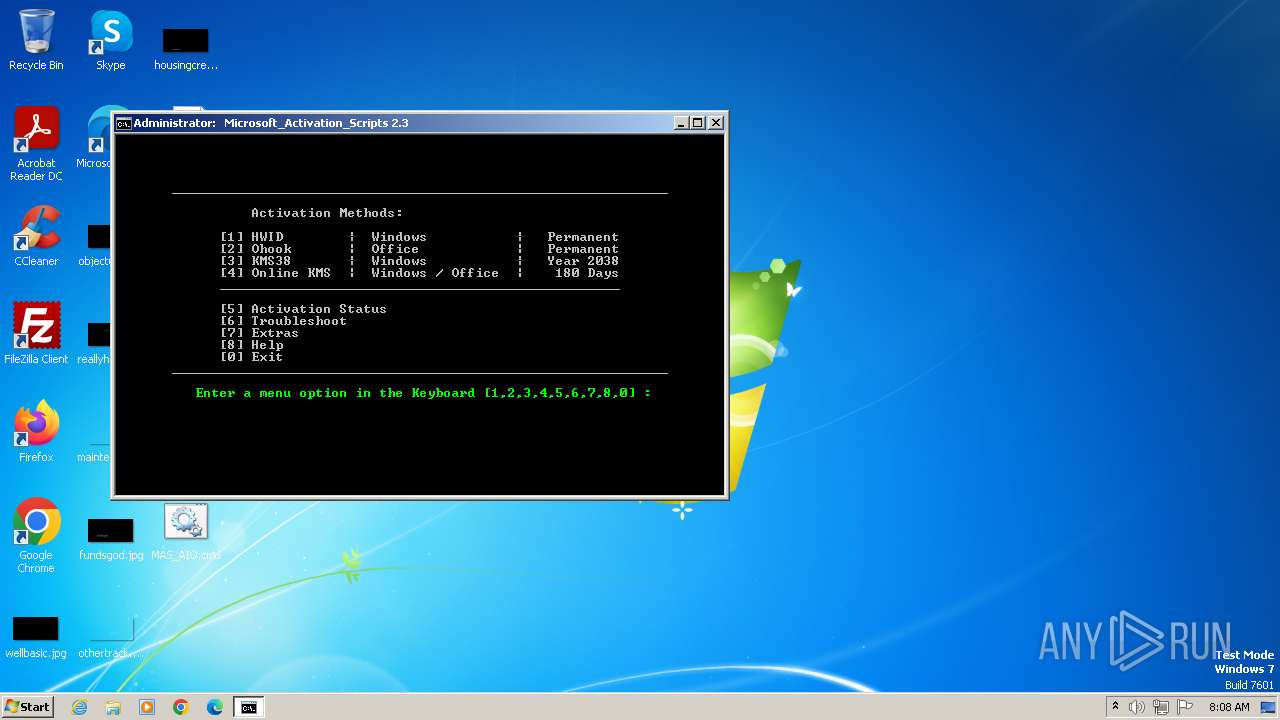
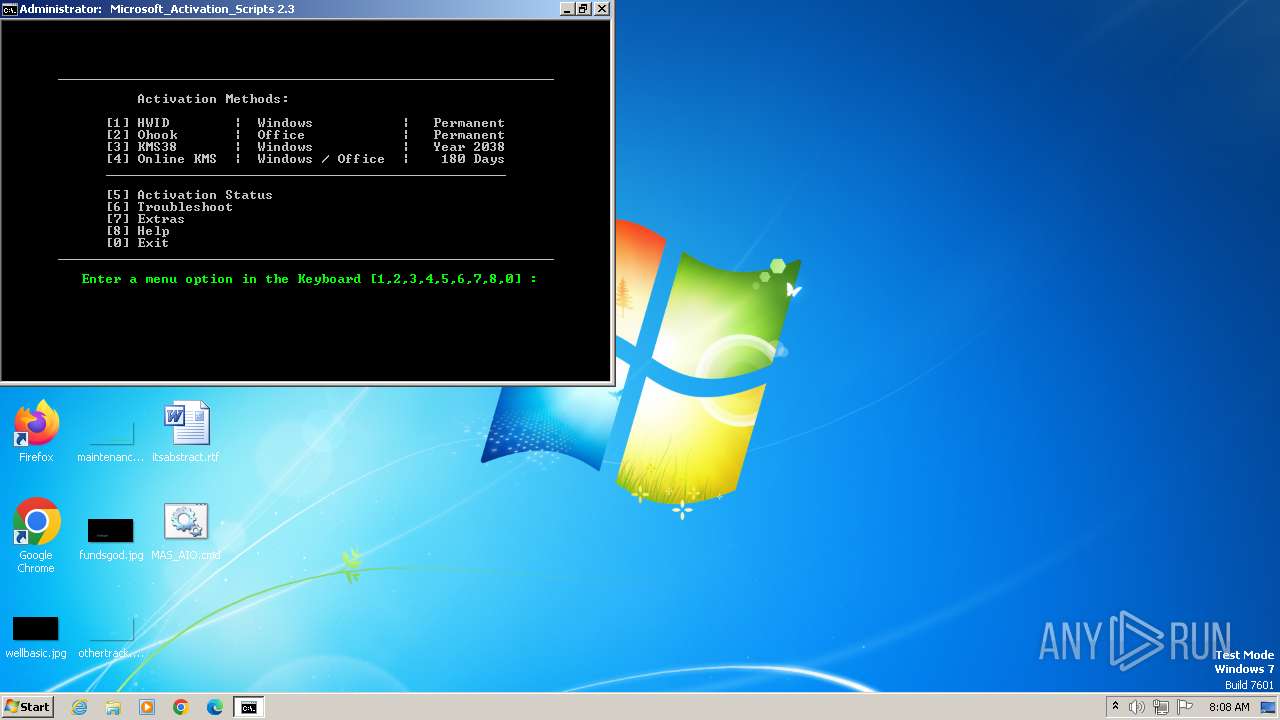
| File name: | MAS_AIO.cmd |
| Full analysis: | https://app.any.run/tasks/0e8327a3-4f58-4b00-94b2-b348e6ffc742 |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2023, 07:08:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 39FDABF84EDBDA37412FE76E8167376B |
| SHA1: | 401EA2A62CBED59C2A2D992B97822C388233931F |
| SHA256: | 08838F181A502B6738C8776F71FBC47512E46F401C1F02DA7C9C5737D9432211 |
| SSDEEP: | 3072:c1j34REl7N/VPyueR/iNiYDdYd3MPfsavJbJuAMTVFp6zGDNSCE2K0xOuW7EOGJ9:gvFQueR6TudUbJu9p6zGDNS0KgOu6m |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- cmd.exe (PID: 1432)
- cmd.exe (PID: 2100)
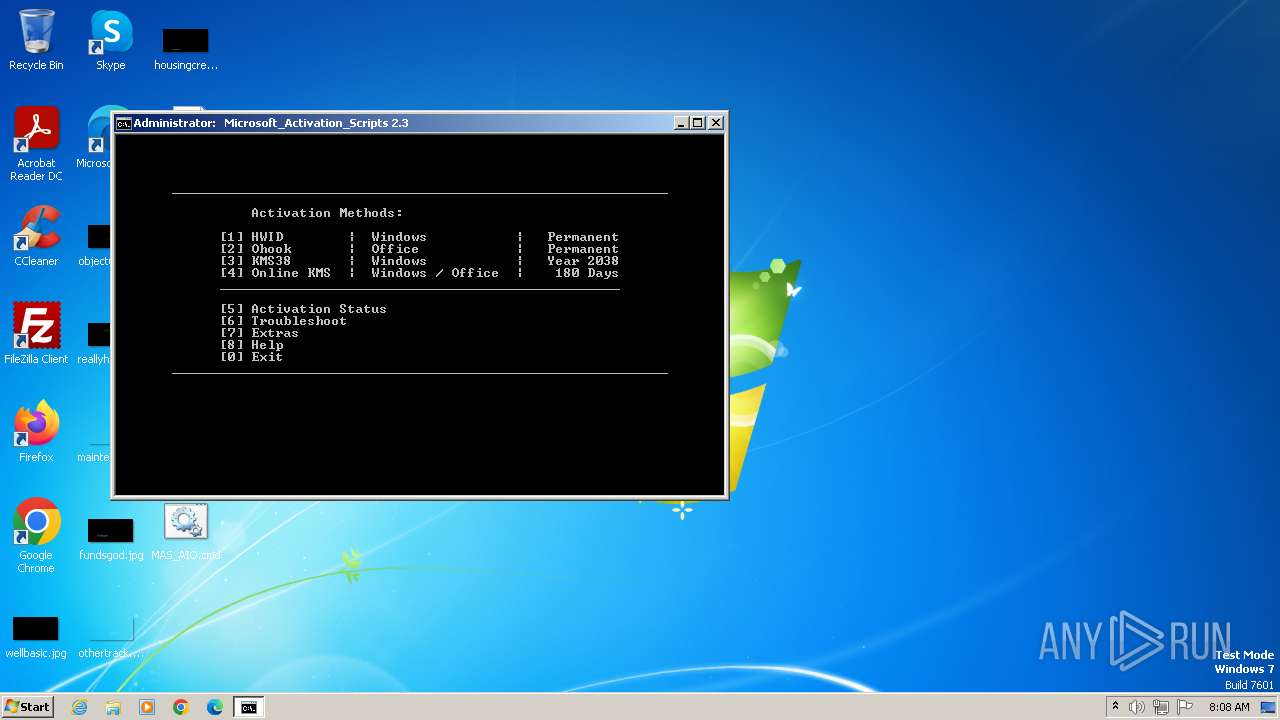
Starts SC.EXE for service management
- cmd.exe (PID: 1432)
- cmd.exe (PID: 2100)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1432)
- cmd.exe (PID: 2100)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1432)
- powershell.exe (PID: 1824)
- cmd.exe (PID: 2100)
Executing commands from ".cmd" file
- cmd.exe (PID: 1432)
- powershell.exe (PID: 1824)
- cmd.exe (PID: 2100)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1432)
- cmd.exe (PID: 2100)
Powershell version downgrade attack
- powershell.exe (PID: 1824)
- powershell.exe (PID: 2696)
- powershell.exe (PID: 3372)
- powershell.exe (PID: 328)
- powershell.exe (PID: 3940)
- powershell.exe (PID: 1248)
- powershell.exe (PID: 3188)
Reads the Internet Settings
- powershell.exe (PID: 1824)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3160)
- cmd.exe (PID: 1432)
- explorer.exe (PID: 3596)
Checks supported languages
- wmpnscfg.exe (PID: 3160)
- mode.com (PID: 3632)
- mode.com (PID: 2200)
- mode.com (PID: 3424)
- mode.com (PID: 1140)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3160)
Reads the computer name
- wmpnscfg.exe (PID: 3160)
Checks operating system version
- cmd.exe (PID: 1432)
- cmd.exe (PID: 2100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .bib/bibtex/txt | | | BibTeX references (100) |
|---|
Total processes
103
Monitored processes
61
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | find "127.69.2.3" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 328 | powershell.exe write-host -back '"Red"' -fore '"white"' '"==== ERROR ===="' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 852 | C:\Windows\system32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1044 | C:\Windows\system32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1140 | find /i "/" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1140 | mode 76, 30 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1248 | powershell.exe write-host -back '"Red"' -fore '"white"' '"==== ERROR ===="' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1432 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\MAS_AIO.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1432 | C:\Windows\system32\cmd.exe /c reg query "HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders" /v Desktop | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1480 | C:\Windows\system32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
9 258
Read events
8 869
Write events
386
Delete events
3
Modification events
| (PID) Process: | (3160) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{8465B67A-2289-41DA-915B-FD0873E77922}\{7D0EC15D-73D5-4D6A-8623-3BA4A7343382} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3160) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{8465B67A-2289-41DA-915B-FD0873E77922} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3160) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{BF8CE93F-19E2-4D7C-9D14-992E6A75265C} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1824) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1824) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1824) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1824) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1824) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2696) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3372) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
22
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1824 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\GSRY4XY74CMOOE55Y12V.temp | binary | |
MD5:CAEA3B1F09925DA2A47C2B8B890AB890 | SHA256:66F29B00CBB7B1DED878F96AAC6F52907C088DE194A1FD0CD6E1FF1916047549 | |||
| 1824 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:CAEA3B1F09925DA2A47C2B8B890AB890 | SHA256:66F29B00CBB7B1DED878F96AAC6F52907C088DE194A1FD0CD6E1FF1916047549 | |||
| 1824 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1f1db2.TMP | binary | |
MD5:CAEA3B1F09925DA2A47C2B8B890AB890 | SHA256:66F29B00CBB7B1DED878F96AAC6F52907C088DE194A1FD0CD6E1FF1916047549 | |||
| 328 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1f6ccc.TMP | binary | |
MD5:CAEA3B1F09925DA2A47C2B8B890AB890 | SHA256:66F29B00CBB7B1DED878F96AAC6F52907C088DE194A1FD0CD6E1FF1916047549 | |||
| 3372 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1f5405.TMP | binary | |
MD5:CAEA3B1F09925DA2A47C2B8B890AB890 | SHA256:66F29B00CBB7B1DED878F96AAC6F52907C088DE194A1FD0CD6E1FF1916047549 | |||
| 3372 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:CAEA3B1F09925DA2A47C2B8B890AB890 | SHA256:66F29B00CBB7B1DED878F96AAC6F52907C088DE194A1FD0CD6E1FF1916047549 | |||
| 3940 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\H2AGURC5I0QLTQDX010C.temp | binary | |
MD5:CAEA3B1F09925DA2A47C2B8B890AB890 | SHA256:66F29B00CBB7B1DED878F96AAC6F52907C088DE194A1FD0CD6E1FF1916047549 | |||
| 2696 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\UE5AJJM3PP2IYTRWG4IE.temp | binary | |
MD5:CAEA3B1F09925DA2A47C2B8B890AB890 | SHA256:66F29B00CBB7B1DED878F96AAC6F52907C088DE194A1FD0CD6E1FF1916047549 | |||
| 328 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\XZSP50HHRZX9S7PZ8JYJ.temp | binary | |
MD5:CAEA3B1F09925DA2A47C2B8B890AB890 | SHA256:66F29B00CBB7B1DED878F96AAC6F52907C088DE194A1FD0CD6E1FF1916047549 | |||
| 328 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:CAEA3B1F09925DA2A47C2B8B890AB890 | SHA256:66F29B00CBB7B1DED878F96AAC6F52907C088DE194A1FD0CD6E1FF1916047549 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
updatecheck.massgrave.dev |
| unknown |