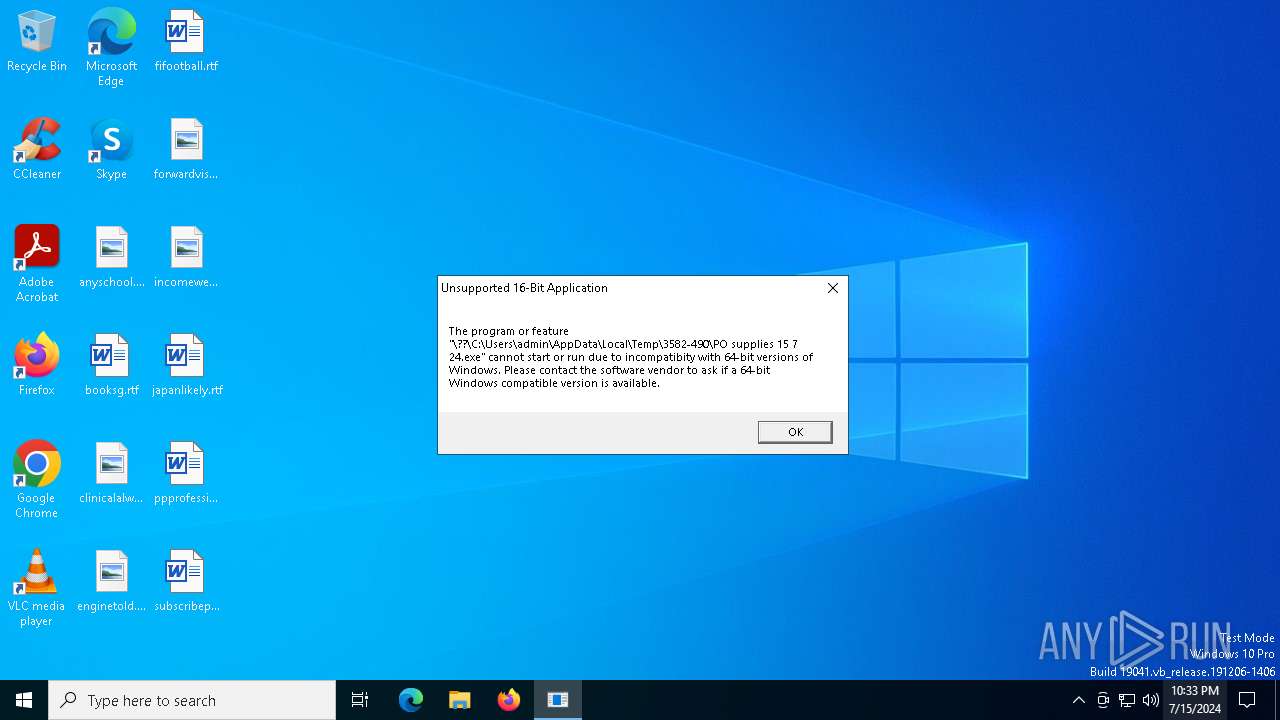
| File name: | PO supplies 15 7 24.exe |
| Full analysis: | https://app.any.run/tasks/eb36b7c9-5fe1-4d57-9125-58a9538f6150 |
| Verdict: | Malicious activity |
| Analysis date: | July 15, 2024, 22:32:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 8C4507C84E866D7A0677244D94C439F6 |
| SHA1: | B7917D2630306F79444A473903C0170CE8E58ABE |
| SHA256: | 08666EF4278F5E77D441949A6069B712FD4908FC75DF489ED9289DAA5FF3CF5E |
| SSDEEP: | 24576:DjyXSHnsLsXs1SgPV2x/DOhcgB/xf5JTHo0ocBd2T:nyX4nsLsXs1TPV2x/DOhcgB/xf5JTHoV |
MALICIOUS
Drops the executable file immediately after the start
- PO supplies 15 7 24.exe (PID: 5116)
- PO supplies 15 7 24.exe (PID: 6240)
Uses Task Scheduler to run other applications
- PO supplies 15 7 24.exe (PID: 5116)
Actions looks like stealing of personal data
- PO supplies 15 7 24.exe (PID: 6240)
SUSPICIOUS
Process drops legitimate windows executable
- PO supplies 15 7 24.exe (PID: 5116)
Starts a Microsoft application from unusual location
- PO supplies 15 7 24.exe (PID: 5116)
- PO supplies 15 7 24.exe (PID: 6240)
Executable content was dropped or overwritten
- PO supplies 15 7 24.exe (PID: 5116)
- PO supplies 15 7 24.exe (PID: 6240)
Reads security settings of Internet Explorer
- PO supplies 15 7 24.exe (PID: 5116)
- PO supplies 15 7 24.exe (PID: 6240)
Reads the date of Windows installation
- PO supplies 15 7 24.exe (PID: 5116)
- PO supplies 15 7 24.exe (PID: 6240)
Application launched itself
- PO supplies 15 7 24.exe (PID: 5116)
Mutex name with non-standard characters
- PO supplies 15 7 24.exe (PID: 6240)
INFO
Reads the machine GUID from the registry
- PO supplies 15 7 24.exe (PID: 5116)
Checks supported languages
- PO supplies 15 7 24.exe (PID: 5116)
- PO supplies 15 7 24.exe (PID: 6240)
Reads the computer name
- PO supplies 15 7 24.exe (PID: 5116)
- PO supplies 15 7 24.exe (PID: 6240)
Creates files or folders in the user directory
- PO supplies 15 7 24.exe (PID: 5116)
.NET Reactor protector has been detected
- PO supplies 15 7 24.exe (PID: 5116)
Create files in a temporary directory
- PO supplies 15 7 24.exe (PID: 5116)
- PO supplies 15 7 24.exe (PID: 6240)
Process checks computer location settings
- PO supplies 15 7 24.exe (PID: 5116)
- PO supplies 15 7 24.exe (PID: 6240)
Reads the software policy settings
- slui.exe (PID: 6804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:15 06:10:08+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 737792 |
| InitializedDataSize: | 2560 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb612e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Assistance SD |
| FileVersion: | 1.0.0.0 |
| InternalName: | SFtz.exe |
| LegalCopyright: | Copyright © Microsoft Corporation. All rights reserved. |
| LegalTrademarks: | - |
| OriginalFileName: | SFtz.exe |
| ProductName: | Assistance SD |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
146
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2716 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\QBloUDNxsti" /XML "C:\Users\admin\AppData\Local\Temp\tmp3655.tmp" | C:\Windows\SysWOW64\schtasks.exe | — | PO supplies 15 7 24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2716 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | "C:\Users\admin\AppData\Local\Temp\PO supplies 15 7 24.exe" | C:\Users\admin\AppData\Local\Temp\PO supplies 15 7 24.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Assistance SD Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6240 | "C:\Users\admin\AppData\Local\Temp\PO supplies 15 7 24.exe" | C:\Users\admin\AppData\Local\Temp\PO supplies 15 7 24.exe | PO supplies 15 7 24.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Assistance SD Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6772 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6804 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 437
Read events
5 420
Write events
17
Delete events
0
Modification events
| (PID) Process: | (5116) PO supplies 15 7 24.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5116) PO supplies 15 7 24.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (5116) PO supplies 15 7 24.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (5116) PO supplies 15 7 24.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6240) PO supplies 15 7 24.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6240) PO supplies 15 7 24.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6240) PO supplies 15 7 24.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6240) PO supplies 15 7 24.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2716) slui.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\sppcomapi.dll,-3200 |
Value: Software Licensing | |||
Executable files
8
Suspicious files
2
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5116 | PO supplies 15 7 24.exe | C:\Users\admin\AppData\Roaming\QBloUDNxsti.exe | executable | |
MD5:8C4507C84E866D7A0677244D94C439F6 | SHA256:08666EF4278F5E77D441949A6069B712FD4908FC75DF489ED9289DAA5FF3CF5E | |||
| 5116 | PO supplies 15 7 24.exe | C:\Users\admin\AppData\Local\Temp\tmp3655.tmp | xml | |
MD5:D4517C39475CB71FCA6A179E3CE2F3B7 | SHA256:711F70FF97E86EB09B999CD268DE82D5E0A841DDB7F6AF0C7C7108DDC54232C1 | |||
| 6240 | PO supplies 15 7 24.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileSyncConfig.exe | executable | |
MD5:D3A414EF031A42BA1123D47603FC88A4 | SHA256:FAA608BCBF259419084DFB51974BEE8B46D761C85CD8A5C4F65AE6A50513BDD8 | |||
| 6240 | PO supplies 15 7 24.exe | C:\Users\admin\AppData\Local\Temp\tmp5023.tmp | binary | |
MD5:3726A1BC26C35AEA43F5FE466F24772D | SHA256:95DAE30A31B1D425E2D3D75205F40290E813F03CDA738CB530C7D270A477E195 | |||
| 6240 | PO supplies 15 7 24.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\OneDrive.exe | executable | |
MD5:20D9FA645254123FD6D109E1D335B84F | SHA256:37D0689A88527EC64E6BD389CDAFF565D8AB1AC097F47CE19A406B450C598581 | |||
| 6240 | PO supplies 15 7 24.exe | C:\ProgramData\Adobe\ARM\S\388\AdobeARMHelper.exe | executable | |
MD5:8A4A3B145D7F991D1BAAAE5826602F82 | SHA256:CAC552F745EC9266994913E4669939213E62D87300A97D48FEC0E711114C38FE | |||
| 6240 | PO supplies 15 7 24.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileSyncHelper.exe | executable | |
MD5:8F9B1CD208452C1B078E61CAA801A1D1 | SHA256:3541C6B5BF2031B56C052033BE3F4D3C8BED817A8BA9D7A71D1E4C255D531C73 | |||
| 6240 | PO supplies 15 7 24.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\OneDriveStandaloneUpdater.exe | executable | |
MD5:D6EC7C3D0D3AD23648916034299F2422 | SHA256:7C660B00206AA49FA67DFBB0E2A18C0BABFFC4A571191819104F86F4E069F586 | |||
| 6240 | PO supplies 15 7 24.exe | C:\Users\admin\AppData\Local\Temp\3582-490\PO supplies 15 7 24.exe | binary | |
MD5:AE303747897DAF45E48698D2AE593960 | SHA256:6AD9D05E2F8AB4B9050DA219CC18AEF707FD79FF7EE6E108BFB5F1D262C26DBB | |||
| 6240 | PO supplies 15 7 24.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | executable | |
MD5:0A054D115D80E0DC4ED8A99EEE83E756 | SHA256:32479DB69F86D7A079A8FF8C34EC92916CDEFFE92009CBB488823F496F6E811E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
76
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1828 | svchost.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6300 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1828 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4632 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6300 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5268 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
4092 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1828 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3868 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4448 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4656 | SearchApp.exe | 104.126.37.171:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1828 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1828 | svchost.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |