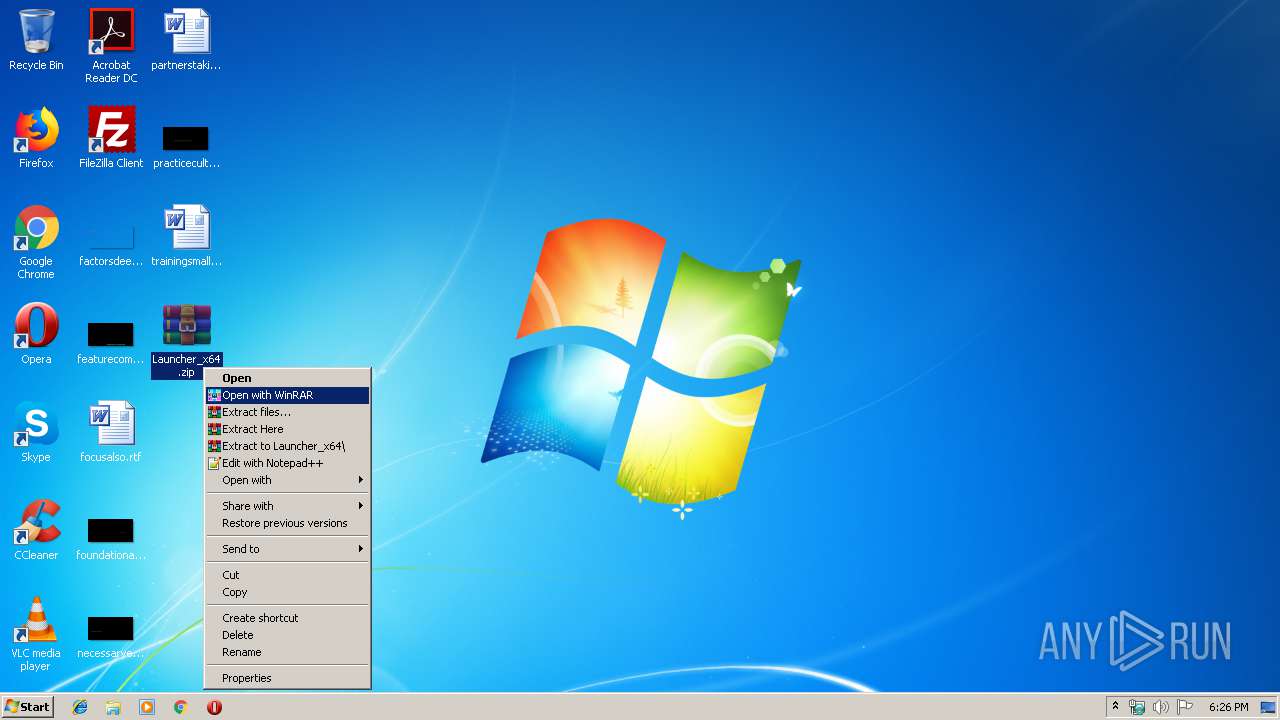
| download: | Launcher_x64.zip |
| Full analysis: | https://app.any.run/tasks/b8651c6f-afa5-485d-a1ab-f8672fcb03f0 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2020, 18:25:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | C63DB239AC50A871475EC8F77F5CEC6E |
| SHA1: | 0602A9459A41172AC18EC08F37E9EF5F9E536B91 |
| SHA256: | 0813F9C1C8E128E4DF002A8DECD23EE65A37ED6AAA4A8AA98F2743587F5430A4 |
| SSDEEP: | 98304:vq72XgABrSzxYkvEFKOV/vgvpsQrEEY8mrYZLuaPwzN9WFSfwXaCx87IW:vJXAzxFvrORmsCG8WyLuaPwzLf9L7IW |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3352)
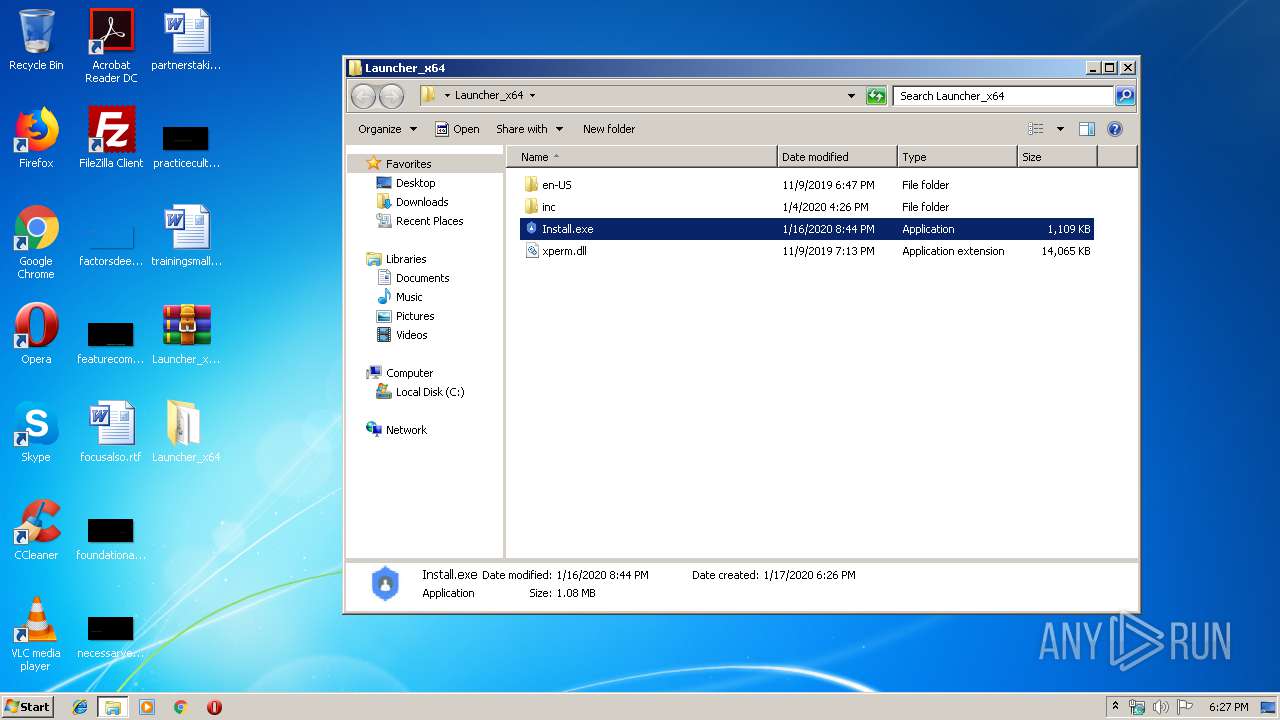
- Install.exe (PID: 3156)
Application was dropped or rewritten from another process
- Install.exe (PID: 3156)
- Install.exe (PID: 1012)
Actions looks like stealing of personal data
- Install.exe (PID: 3156)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2580)
- Install.exe (PID: 3156)
Application launched itself
- Install.exe (PID: 1012)
Creates files in the user directory
- Install.exe (PID: 3156)
Reads the cookies of Google Chrome
- Install.exe (PID: 3156)
Reads the cookies of Mozilla Firefox
- Install.exe (PID: 3156)
Checks for external IP
- Install.exe (PID: 3156)
INFO
Manual execution by user
- Install.exe (PID: 1012)
- WinRAR.exe (PID: 2580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:11:09 21:47:21 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | en-US/ |
Total processes
39
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
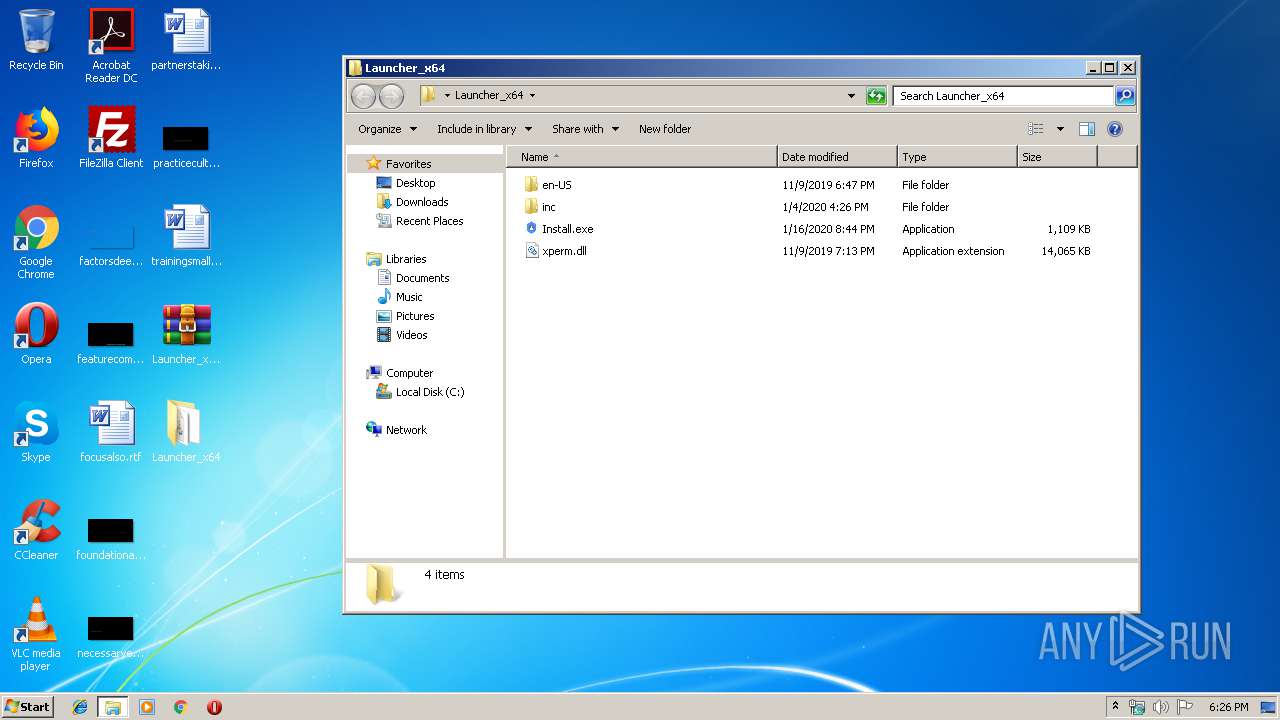
| 1012 | "C:\Users\admin\Desktop\Launcher_x64\Install.exe" | C:\Users\admin\Desktop\Launcher_x64\Install.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2580 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Launcher_x64.zip" C:\Users\admin\Desktop\Launcher_x64\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3156 | "C:\Users\admin\Desktop\Launcher_x64\Install.exe" | C:\Users\admin\Desktop\Launcher_x64\Install.exe | Install.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3352 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3980 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\Launcher_x64.zip.xpi | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
506
Read events
452
Write events
54
Delete events
0
Modification events
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | LangID |
Value: 0904 | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Internet Explorer\iexplore.exe |
Value: Internet Explorer | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (3980) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
Executable files
52
Suspicious files
0
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2580 | WinRAR.exe | C:\Users\admin\Desktop\Launcher_x64\Install.exe | executable | |
MD5:— | SHA256:— | |||
| 3156 | Install.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@mywps[1].txt | text | |
MD5:— | SHA256:— | |||
| 2580 | WinRAR.exe | C:\Users\admin\Desktop\Launcher_x64\inc\bin.dll | executable | |
MD5:— | SHA256:— | |||
| 2580 | WinRAR.exe | C:\Users\admin\Desktop\Launcher_x64\xperm.dll | executable | |
MD5:— | SHA256:— | |||
| 2580 | WinRAR.exe | C:\Users\admin\Desktop\Launcher_x64\en-US\lan-eng.lg | executable | |
MD5:— | SHA256:— | |||
| 3156 | Install.exe | C:\Users\admin\AppData\Local\Temp\9622D276\api-ms-win-core-heap-l1-1-0.dll | executable | |
MD5:2EA3901D7B50BF6071EC8732371B821C | SHA256:44F6DF4280C8ECC9C6E609B1A4BFEE041332D337D84679CFE0D6678CE8F2998A | |||
| 3156 | Install.exe | C:\Users\admin\AppData\Local\Temp\9622D276\api-ms-win-core-interlocked-l1-1-0.dll | executable | |
MD5:D97A1CB141C6806F0101A5ED2673A63D | SHA256:DECCD75FC3FC2BB31338B6FE26DEFFBD7914C6CD6A907E76FD4931B7D141718C | |||
| 3156 | Install.exe | C:\Users\admin\AppData\Local\Temp\9622D276\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:502263C56F931DF8440D7FD2FA7B7C00 | SHA256:94A5DF1227818EDBFD0D5091C6A48F86B4117C38550343F780C604EEE1CD6231 | |||
| 3156 | Install.exe | C:\Users\admin\AppData\Local\Temp\9622D276\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:E479444BDD4AE4577FD32314A68F5D28 | SHA256:C85DC081B1964B77D289AAC43CC64746E7B141D036F248A731601EB98F827719 | |||
| 3156 | Install.exe | C:\Users\admin\AppData\Local\Temp\9622D276\api-ms-win-core-file-l1-1-0.dll | executable | |
MD5:94AE25C7A5497CA0BE6882A00644CA64 | SHA256:7EA06B7050F9EA2BCC12AF34374BDF1173646D4E5EBF66AD690B37F4DF5F3D4E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
2
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3156 | Install.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | text | 264 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3156 | Install.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
3156 | Install.exe | 104.18.56.40:443 | fiasyfssa.mywps.me | Cloudflare Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fiasyfssa.mywps.me |
| suspicious |
ip-api.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3156 | Install.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
3156 | Install.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |