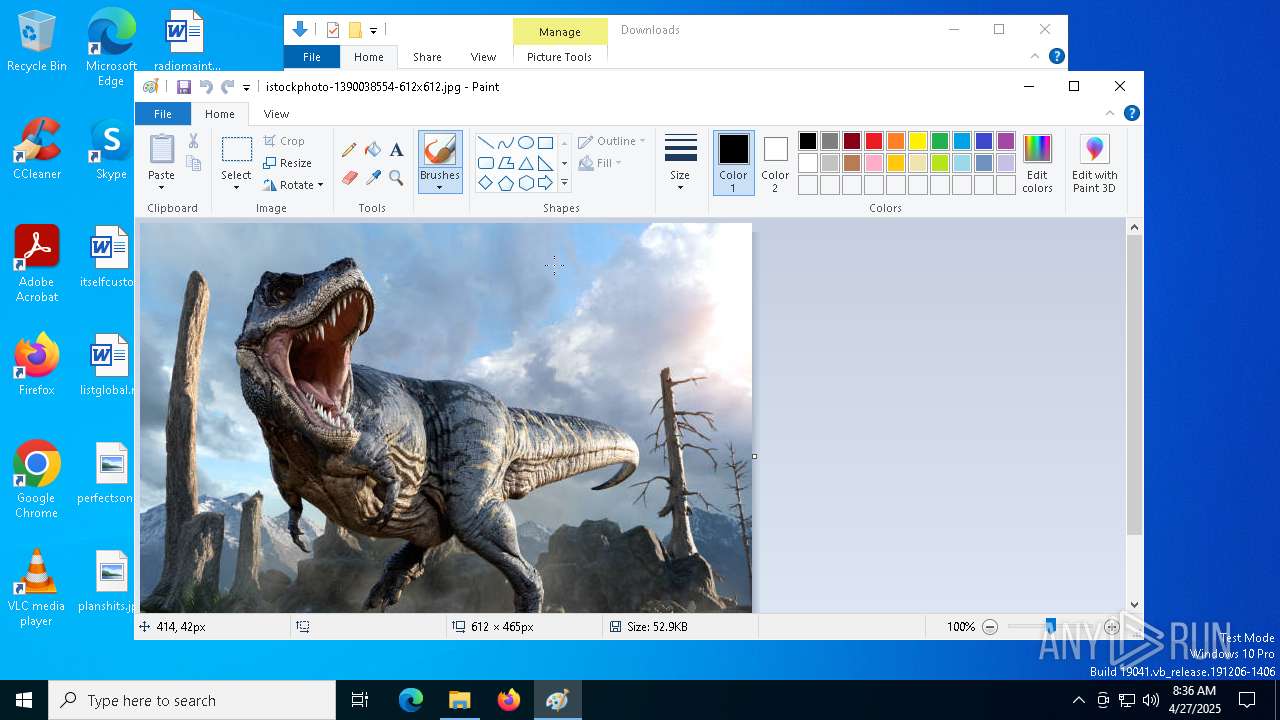
| File name: | istockphoto-1390038554-612x612.jpg |
| Full analysis: | https://app.any.run/tasks/b178c889-dd18-4405-8625-3e451281dbf0 |
| Verdict: | Malicious activity |
| Analysis date: | April 27, 2025, 08:34:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | image/jpeg |
| File info: | JPEG image data, JFIF standard 1.01, resolution (DPI), density 300x300, segment length 16, Exif Standard: [TIFF image data, little-endian, direntries=3, description=Tyrannosaurus from the Cretaceous era 3D illustration,\001, xresolution=103, yresolution=111], progressive, precision 8, 612x465, components 3 |
| MD5: | 220A2CDC0FD157A22B356161750B9CB2 |
| SHA1: | D52CC03E652037C5E34336FA22BC3E4897BD39F0 |
| SHA256: | 07E5214AB3252AE7DDF79152C4958746EFA4BCBF3C15224376D9FE54218AAEB7 |
| SSDEEP: | 1536:RA1WBFHM71mAX2djkolrI196muZ7cU6d0O:OWBFHM7AAGdZWjo7cU6P |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- powershell.exe (PID: 3240)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 5112)
SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 3240)
Executes script without checking the security policy
- powershell.exe (PID: 3240)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- mshta.exe (PID: 6808)
Creates an object to access WMI (SCRIPT)
- mshta.exe (PID: 6808)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 3240)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 3240)
INFO
Checks proxy server information
- mshta.exe (PID: 6808)
- powershell.exe (PID: 5112)
Reads Internet Explorer settings
- mshta.exe (PID: 6808)
Creates or changes the value of an item property via Powershell
- powershell.exe (PID: 3240)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3240)
- powershell.exe (PID: 5112)
Disables trace logs
- powershell.exe (PID: 5112)
Manual execution by a user
- msedge.exe (PID: 2420)
- mspaint.exe (PID: 472)
Reads the software policy settings
- slui.exe (PID: 1228)
Checks supported languages
- identity_helper.exe (PID: 7748)
- identity_helper.exe (PID: 7948)
Reads Environment values
- identity_helper.exe (PID: 7748)
- identity_helper.exe (PID: 7948)
Application launched itself
- msedge.exe (PID: 2420)
- msedge.exe (PID: 776)
Reads the computer name
- identity_helper.exe (PID: 7748)
- identity_helper.exe (PID: 7948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jpg | | | JFIF-EXIF JPEG Bitmap (38.4) |
|---|---|---|
| .jpg | | | JFIF JPEG bitmap (30.7) |
| .jpg | | | JPEG bitmap (23) |
| .mp3 | | | MP3 audio (7.6) |
EXIF
JFIF
| JFIFVersion: | 1.01 |
|---|---|
| ResolutionUnit: | inches |
| XResolution: | 300 |
| YResolution: | 300 |
EXIF
| ImageDescription: | Tyrannosaurus from the Cretaceous era 3D illustration |
|---|---|
| XResolution: | 300 |
| YResolution: | 300 |
XMP
| Credit: | Getty Images/iStockphoto |
|---|---|
| AssetID: | 1390038554 |
| WebStatement: | https://www.istockphoto.com/legal/license-agreement?utm_medium=organic&utm_source=google&utm_campaign=iptcurl |
| DataMining: | Prohibited except for search engine indexing |
| Creator: | Warpaintcobra |
| Description: | Tyrannosaurus from the Cretaceous era 3D illustration |
| LicensorURL: | https://www.istockphoto.com/photo/license-gm1390038554-?utm_medium=organic&utm_source=google&utm_campaign=iptcurl |
IPTC
| By-line: | Warpaintcobra |
|---|---|
| Caption-Abstract: | Tyrannosaurus from the Cretaceous era 3D illustration |
| Credit: | Getty Images/iStockphoto |
Composite
| ImageSize: | 612x465 |
|---|---|
| Megapixels: | 0.285 |
Total processes
200
Monitored processes
66
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Downloads\istockphoto-1390038554-612x612.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --no-appcompat-clear --mojo-platform-channel-handle=6068 --field-trial-handle=2360,i,5090940869496674985,2731578998464836514,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 632 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5320 --field-trial-handle=2320,i,9945706264552504112,3130344969678927858,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 776 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 976 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2356 --field-trial-handle=2360,i,5090940869496674985,2731578998464836514,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2308 --field-trial-handle=2320,i,9945706264552504112,3130344969678927858,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1228 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --mojo-platform-channel-handle=5208 --field-trial-handle=2320,i,9945706264552504112,3130344969678927858,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1660 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3508 --field-trial-handle=2360,i,5090940869496674985,2731578998464836514,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2096 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4308 --field-trial-handle=2360,i,5090940869496674985,2731578998464836514,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
20 793
Read events
20 717
Write events
75
Delete events
1
Modification events
| (PID) Process: | (6808) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6808) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6808) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5112) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5112) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5112) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5112) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5112) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5112) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5112) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
47
Suspicious files
750
Text files
162
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hb4rpsuk.zge.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6808 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:4B9F44793CEF5A59003F828373FF45AD | SHA256:B1C78036F3B862D37AAC11E8C54F35BC0DB08E2EDDEDCC4CE98F7E6FDE5485EA | |||
| 6808 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:9ED263ECFB6A4EFD335C2D736A1DE037 | SHA256:58448A801962742E37BC8CF395AF112AE51B9587EC5980E5EEE98BCF1DC1459B | |||
| 3240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_b12fqujk.rht.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6808 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\i1st[1].tmp | binary | |
MD5:4FA0A17740E95559FEC58ADBB2C1F0CB | SHA256:5A7F72BFCC8CBED465C67254A83AF7FCAC9CEC5126BAFDBFA95B4160439FA2BE | |||
| 6808 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:1FBB37F79B317A9A248E7C4CE4F5BAC5 | SHA256:9BF639C595FE335B6F694EE35990BEFD2123F5E07FD1973FF619E3FC88F5F49F | |||
| 2420 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF119008.TMP | — | |
MD5:— | SHA256:— | |||
| 2420 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF119008.TMP | — | |
MD5:— | SHA256:— | |||
| 2420 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF119008.TMP | — | |
MD5:— | SHA256:— | |||
| 2420 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF119008.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
130
DNS requests
130
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7660 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1746053247&P2=404&P3=2&P4=n0RgAVEHvLRZxg64ZnjFGYVwEBwZ2lnOl%2bok5HLZ1sNPMRLMG7SpnJnANu5rGxI0zCCGrWmELOrbyWa64SXeGA%3d%3d | unknown | — | — | whitelisted |
7660 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1746053247&P2=404&P3=2&P4=n0RgAVEHvLRZxg64ZnjFGYVwEBwZ2lnOl%2bok5HLZ1sNPMRLMG7SpnJnANu5rGxI0zCCGrWmELOrbyWa64SXeGA%3d%3d | unknown | — | — | whitelisted |
7660 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1746053247&P2=404&P3=2&P4=n0RgAVEHvLRZxg64ZnjFGYVwEBwZ2lnOl%2bok5HLZ1sNPMRLMG7SpnJnANu5rGxI0zCCGrWmELOrbyWa64SXeGA%3d%3d | unknown | — | — | whitelisted |
7660 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1746053247&P2=404&P3=2&P4=n0RgAVEHvLRZxg64ZnjFGYVwEBwZ2lnOl%2bok5HLZ1sNPMRLMG7SpnJnANu5rGxI0zCCGrWmELOrbyWa64SXeGA%3d%3d | unknown | — | — | whitelisted |
7660 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1746053247&P2=404&P3=2&P4=n0RgAVEHvLRZxg64ZnjFGYVwEBwZ2lnOl%2bok5HLZ1sNPMRLMG7SpnJnANu5rGxI0zCCGrWmELOrbyWa64SXeGA%3d%3d | unknown | — | — | whitelisted |
7660 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1746053247&P2=404&P3=2&P4=n0RgAVEHvLRZxg64ZnjFGYVwEBwZ2lnOl%2bok5HLZ1sNPMRLMG7SpnJnANu5rGxI0zCCGrWmELOrbyWa64SXeGA%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6808 | mshta.exe | GET | 200 | 142.250.186.67:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6808 | mshta.exe | GET | 200 | 142.250.186.67:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6808 | mshta.exe | 104.21.32.1:443 | zeniva.ws | CLOUDFLARENET | — | unknown |
6808 | mshta.exe | 142.250.186.67:80 | c.pki.goog | GOOGLE | US | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
zeniva.ws |
| unknown |
c.pki.goog |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
q.cylinderacronym.top |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
5112 | powershell.exe | Potentially Bad Traffic | ET HUNTING Request to .TOP Domain with Minimal Headers |
5112 | powershell.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |