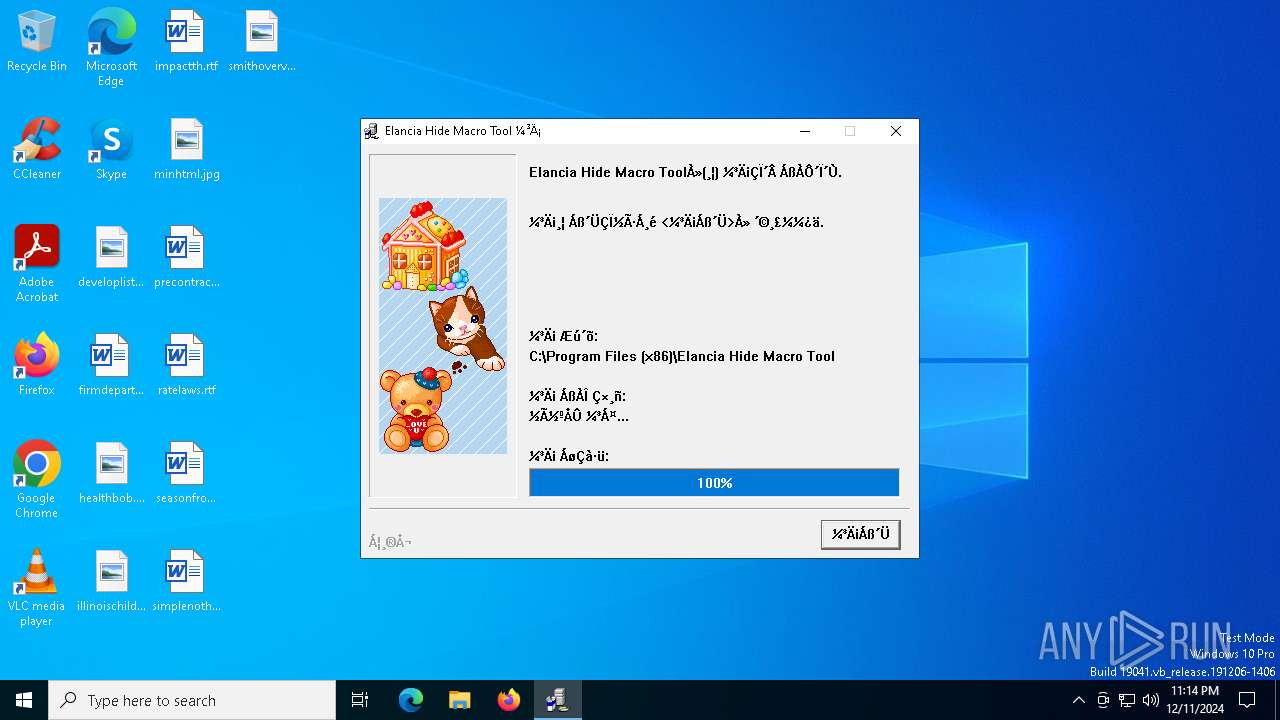
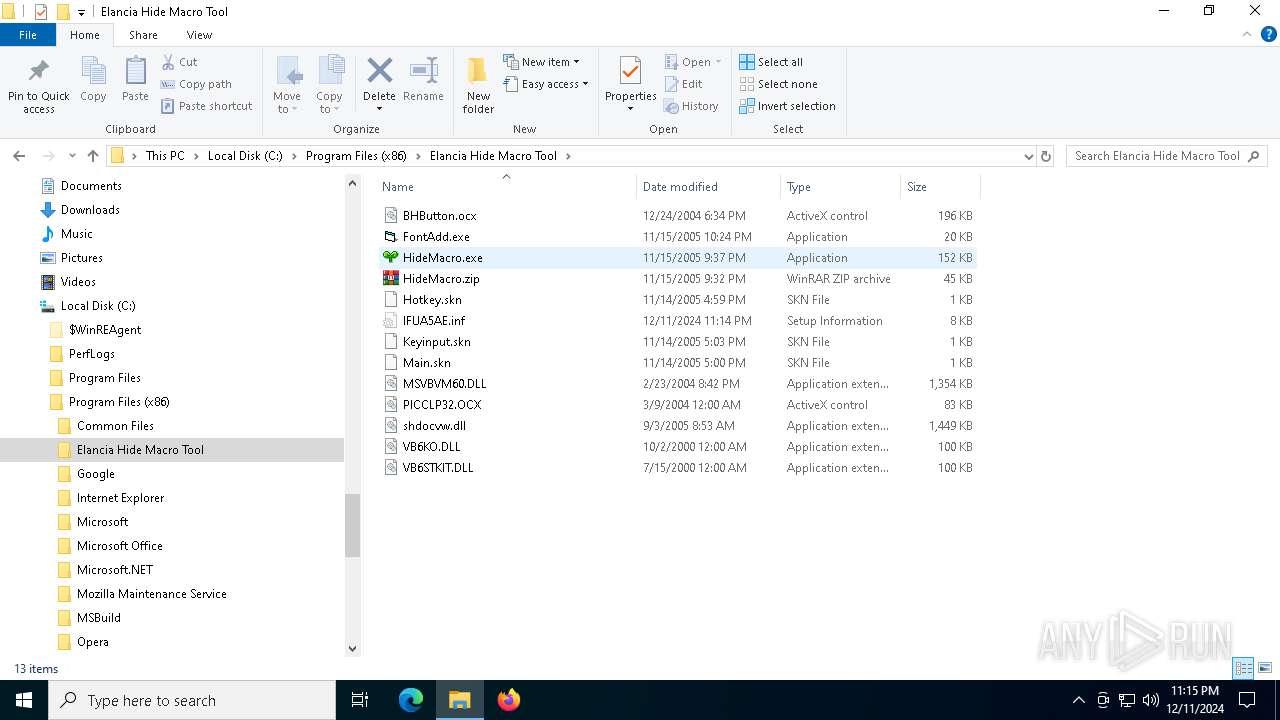
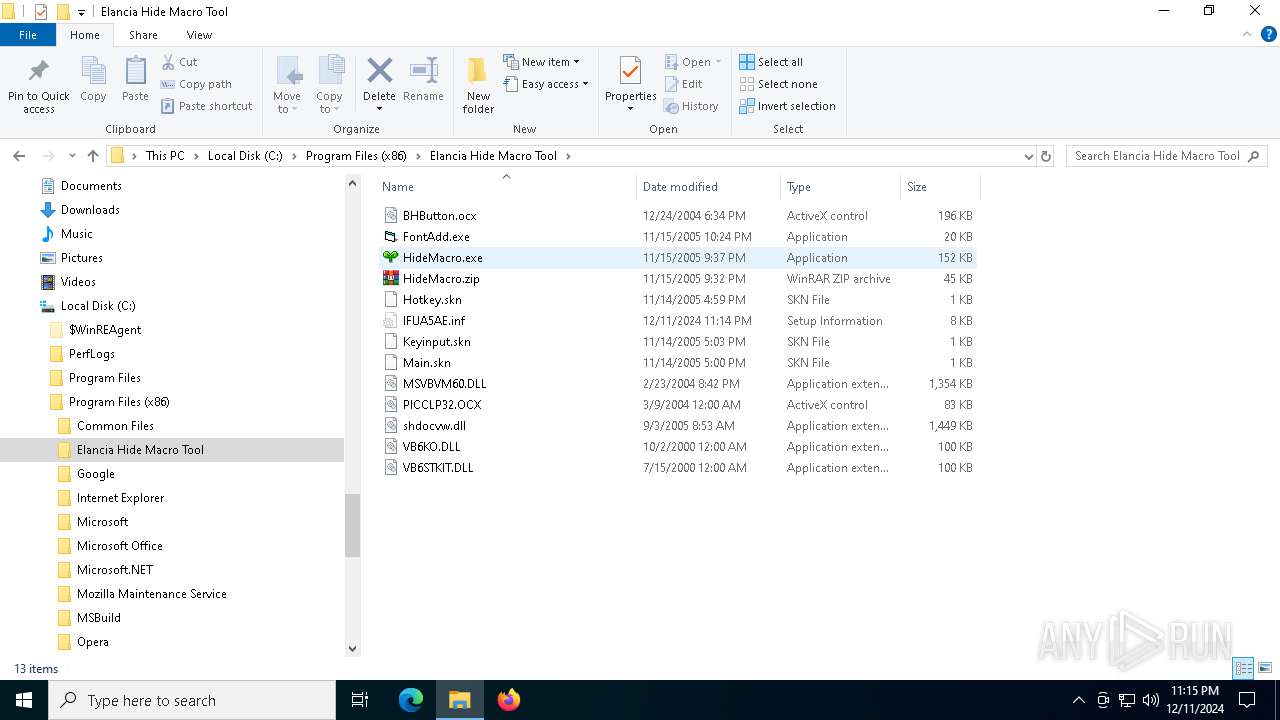
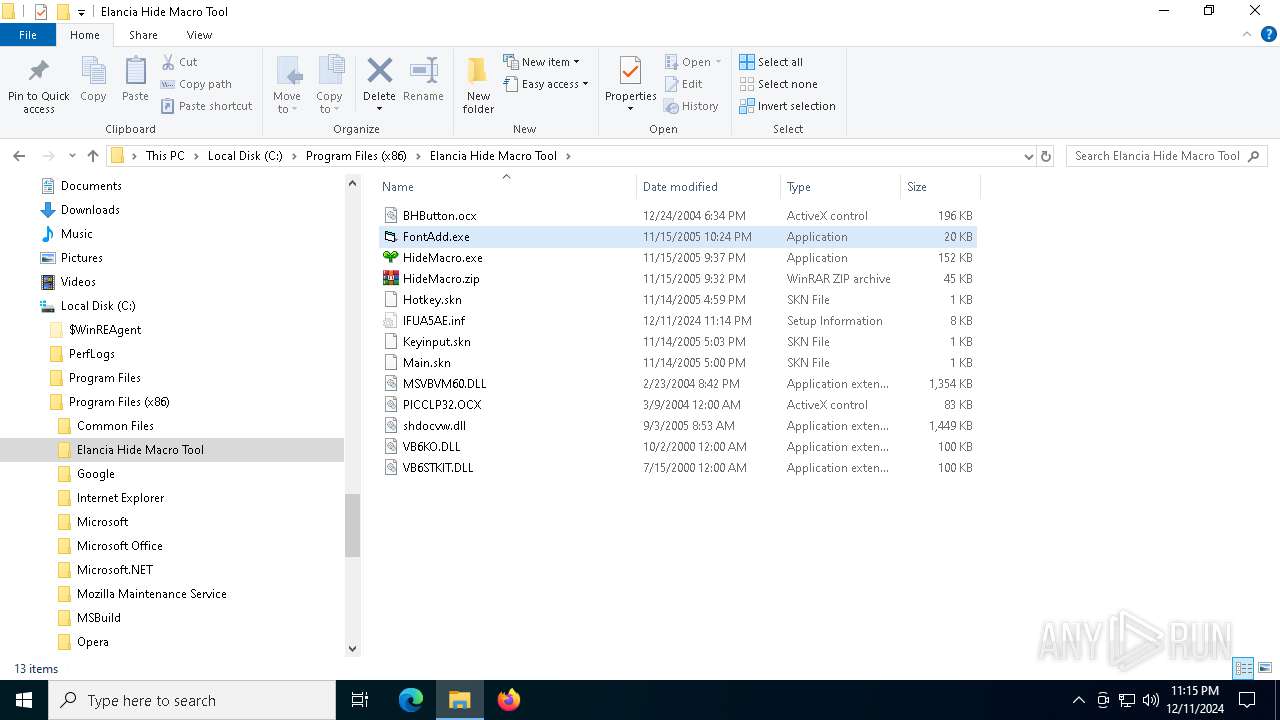
| File name: | Elancia_Hide_Macro_Tool_Install.exe |
| Full analysis: | https://app.any.run/tasks/b31b3c6a-2bd0-41e2-aa31-94beaaf4be9a |
| Verdict: | Malicious activity |
| Analysis date: | December 11, 2024, 23:14:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | F8E31EFA3903F63E2A1C53A2736F529E |
| SHA1: | 6E9D1C1996C5062FFD143168844A57D414933092 |
| SHA256: | 08121FEA32F64A00C8F789EDC01284310AEFFA29A9EA0A940599292E1881A96B |
| SSDEEP: | 98304:9qK6tWkNyECI6oE/TP2WWnF7Uk6v1gqnLC5cT+d9FiecJ+gQ0tg/w7V3VYaBfVLN:0gUK |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts itself from another location
- Elancia_Hide_Macro_Tool_Install.exe (PID: 512)
Executable content was dropped or overwritten
- Elancia_Hide_Macro_Tool_Install.exe (PID: 512)
- IFinst27.exe (PID: 5780)
Process drops legitimate windows executable
- IFinst27.exe (PID: 5780)
Creates a software uninstall entry
- IFinst27.exe (PID: 5780)
Reads security settings of Internet Explorer
- FontAdd.exe (PID: 6920)
- IFinst27.exe (PID: 5780)
- FontAdd.exe (PID: 4444)
- FontAdd.exe (PID: 5032)
Reads Microsoft Outlook installation path
- FontAdd.exe (PID: 6920)
- FontAdd.exe (PID: 4444)
- FontAdd.exe (PID: 5032)
INFO
UPX packer has been detected
- IFinst27.exe (PID: 5780)
Checks supported languages
- Elancia_Hide_Macro_Tool_Install.exe (PID: 512)
- IFinst27.exe (PID: 5780)
- FontAdd.exe (PID: 6920)
- FontAdd.exe (PID: 4444)
- FontAdd.exe (PID: 5032)
Reads the computer name
- IFinst27.exe (PID: 5780)
- FontAdd.exe (PID: 6920)
- FontAdd.exe (PID: 4444)
- FontAdd.exe (PID: 5032)
Create files in a temporary directory
- IFinst27.exe (PID: 5780)
Creates files in the program directory
- IFinst27.exe (PID: 5780)
The sample compiled with english language support
- IFinst27.exe (PID: 5780)
Creates files or folders in the user directory
- IFinst27.exe (PID: 5780)
Checks proxy server information
- FontAdd.exe (PID: 6920)
- FontAdd.exe (PID: 4444)
- FontAdd.exe (PID: 5032)
Manual execution by a user
- FontAdd.exe (PID: 4444)
- FontAdd.exe (PID: 5032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2000:12:06 19:37:33+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 61440 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | 106496 |
| EntryPoint: | 0x29940 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
135
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 512 | "C:\Users\admin\AppData\Local\Temp\Elancia_Hide_Macro_Tool_Install.exe" | C:\Users\admin\AppData\Local\Temp\Elancia_Hide_Macro_Tool_Install.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1448 | "C:\Users\admin\AppData\Local\Temp\Elancia_Hide_Macro_Tool_Install.exe" | C:\Users\admin\AppData\Local\Temp\Elancia_Hide_Macro_Tool_Install.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 4444 | "C:\Program Files (x86)\Elancia Hide Macro Tool\FontAdd.exe" | C:\Program Files (x86)\Elancia Hide Macro Tool\FontAdd.exe | — | explorer.exe | |||||||||||
User: admin Company: 제리클™ Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 5032 | "C:\Program Files (x86)\Elancia Hide Macro Tool\FontAdd.exe" | C:\Program Files (x86)\Elancia Hide Macro Tool\FontAdd.exe | — | explorer.exe | |||||||||||
User: admin Company: 제리클™ Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 5780 | "C:\WINDOWS\IFinst27.exe" -IC:\Users\admin\AppData\Local\Temp\Elancia_Hide_Macro_Tool_Install.exe | C:\Windows\IFinst27.exe | Elancia_Hide_Macro_Tool_Install.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6920 | "C:\Program Files (x86)\Elancia Hide Macro Tool\FontAdd.exe" | C:\Program Files (x86)\Elancia Hide Macro Tool\FontAdd.exe | — | IFinst27.exe | |||||||||||
User: admin Company: 제리클™ Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 7056 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 021
Read events
2 011
Write events
3
Delete events
7
Modification events
| (PID) Process: | (5780) IFinst27.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | Elancia Hide Macro Tool |
Value: | |||
| (PID) Process: | (5780) IFinst27.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Elancia Hide Macro Tool |
| Operation: | write | Name: | DisplayName |
Value: Elancia Hide Macro Tool Uninstall | |||
| (PID) Process: | (5780) IFinst27.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Elancia Hide Macro Tool |
| Operation: | write | Name: | UninstallString |
Value: "C:\WINDOWS\IFinst27.exe" -UC:\Program Files (x86)\Elancia Hide Macro Tool\IFUA5AE.inf | |||
| (PID) Process: | (6920) FontAdd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {BD84B380-8CA2-1069-AB1D-08000948F534} {000214E6-0000-0000-C000-000000000046} 0xFFFF |
Value: 010000000000000030B49B6F224CDB01 | |||
| (PID) Process: | (6920) FontAdd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (6920) FontAdd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (4444) FontAdd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (4444) FontAdd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (5032) FontAdd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (5032) FontAdd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
Executable files
10
Suspicious files
7
Text files
6
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 512 | Elancia_Hide_Macro_Tool_Install.exe | C:\Windows\IFinst27.exe | executable | |
MD5:9C17BCA3EF837BACDED7E4299508E71D | SHA256:2405E5479AEB7D43D1362969B9C439E5931B8F900F9ADFE0FAAA986365415193 | |||
| 5780 | IFinst27.exe | C:\Users\admin\AppData\Local\Temp\_if5E7F.tmp | text | |
MD5:2014F94A4C753B9296834CD05FC579FE | SHA256:56D34F306B416ACA7F2FDCAE2D7D5BD30AE8003B3721748A71CA1E9D20E95102 | |||
| 5780 | IFinst27.exe | C:\Program Files (x86)\Elancia Hide Macro Tool\Keyinput.skn | text | |
MD5:8C53ACF8DC5BC840E0B25E48C6285410 | SHA256:4F5A7C83B6925AFA9EDC86DA17E5FDBAFFCF4ED842FB2C8C1888DCC3CA1F3BF1 | |||
| 5780 | IFinst27.exe | C:\Program Files (x86)\Elancia Hide Macro Tool\PICCLP32.OCX | executable | |
MD5:380D13794FF7642B1091BD7F9A05AFD3 | SHA256:A1134BD48B0D243E1F9AD6CCC08F1D56C8793D76F3AE7DD4BF1EB02AF086443C | |||
| 5780 | IFinst27.exe | C:\Windows\Fonts\¿£ÅÍ-°¥ÀÙ9_Beta2.1.ttf | binary | |
MD5:25609C804C5FA8765C8FFB836713447F | SHA256:5D4805D655ADA74AEAA9B925692FA12C7569995191319C0909E1F1F0551E1A32 | |||
| 5780 | IFinst27.exe | C:\Program Files (x86)\Elancia Hide Macro Tool\Main.skn | text | |
MD5:E88E45CE8CE9B2D3BFE22E35777075BE | SHA256:A113BFE07D812460EEB589233811BC079141FF92CA0820F752DC571B5090BC35 | |||
| 5780 | IFinst27.exe | C:\Windows\Fonts\¿£ÅÍ-Ç®ÀÙ9.ttf | binary | |
MD5:380FDDB5F42B2807A5078DDBE7D5AB2E | SHA256:6CA7E4B3F0FCE50DE08EAF9D84FC0CAD3EA8CC8626F94CB47786B33D88CD2CE4 | |||
| 5780 | IFinst27.exe | C:\Windows\Fonts\¿£ÅÍ-¼ÖÀÙ9_beta3.5_20051010.ttf | binary | |
MD5:C36054449816588A3C4BF246A4CB3469 | SHA256:B6A441B5B359AD9C94CAC049E4BC4F1D42D69A3D16736AE6D3BD150C46B57C0B | |||
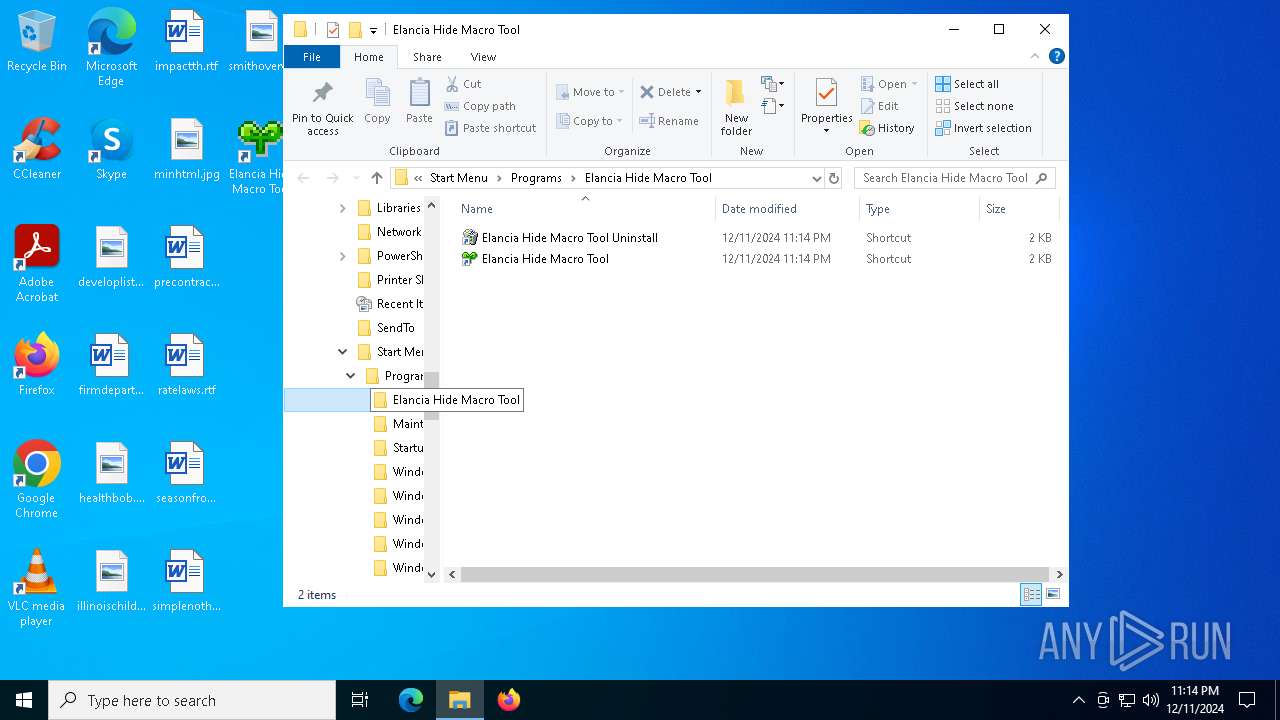
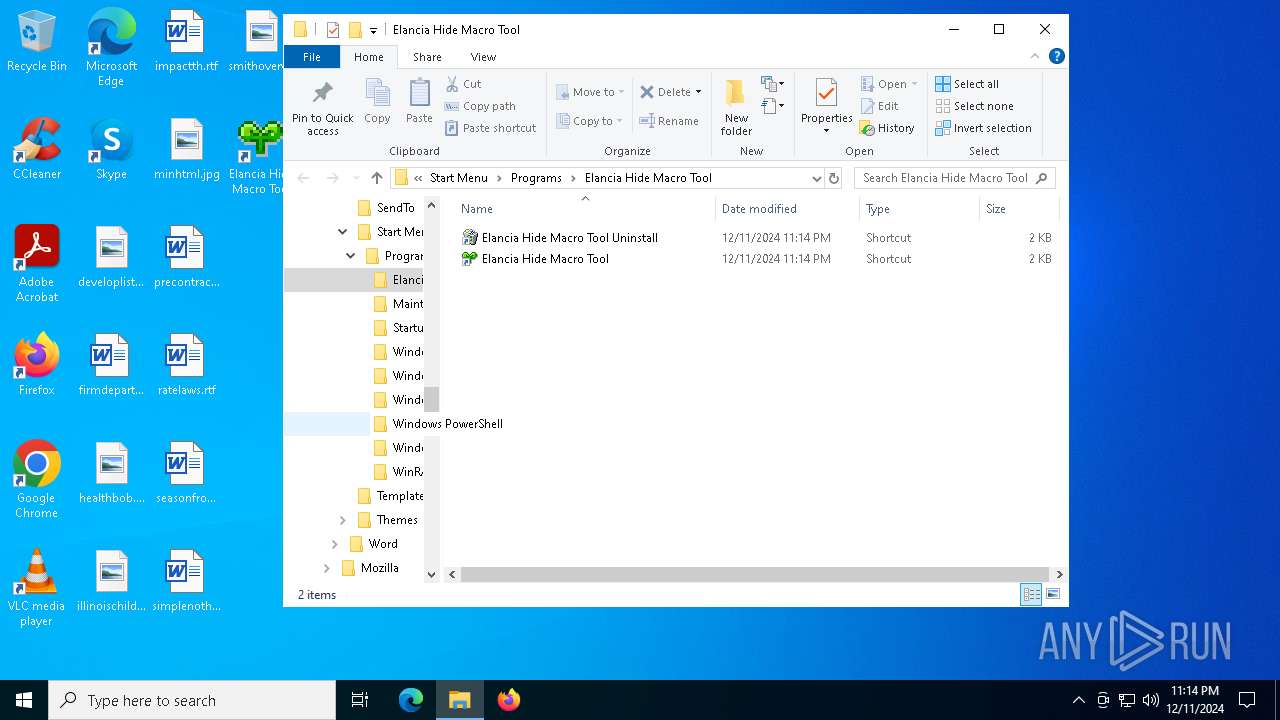
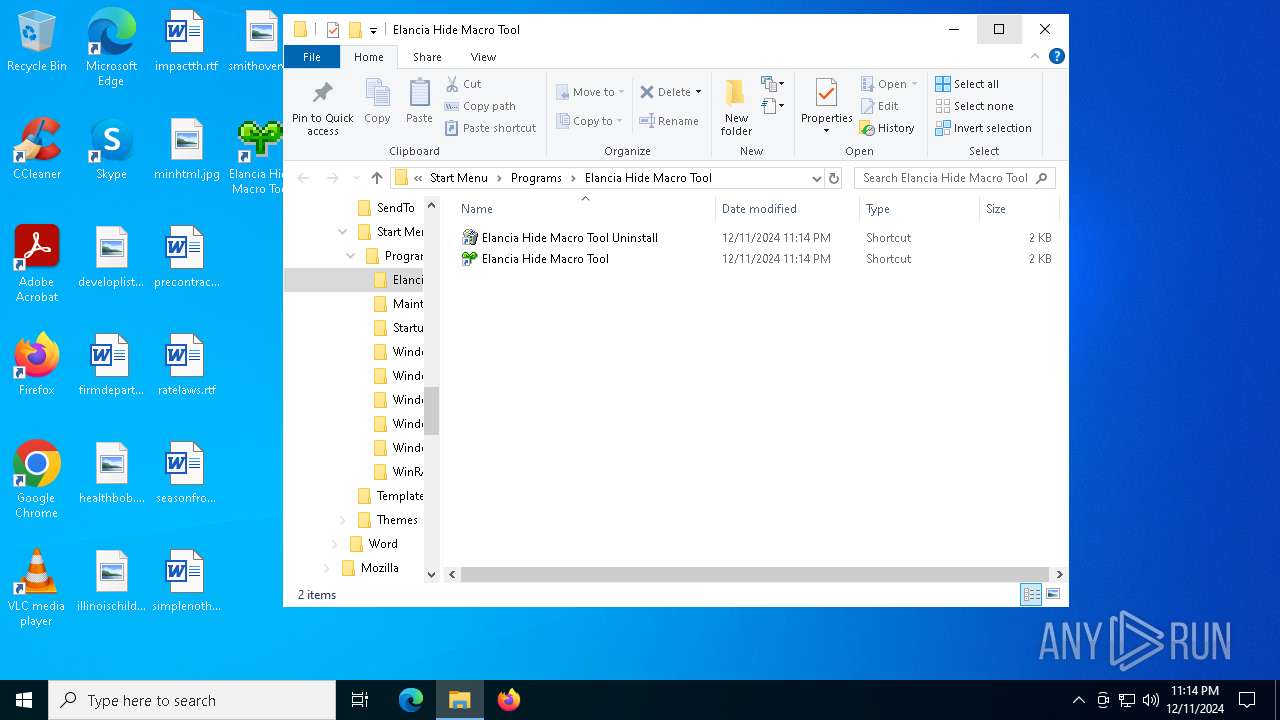
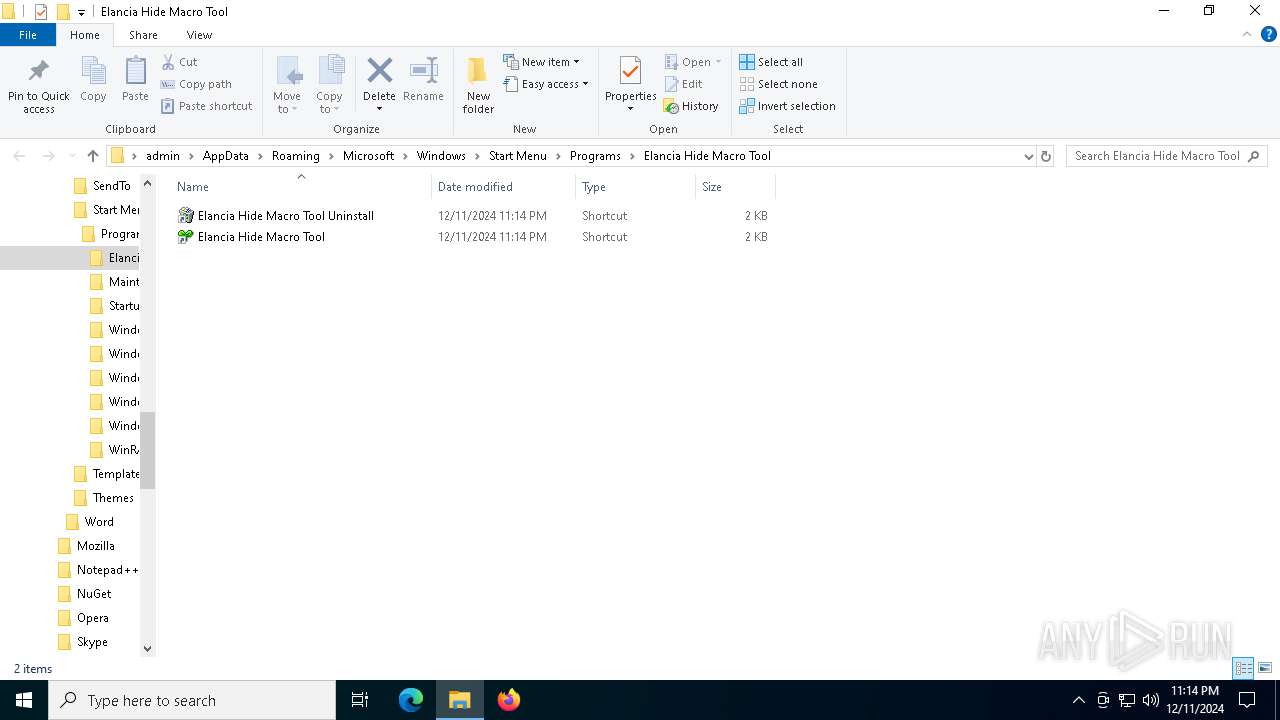
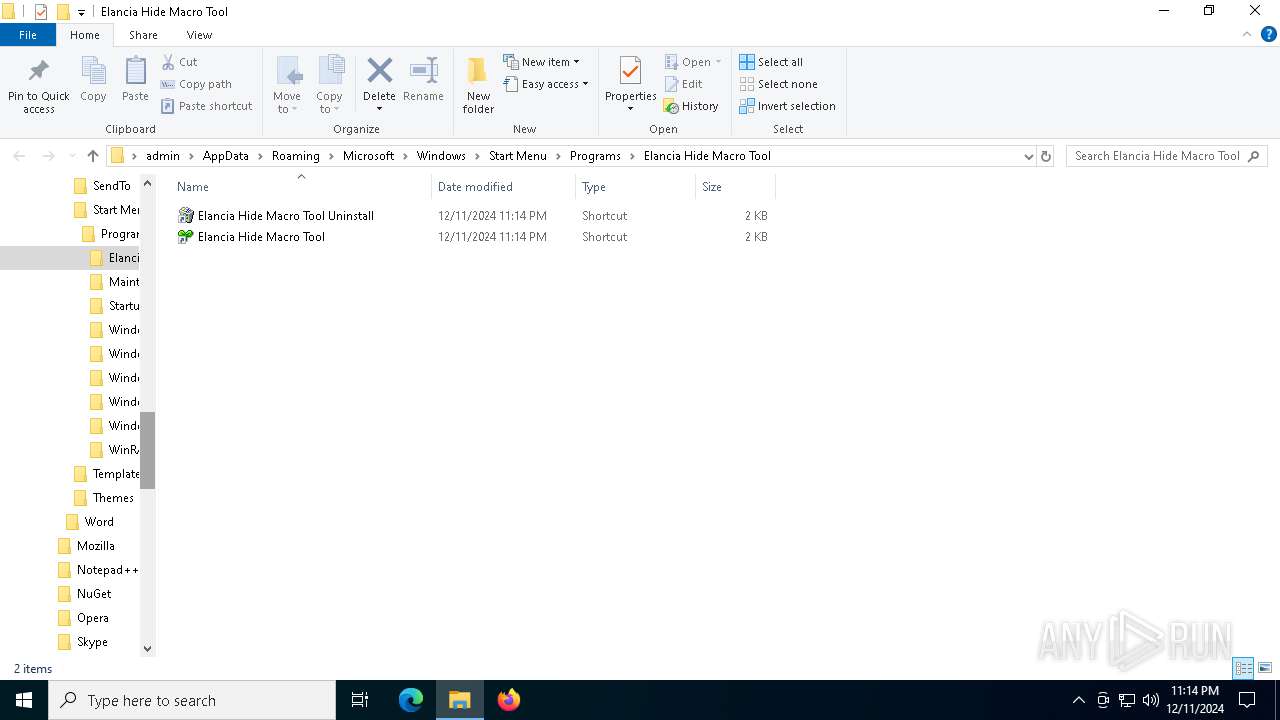
| 5780 | IFinst27.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Elancia Hide Macro Tool\Elancia Hide Macro Tool.LNK | lnk | |
MD5:410E2F5AF2920328511085231C8357C1 | SHA256:C5F42649FAA44B61148776C3A636C04C081F904601C032C2B43AD71497C465D8 | |||
| 5780 | IFinst27.exe | C:\Users\admin\Desktop\Elancia Hide Macro Tool.LNK | binary | |
MD5:BE55A5DB0A54CB5400F35C3F8A6185B2 | SHA256:0E2AA5B1EAF4618FA0AF99BDA8A830A0C6688C3F120D4E192A4EACA424AA60FC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
34
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
188 | svchost.exe | GET | 200 | 23.53.40.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
188 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5616 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5616 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6540 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.139:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
188 | svchost.exe | 23.53.40.139:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
188 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
188 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |