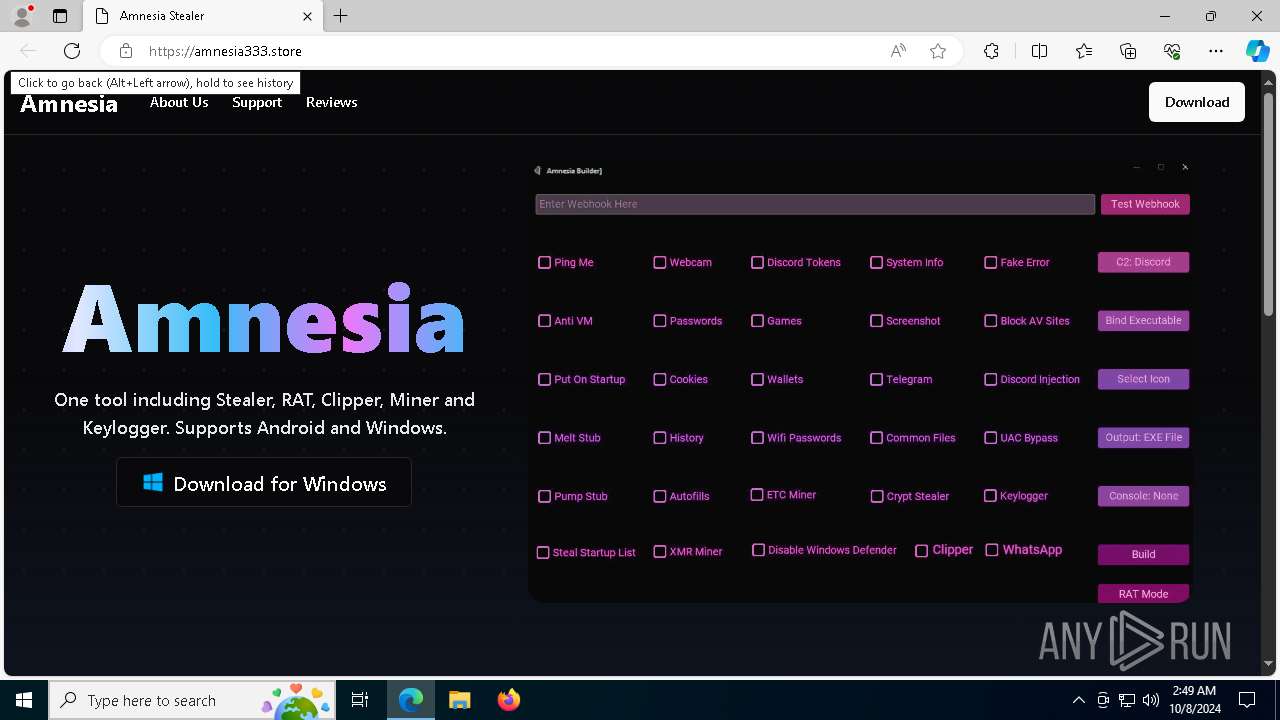
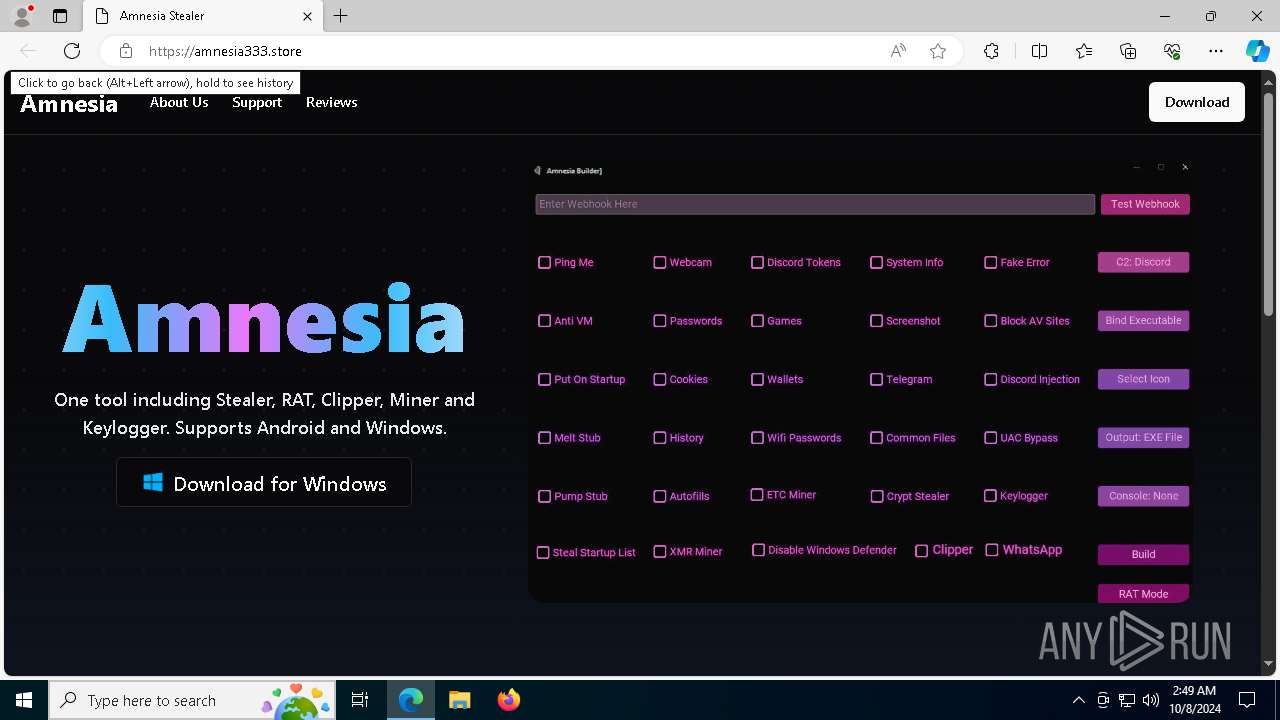
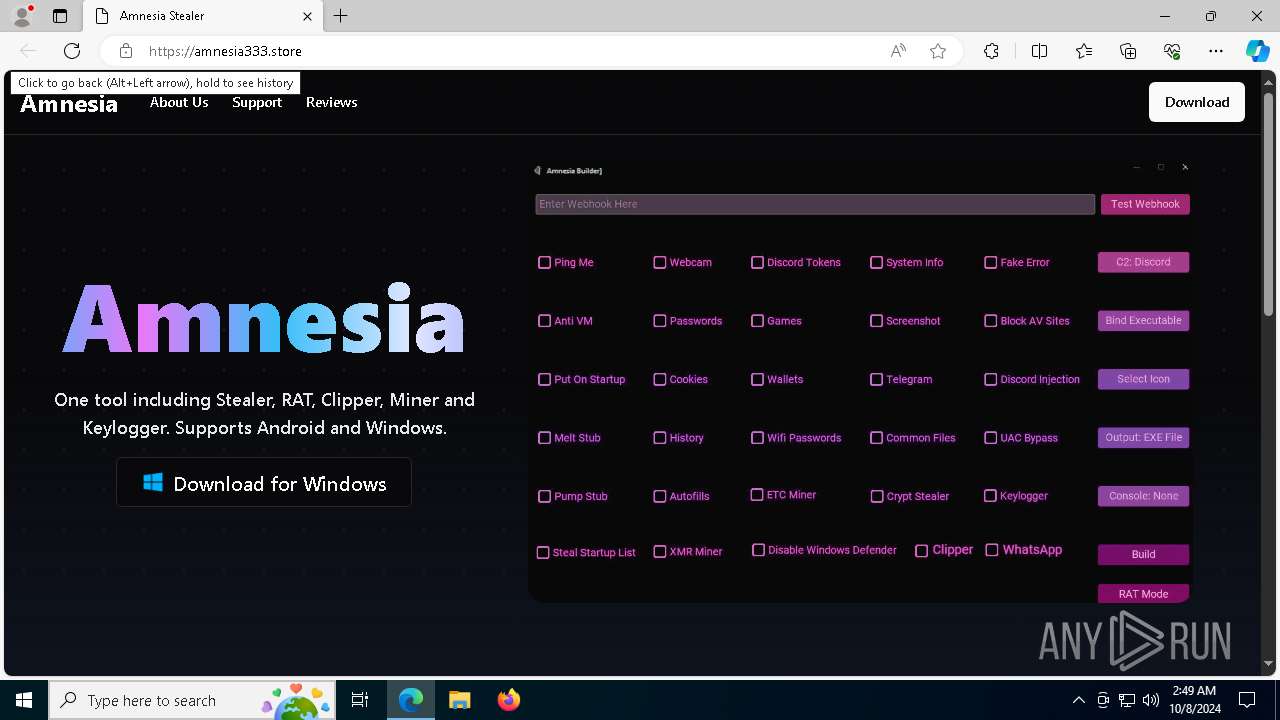
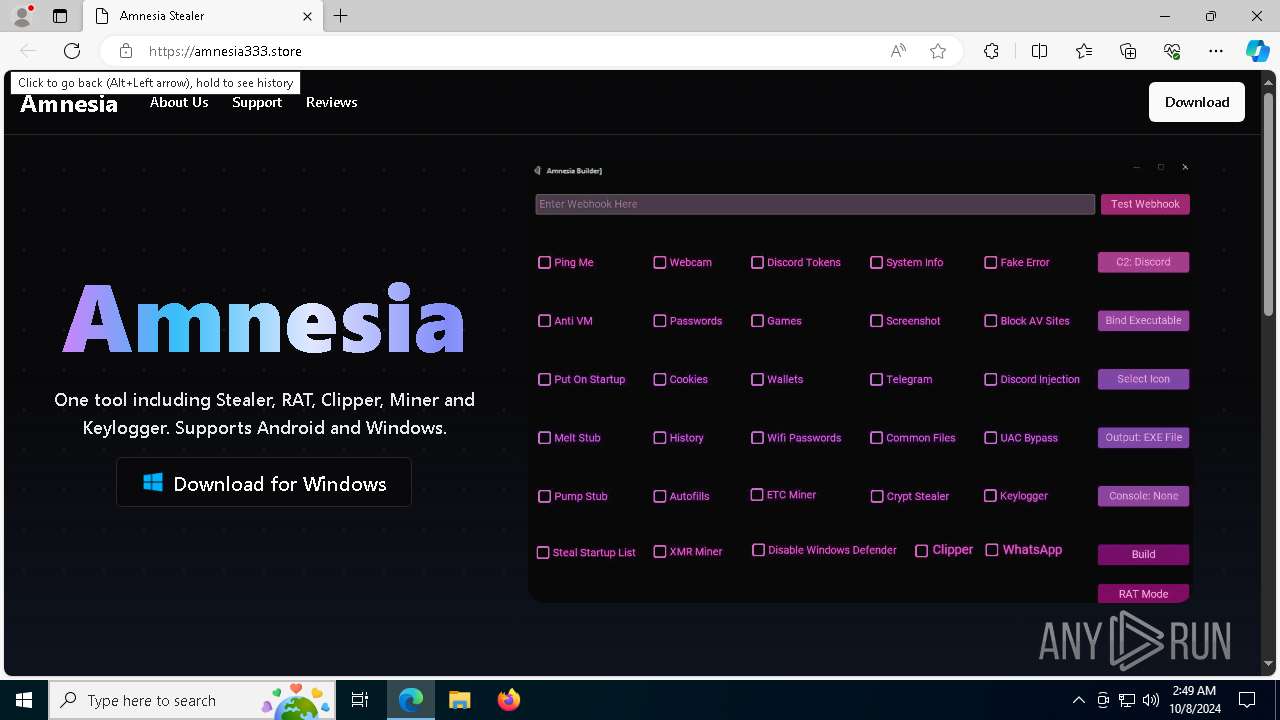
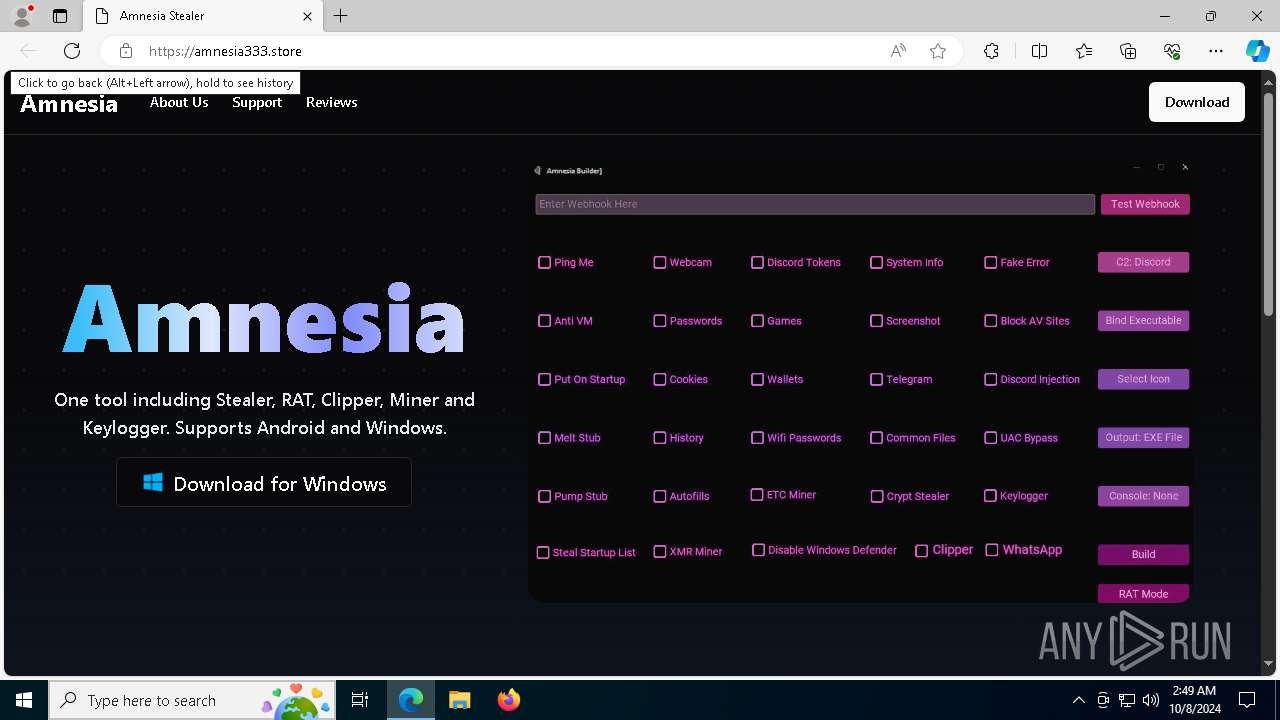
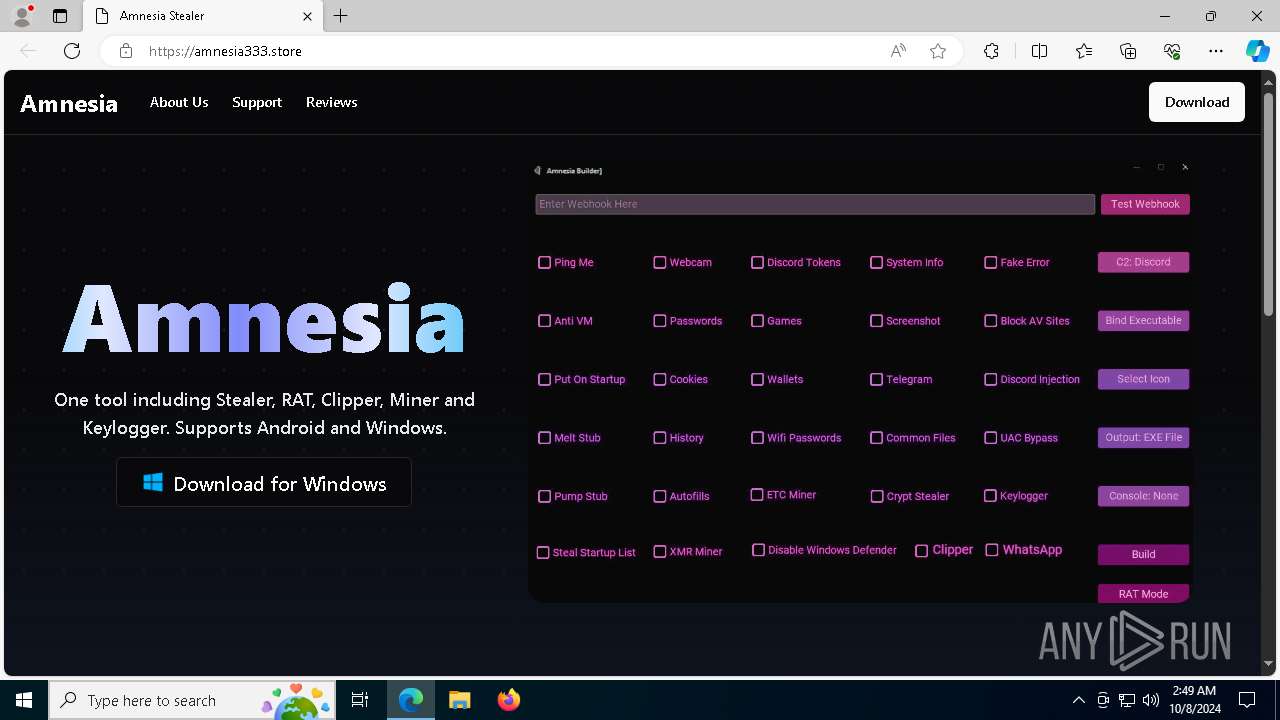
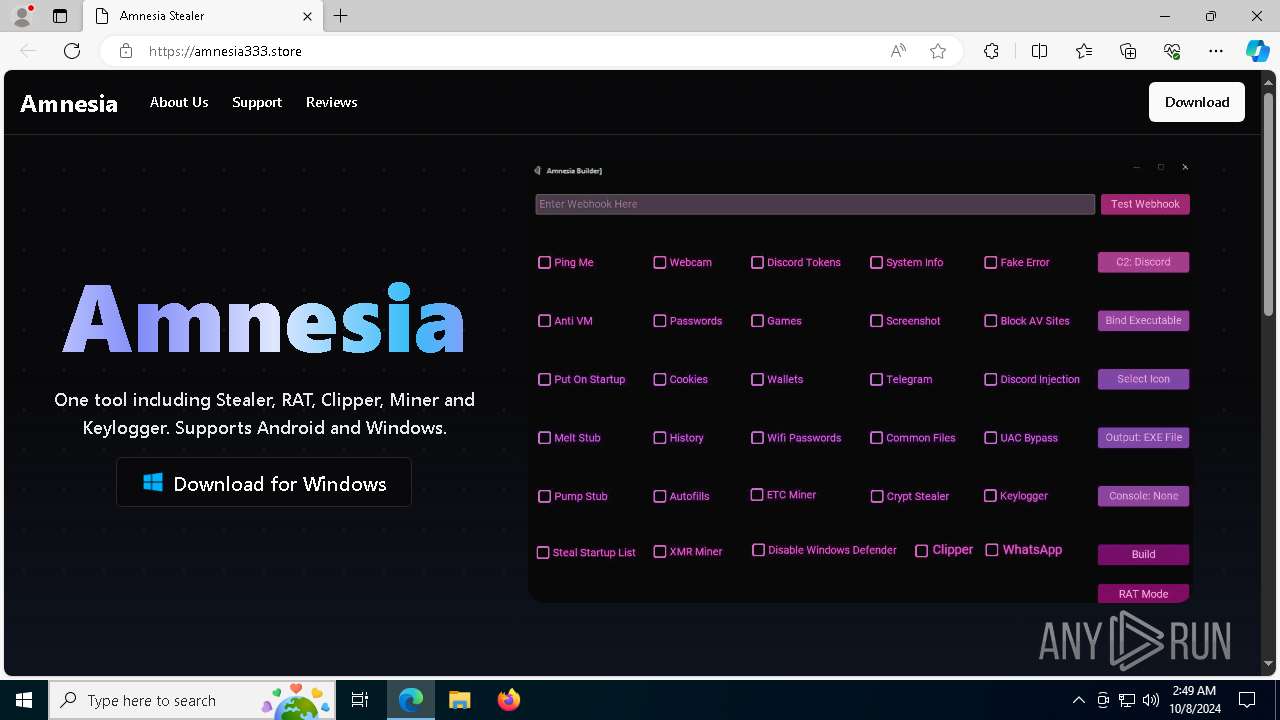
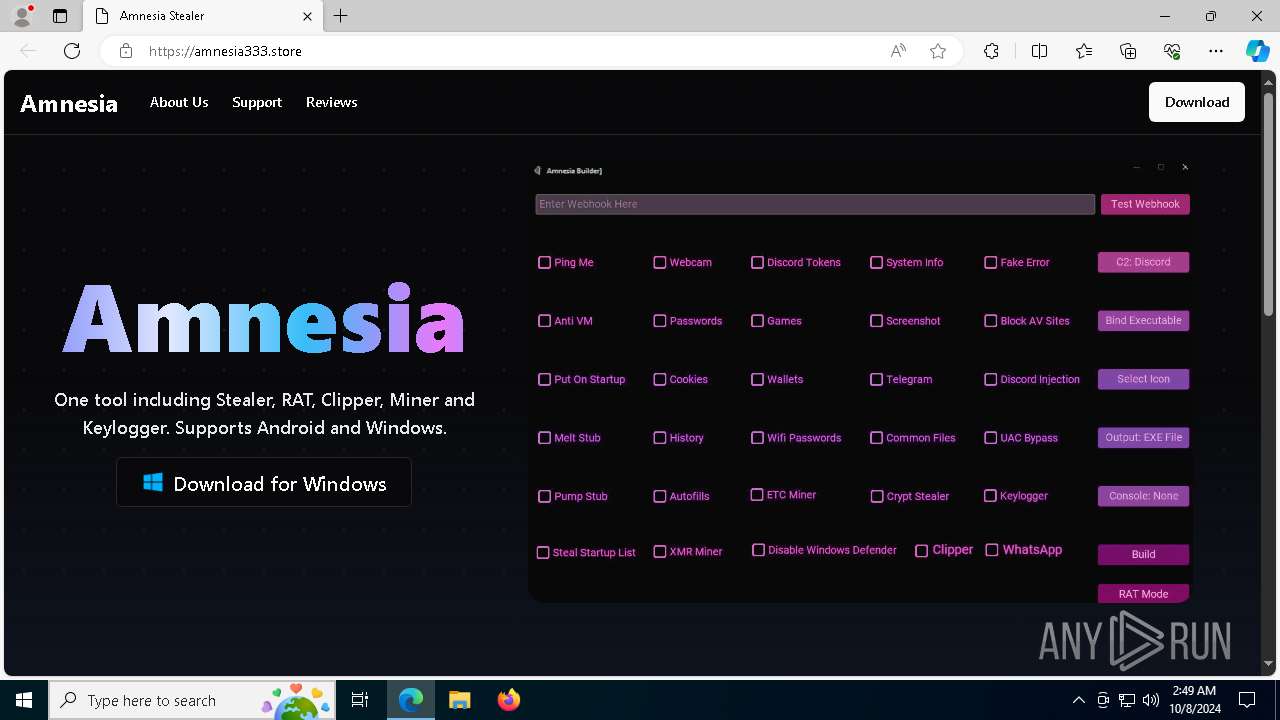
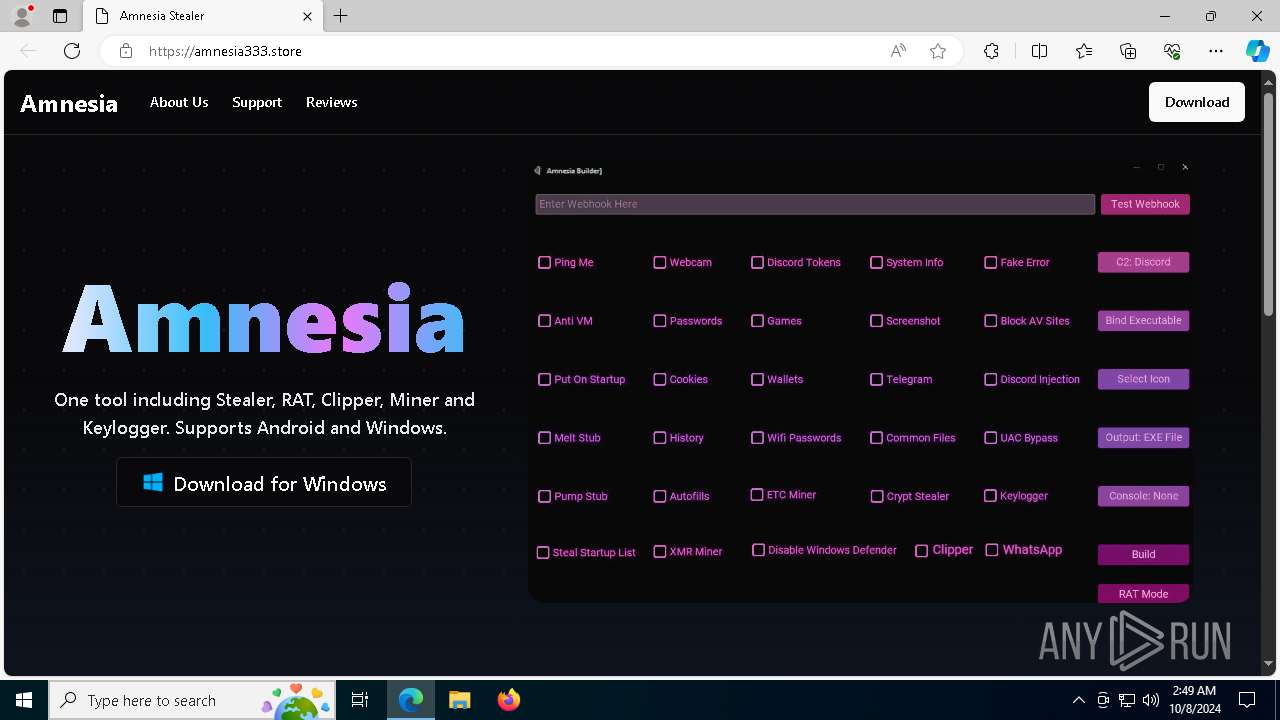
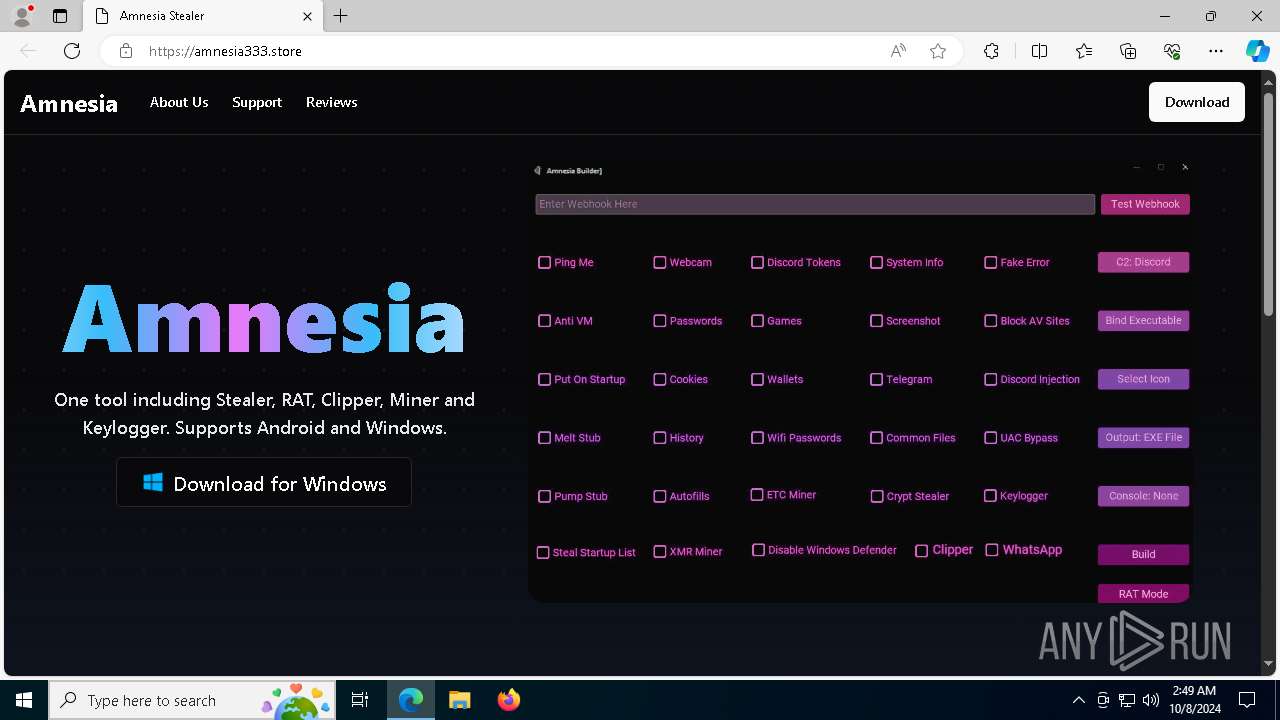
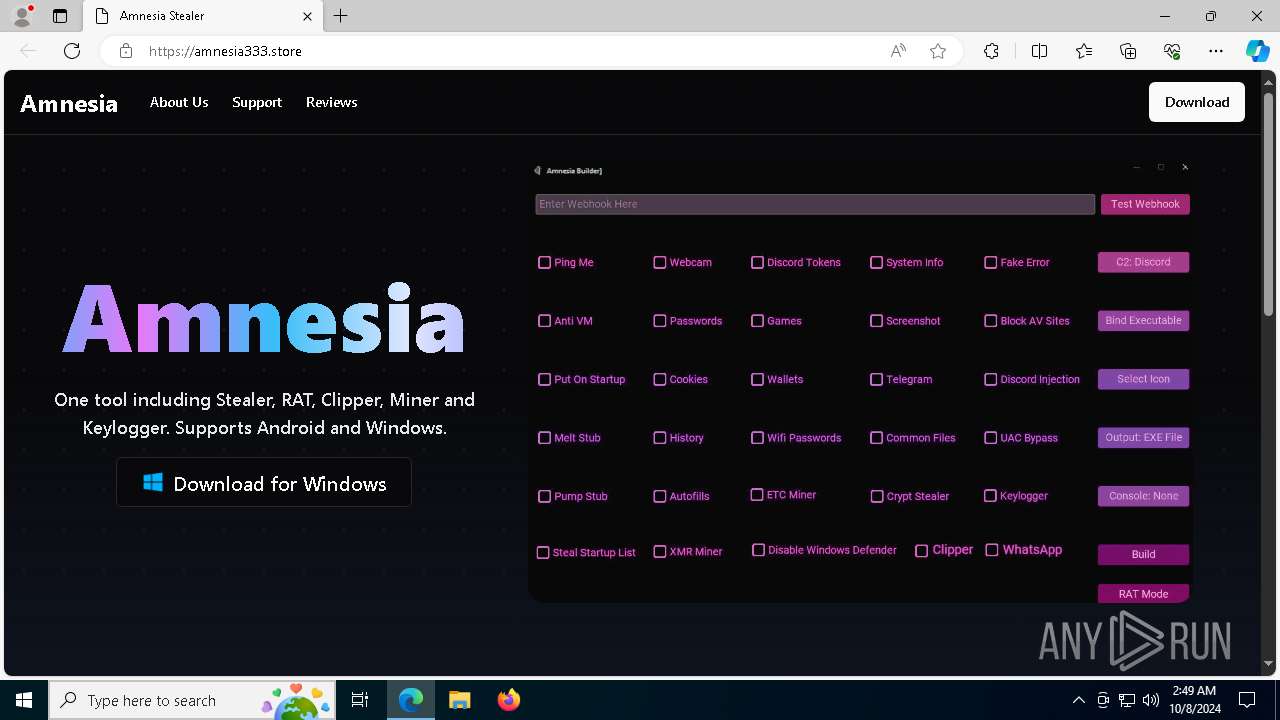
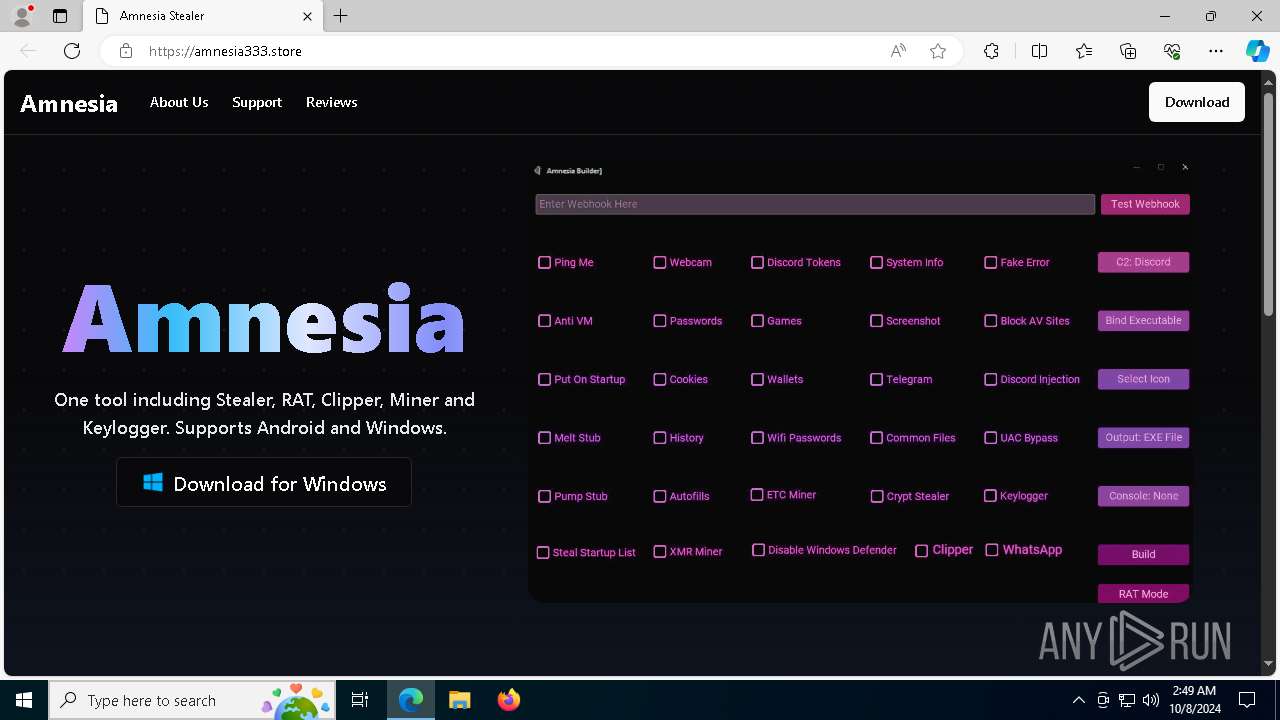
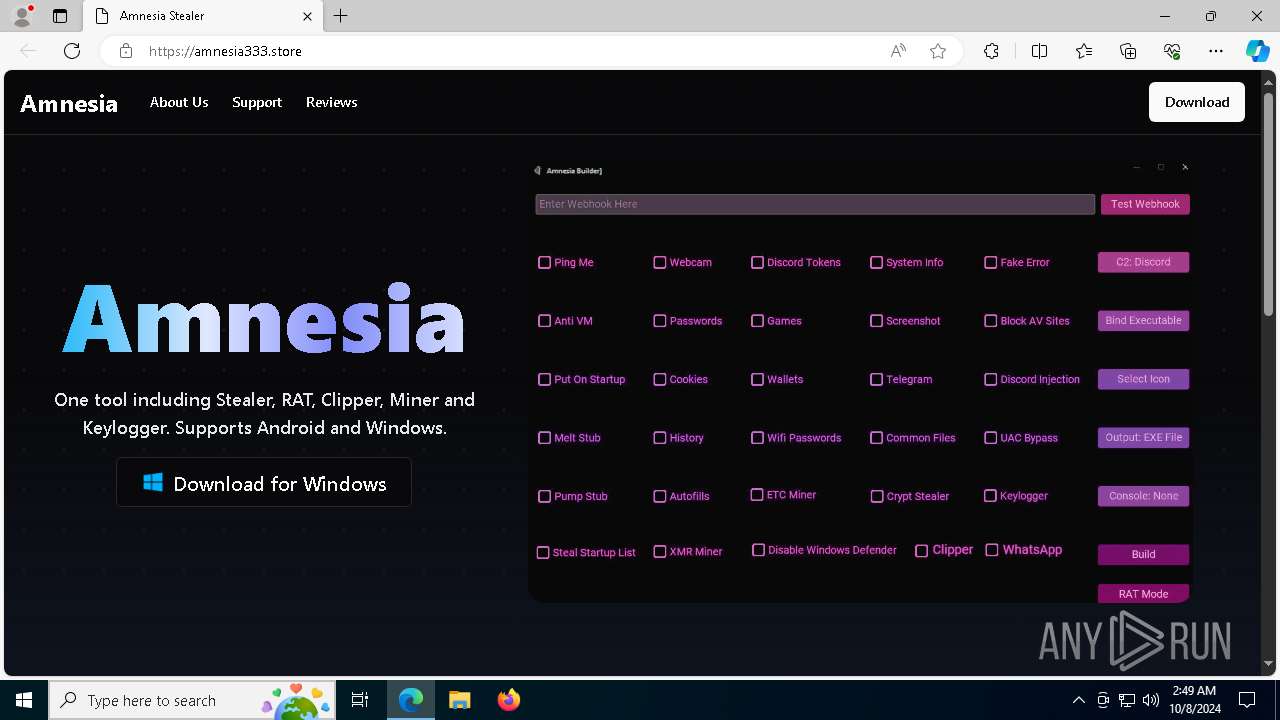
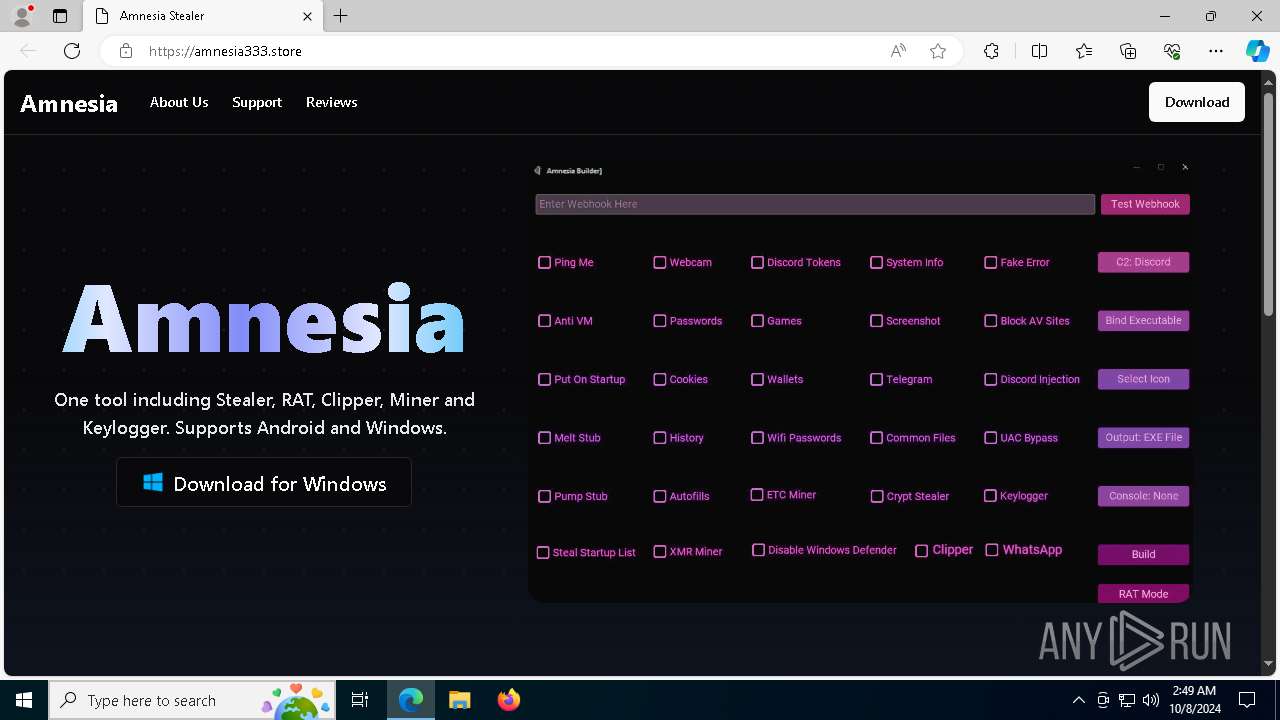
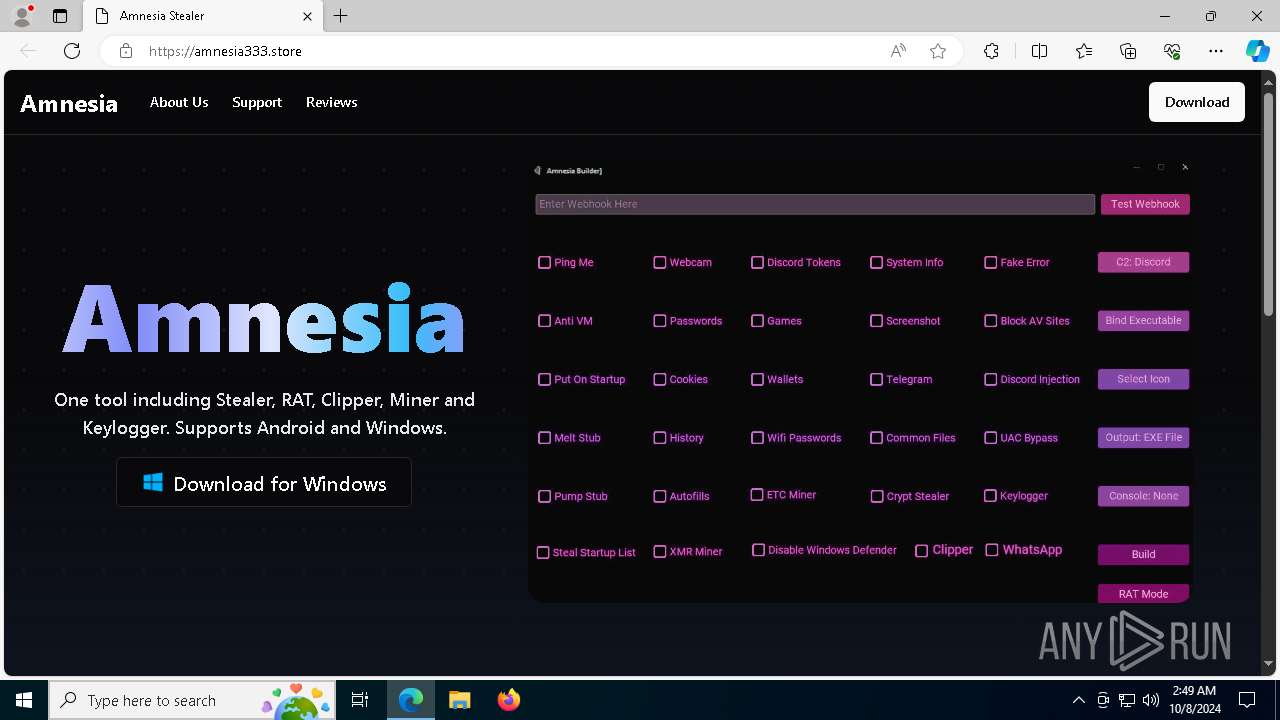
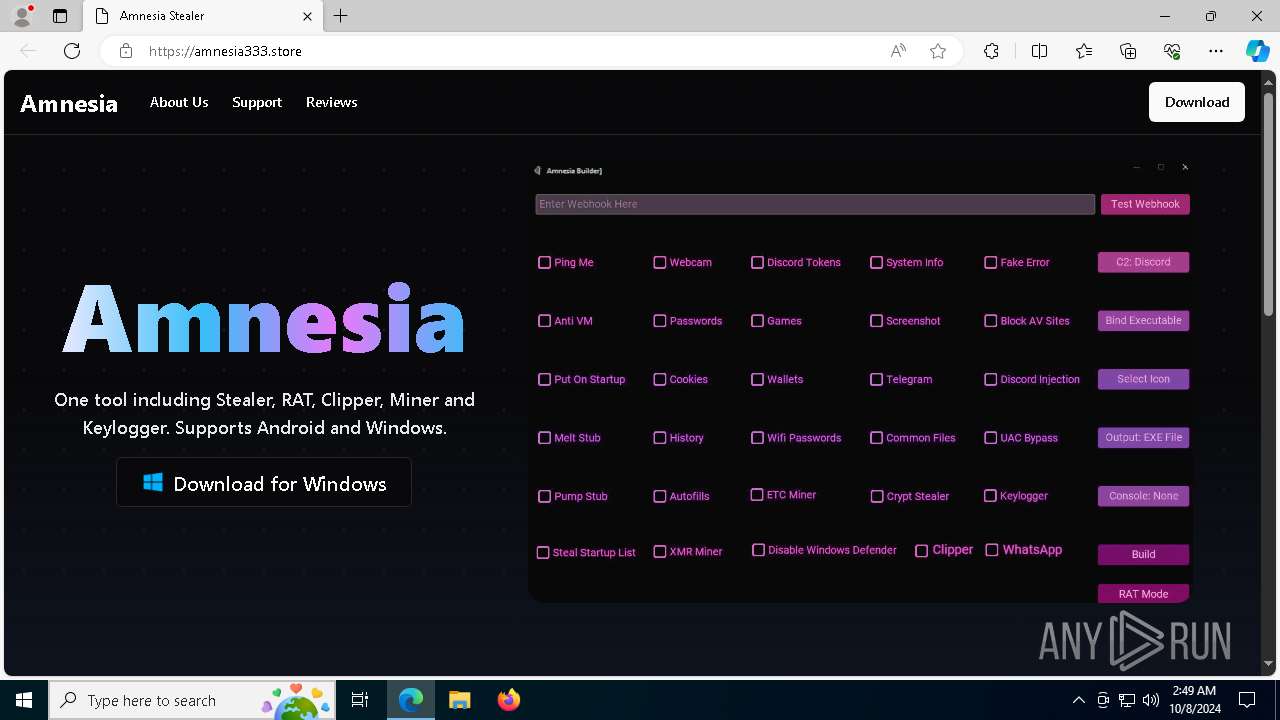
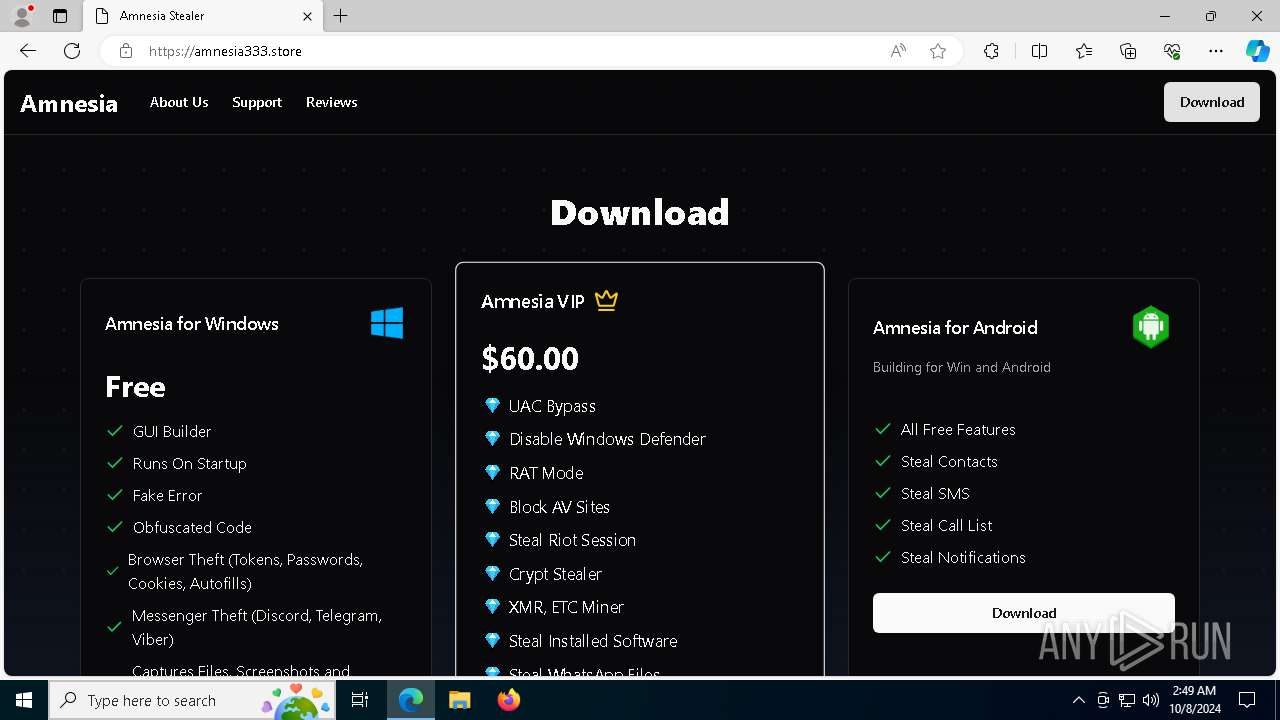
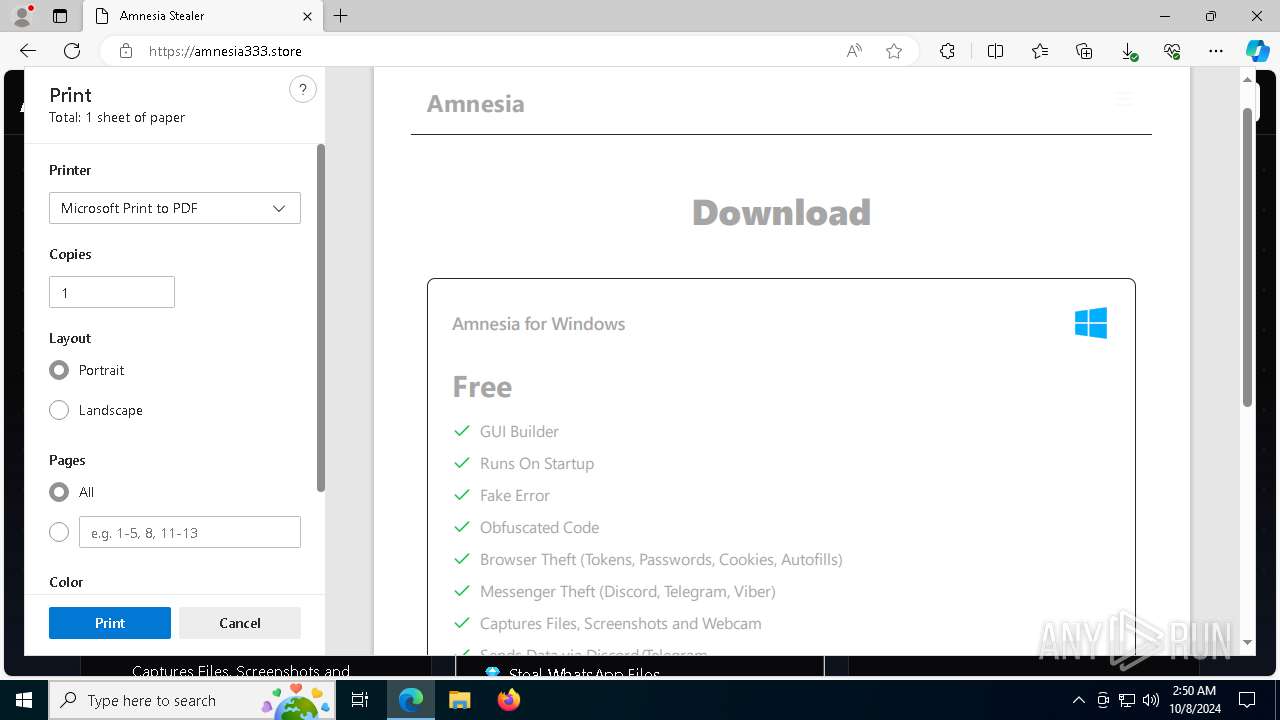
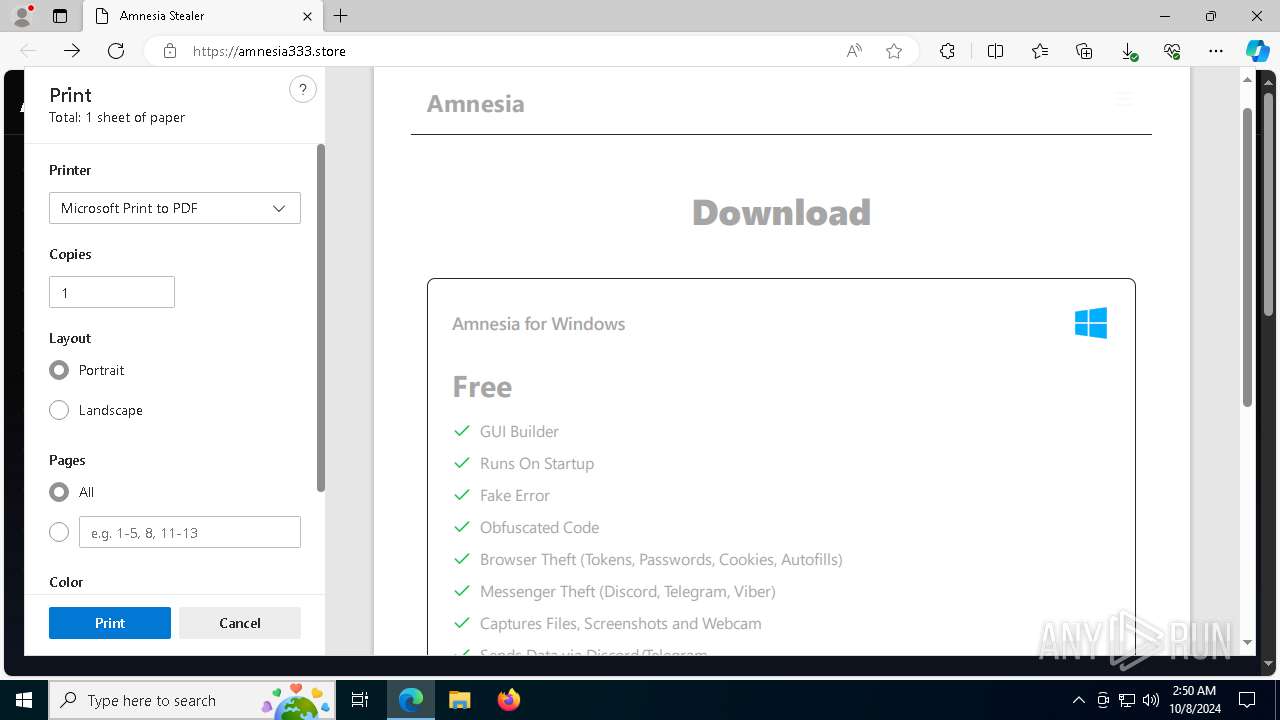
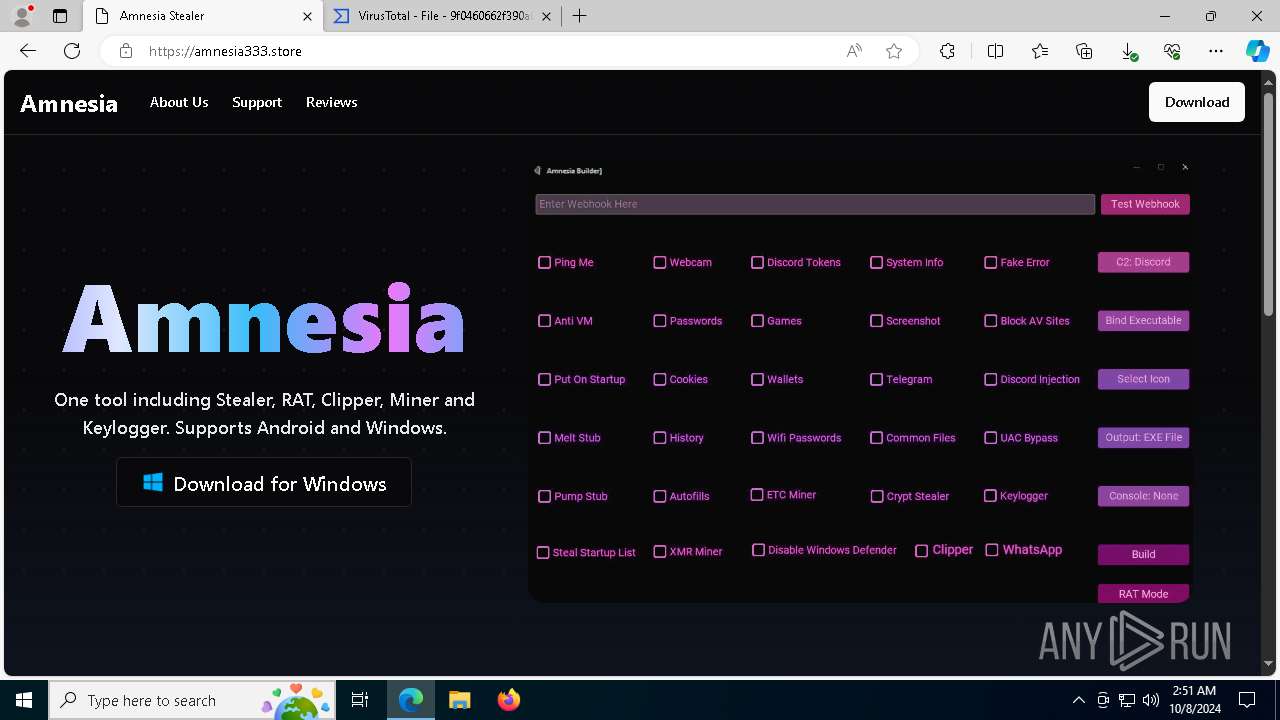
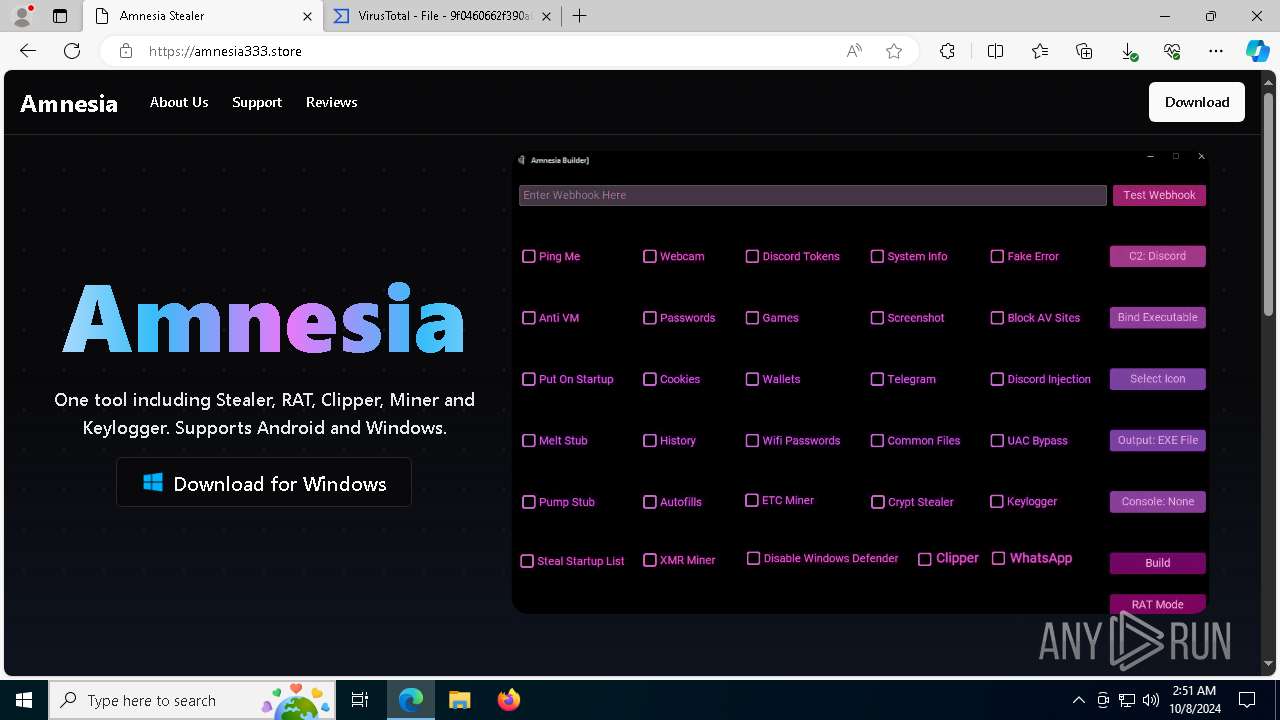
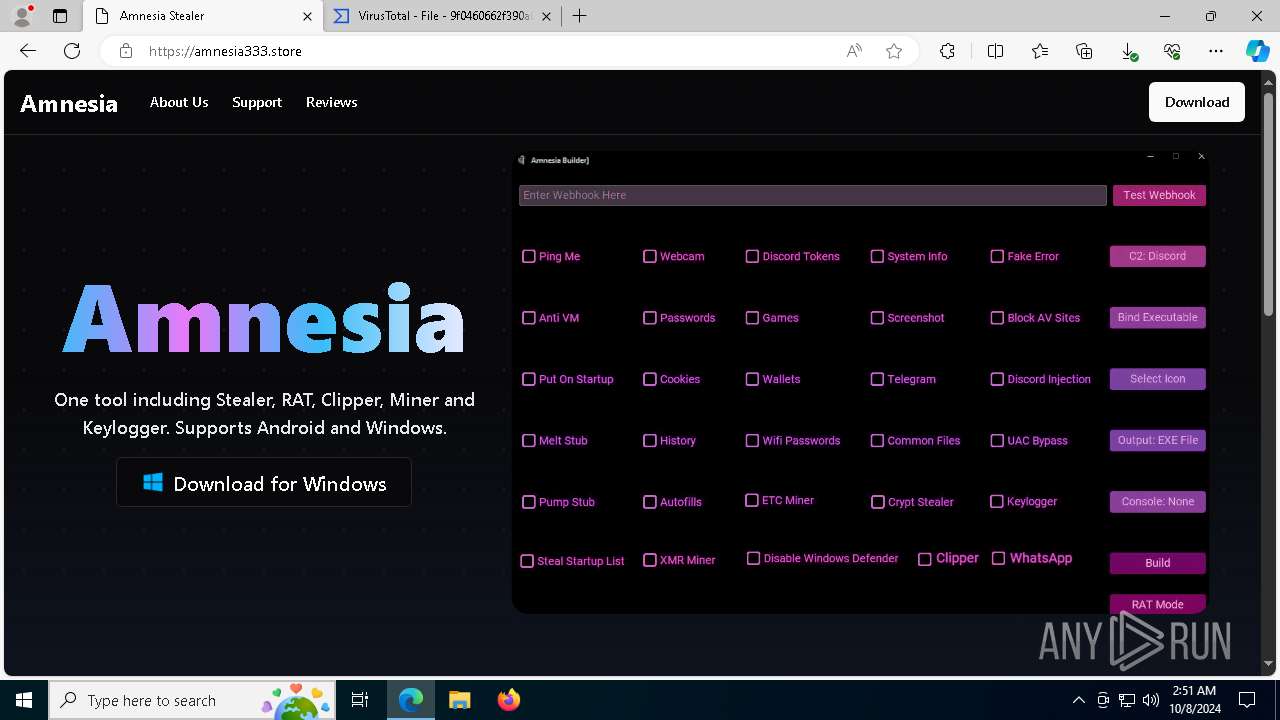
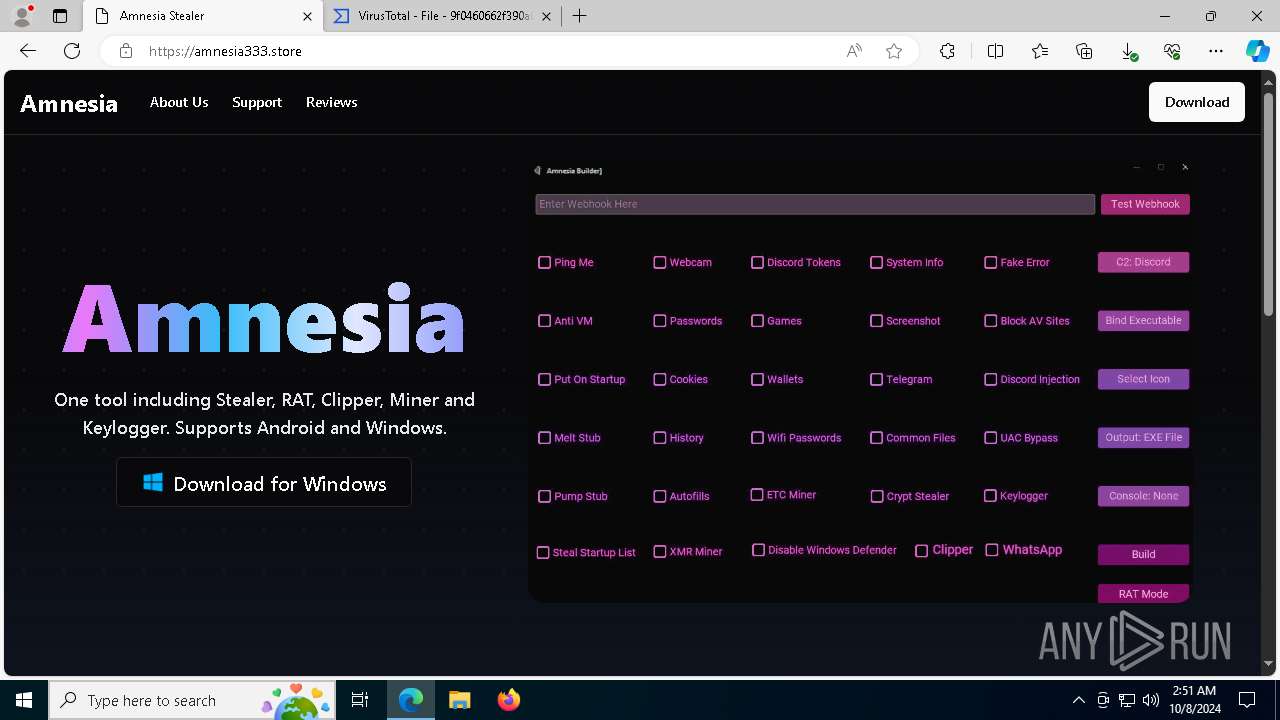
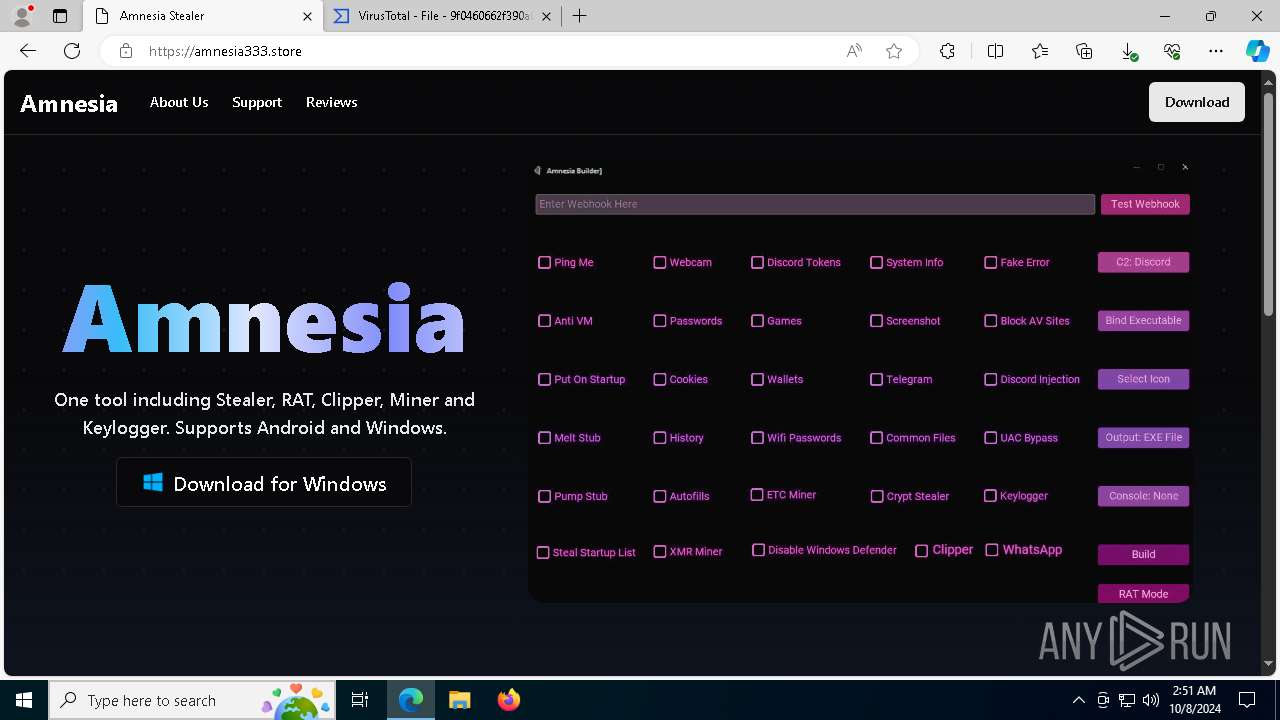
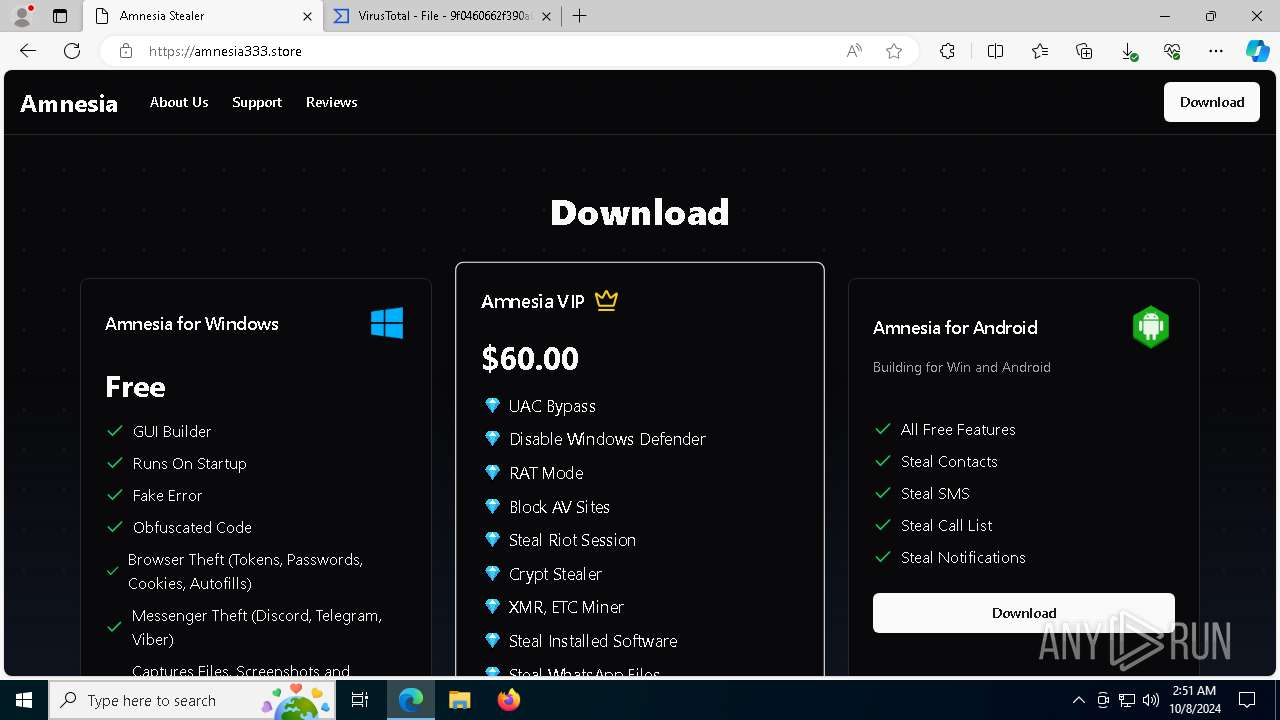
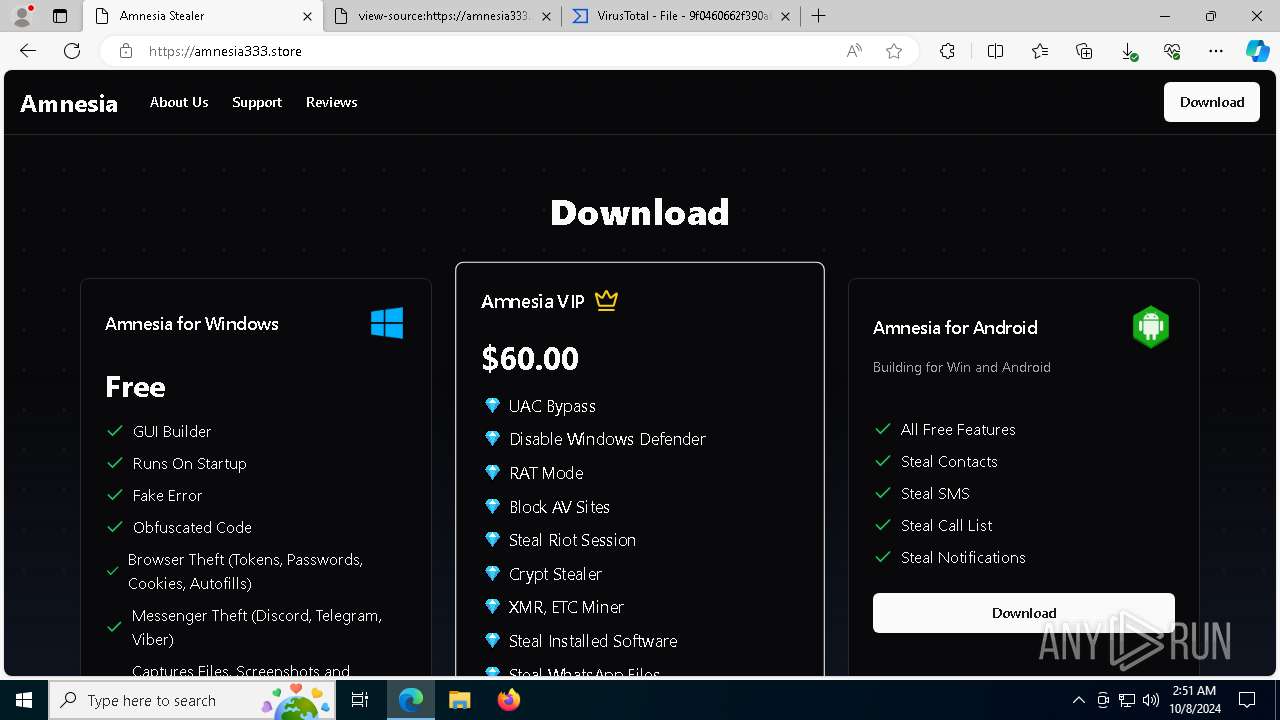
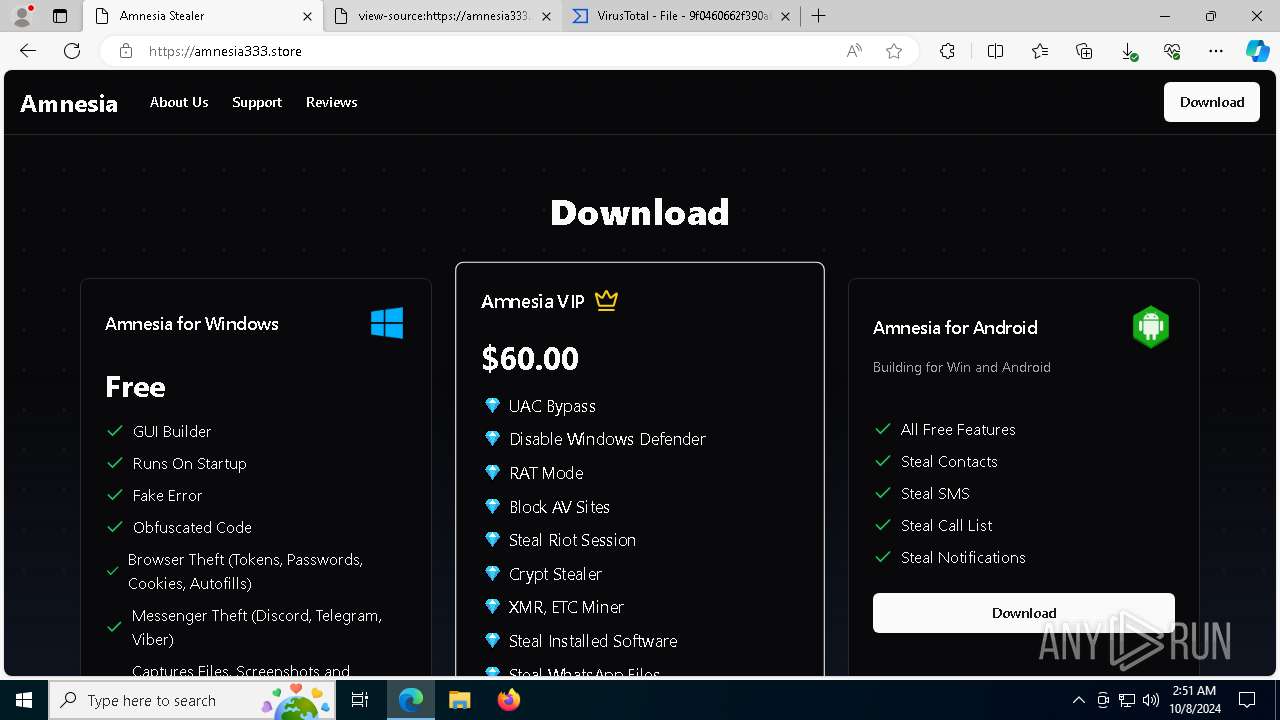
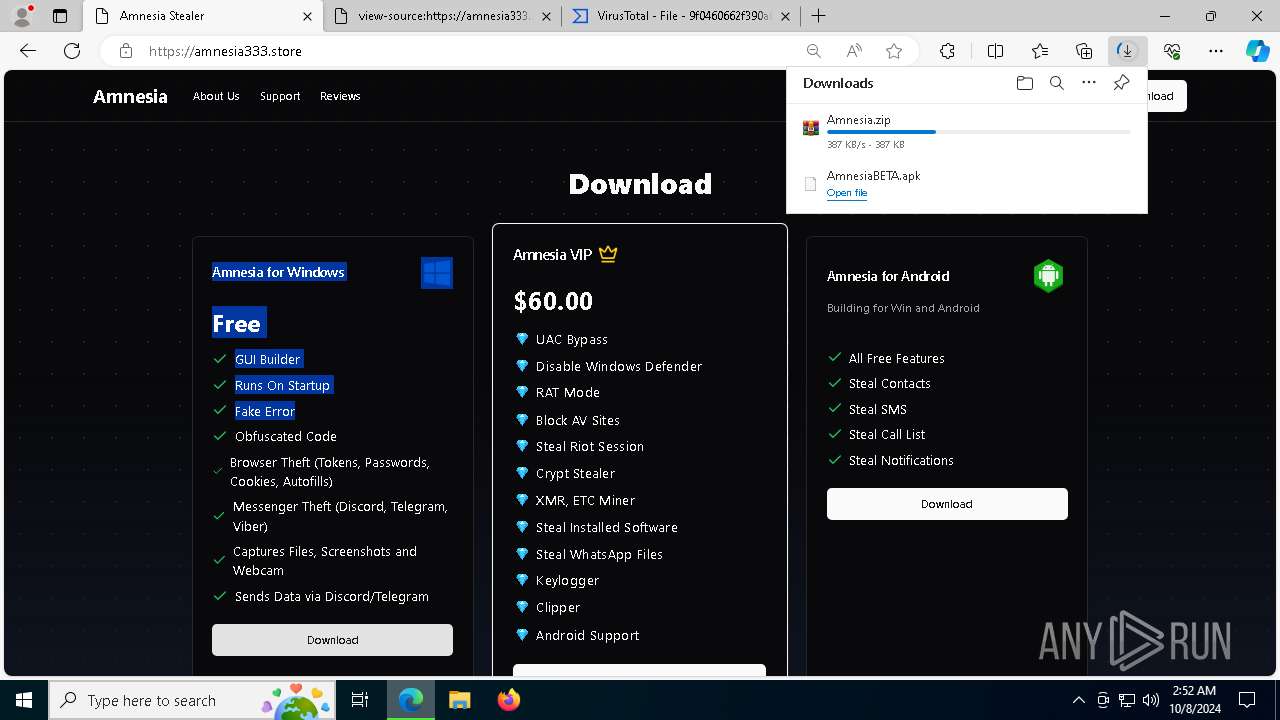
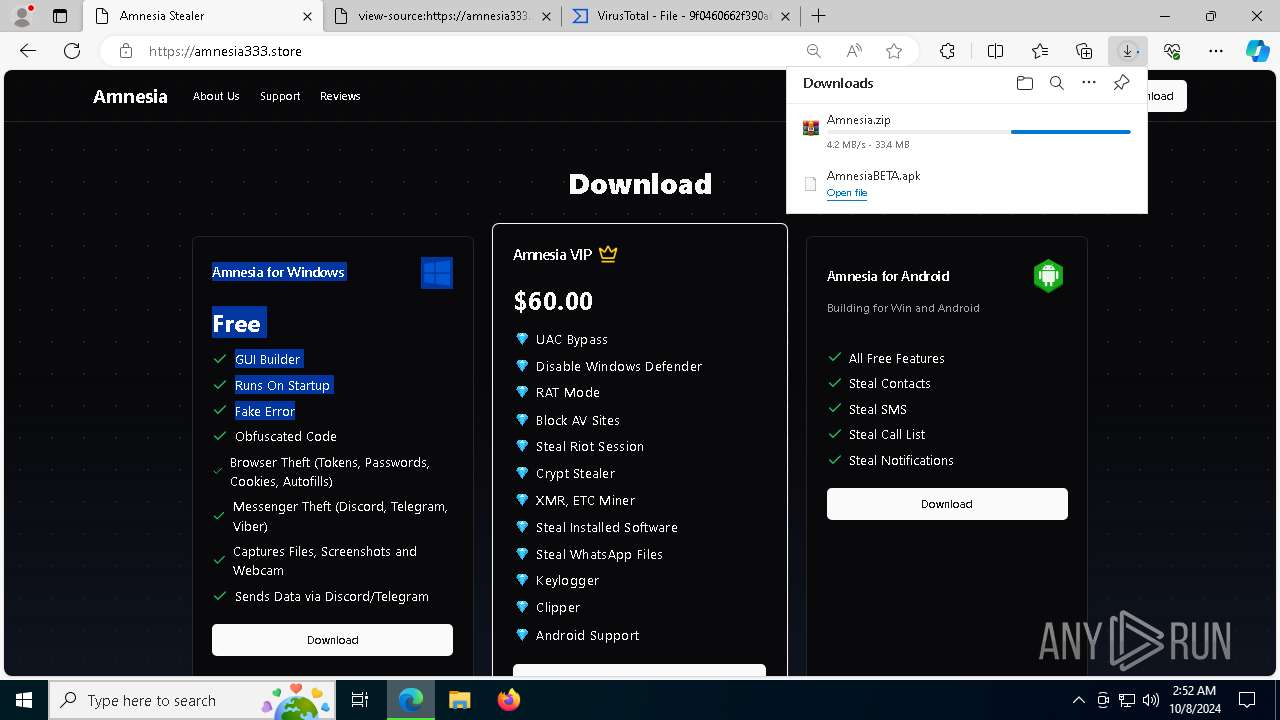
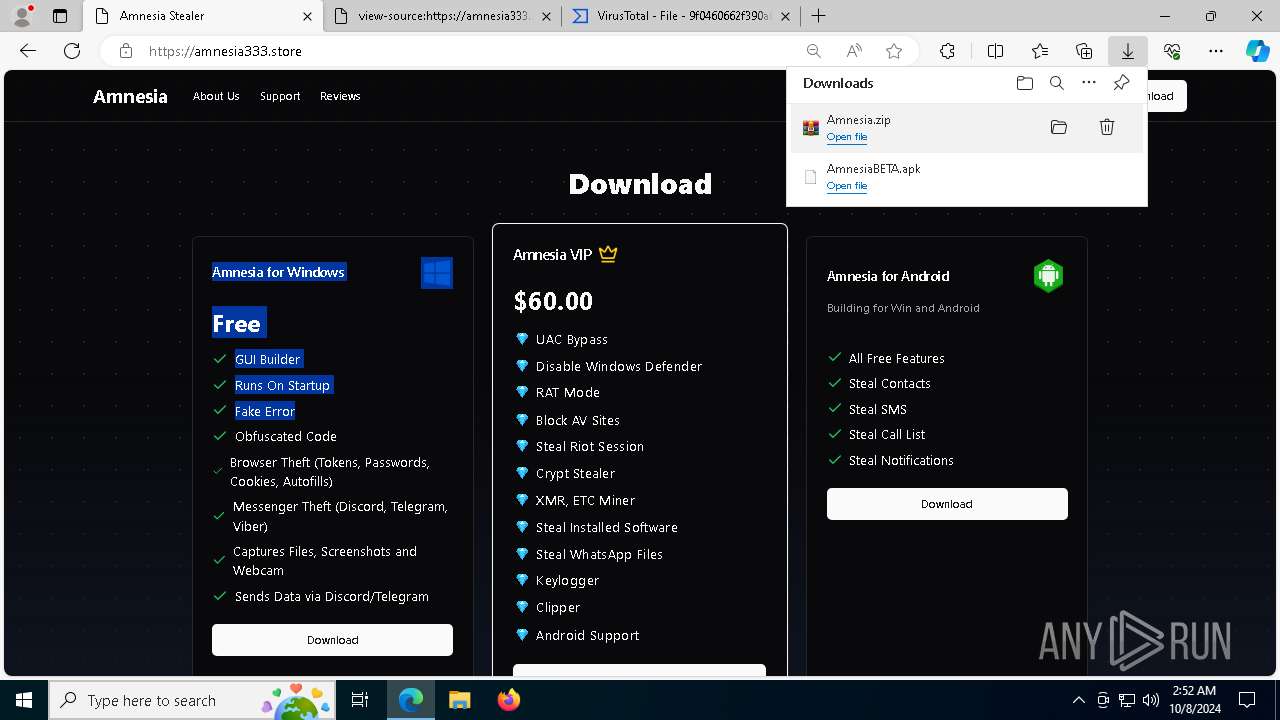
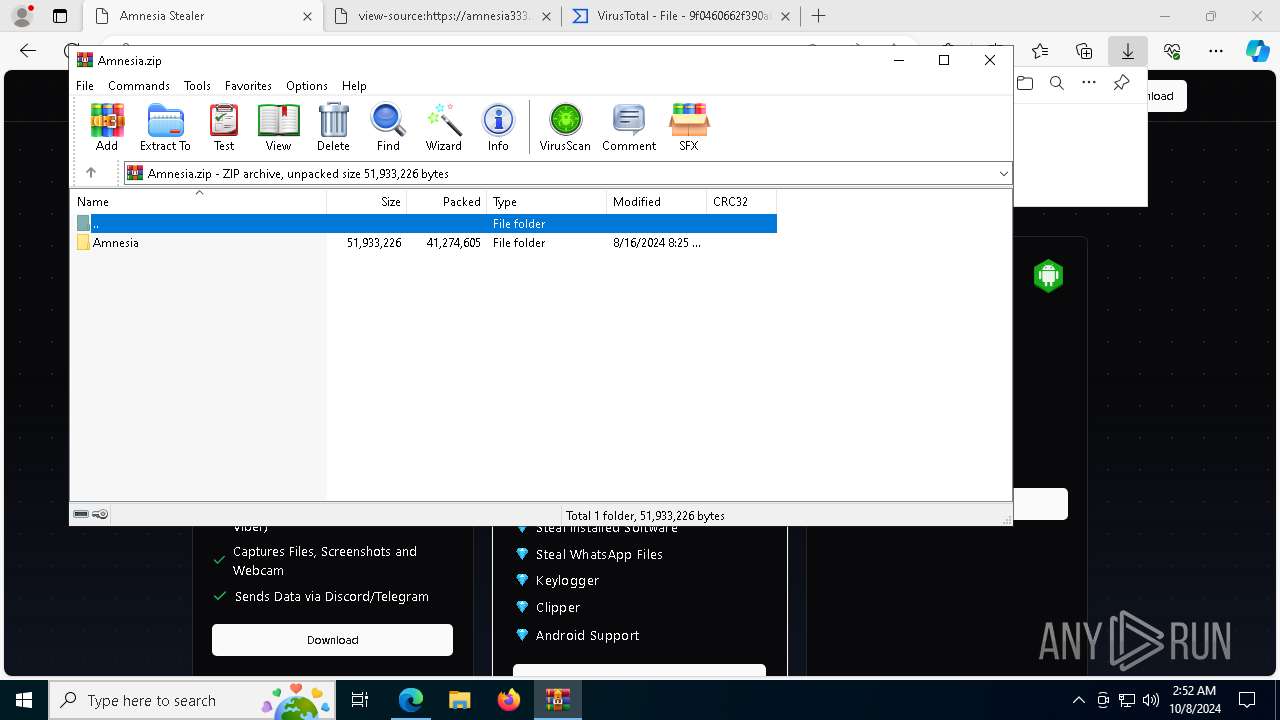
| URL: | https://amnesia333.store/ |
| Full analysis: | https://app.any.run/tasks/61a2a12d-ca90-44a9-9bd2-0faddbcf8221 |
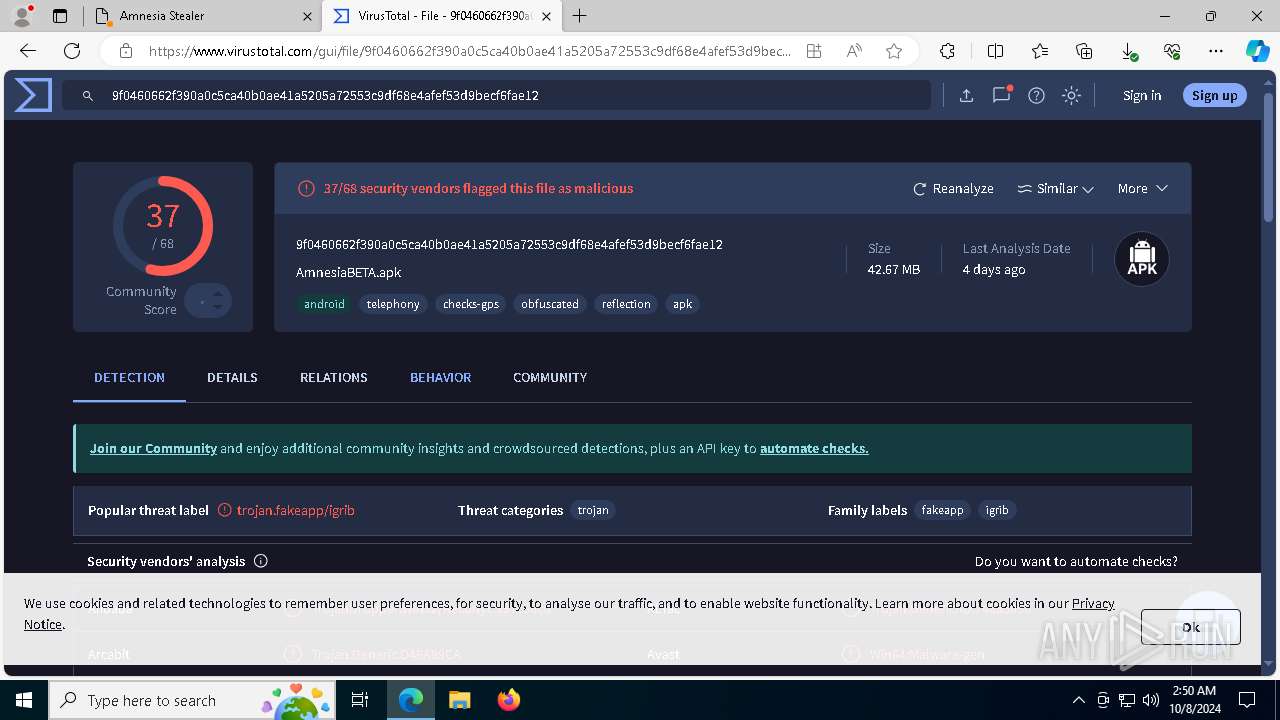
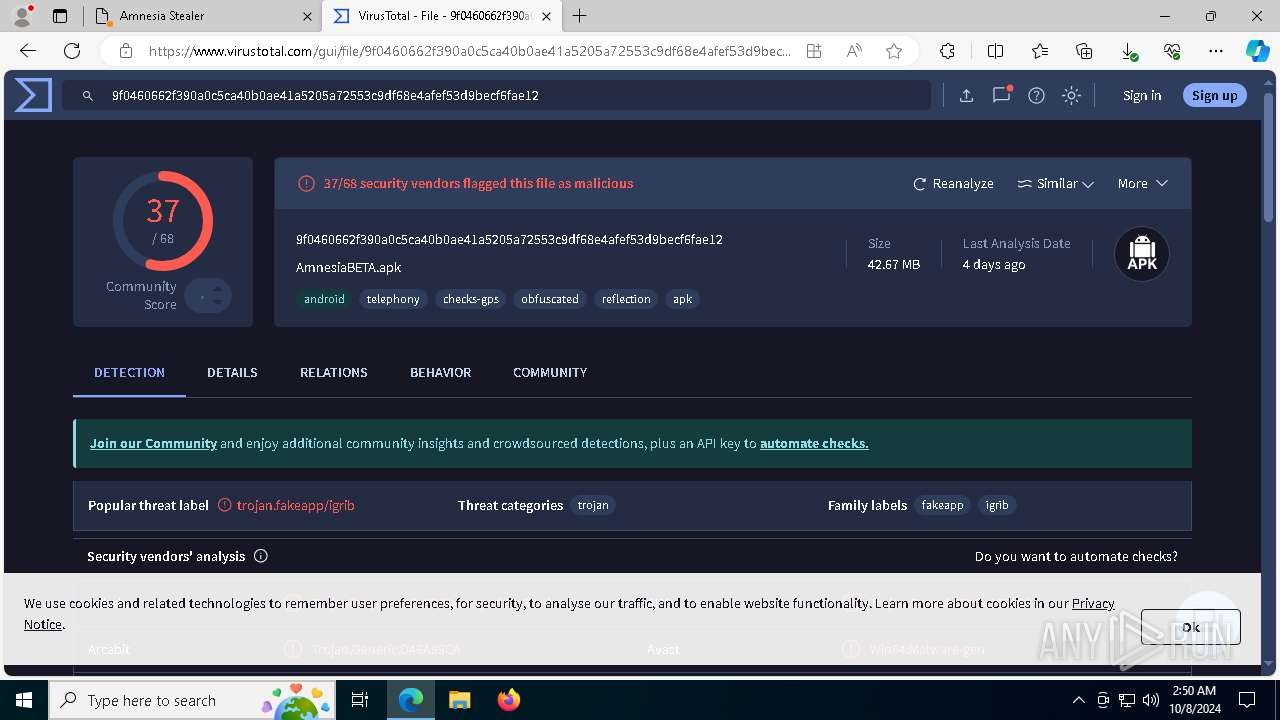
| Verdict: | Malicious activity |
| Analysis date: | October 08, 2024, 02:49:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 4638890281D1D1656F5AFE69538037FB |
| SHA1: | C073B5A3703B847BCF5C9C42E9F4D168BE47B140 |
| SHA256: | 086C51B05D99AA3D097252D9EC8B540F06E4FA70ADCBC86D8CCCE652C0AC1599 |
| SSDEEP: | 3:N8ALsK:2ALsK |
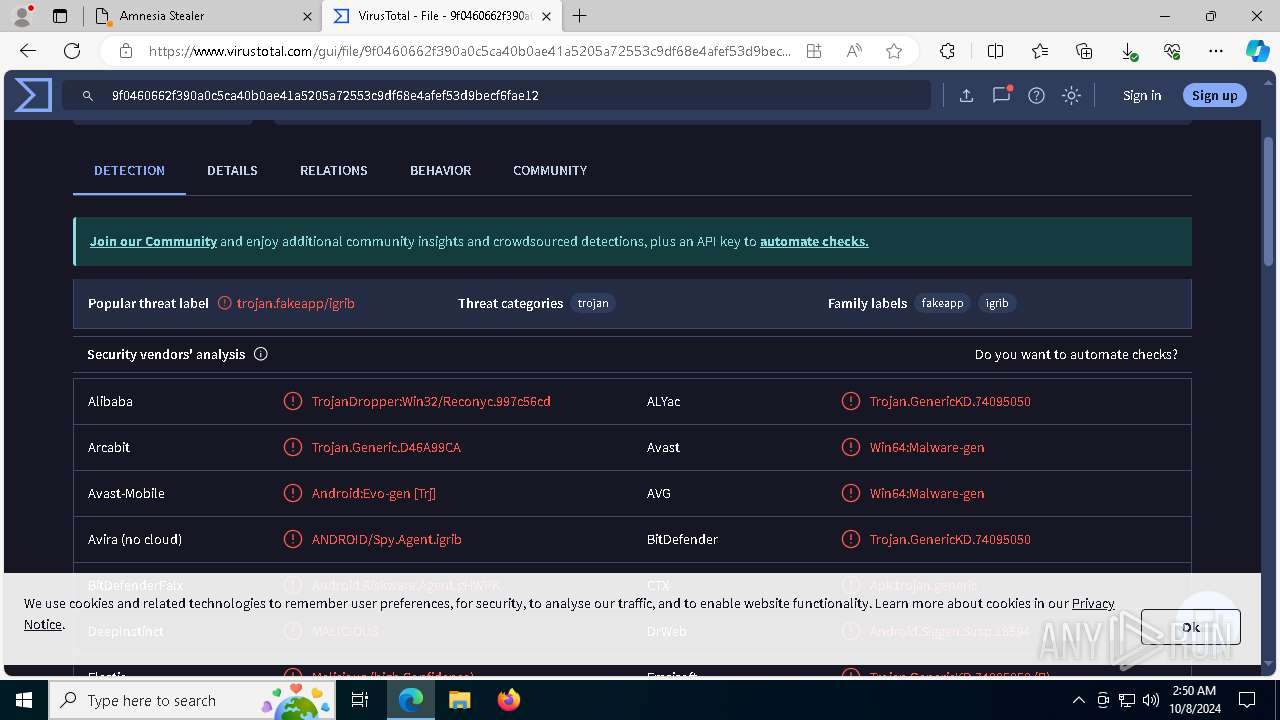
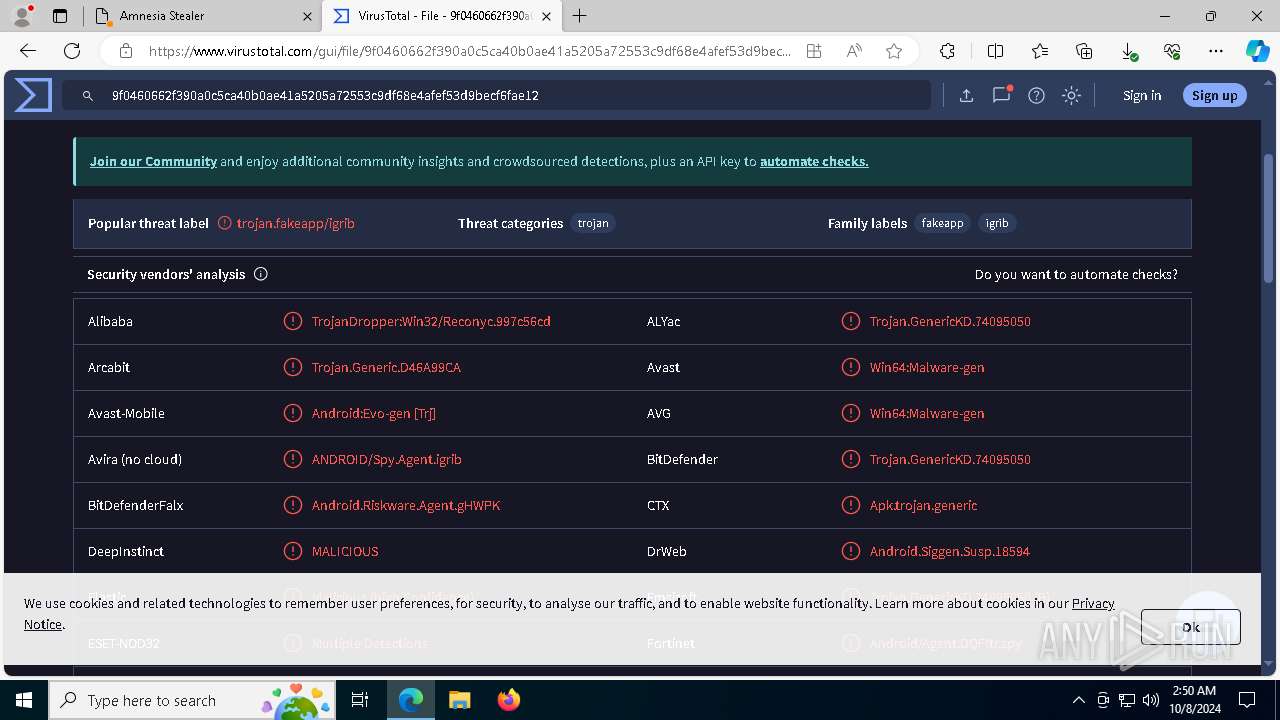
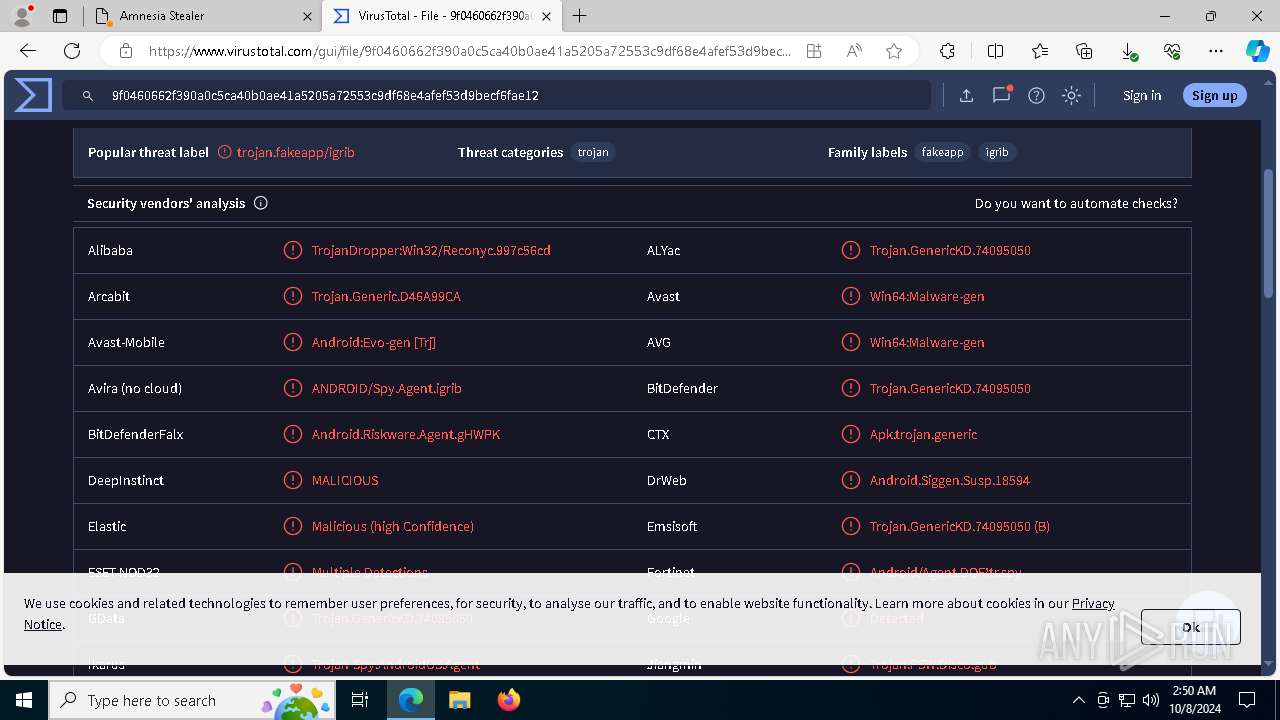
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Attempting to use instant messaging service
- msedge.exe (PID: 5032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
219
Monitored processes
13
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
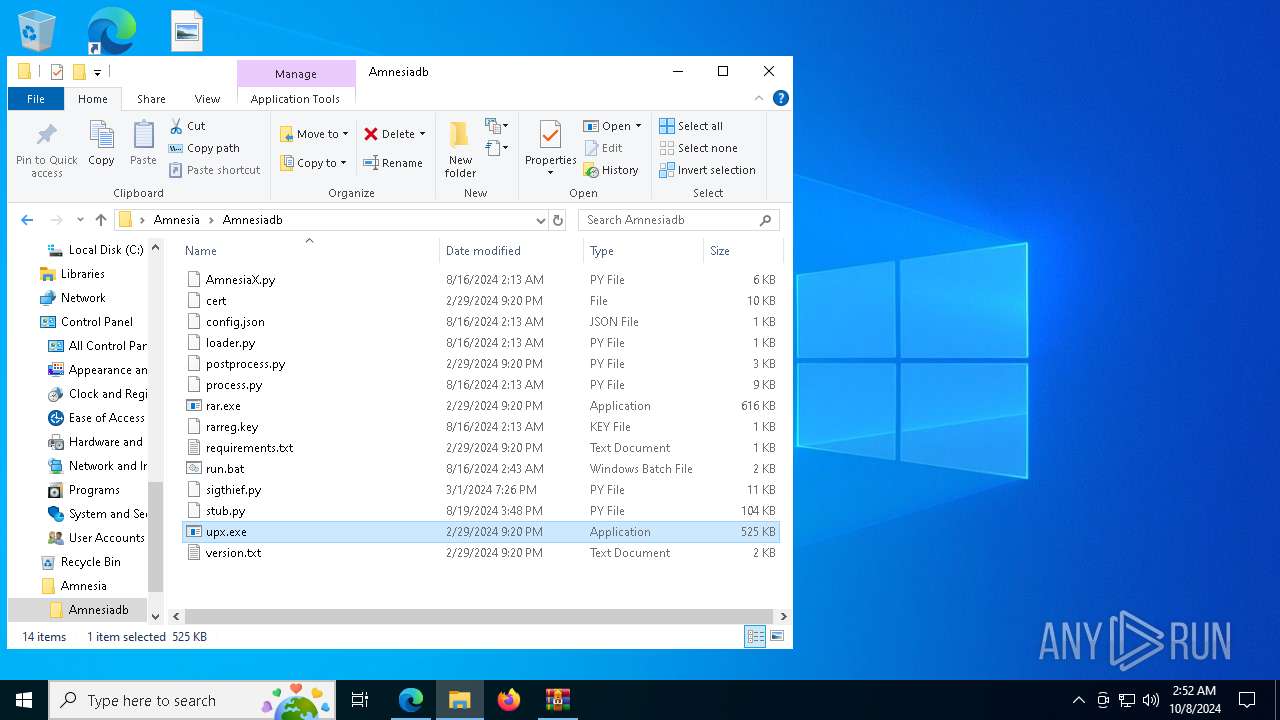
| 2244 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Amnesia\Amnesiadb\run.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
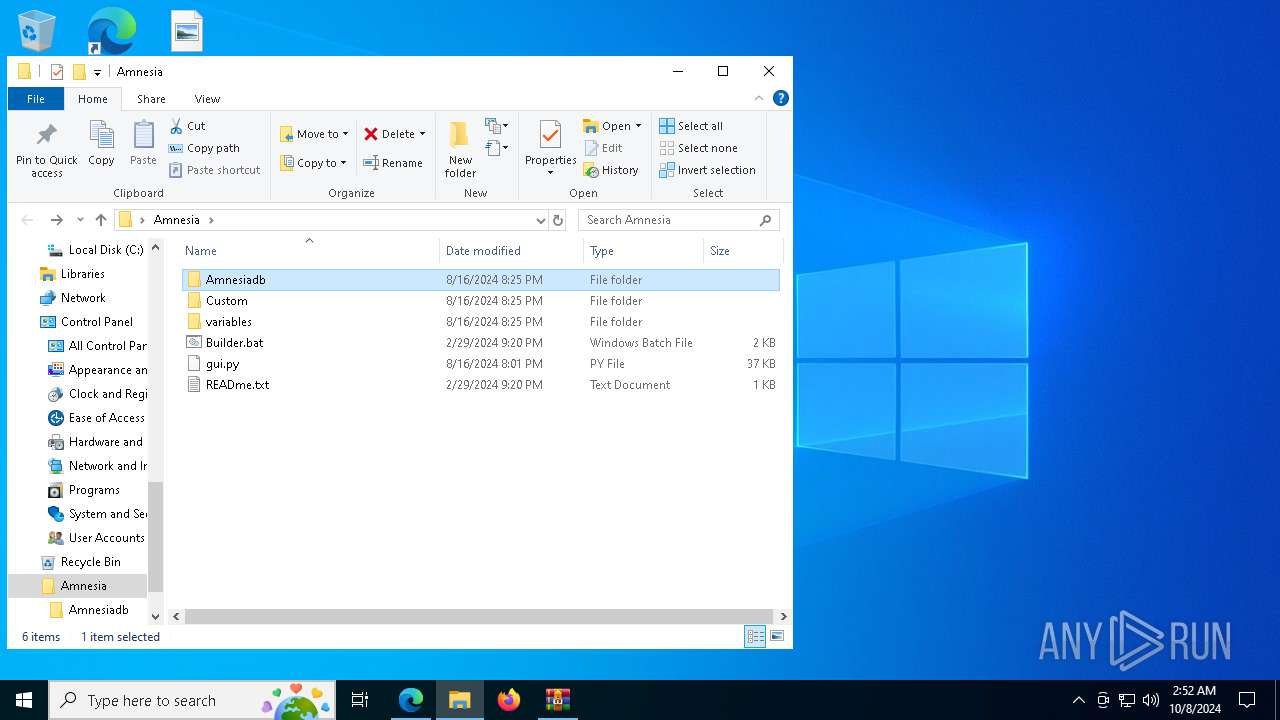
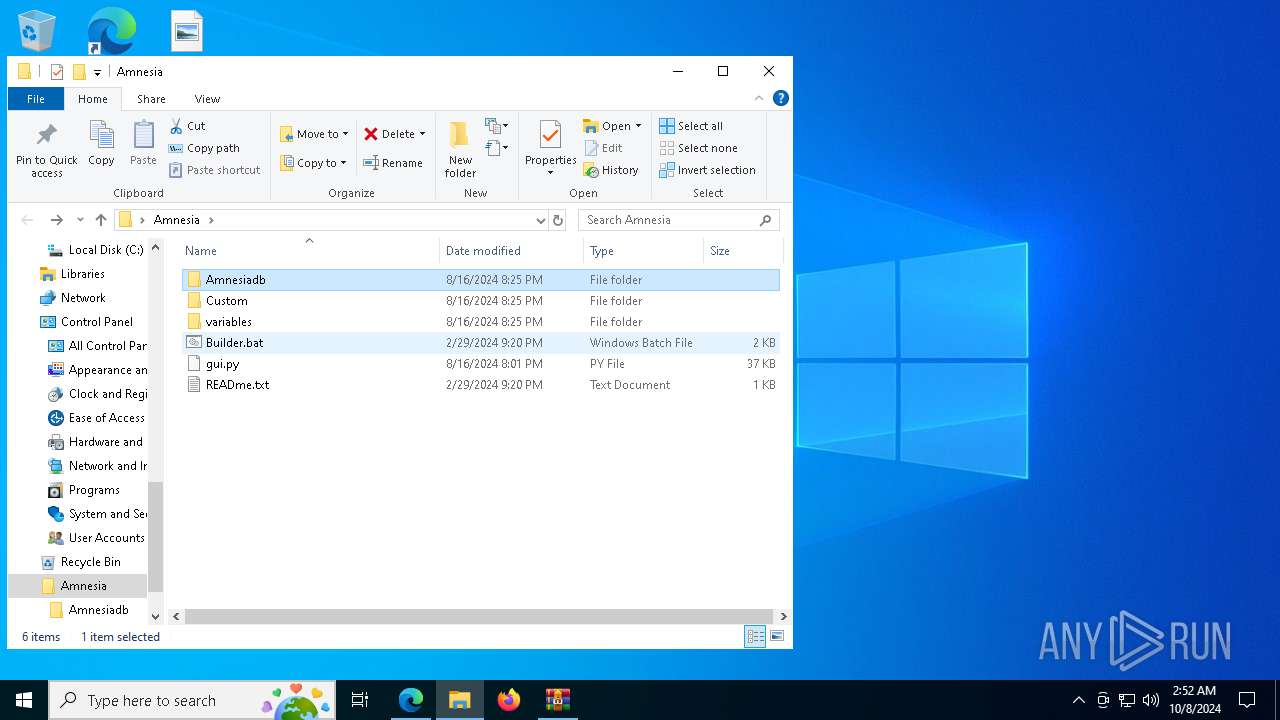
| 2252 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Amnesia\Builder.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
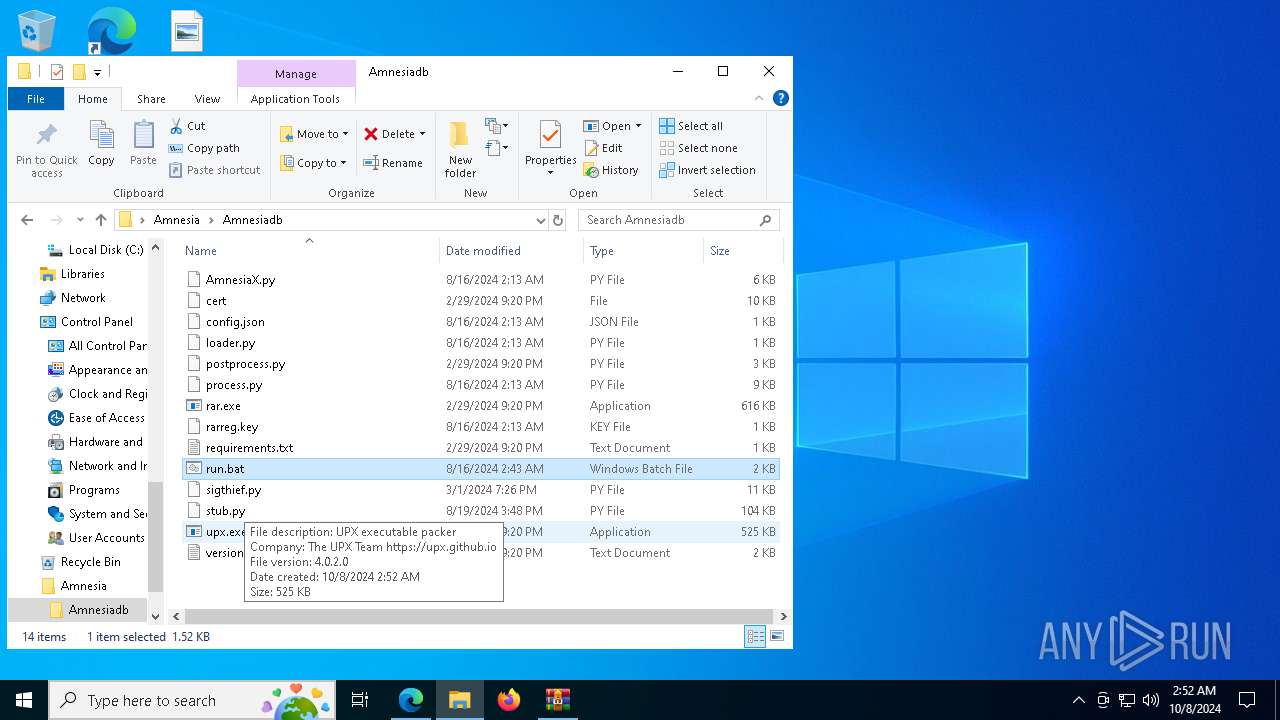
| 2424 | "C:\Users\admin\Desktop\Amnesia\Amnesiadb\upx.exe" | C:\Users\admin\Desktop\Amnesia\Amnesiadb\upx.exe | — | explorer.exe | |||||||||||
User: admin Company: The UPX Team https://upx.github.io Integrity Level: MEDIUM Description: UPX executable packer Exit code: 1 Version: 4.0.2 (2023-01-30) Modules
| |||||||||||||||
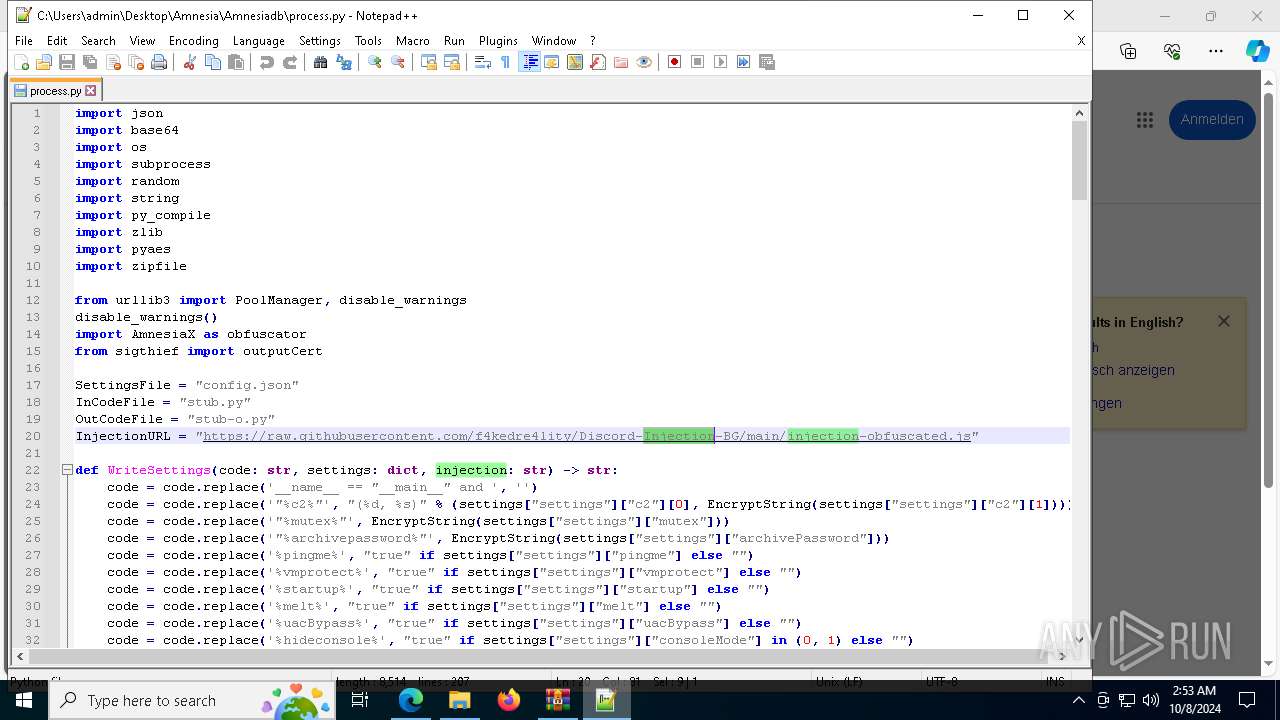
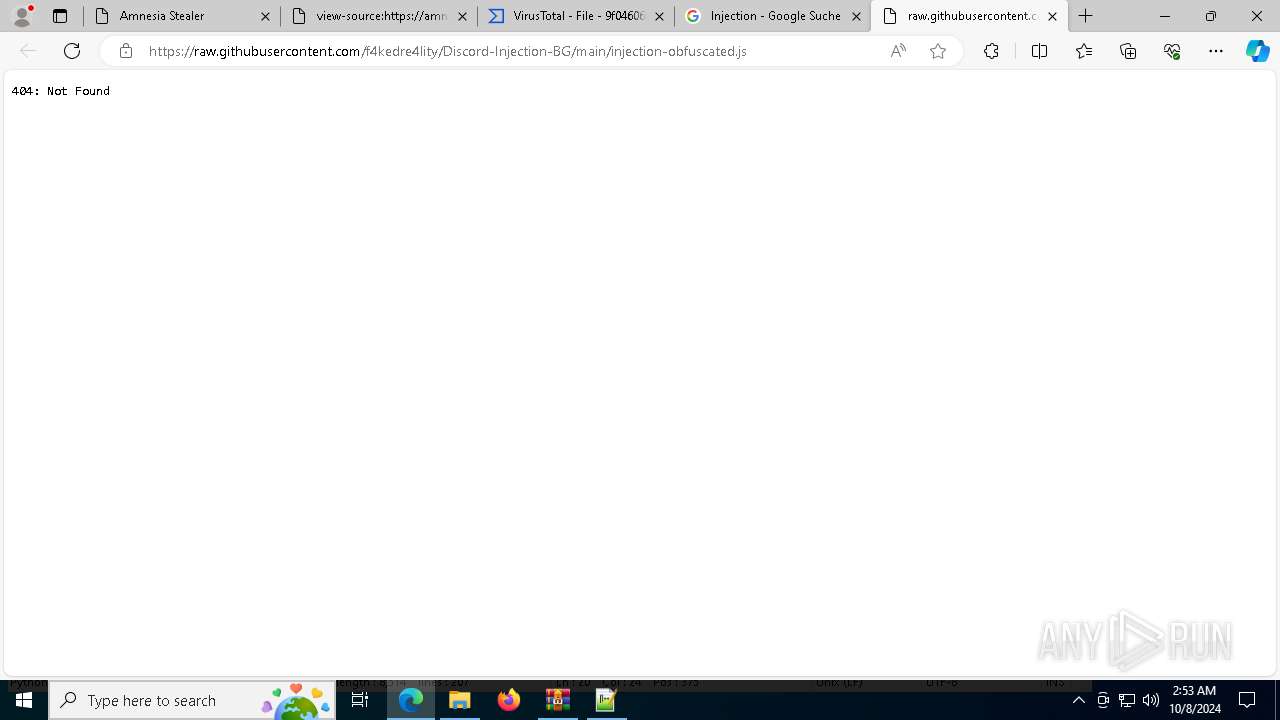
| 3332 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://raw.githubusercontent.com/f4kedre4lity/Discord-Injection-BG/main/injection-obfuscated.js | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | notepad++.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4528 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | upx.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5032 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2400 --field-trial-handle=2312,i,13373624039057699070,11798397339410377127,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
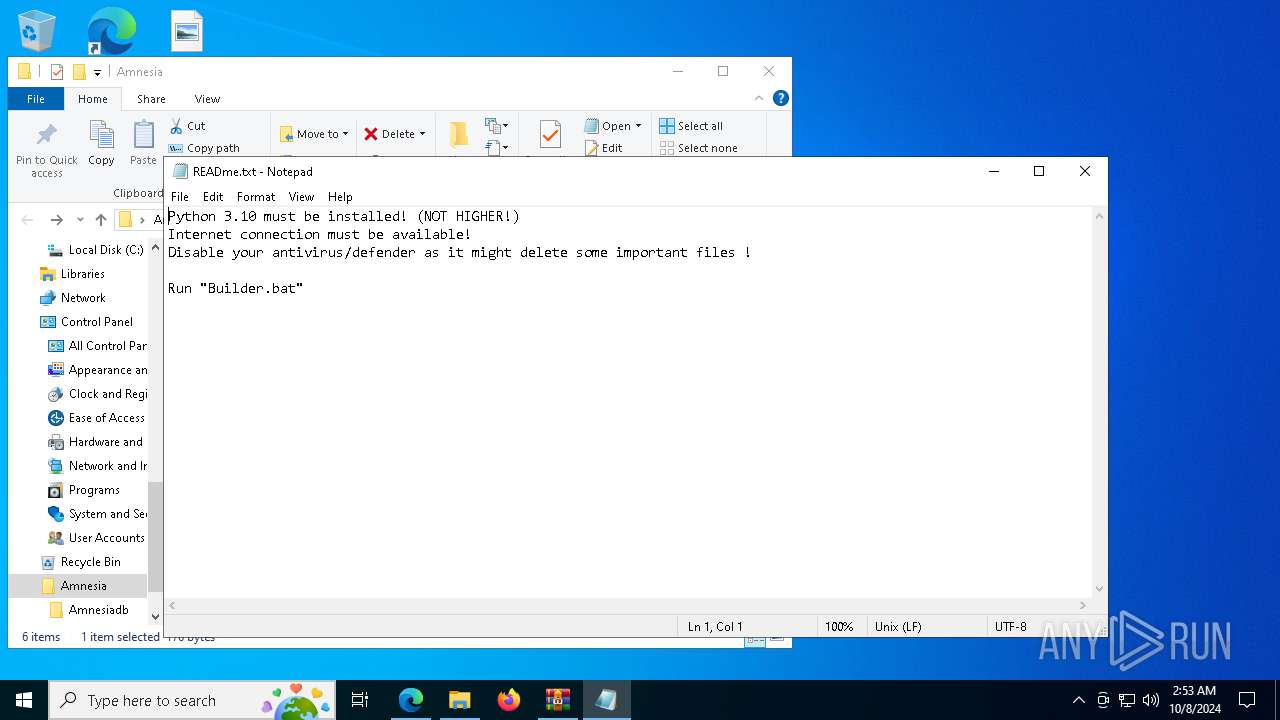
| 5656 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Amnesia\READme.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
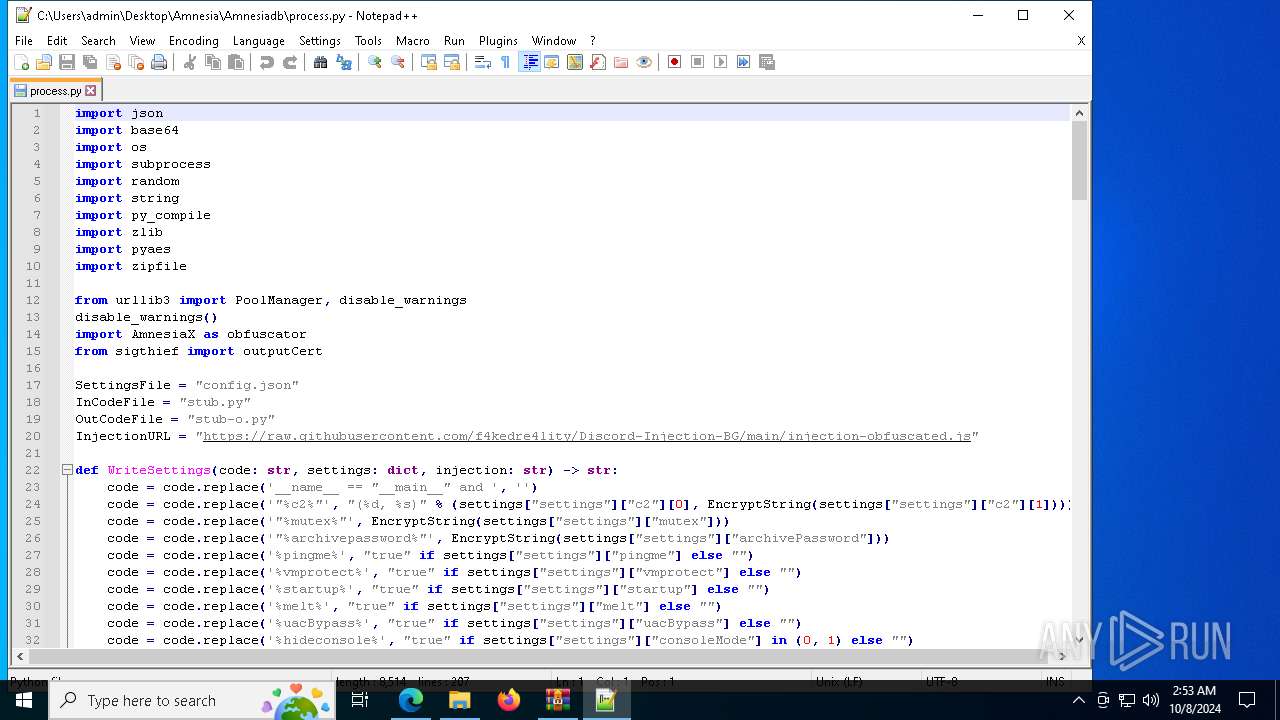
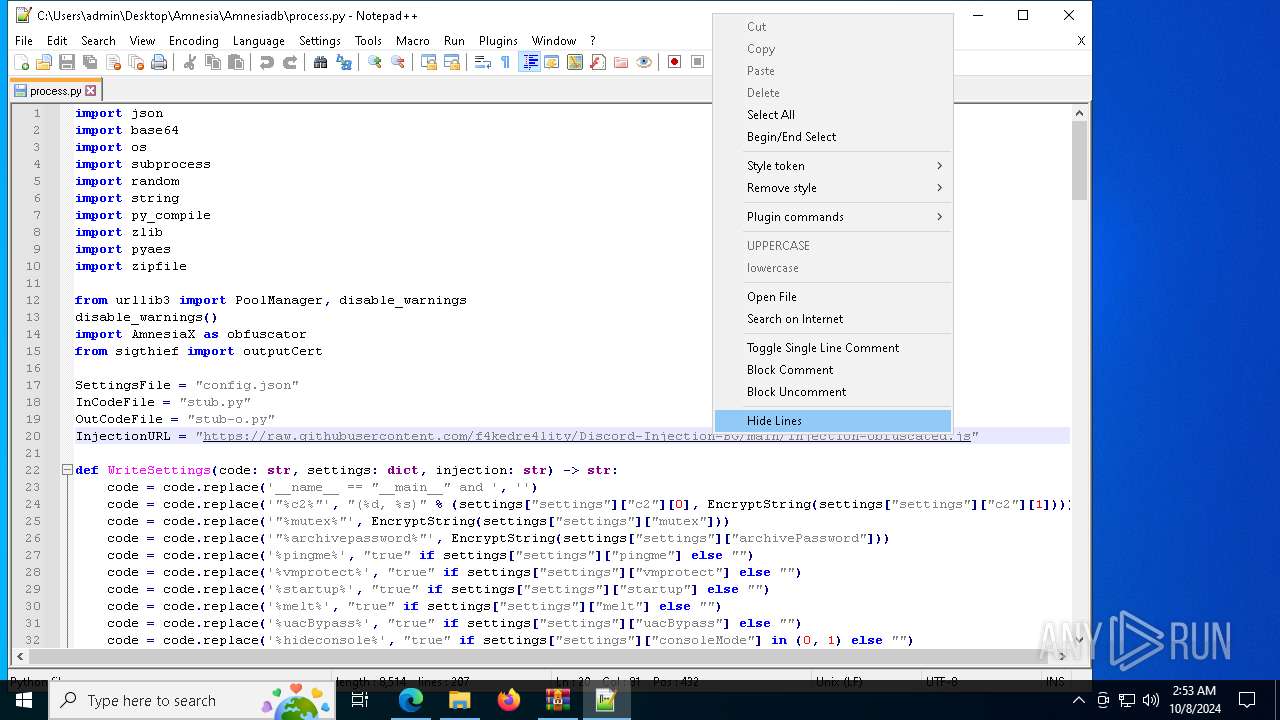
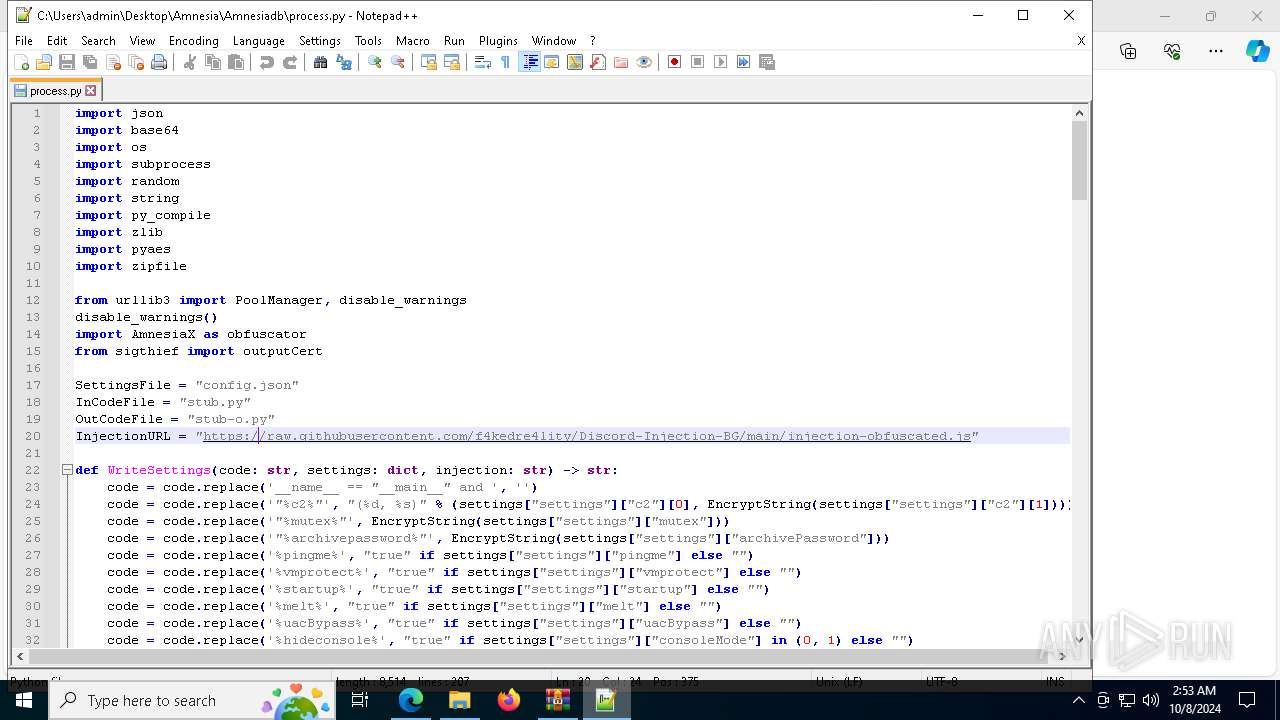
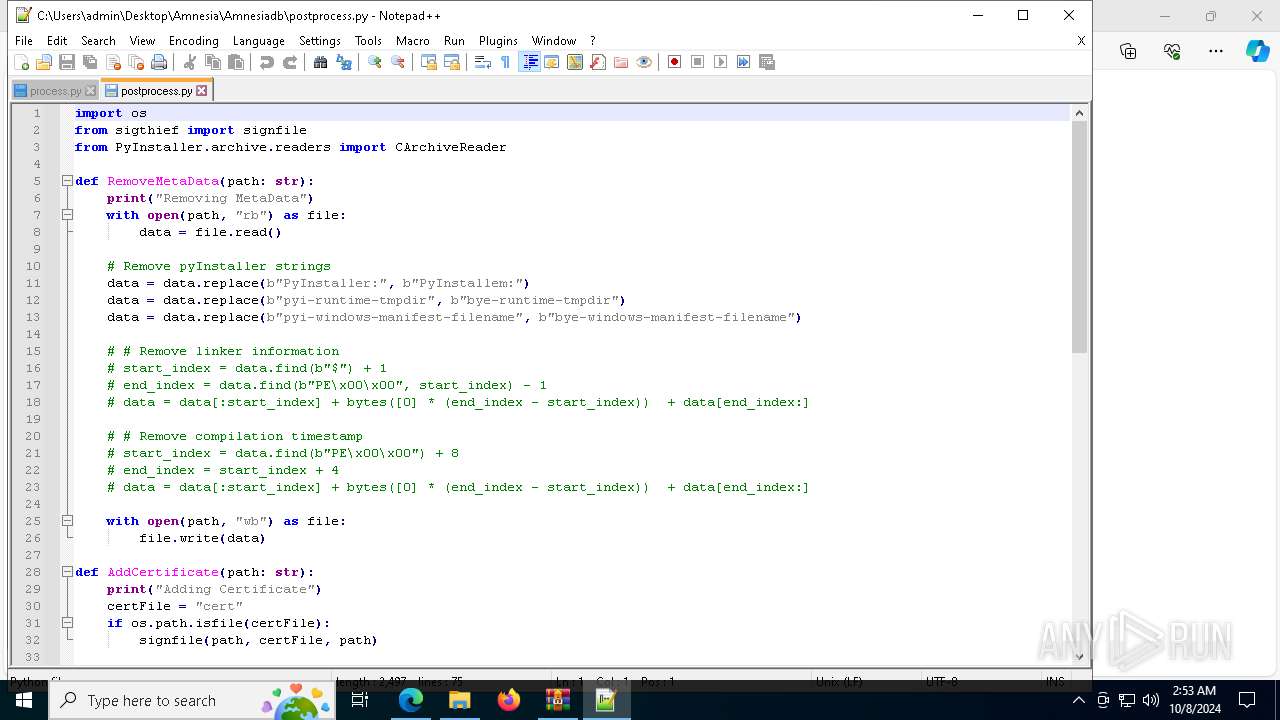
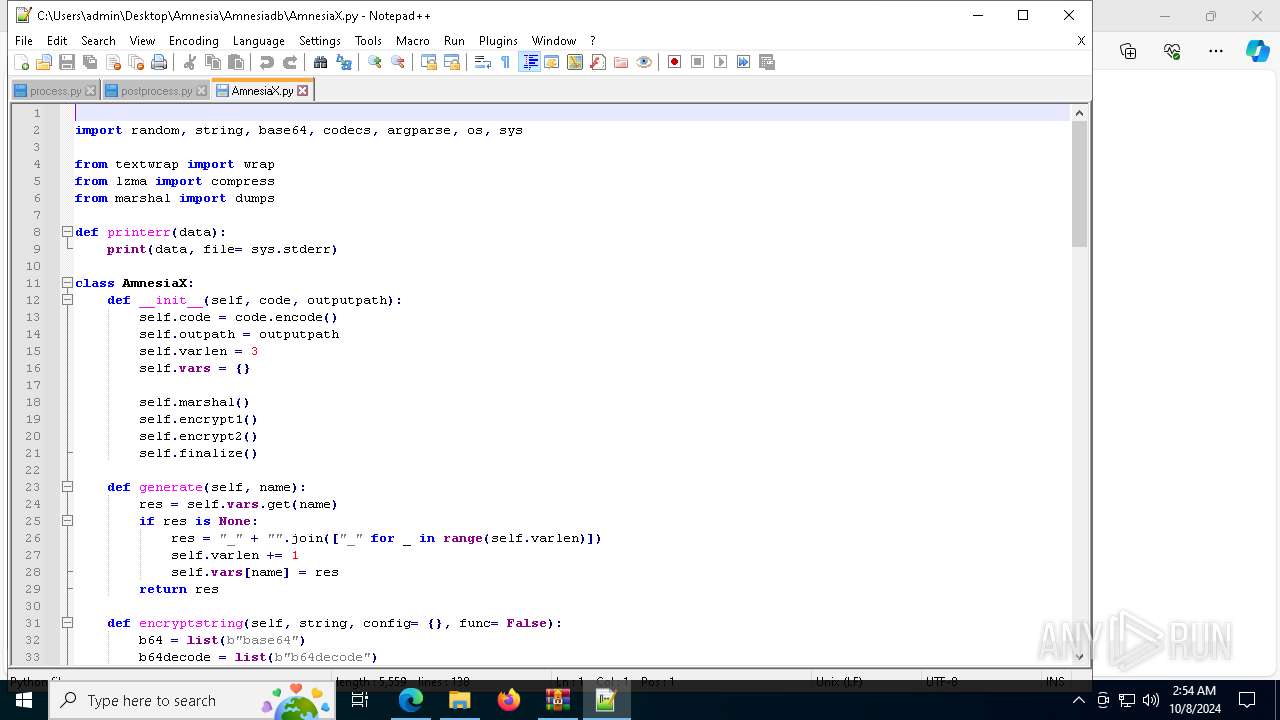
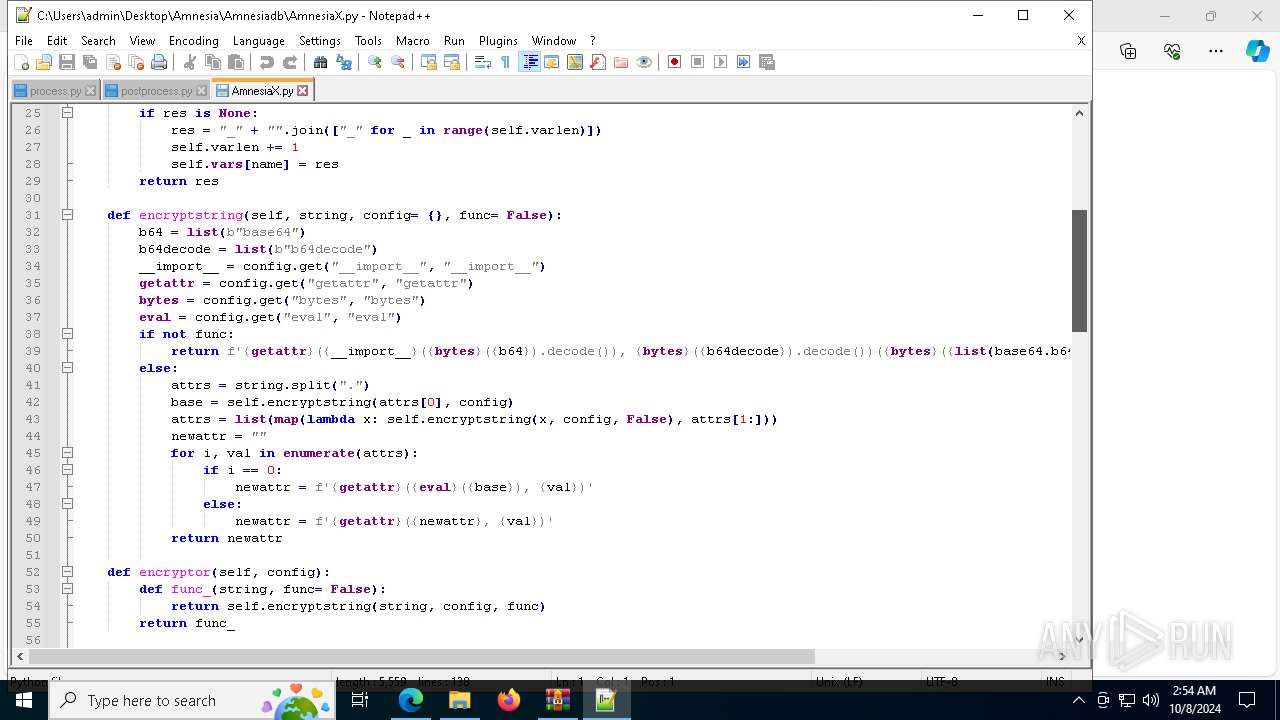
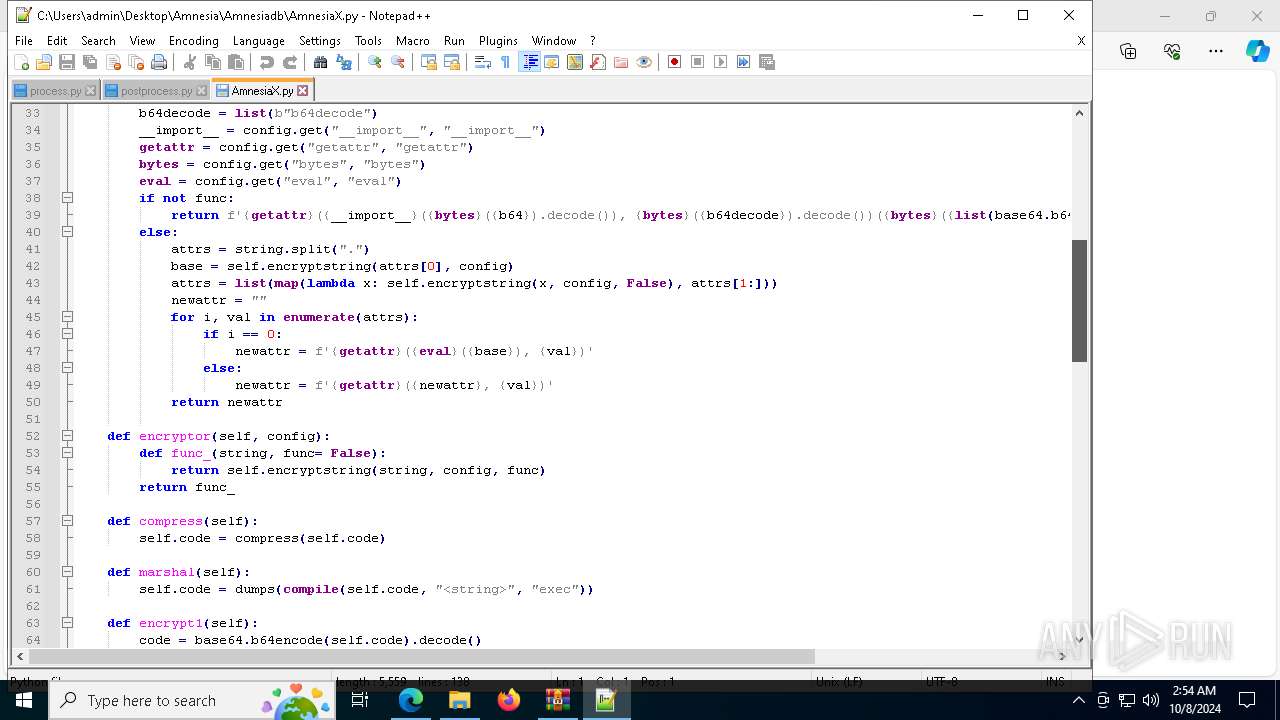
| 6128 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\Amnesia\Amnesiadb\process.py" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 6152 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6844 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 027
Read events
1 017
Write events
10
Delete events
0
Modification events
| (PID) Process: | (6128) notepad++.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6128) notepad++.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6128) notepad++.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6128) notepad++.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7820) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7820) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7820) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3332) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3332) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3332) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
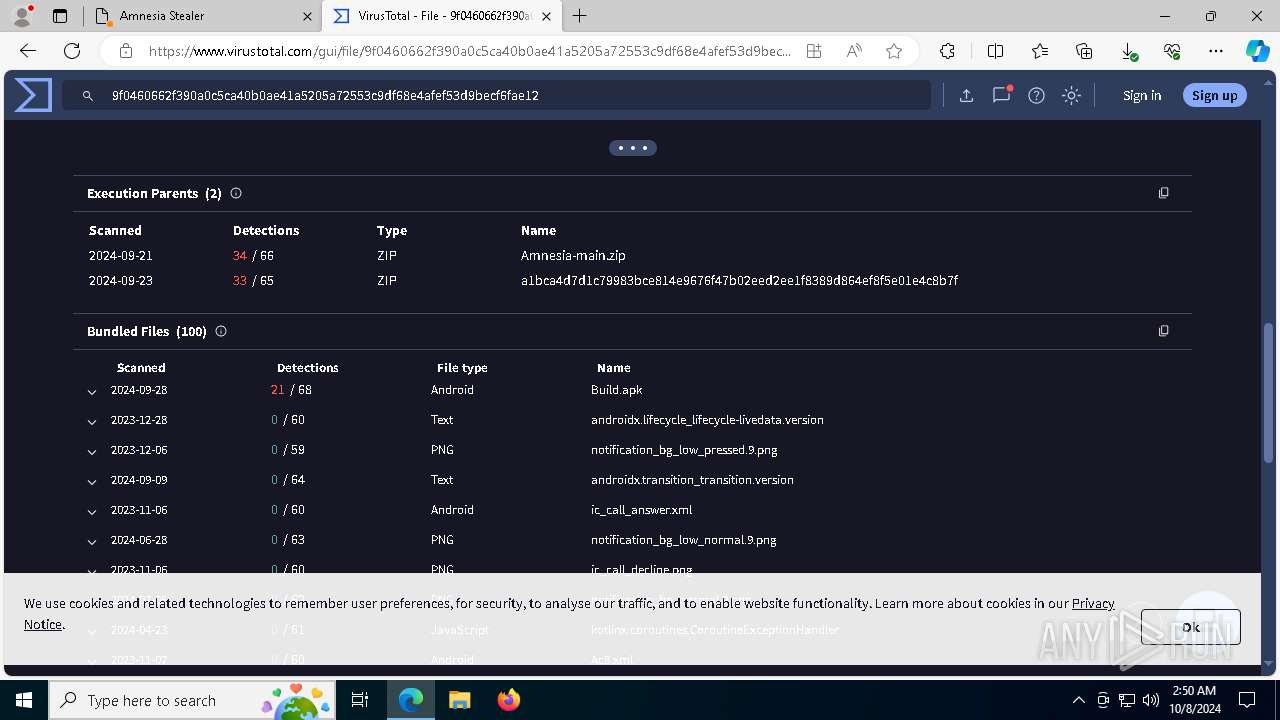
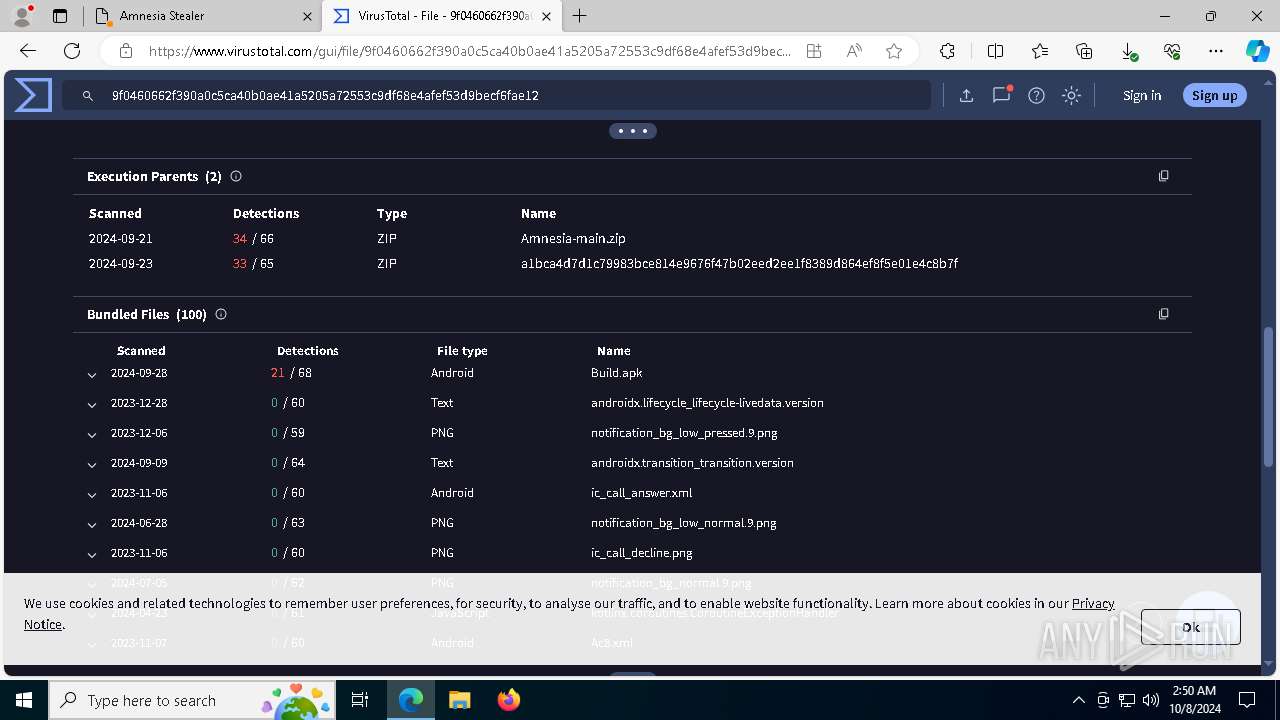
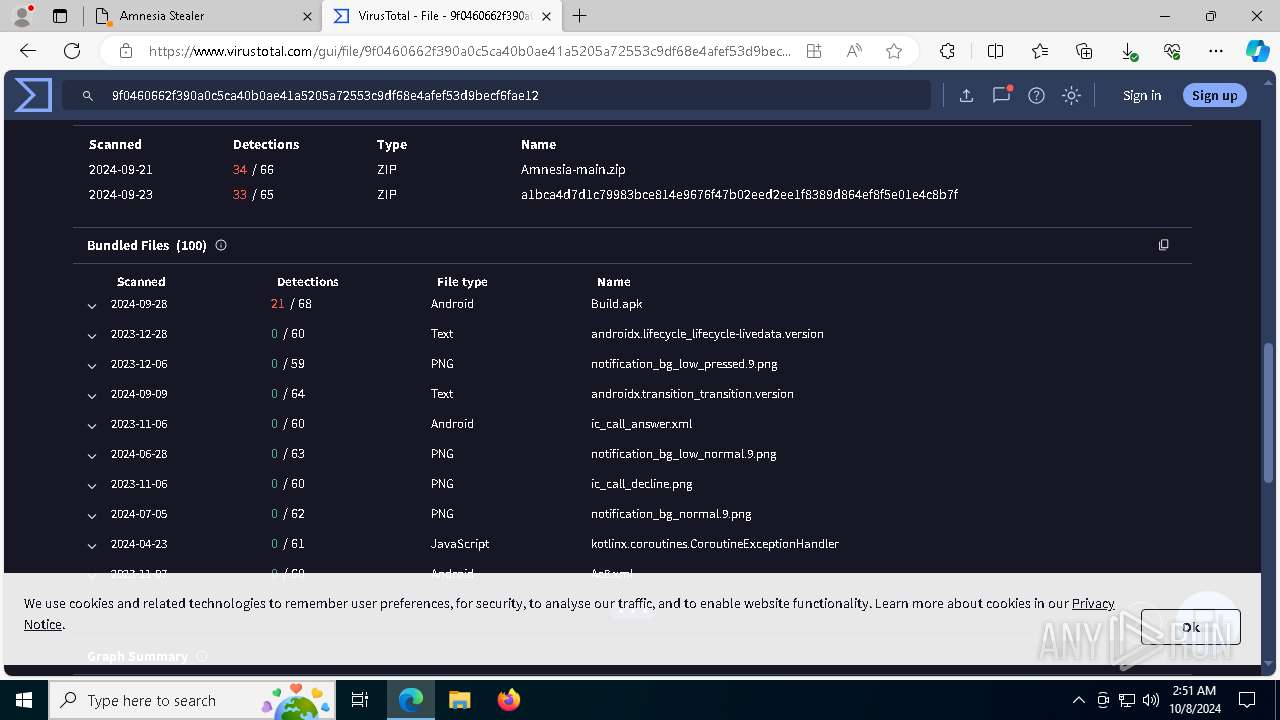
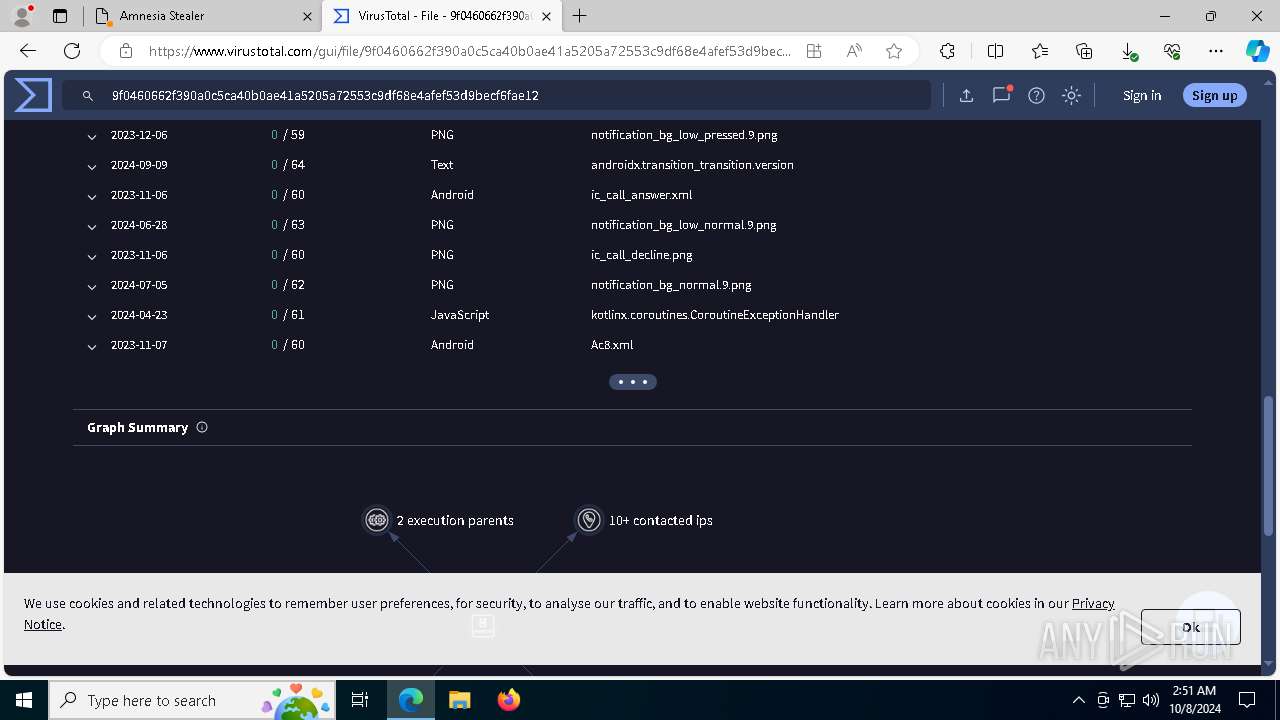
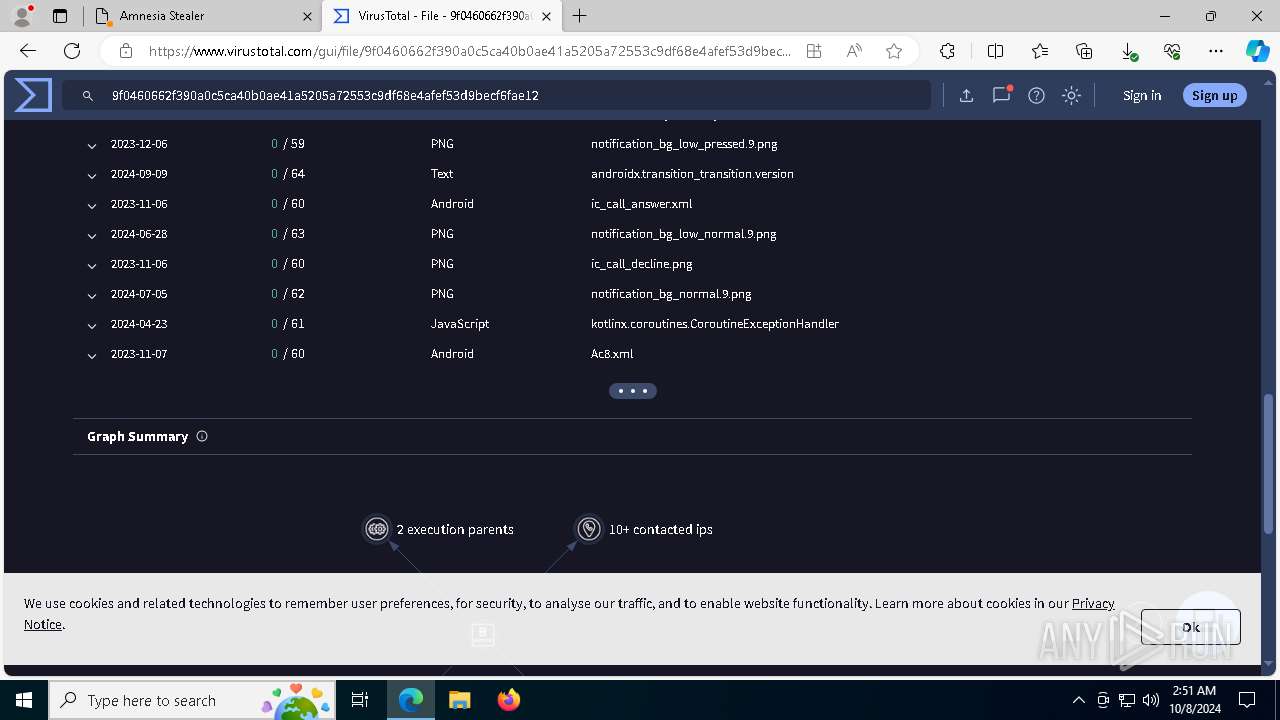
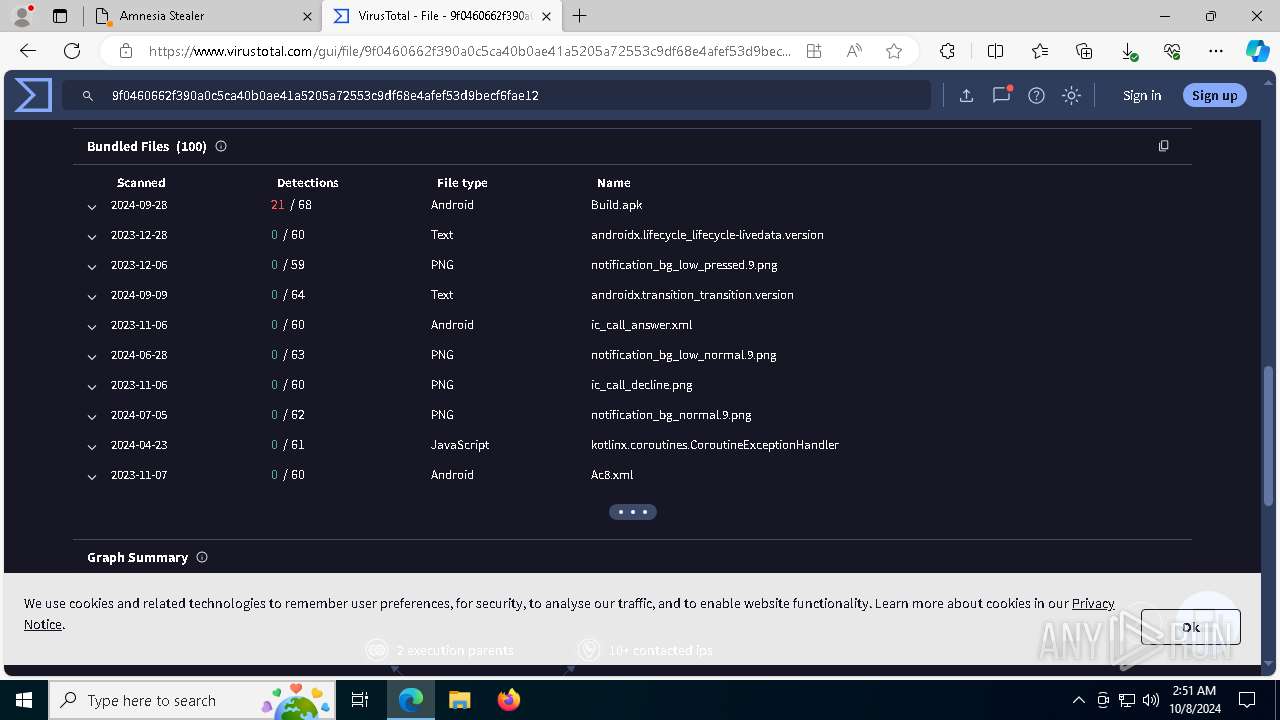
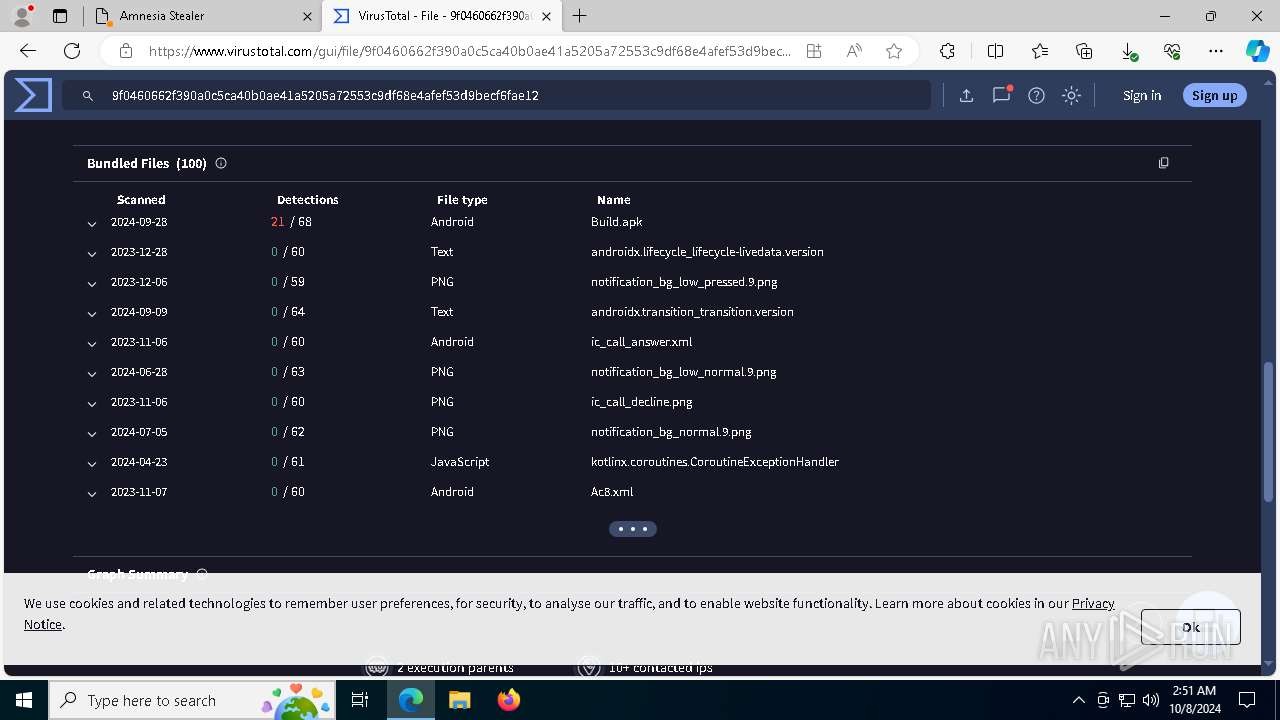
Executable files
4
Suspicious files
76
Text files
80
Unknown types
0
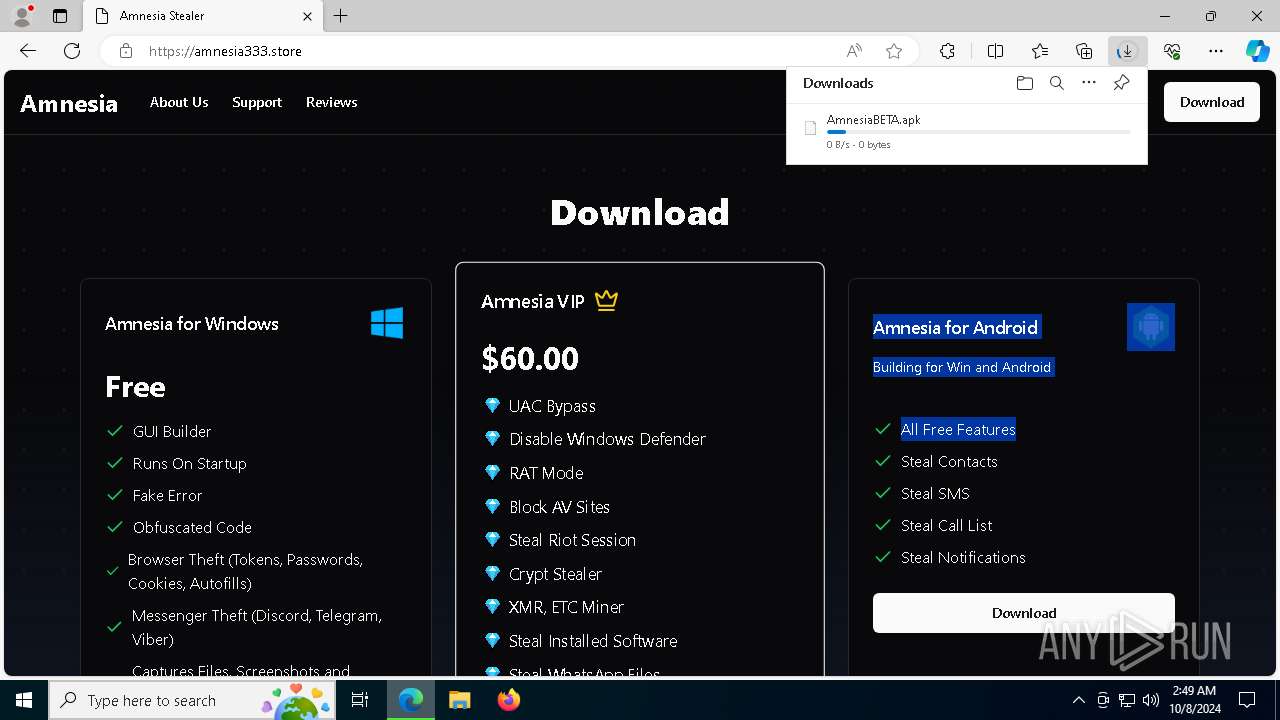
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_00025c | compressed | |
MD5:73C6439358B5F5DFC5862838B0E70008 | SHA256:61FCF8B0861D2AFE9DF01FF51ABB78FB36783BB995701CDAA473402825D42F45 | |||
| 5032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\f3035b6c-44e8-4997-a80c-9c0b78179f5d.tmp | ini | |
MD5:D751713988987E9331980363E24189CE | SHA256:4F53CDA18C2BAA0C0354BB5F9A3ECBE5ED12AB4D8E11BA873C2F11161202B945 | |||
| 5032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000258 | binary | |
MD5:93496B52B1C72DCDE8EE2CF7CB79E49B | SHA256:C650A2C7791790D23DEE7884217C64CF4167AFABCBD5620D430800D6BEFCF4B6 | |||
| 5032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\c43fa56b-6f48-48d9-8b18-7f7db59f7f59.tmp | binary | |
MD5:AC443DDBE91607315CFB9AB104061699 | SHA256:AC2BF0155F317B6248D03F203F927773FF8192BA5FC025F50A01D80898A9B87C | |||
| 5032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\SCT Auditing Pending Reports | ini | |
MD5:D751713988987E9331980363E24189CE | SHA256:4F53CDA18C2BAA0C0354BB5F9A3ECBE5ED12AB4D8E11BA873C2F11161202B945 | |||
| 5032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_00025a | image | |
MD5:4EACFF75CA34465CE2735D391DE748EC | SHA256:CC42F5E037137FA03DAD4090648B3E2CD0804AB4CEC8CFC66260AFE46CA6EE73 | |||
| 5032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\89c620eb-1411-4da0-b2de-7c29f5aa6554.tmp | binary | |
MD5:20D4B8FA017A12A108C87F540836E250 | SHA256:6028BD681DBF11A0A58DDE8A0CD884115C04CAA59D080BA51BDE1B086CE0079D | |||
| 5032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Sdch Dictionaries~RF3f7915.TMP | binary | |
MD5:20D4B8FA017A12A108C87F540836E250 | SHA256:6028BD681DBF11A0A58DDE8A0CD884115C04CAA59D080BA51BDE1B086CE0079D | |||
| 5032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\7ec401f1-6f0c-4c57-9d68-e6d07f71140f.tmp | ini | |
MD5:D751713988987E9331980363E24189CE | SHA256:4F53CDA18C2BAA0C0354BB5F9A3ECBE5ED12AB4D8E11BA873C2F11161202B945 | |||
| 5032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\TransportSecurity | binary | |
MD5:AC443DDBE91607315CFB9AB104061699 | SHA256:AC2BF0155F317B6248D03F203F927773FF8192BA5FC025F50A01D80898A9B87C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
194
DNS requests
227
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7028 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
740 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
8164 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8164 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5032 | msedge.exe | GET | 304 | 95.101.54.195:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | unknown | — | — | whitelisted |
5032 | msedge.exe | GET | 304 | 2.23.197.184:80 | http://x1.i.lencr.org/ | unknown | — | — | whitelisted |
5032 | msedge.exe | GET | 304 | 2.23.197.184:80 | http://r3.i.lencr.org/ | unknown | — | — | whitelisted |
3440 | svchost.exe | HEAD | 200 | 87.248.204.0:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0fbe8575-0922-4072-bf12-0eeea2f0e967?P1=1728680474&P2=404&P3=2&P4=JdRPMfR9d8cWE3cRd8AfO4B0oBGO1nQPTr4q5UPshL4KJIkW4mCWW8I%2bD3LmjCgUZ%2fSJ8beyo1A4so81evV7EQ%3d%3d | unknown | — | — | whitelisted |
3440 | svchost.exe | GET | 206 | 87.248.204.0:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0fbe8575-0922-4072-bf12-0eeea2f0e967?P1=1728680474&P2=404&P3=2&P4=JdRPMfR9d8cWE3cRd8AfO4B0oBGO1nQPTr4q5UPshL4KJIkW4mCWW8I%2bD3LmjCgUZ%2fSJ8beyo1A4so81evV7EQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7028 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
7028 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
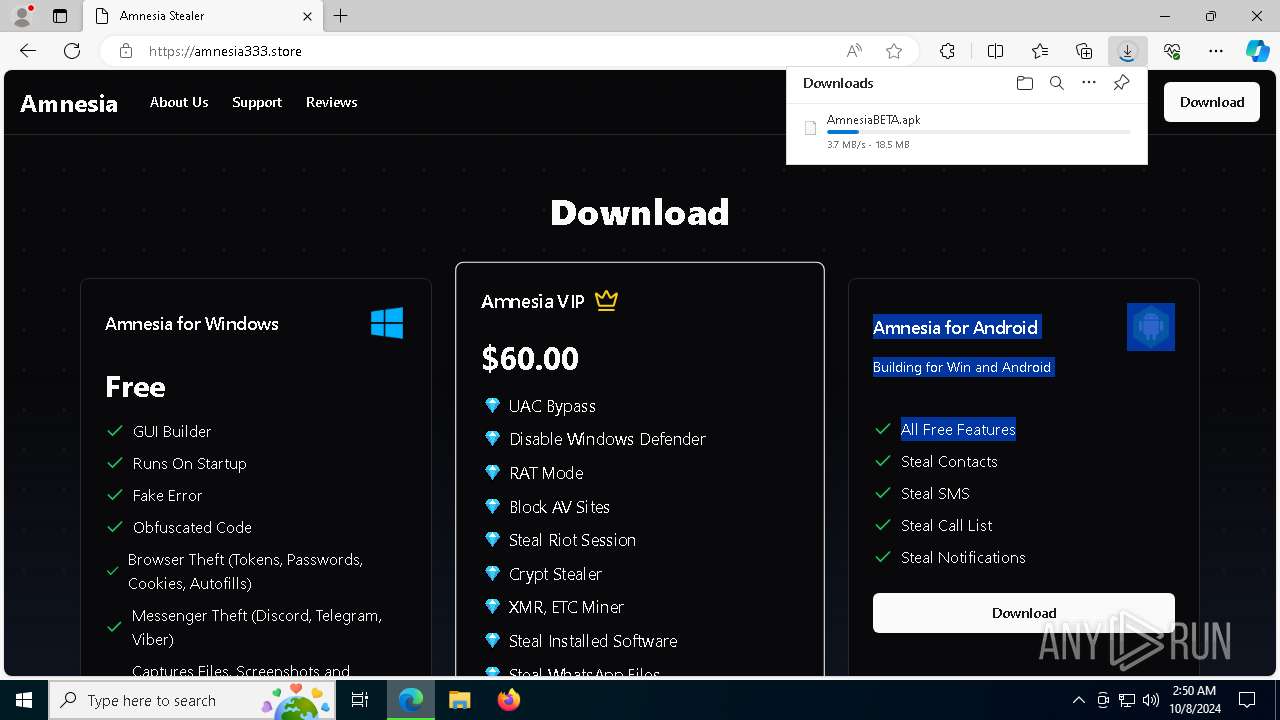
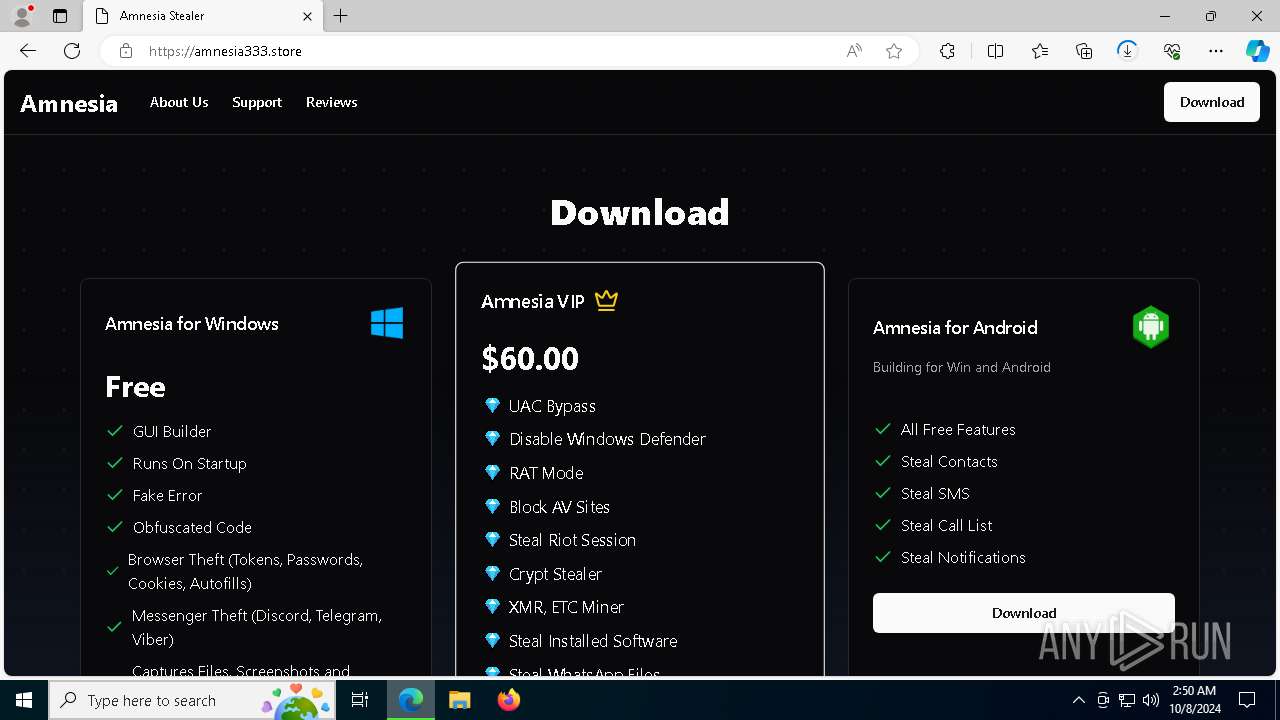
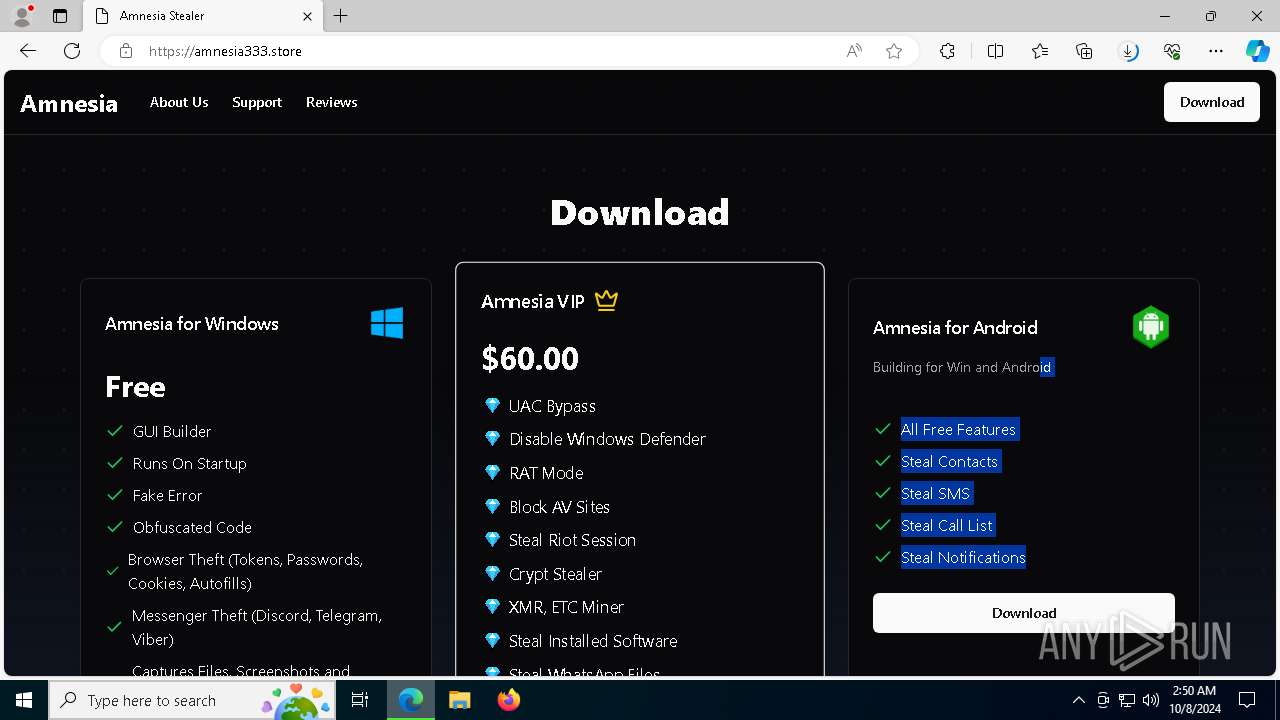
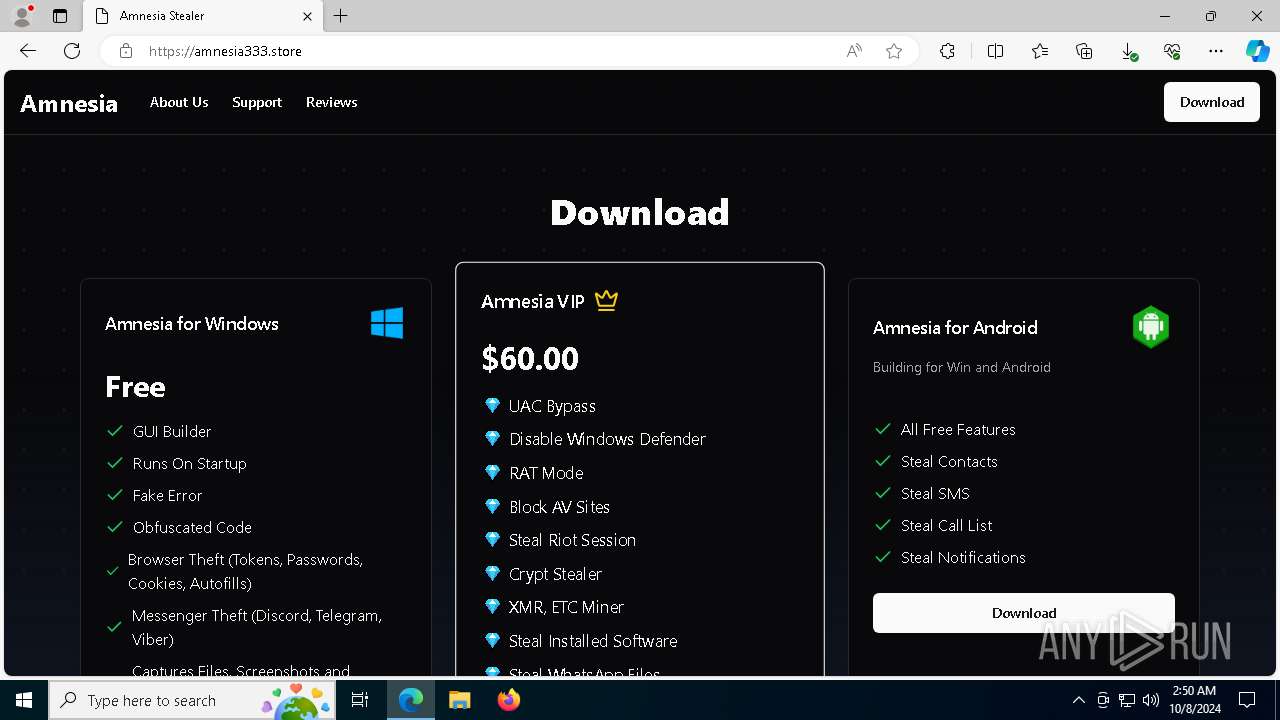
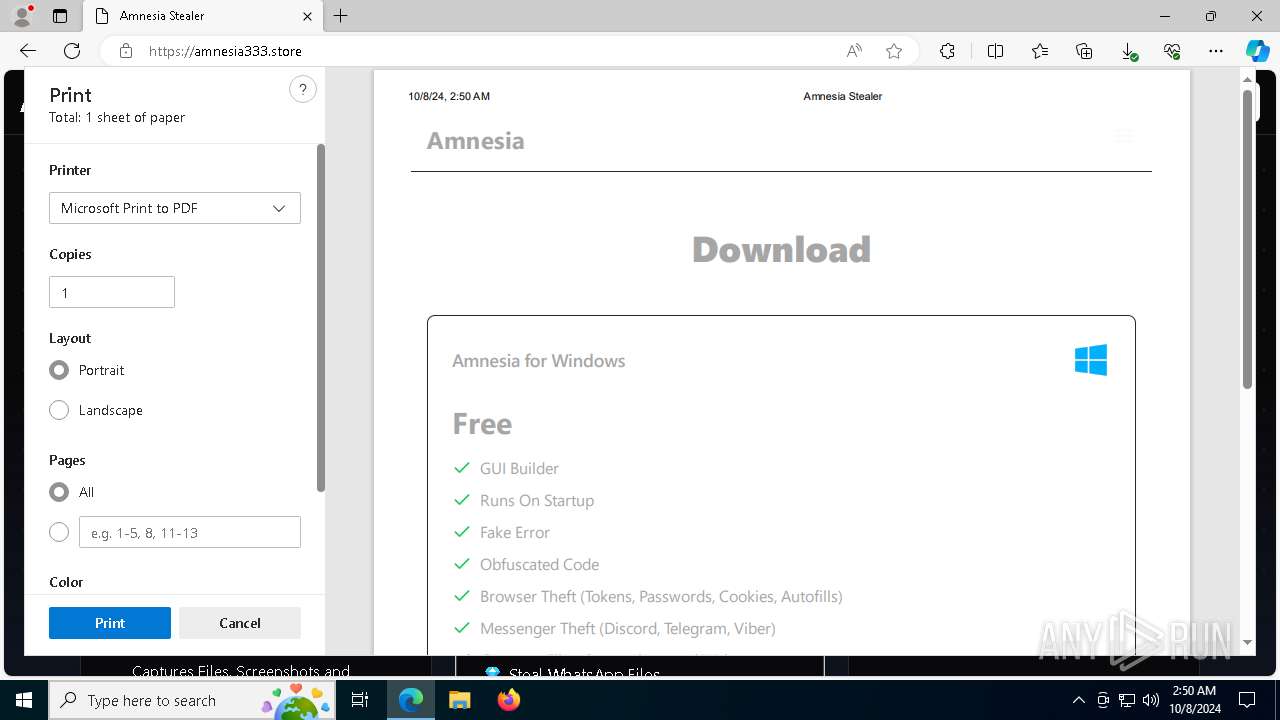
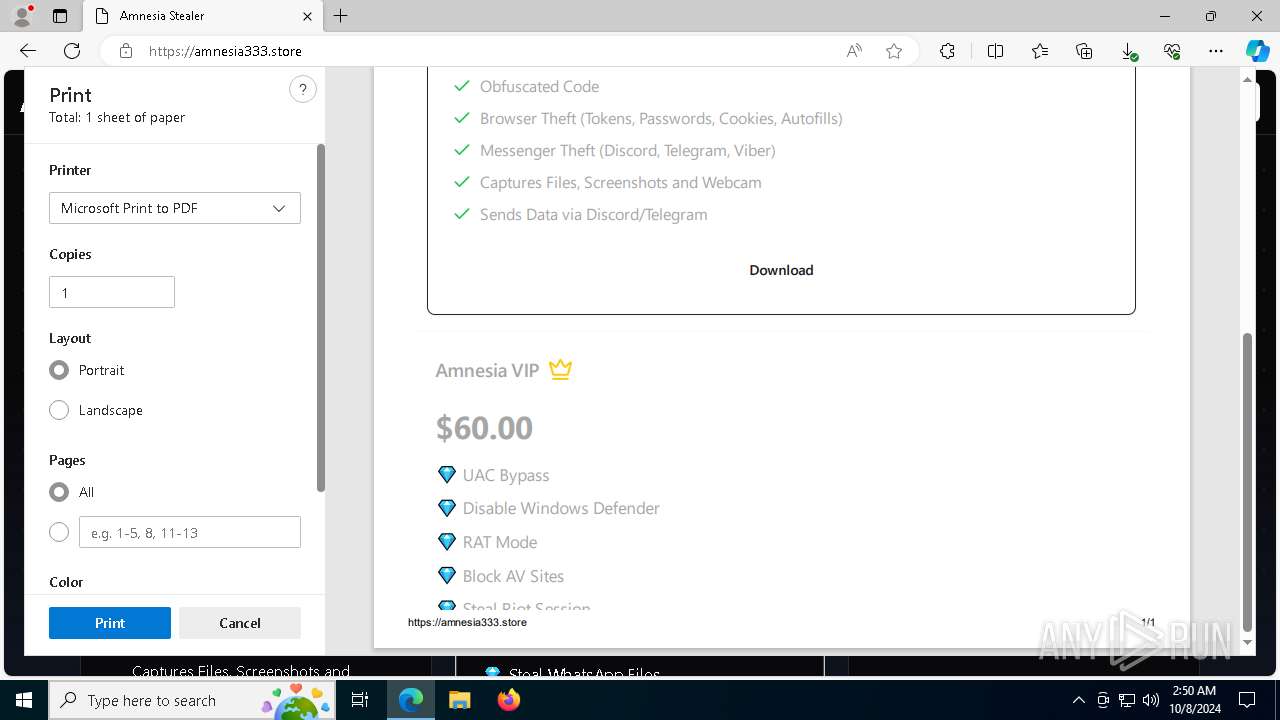
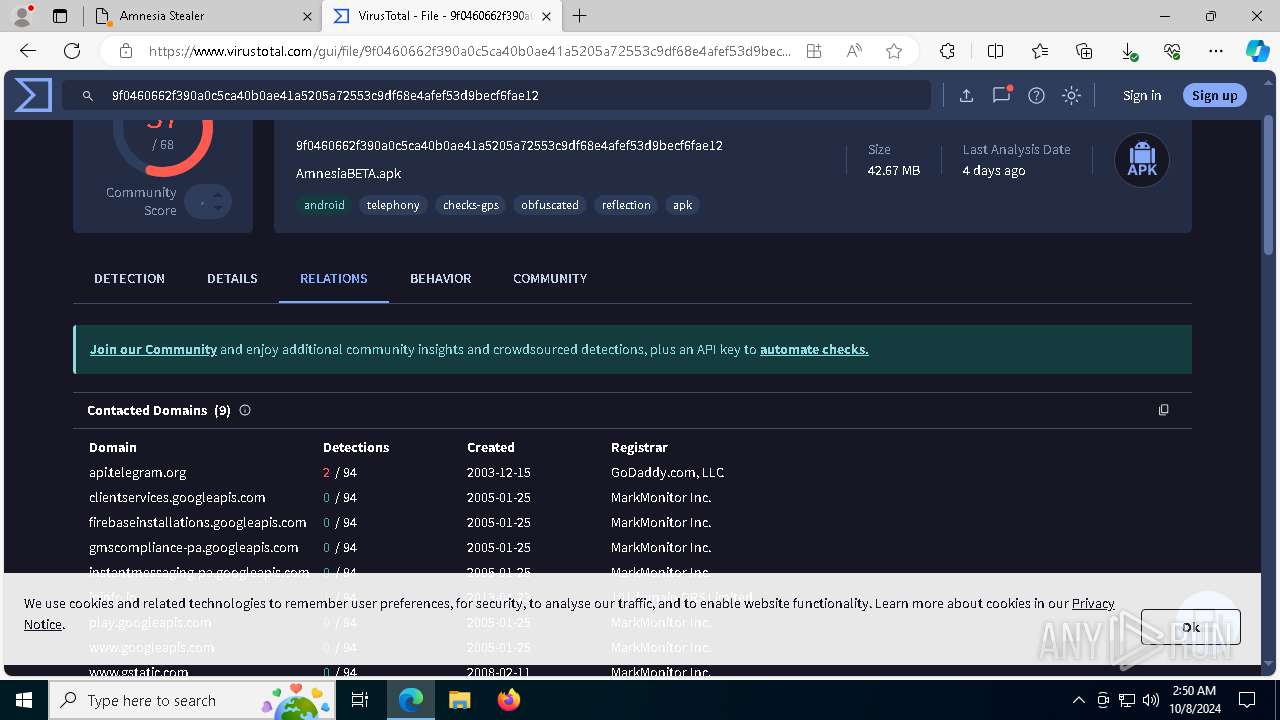
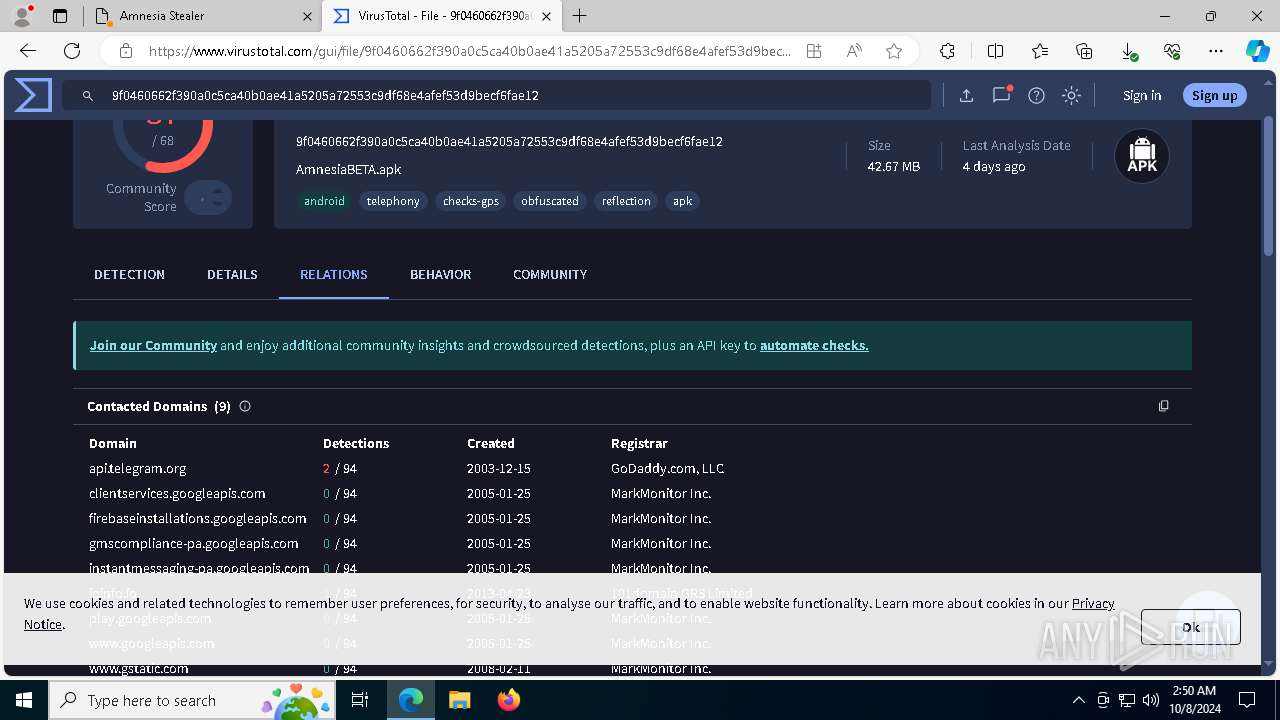
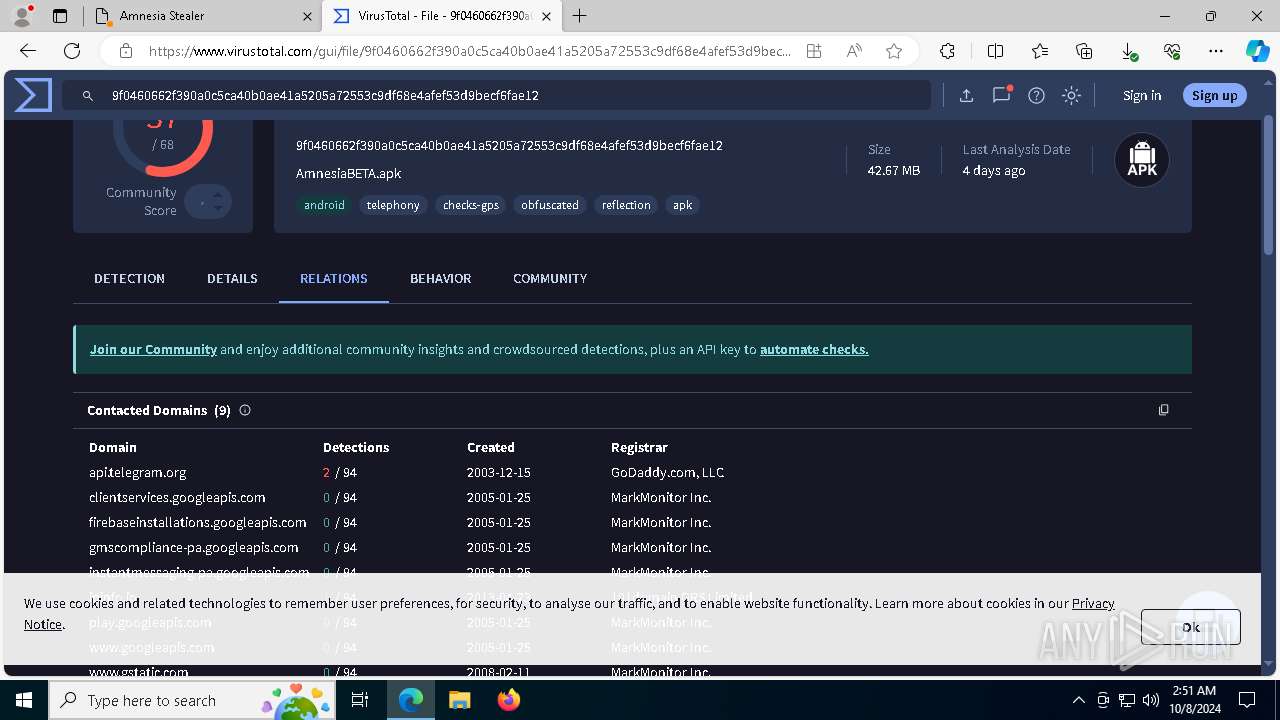
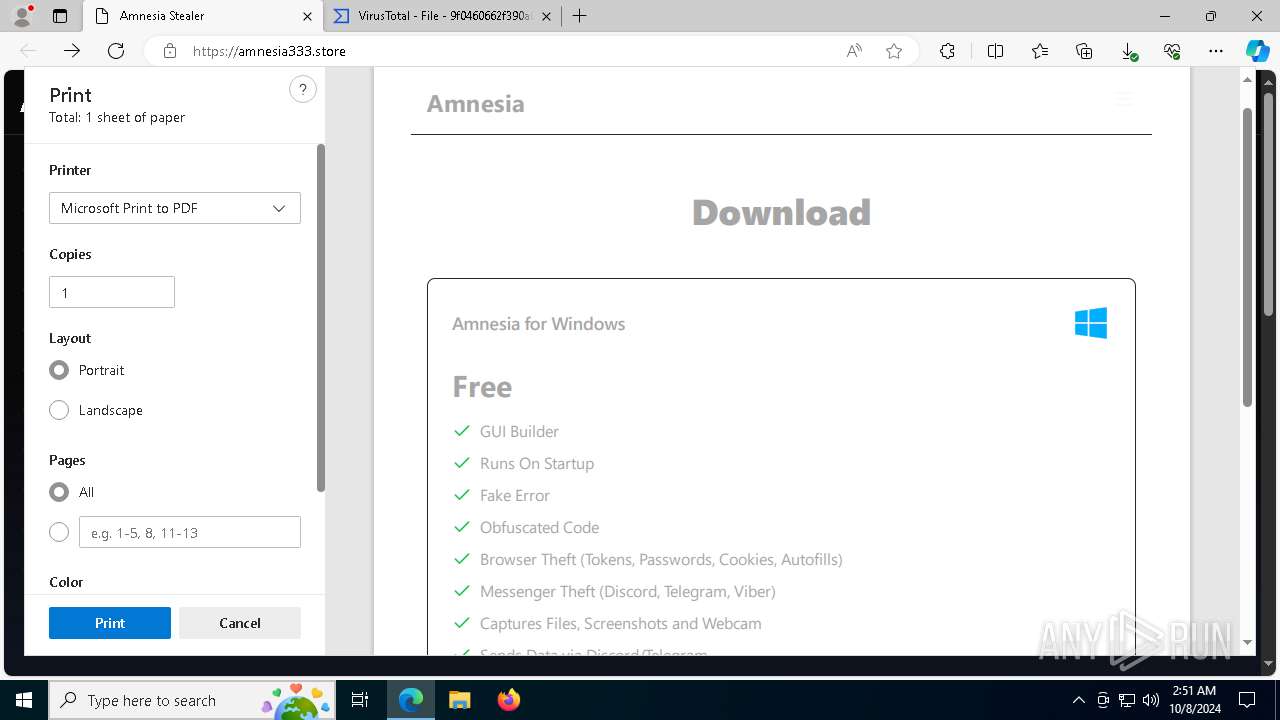
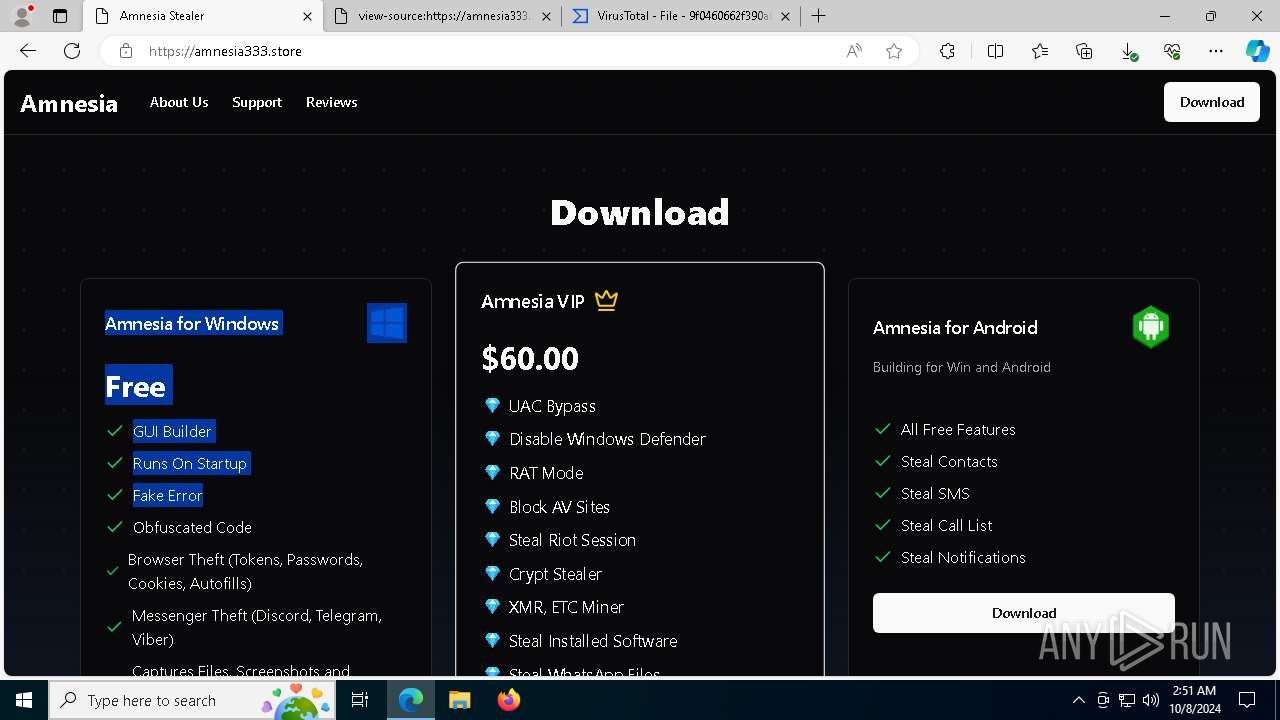
— | — | 15.197.225.128:443 | amnesia333.store | AMAZON-02 | US | unknown |
— | — | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
amnesia333.store |
| unknown |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
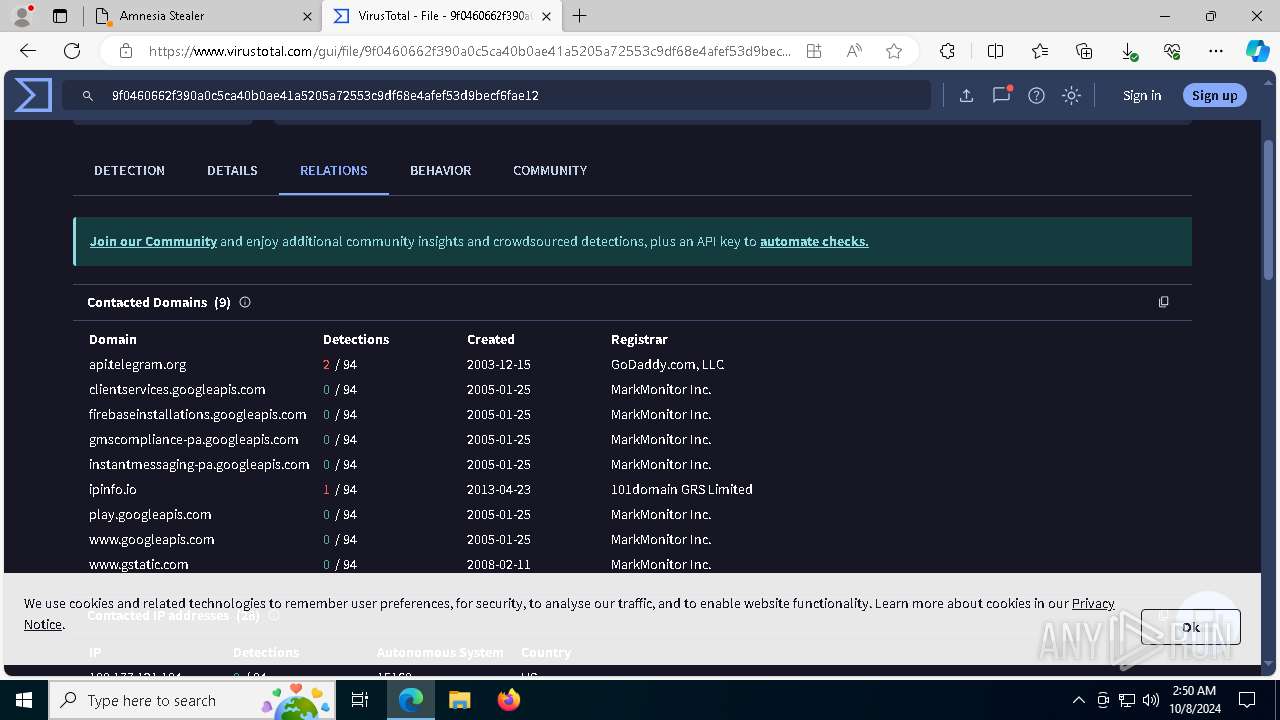
— | — | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
— | — | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
— | — | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
— | — | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
— | — | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
— | — | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
— | — | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
— | — | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
5032 | msedge.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
5032 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|