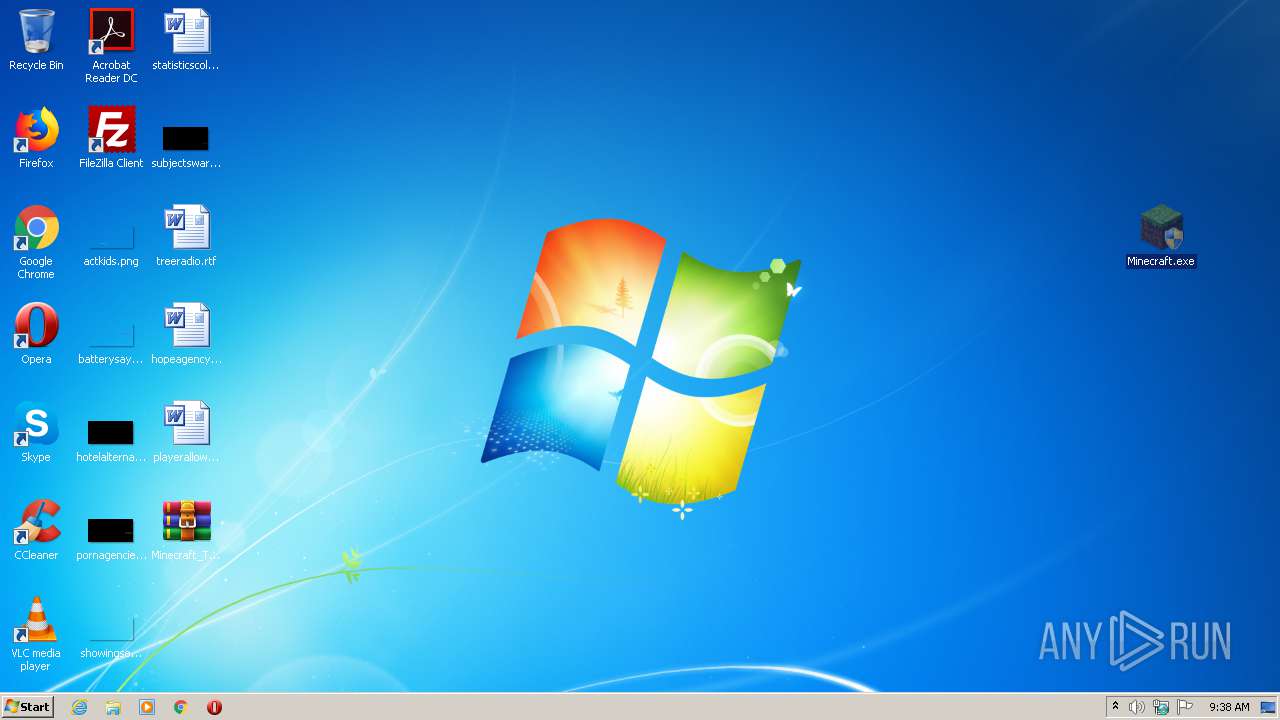
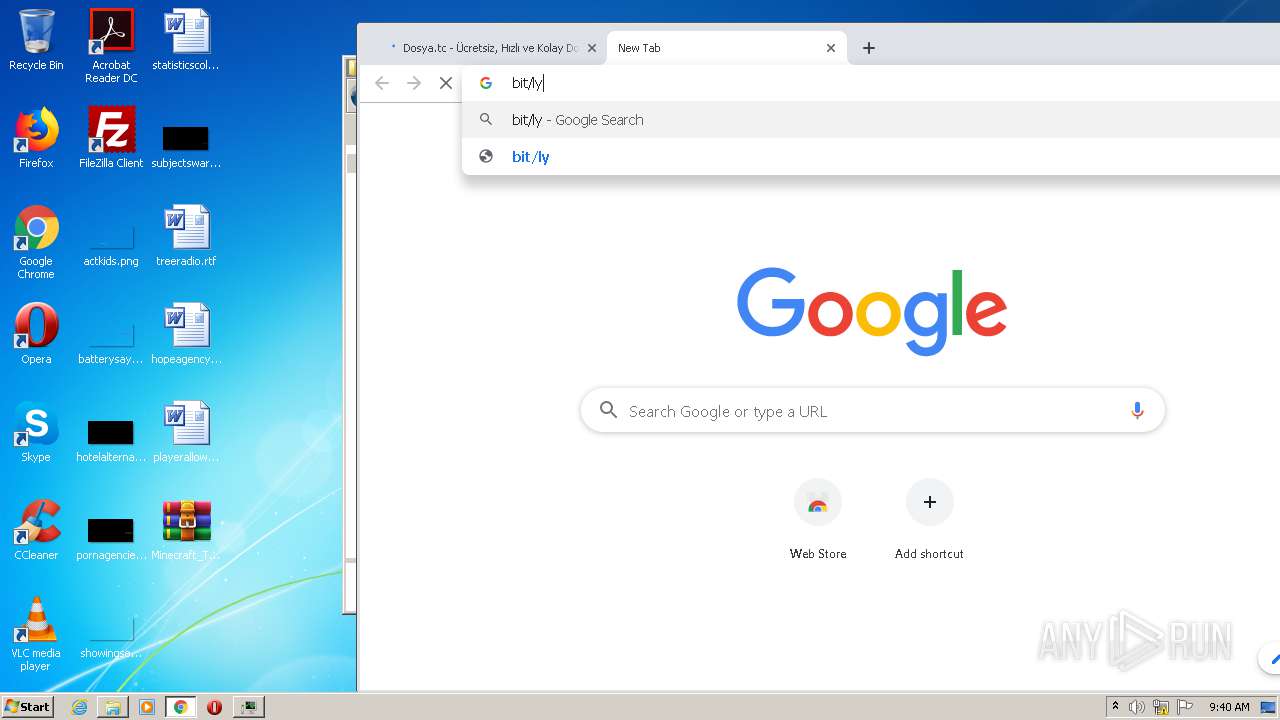
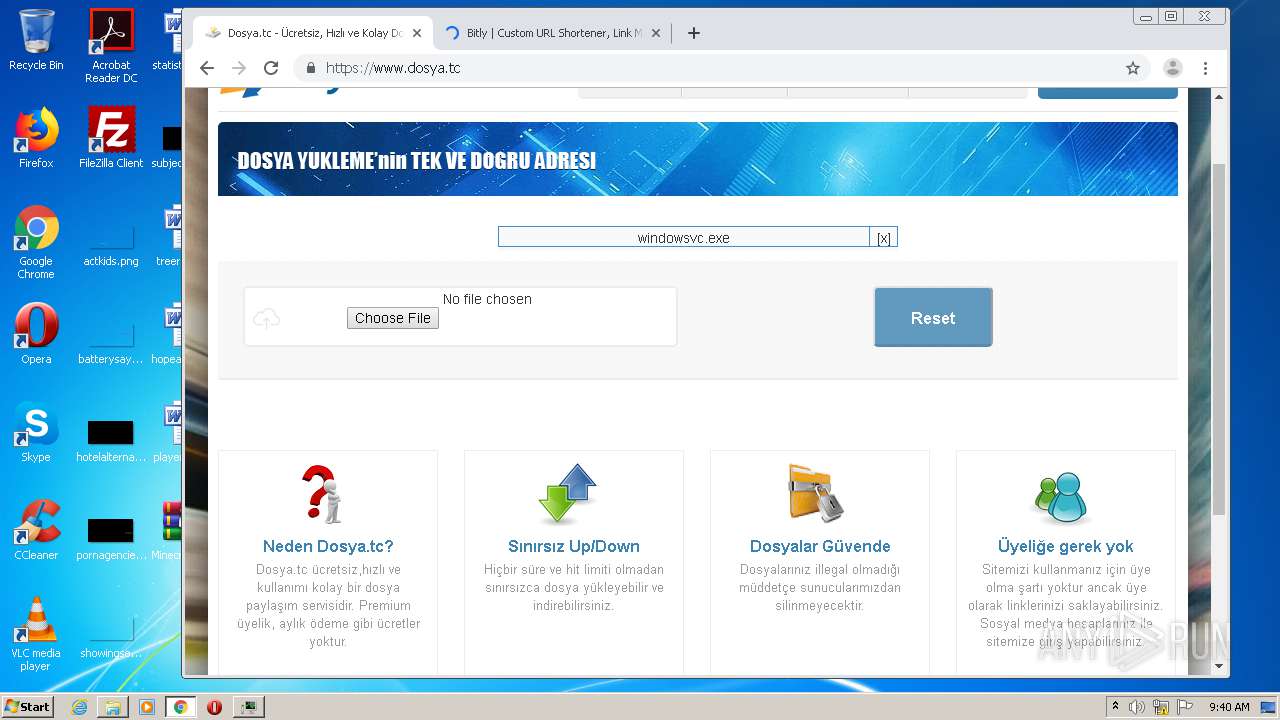
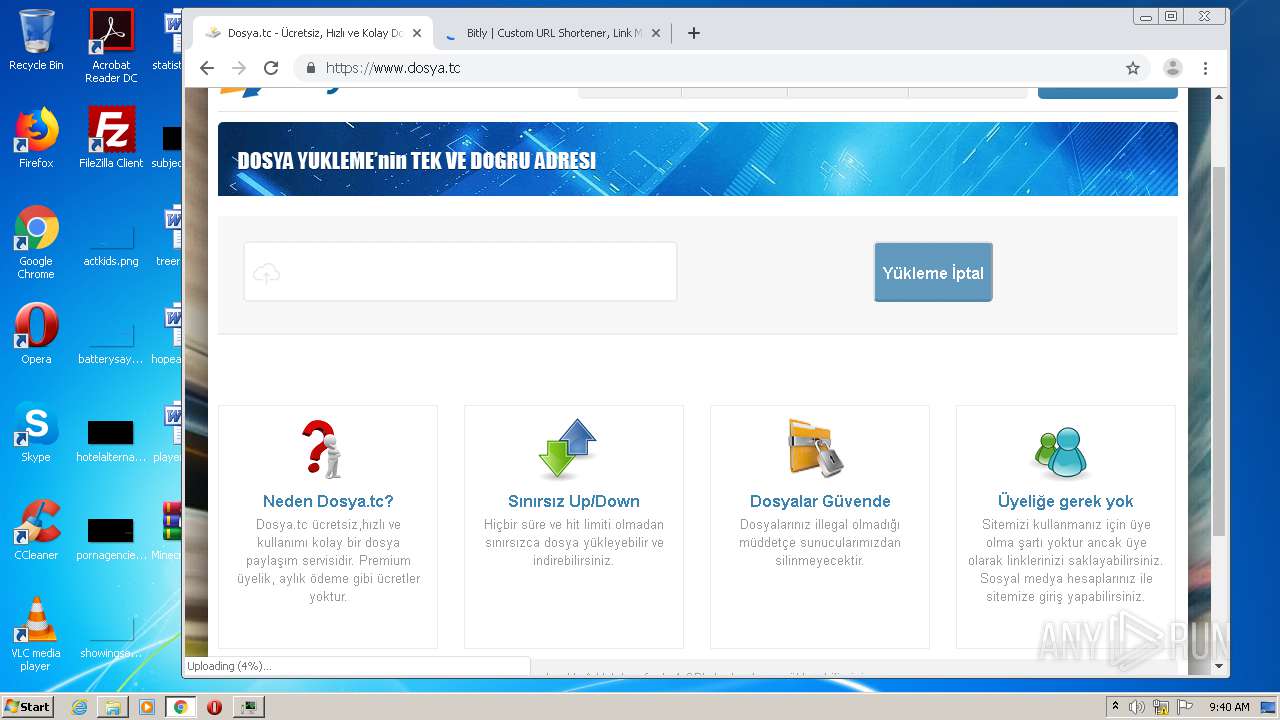
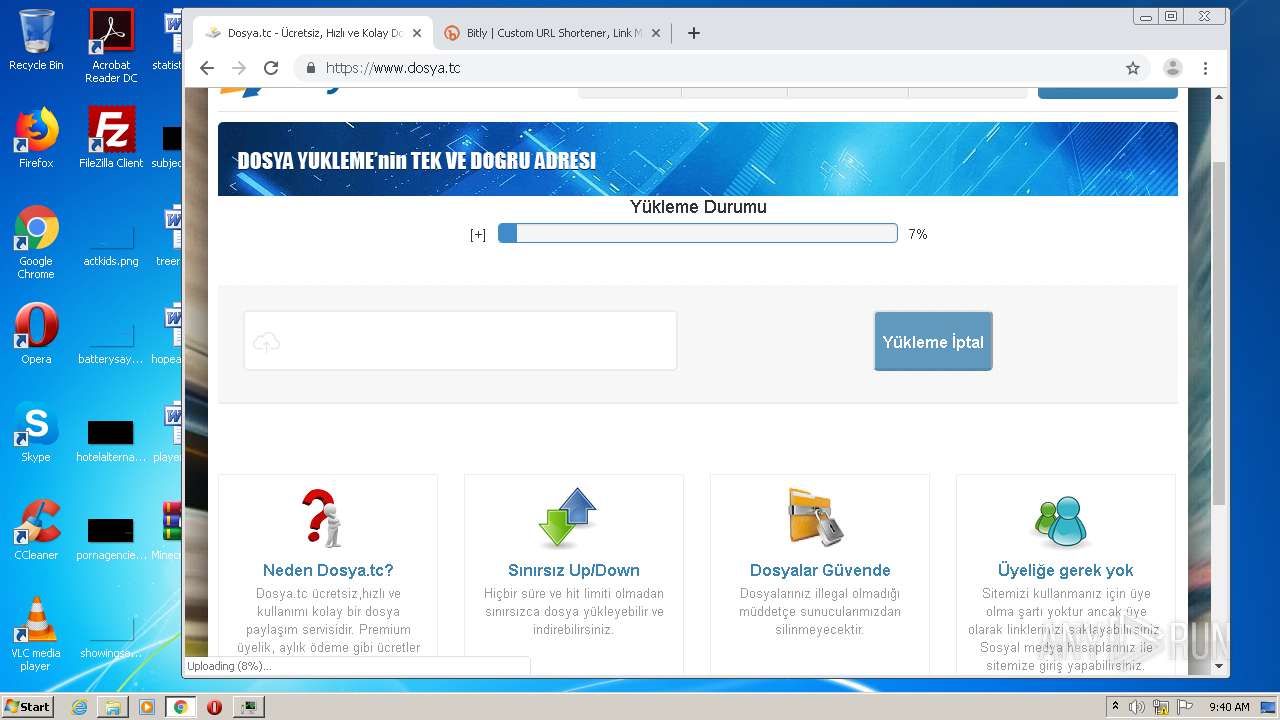
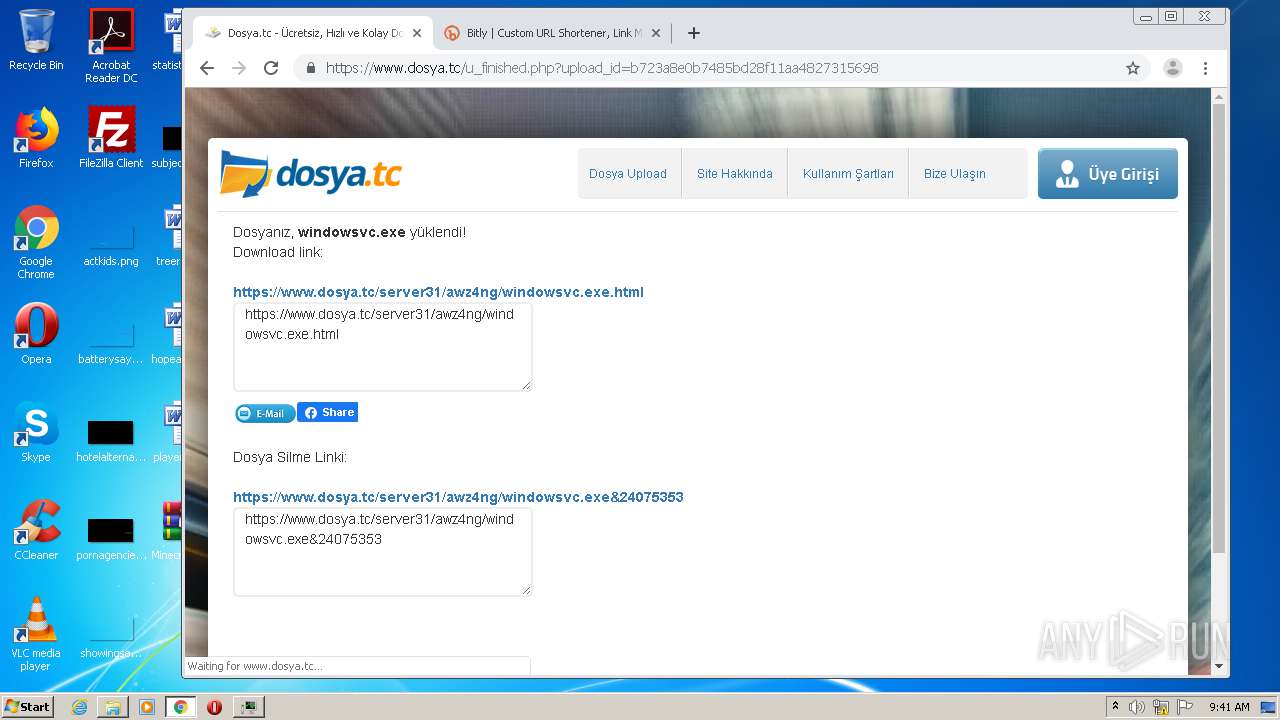
| File name: | Minecraft_TeamExtreme_1.12.2.rar |
| Full analysis: | https://app.any.run/tasks/18fa7a4c-0555-49fa-aa13-edeec1c9f471 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 08:38:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 41F7B389B6546F743E7C20CC6620DD1E |
| SHA1: | 3C47C73FDA7F895C47F0AA8203B00E13BB6B75AB |
| SHA256: | 0803CCE1CC4C7DB24E30C546116FAC4F7218BCA2EE5FF1141EAC81290C3906EA |
| SSDEEP: | 98304:WY/ANpM/oc5Tf5NNPzWVgqgL/c85olfDoiVh:WYIYAc5Tfb1WVgqM08mFoa |
MALICIOUS
Application was dropped or rewritten from another process
- Minecraft.exe (PID: 2224)
- Minecraft.exe (PID: 2700)
- app.exe (PID: 3860)
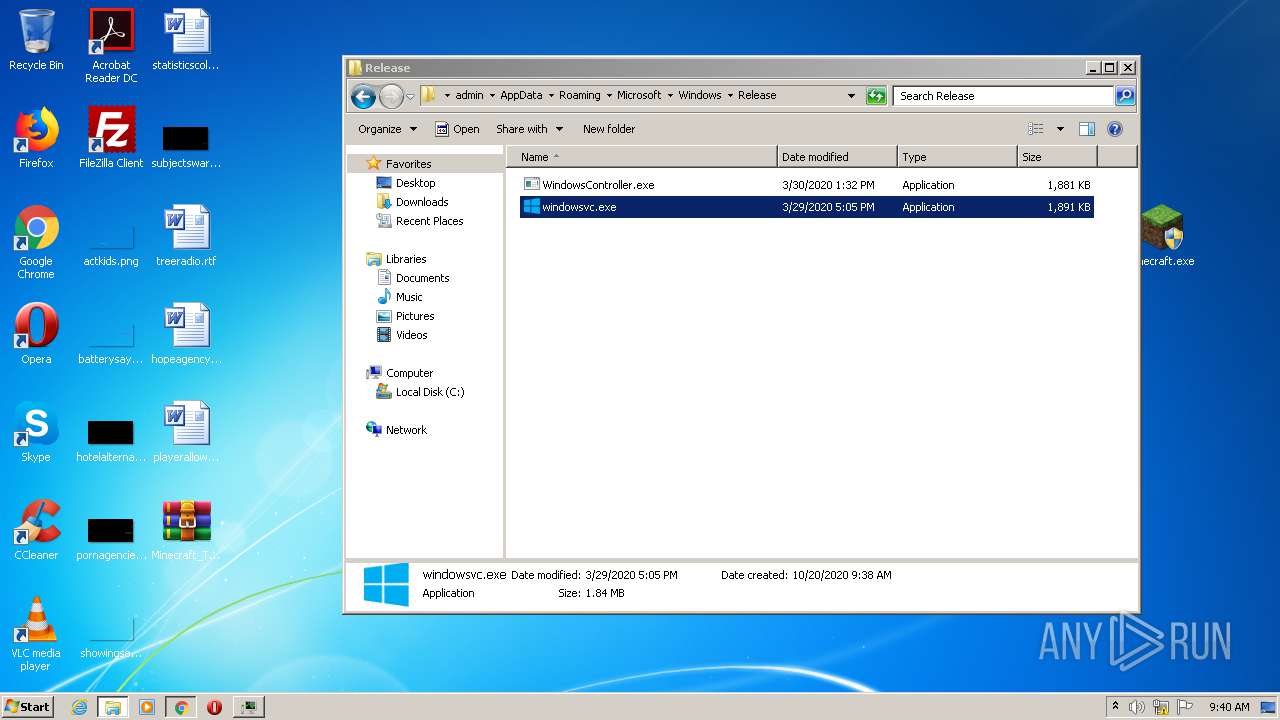
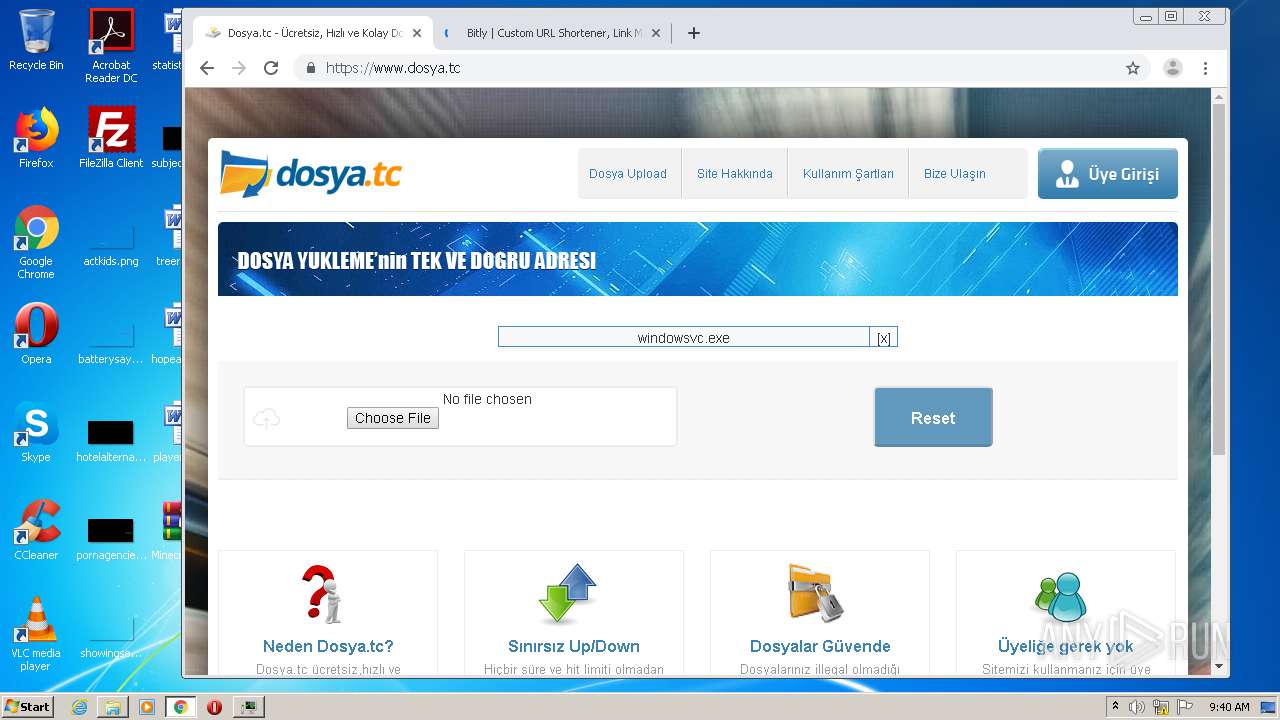
- windowsvc.exe (PID: 4020)
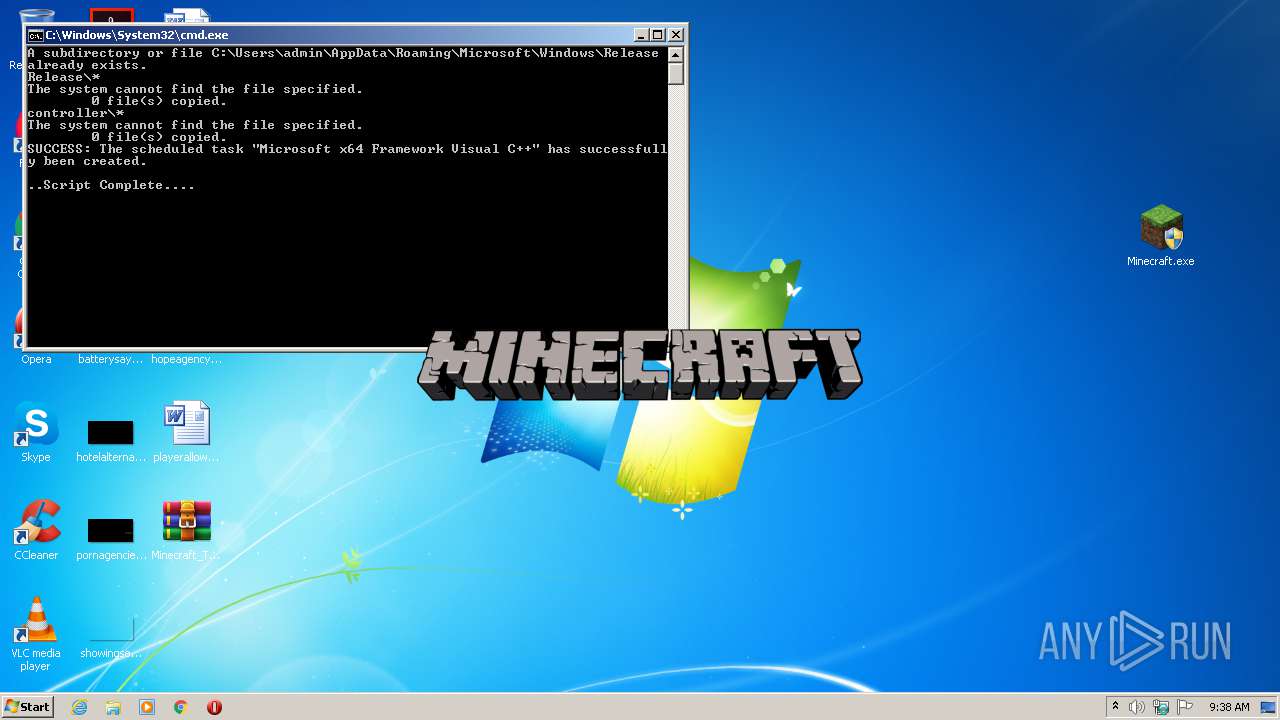
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 3168)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2624)
SUSPICIOUS
Executable content was dropped or overwritten
- Minecraft.exe (PID: 2700)
- WinRAR.exe (PID: 3768)
- cmd.exe (PID: 2244)
- windowsvc.exe (PID: 4020)
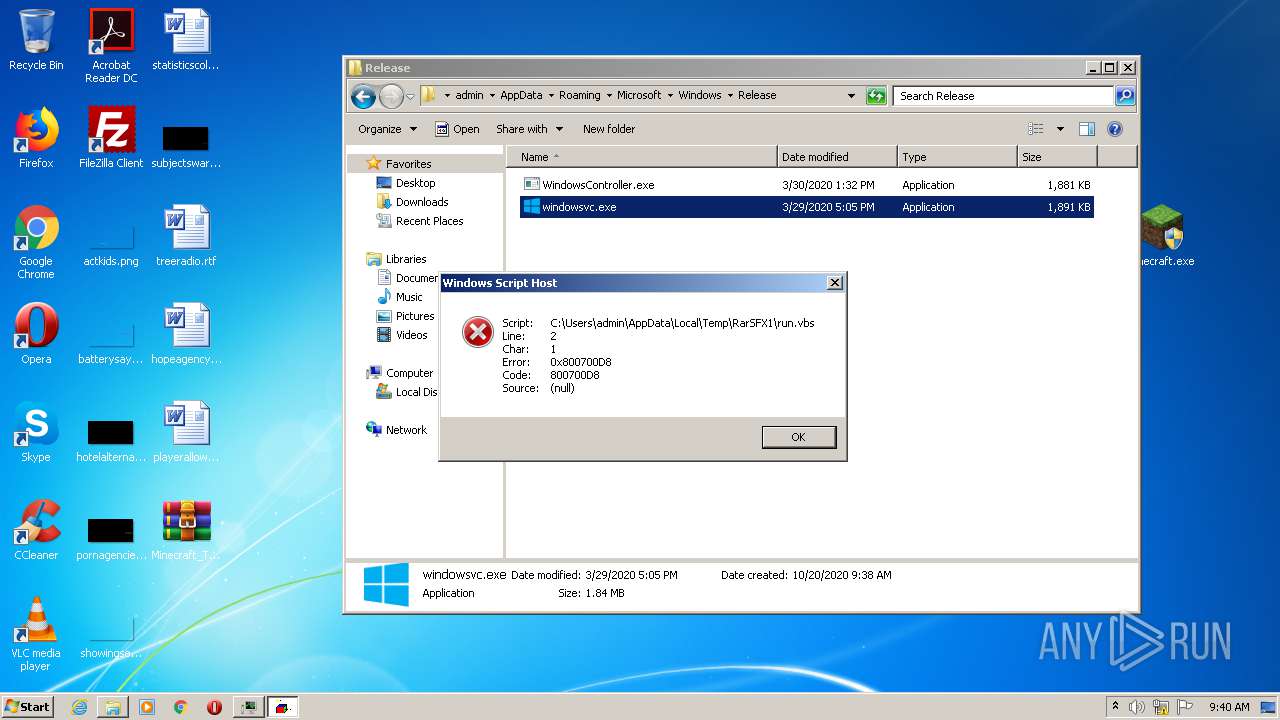
Executes scripts
- Minecraft.exe (PID: 2700)
- cmd.exe (PID: 2244)
- windowsvc.exe (PID: 4020)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 3244)
- WScript.exe (PID: 2292)
Executes JAVA applets
- app.exe (PID: 3860)
Creates files in the user directory
- cmd.exe (PID: 2244)
- javaw.exe (PID: 2328)
INFO
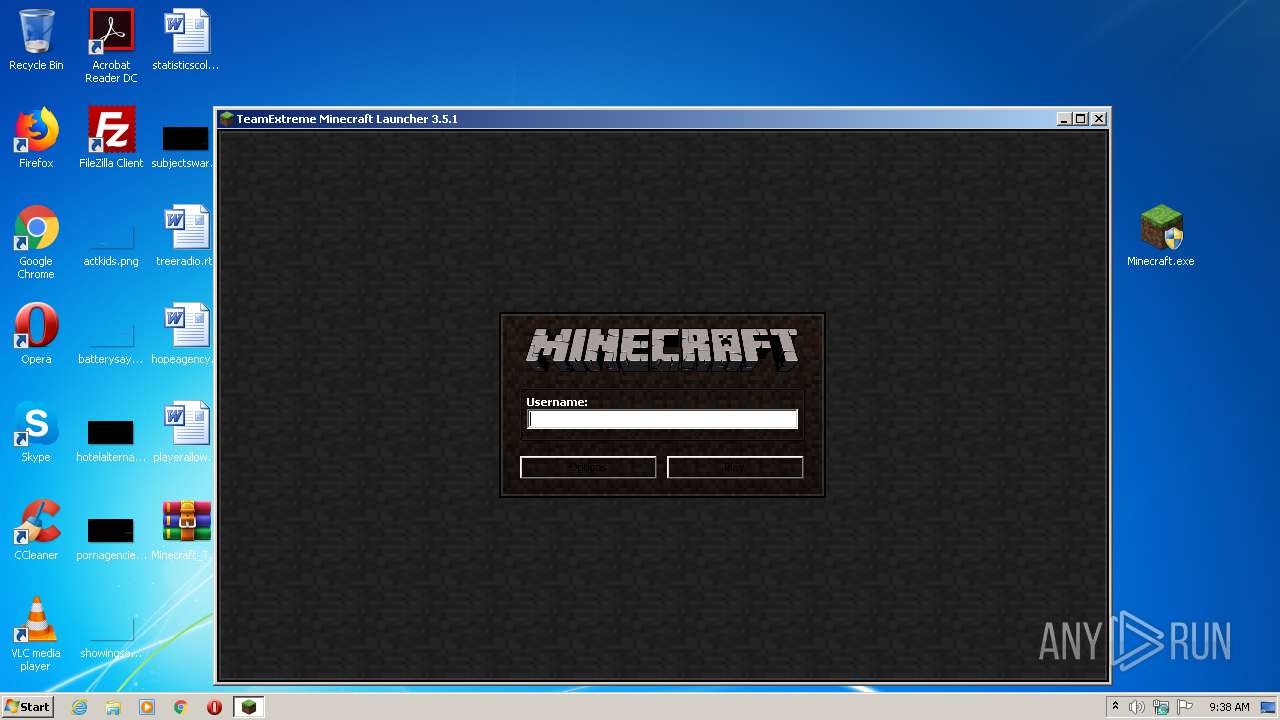
Manual execution by user
- Minecraft.exe (PID: 2700)
- windowsvc.exe (PID: 4020)
- Minecraft.exe (PID: 2224)
- taskmgr.exe (PID: 3572)
- verclsid.exe (PID: 2804)
- chrome.exe (PID: 2564)
Application launched itself
- chrome.exe (PID: 2564)
Reads the hosts file
- chrome.exe (PID: 3592)
- chrome.exe (PID: 2564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
89
Monitored processes
44
Malicious processes
1
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1040,9463131051610690565,8765769049538227716,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10157307115685977415 --mojo-platform-channel-handle=3424 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6e86a9d0,0x6e86a9e0,0x6e86a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1040,9463131051610690565,8765769049538227716,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3950850556048885644 --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3584 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1260 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1040,9463131051610690565,8765769049538227716,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17904567883533876003 --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3828 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1040,9463131051610690565,8765769049538227716,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=15295047919248712897 --mojo-platform-channel-handle=2972 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1040,9463131051610690565,8765769049538227716,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16461595183624760359 --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3684 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2224 | "C:\Users\admin\Desktop\Minecraft.exe" | C:\Users\admin\Desktop\Minecraft.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2244 | cmd /c ""C:\Users\admin\AppData\Local\Temp\RarSFX0\sch.bat" " | C:\Windows\System32\cmd.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2292 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\RarSFX0\run.vbs" | C:\Windows\System32\WScript.exe | — | Minecraft.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2328 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -Xms256m -Xmx512m -jar "C:\Users\admin\AppData\Local\Temp\RarSFX0\app.exe" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | app.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
Total events
3 231
Read events
3 087
Write events
140
Delete events
4
Modification events
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Minecraft_TeamExtreme_1.12.2.rar | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
8
Suspicious files
66
Text files
106
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2328 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio1105602099691704918.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio6711793204984012761.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio2840065571031111589.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio4507240911262294794.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio239763250966024734.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio864298219010677600.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio6088074444757520115.tmp | — | |
MD5:— | SHA256:— | |||
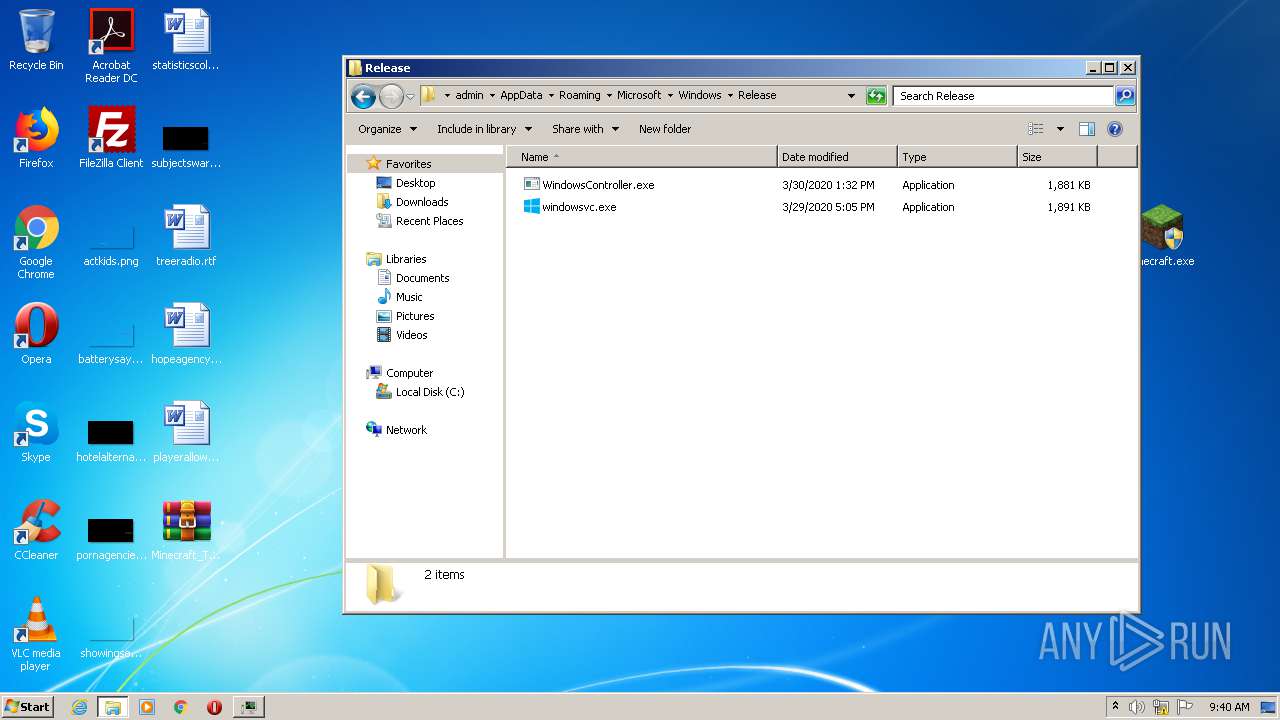
| 2700 | Minecraft.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Release\windowsvc.exe | executable | |
MD5:— | SHA256:— | |||
| 2244 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | text | |
MD5:— | SHA256:— | |||
| 2700 | Minecraft.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\run.vbs | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
74
DNS requests
43
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
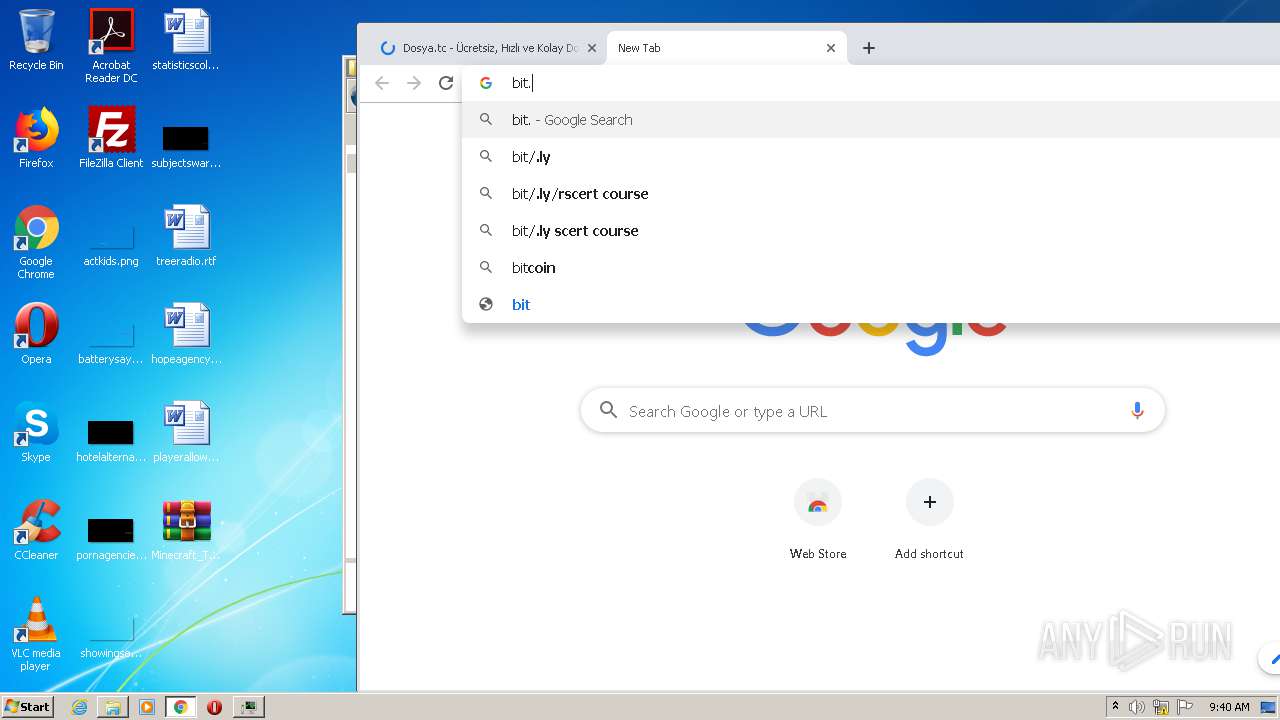
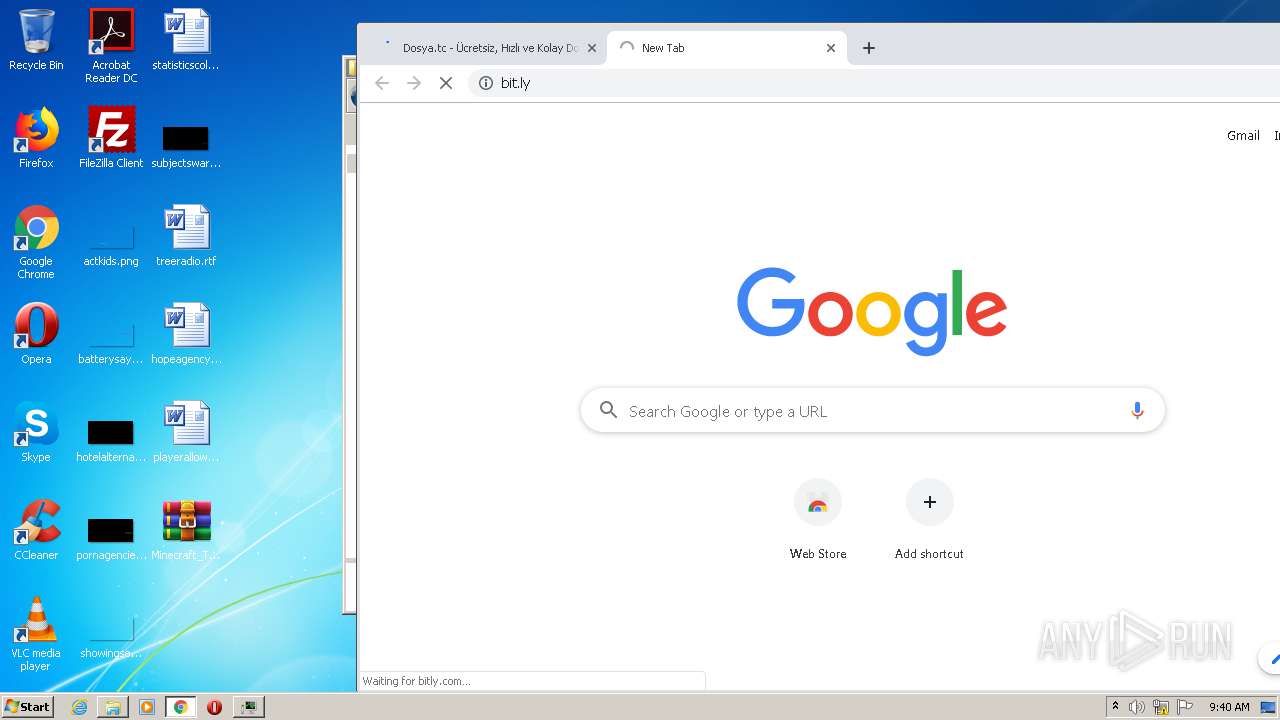
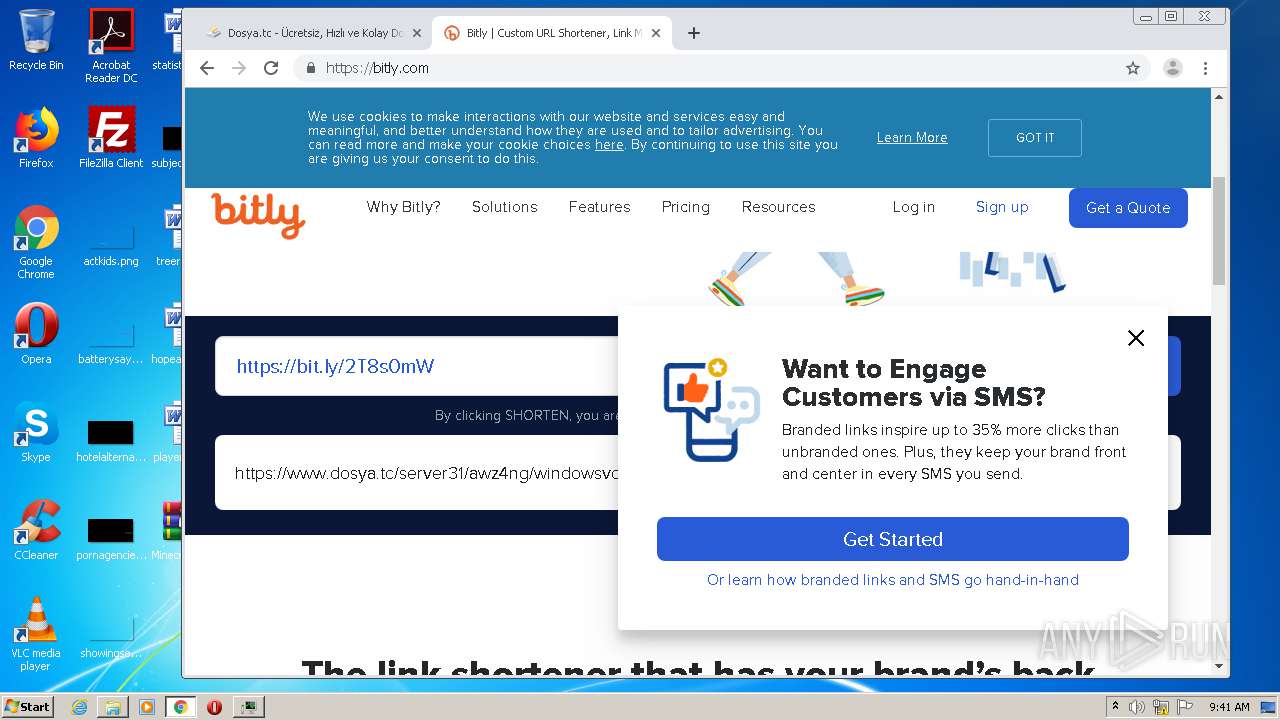
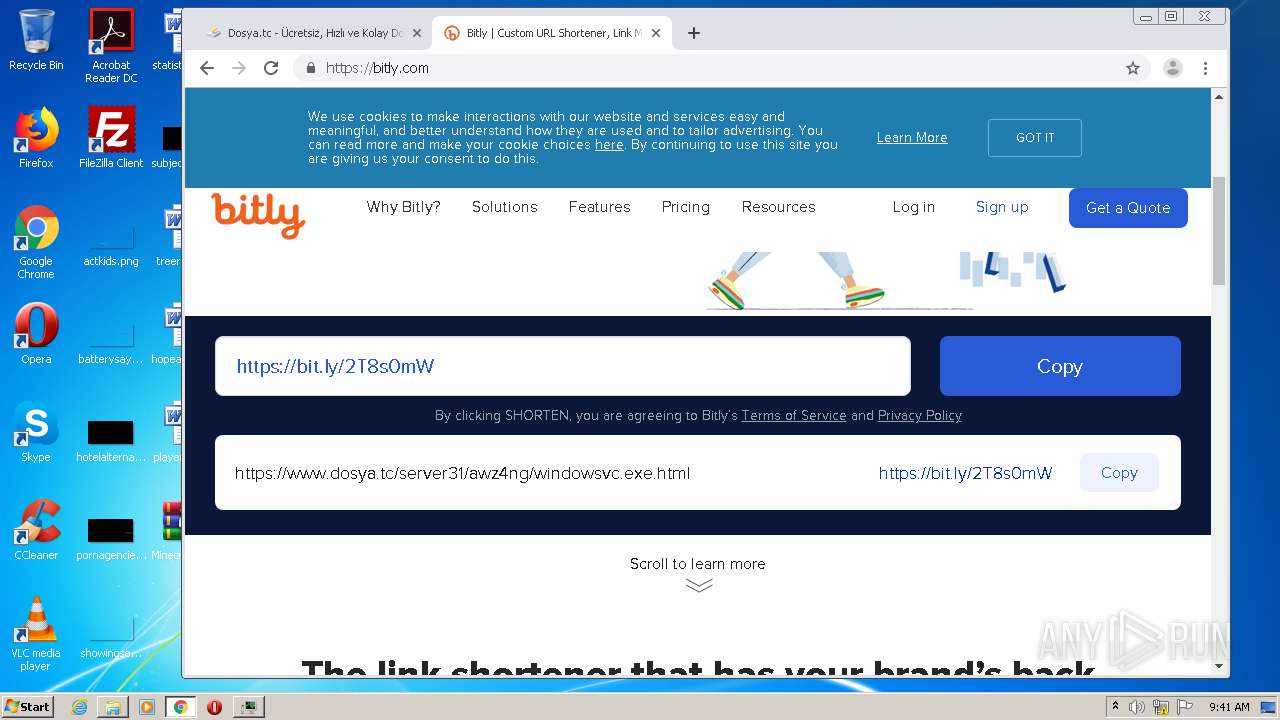
3592 | chrome.exe | GET | 302 | 67.199.248.11:80 | http://bit.ly/ | US | html | 154 b | shared |
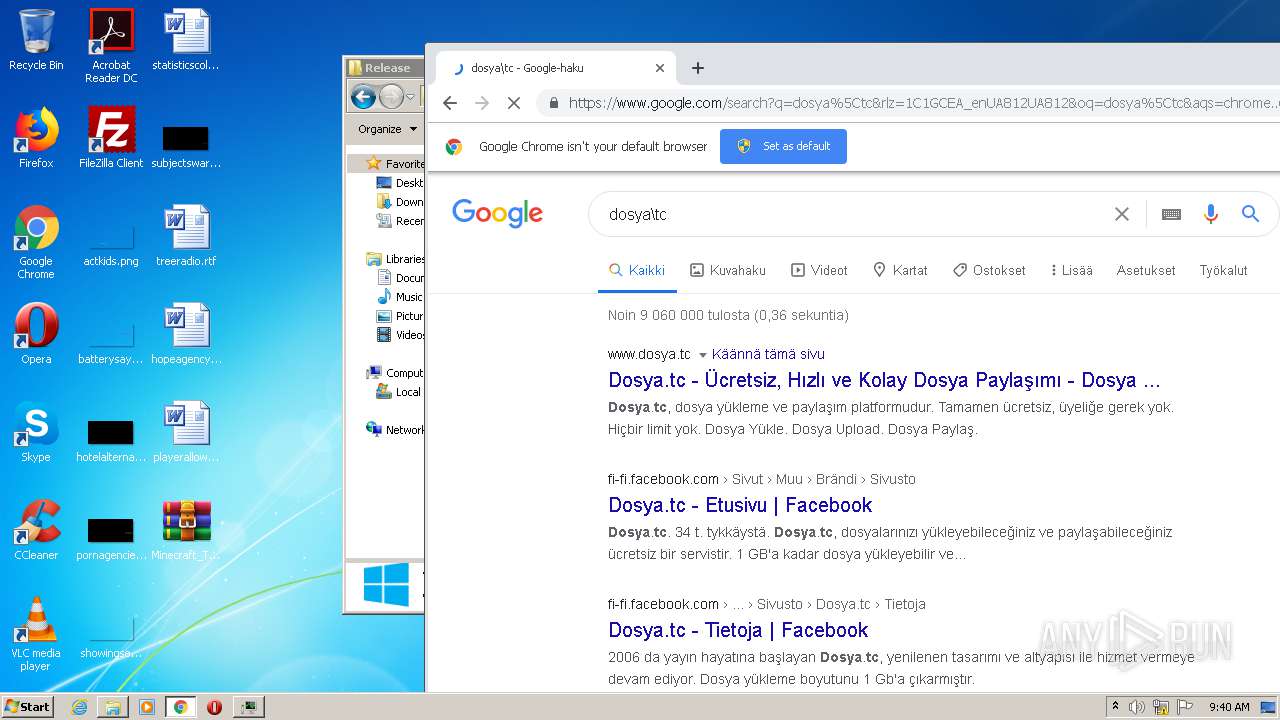
2328 | javaw.exe | GET | 200 | 198.54.115.64:80 | http://teamextrememc.com/failsafe/url.txt | US | text | 36 b | malicious |
2328 | javaw.exe | GET | 404 | 198.54.115.64:80 | http://teamextrememc.com/failsafe/launcherversion.txt | US | html | 315 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2328 | javaw.exe | 162.125.66.15:443 | dl.dropboxusercontent.com | Dropbox, Inc. | DE | malicious |
2328 | javaw.exe | 198.54.115.64:80 | teamextrememc.com | Namecheap, Inc. | US | malicious |
2328 | javaw.exe | 52.216.176.45:443 | s3.amazonaws.com | Amazon.com, Inc. | US | unknown |
3592 | chrome.exe | 216.58.212.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
3592 | chrome.exe | 216.58.206.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3592 | chrome.exe | 172.217.22.110:443 | apis.google.com | Google Inc. | US | whitelisted |
3592 | chrome.exe | 172.217.22.14:443 | clients2.google.com | Google Inc. | US | whitelisted |
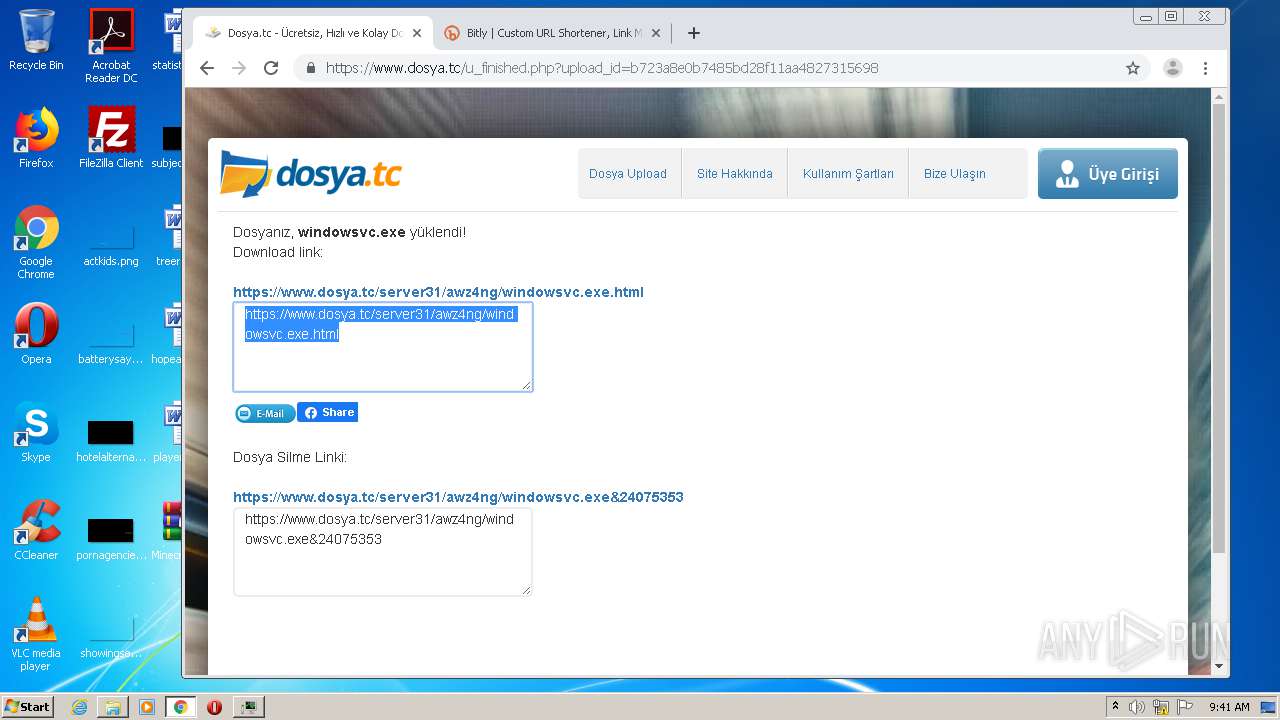
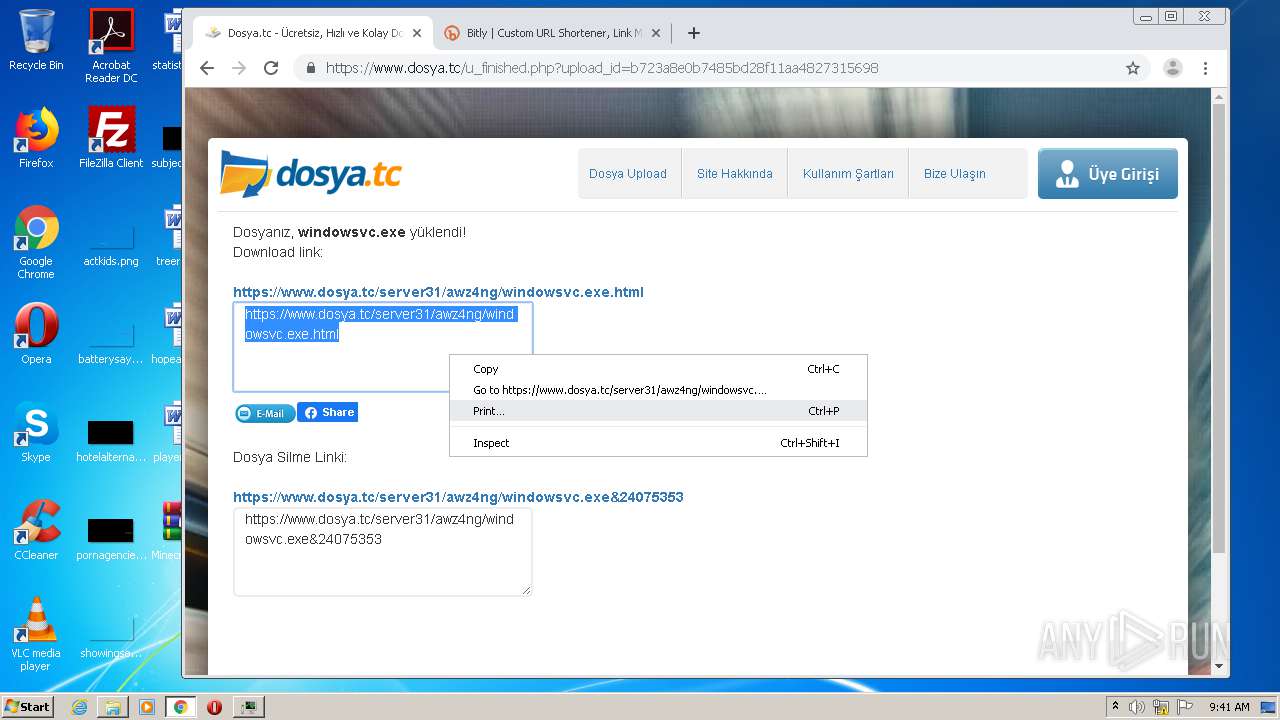
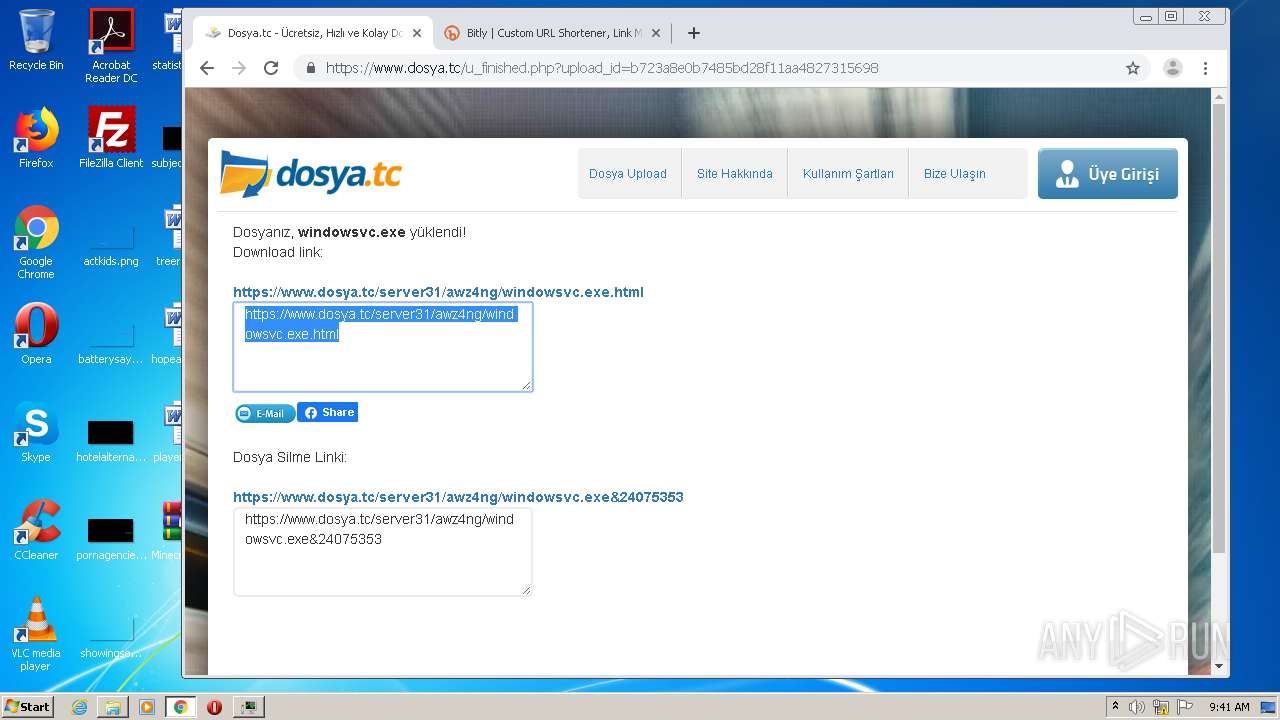
3592 | chrome.exe | 136.243.28.94:443 | www.dosya.tc | Hetzner Online GmbH | DE | suspicious |
3592 | chrome.exe | 172.217.22.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3592 | chrome.exe | 172.217.22.54:443 | i.ytimg.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dl.dropboxusercontent.com |
| shared |
teamextrememc.com |
| malicious |
dl.dropbox.com |
| shared |
s3.amazonaws.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |