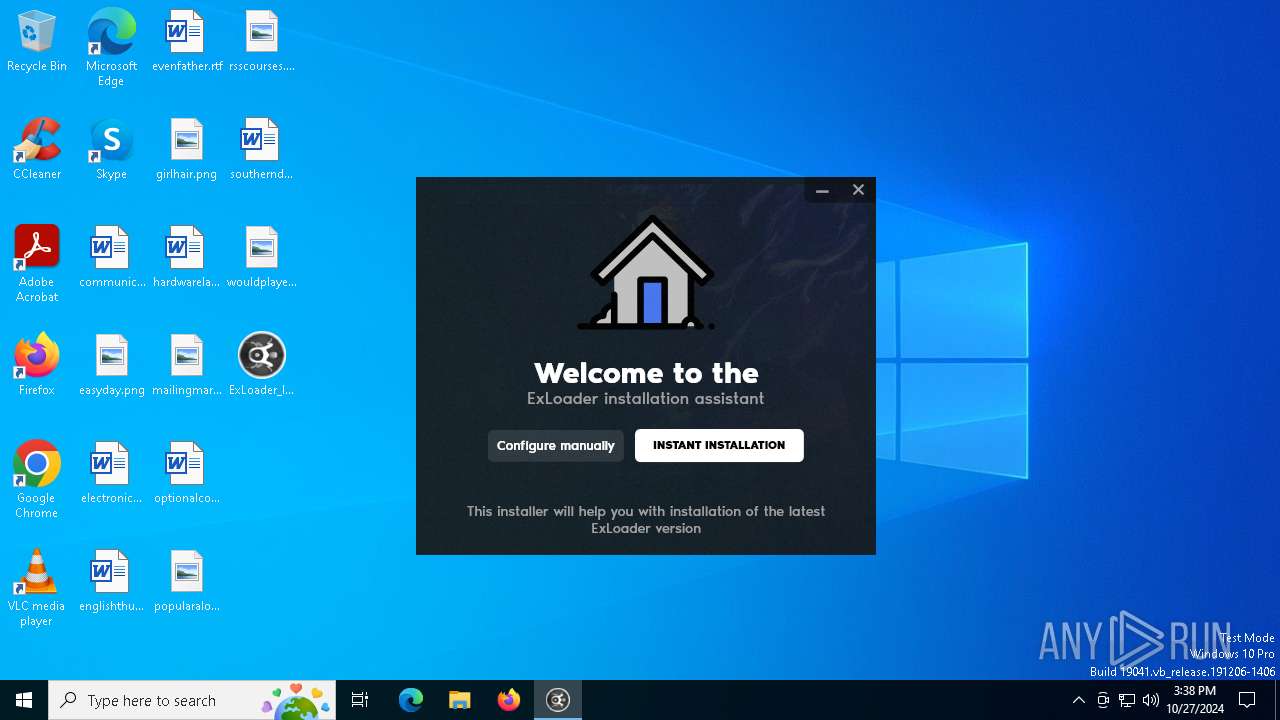
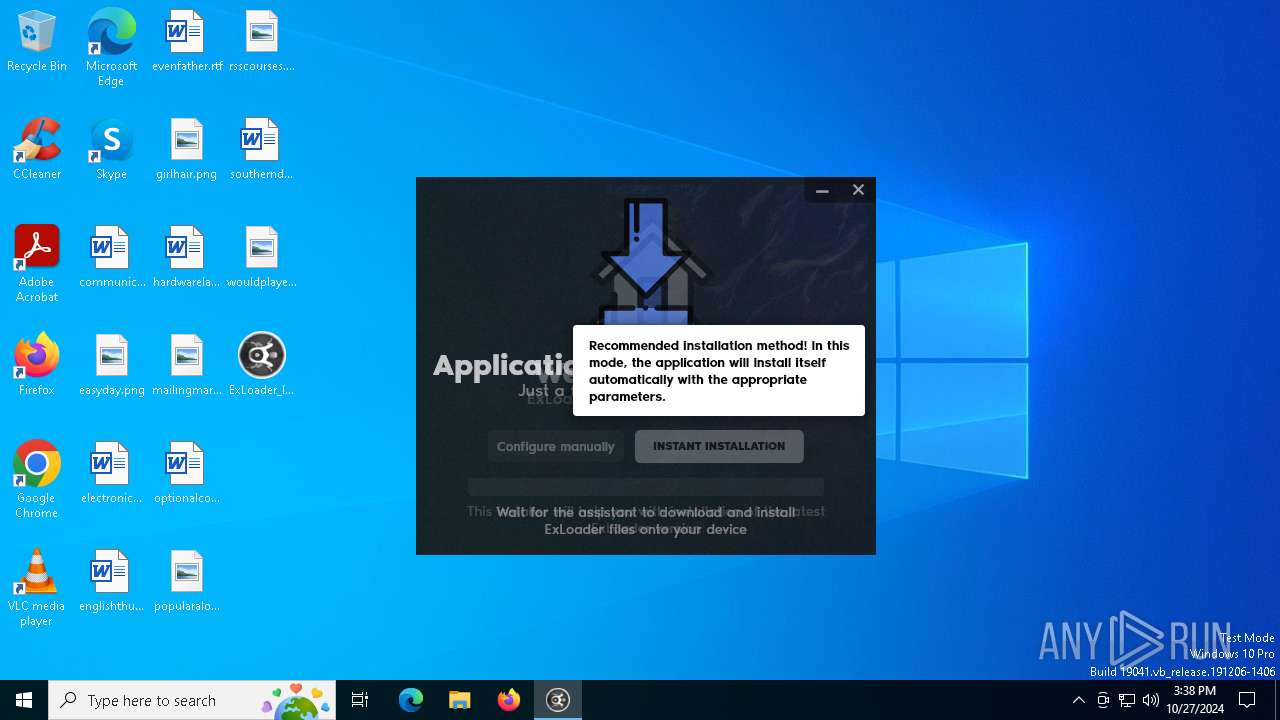
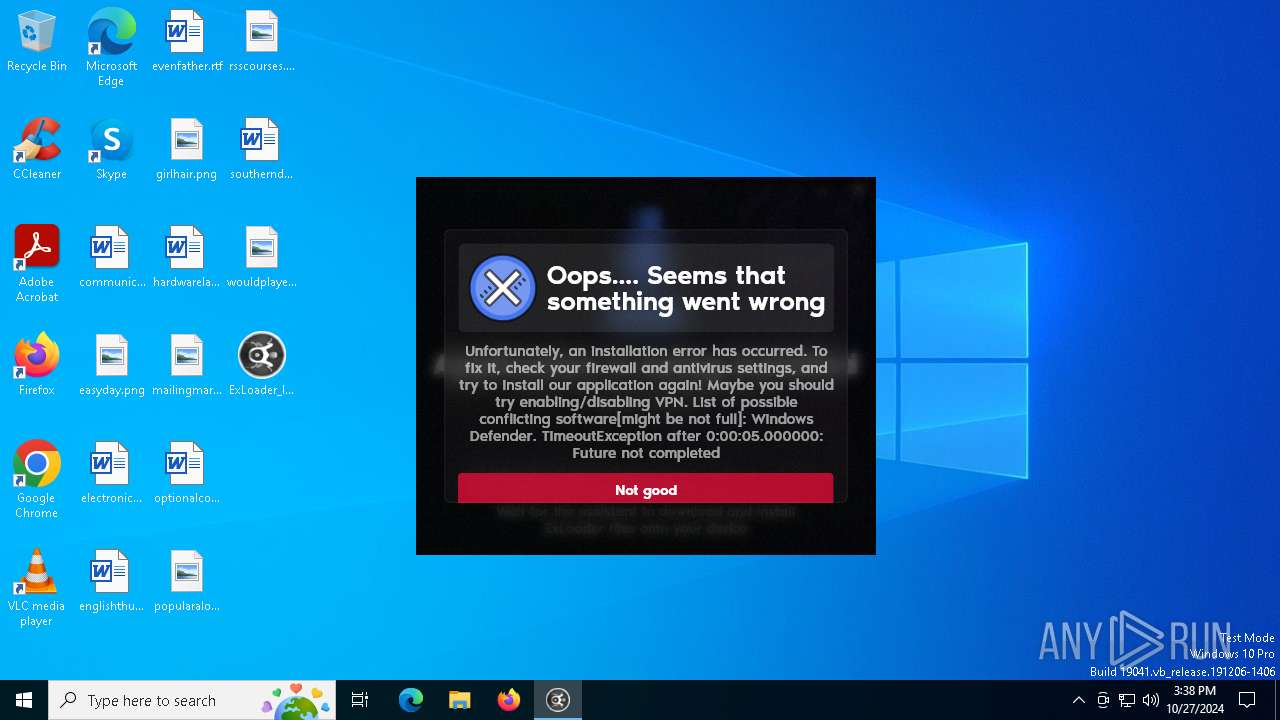
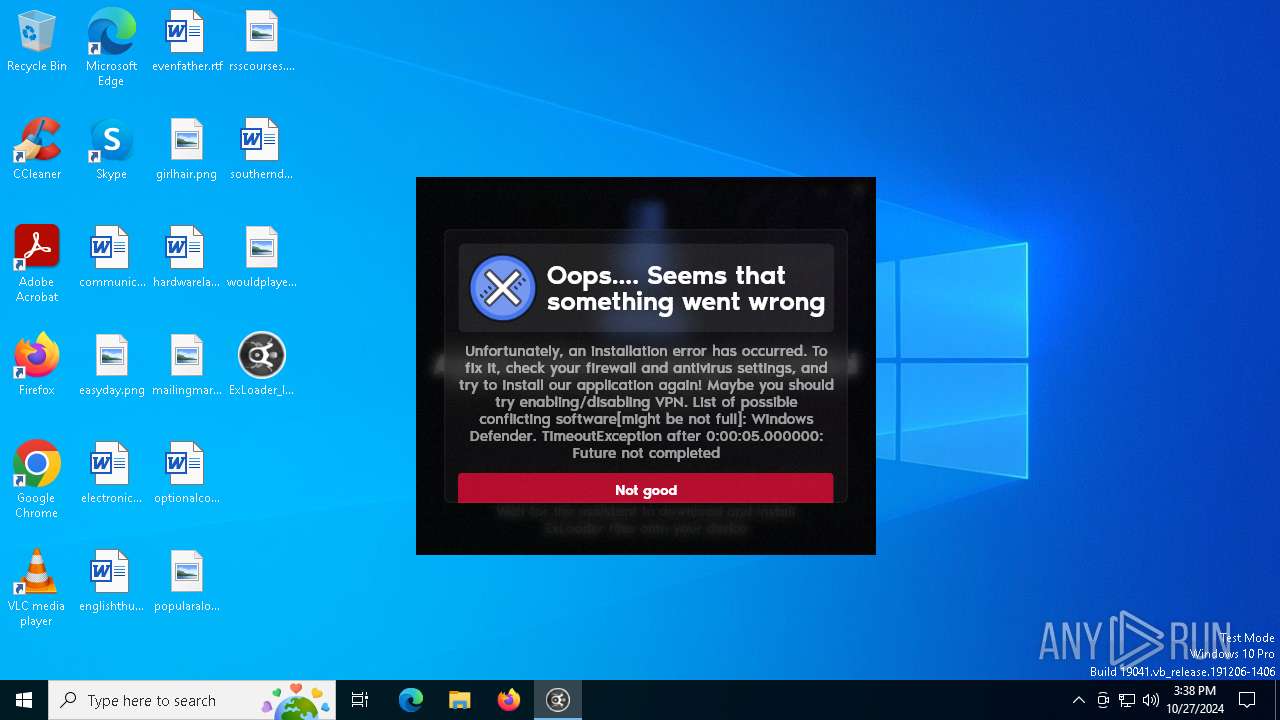
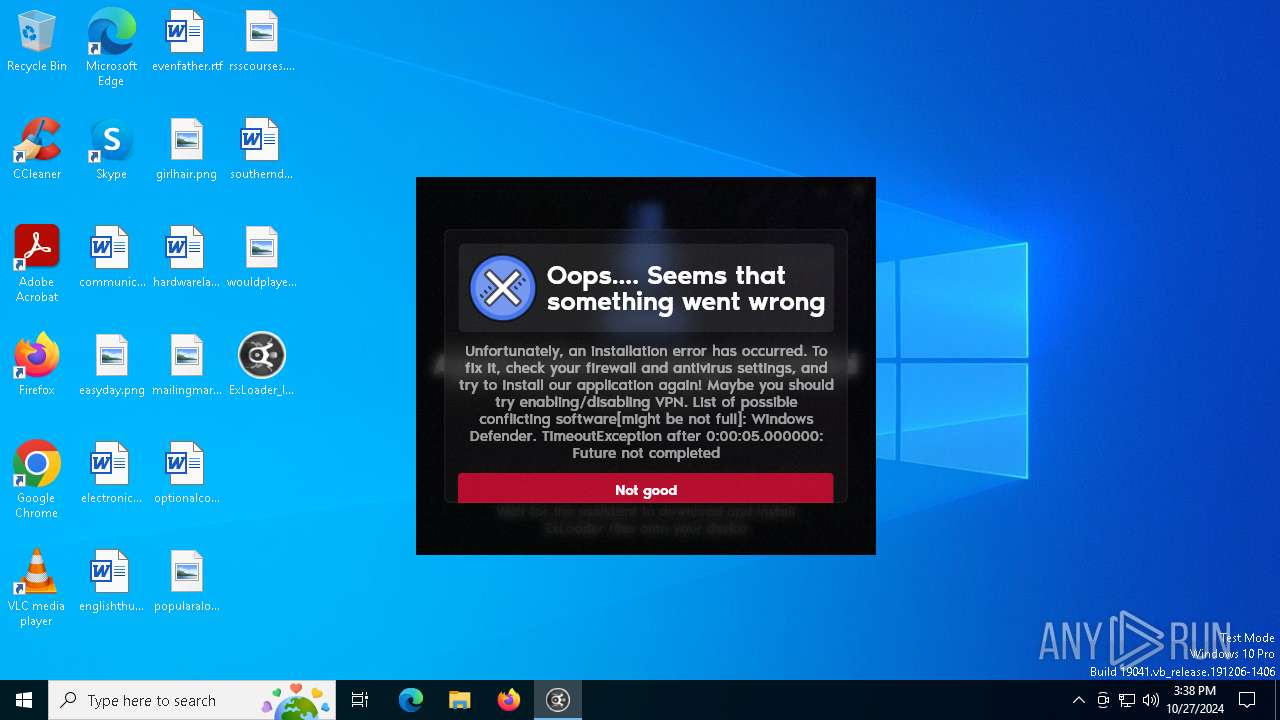
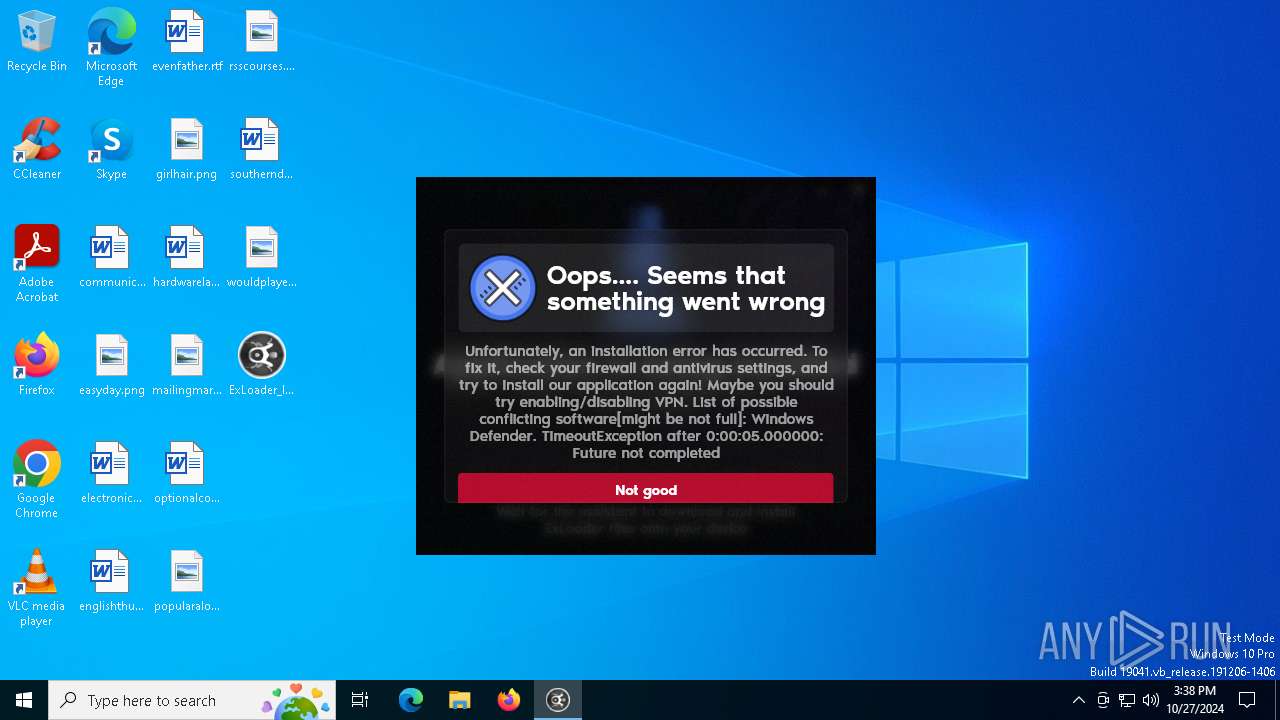
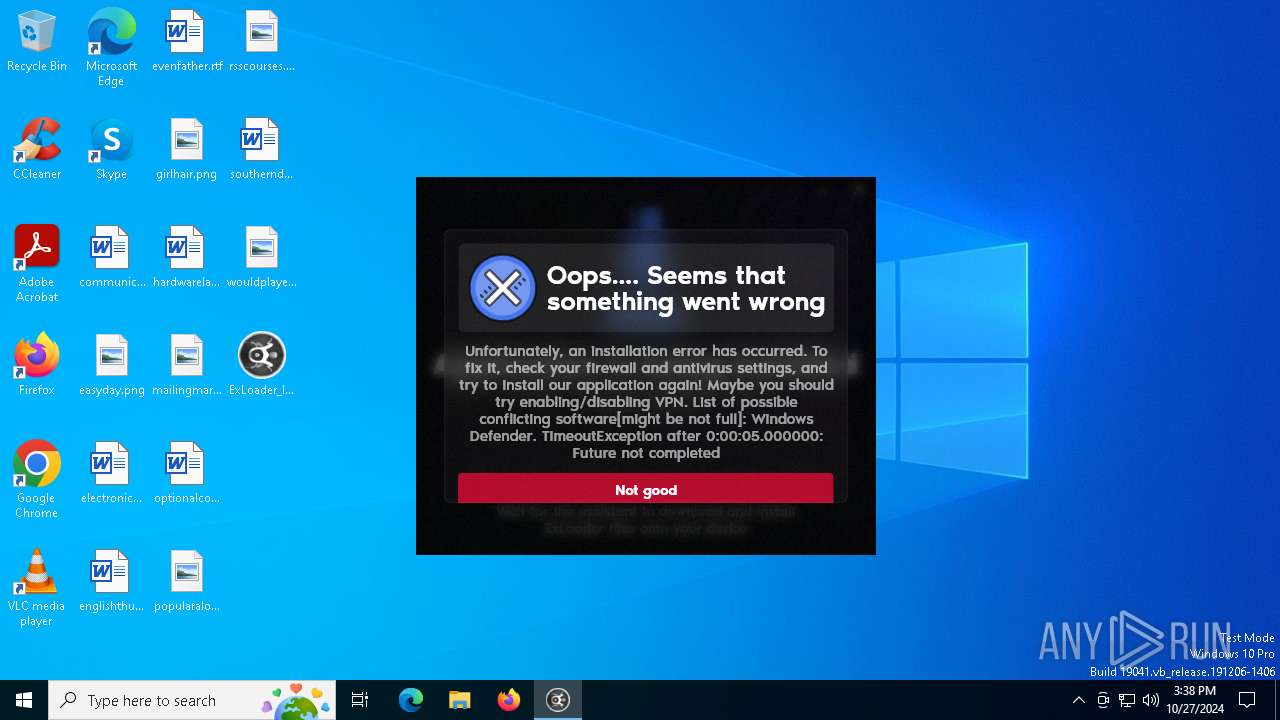
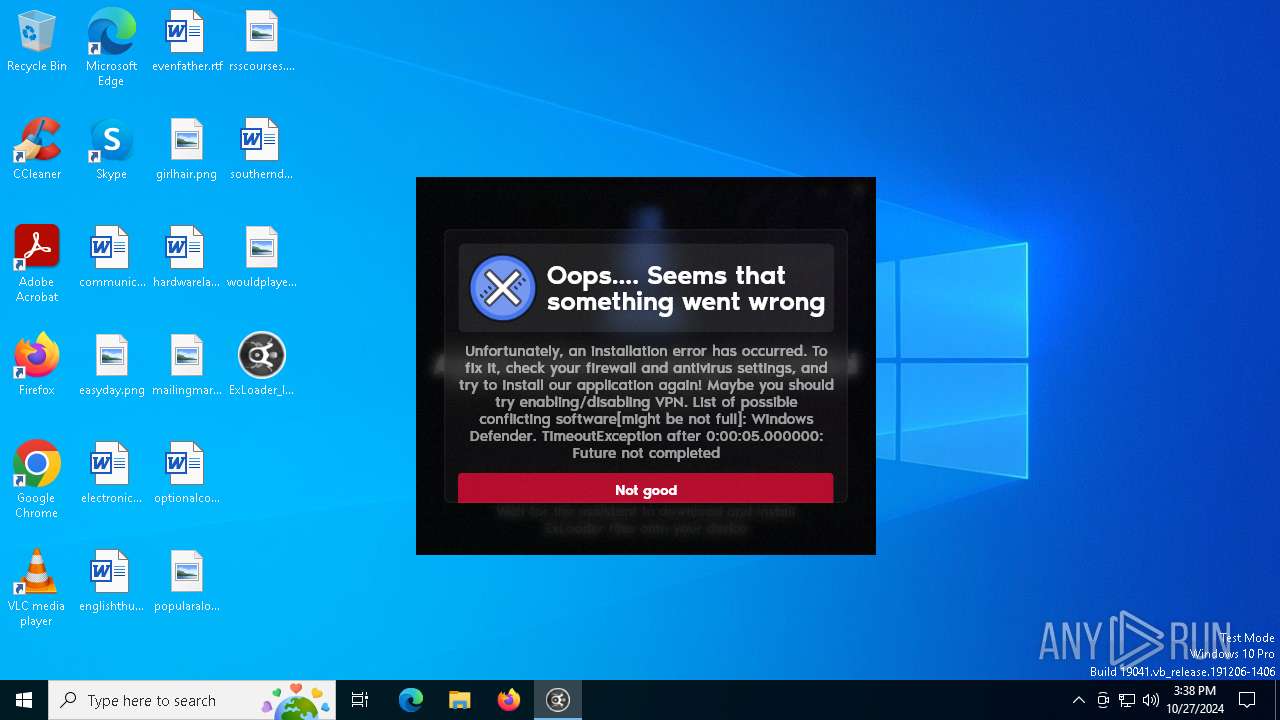
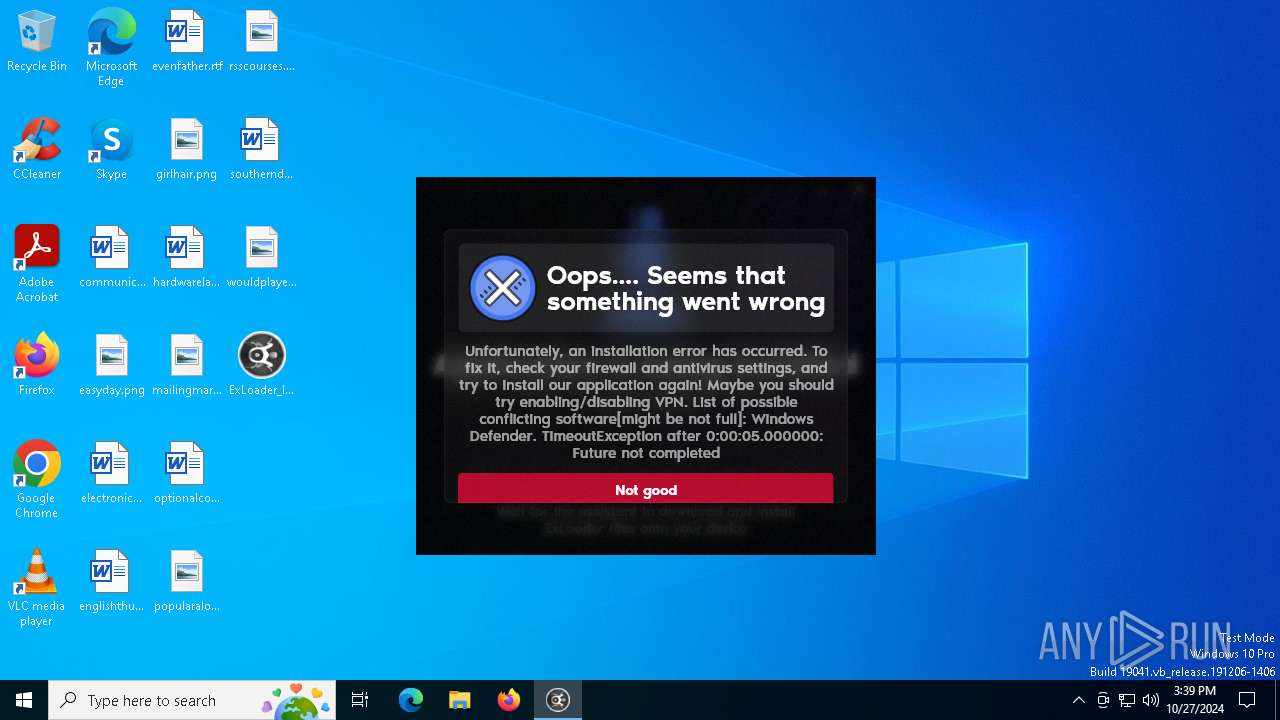
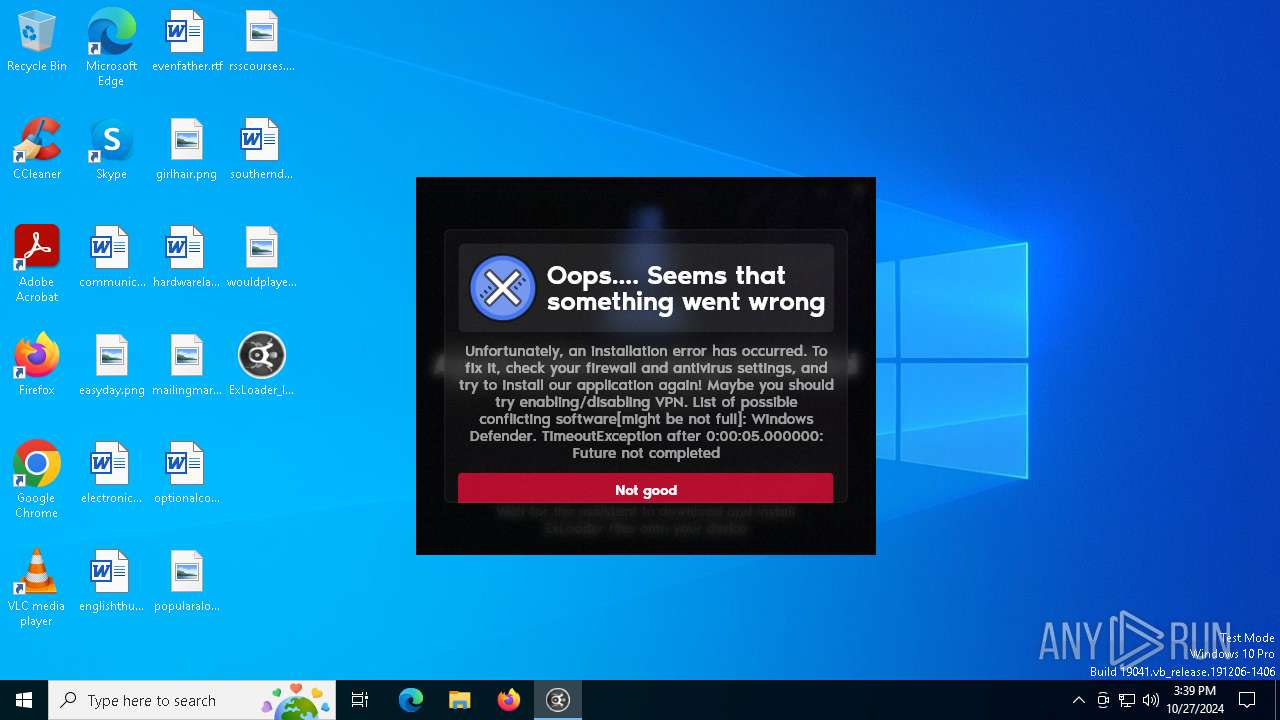
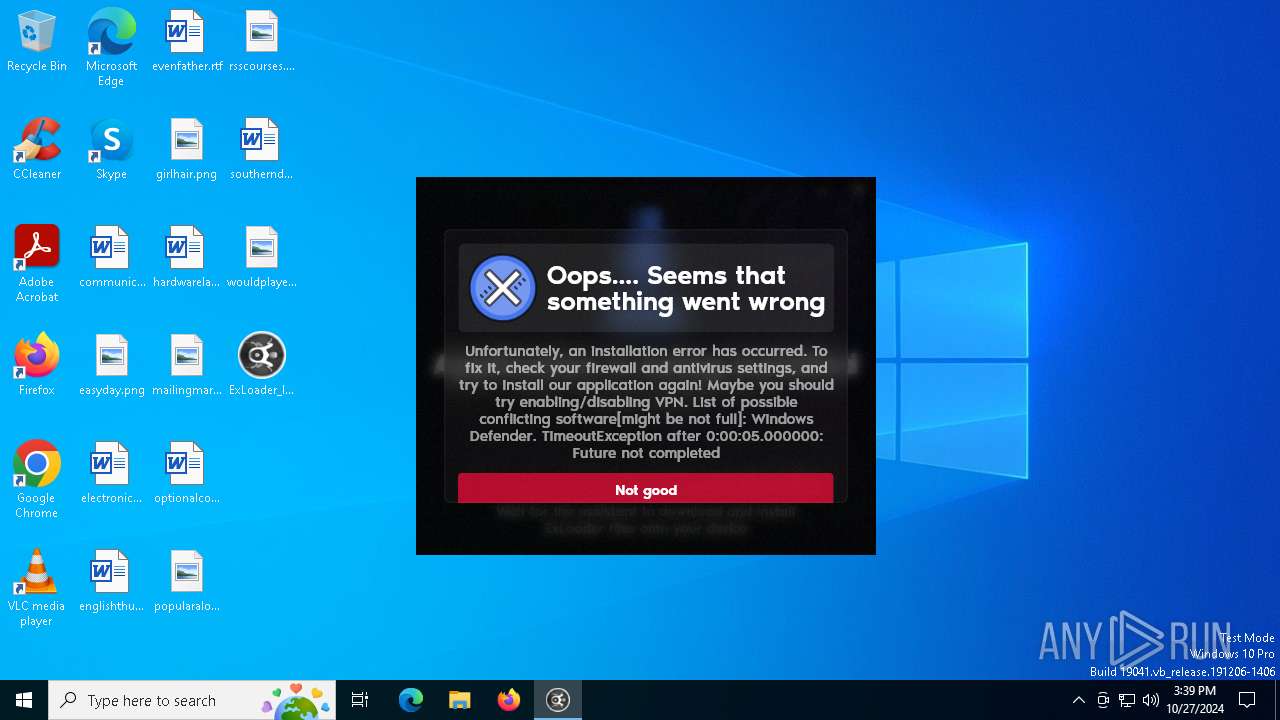
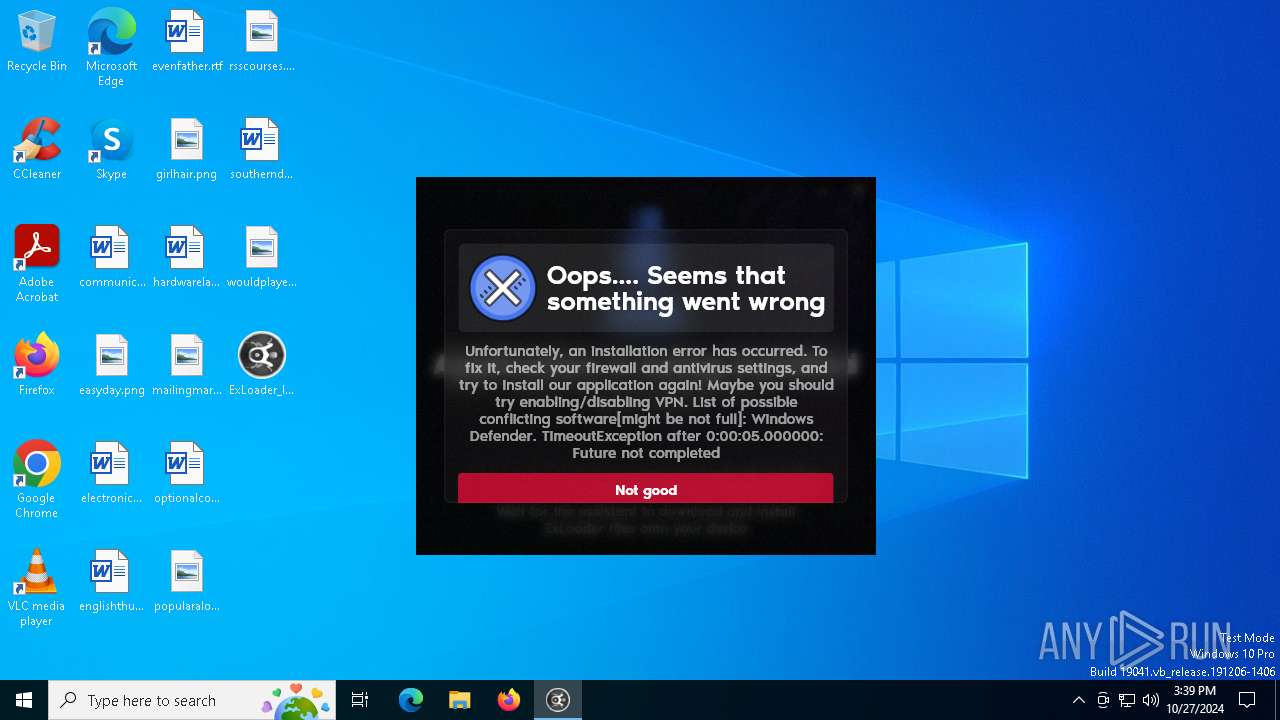
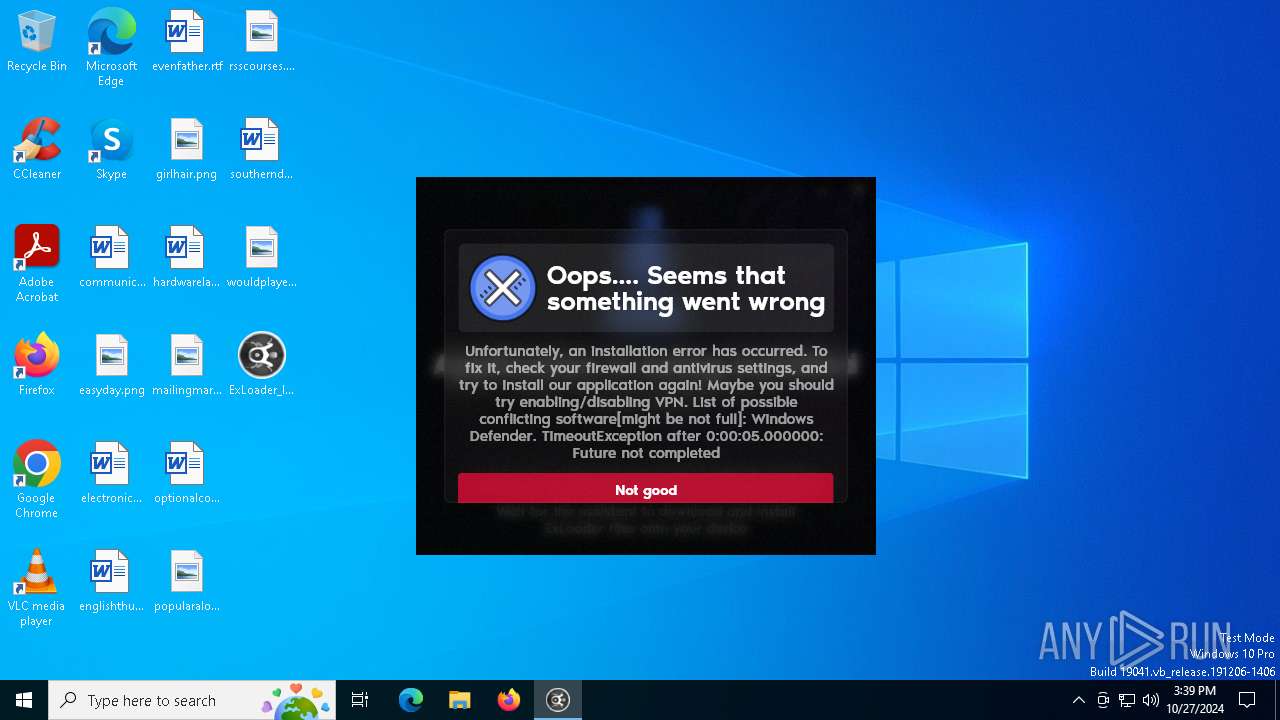
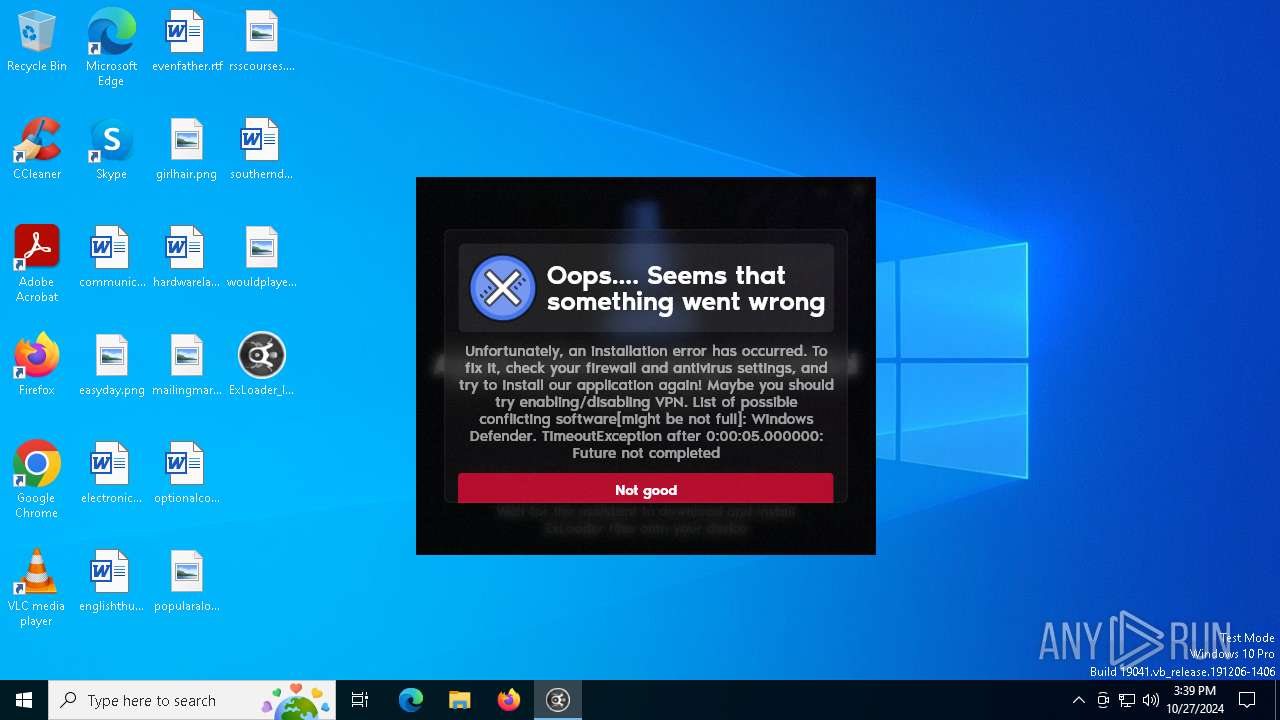
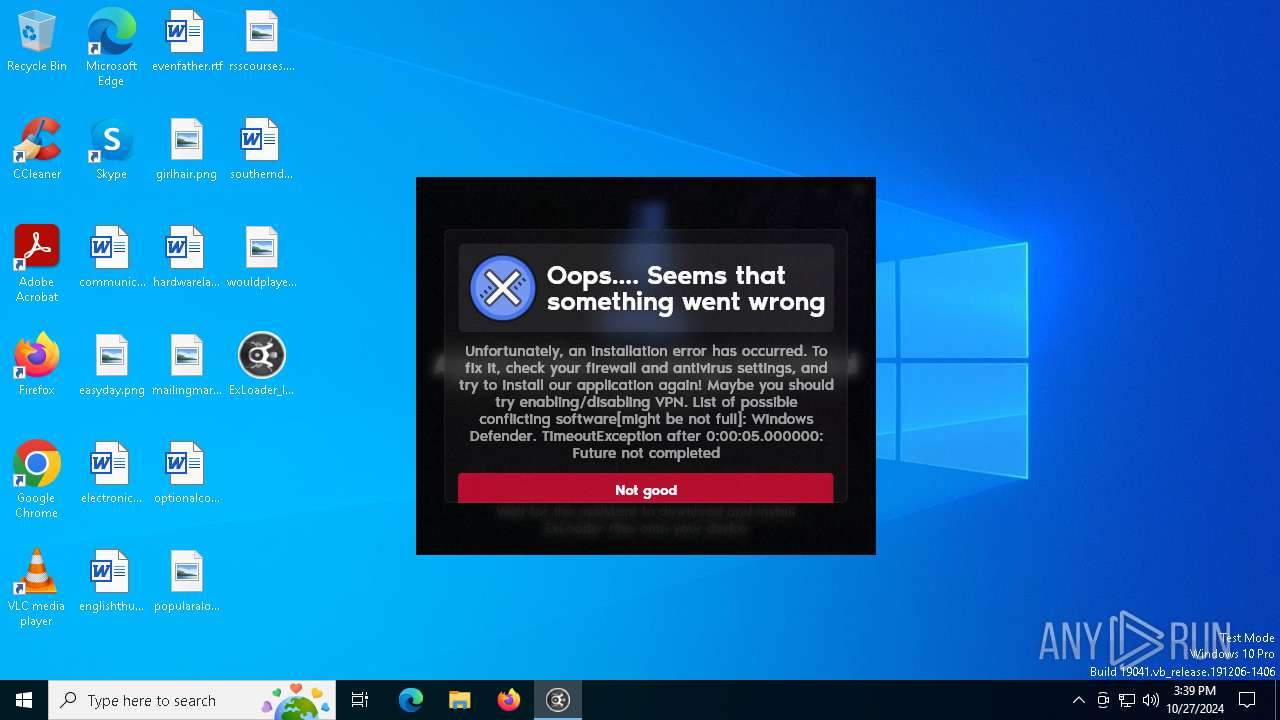
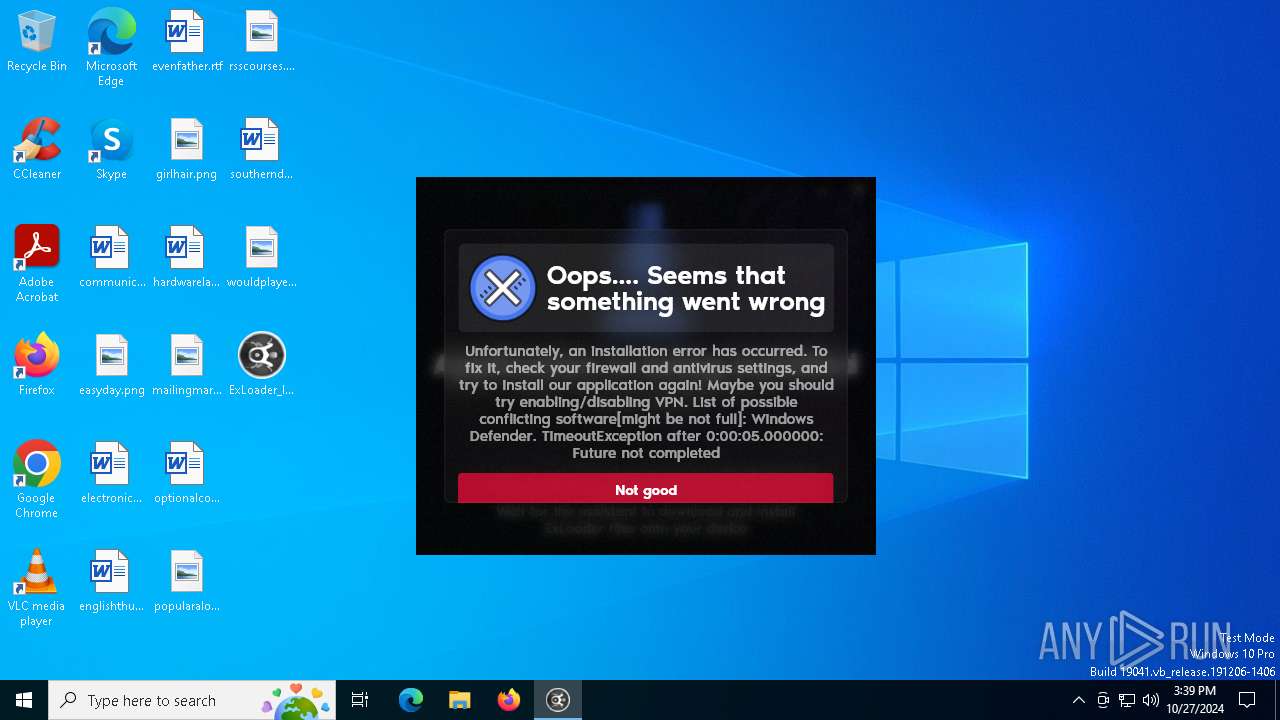
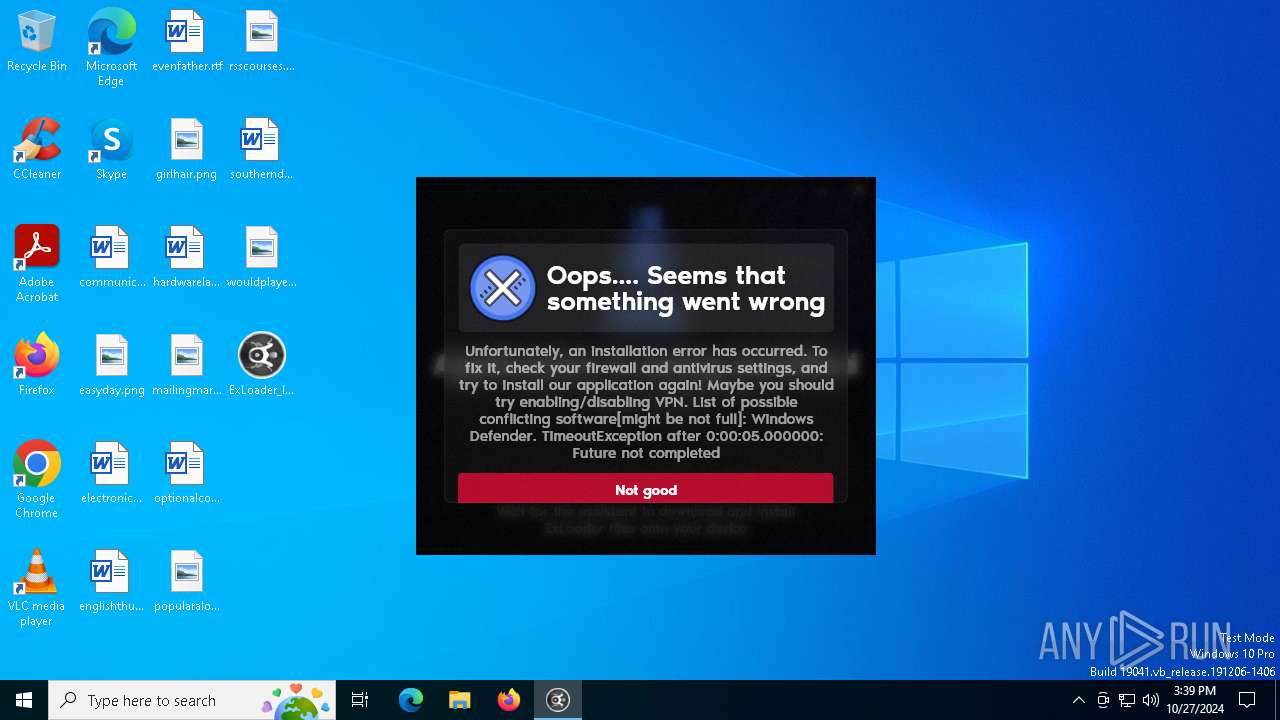
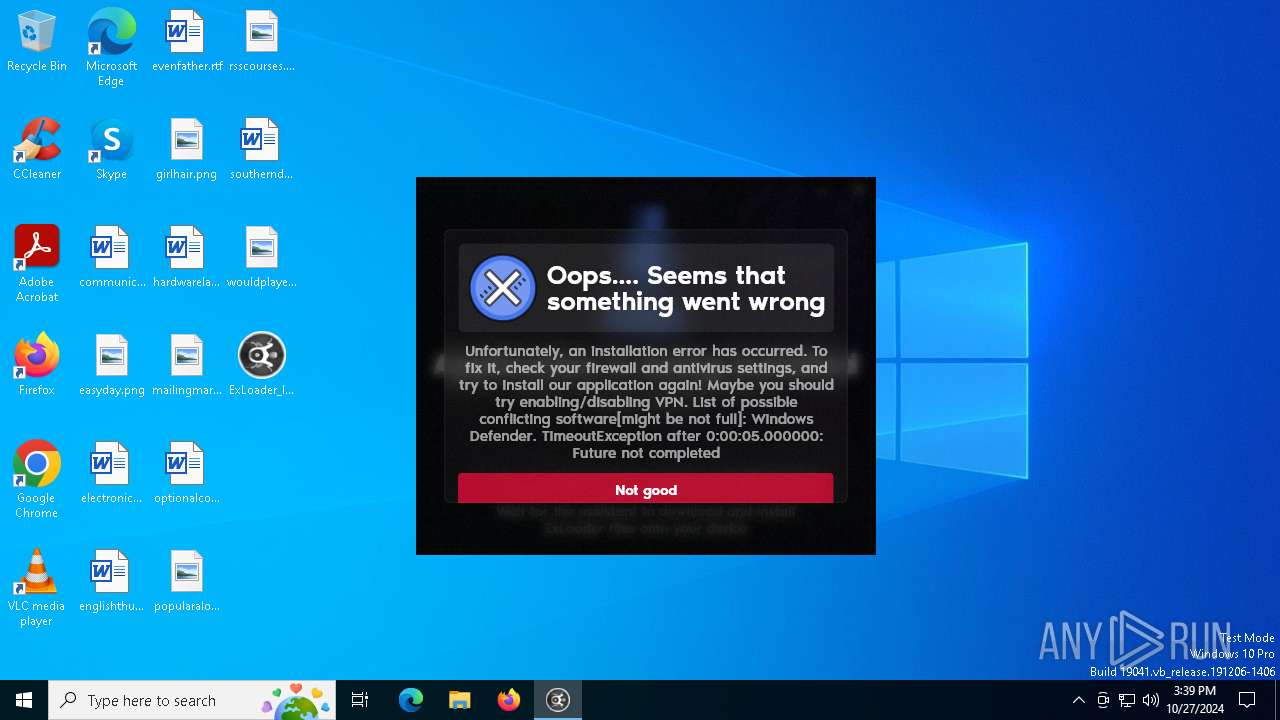
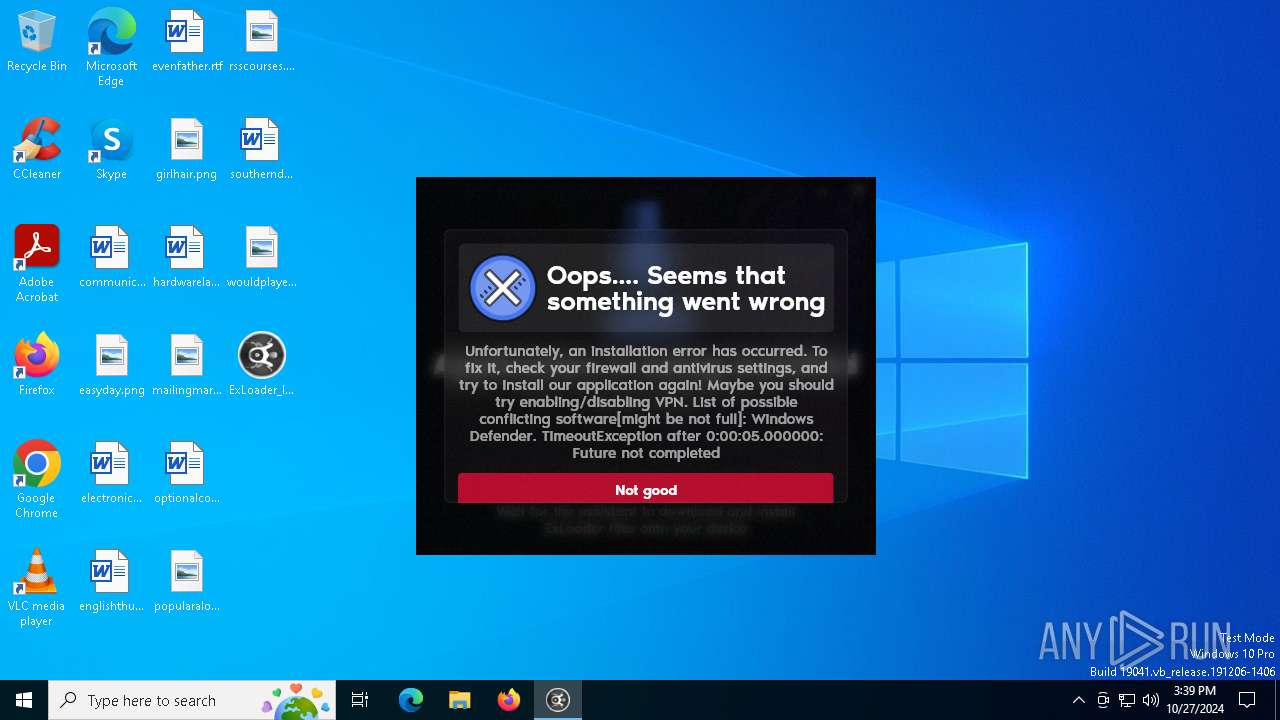
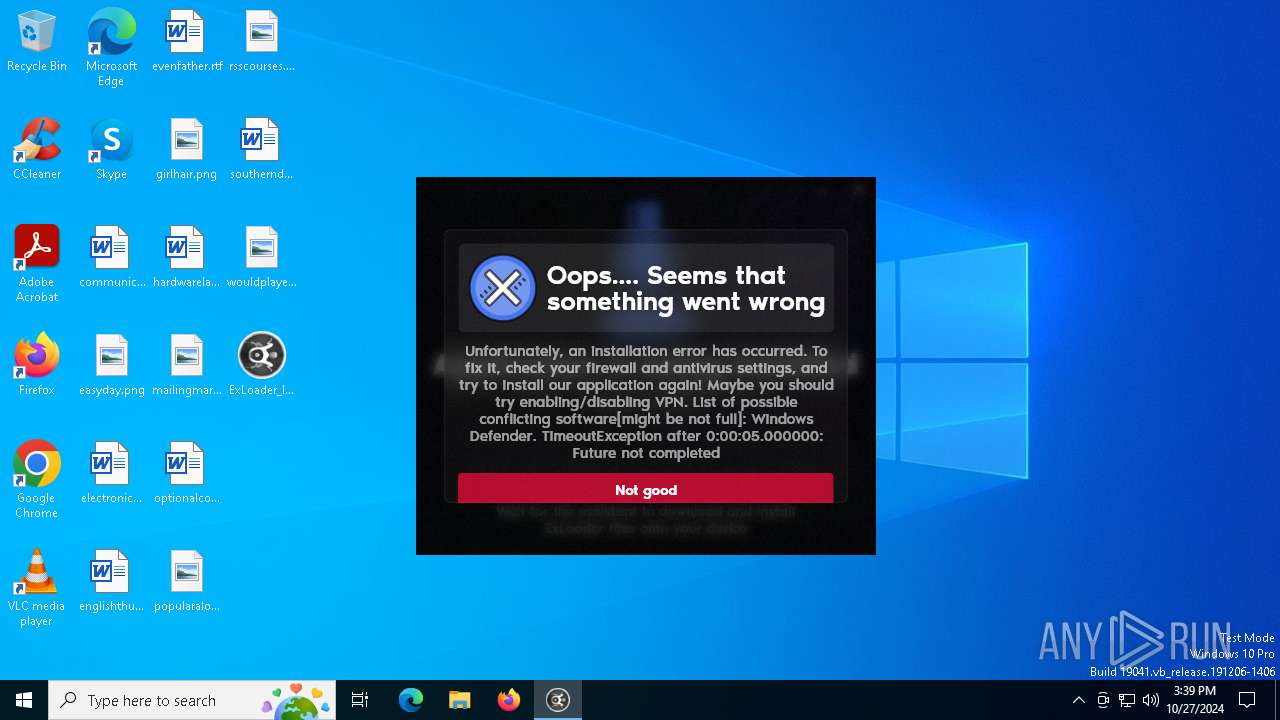
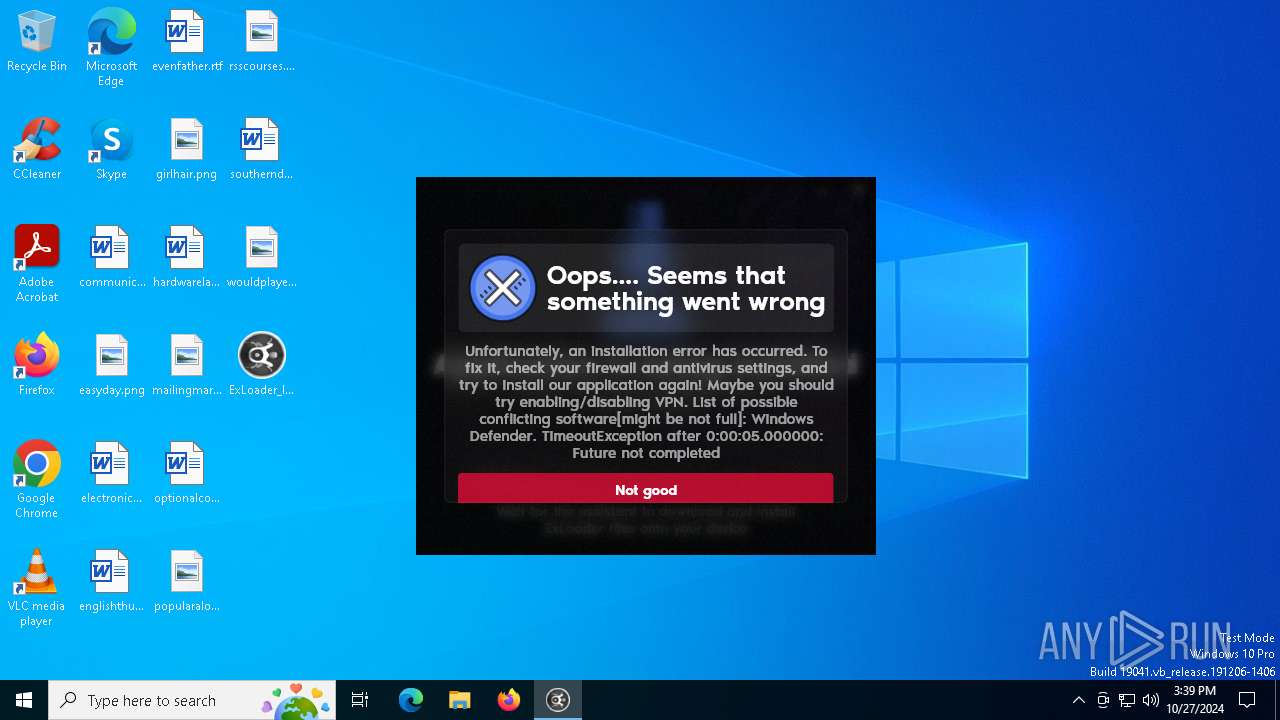
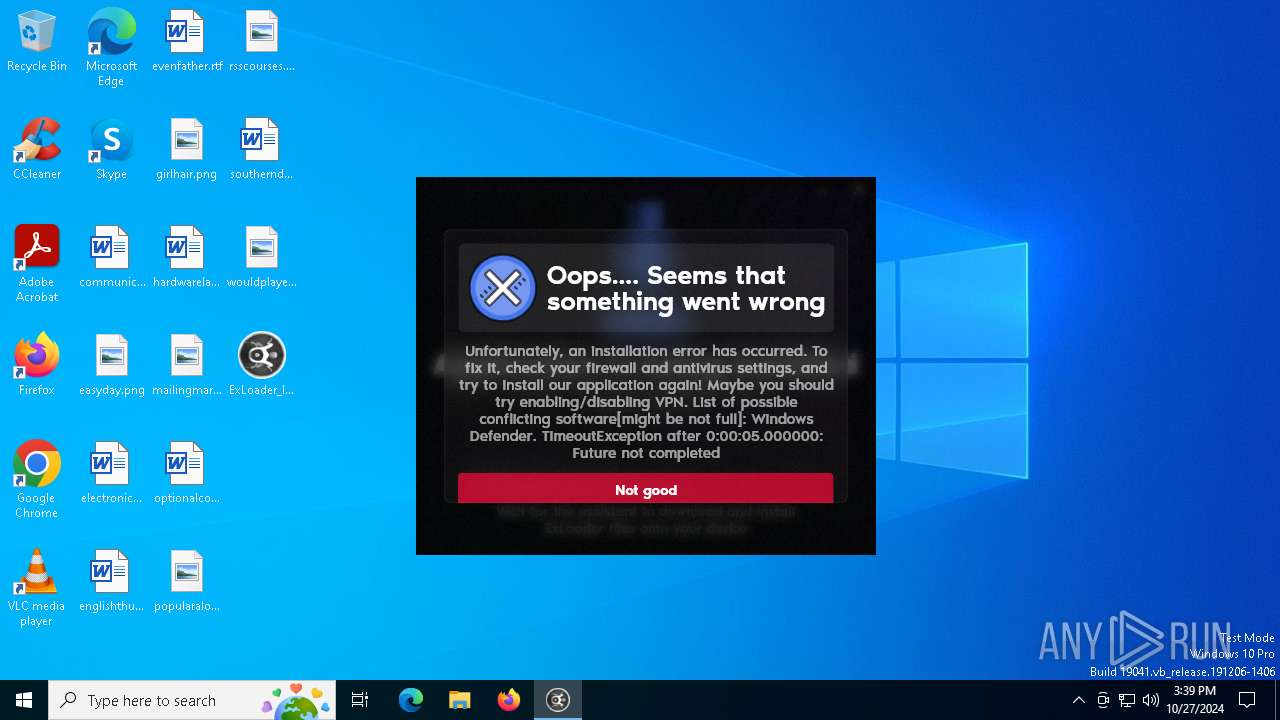
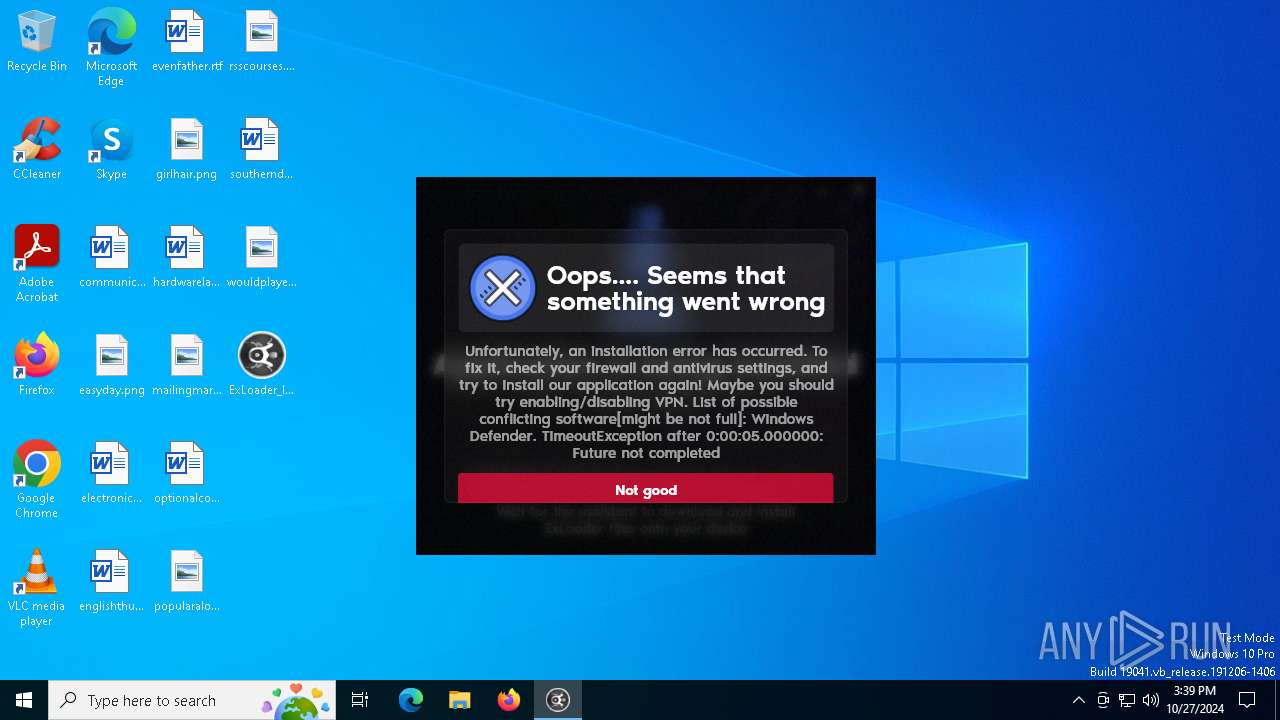
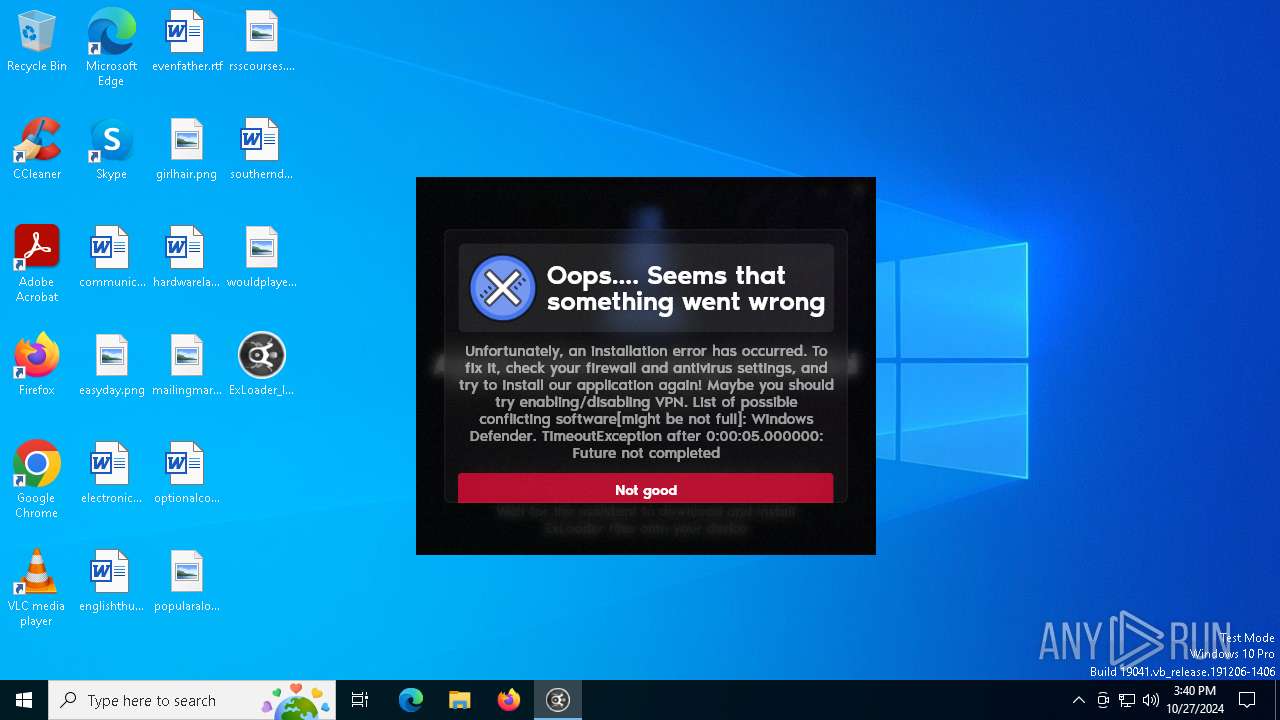
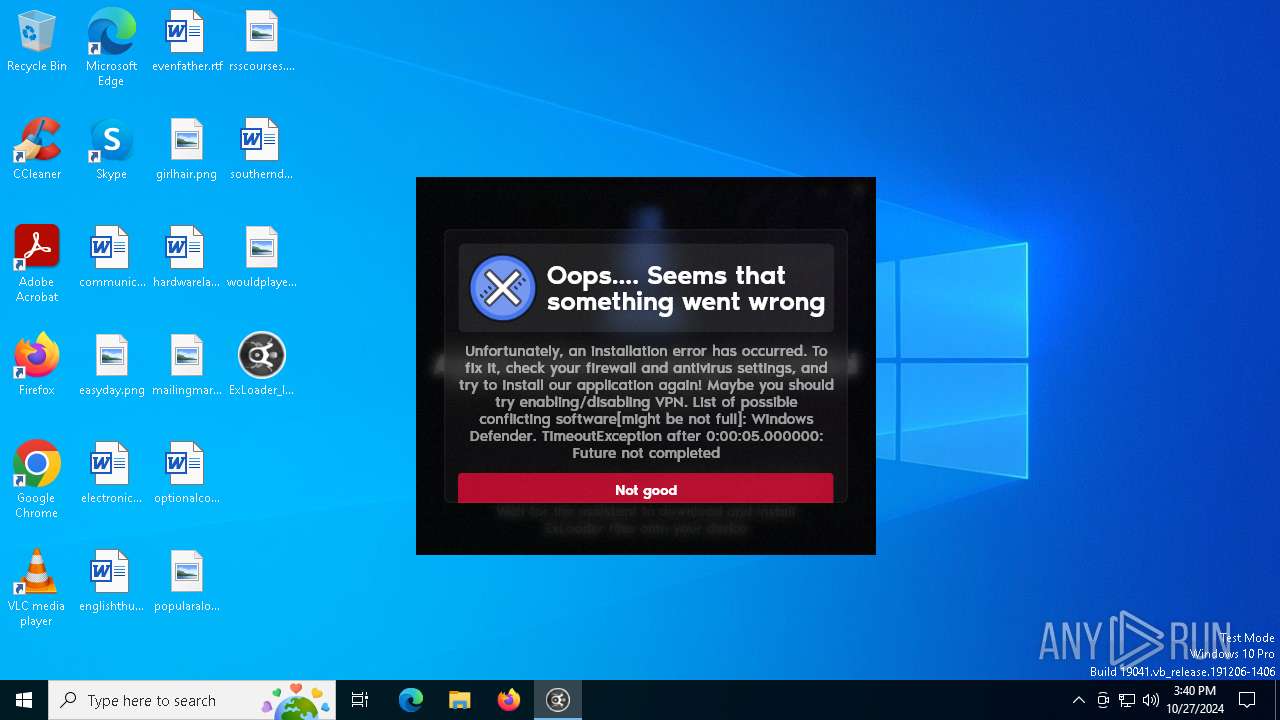
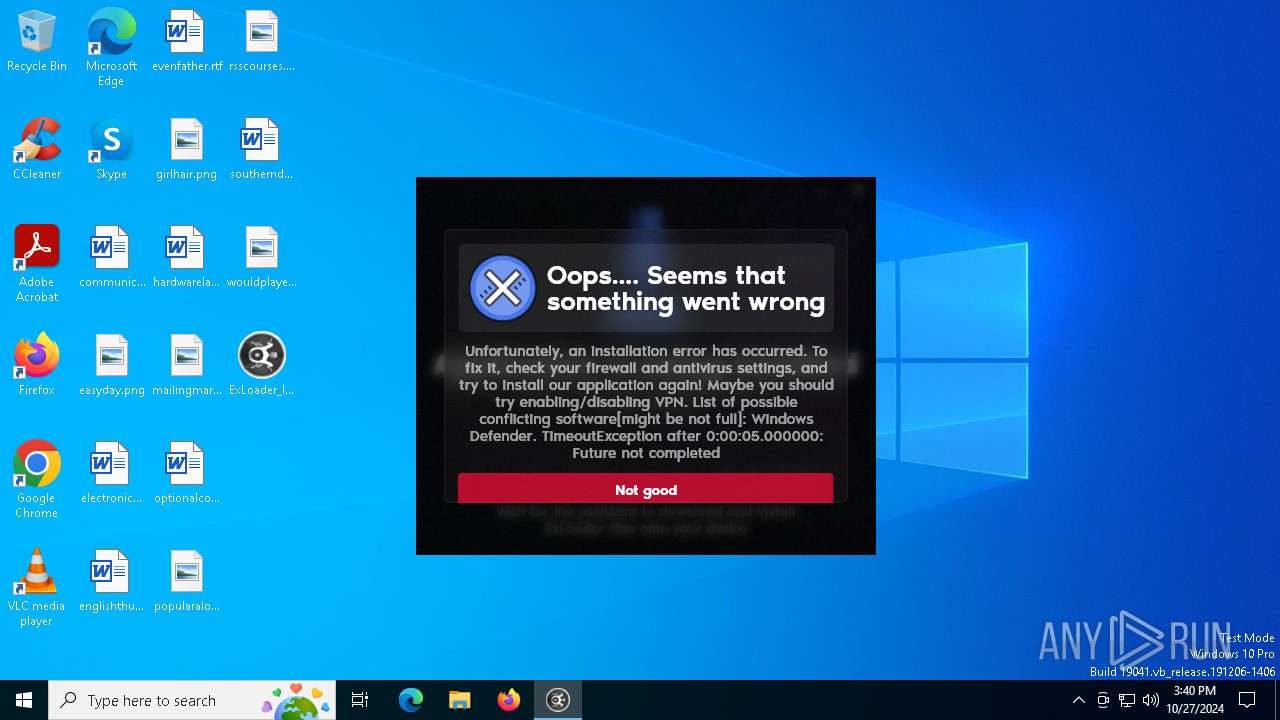
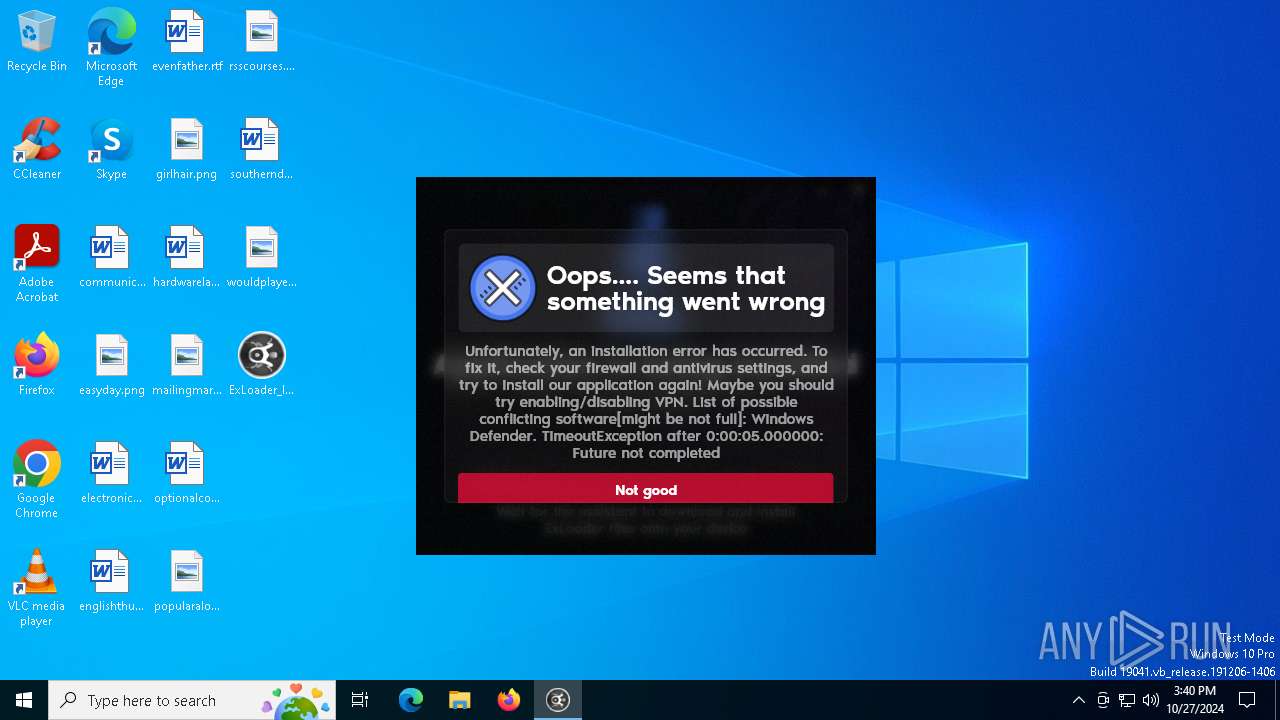
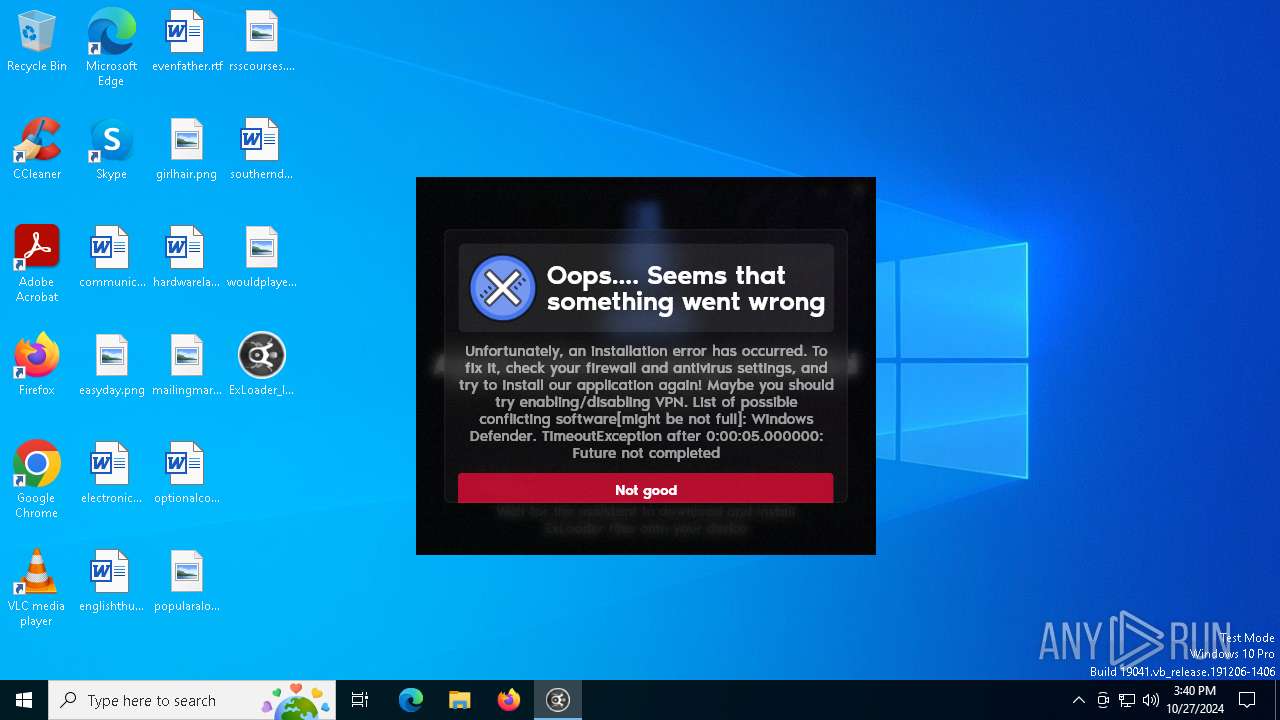
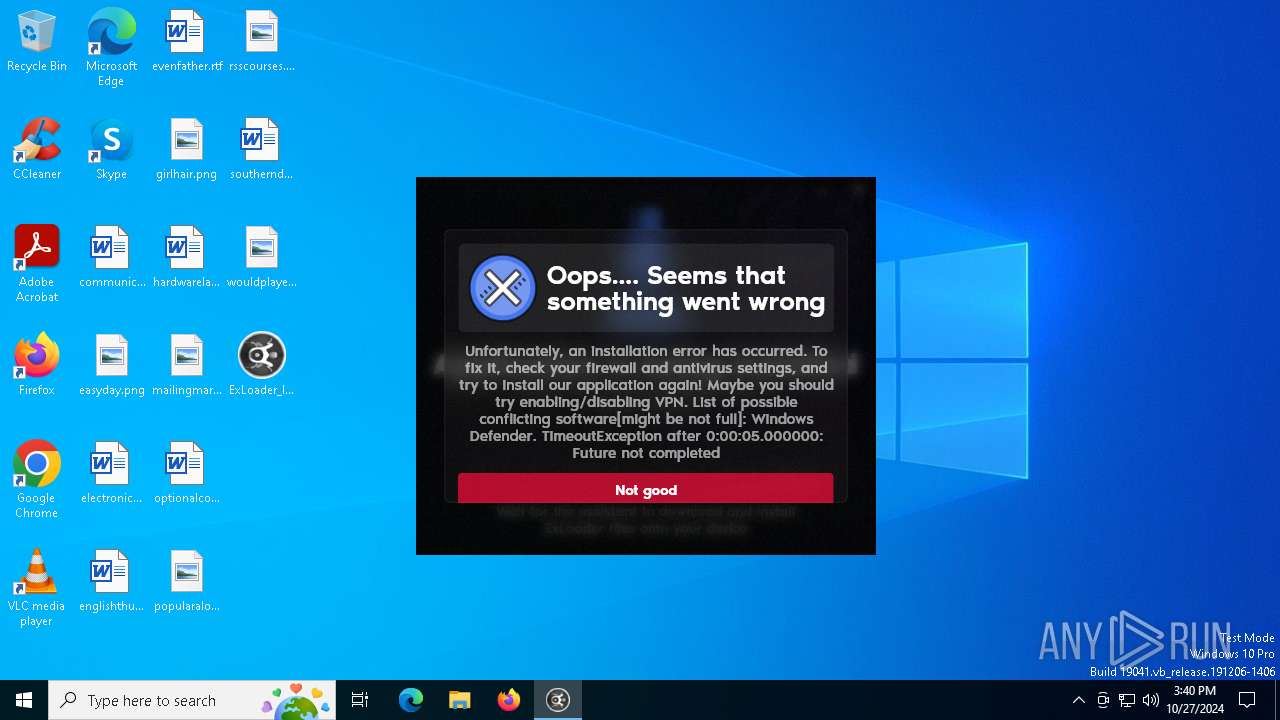
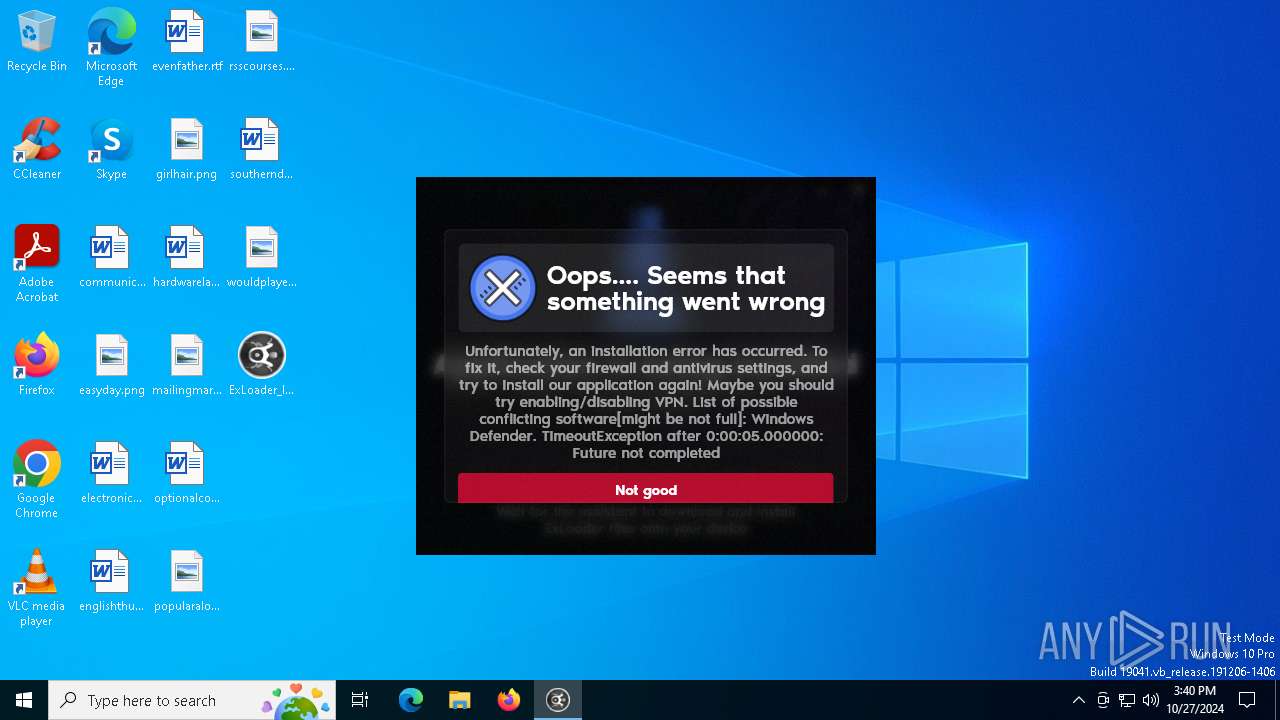
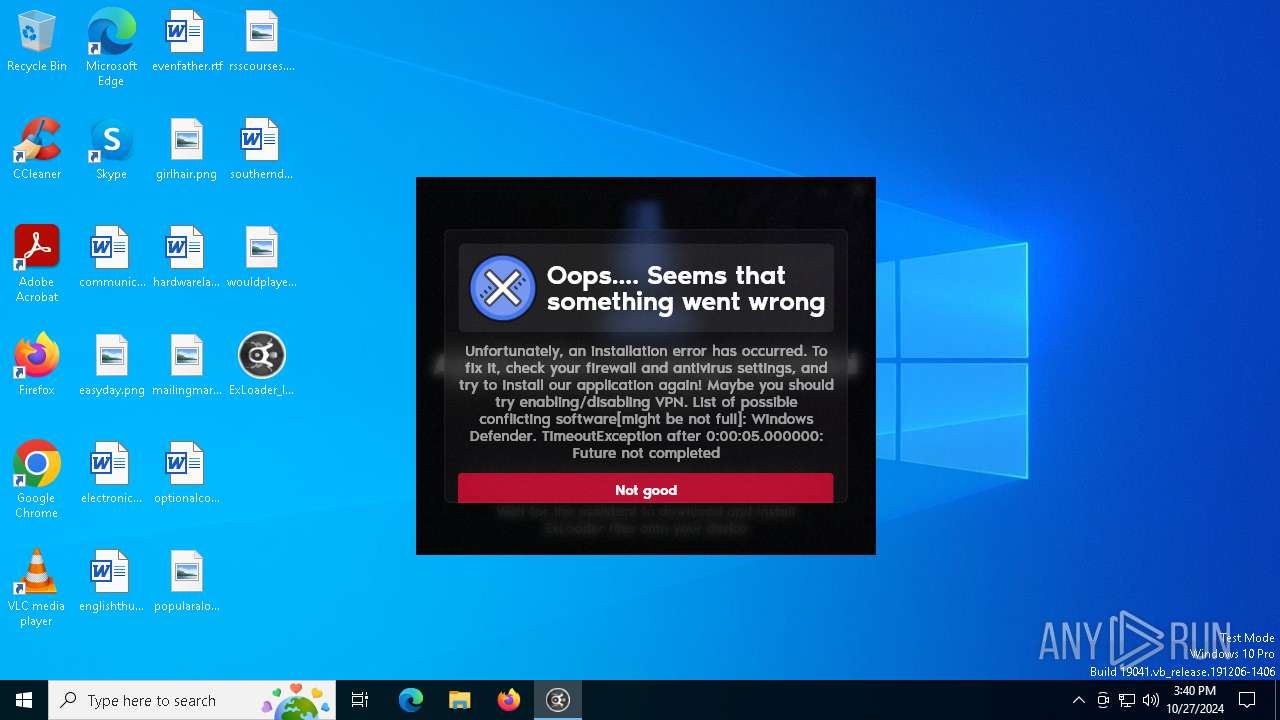
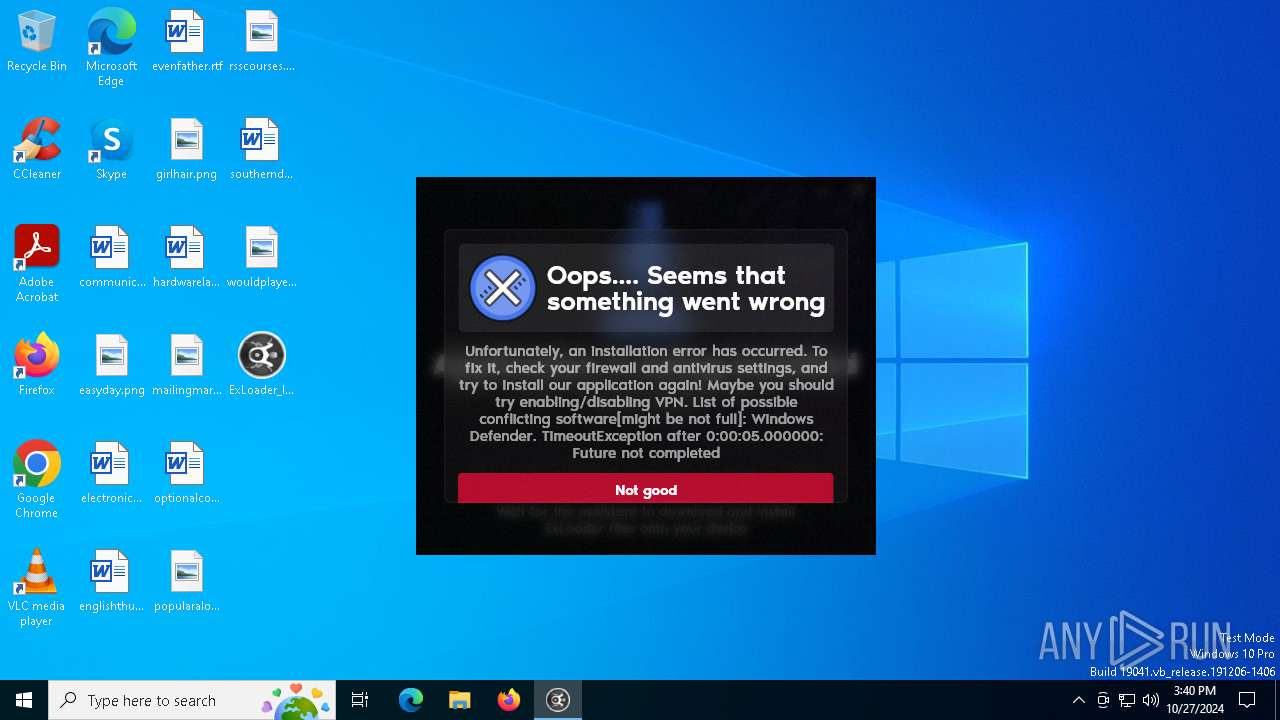
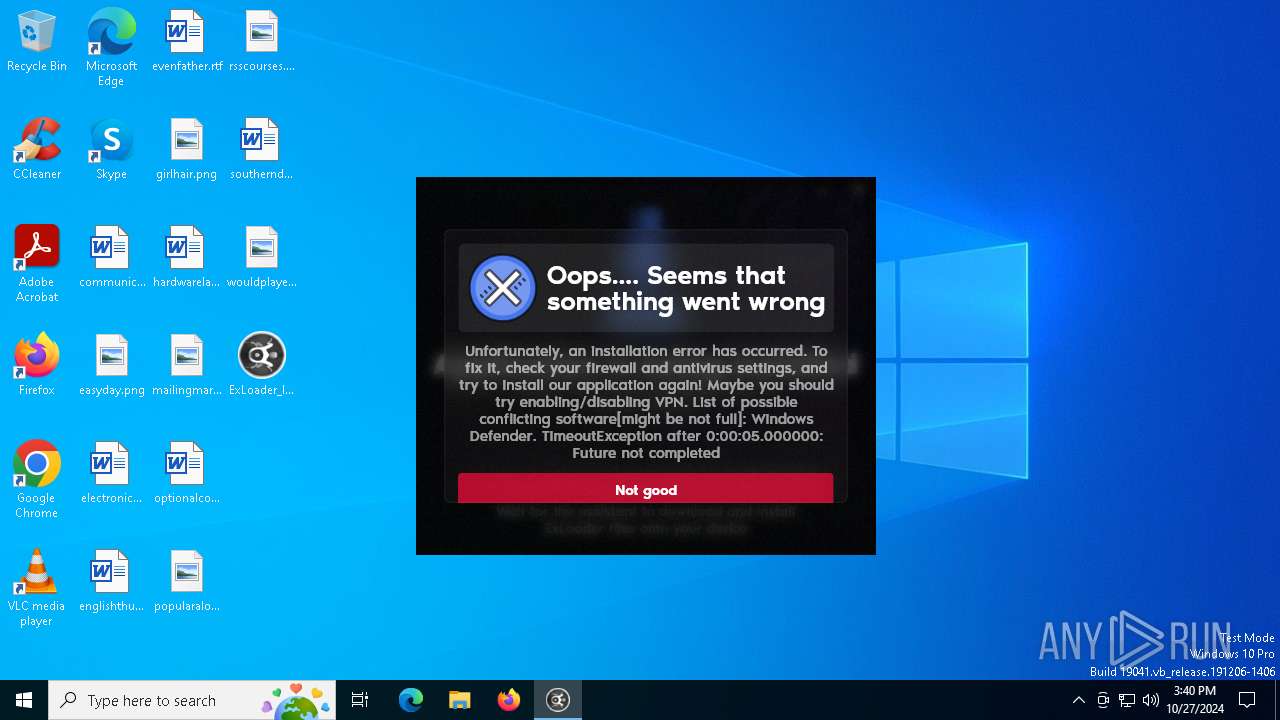
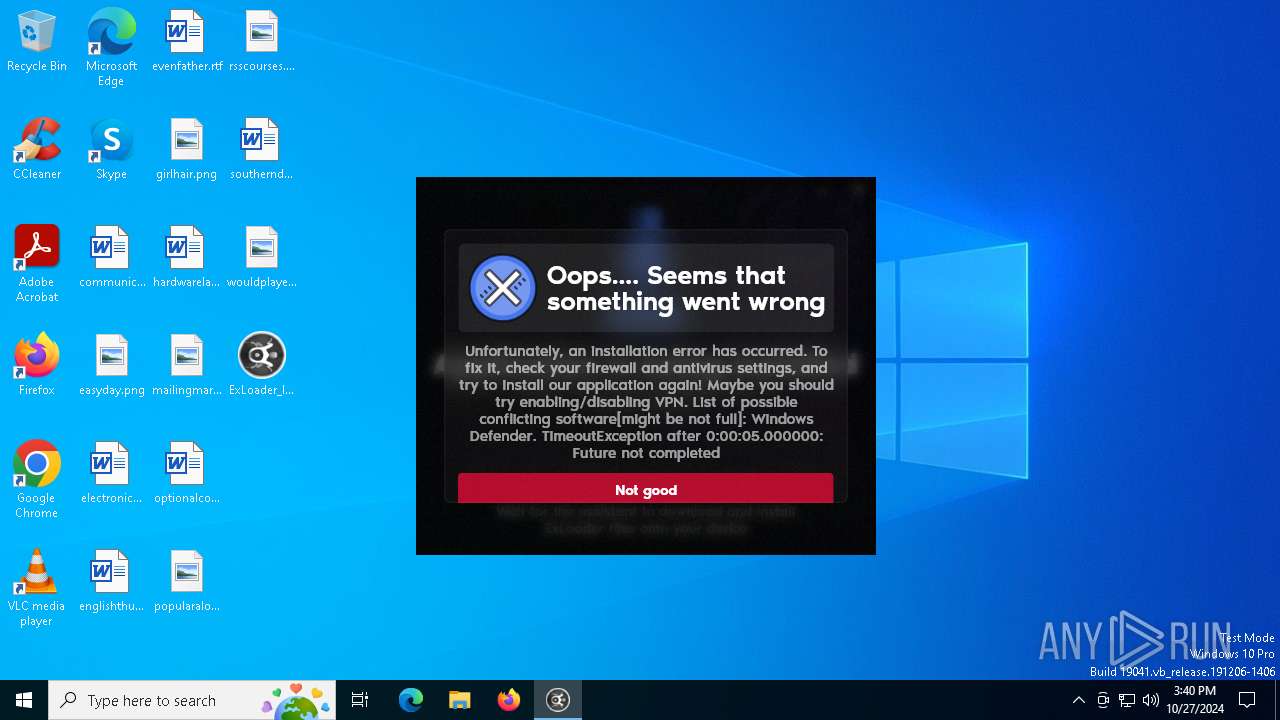
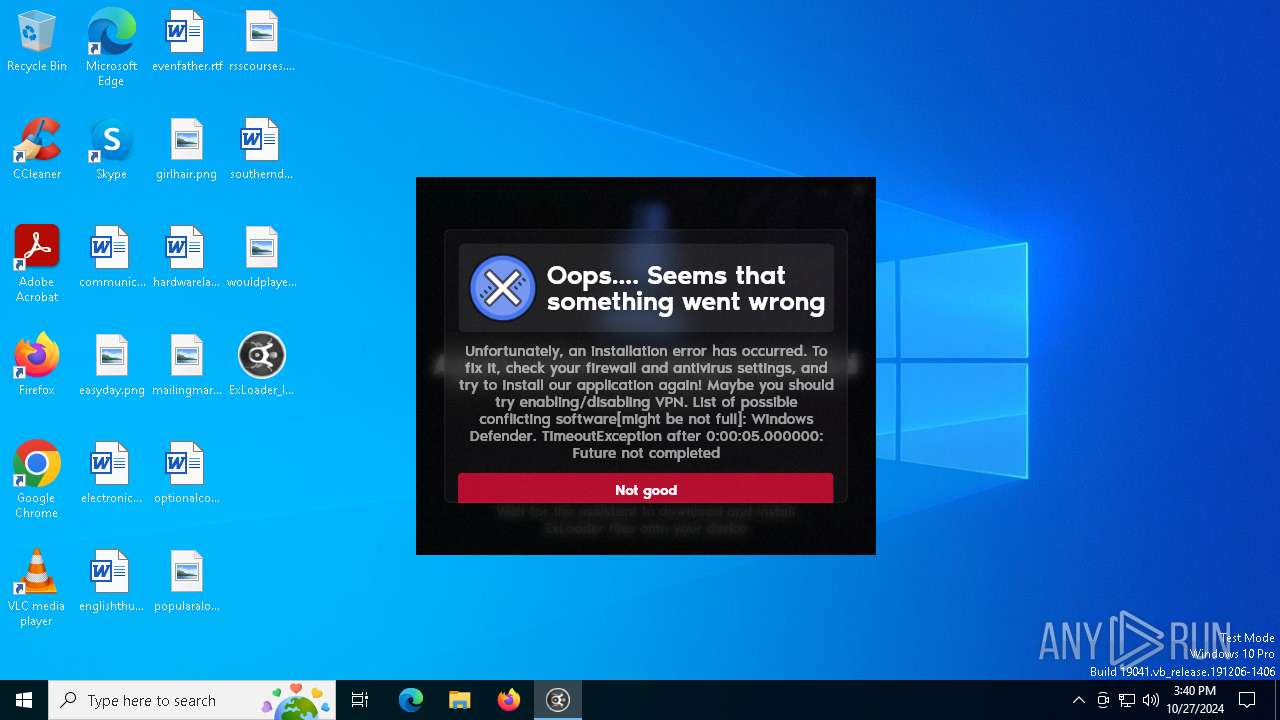
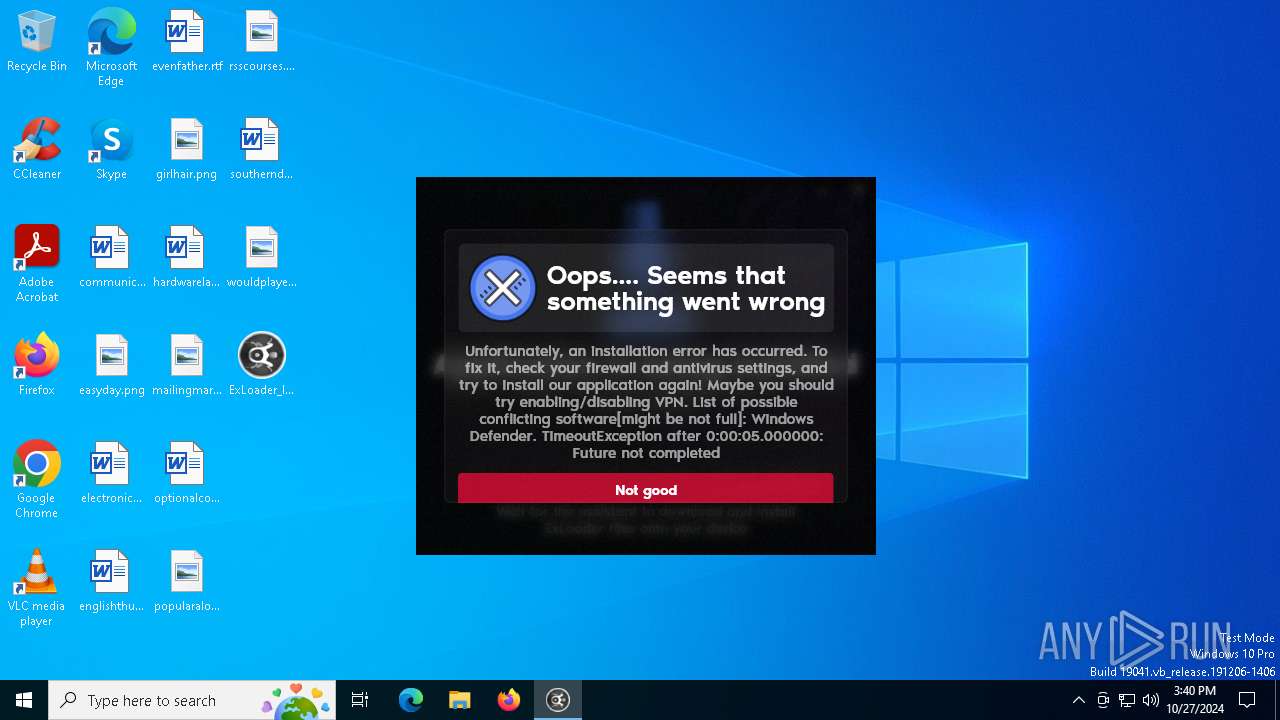
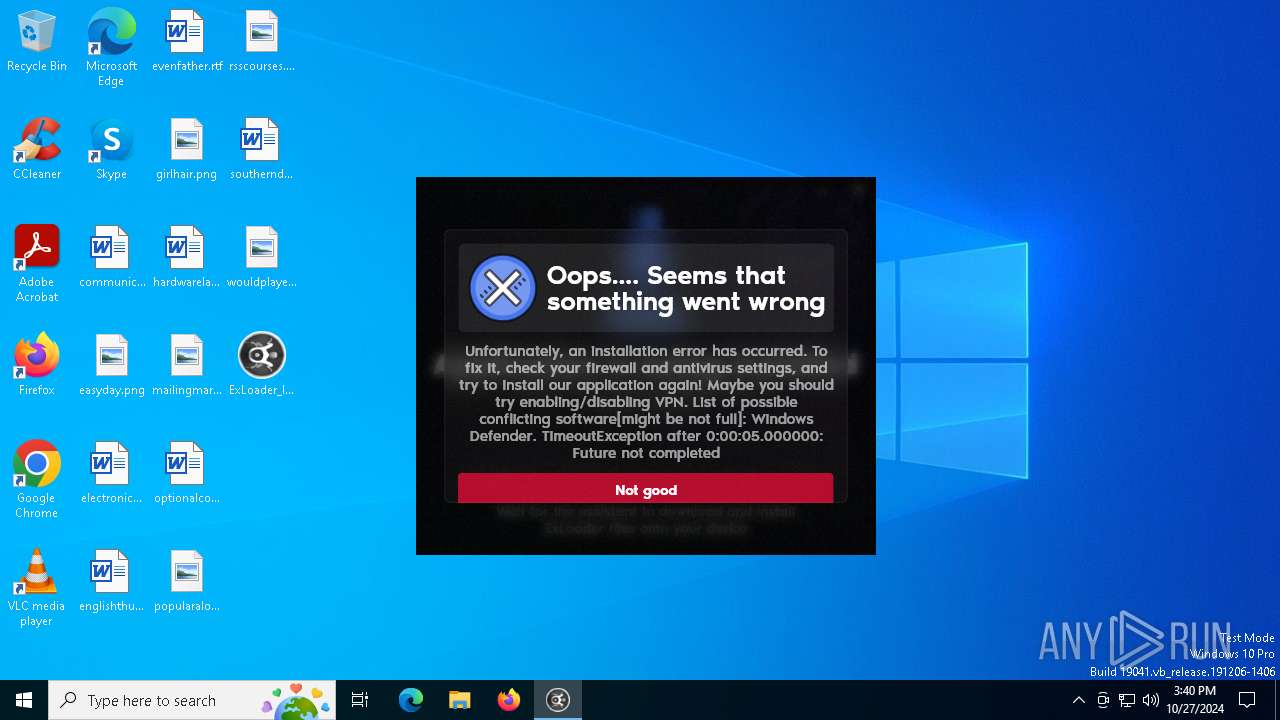
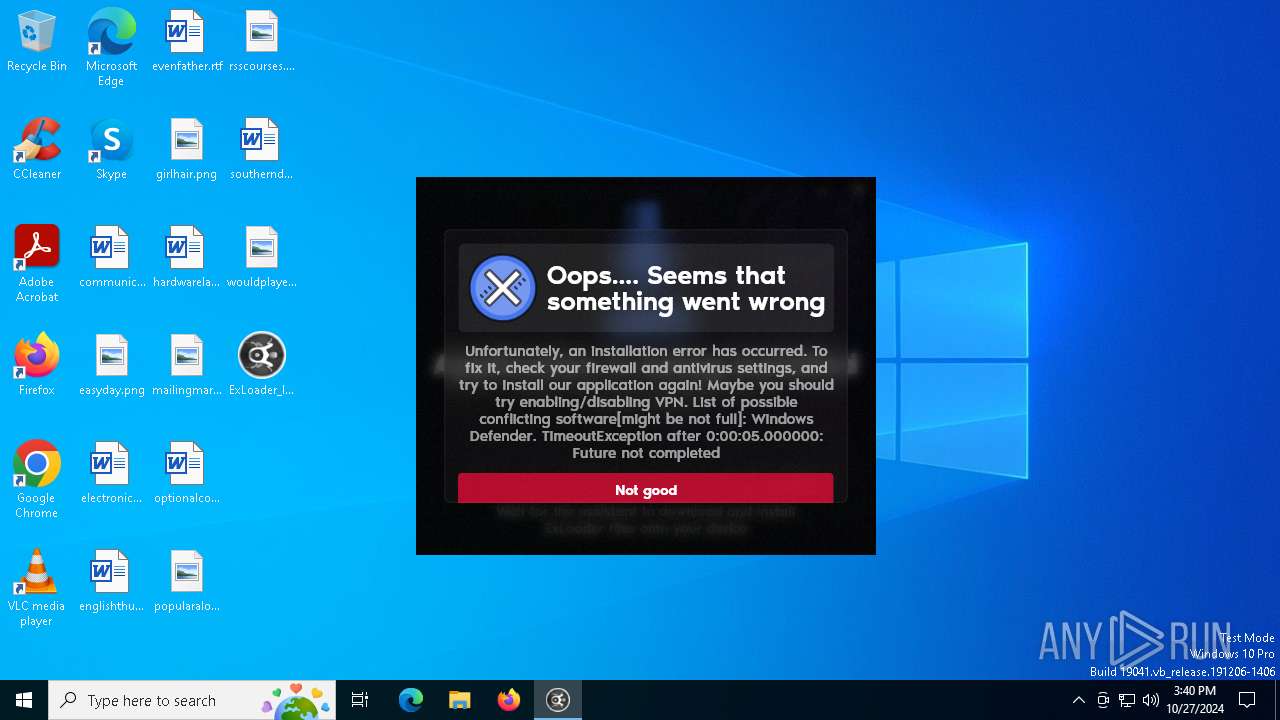
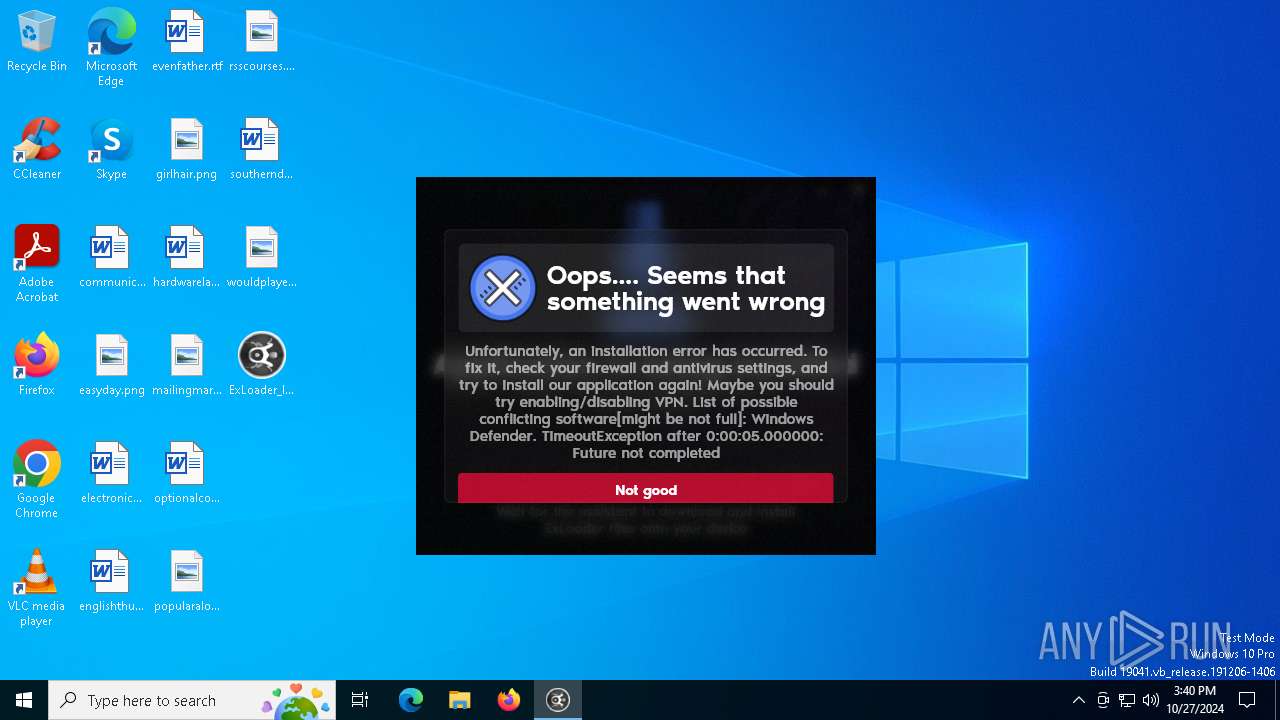
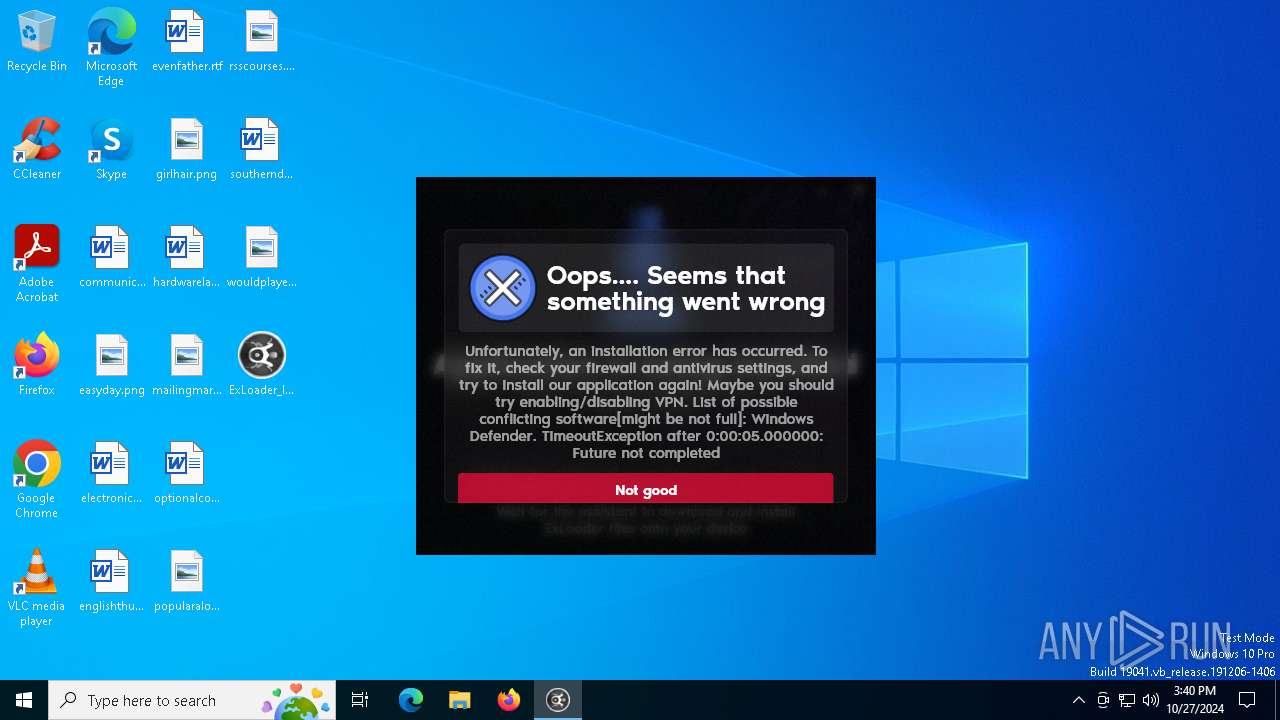
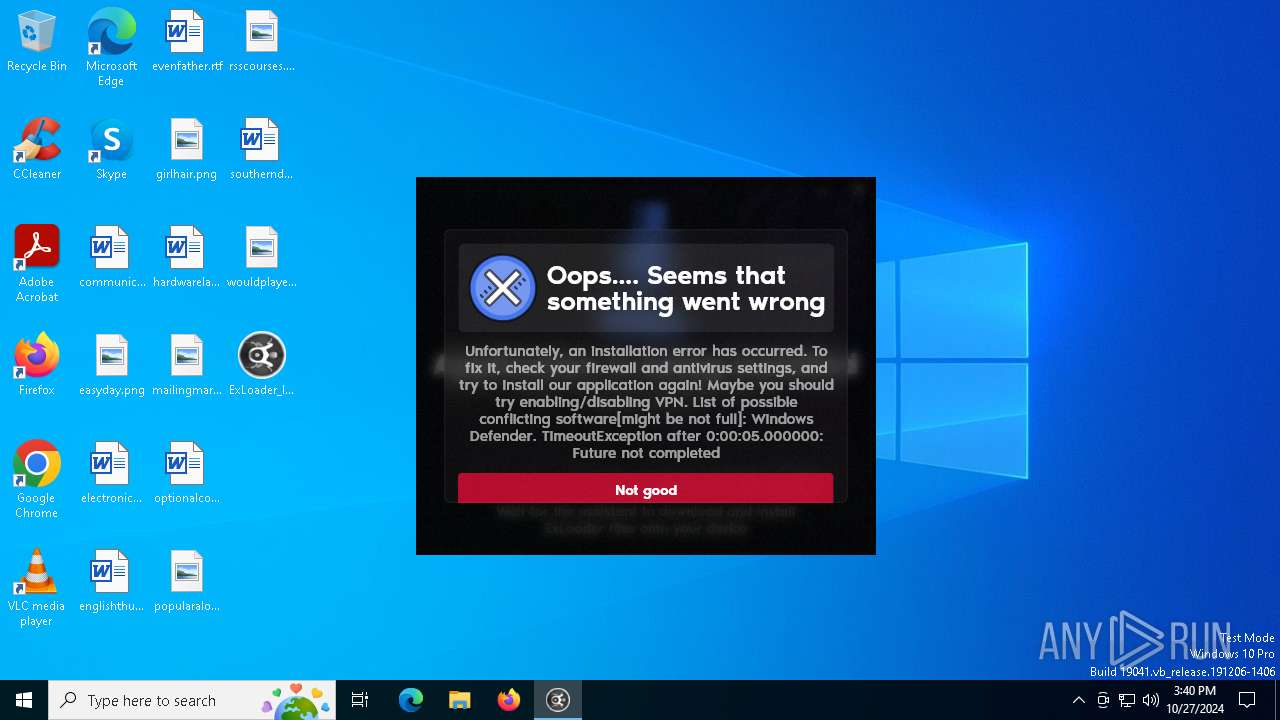
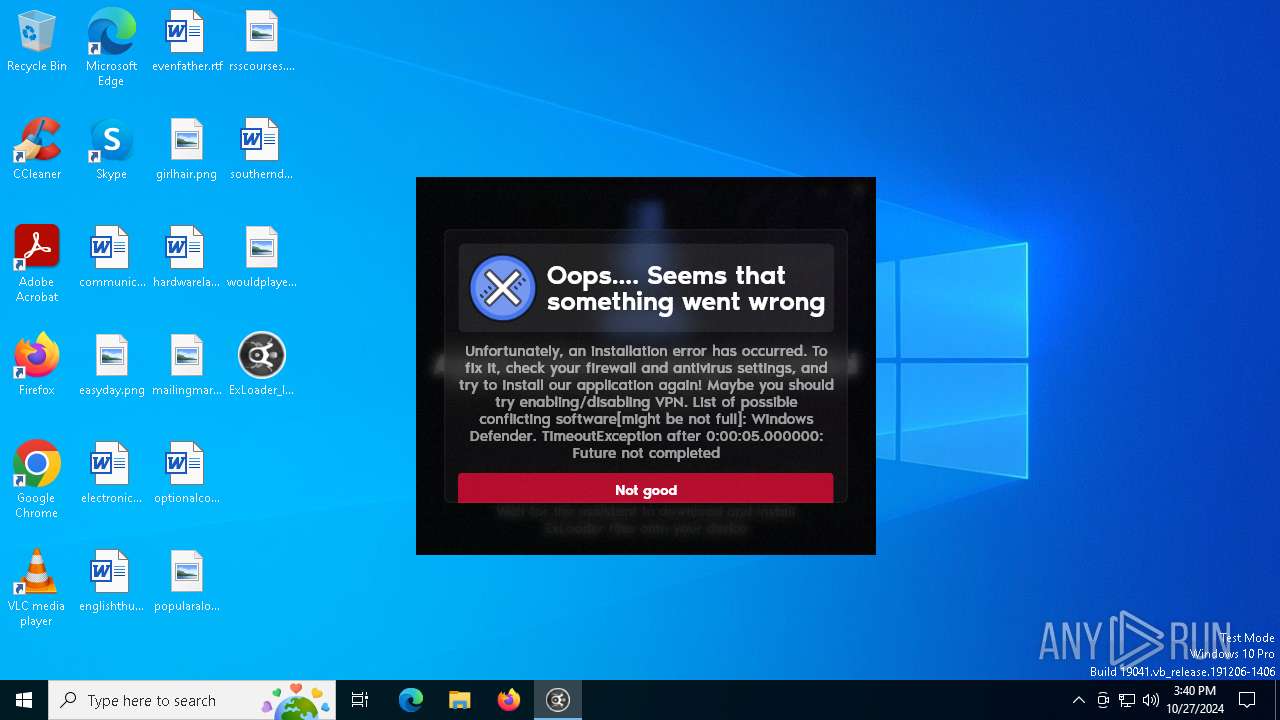
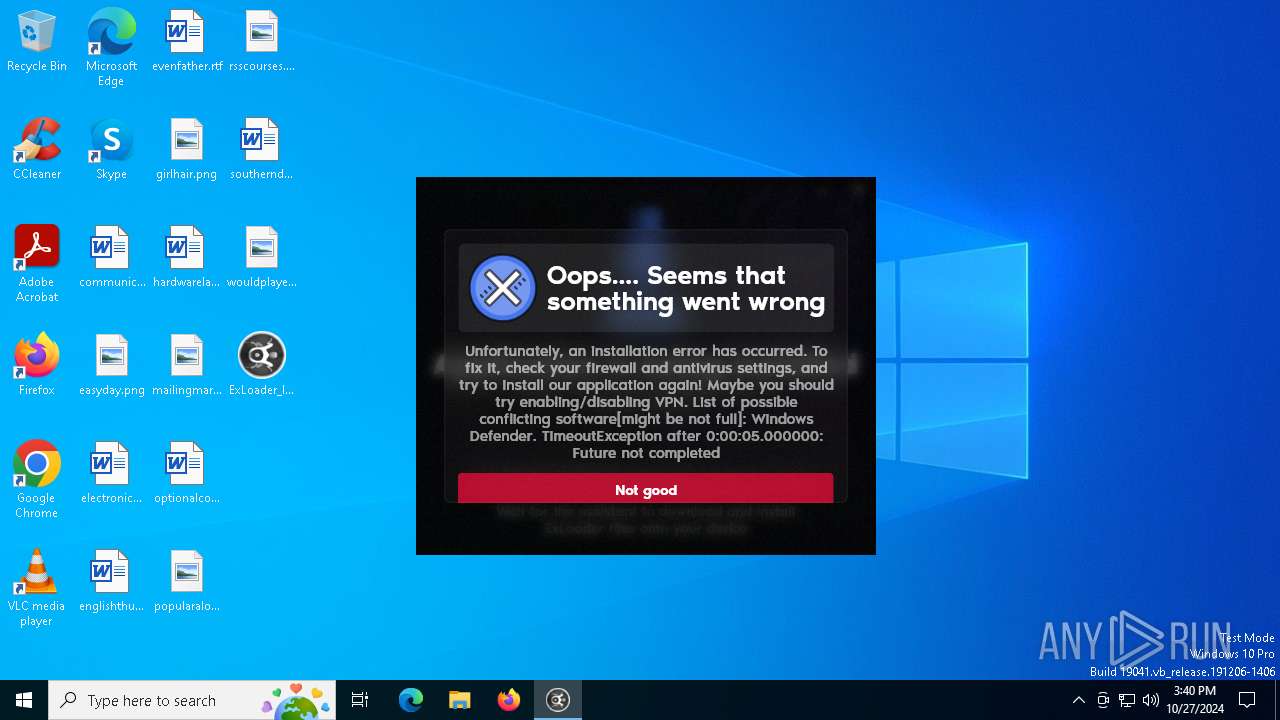
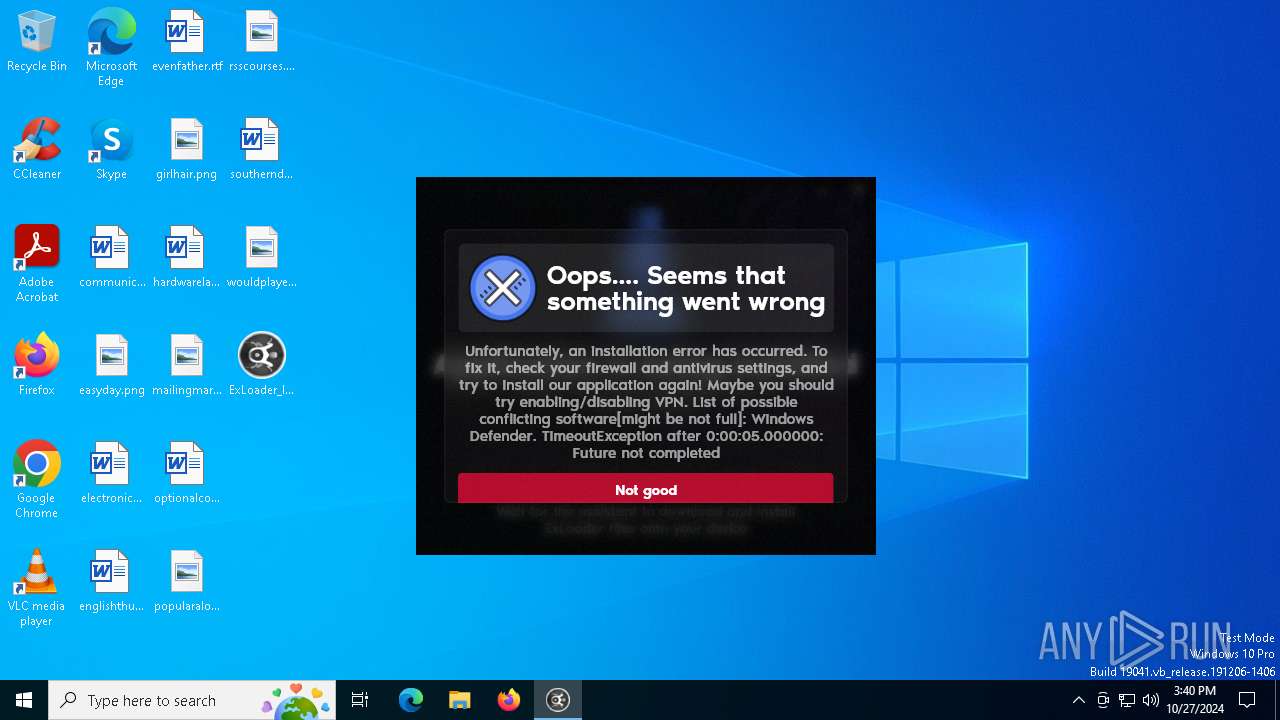
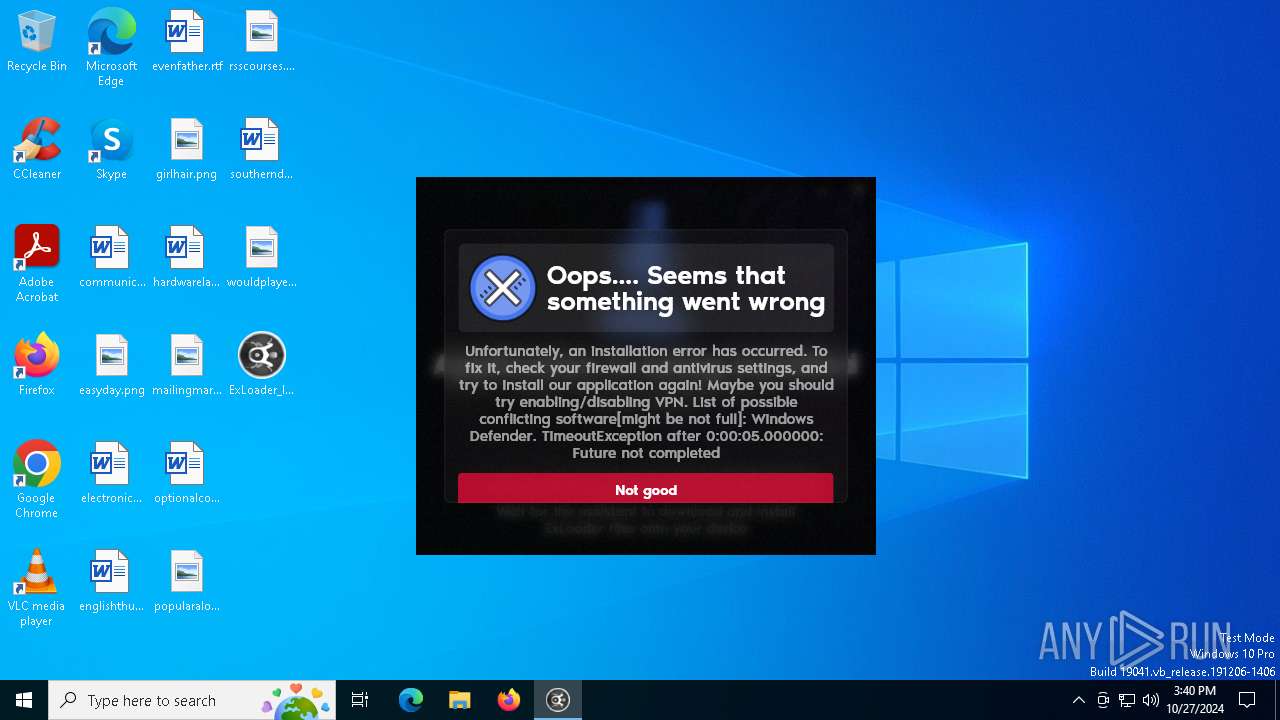
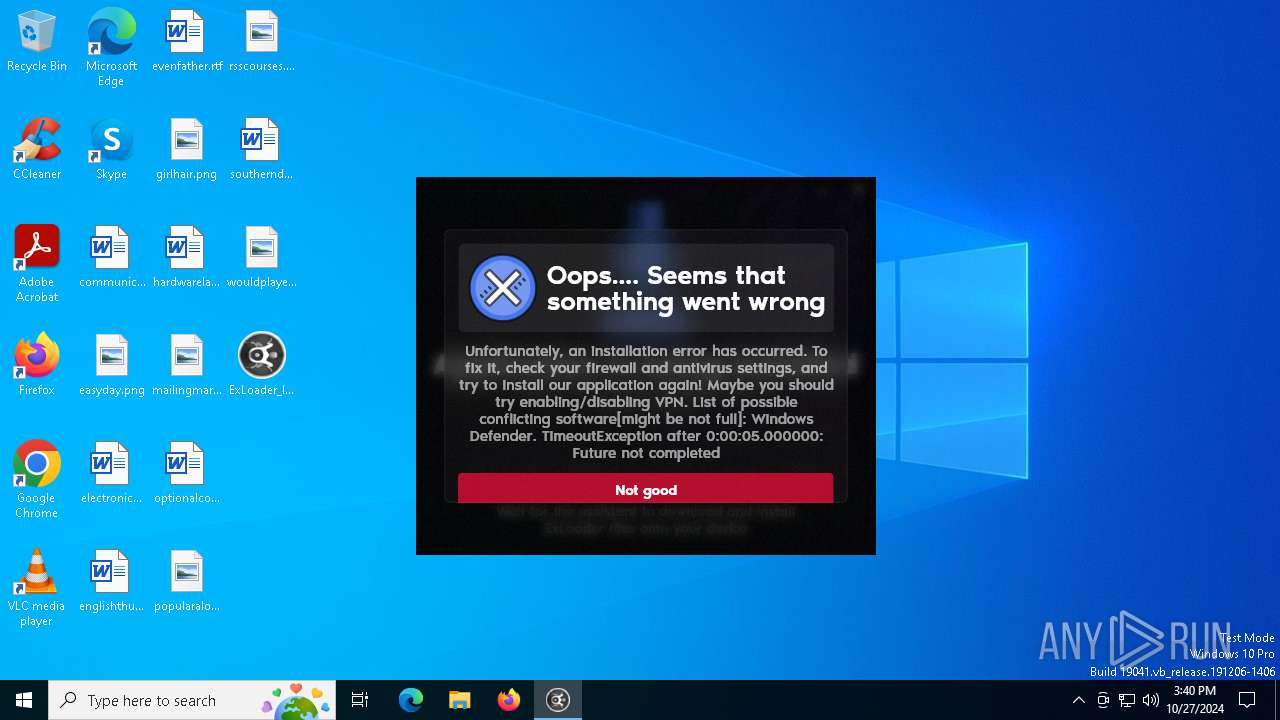
| File name: | ExLoader_Installer.exe |
| Full analysis: | https://app.any.run/tasks/8a6c61b8-5ec1-47b3-8e66-f1713e852c98 |
| Verdict: | Malicious activity |
| Analysis date: | October 27, 2024, 15:38:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 51D5E87AE7BC99D3ACC39DAA20B03431 |
| SHA1: | 7320A8CD779BD18F572422AA53B241FADEAE6A34 |
| SHA256: | 07F61F7C87BDEACFE34388001489136C563F55891D1A7E4481048B0E26E888A4 |
| SSDEEP: | 393216:teNo204poUswQ/1XMaen2YYJLB/AuYpuVo48r4YI:te/nsTpB/AjYhkY |
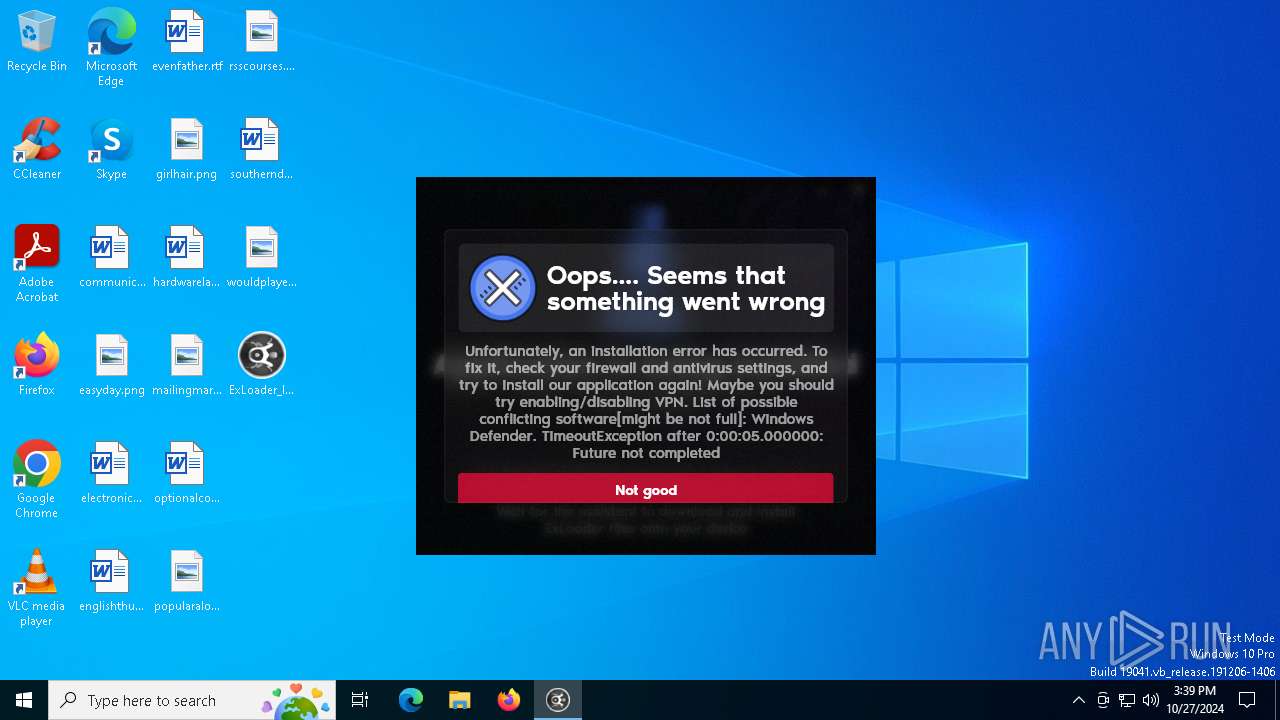
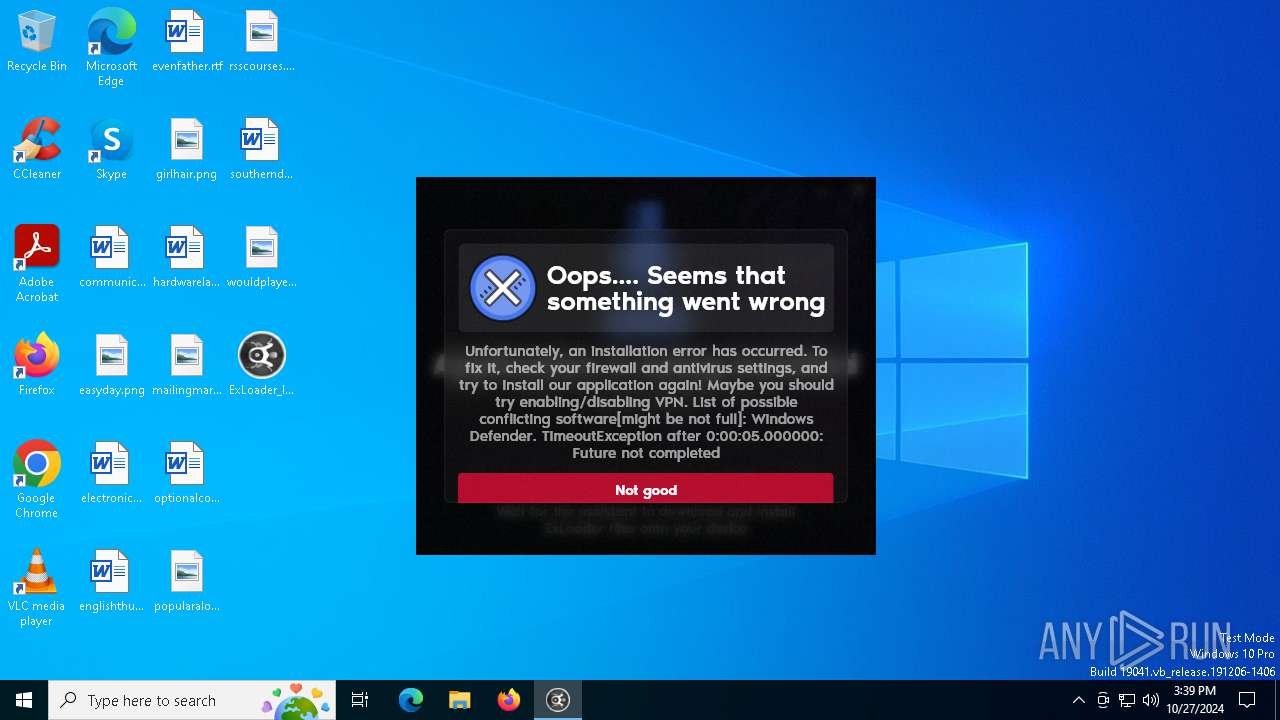
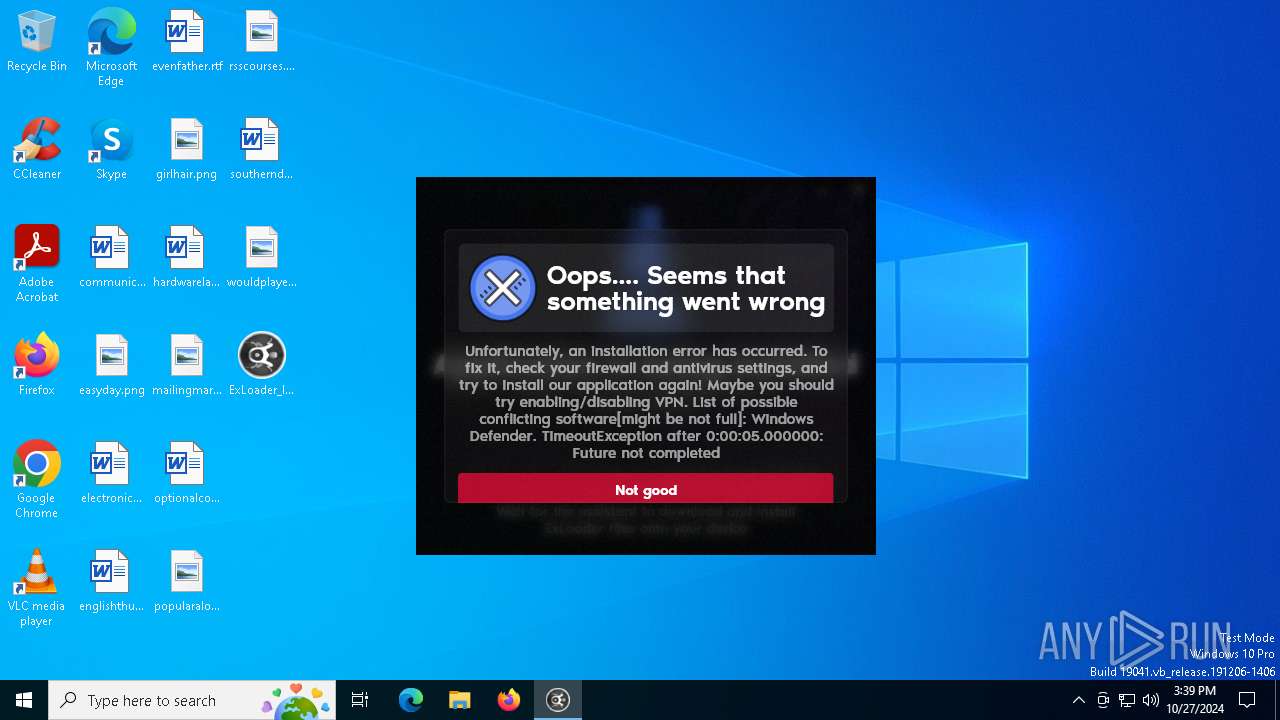
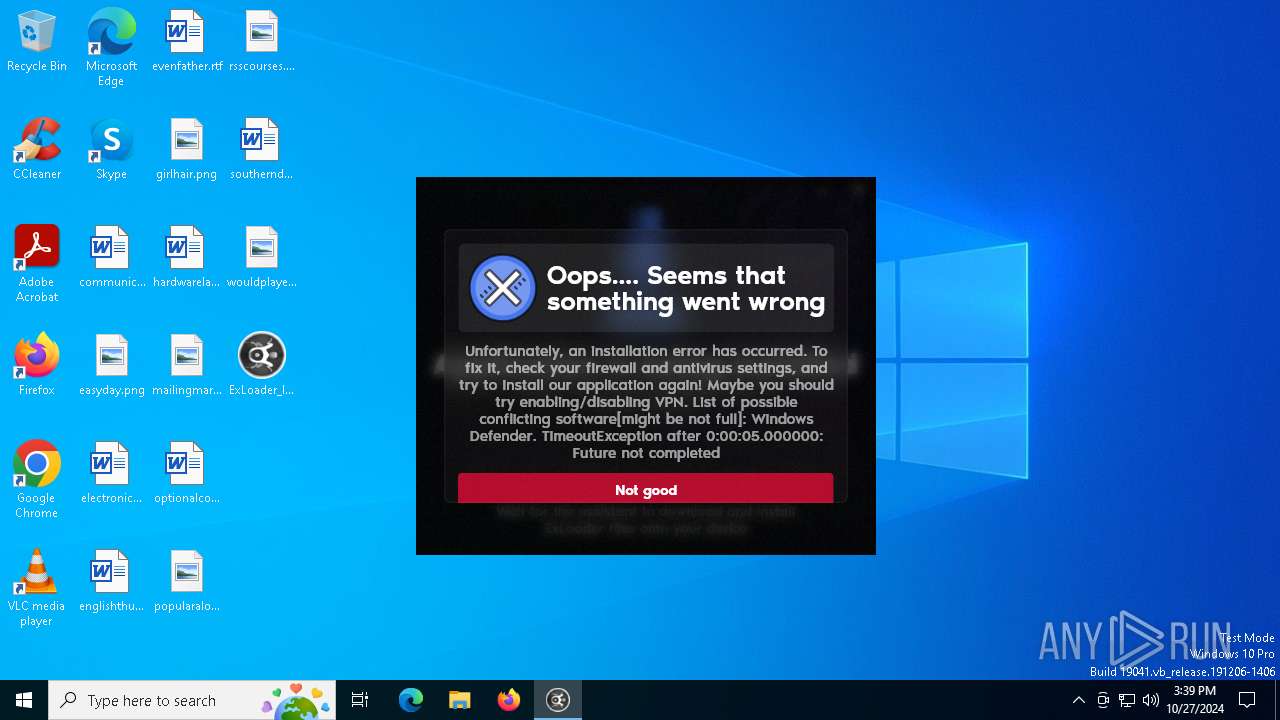
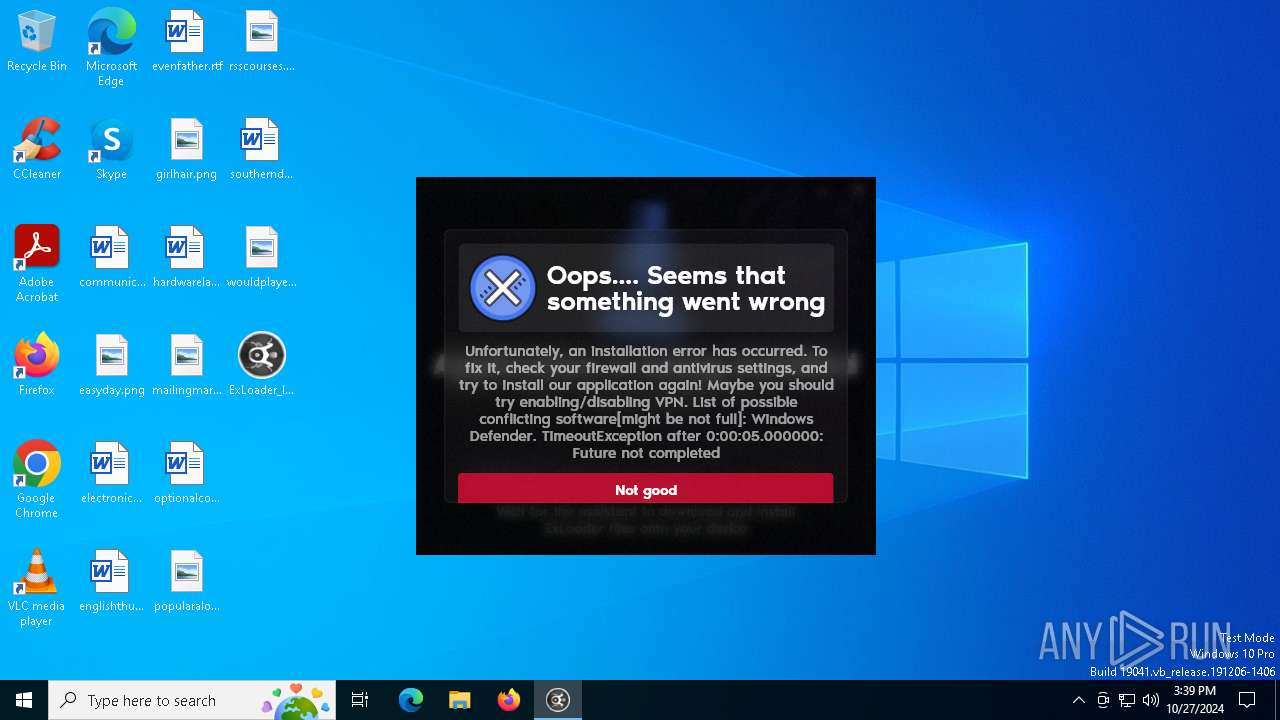
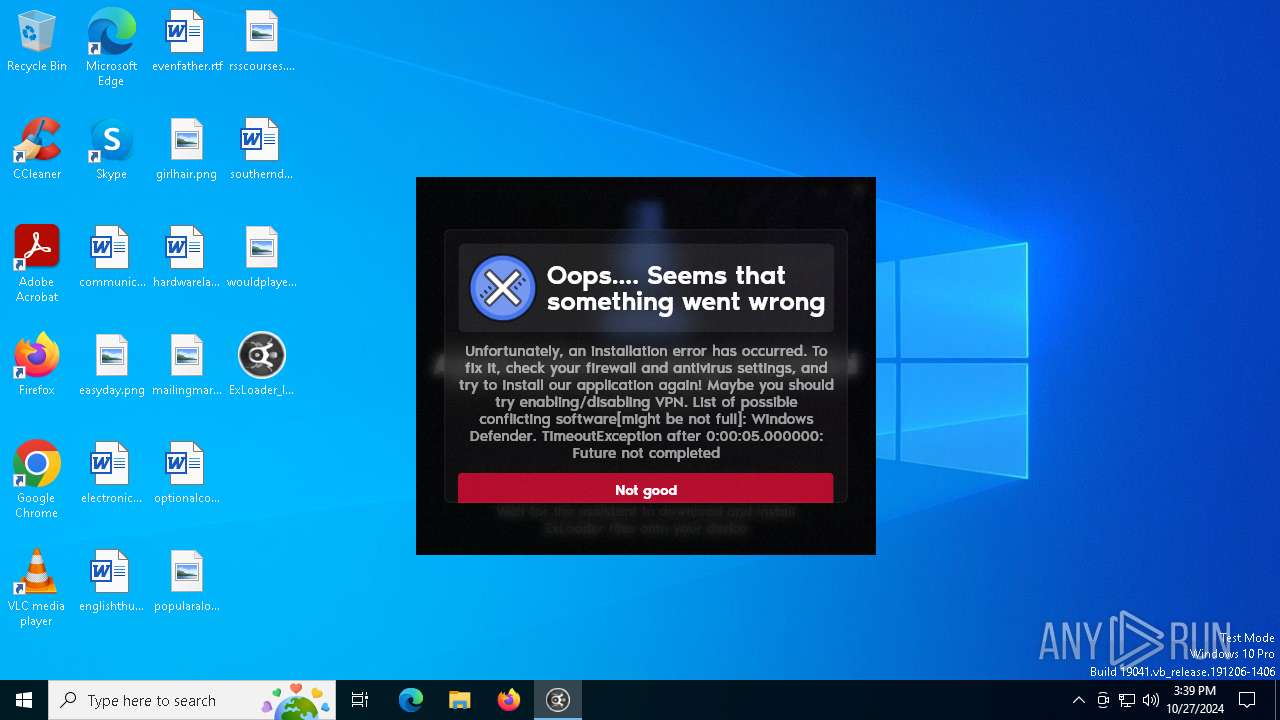
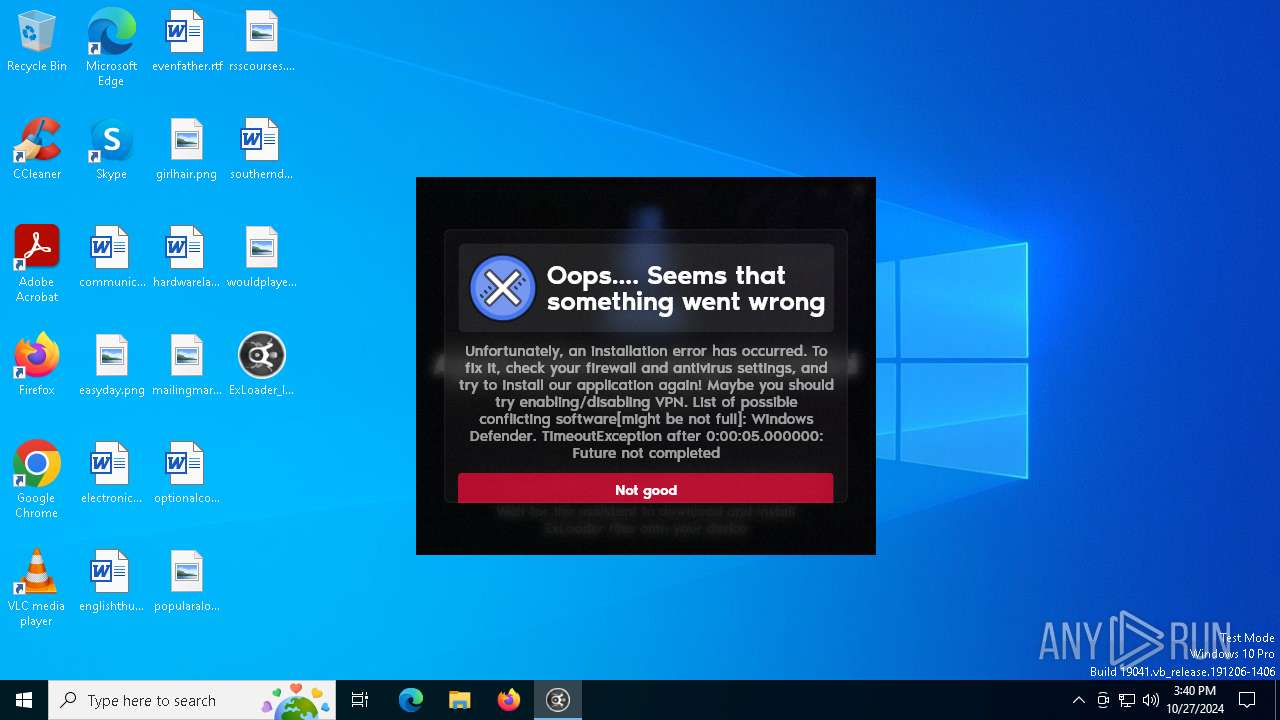
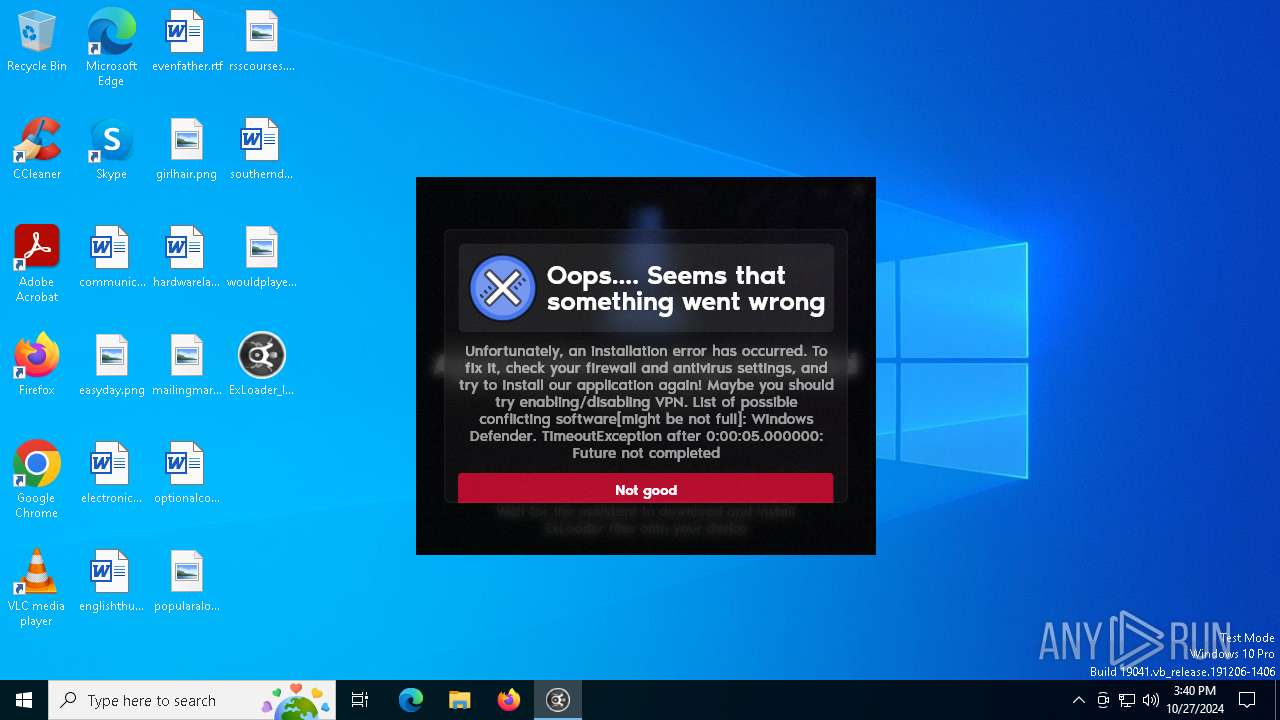
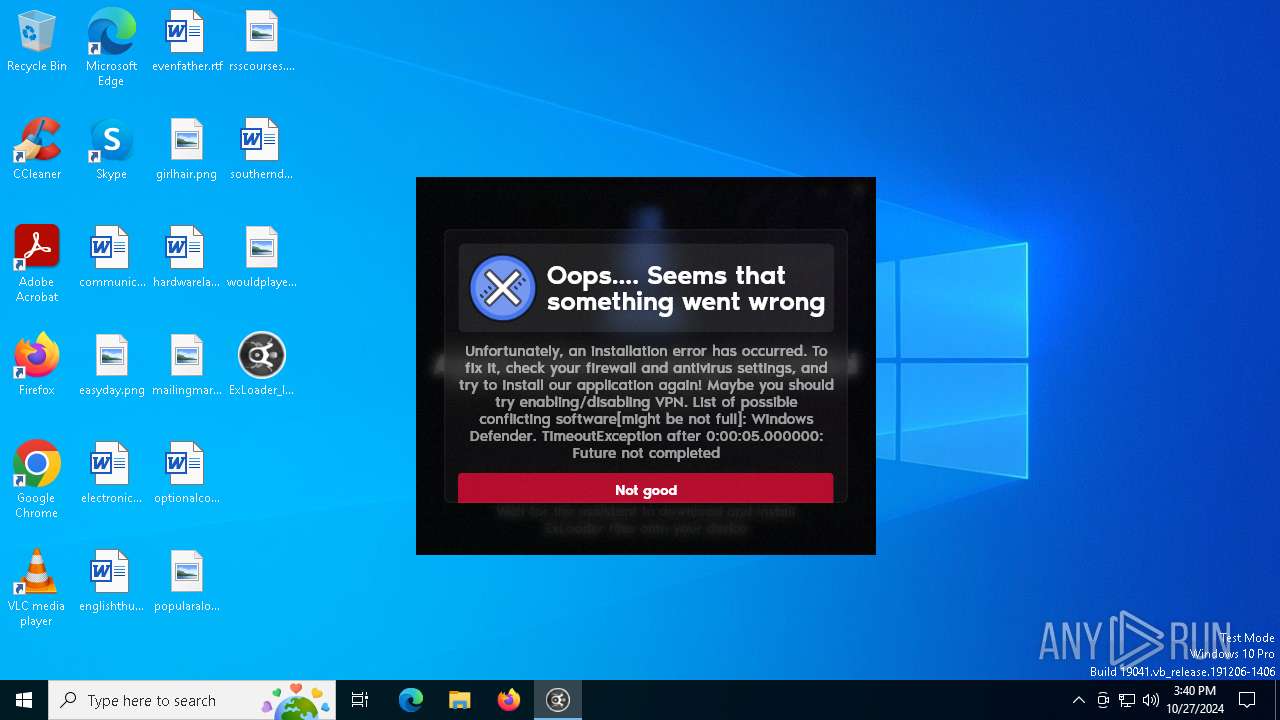
MALICIOUS
Adds path to the Windows Defender exclusion list
- ExLoader_Installer.exe (PID: 6240)
SUSPICIOUS
Process drops legitimate windows executable
- ExLoader_Installer.exe (PID: 3648)
Executable content was dropped or overwritten
- ExLoader_Installer.exe (PID: 3648)
Reads security settings of Internet Explorer
- ExLoader_Installer.exe (PID: 3648)
The process drops C-runtime libraries
- ExLoader_Installer.exe (PID: 3648)
Reads the date of Windows installation
- ExLoader_Installer.exe (PID: 3648)
Starts POWERSHELL.EXE for commands execution
- ExLoader_Installer.exe (PID: 6240)
Script adds exclusion path to Windows Defender
- ExLoader_Installer.exe (PID: 6240)
Uses WMIC.EXE to obtain Windows Installer data
- powershell.exe (PID: 5444)
INFO
Checks supported languages
- ExLoader_Installer.exe (PID: 3648)
- ExLoader_Installer.exe (PID: 6240)
Reads the computer name
- ExLoader_Installer.exe (PID: 3648)
- ExLoader_Installer.exe (PID: 6240)
Create files in a temporary directory
- ExLoader_Installer.exe (PID: 3648)
The process uses the downloaded file
- ExLoader_Installer.exe (PID: 3648)
Process checks computer location settings
- ExLoader_Installer.exe (PID: 3648)
- ExLoader_Installer.exe (PID: 6240)
Creates files in the program directory
- ExLoader_Installer.exe (PID: 6240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2009:08:16 11:05:47+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 9 |
| CodeSize: | 59904 |
| InitializedDataSize: | 128512 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa9ec |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
130
Monitored processes
10
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\Windows\System32\wbem\wmic.exe" /node:localhost /namespace:\\root\SecurityCenter2 path AntiVirusProduct | C:\Windows\System32\wbem\WMIC.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1700 | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -command Add-MpPreference -ExclusionPath "\"C:\Program Files\ExLoader\"" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | ExLoader_Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3648 | "C:\Users\admin\Desktop\ExLoader_Installer.exe" | C:\Users\admin\Desktop\ExLoader_Installer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4808 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5444 | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -command C:\Windows\System32\wbem\wmic.exe /node:localhost /namespace:\\root\SecurityCenter2 path AntiVirusProduct | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | ExLoader_Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6240 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\ExLoader_Installer.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\ExLoader_Installer.exe | ExLoader_Installer.exe | ||||||||||||
User: admin Company: com.swiftsoft Integrity Level: HIGH Description: Installer for unified library of game modifications. Version: 3.5.101+1419 Modules
| |||||||||||||||
| 6792 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\ExLoader_Installer.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\ExLoader_Installer.exe | — | ExLoader_Installer.exe | |||||||||||
User: admin Company: com.swiftsoft Integrity Level: MEDIUM Description: Installer for unified library of game modifications. Exit code: 3221226540 Version: 3.5.101+1419 Modules
| |||||||||||||||
| 6952 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7120 | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -command Add-MpPreference -ExclusionPath "\"C:\Program Files\ExLoader\"" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | ExLoader_Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 333
Read events
18 332
Write events
1
Delete events
0
Modification events
| (PID) Process: | (3648) ExLoader_Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX |
| Operation: | write | Name: | C%%Users%admin%AppData%Local%Temp |
Value: C:\Users\admin\AppData\Local\Temp\RarSFX0 | |||
Executable files
8
Suspicious files
23
Text files
183
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3648 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\data\app.so | — | |
MD5:— | SHA256:— | |||
| 3648 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\data\flutter_assets\resources\audio\CSGO_press.wav | binary | |
MD5:5CF6F422F37B61B16F732E177C4A67CE | SHA256:880CC2BE6F458BF853DBA78CAF06BD2B97BC4B06FEA141599DB74E95BBD59528 | |||
| 3648 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\data\flutter_assets\resources\audio\AbominationPissed_RU.wav | binary | |
MD5:5C4C79FF61BC28F30FC6B2A221975B98 | SHA256:D5F7EA66BB3BC77DE30B0B450B37DBAC1DFA2F30B8108FCE9AC2752CE9AD2838 | |||
| 3648 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\vcruntime140.dll | executable | |
MD5:E9B690FBE5C4B96871214379659DD928 | SHA256:A06C9EA4F815DAC75D2C99684D433FBFC782010FAE887837A03F085A29A217E8 | |||
| 3648 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\data\flutter_assets\AssetManifest.bin | binary | |
MD5:E6EE07A908803B70DCDF31271BBC05BC | SHA256:5BC7D9A70129040CB1A99067D26A8A74F1679B345AE7E7FBD6C71D26A97E2688 | |||
| 3648 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\data\flutter_assets\resources\audio\AbominationPissed_EN.wav | binary | |
MD5:04DE7B1FD5D0FCE157B378EBEDE59DF1 | SHA256:3939FCAA3B0EFD6D601DA475ABEA862D9F7C078643F1063DF51C83609CF47A6F | |||
| 3648 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\data\flutter_assets\NOTICES.Z | compressed | |
MD5:CC8E60C916BE3DA7094842AB562C72AD | SHA256:D091FD114AADC99D4391D279ABC5AC2FABB184AB8BA945E1317551F252C64C50 | |||
| 3648 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\data\flutter_assets\AssetManifest.json | binary | |
MD5:8DAB30C01916D845D7082D8581BA1F7C | SHA256:8F6EE8C6AEE1D574D5C0BBB03E1F3287E8D940514DDA839C80F6C8B124E9494B | |||
| 3648 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\data\flutter_assets\fonts\MaterialIcons-Regular.otf | binary | |
MD5:E7069DFD19B331BE16BED984668FE080 | SHA256:D9865B671A09D683D13A863089D8825E0F61A37696CE5D7D448BC8023AA62453 | |||
| 3648 | ExLoader_Installer.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\data\flutter_assets\resources\audio\CSGO_hover.wav | binary | |
MD5:8D6E22BDE35607FE3801E02FDB12B022 | SHA256:AAA3F0F824D04CE5E93D1DA17873D3AEB3C4D3A8FEE25B7006851E4089BFADFC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
35
DNS requests
18
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 204.79.197.203:443 | https://www.msn.com/en-us/weather/forecast | unknown | html | 350 Kb | whitelisted |
— | — | GET | 200 | 142.250.185.100:443 | https://www.google.com/search?q=weather&hl=en&sclient=gws-wiz&uact=5 | unknown | html | 157 Kb | whitelisted |
— | — | GET | 200 | 212.82.100.137:443 | https://search.yahoo.com/search?p=weather&fr=yfp-t&&ei=UTF-8&fp=1 | unknown | binary | 200 Kb | whitelisted |
— | — | GET | 200 | 213.180.193.146:443 | https://meteum.ai/weather/en-US | unknown | html | 580 Kb | unknown |
— | — | GET | 200 | 104.21.16.53:443 | https://data.exloader.net/ExLoader.zip | unknown | compressed | 45.1 Mb | unknown |
— | — | GET | 302 | 213.180.193.146:443 | https://meteum.ai/ | unknown | text | 14 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.209.161:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6944 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
meteum.ai |
| unknown |
www.google.com |
| whitelisted |
www.msn.com |
| whitelisted |
search.yahoo.com |
| whitelisted |
data.exloader.net |
| unknown |
Threats
14 ETPRO signatures available at the full report