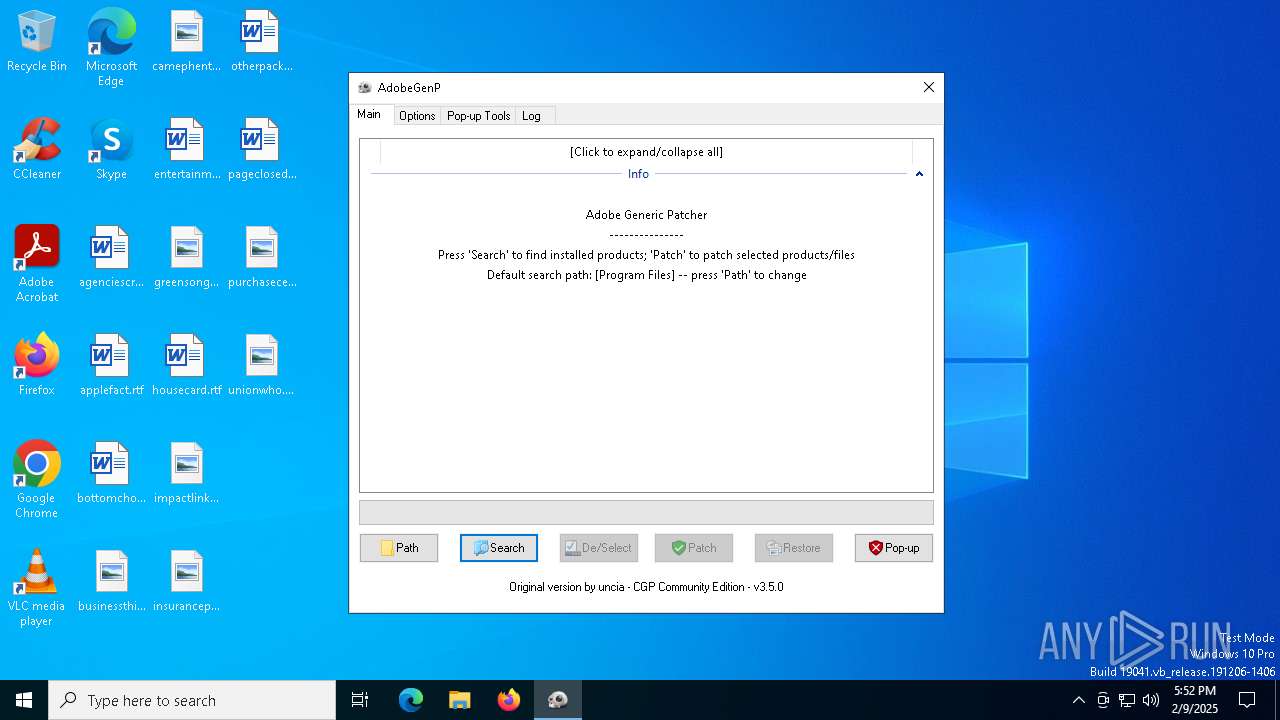
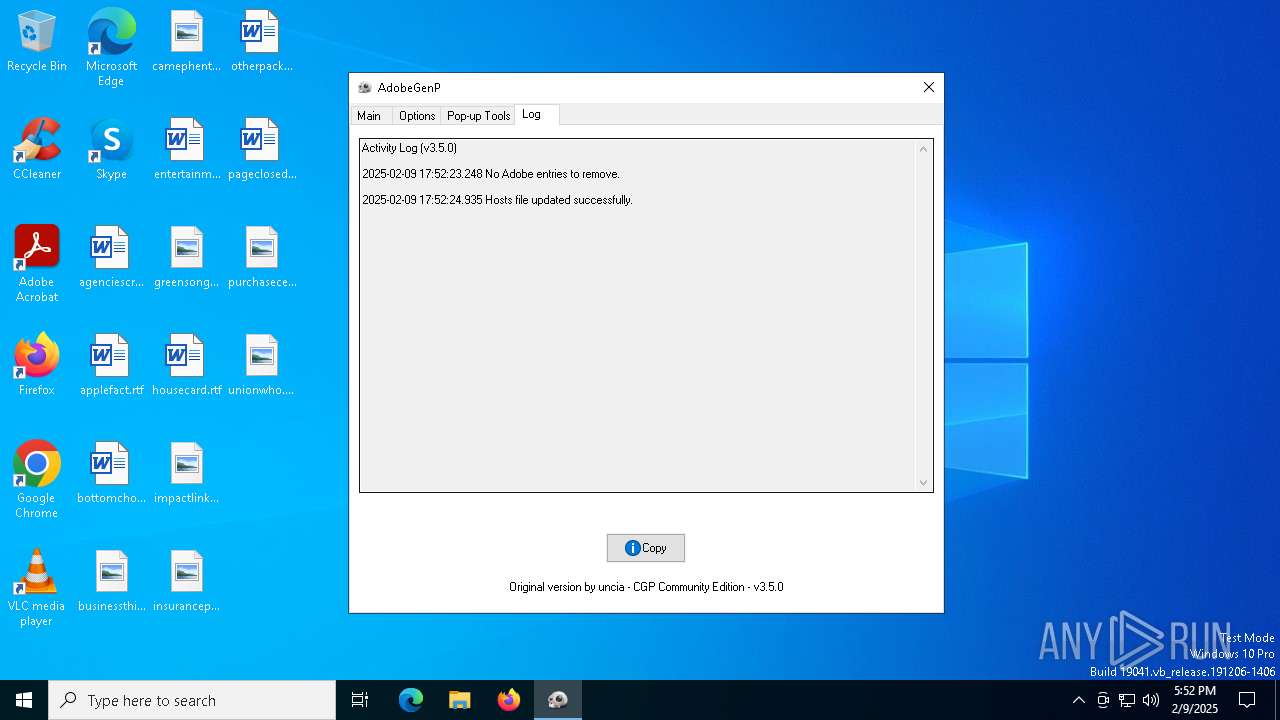
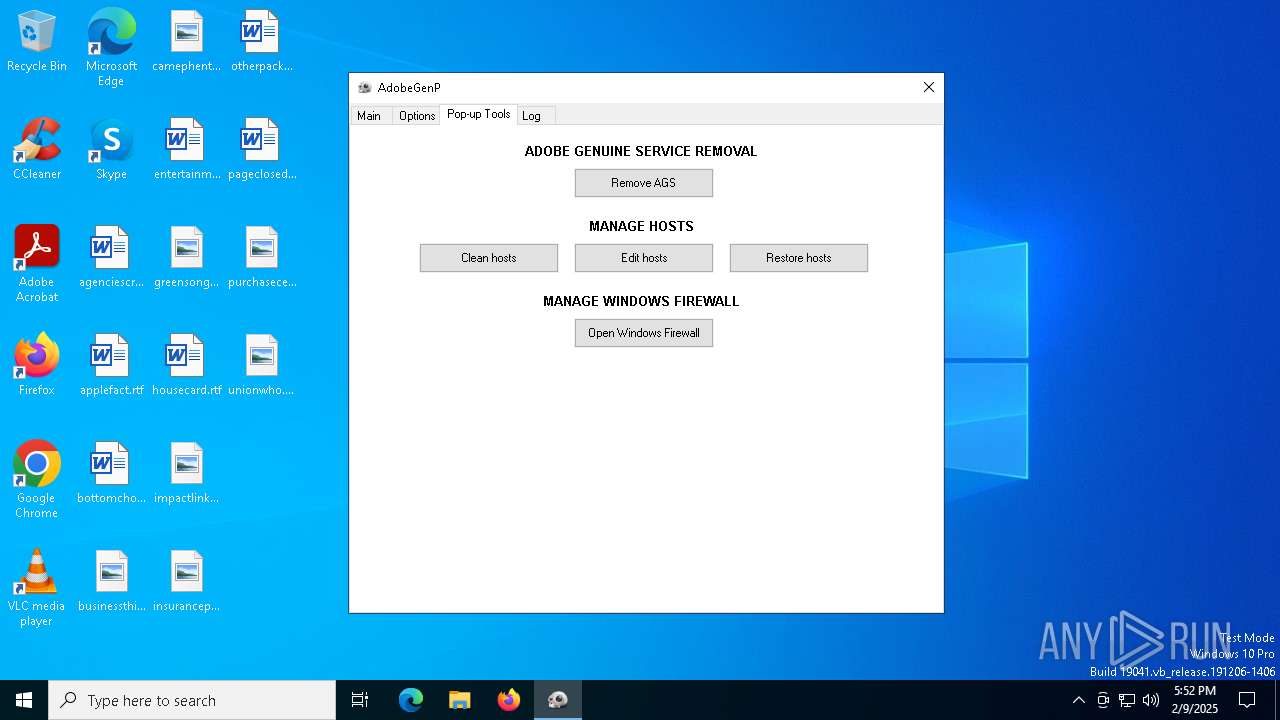
| File name: | GenP 3.5.0.exe |
| Full analysis: | https://app.any.run/tasks/a346181e-704b-49f8-827b-67a918ba073c |
| Verdict: | Malicious activity |
| Analysis date: | February 09, 2025, 17:52:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 362A9B5AB6C70AFF8C686FD35602E999 |
| SHA1: | 0CAD509C5E822A384198AEC3A5B4D78D7C4E1CC6 |
| SHA256: | 079E33038561CB759CA9EEBCB74C97C435593469509DFC90CC07A4CA80A2CCDC |
| SSDEEP: | 24576:Pp+/4UURxUruRrax70p5O9Qx+aAm0vYRO8tSp/QTbV4n2:PE/XUraxm5O9QMal0QRO8tSp/QTbV4n |
MALICIOUS
No malicious indicators.SUSPICIOUS
ADOBEGENP mutex has been found
- GenP 3.5.0.exe (PID: 6412)
Checks Windows Trust Settings
- GenP 3.5.0.exe (PID: 6412)
Creates files in the driver directory
- GenP 3.5.0.exe (PID: 6412)
There is functionality for taking screenshot (YARA)
- GenP 3.5.0.exe (PID: 6412)
Reads security settings of Internet Explorer
- GenP 3.5.0.exe (PID: 6412)
INFO
The sample compiled with english language support
- GenP 3.5.0.exe (PID: 6412)
Reads mouse settings
- GenP 3.5.0.exe (PID: 6412)
Reads the computer name
- GenP 3.5.0.exe (PID: 6412)
Creates files or folders in the user directory
- GenP 3.5.0.exe (PID: 6412)
Create files in a temporary directory
- GenP 3.5.0.exe (PID: 6412)
Reads the machine GUID from the registry
- GenP 3.5.0.exe (PID: 6412)
Checks proxy server information
- GenP 3.5.0.exe (PID: 6412)
Checks supported languages
- GenP 3.5.0.exe (PID: 6412)
The process uses AutoIt
- GenP 3.5.0.exe (PID: 6412)
Reads the software policy settings
- GenP 3.5.0.exe (PID: 6412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:02:04 22:16:57+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.16 |
| CodeSize: | 734208 |
| InitializedDataSize: | 533504 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2549c |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.5.0.0 |
| ProductVersionNumber: | 3.5.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileVersion: | 3.5.0.0 |
| Comments: | AdobeGenP |
| FileDescription: | Adobe Generic Patcher |
| ProductName: | AdobeGenP |
| ProductVersion: | 3.5.0 |
| CompanyName: | AdobeGenp |
| LegalCopyright: | AdobeGenP 2025 |
| LegalTradeMarks: | AdobeGenP 2025 |
Total processes
125
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6280 | "C:\Users\admin\Desktop\GenP 3.5.0.exe" | C:\Users\admin\Desktop\GenP 3.5.0.exe | — | explorer.exe | |||||||||||
User: admin Company: AdobeGenp Integrity Level: MEDIUM Description: Adobe Generic Patcher Exit code: 3221226540 Version: 3.5.0.0 Modules
| |||||||||||||||
| 6412 | "C:\Users\admin\Desktop\GenP 3.5.0.exe" | C:\Users\admin\Desktop\GenP 3.5.0.exe | explorer.exe | ||||||||||||
User: admin Company: AdobeGenp Integrity Level: HIGH Description: Adobe Generic Patcher Version: 3.5.0.0 Modules
| |||||||||||||||
Total events
624
Read events
621
Write events
3
Delete events
0
Modification events
| (PID) Process: | (6412) GenP 3.5.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6412) GenP 3.5.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6412) GenP 3.5.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
1
Suspicious files
5
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6412 | GenP 3.5.0.exe | C:\Users\admin\Desktop\config.ini | text | |
MD5:3D6ACE120BB21EF7661F9BAA3A828BA0 | SHA256:0BC155DC39DD420893CE4228EAD4066D3C54A5CFE09C40AA3B6183FC0F4D68E6 | |||
| 6412 | GenP 3.5.0.exe | C:\Users\admin\AppData\Local\Temp\aut52F5.tmp | binary | |
MD5:4858736902FBC470F96AAEE483EFDFD2 | SHA256:D3569ED2DFD800B44D2F11303D522EDFB2BD1E094A7EC6E081913A552FB289E5 | |||
| 6412 | GenP 3.5.0.exe | C:\Users\admin\AppData\Local\Temp\~gqaupha.tmp | text | |
MD5:34B8B33A6E33B6BED9BE3F42A3F7F2F8 | SHA256:FBFB9621CE0215E9589BACBD4C9AB63B6432ADF908153BC4885E4E70870F855F | |||
| 6412 | GenP 3.5.0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:FCC889BD10D5C1077294572204CEE940 | SHA256:E27AC7FA9D0A20A6ADCDB33BB790288C63D55AF3411B05162D872000C8E3B424 | |||
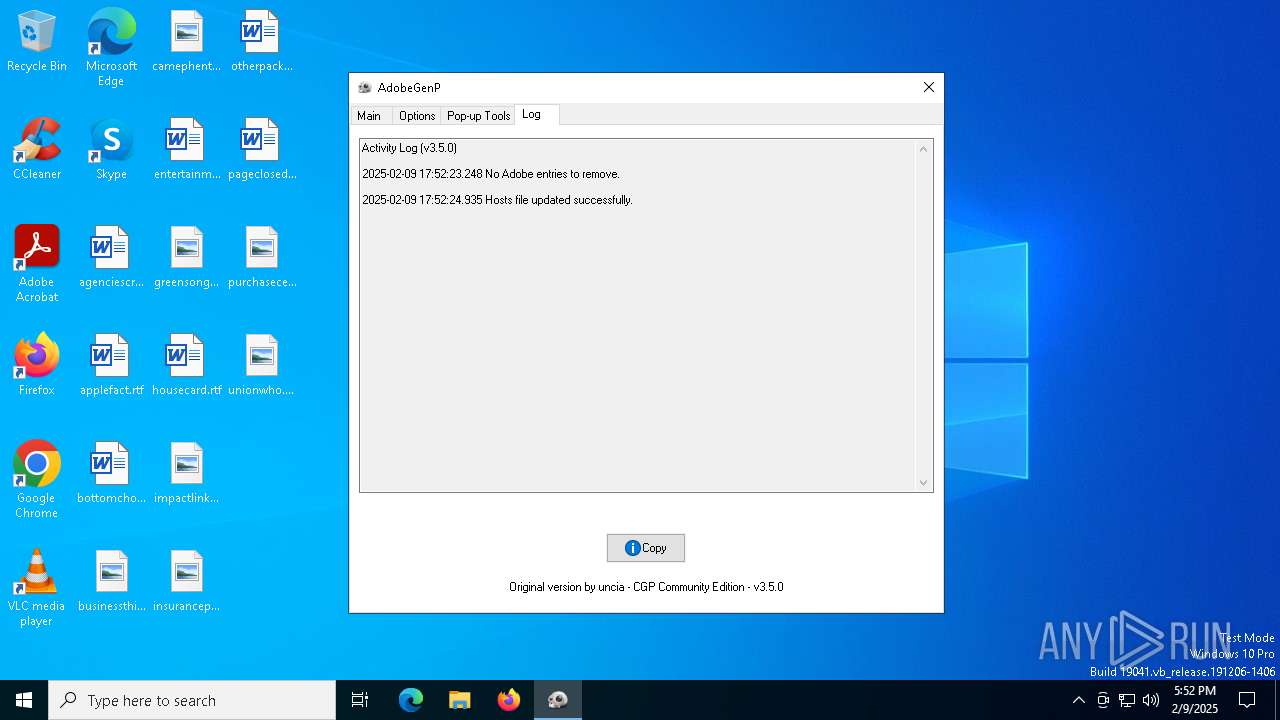
| 6412 | GenP 3.5.0.exe | C:\Windows\System32\drivers\etc\hosts.bak | text | |
MD5:C40F0E533A52F202035621D27E732F5A | SHA256:408442168118E82FAF7D419AA4F0D8FA04F45A5E6D0E7065A9CDC723782C5AE3 | |||
| 6412 | GenP 3.5.0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 6412 | GenP 3.5.0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:C9BE626E9715952E9B70F92F912B9787 | SHA256:C13E8D22800C200915F87F71C31185053E4E60CA25DE2E41E160E09CD2D815D4 | |||
| 6412 | GenP 3.5.0.exe | C:\Windows\System32\drivers\etc\hosts | text | |
MD5:503D9B65295A3AF0494704F6F0C47CB5 | SHA256:E6F5752C3AAE7D7D69AC9574A7C89D920A882CAF0CE18A0FBB2BA1895154D8FC | |||
| 6412 | GenP 3.5.0.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\list[1].txt | text | |
MD5:34B8B33A6E33B6BED9BE3F42A3F7F2F8 | SHA256:FBFB9621CE0215E9589BACBD4C9AB63B6432ADF908153BC4885E4E70870F855F | |||
| 6412 | GenP 3.5.0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:37EF9E1157528A5587DF12824AE4C928 | SHA256:9303E2A5198F0E475EB2136CFF12D3B96B5D1C64FA330CF3B0BF7D07A0C89F8A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
30
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4516 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6504 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4516 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6412 | GenP 3.5.0.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6412 | GenP 3.5.0.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 92.123.104.59:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
a.dove.isdumb.one |
| unknown |
c.pki.goog |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |