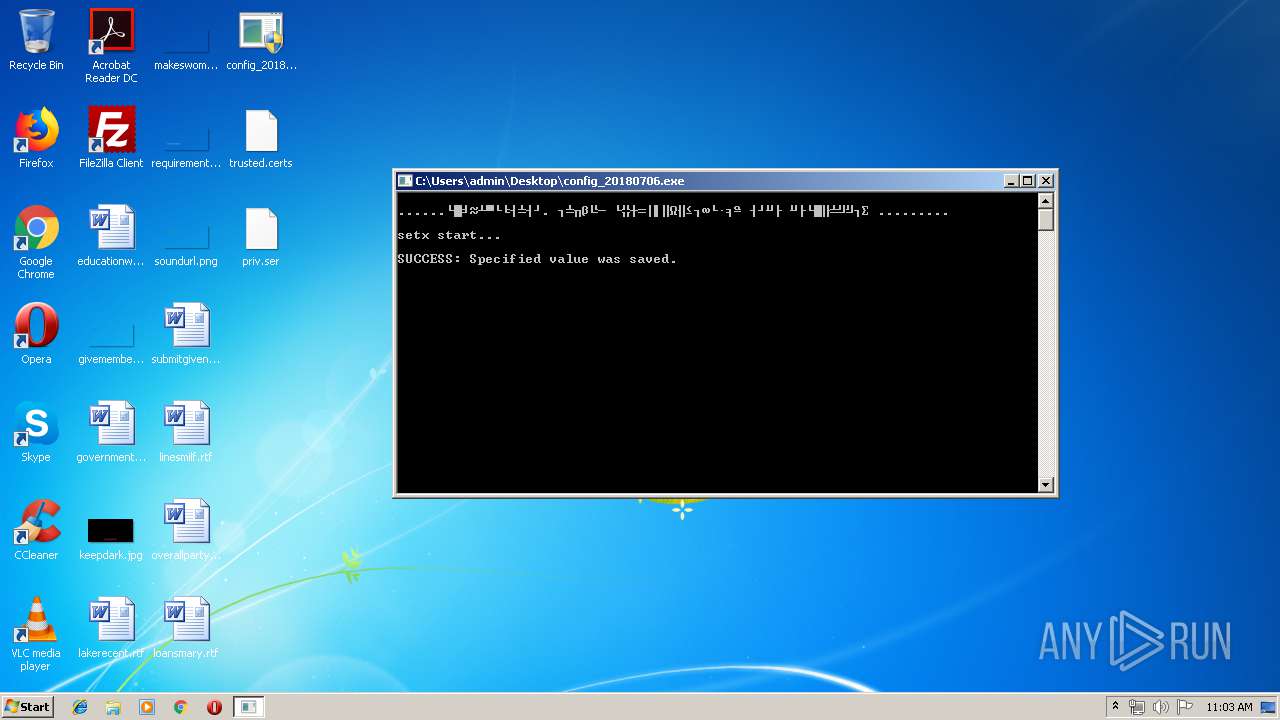
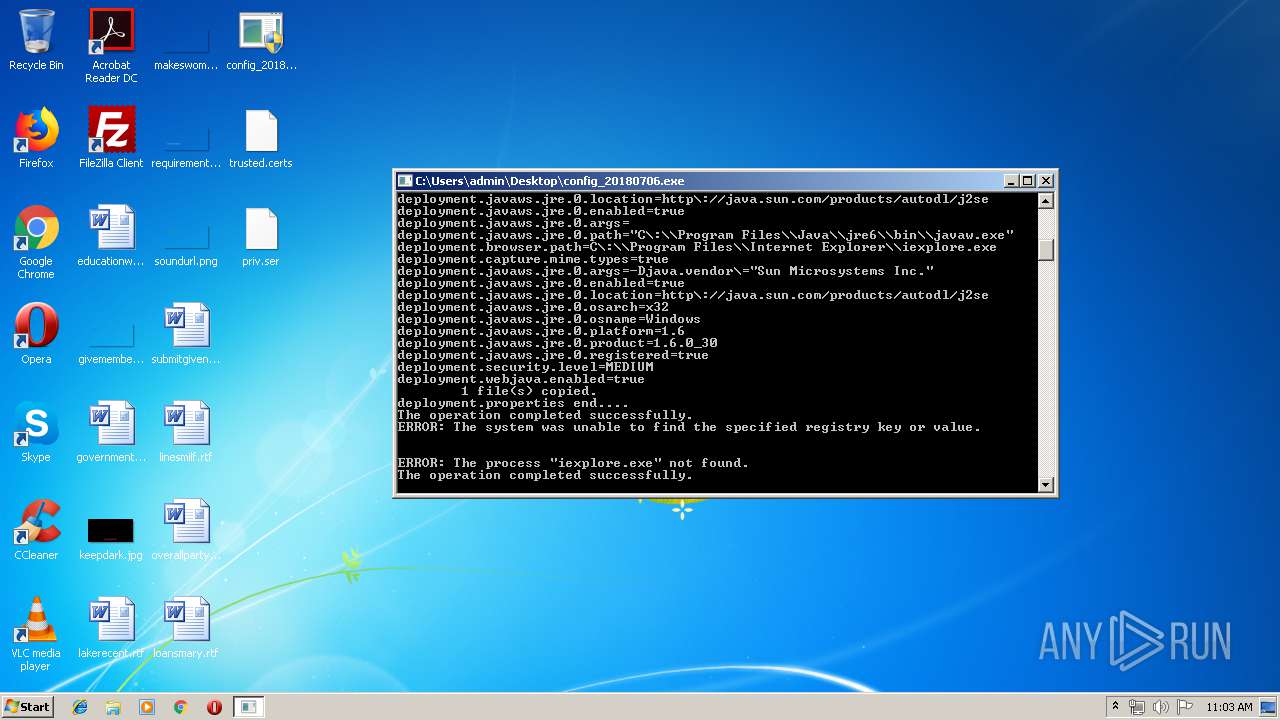
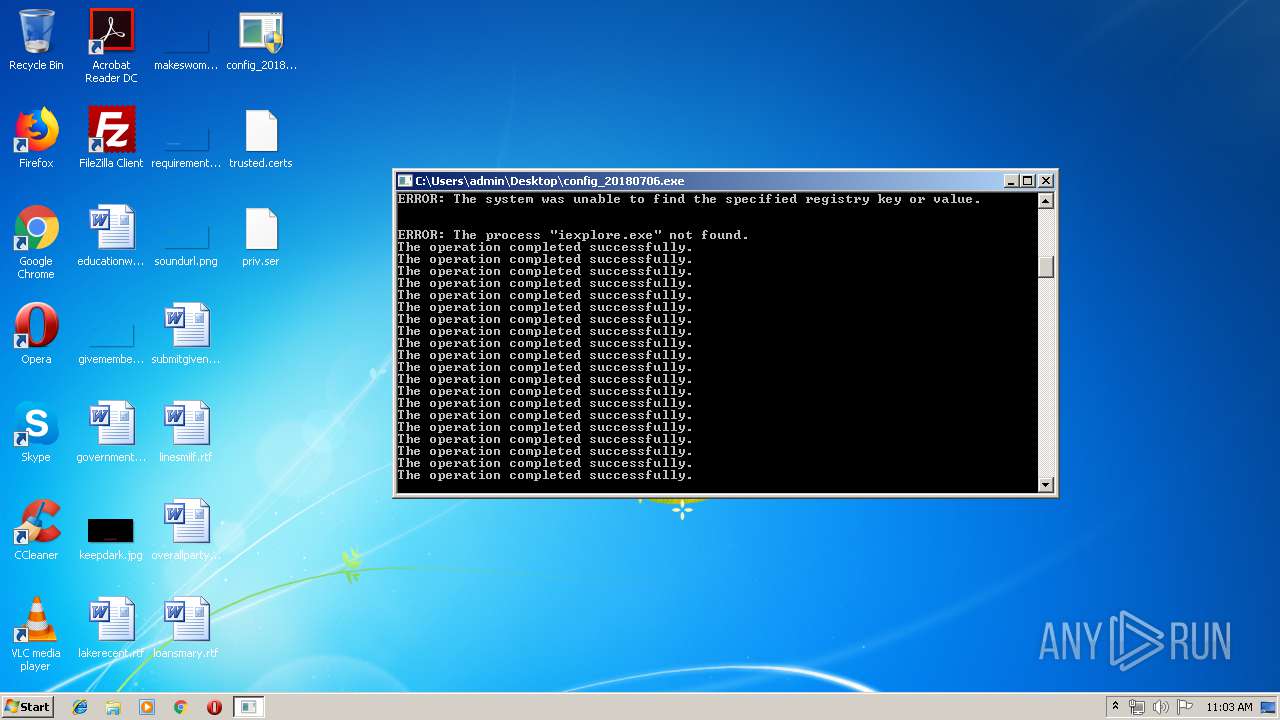
| File name: | config_20180706.exe |
| Full analysis: | https://app.any.run/tasks/80109919-f430-4dd2-956e-c9db9d893923 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2019, 10:02:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 00CBA2112C9EB46E844D8EAC43FA3B5A |
| SHA1: | FBEA05E845B072CC4A714D8344976F58A59BF037 |
| SHA256: | 077904AAFD3F9D33AF98ABB2125289B4E4B9711C52841E7B8A507CA8156E4DA6 |
| SSDEEP: | 1536:MVIn7vLAsry2eslLS8Ti1nQyd9O3jKVfO1HoHoSSq+0Elh6:MU/9+vstGGGFO9SzEi |
MALICIOUS
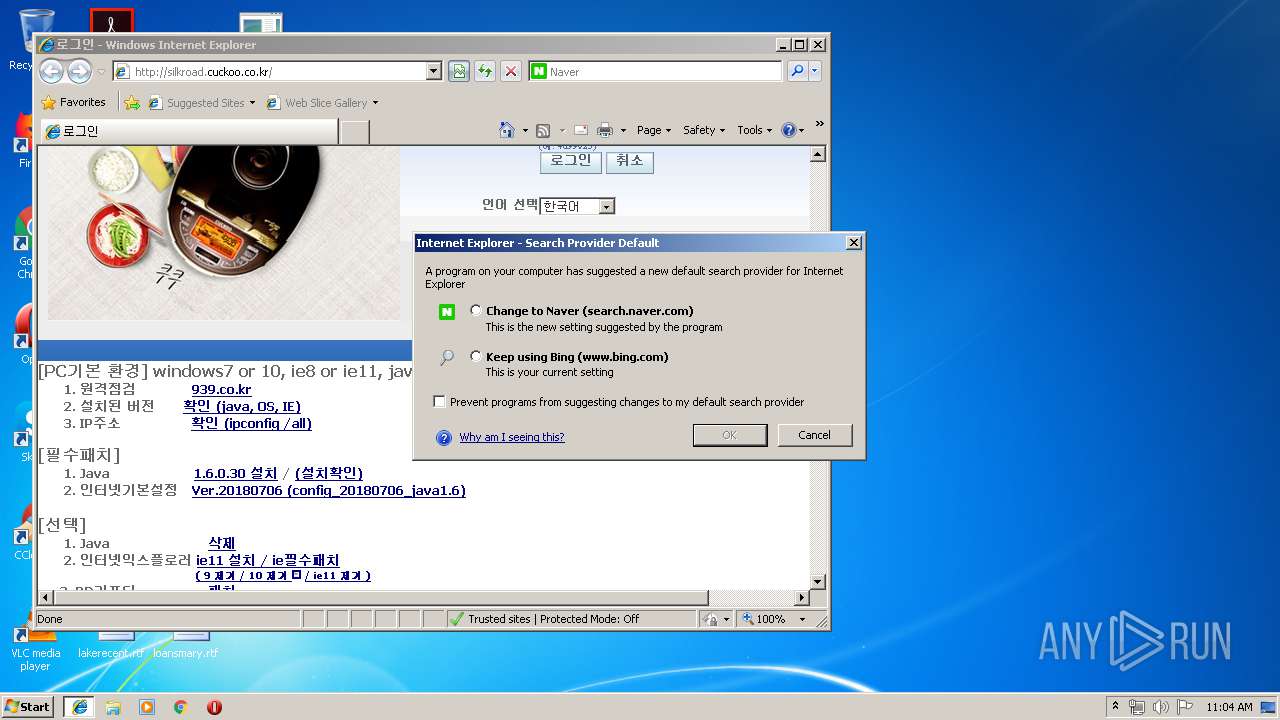
Changes internet zones settings
- reg.exe (PID: 960)
- reg.exe (PID: 324)
- reg.exe (PID: 920)
- reg.exe (PID: 3932)
- reg.exe (PID: 1336)
- reg.exe (PID: 2896)
- reg.exe (PID: 2068)
- reg.exe (PID: 4028)
- reg.exe (PID: 3984)
- reg.exe (PID: 2652)
- reg.exe (PID: 1972)
- reg.exe (PID: 3640)
- reg.exe (PID: 3360)
- reg.exe (PID: 3860)
- reg.exe (PID: 3120)
- reg.exe (PID: 2568)
- reg.exe (PID: 980)
- reg.exe (PID: 2904)
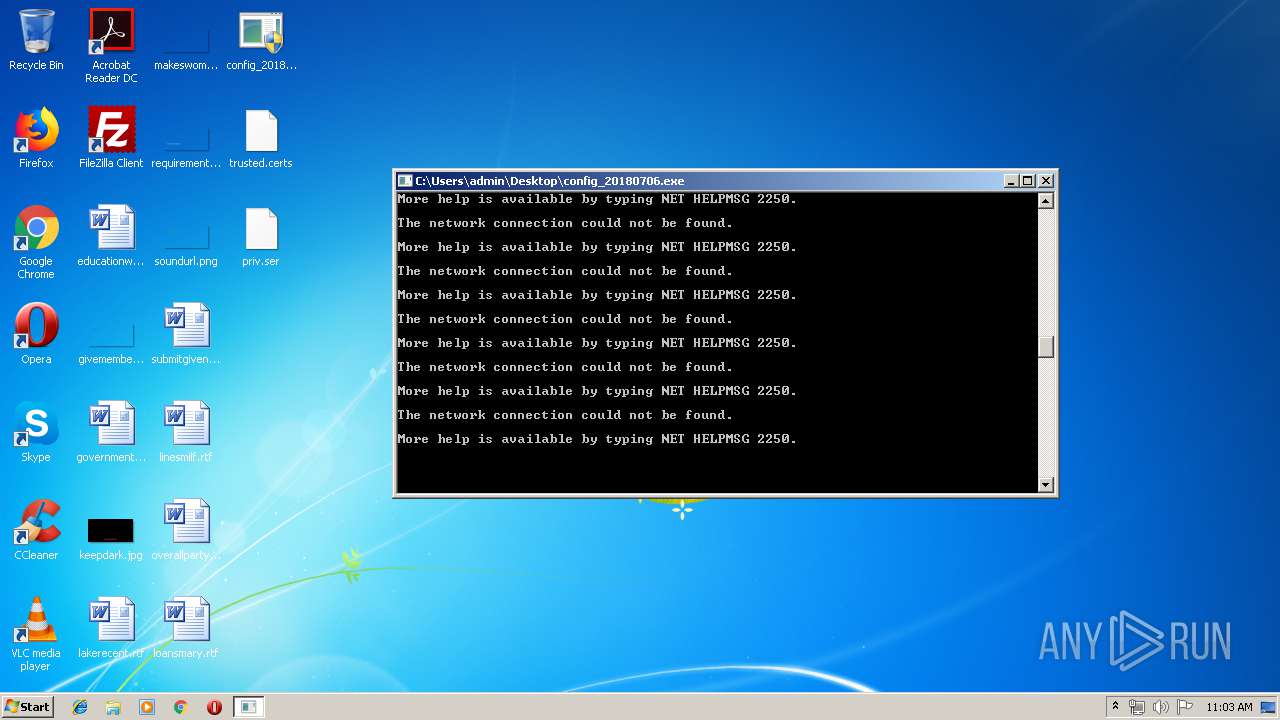
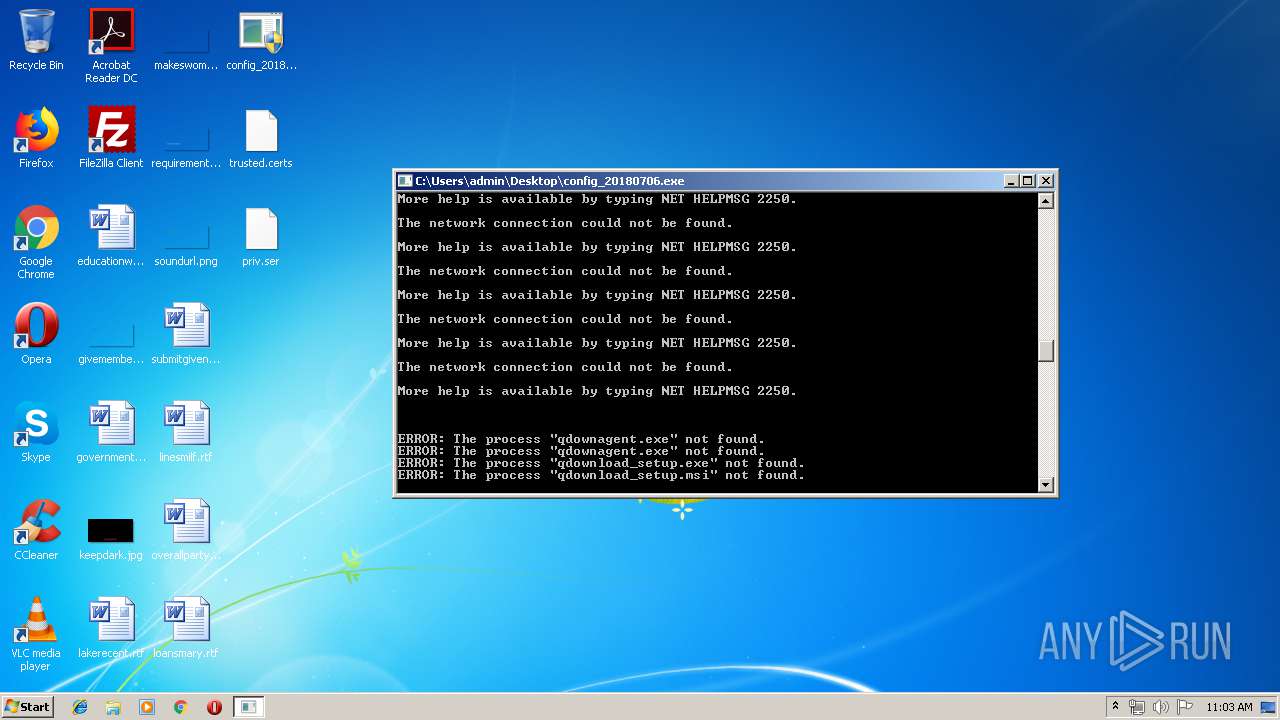
Starts NET.EXE for connection to shared resources
- cmd.exe (PID: 2504)
Starts NET.EXE for service management
- cmd.exe (PID: 2504)
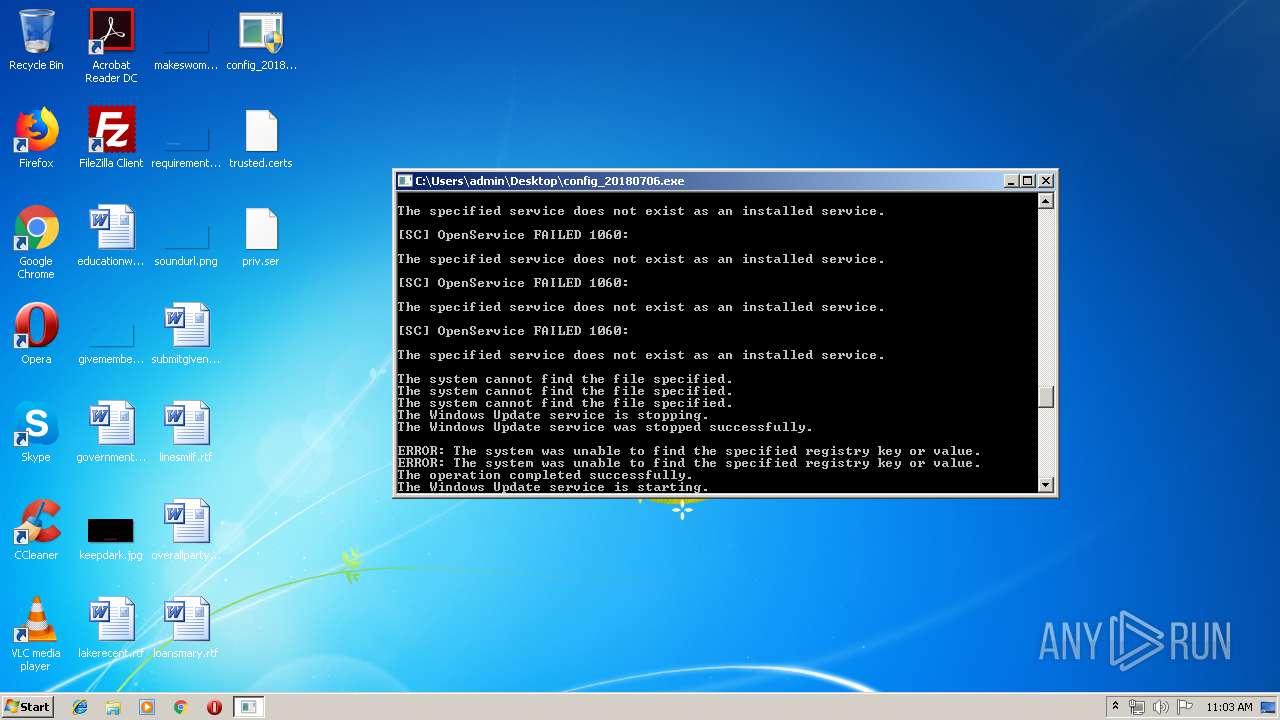
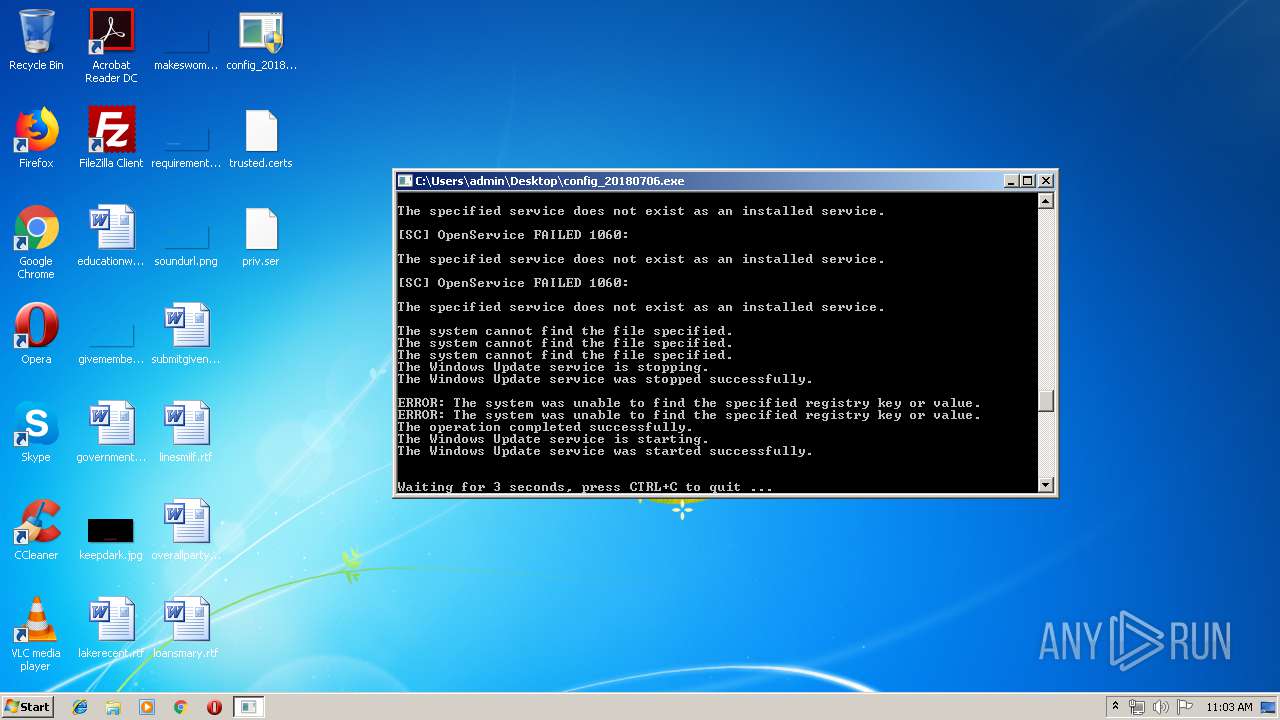
Uses NET.EXE to stop Windows Update service
- cmd.exe (PID: 2504)
SUSPICIOUS
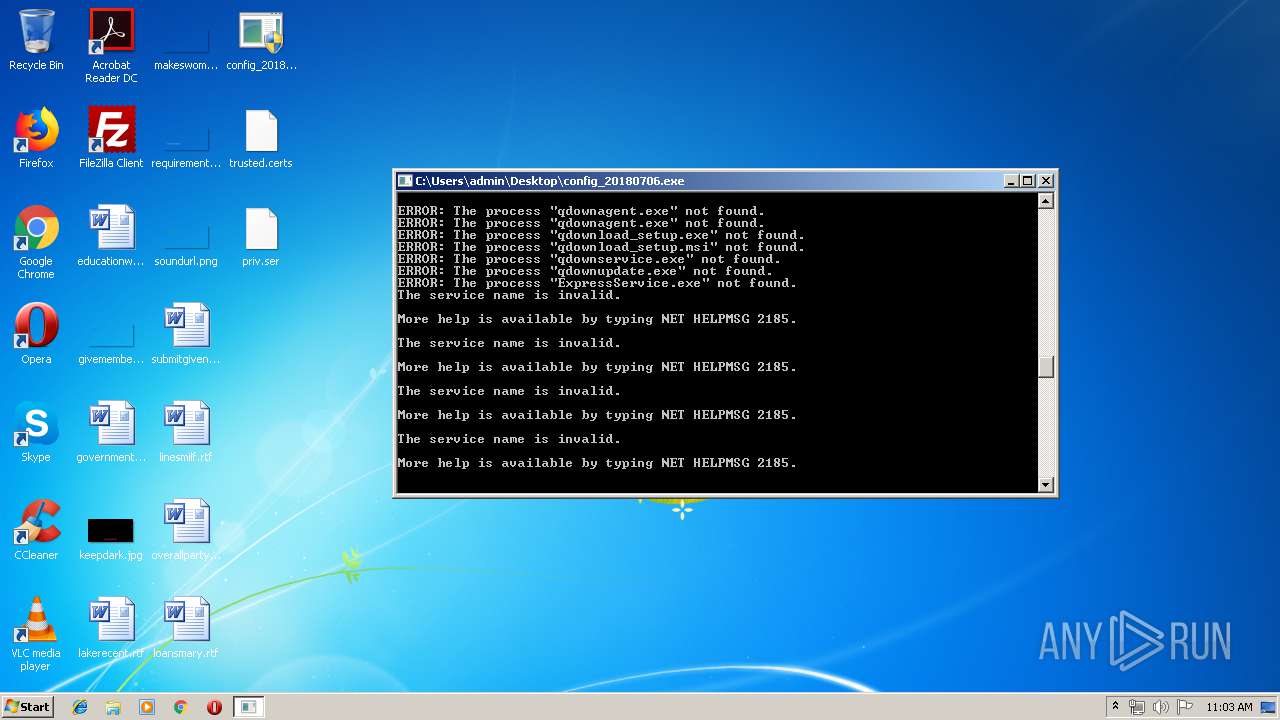
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2504)
Application launched itself
- cmd.exe (PID: 2504)
Starts CMD.EXE for commands execution
- config_20180706.exe (PID: 3688)
- cmd.exe (PID: 2504)
Creates files in the user directory
- xcopy.exe (PID: 3292)
- cmd.exe (PID: 2504)
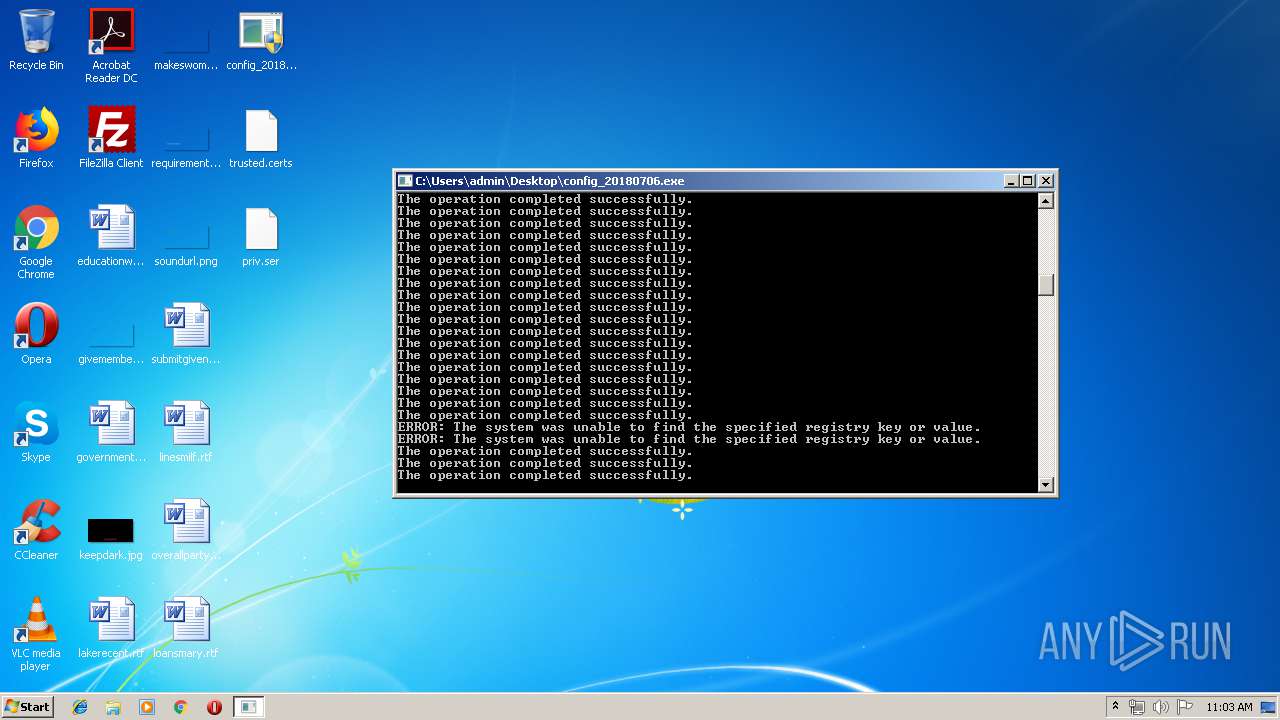
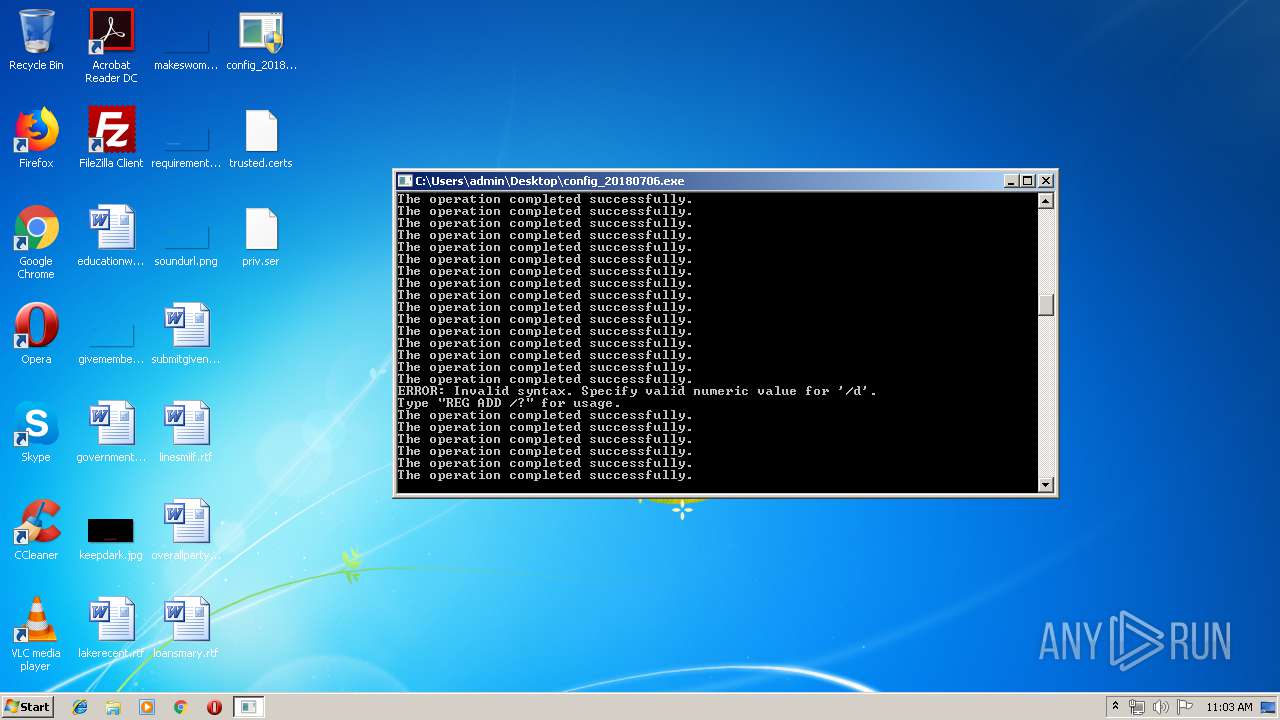
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2504)
Modifies the phishing filter of IE
- reg.exe (PID: 3504)
- reg.exe (PID: 1572)
Changes the started page of IE
- reg.exe (PID: 892)
Creates files in the Windows directory
- cmd.exe (PID: 2504)
Starts SC.EXE for service management
- cmd.exe (PID: 2504)
Starts Internet Explorer
- cmd.exe (PID: 2504)
INFO
Creates files in the user directory
- iexplore.exe (PID: 1020)
- iexplore.exe (PID: 3396)
Application launched itself
- iexplore.exe (PID: 1020)
Changes internet zones settings
- iexplore.exe (PID: 1020)
Reads internet explorer settings
- iexplore.exe (PID: 3396)
Reads Internet Cache Settings
- iexplore.exe (PID: 3396)
- iexplore.exe (PID: 1020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable PureBasic (generic) (58) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (17.2) |
| .exe | | | Win64 Executable (generic) (15.2) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.6) |
| .exe | | | Win32 Executable (generic) (2.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:01:18 11:10:31+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 61440 |
| InitializedDataSize: | 23552 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 18-Jan-2017 10:10:31 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 18-Jan-2017 10:10:31 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.code | 0x00001000 | 0x000035B7 | 0x00003600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.26514 |
.text | 0x00005000 | 0x0000B8BB | 0x0000BA00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.57376 |
.rdata | 0x00011000 | 0x0000098E | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.61645 |
.data | 0x00012000 | 0x00001C58 | 0x00001600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.51551 |
.rsrc | 0x00014000 | 0x00003B64 | 0x00003C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.74554 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.08821 | 672 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
18E747D2FAC6E4DDDF94C2F42BA6D6F3 | 7.9775 | 8444 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
31E81A43F23E3702349C634706F5C27B | 5.32307 | 44 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
40C70B0595CC3EAAD8DE9429D807ED50 | 7.24058 | 5316 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
6ABBCDA4AE3D0AF1CDD41FD12CB16D57 | 5.16993 | 36 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
7A811C37905472EE8758C73DE1F5D192 | 0.918296 | 6 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
Imports
COMCTL32.DLL |
GDI32.DLL |
KERNEL32.dll |
MSVCRT.dll |
OLE32.DLL |
SHELL32.DLL |
SHLWAPI.DLL |
USER32.DLL |
Total processes
174
Monitored processes
136
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | net use /d n: | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 116 | reg add "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings" /v UrlEncoding /t reg_dword /d 0 /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 324 | reg add "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2" /v 1409 /t REG_DWORD /d 3 /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 328 | reg add "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\cuckoo.co.kr" /v "http" /t REG_DWORD /d 2 /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
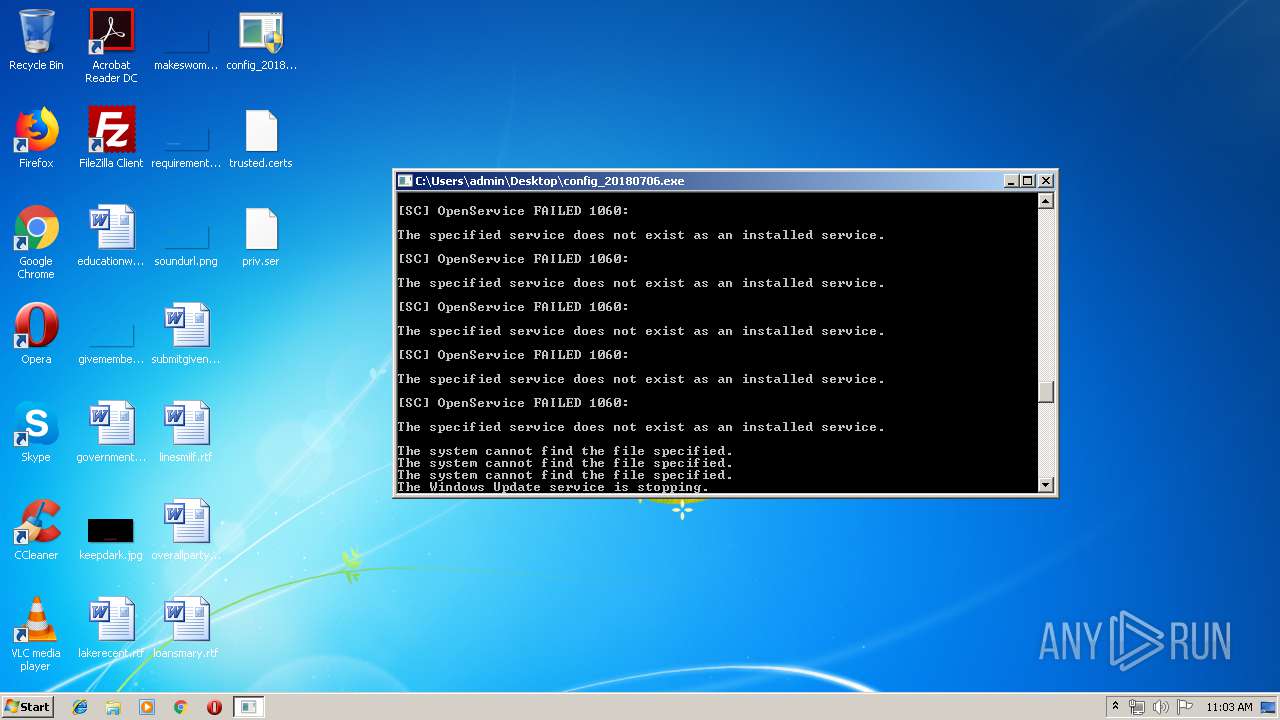
| 480 | sc delete "QuickDownload Agent" | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 536 | timeout /nobreak /t 3 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 704 | net start wuauserv | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 724 | xcopy /y priv.ser "C:\Users\admin\AppData\Roaming\..\locallow\.wt" | C:\Windows\system32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 856 | net use /d \\172.10.0.2000\d$ | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 856 | C:\Windows\system32\net1 start wuauserv | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
510
Read events
377
Write events
130
Delete events
3
Modification events
| (PID) Process: | (3380) setx.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager\Environment |
| Operation: | write | Name: | JAVA_TOOL_OPTIONS |
Value: -Djava.vendor='Sun Microsystems Inc.' | |||
| (PID) Process: | (908) setx.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager\Environment |
| Operation: | write | Name: | JAVA_HOME |
Value: C:\Program Files\java\jre6 | |||
| (PID) Process: | (2688) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\BrowserEmulation\ClearableListData |
| Operation: | write | Name: | UserFilter |
Value: 411F00005308ADBA020000006200000001000000020000000C000000EBB23155DF1FD301010000000C006300750063006B006F006F002E0063006F002E006B0072000C00000021BDA49A5E20D301010000000D006300750063006B006F006F002E0064006F006D00610069006E00 | |||
| (PID) Process: | (1336) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2 |
| Operation: | write | Name: | 1809 |
Value: 3 | |||
| (PID) Process: | (4024) reg.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\Java Update\Policy |
| Operation: | write | Name: | EnableAutoUpdateCheck |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000CC700B22821A48429B4B3FF2B5ABB4EC0000000002000000000003660000C000000010000000D7F5D95A87E042F5C72CCAD82FC304EA0000000004800000A0000000100000007DA00FEDF908B9DE9489A7731C1A842B08000000A8FEE4BD7990A5CC14000000CC6BA7DFDFCA71FC5C1FBBB09D1D65DB40FE04EA | |||
| (PID) Process: | (324) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2 |
| Operation: | write | Name: | 1409 |
Value: 3 | |||
| (PID) Process: | (2896) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3 |
| Operation: | write | Name: | 1409 |
Value: 3 | |||
| (PID) Process: | (920) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2 |
| Operation: | write | Name: | 1001 |
Value: 0 | |||
| (PID) Process: | (1972) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3 |
| Operation: | write | Name: | 1001 |
Value: 1 | |||
| (PID) Process: | (3932) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2 |
| Operation: | write | Name: | 1004 |
Value: 1 | |||
Executable files
0
Suspicious files
3
Text files
55
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2344 | xcopy.exe | C:\Users\admin\AppData\.wt\priv.ser | binary | |
MD5:— | SHA256:— | |||
| 3292 | xcopy.exe | C:\Users\admin\AppData\Roaming\Sun\Java\Deployment\security\trusted.certs | jks | |
MD5:— | SHA256:— | |||
| 724 | xcopy.exe | C:\Users\admin\AppData\locallow\.wt\priv.ser | binary | |
MD5:— | SHA256:— | |||
| 3688 | config_20180706.exe | C:\Users\admin\Desktop\priv.ser | binary | |
MD5:— | SHA256:— | |||
| 2504 | cmd.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\deployment.properties.bak | text | |
MD5:— | SHA256:— | |||
| 2504 | cmd.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\deployment.properties | text | |
MD5:— | SHA256:— | |||
| 2504 | cmd.exe | C:\Users\admin\AppData\Roaming\Sun\Java\Deployment\deployment.properties | text | |
MD5:— | SHA256:— | |||
| 2504 | cmd.exe | C:\Windows\ipp.bat | text | |
MD5:— | SHA256:— | |||
| 2504 | cmd.exe | C:\wsus_id_reset.log | text | |
MD5:— | SHA256:— | |||
| 3688 | config_20180706.exe | C:\Users\admin\Desktop\trusted.certs | jks | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
21
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
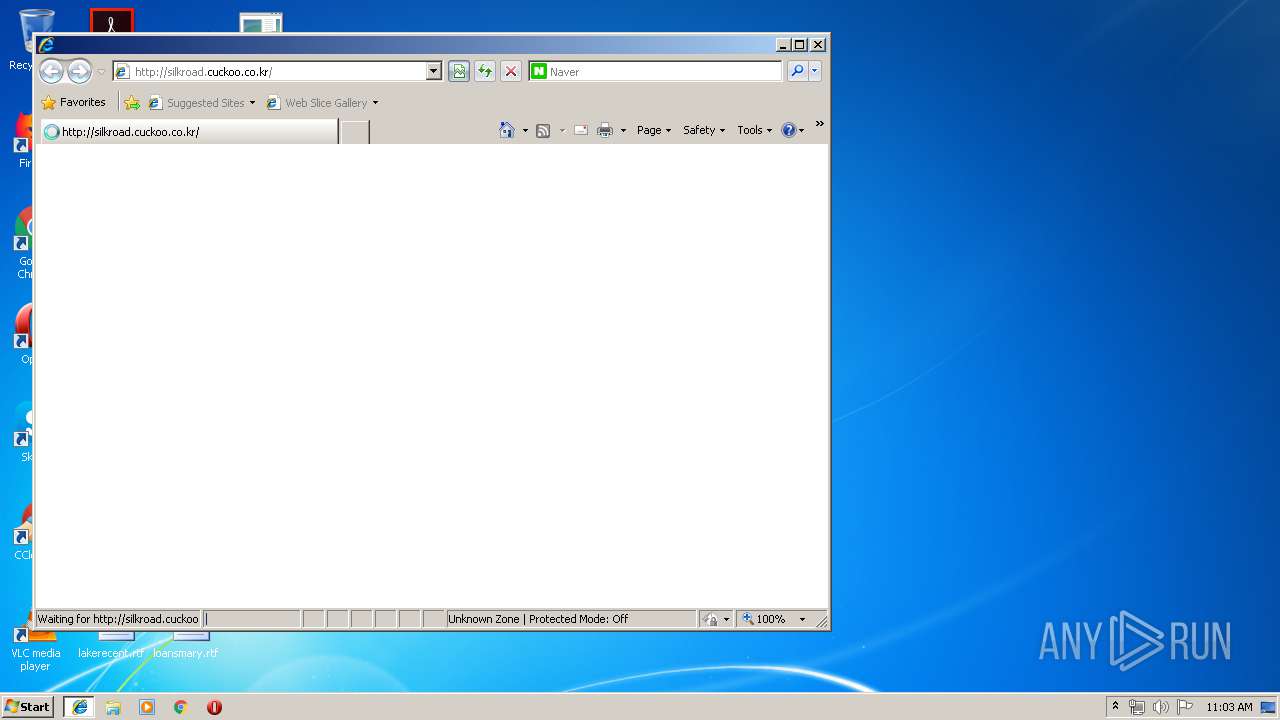
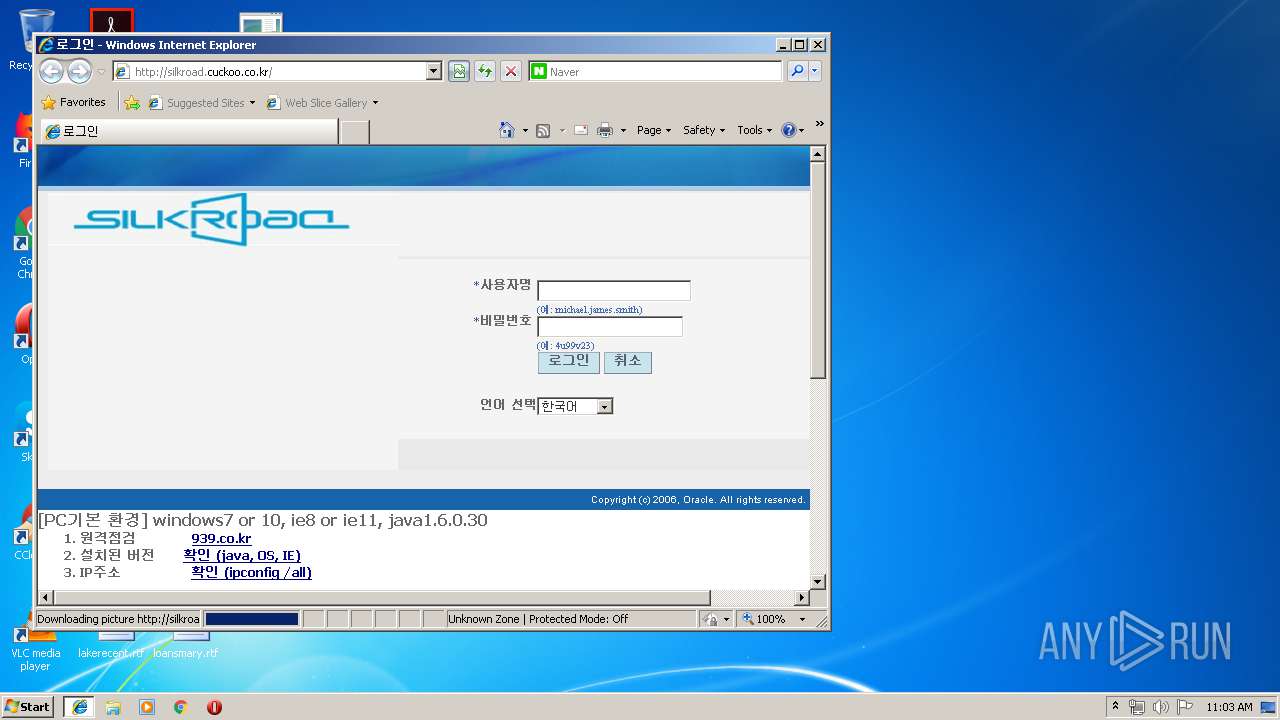
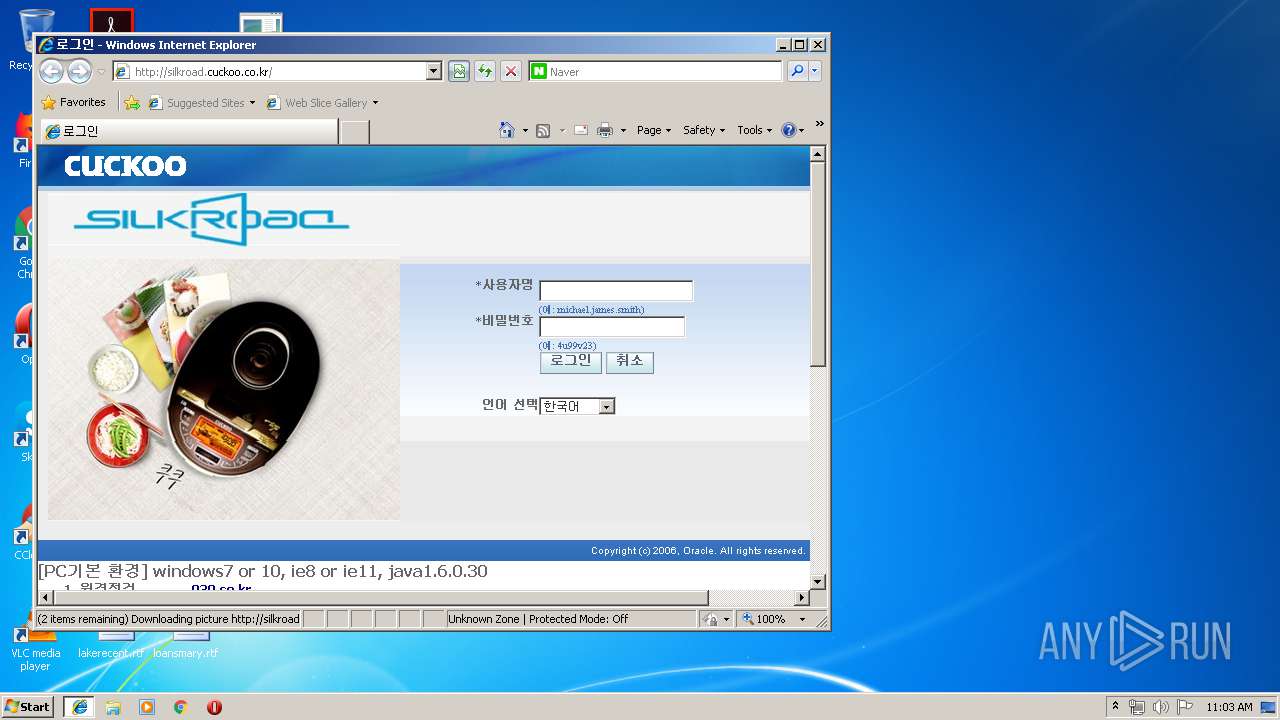
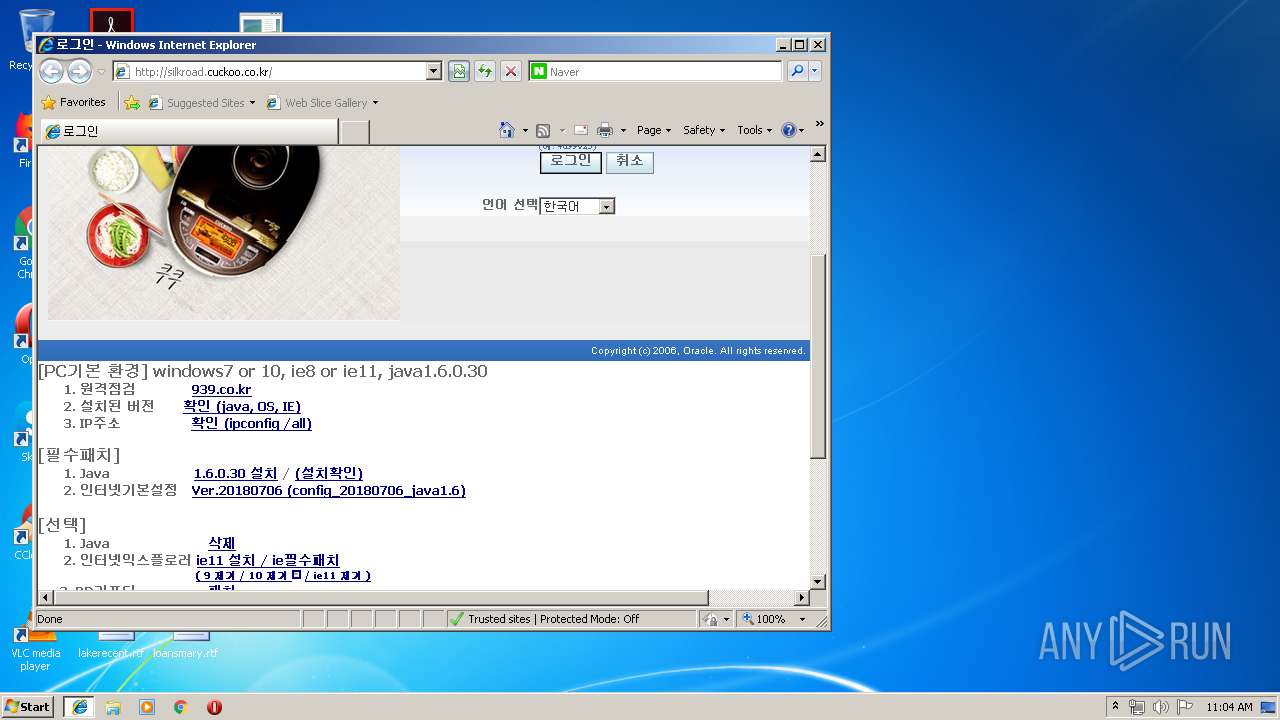
3396 | iexplore.exe | GET | — | 210.105.131.211:80 | http://silkroad.cuckoo.co.kr/ohs_images/lightBlue_back.jpg | KR | — | — | suspicious |
3396 | iexplore.exe | GET | — | 210.105.131.211:80 | http://silkroad.cuckoo.co.kr/ohs_images/swanEXTN-custom-2_3_6_5-ko-ie-windows.css | KR | — | — | suspicious |
3396 | iexplore.exe | GET | 200 | 210.105.131.211:80 | http://silkroad.cuckoo.co.kr/ohs_images/t.htm | KR | html | 29 b | suspicious |
3396 | iexplore.exe | GET | 200 | 210.105.131.211:80 | http://silkroad.cuckoo.co.kr/ | KR | html | 16.9 Kb | suspicious |
3396 | iexplore.exe | GET | 200 | 210.105.131.211:80 | http://silkroad.cuckoo.co.kr/ohs_images/topLines.gif | KR | image | 9.66 Kb | suspicious |
3396 | iexplore.exe | GET | 200 | 210.105.131.211:80 | http://silkroad.cuckoo.co.kr/ohs_images/people.jpg | KR | image | 971 b | suspicious |
3396 | iexplore.exe | GET | 200 | 210.105.131.211:80 | http://silkroad.cuckoo.co.kr/blank.html | KR | html | 107 b | suspicious |
3396 | iexplore.exe | GET | 200 | 210.105.131.211:80 | http://silkroad.cuckoo.co.kr/ohs_images/FNDSSCORP.gif | KR | image | 322 b | suspicious |
3396 | iexplore.exe | GET | 200 | 210.105.131.211:80 | http://silkroad.cuckoo.co.kr/ohs_images/globalTop.jpg | KR | image | 19.3 Kb | suspicious |
3396 | iexplore.exe | GET | 200 | 210.105.131.211:80 | http://silkroad.cuckoo.co.kr/ohs_images/silkroad.jpg | KR | image | 1.04 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3396 | iexplore.exe | 210.105.131.211:80 | silkroad.cuckoo.co.kr | Korea Telecom | KR | suspicious |
1020 | iexplore.exe | 23.210.249.75:80 | www.naver.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
silkroad.cuckoo.co.kr |
| suspicious |
www.naver.com |
| whitelisted |