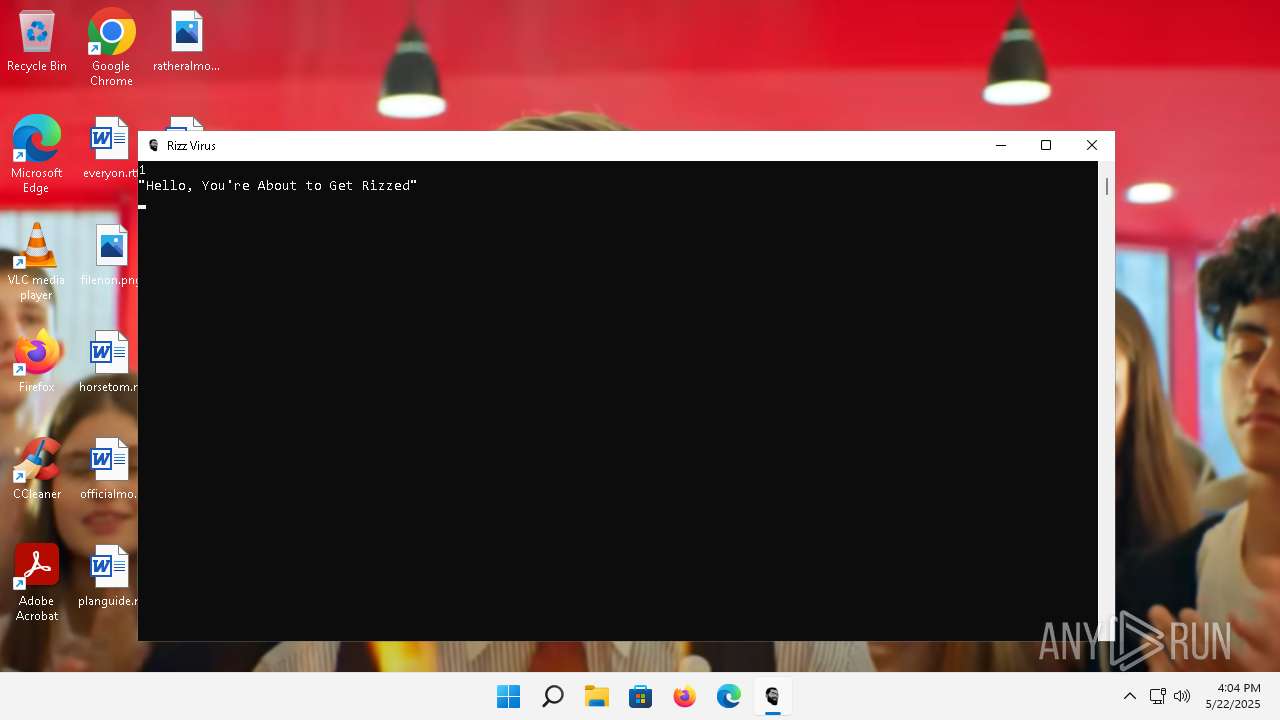
| File name: | Rizz.exe |
| Full analysis: | https://app.any.run/tasks/ef2fa358-9d7a-4f0e-b883-c2c7ef31c5ec |
| Verdict: | Malicious activity |
| Analysis date: | May 22, 2025, 16:04:12 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 0155390AC813EDDBCB5DB0FF1DF25271 |
| SHA1: | 4B010DB1811D04339C19736657CBC6F59CE9CAEE |
| SHA256: | 082C168D2364E7D670AB1EEFF480E739C0432176271C499705B7C37B39EBC2B4 |
| SSDEEP: | 6144:N1obzNGjj/bqihawuqYzet0YX82ytbC6W2hw5wvjjjPjjjj0:H0R+jAmZvwvjjjPjjjj0 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4824)
Downloads file from URI via Powershell
- powershell.exe (PID: 784)
Starts CMD.EXE for commands execution
- Rizz.exe (PID: 2268)
Executing commands from a ".bat" file
- Rizz.exe (PID: 2268)
Imports DLL using pinvoke
- powershell.exe (PID: 1428)
Reads the Internet Settings
- powershell.exe (PID: 784)
- wscript.exe (PID: 3372)
- cmd.exe (PID: 4824)
CSC.EXE is used to compile C# code
- csc.exe (PID: 5176)
Changes the desktop background image
- powershell.exe (PID: 1428)
Executable content was dropped or overwritten
- csc.exe (PID: 5176)
The process executes VB scripts
- cmd.exe (PID: 4824)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4824)
INFO
Checks supported languages
- Rizz.exe (PID: 2268)
- csc.exe (PID: 5176)
- cvtres.exe (PID: 2028)
The sample compiled with english language support
- Rizz.exe (PID: 2268)
Create files in a temporary directory
- Rizz.exe (PID: 2268)
- cvtres.exe (PID: 2028)
- csc.exe (PID: 5176)
Disables trace logs
- powershell.exe (PID: 784)
Changes the registry key values via Powershell
- cmd.exe (PID: 4824)
Reads the machine GUID from the registry
- csc.exe (PID: 5176)
Checks proxy server information
- powershell.exe (PID: 784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.2) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2019:07:30 08:52:08+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 92672 |
| InitializedDataSize: | 158720 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 2.1.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 2.1.0.0 |
| ProductVersion: | 2.0.0.0 |
| ProductName: | RizzVirus |
| OriginalFileName: | RizzU |
| InternalName: | Rizz |
| FileDescription: | rizz |
| CompanyName: | WareForge Inc. |
| LegalTrademarks: | Rizz |
| LegalCopyright: | Script Copyright© |
| PrivateBuild: | None |
| SpecialBuild: | None |
| Comments: | so rizz ?????? |
Total processes
111
Monitored processes
12
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\speech.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 784 | powershell -Command "Invoke-WebRequest -Uri 'https://i.postimg.cc/7P96ygVv/Betsy-Sigma-Boy-Official-Music-Video-You-Tube-Google-Chrome-2025-05-22-17.png' -OutFile 'C:\Users\admin\AppData\Local\Temp\rizz_wallpaper.jpg'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1428 | powershell -Command "Set-ItemProperty -Path 'HKCU:\Control Panel\Desktop\' -Name Wallpaper -Value 'C:\Users\admin\AppData\Local\Temp\rizz_wallpaper.jpg'; Add-Type -TypeDefinition 'using System; using System.Runtime.InteropServices; public class Wallpaper { [DllImport(\"user32.dll\")] public static extern int SystemParametersInfo(int uAction, int uParam, string lpvParam, int fuWinIni); }'; [Wallpaper]::SystemParametersInfo(20, 0, 'C:\Users\admin\AppData\Local\Temp\rizz_wallpaper.jpg', 3)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1664 | C:\Windows\system32\svchost.exe -k NetworkService -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2028 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES596F.tmp" "c:\Users\admin\AppData\Local\Temp\CSCFD1BB8A47BB4379A6E15D18BDEC8255.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 2268 | "C:\Users\admin\Desktop\Rizz.exe" | C:\Users\admin\Desktop\Rizz.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3324 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3372 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\speech.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4124 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Rizz.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4824 | "C:\Windows\system32\cmd" /c "C:\Users\admin\AppData\Local\Temp\401B.tmp\401C.tmp\401D.bat C:\Users\admin\Desktop\Rizz.exe" | C:\Windows\System32\cmd.exe | — | Rizz.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 555
Read events
13 363
Write events
192
Delete events
0
Modification events
| (PID) Process: | (1428) powershell.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: C:\Users\admin\AppData\Local\Temp\rizz_wallpaper.jpg | |||
| (PID) Process: | (4824) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ApplicationAssociationToasts |
| Operation: | write | Name: | VBSFile_.vbs |
Value: 0 | |||
| (PID) Process: | (4824) cmd.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\System32\WScript.exe.FriendlyAppName |
Value: Microsoft ® Windows Based Script Host | |||
| (PID) Process: | (4824) cmd.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\System32\WScript.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (4824) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (4824) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4824) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4824) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4824) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3372) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
4
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2268 | Rizz.exe | C:\Users\admin\AppData\Local\Temp\401B.tmp\401C.tmp\401D.bat | text | |
MD5:6B1CB29B56D5109D62CF569E4FEE88CE | SHA256:A4CA301D2906A697C54037702D4CBAC55F1AA82C9B15936B5C20EF5DAD7DD6A7 | |||
| 784 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:60F8A223A937F3B11959366994F3C4F2 | SHA256:AE2ADAD49CDCBD15711D840A5C7A223F3CCAB7CF118F82CEAAA003DA05037B4C | |||
| 784 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ar34bjfy.daw.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1428 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5q3arzee.1xc.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 784 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\CLR_v4.0\UsageLogs\powershell.exe.log | text | |
MD5:FD76E9A67A0A9BE485B8A6F176C5034F | SHA256:FDFE950055868366771B1EE65C0CDF831650DE21B28FE17E4232A9744EABE342 | |||
| 1428 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_z50qjowu.guf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 784 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_d2iieozt.3cr.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5176 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCFD1BB8A47BB4379A6E15D18BDEC8255.TMP | binary | |
MD5:1850ABCF7F67B03C02481A98CD493C6A | SHA256:DA4658B94B668D26FEF84E92452AC517A600A570FC8D5C92DB8A165372BC970E | |||
| 1428 | powershell.exe | C:\Users\admin\AppData\Local\Temp\3jfqpvpe.cmdline | text | |
MD5:A098A9C4ABC0ADBD5057F6C4D070AB02 | SHA256:7379FD8A7B28DCB307377C95367B64EC2B899F3AEF660D07914186388894CEA7 | |||
| 5176 | csc.exe | C:\Users\admin\AppData\Local\Temp\3jfqpvpe.out | text | |
MD5:3E0B4BBB7FBDFDAF5C0A46C9749EDE1E | SHA256:203121070EA537FBC6295F96610B1B015C97FE09796CC356F0A23A1972B0DA77 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
15
DNS requests
11
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5812 | MoUsoCoreWorker.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f2fbad1876816921 | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.18.64.197:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.0:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.0:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.3:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
— | — | GET | 200 | 104.21.85.204:443 | https://i.postimg.cc/7P96ygVv/Betsy-Sigma-Boy-Official-Music-Video-You-Tube-Google-Chrome-2025-05-22-17.png | unknown | — | — | unknown |
— | — | POST | 200 | 4.231.66.184:443 | https://checkappexec.microsoft.com/windows/shell/actions | unknown | binary | 182 b | whitelisted |
— | — | GET | 200 | 23.212.222.21:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | binary | 55 b | whitelisted |
— | — | HEAD | 200 | 23.212.222.21:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | unknown |
2768 | svchost.exe | GET | 200 | 208.89.74.31:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?6e74c5411d5b84cd | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.18.64.197:80 | — | Administracion Nacional de Telecomunicaciones | UY | unknown |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5812 | MoUsoCoreWorker.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
3640 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1924 | smartscreen.exe | 51.137.3.145:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
784 | powershell.exe | 162.249.168.129:443 | i.postimg.cc | PUREVOLTAGE-INC | US | whitelisted |
1084 | svchost.exe | 23.212.222.21:443 | fs.microsoft.com | AKAMAI-AS | AU | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2768 | svchost.exe | 208.89.74.31:80 | ctldl.windowsupdate.com | — | US | whitelisted |
2988 | OfficeClickToRun.exe | 20.189.173.1:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
login.live.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
i.postimg.cc |
| whitelisted |
dns.msftncsi.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
— | — | A Network Trojan was detected | ET HUNTING Suspicious POST With Reference to WINDOWS Folder Possible Malware Infection |
1664 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |