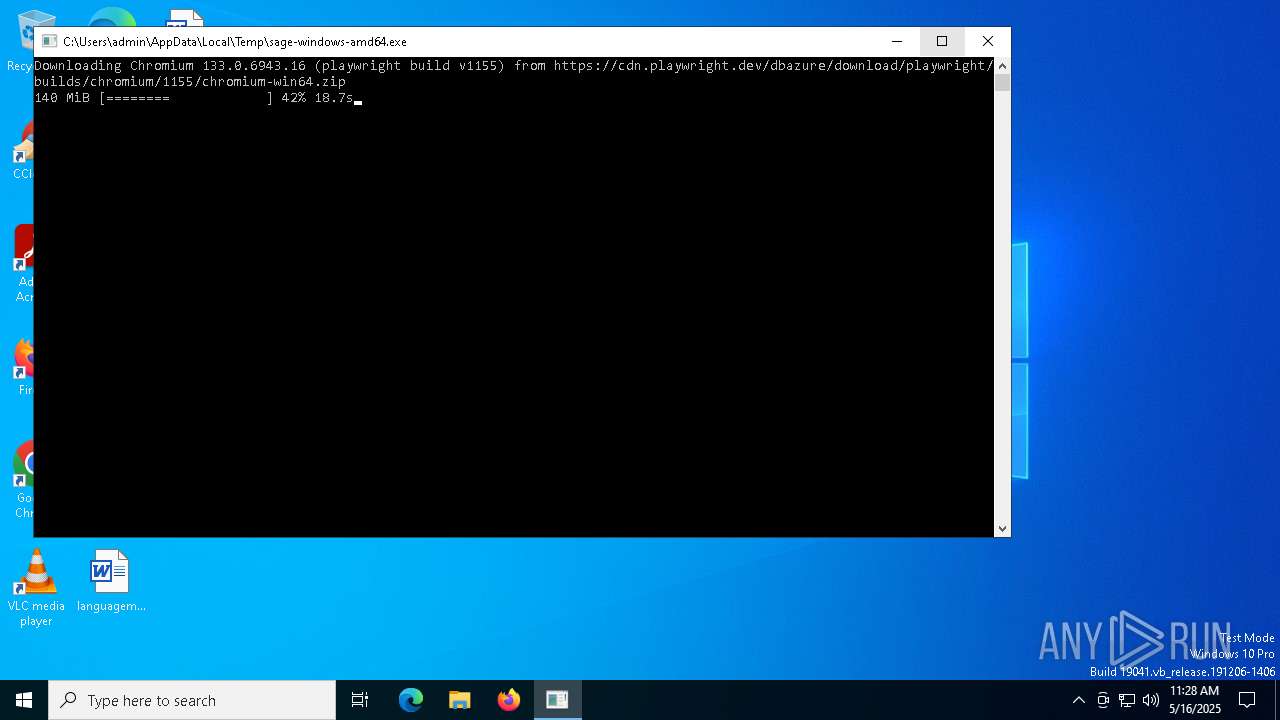
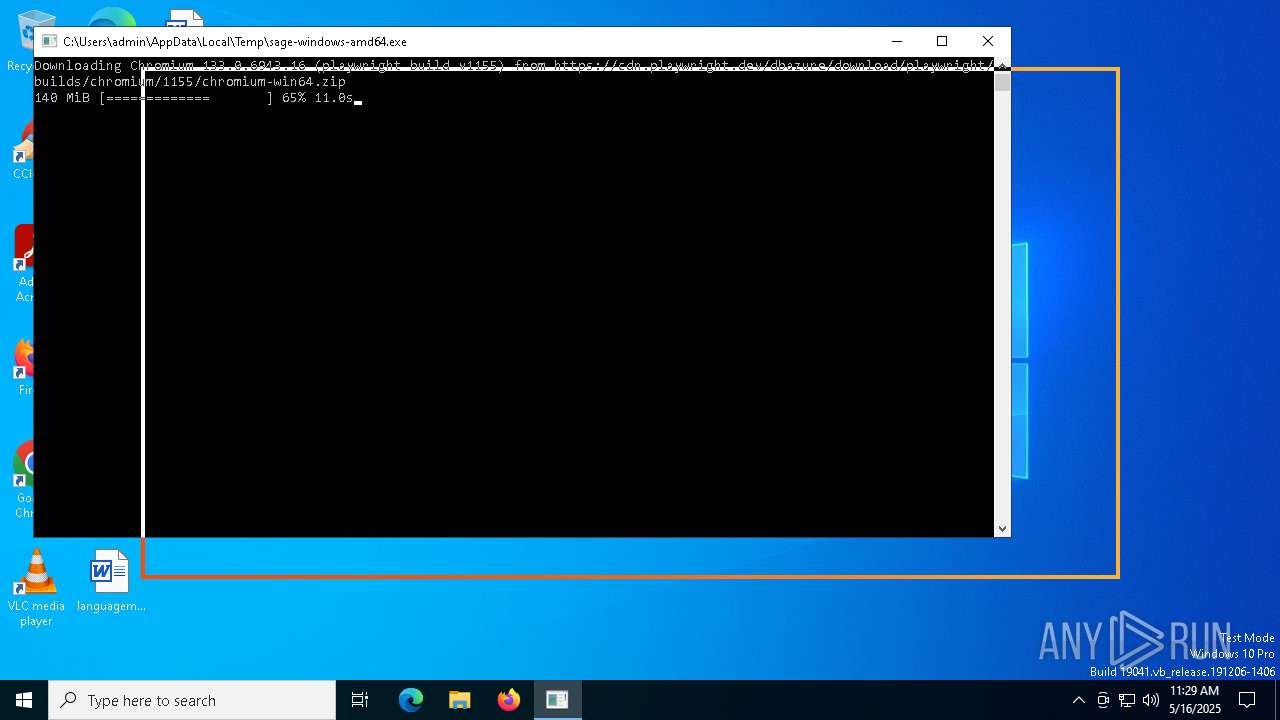
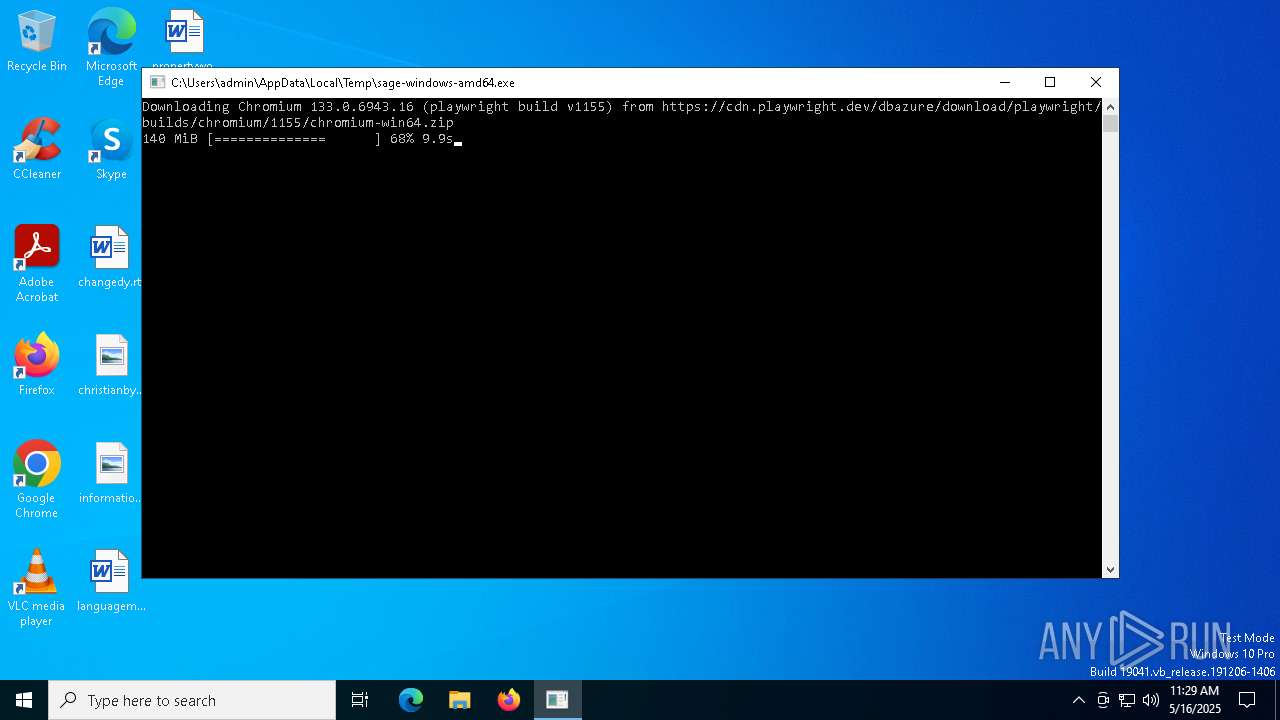
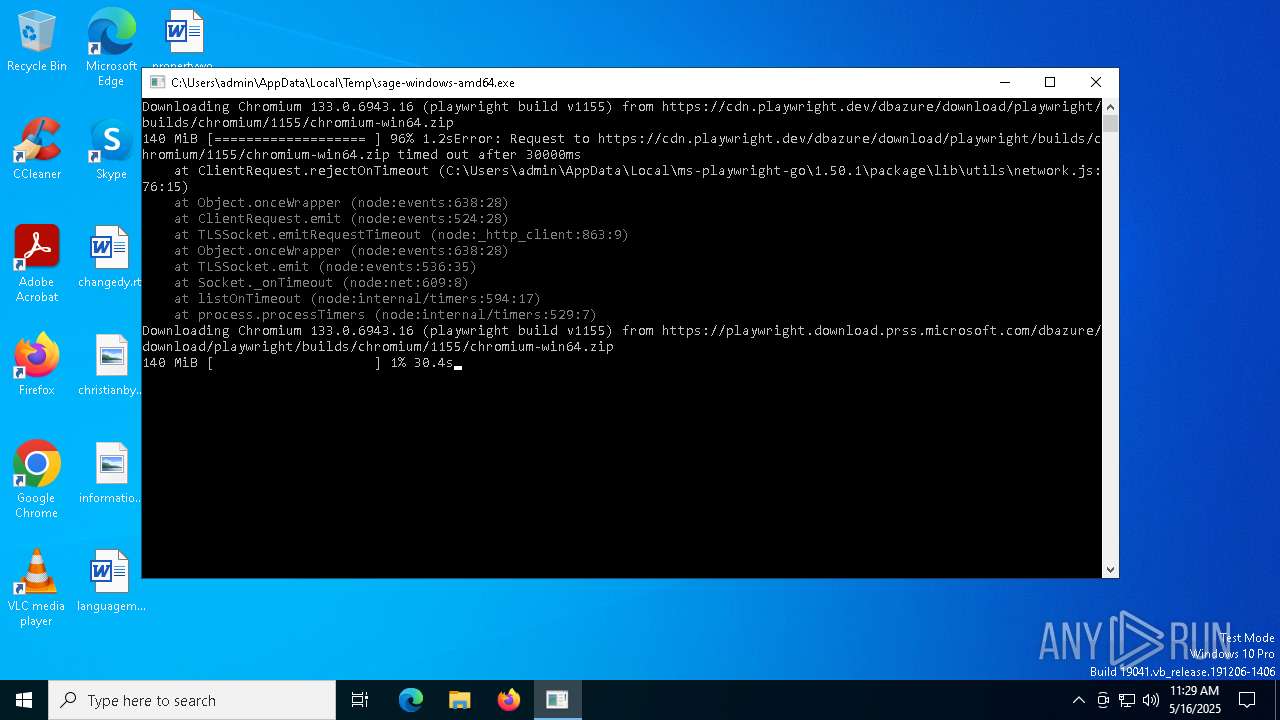
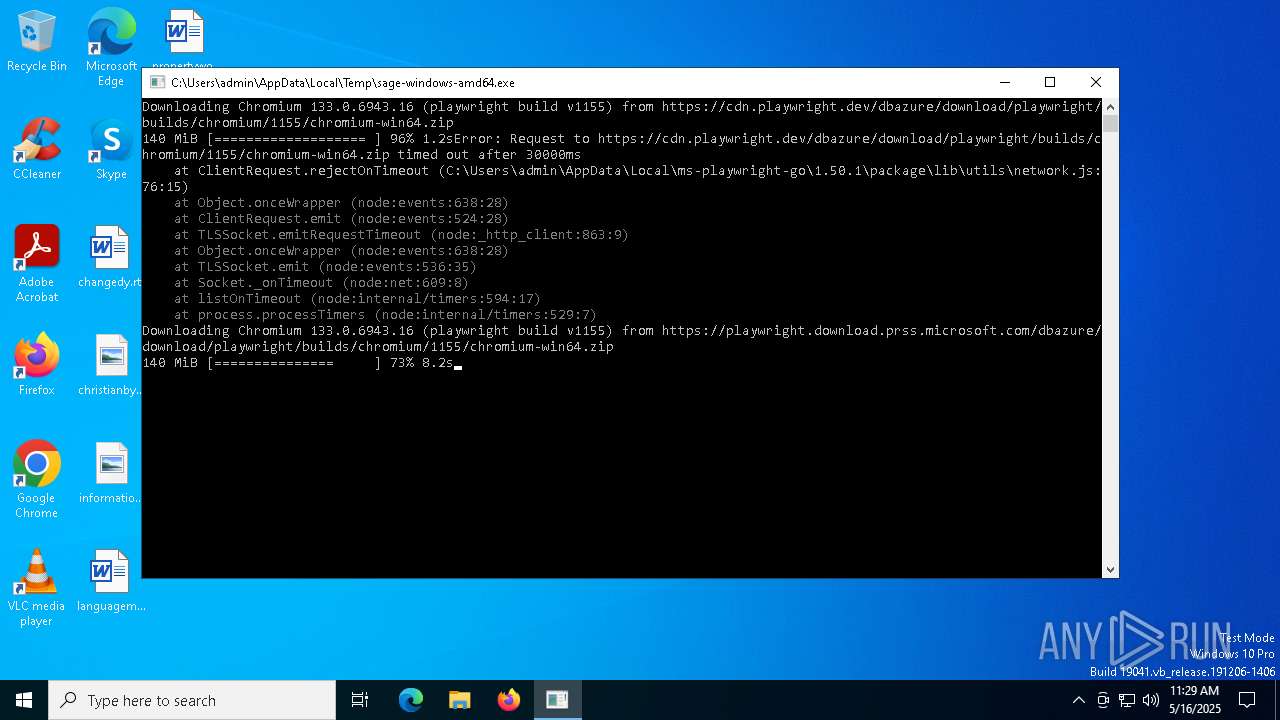
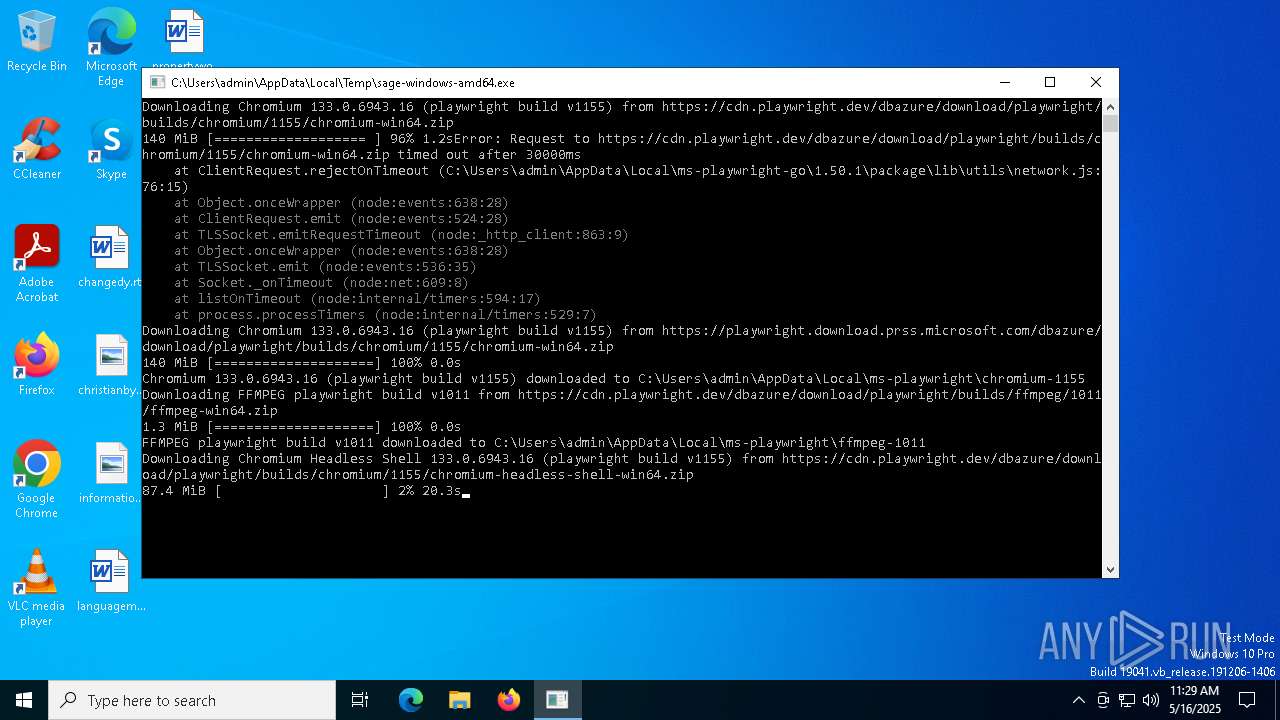
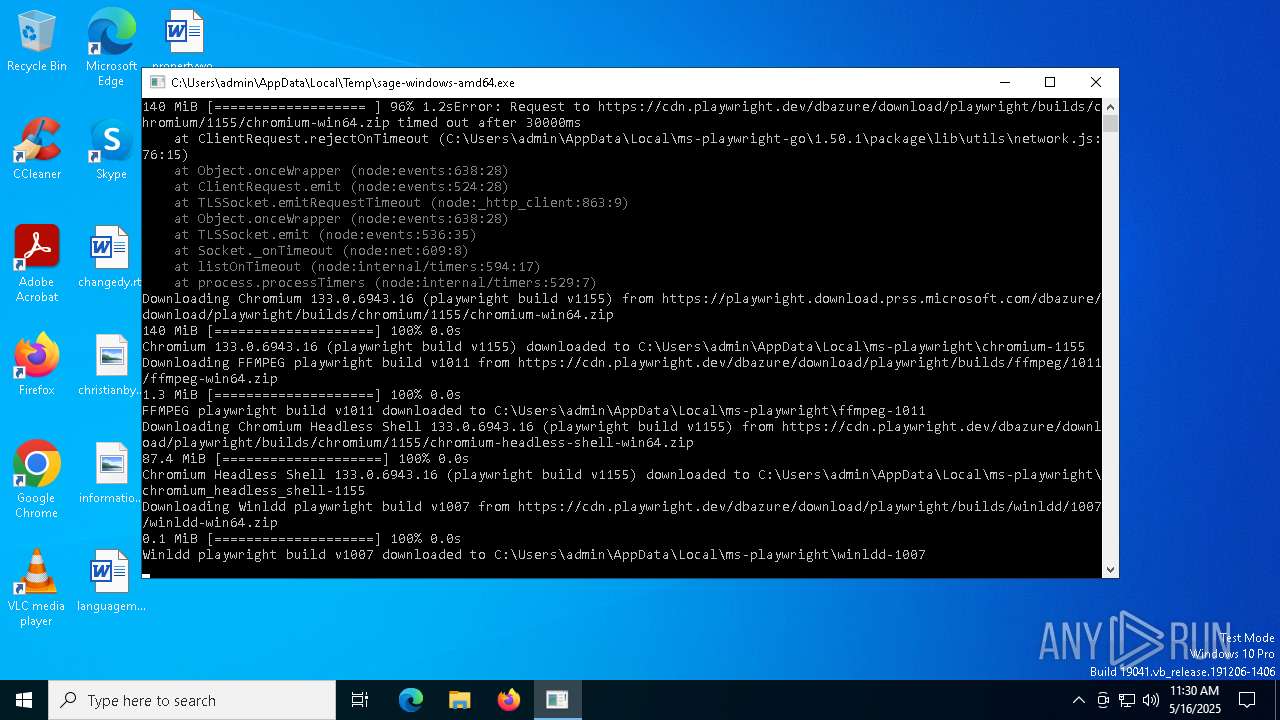
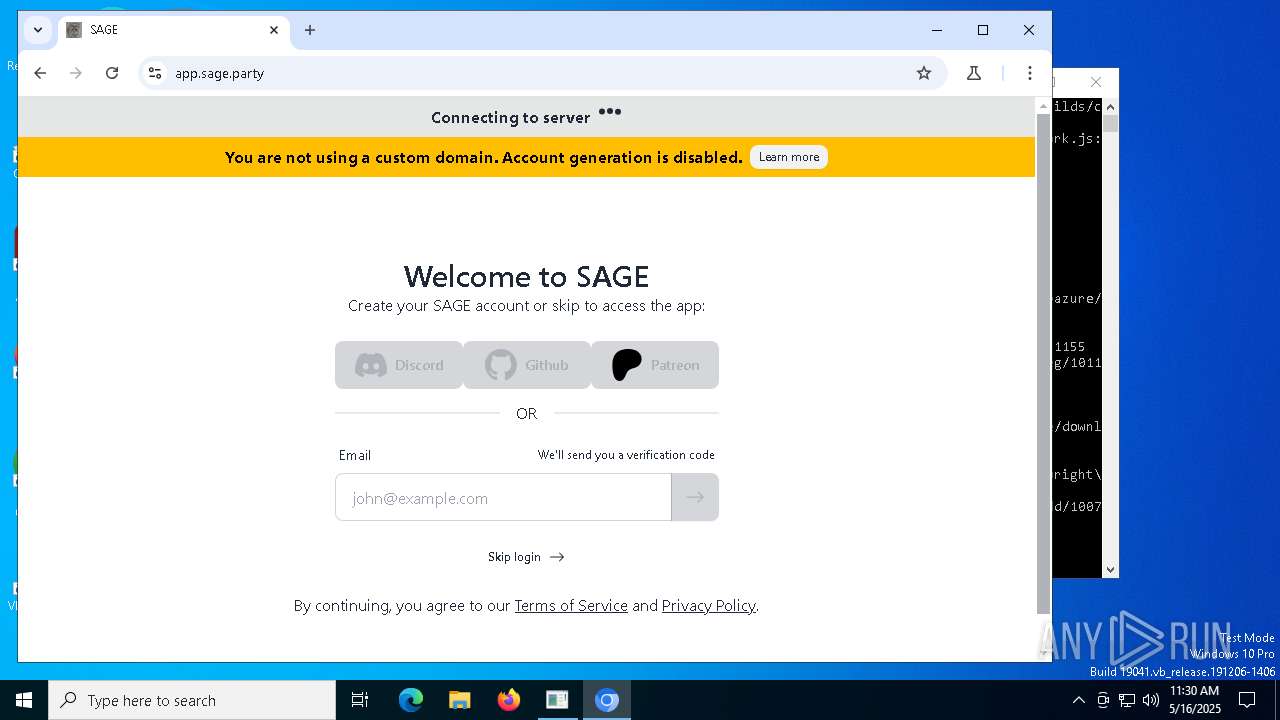
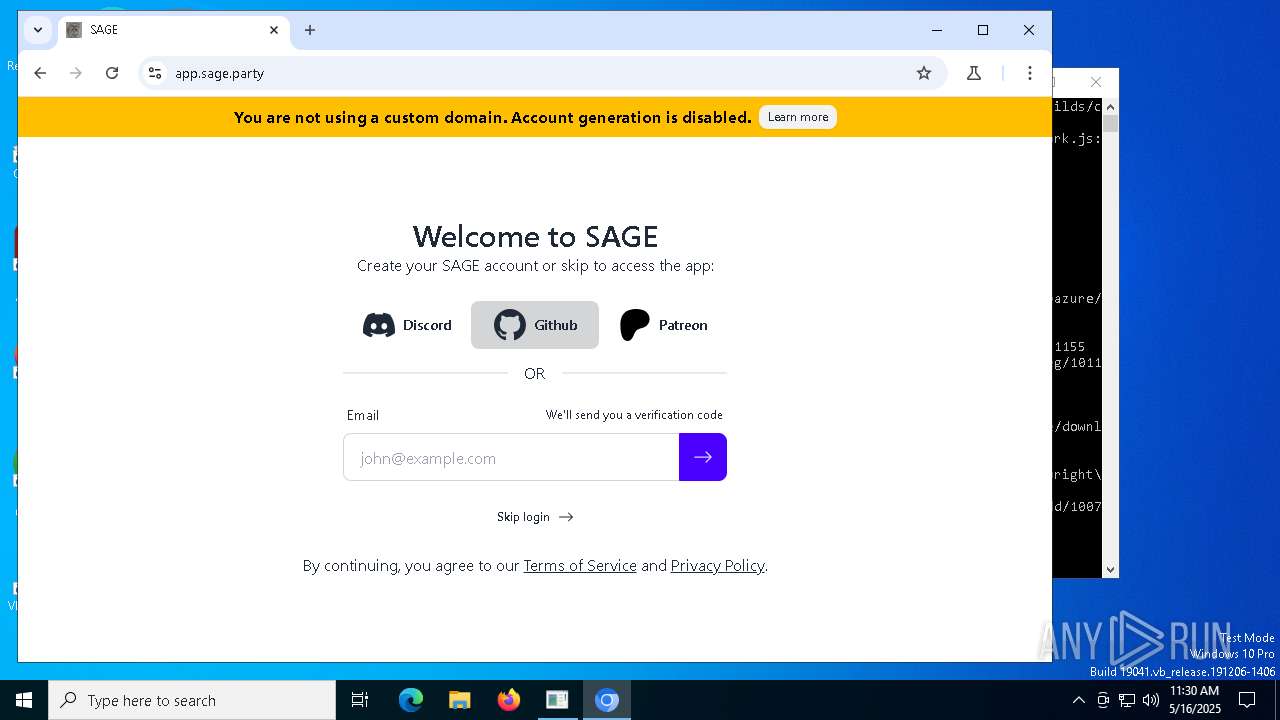
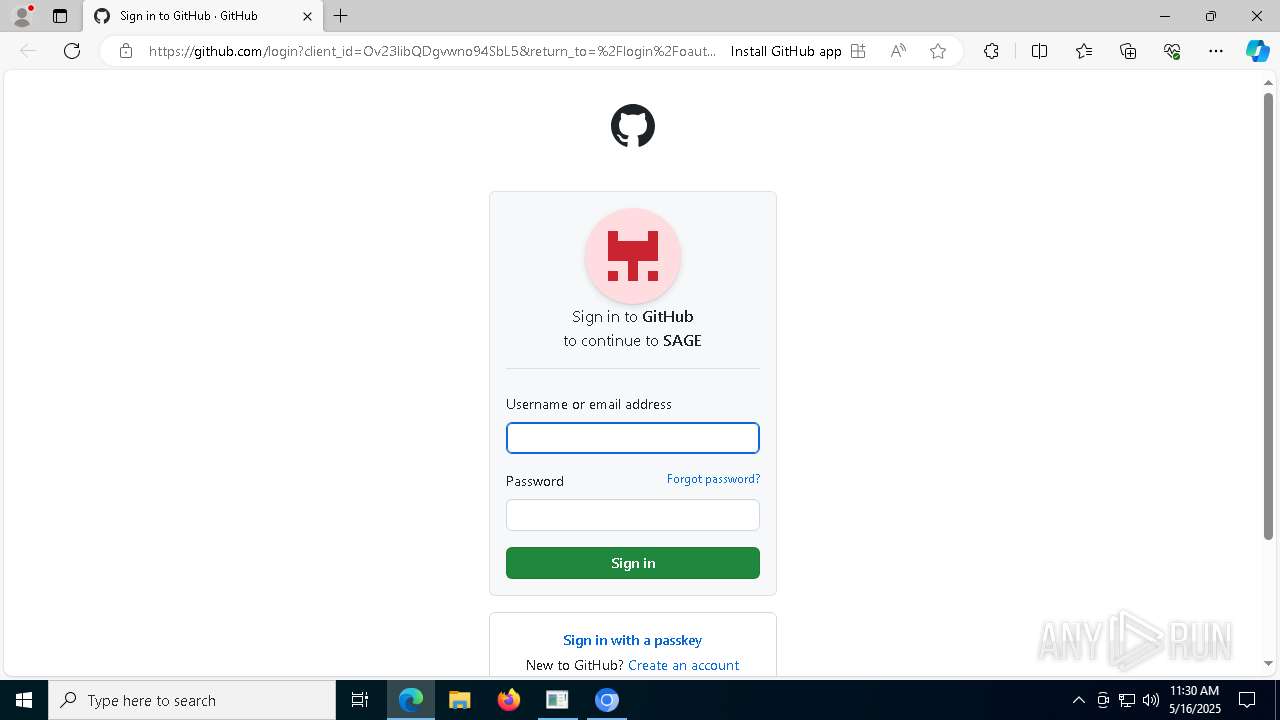
| File name: | sage-windows-amd64.exe |
| Full analysis: | https://app.any.run/tasks/945be302-a727-40d7-8a58-6c6aa85aba94 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 11:28:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64 (stripped to external PDB), for MS Windows, 11 sections |
| MD5: | DE9C93F92716C283A72B89B23B4866AE |
| SHA1: | F193BD26D4DE24C127D05DC27C9578321E27A934 |
| SHA256: | 07E16FC64EC4C66BD6E06CBE77DF40F0DCA2F7FE211F54FF2C6217907BF8C959 |
| SSDEEP: | 98304:nKNBqkxEnJl1VIhttDqbe6uWppULb5dQxGoJQtSuQaOhG34w24qNOjyLBiRCYNyM:odpFxw6 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- sage-windows-amd64.exe (PID: 7604)
The process bypasses the loading of PowerShell profile settings
- sage-windows-amd64.exe (PID: 7604)
There is functionality for taking screenshot (YARA)
- sage-windows-amd64.exe (PID: 7604)
Executes script using NodeJS
- node.exe (PID: 8028)
- node.exe (PID: 8096)
- node.exe (PID: 2108)
- node.exe (PID: 7276)
- node.exe (PID: 5608)
- node.exe (PID: 3900)
- node.exe (PID: 5136)
- node.exe (PID: 7356)
Application launched itself
- node.exe (PID: 8028)
- chrome.exe (PID: 2340)
Executable content was dropped or overwritten
- node.exe (PID: 7276)
- node.exe (PID: 2108)
- node.exe (PID: 3900)
- node.exe (PID: 5608)
Process drops legitimate windows executable
- node.exe (PID: 7276)
The process creates files with name similar to system file names
- node.exe (PID: 3900)
The process checks if it is being run in the virtual environment
- chrome.exe (PID: 2340)
Uses RUNDLL32.EXE to load library
- sage-windows-amd64.exe (PID: 7604)
INFO
Checks supported languages
- sage-windows-amd64.exe (PID: 7604)
- node.exe (PID: 8028)
- node.exe (PID: 8096)
- node.exe (PID: 7276)
- node.exe (PID: 2108)
- node.exe (PID: 3900)
- node.exe (PID: 5608)
- PrintDeps.exe (PID: 4944)
- PrintDeps.exe (PID: 6044)
- PrintDeps.exe (PID: 3956)
- PrintDeps.exe (PID: 7500)
- PrintDeps.exe (PID: 7476)
- PrintDeps.exe (PID: 7484)
- PrintDeps.exe (PID: 4380)
- PrintDeps.exe (PID: 3300)
- PrintDeps.exe (PID: 7404)
- PrintDeps.exe (PID: 7408)
- PrintDeps.exe (PID: 7508)
- PrintDeps.exe (PID: 3268)
- PrintDeps.exe (PID: 7560)
- PrintDeps.exe (PID: 7580)
- PrintDeps.exe (PID: 5228)
- PrintDeps.exe (PID: 1196)
- PrintDeps.exe (PID: 7964)
- node.exe (PID: 5136)
- node.exe (PID: 7356)
- chrome.exe (PID: 2340)
- PrintDeps.exe (PID: 1300)
- PrintDeps.exe (PID: 856)
- PrintDeps.exe (PID: 7000)
- chrome.exe (PID: 6416)
- chrome.exe (PID: 2568)
- chrome.exe (PID: 7268)
- chrome.exe (PID: 4688)
- chrome.exe (PID: 904)
- chrome.exe (PID: 8176)
- chrome.exe (PID: 8172)
- identity_helper.exe (PID: 7716)
Reads the computer name
- sage-windows-amd64.exe (PID: 7604)
- node.exe (PID: 8028)
- node.exe (PID: 8096)
- node.exe (PID: 7276)
- node.exe (PID: 3900)
- node.exe (PID: 2108)
- node.exe (PID: 5608)
- node.exe (PID: 5136)
- node.exe (PID: 7356)
- chrome.exe (PID: 2340)
- chrome.exe (PID: 6416)
- chrome.exe (PID: 2568)
- chrome.exe (PID: 4688)
- identity_helper.exe (PID: 7716)
Reads the machine GUID from the registry
- sage-windows-amd64.exe (PID: 7604)
- chrome.exe (PID: 2340)
Creates files or folders in the user directory
- sage-windows-amd64.exe (PID: 7604)
- node.exe (PID: 8028)
- node.exe (PID: 7276)
- node.exe (PID: 3900)
- node.exe (PID: 2108)
- node.exe (PID: 5608)
Drops encrypted JS script (Microsoft Script Encoder)
- sage-windows-amd64.exe (PID: 7604)
Reads the software policy settings
- sage-windows-amd64.exe (PID: 7604)
- slui.exe (PID: 1180)
Detects GO elliptic curve encryption (YARA)
- sage-windows-amd64.exe (PID: 7604)
Reads product name
- node.exe (PID: 8028)
- node.exe (PID: 7276)
- node.exe (PID: 2108)
- node.exe (PID: 8096)
- node.exe (PID: 3900)
- node.exe (PID: 5608)
- node.exe (PID: 5136)
- node.exe (PID: 7356)
Application based on Golang
- sage-windows-amd64.exe (PID: 7604)
Reads Environment values
- node.exe (PID: 8028)
- node.exe (PID: 7276)
- node.exe (PID: 8096)
- node.exe (PID: 3900)
- node.exe (PID: 2108)
- node.exe (PID: 5608)
- node.exe (PID: 5136)
- node.exe (PID: 7356)
- identity_helper.exe (PID: 7716)
Create files in a temporary directory
- node.exe (PID: 8096)
- node.exe (PID: 7276)
- node.exe (PID: 3900)
- node.exe (PID: 2108)
- node.exe (PID: 5608)
- chrome.exe (PID: 2340)
- chrome.exe (PID: 2568)
The sample compiled with english language support
- node.exe (PID: 7276)
- node.exe (PID: 3900)
Checks proxy server information
- chrome.exe (PID: 2340)
- slui.exe (PID: 1180)
Process checks computer location settings
- chrome.exe (PID: 2340)
- chrome.exe (PID: 8176)
- chrome.exe (PID: 904)
- chrome.exe (PID: 8172)
Reads CPU info
- chrome.exe (PID: 2340)
Application launched itself
- msedge.exe (PID: 4112)
- msedge.exe (PID: 1676)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 4408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 2.39 |
| CodeSize: | 6195712 |
| InitializedDataSize: | 14245376 |
| UninitializedDataSize: | 360960 |
| EntryPoint: | 0x13f0 |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
Total processes
223
Monitored processes
95
Malicious processes
2
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5644 --field-trial-handle=2408,i,7450366495487334749,14041459632763779098,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PrintDeps.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | C:\Users\admin\AppData\Local\ms-playwright\winldd-1007\PrintDeps.exe C:\Users\admin\AppData\Local\ms-playwright\chromium_headless_shell-1155\chrome-win\libEGL.dll | C:\Users\admin\AppData\Local\ms-playwright\winldd-1007\PrintDeps.exe | — | node.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 904 | "C:\Users\admin\AppData\Local\ms-playwright\chromium-1155\chrome-win\chrome.exe" --type=renderer --string-annotations --user-data-dir="C:\Users\admin\AppData\Local\Temp\playwright_chromiumdev_profile-IAreGJ" --no-sandbox --disable-back-forward-cache --disable-background-timer-throttling --disable-breakpad --force-color-profile=srgb --remote-debugging-pipe --allow-pre-commit-input --disable-databases --disable-blink-features=AutomationControlled --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --field-trial-handle=3536,i,779114660269898817,15142771697453790890,262144 --disable-features=AcceptCHFrame,AutoExpandDetailsElement,AvoidUnnecessaryBeforeUnloadCheckSync,CertificateTransparencyComponentUpdater,DestroyProfileOnBrowserClose,DialMediaRouteProvider,GlobalMediaControls,HttpsUpgrades,ImprovedCookieControls,LazyFrameLoading,LensOverlay,MediaRouter,PaintHolding,PlzDedicatedWorker,ThirdPartyStoragePartitioning,Translate --variations-seed-version --mojo-platform-channel-handle=3544 /prefetch:1 | C:\Users\admin\AppData\Local\ms-playwright\chromium-1155\chrome-win\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: The Chromium Authors Integrity Level: MEDIUM Description: Chromium Exit code: 0 Version: 133.0.6943.16 Modules
| |||||||||||||||
| 1072 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4296 --field-trial-handle=2356,i,6088250341712251649,10727156145151523392,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1180 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | C:\Users\admin\AppData\Local\ms-playwright\winldd-1007\PrintDeps.exe C:\Users\admin\AppData\Local\ms-playwright\chromium_headless_shell-1155\chrome-win\vulkan-1.dll | C:\Users\admin\AppData\Local\ms-playwright\winldd-1007\PrintDeps.exe | — | node.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1300 | C:\Users\admin\AppData\Local\ms-playwright\winldd-1007\PrintDeps.exe C:\Users\admin\AppData\Local\ms-playwright\chromium-1155\chrome-win\vulkan-1.dll | C:\Users\admin\AppData\Local\ms-playwright\winldd-1007\PrintDeps.exe | — | node.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1328 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5216 --field-trial-handle=2356,i,6088250341712251649,10727156145151523392,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PrintDeps.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 229
Read events
20 171
Write events
57
Delete events
1
Modification events
| (PID) Process: | (2340) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Chromium\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2340) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Chromium |
| Operation: | write | Name: | metricsid |
Value: eb81a9da-e5ad-4722-9645-946af3a32a2f | |||
| (PID) Process: | (2340) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Chromium |
| Operation: | write | Name: | metricsid_installdate |
Value: 1747395019 | |||
| (PID) Process: | (2340) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Chromium |
| Operation: | write | Name: | metricsid_enableddate |
Value: 1747395019 | |||
| (PID) Process: | (2340) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Chromium |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2340) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Chromium |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (2340) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Chromium |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (2340) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Chromium |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
| (PID) Process: | (2340) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Chromium\PreferenceMACs\Default |
| Operation: | write | Name: | extensions.ui.developer_mode |
Value: 37B859FC616C47C396331F3FC1D9BA17835B8484F837F55F806FE1C020DD890B | |||
| (PID) Process: | (2340) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Chromium\PreferenceMACs\Default |
| Operation: | write | Name: | google.services.last_signed_in_username |
Value: 757CFEBCD9B0B29F2606735EA86823C2CDD92CD76E8EE950C507FB0778DB914B | |||
Executable files
37
Suspicious files
623
Text files
116
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7604 | sage-windows-amd64.exe | C:\Users\admin\AppData\Local\ms-playwright-go\1.50.1\node.exe | — | |
MD5:— | SHA256:— | |||
| 7604 | sage-windows-amd64.exe | C:\Users\admin\AppData\Local\ms-playwright-go\1.50.1\package\index.mjs | binary | |
MD5:B27374F864BCAF5AA12E3C83EB9A1605 | SHA256:3D36E2132D3C8B62397D23F0BB4177336AAEE503203AE2A2C90FBEB5BF3317DD | |||
| 7688 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ciodtegk.kjs.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7688 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nge00zvs.t1w.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7688 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kisersqh.byo.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7688 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nhdd51qz.gk1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7604 | sage-windows-amd64.exe | C:\Users\admin\AppData\Local\ms-playwright-go\1.50.1\package\lib\utilsBundleImpl\xdg-open | text | |
MD5:FC9FD8296946E1F00AC0E497AC98EE1E | SHA256:2E79A4D5171DD384D20A75B023DFE0E9F4330CDB5D441F6C3859A11FCE3DB51A | |||
| 7688 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:8713C128E8DA7BA2E934B2433644D6E9 | SHA256:FBB00073817AA7271D4646BE0803344515E323FC12977AD82E0B5C7C22375375 | |||
| 7604 | sage-windows-amd64.exe | C:\Users\admin\AppData\Local\ms-playwright-go\1.50.1\LICENSE | text | |
MD5:0BD28A461ECCAD39F85A29E33E8F879F | SHA256:9D72CCE9B104ECB67FEB8AF38618511685190AE5A119CC0488ECAE66B221000D | |||
| 7604 | sage-windows-amd64.exe | C:\Users\admin\AppData\Local\ms-playwright-go\1.50.1\package\lib\cli\program.js | binary | |
MD5:8063B856D2BEEBDF9A2CE6A9F7412A81 | SHA256:1A76F7FD901D9AB1F03A1275767FCC04A524FD50A299821F3012F5EE45BE7D04 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
80
DNS requests
77
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7084 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7084 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2568 | chrome.exe | GET | 200 | 142.250.186.46:80 | http://clients2.google.com/time/1/current?cup2key=8:pwYINUN44OlxpuU6gm9JutgHSySJksNPSsJo7O--G9k&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
playwright.azureedge.net |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cdn.playwright.dev |
| unknown |
playwright.download.prss.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2568 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2568 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2568 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2568 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2568 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2568 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2568 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2568 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2568 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2568 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |