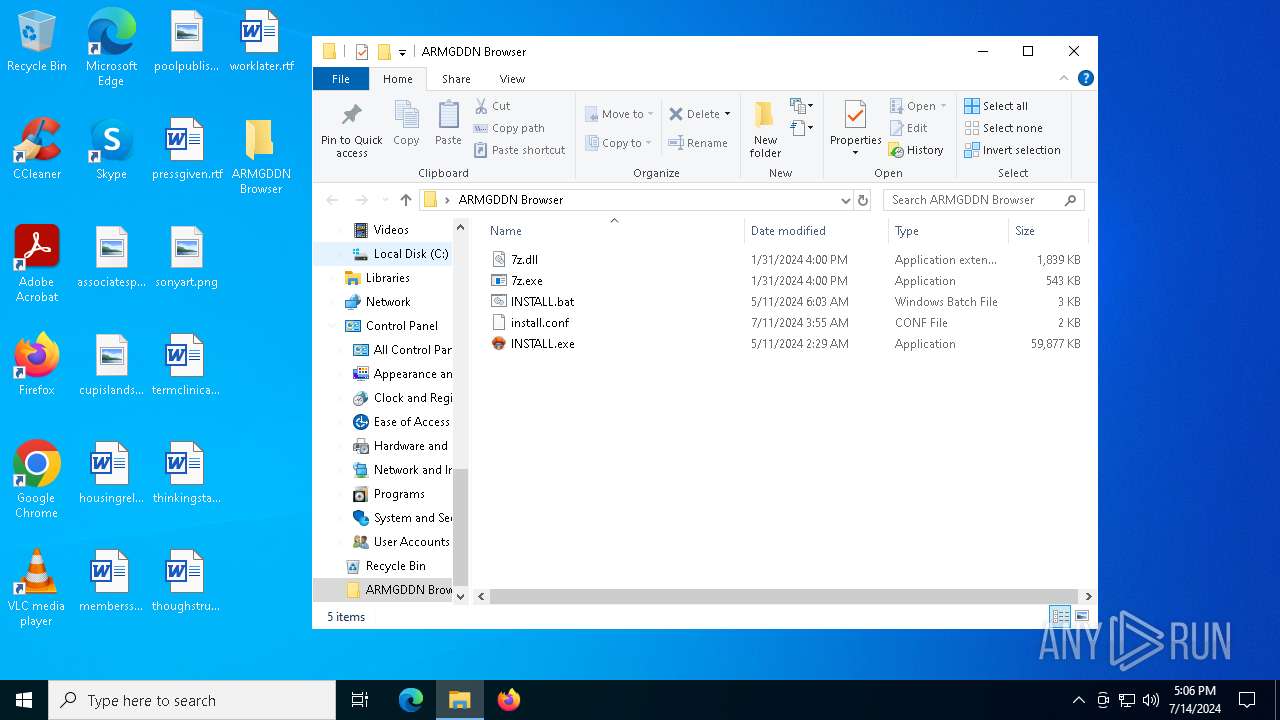
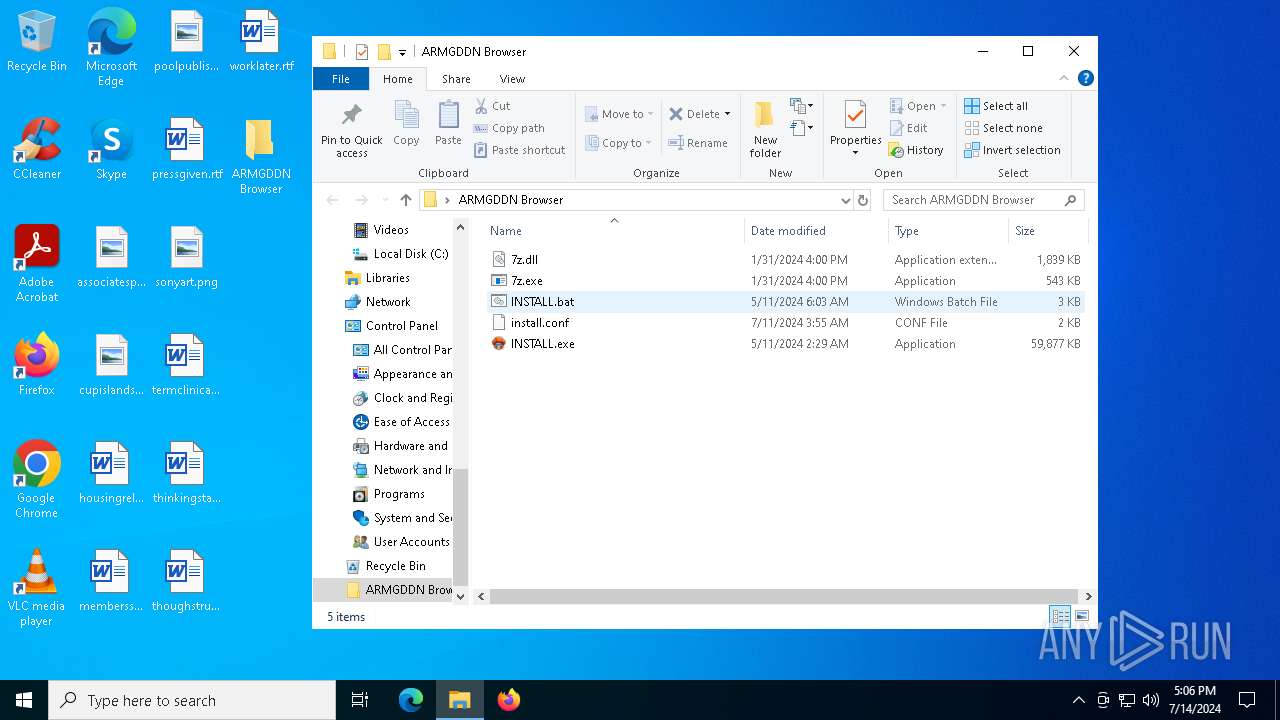
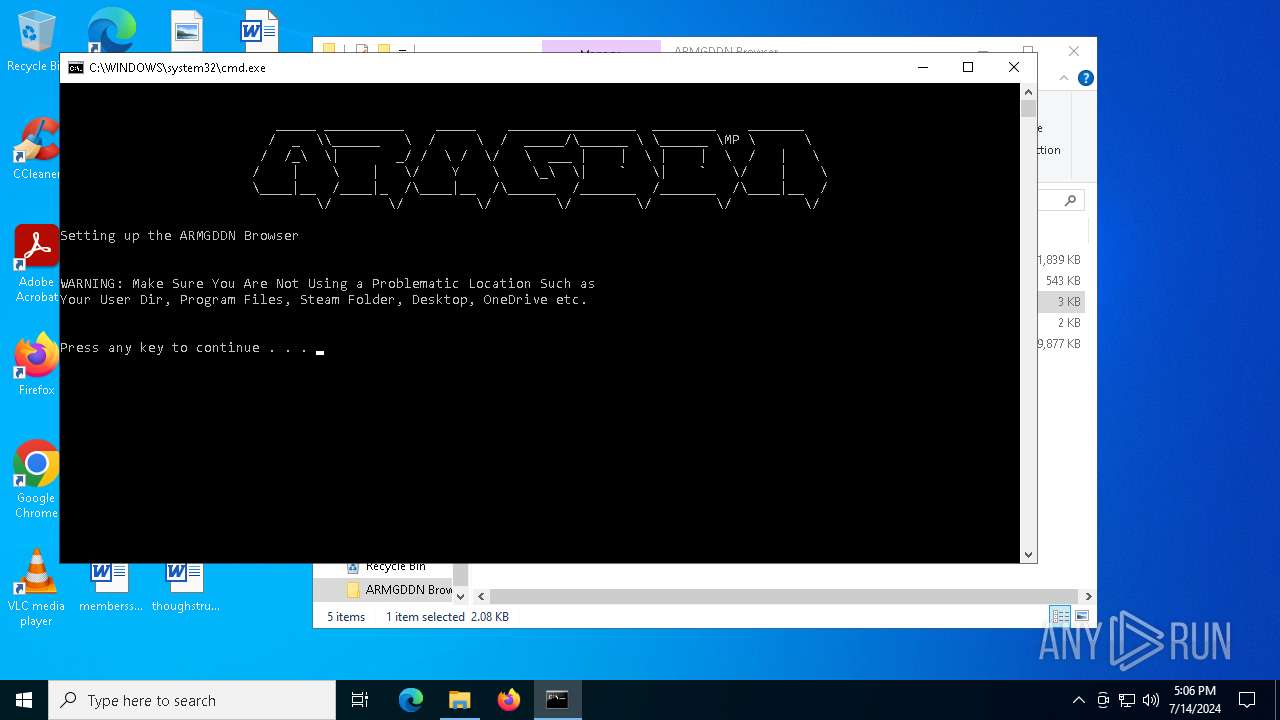
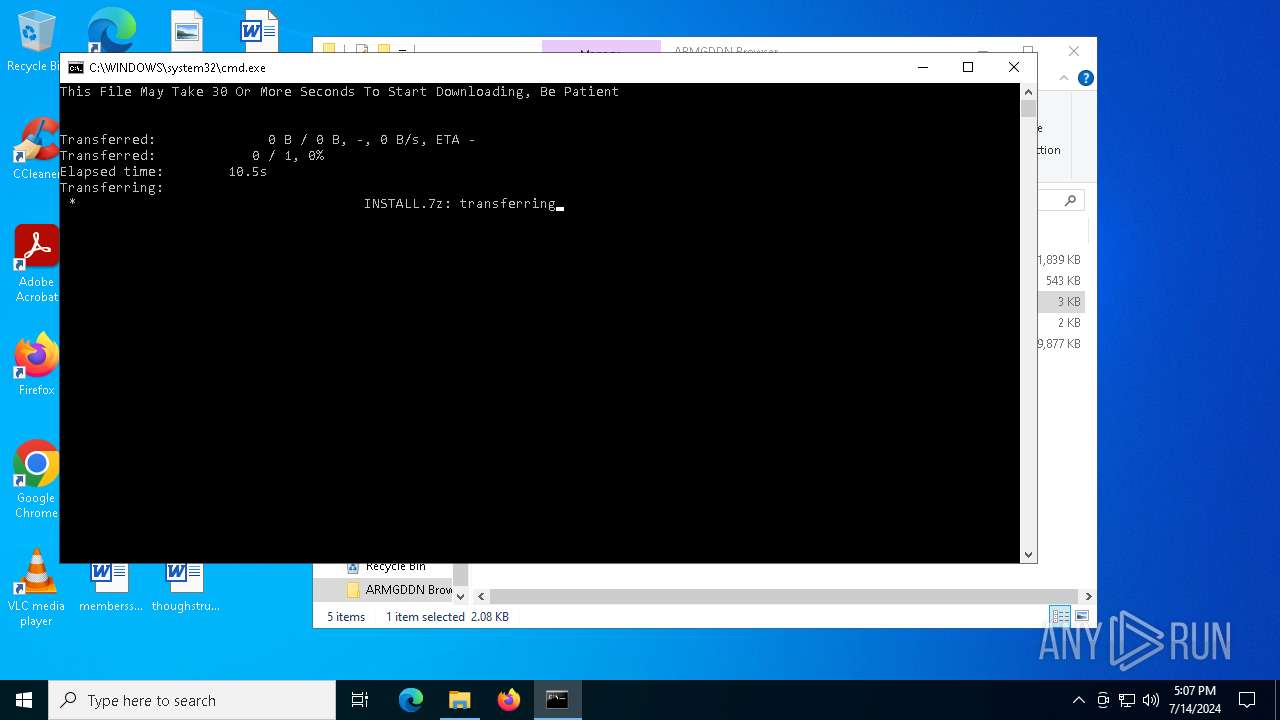
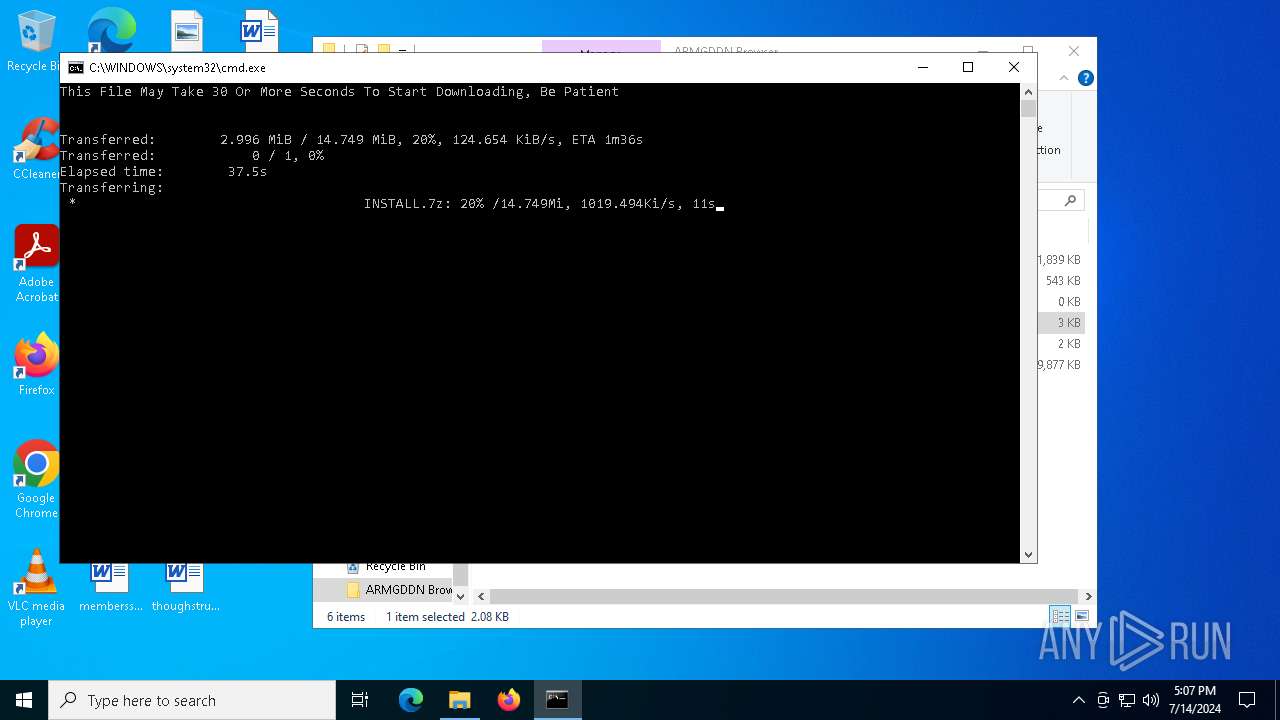
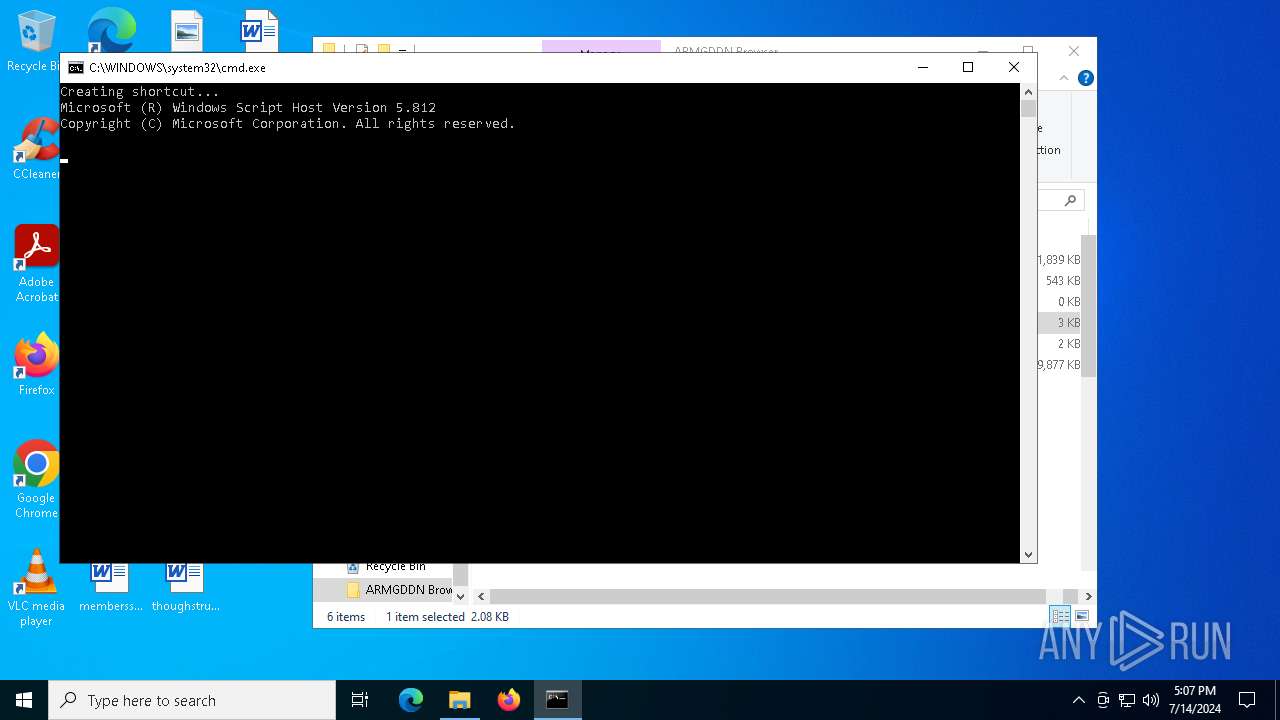
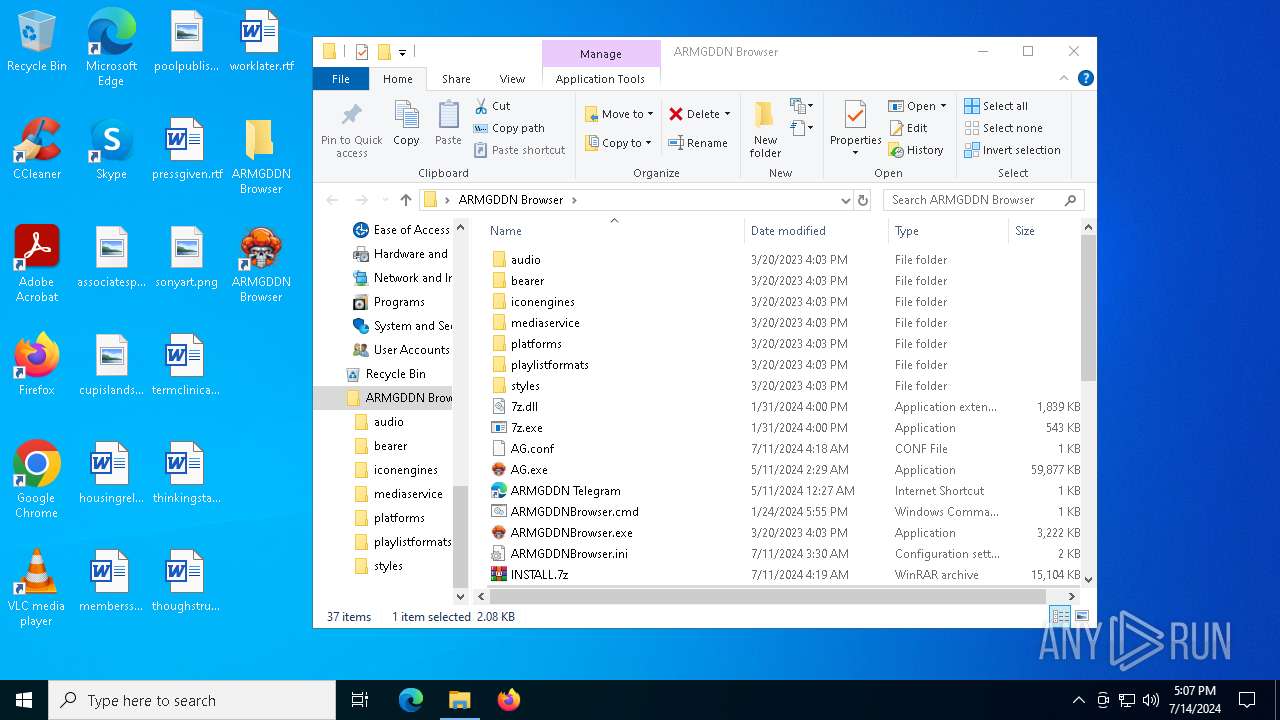
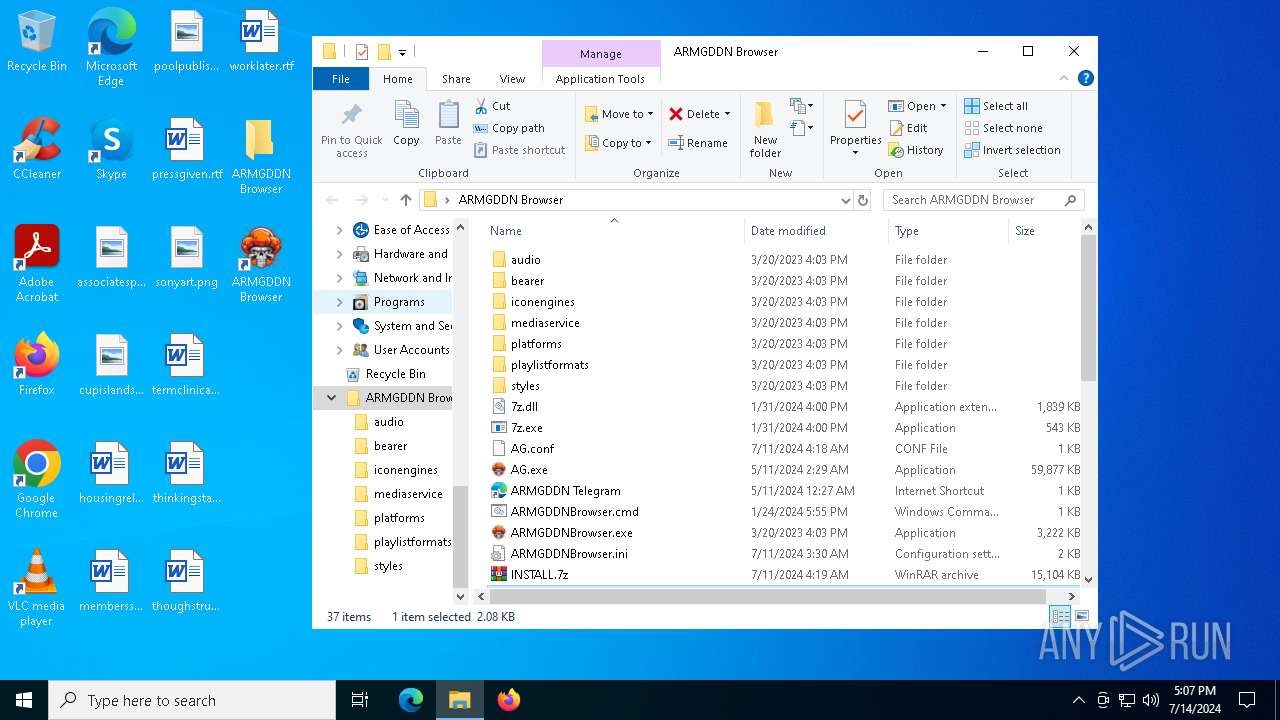
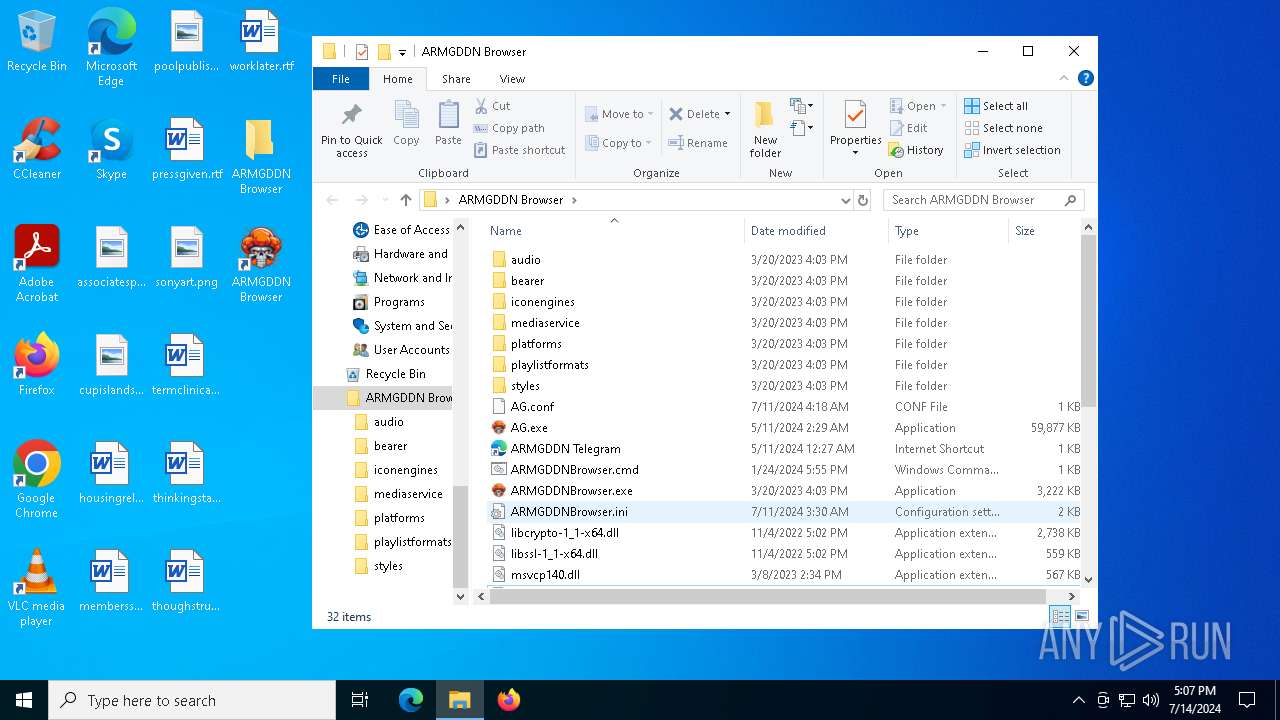
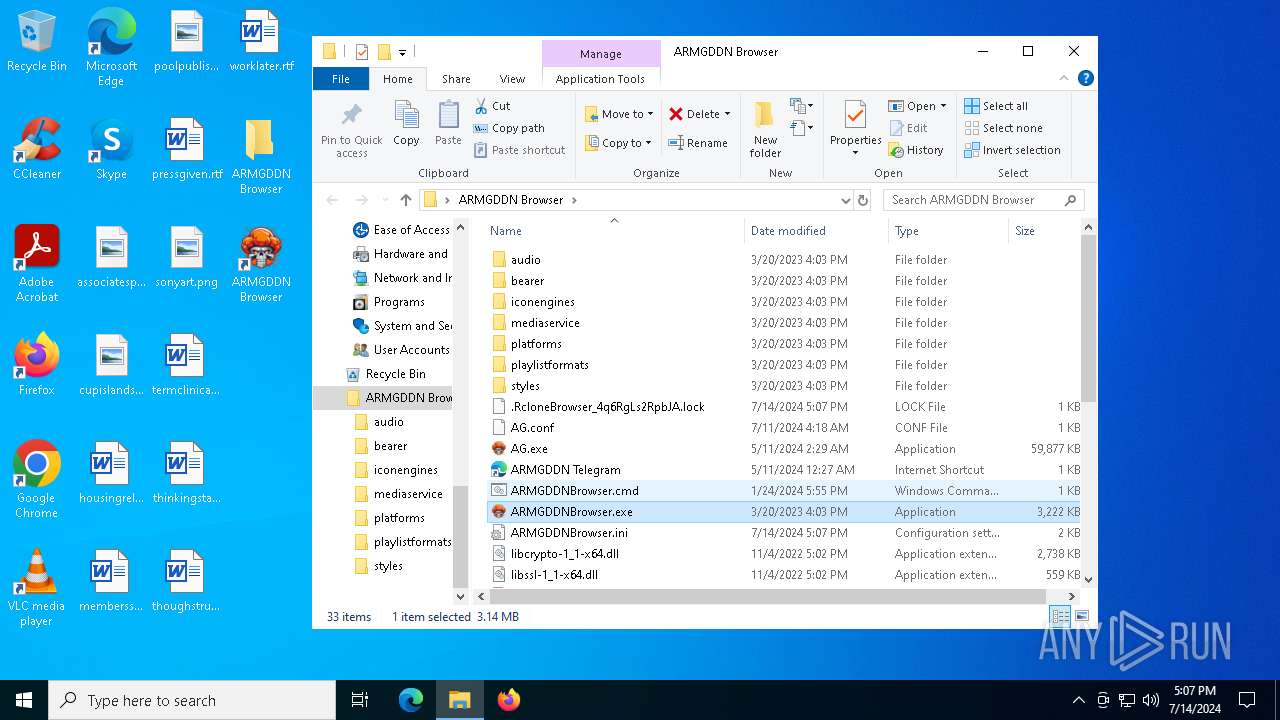
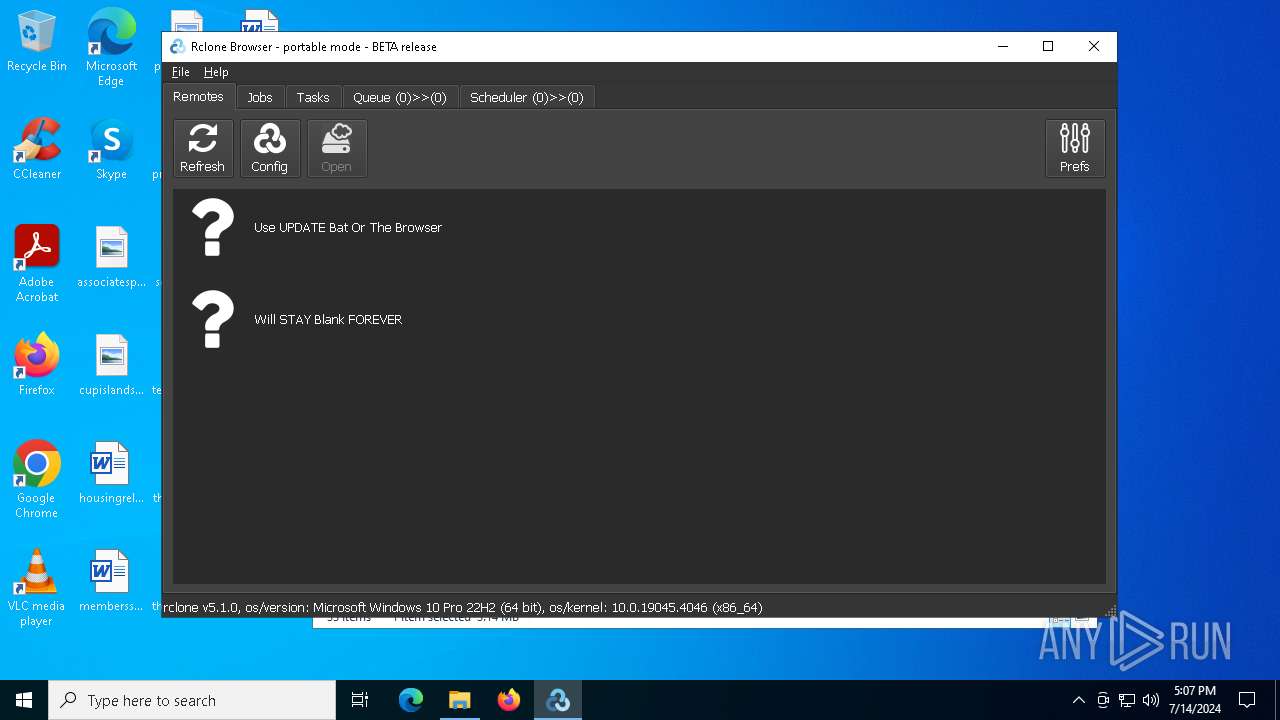
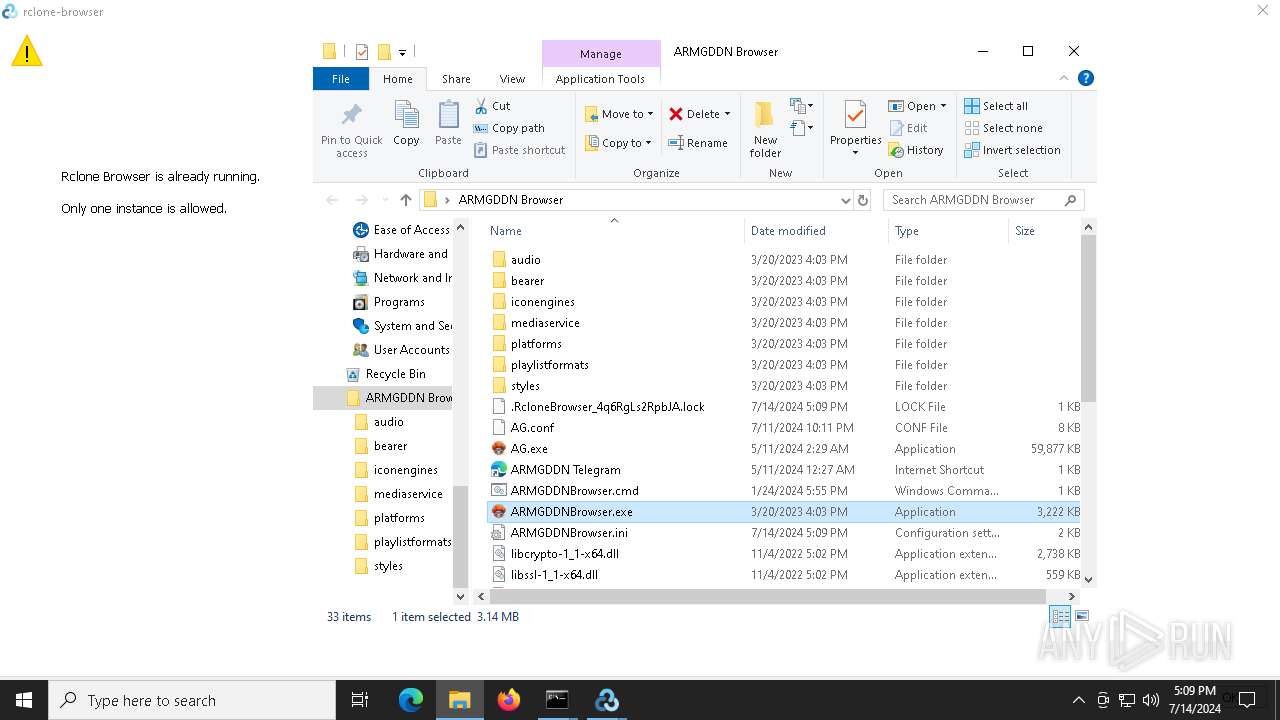
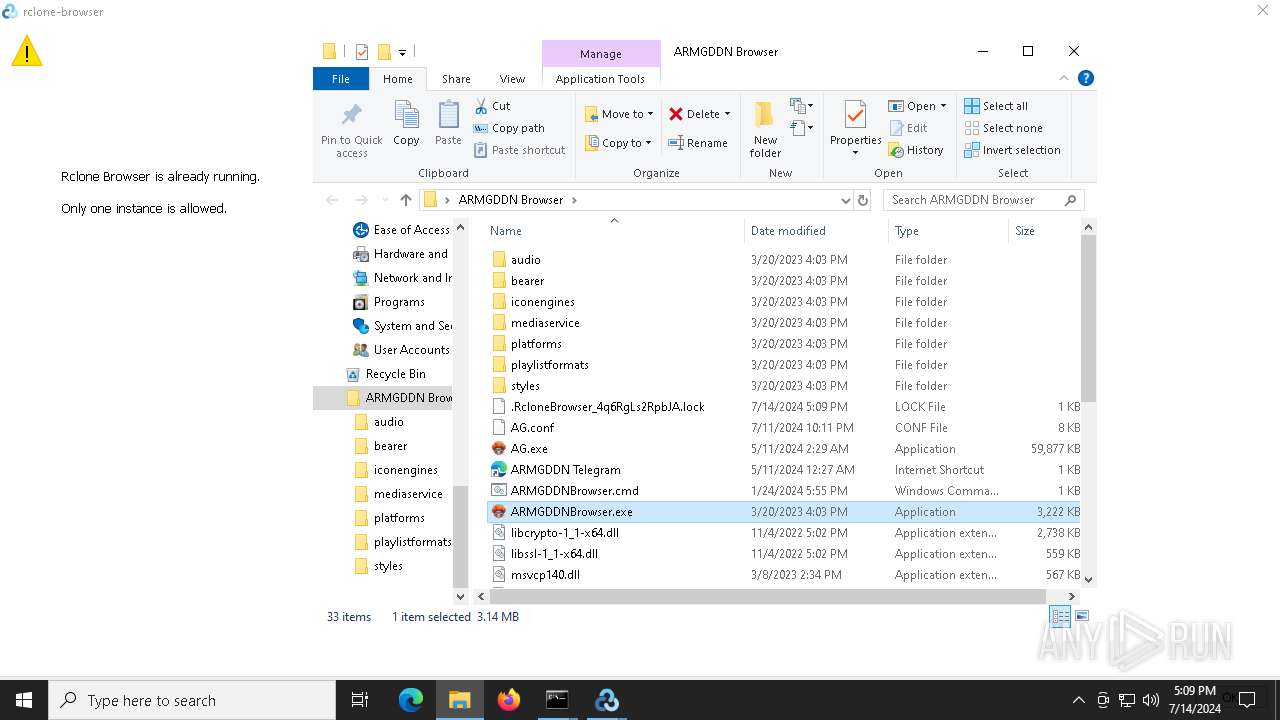
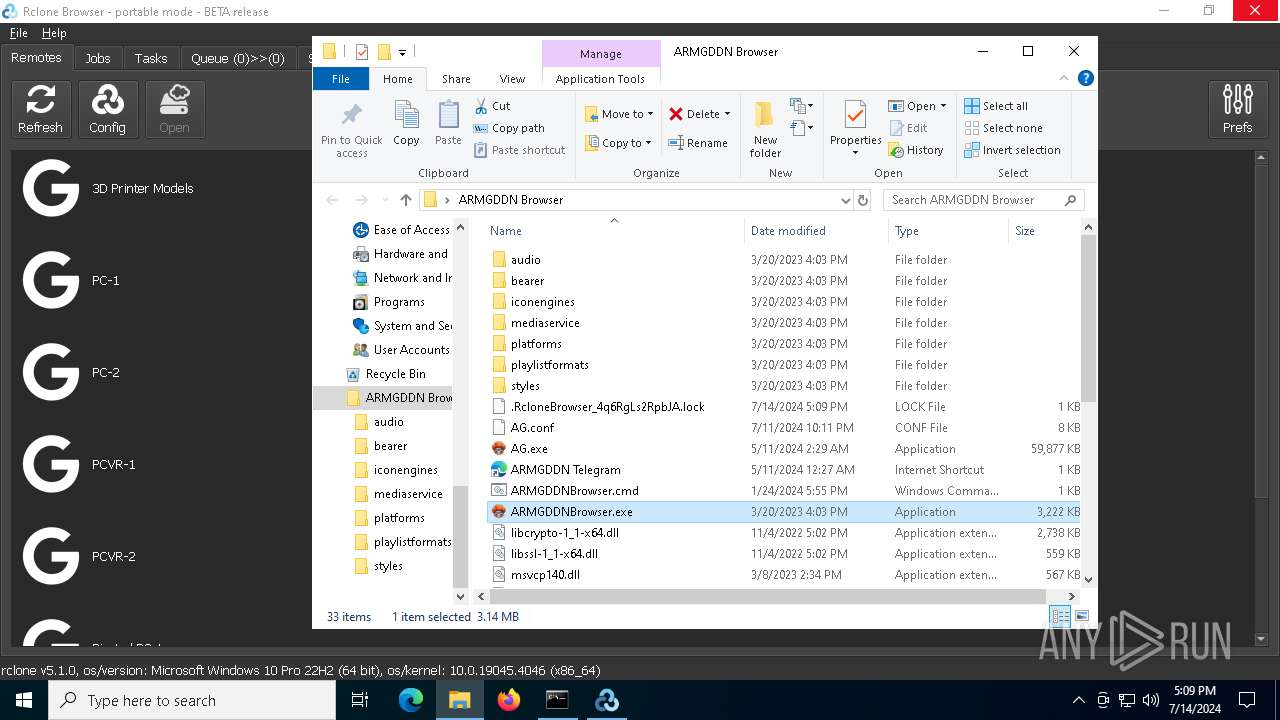
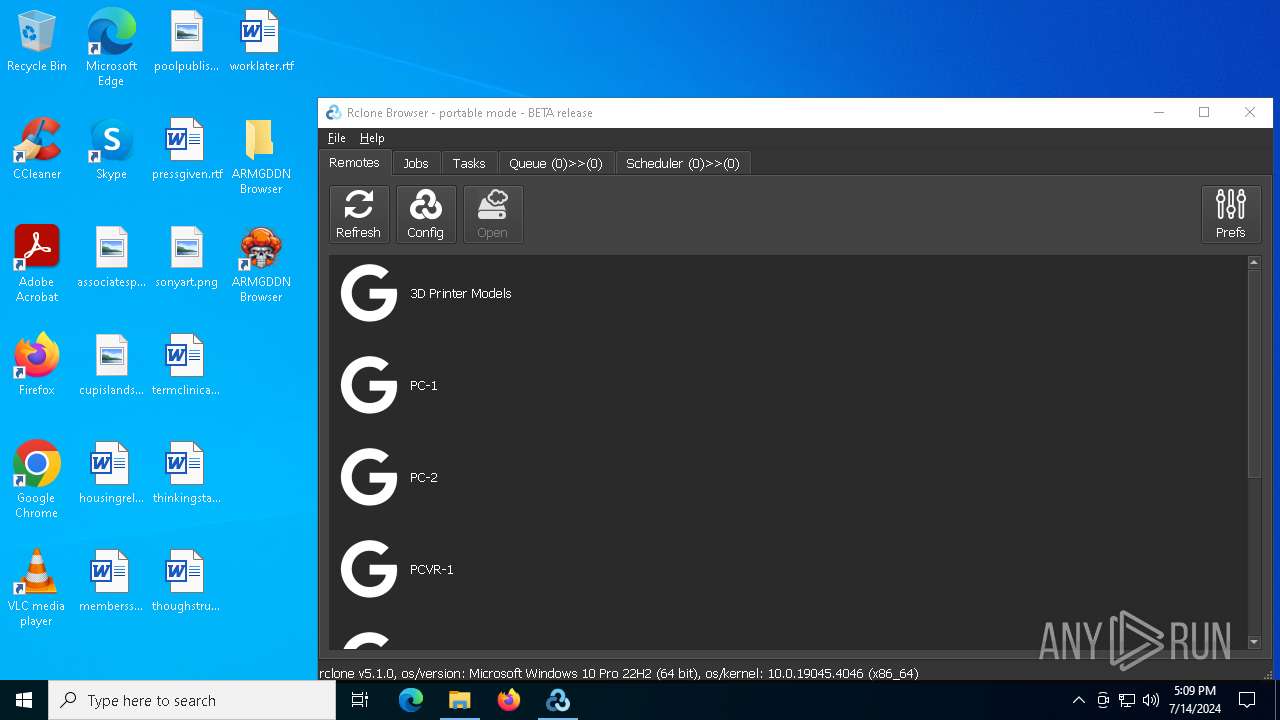
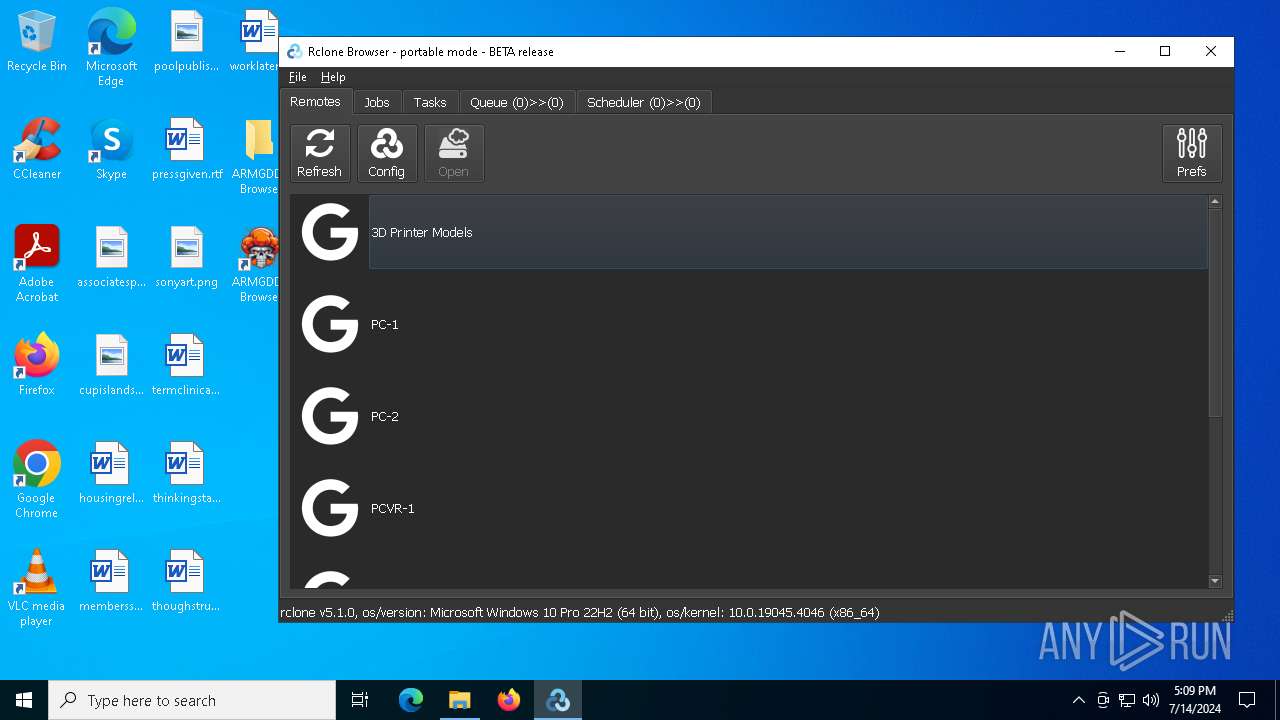
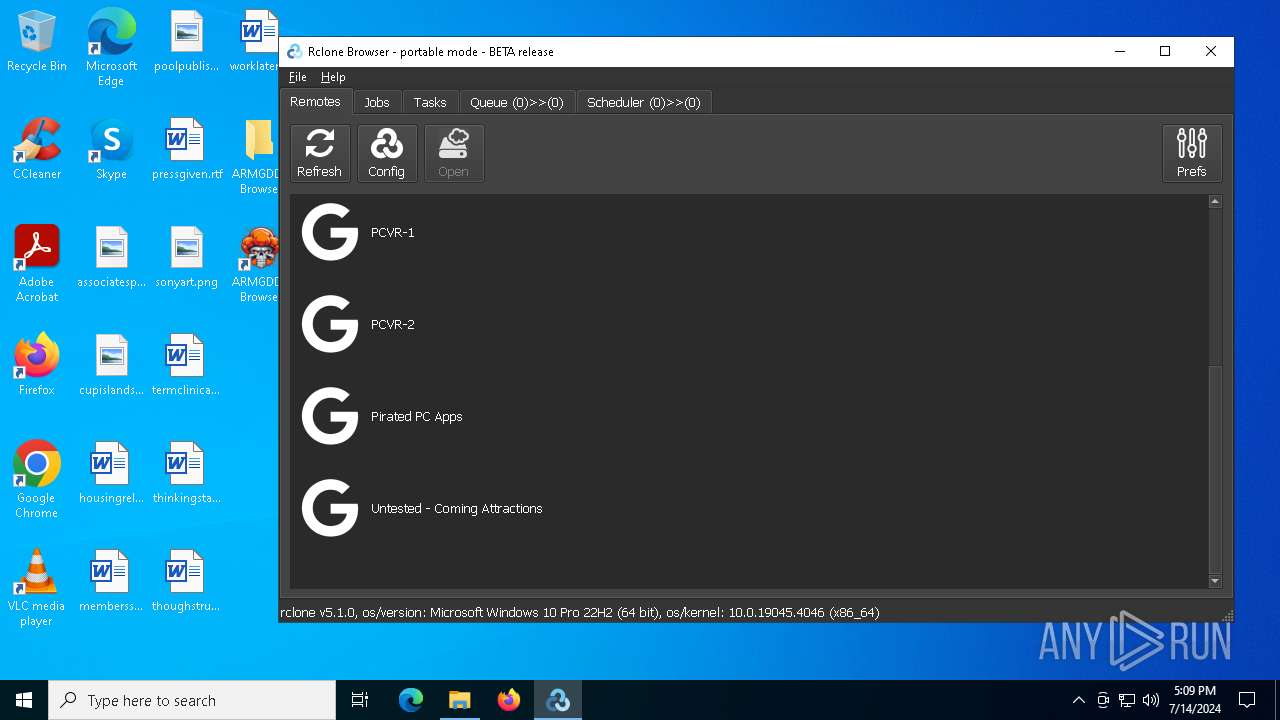
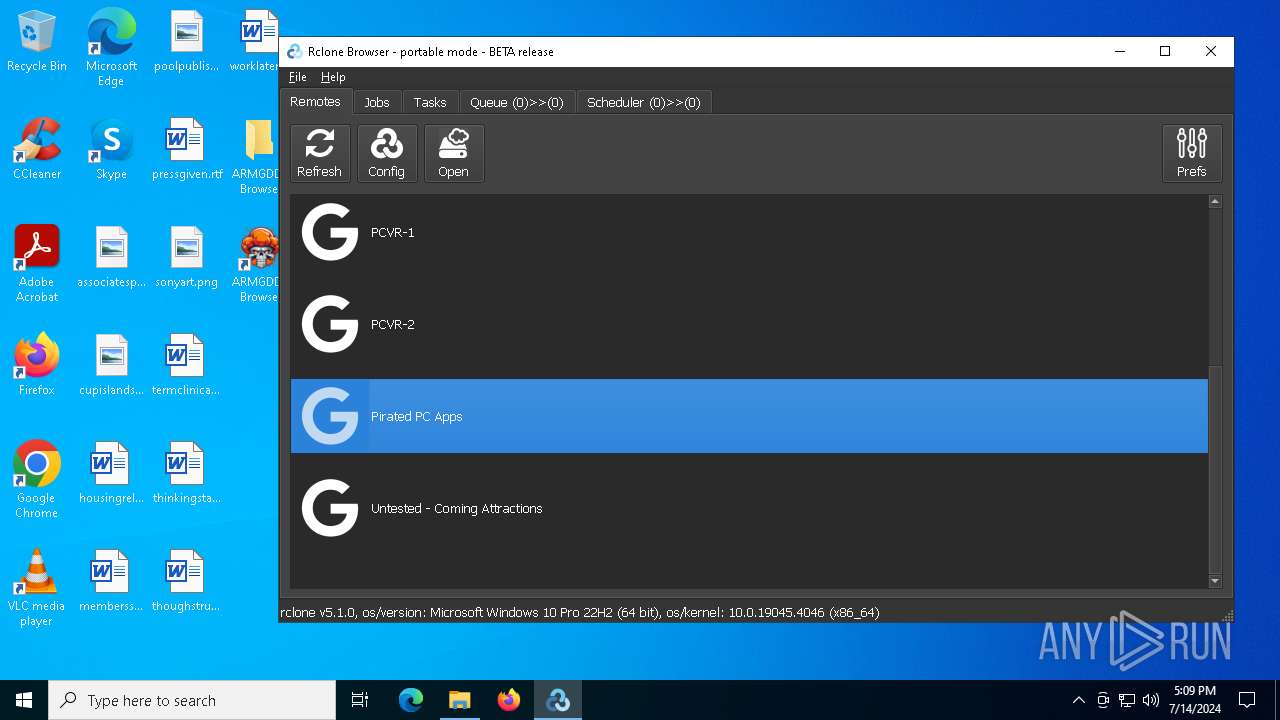
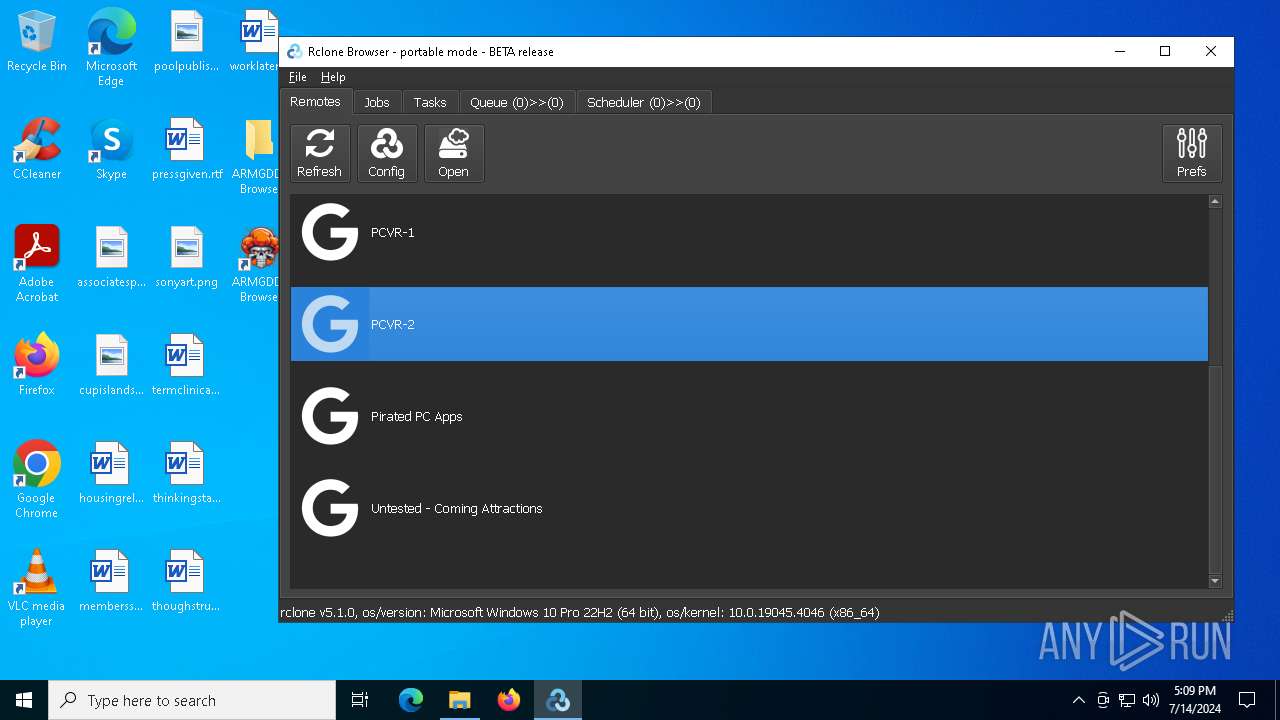
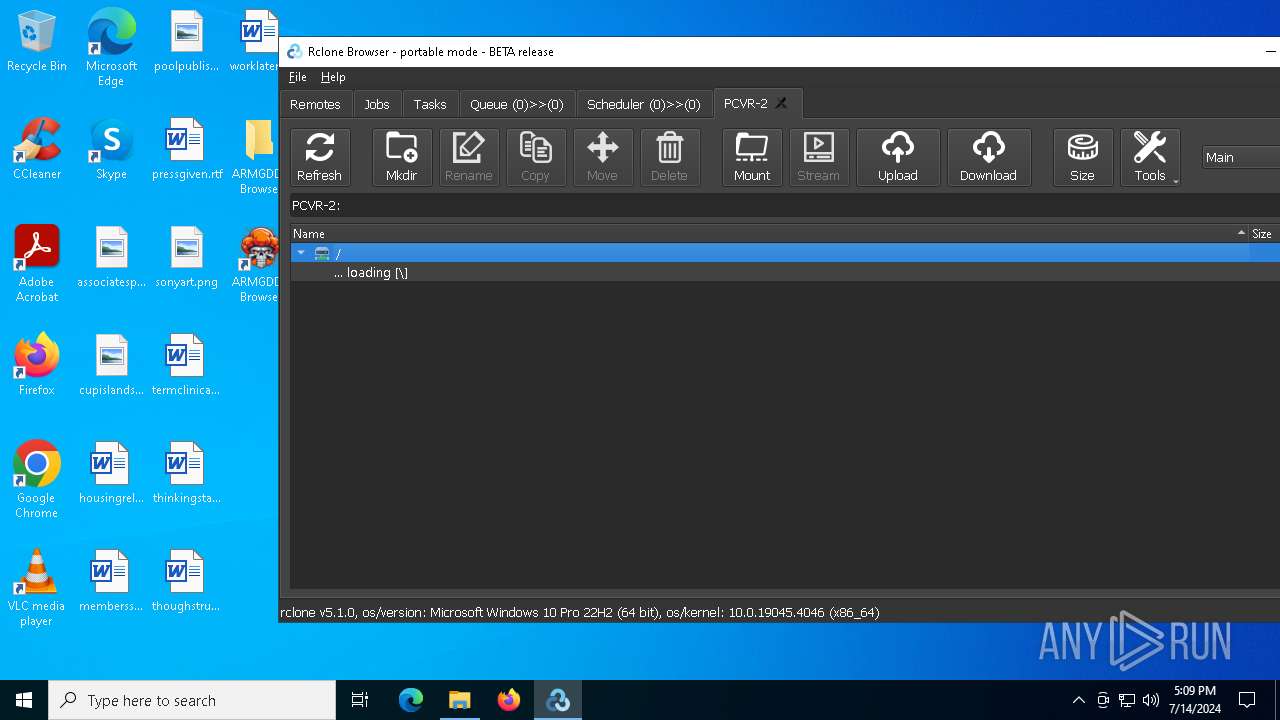
| File name: | SETUP.7z |
| Full analysis: | https://app.any.run/tasks/c6630192-598c-474d-9702-f597d1e79124 |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2024, 17:06:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 6A4CF377D0AD3E5FFBFFA7DBB49B7918 |
| SHA1: | 1CD779DBEDEBBD35B8152AB93E5295C16E999538 |
| SHA256: | 07AE365E03954A7248A358A7E3F2D0179997F916A5C05C46DFD670BB7D0E13EE |
| SSDEEP: | 98304:nVAiQxR/w9nmxcXfiEKZ5vPDWAk3J8u+34nFyBB3A5SUm9HR8TuiVWO94hmM1Aox:pZaBmIOLB2rYZEVtv2P3xHQI7Y |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 5004)
- 7z.exe (PID: 7096)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 5004)
Process drops legitimate windows executable
- 7z.exe (PID: 7096)
The process drops C-runtime libraries
- 7z.exe (PID: 7096)
Executable content was dropped or overwritten
- 7z.exe (PID: 7096)
The process executes VB scripts
- cmd.exe (PID: 2440)
Runs shell command (SCRIPT)
- cscript.exe (PID: 6692)
Application launched itself
- cmd.exe (PID: 6620)
- cmd.exe (PID: 6036)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6620)
- cmd.exe (PID: 6036)
Executing commands from a ".bat" file
- cmd.exe (PID: 6620)
- cmd.exe (PID: 6036)
There is functionality for VM detection (antiVM strings)
- AG.exe (PID: 6508)
- AG.exe (PID: 4256)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5004)
Checks supported languages
- INSTALL.exe (PID: 3540)
- 7z.exe (PID: 7096)
- ARMGDDNBrowser.exe (PID: 2452)
- AG.exe (PID: 5436)
- AG.exe (PID: 7128)
- AG.exe (PID: 4308)
- AG.exe (PID: 6992)
- ARMGDDNBrowser.exe (PID: 3844)
- AG.exe (PID: 1188)
- ARMGDDNBrowser.exe (PID: 5912)
- AG.exe (PID: 6388)
- AG.exe (PID: 1164)
- AG.exe (PID: 4756)
- AG.exe (PID: 5992)
- AG.exe (PID: 6216)
- AG.exe (PID: 6508)
- AG.exe (PID: 6948)
- AG.exe (PID: 2568)
- AG.exe (PID: 3068)
- AG.exe (PID: 4256)
Reads the computer name
- INSTALL.exe (PID: 3540)
- 7z.exe (PID: 7096)
- ARMGDDNBrowser.exe (PID: 2452)
- AG.exe (PID: 6992)
- AG.exe (PID: 5436)
- AG.exe (PID: 7128)
- AG.exe (PID: 4308)
- AG.exe (PID: 1188)
- ARMGDDNBrowser.exe (PID: 5912)
- ARMGDDNBrowser.exe (PID: 3844)
- AG.exe (PID: 6388)
- AG.exe (PID: 1164)
- AG.exe (PID: 5992)
- AG.exe (PID: 6508)
- AG.exe (PID: 4756)
- AG.exe (PID: 6216)
- AG.exe (PID: 3068)
- AG.exe (PID: 2568)
- AG.exe (PID: 6948)
- AG.exe (PID: 4256)
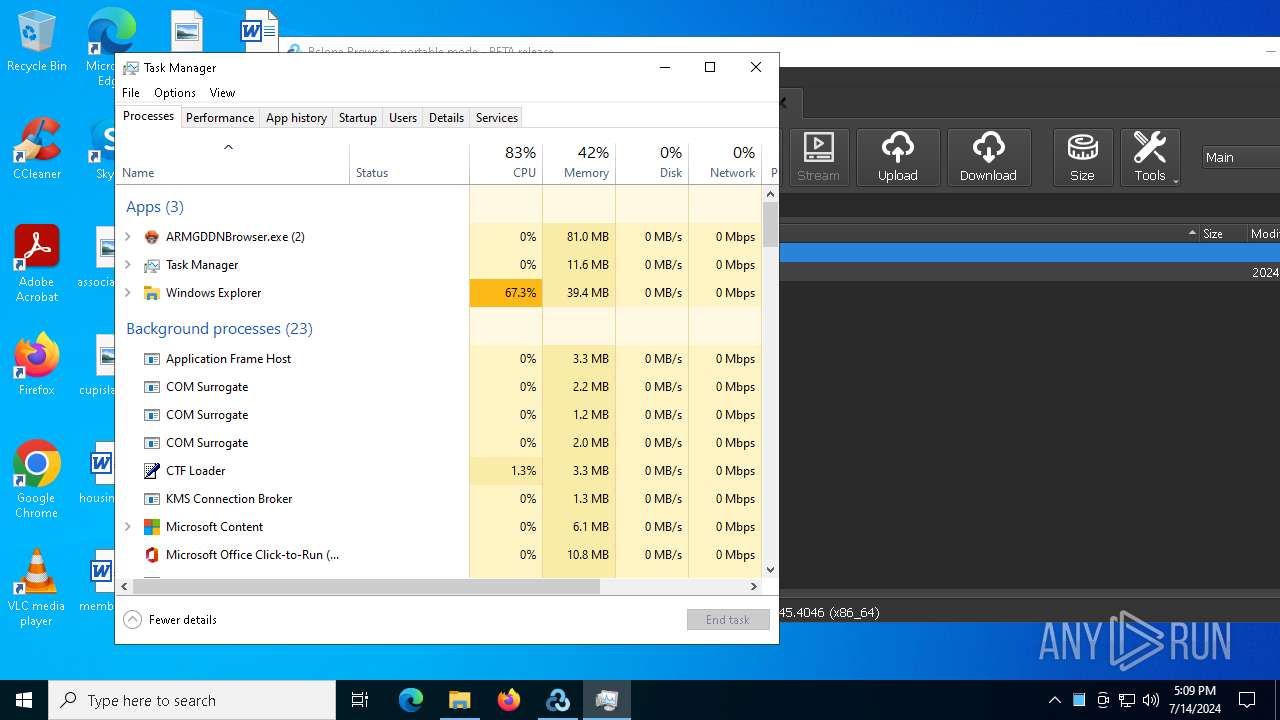
Manual execution by a user
- cmd.exe (PID: 2440)
- ARMGDDNBrowser.exe (PID: 2452)
- cmd.exe (PID: 6620)
- cmd.exe (PID: 6036)
- Taskmgr.exe (PID: 6732)
- Taskmgr.exe (PID: 3868)
Reads the machine GUID from the registry
- INSTALL.exe (PID: 3540)
- ARMGDDNBrowser.exe (PID: 2452)
- AG.exe (PID: 4308)
- AG.exe (PID: 1188)
- ARMGDDNBrowser.exe (PID: 3844)
- ARMGDDNBrowser.exe (PID: 5912)
- AG.exe (PID: 5992)
- AG.exe (PID: 4756)
- AG.exe (PID: 6216)
- AG.exe (PID: 6508)
- AG.exe (PID: 2568)
- AG.exe (PID: 3068)
- AG.exe (PID: 6948)
- AG.exe (PID: 4256)
Reads the software policy settings
- INSTALL.exe (PID: 3540)
- slui.exe (PID: 6536)
- AG.exe (PID: 4308)
- AG.exe (PID: 1188)
- AG.exe (PID: 5992)
- AG.exe (PID: 4756)
- AG.exe (PID: 6216)
- AG.exe (PID: 6508)
- slui.exe (PID: 6984)
- AG.exe (PID: 3068)
- AG.exe (PID: 2568)
- AG.exe (PID: 6948)
- AG.exe (PID: 4256)
Reads security settings of Internet Explorer
- cscript.exe (PID: 6692)
- Taskmgr.exe (PID: 3868)
Reads product name
- AG.exe (PID: 6992)
- AG.exe (PID: 6388)
Reads Environment values
- AG.exe (PID: 6992)
- AG.exe (PID: 6388)
Create files in a temporary directory
- AG.exe (PID: 1188)
Checks proxy server information
- slui.exe (PID: 6984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
192
Monitored processes
51
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 900 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1064 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AG.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\Users\admin\Desktop\ARMGDDN Browser\AG.exe" listremotes --config "C:/Users/admin/Desktop/ARMGDDN Browser/AG.conf" --fast-list --drive-acknowledge-abuse --long --ask-password=false | C:\Users\admin\Desktop\ARMGDDN Browser\AG.exe | — | ARMGDDNBrowser.exe | |||||||||||
User: admin Company: ARMGDDN Games Integrity Level: MEDIUM Description: AG Exit code: 0 Version: 5.1.0 Modules
| |||||||||||||||
| 1188 | AG copy "BrowserUpdate:AG.conf" "C:\Users\admin\Desktop\ARMGDDN Browser\\" --config update.conf | C:\Users\admin\Desktop\ARMGDDN Browser\AG.exe | cmd.exe | ||||||||||||
User: admin Company: ARMGDDN Games Integrity Level: MEDIUM Description: AG Exit code: 0 Version: 5.1.0 Modules
| |||||||||||||||
| 1444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AG.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1768 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2020 | cmd /c "update.bat & start "" /WAIT /MAX "ARMGDDNBrowser.exe"" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2104 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AG.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2288 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2440 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\ARMGDDN Browser\INSTALL.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
79 335
Read events
79 067
Write events
267
Delete events
1
Modification events
| (PID) Process: | (5004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SETUP.7z | |||
| (PID) Process: | (5004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF1C0100005D000000DC0400002D020000 | |||
| (PID) Process: | (5004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
31
Suspicious files
1
Text files
478
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
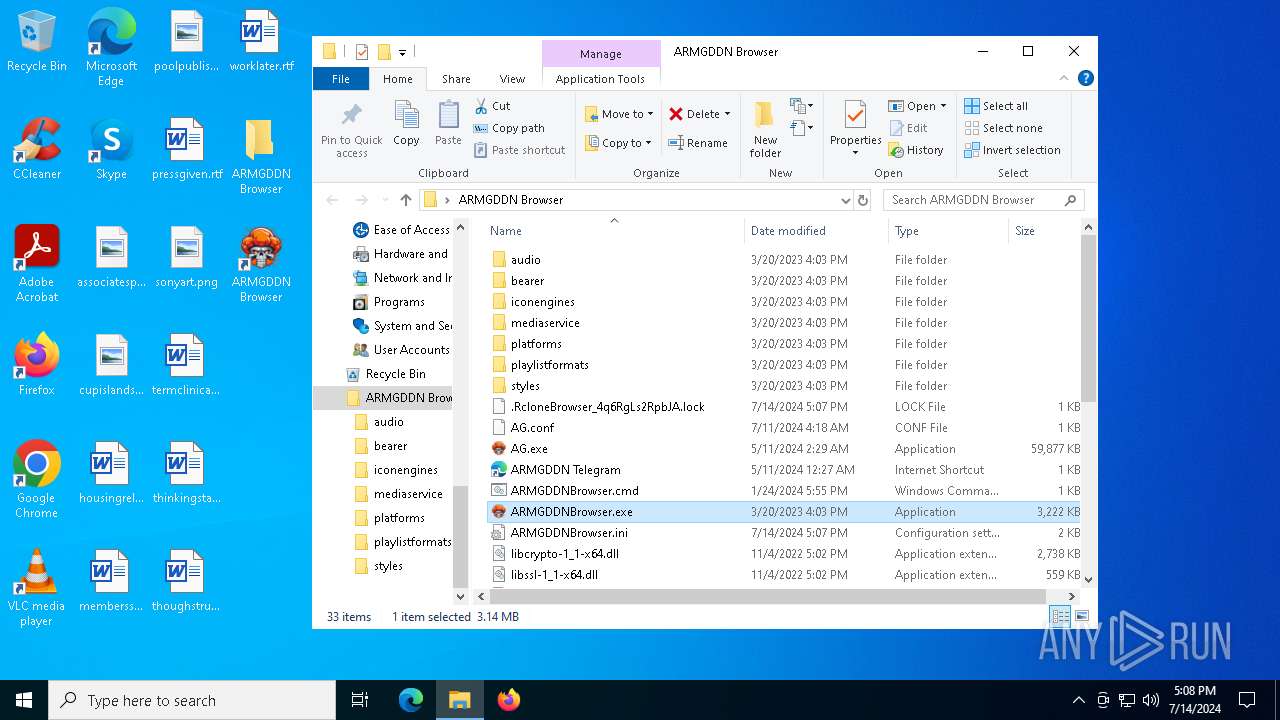
| 5004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5004.10669\ARMGDDN Browser\INSTALL.exe | — | |
MD5:— | SHA256:— | |||
| 3540 | INSTALL.exe | C:\Users\admin\Desktop\ARMGDDN Browser\INSTALL.7z.wolelaq1.partial | — | |
MD5:— | SHA256:— | |||
| 3540 | INSTALL.exe | C:\Users\admin\Desktop\ARMGDDN Browser\INSTALL.7z | — | |
MD5:— | SHA256:— | |||
| 5004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5004.10669\ARMGDDN Browser\7z.dll | executable | |
MD5:325164288F23CCFFF4891B050BF4A43E | SHA256:1AF1B530F6295207F719697184D4AB5587E2F11586DA4564CE352A743E7B8CCB | |||
| 5004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5004.10669\ARMGDDN Browser\7z.exe | executable | |
MD5:2F58D2175BD282F29CB215275A18100F | SHA256:CF20CF85335562D6D62BA191614393F8DA80664D3D6126C9FBAEC9C7CAADAAA2 | |||
| 3540 | INSTALL.exe | C:\Users\admin\Desktop\ARMGDDN Browser\install.conf3611506708 | text | |
MD5:D666C56D6247CAF1B691AB6DD7794BE6 | SHA256:77B77D89A226588A59220B50391D6E8A6FFE57BCE4C046BB8D82FE8973FA780A | |||
| 3540 | INSTALL.exe | C:\Users\admin\Desktop\ARMGDDN Browser\install.conf.old4260288846 | text | |
MD5:9F15DD2EF4C26A77692CD1F37940A53F | SHA256:8EB09C158FD267E6A682E257F796F69E2006491D94C43CB36F3D8522D57D2A83 | |||
| 5004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5004.10669\ARMGDDN Browser\INSTALL.bat | text | |
MD5:5FEA3E8D81AE23C1FC1203C7F2B9D221 | SHA256:103A9DF6A8A93415E80C6B98075CEC69D83D5E579B828F8D3FEF80F00485D4FF | |||
| 5004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5004.10669\ARMGDDN Browser\install.conf | text | |
MD5:9F15DD2EF4C26A77692CD1F37940A53F | SHA256:8EB09C158FD267E6A682E257F796F69E2006491D94C43CB36F3D8522D57D2A83 | |||
| 3540 | INSTALL.exe | C:\Users\admin\Desktop\ARMGDDN Browser\install.conf | text | |
MD5:D666C56D6247CAF1B691AB6DD7794BE6 | SHA256:77B77D89A226588A59220B50391D6E8A6FFE57BCE4C046BB8D82FE8973FA780A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
89
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1972 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3760 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6152 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2728 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2728 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.110.123:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1972 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1972 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |