| File name: | 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.7z |
| Full analysis: | https://app.any.run/tasks/63483db7-b53b-40c9-9e25-b25ebdae5a40 |
| Verdict: | Malicious activity |
| Analysis date: | May 29, 2025, 11:39:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | A0B696053E3143CDF90FD7EF1CFF4AFF |
| SHA1: | 1EC97C920AF09C8CDDF2C05A083E7615492F14FC |
| SHA256: | 0769DE18481BEDB05E7B211869C8763D61F701E595518626FE37E03559C2813E |
| SSDEEP: | 1536:yw0cbK4cngTocL5qHgIZvBX+vtEM6Qg0lKYpY/xQTWXyXJLZc4xYB9f3:KcbPuQug+vByEM6p0l7uZQhXJt7eL3 |
MALICIOUS
Create files in the Startup directory
- 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe (PID: 5204)
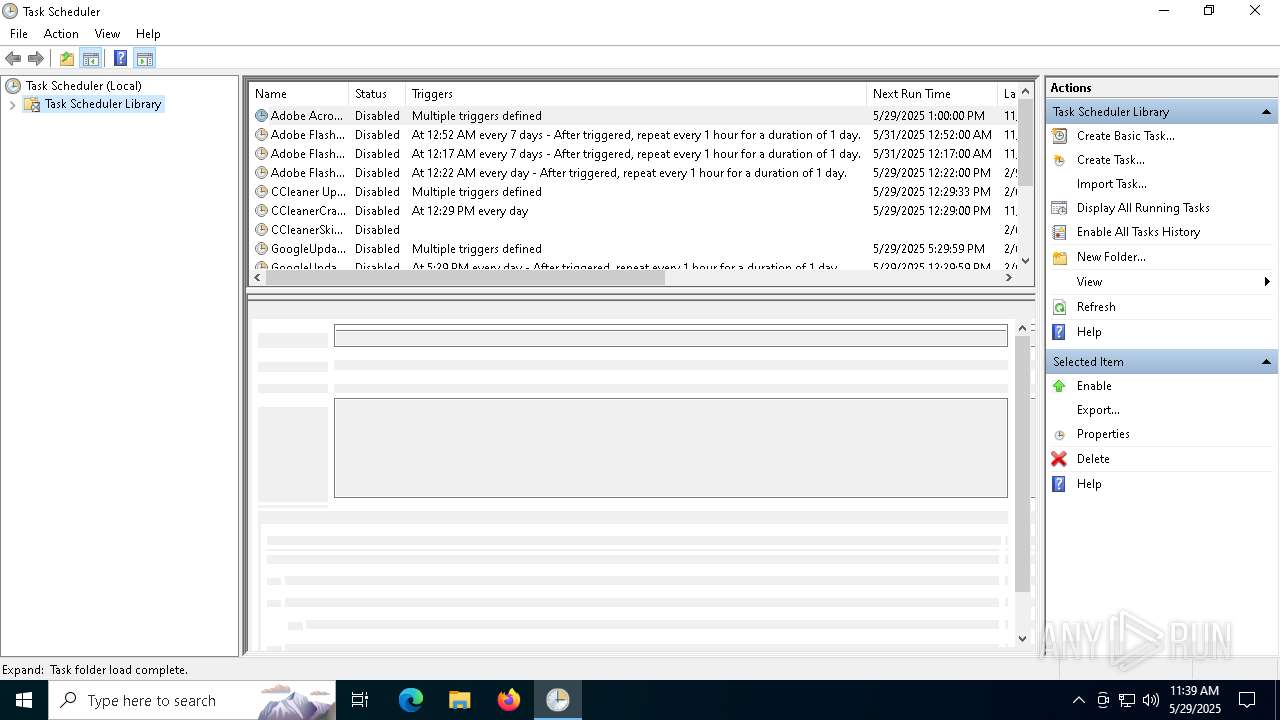
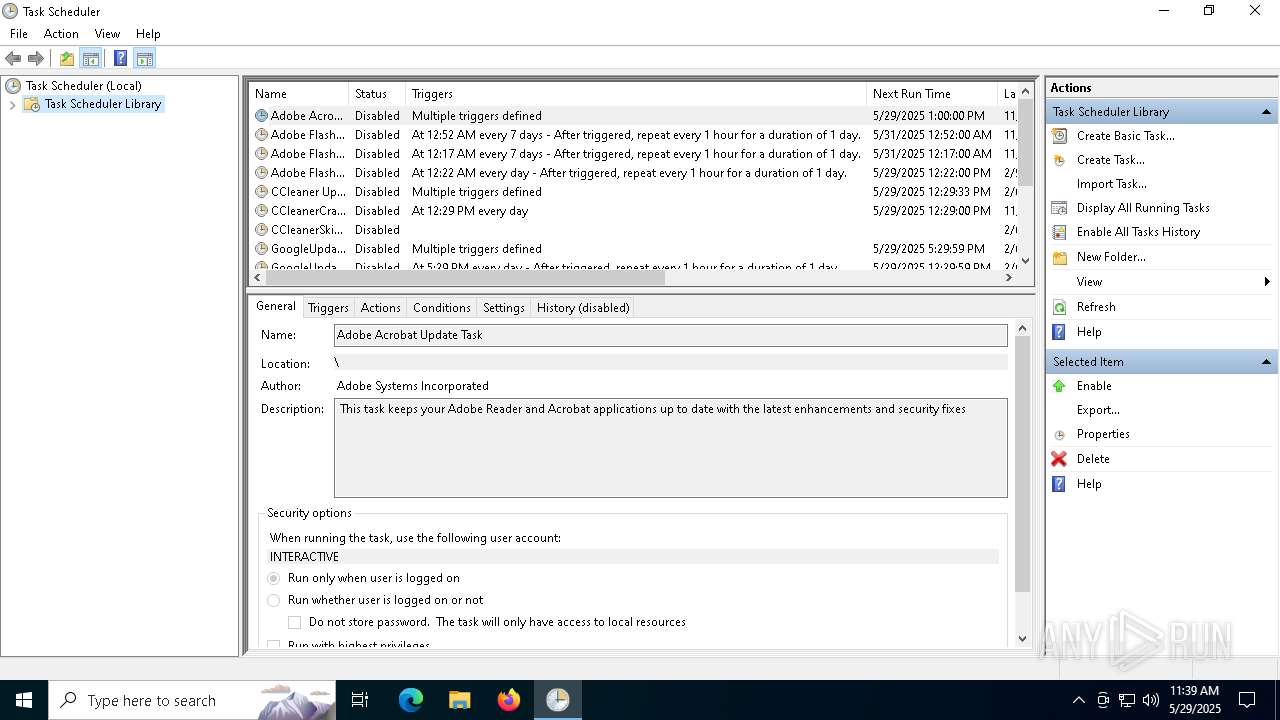
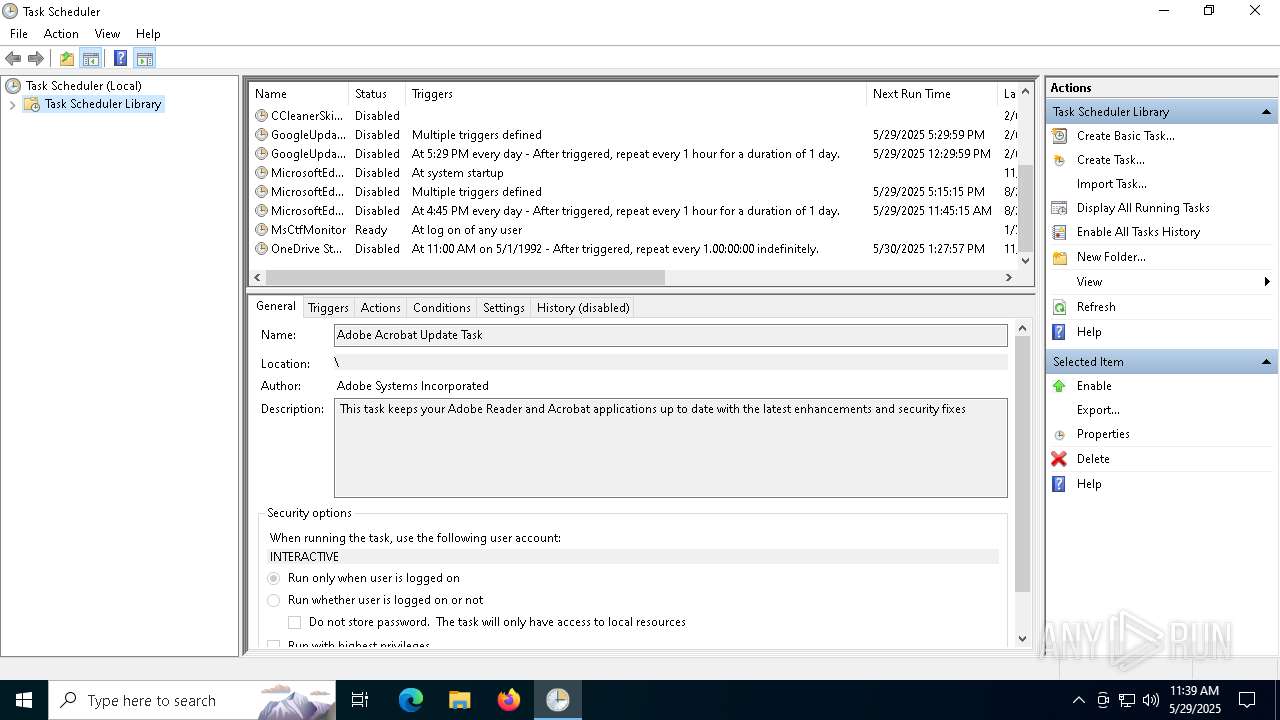
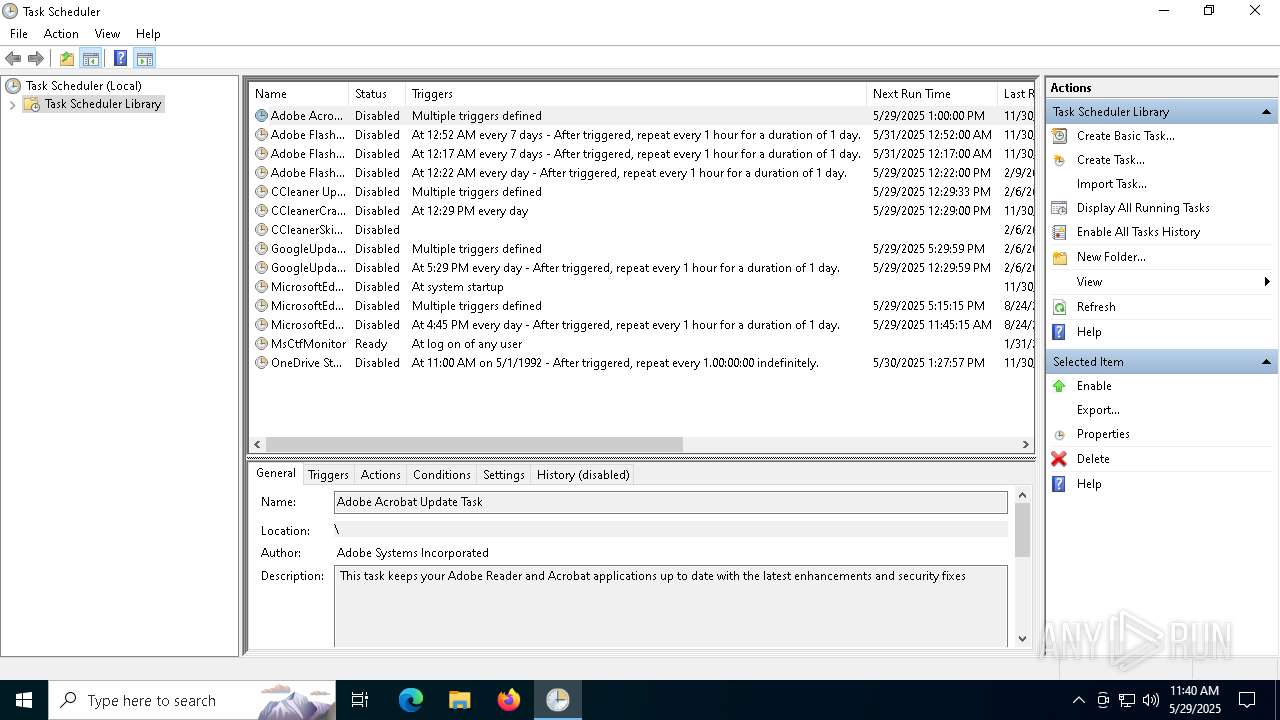
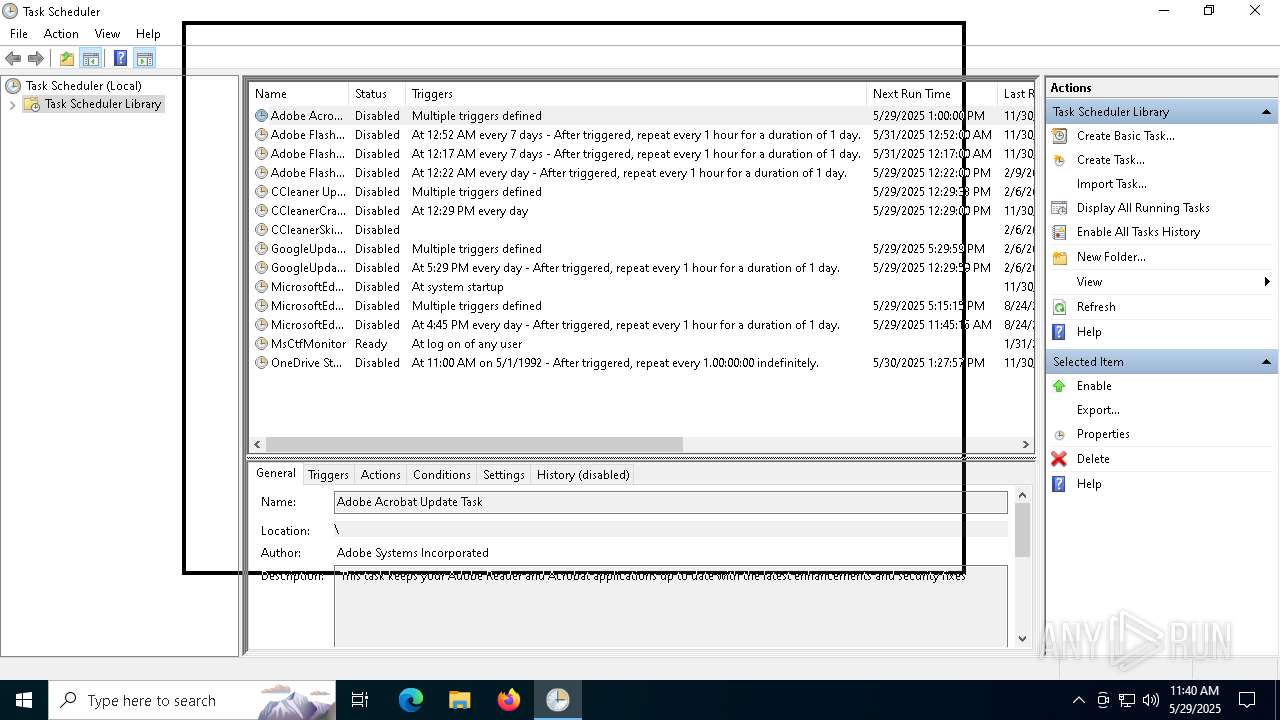
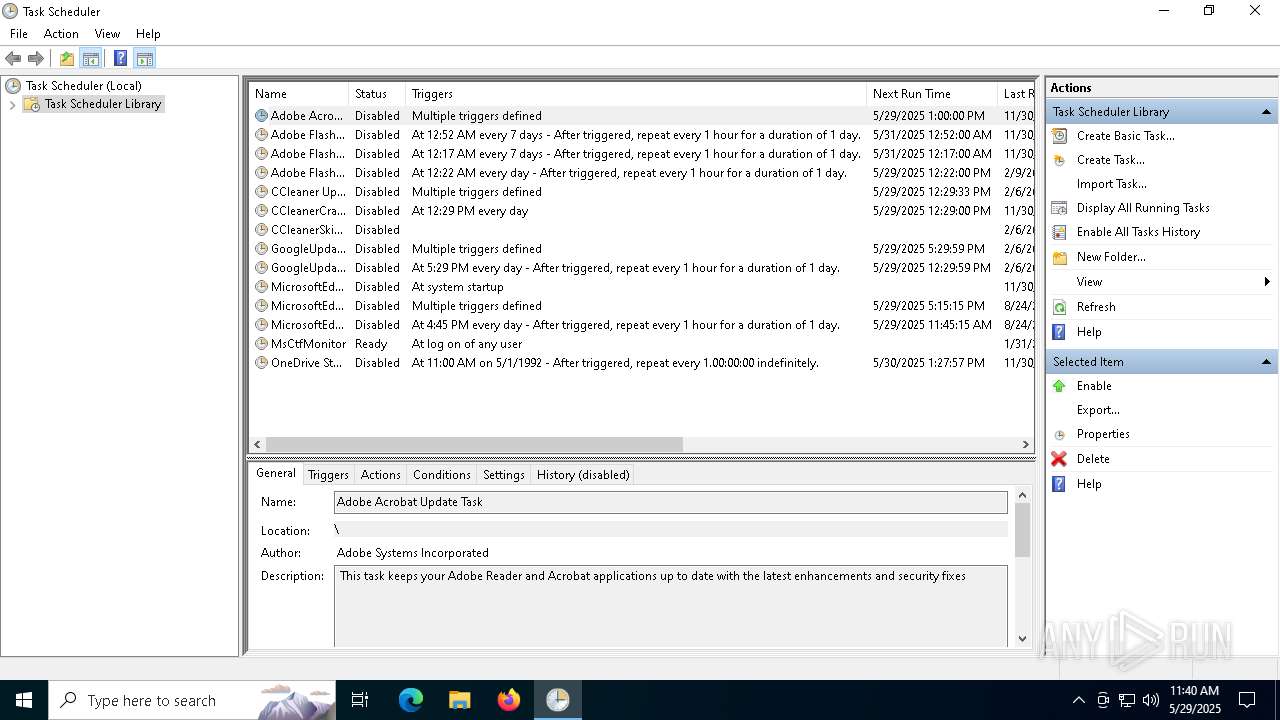
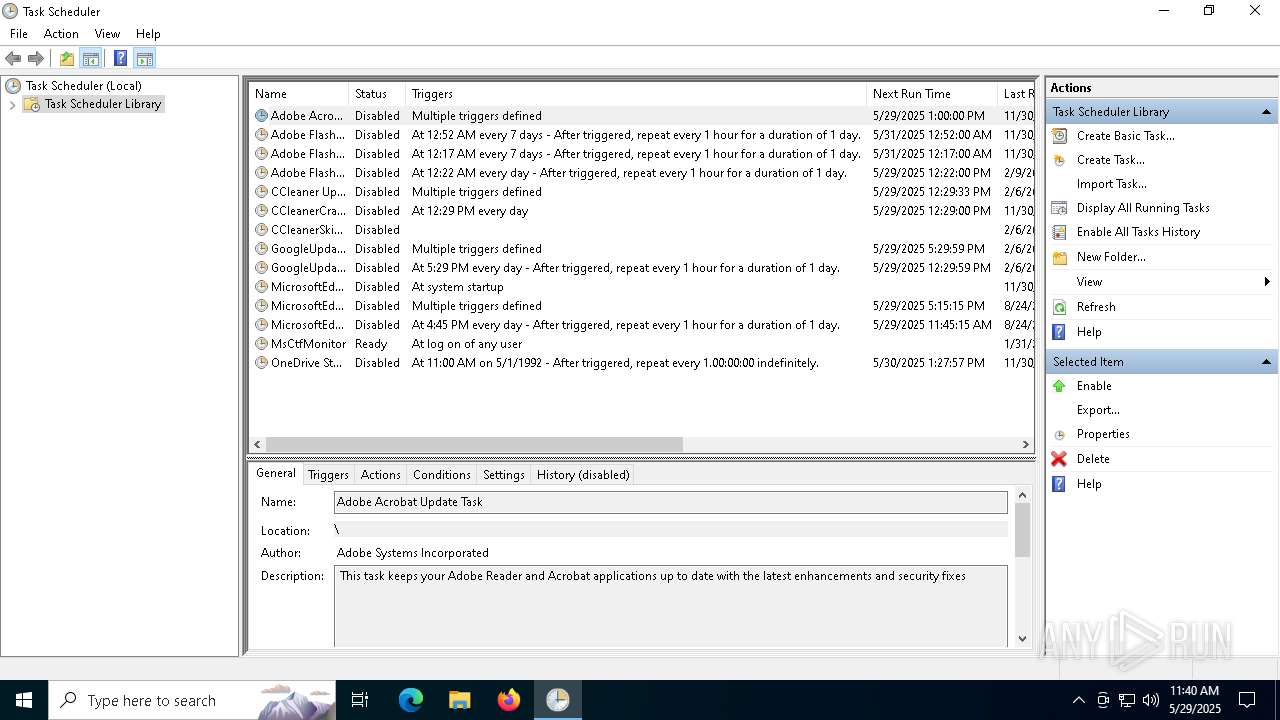
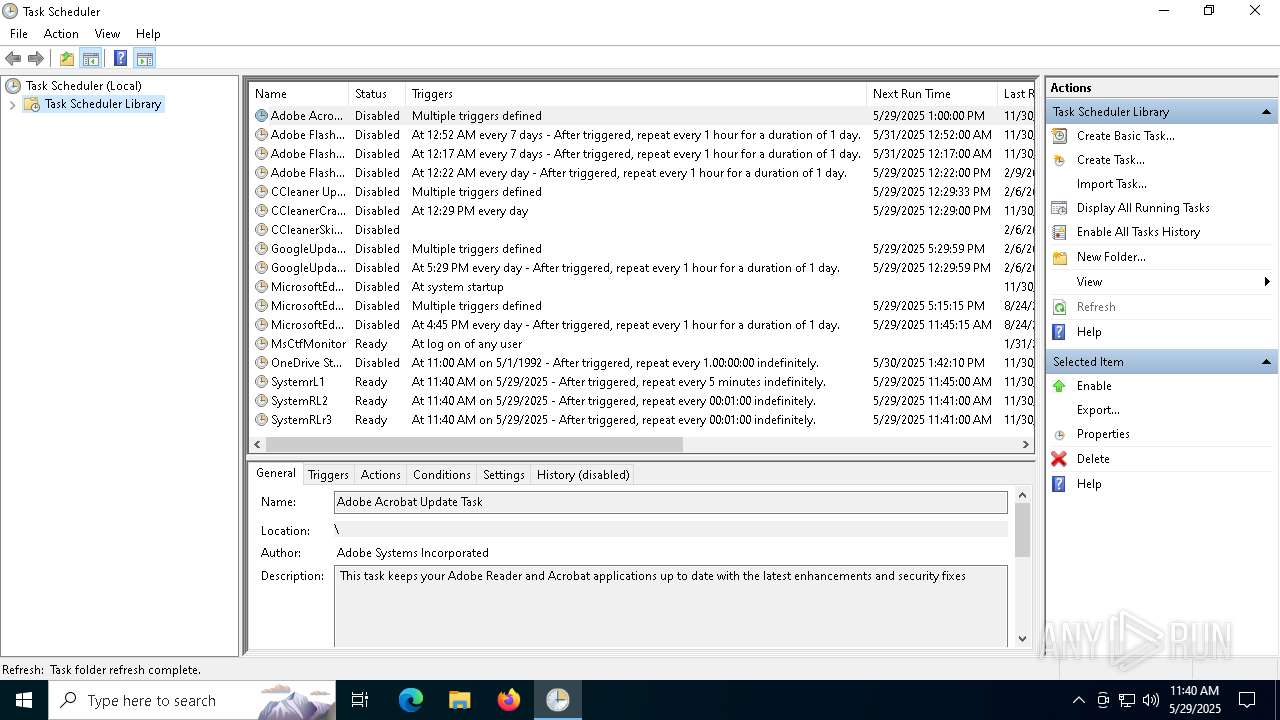
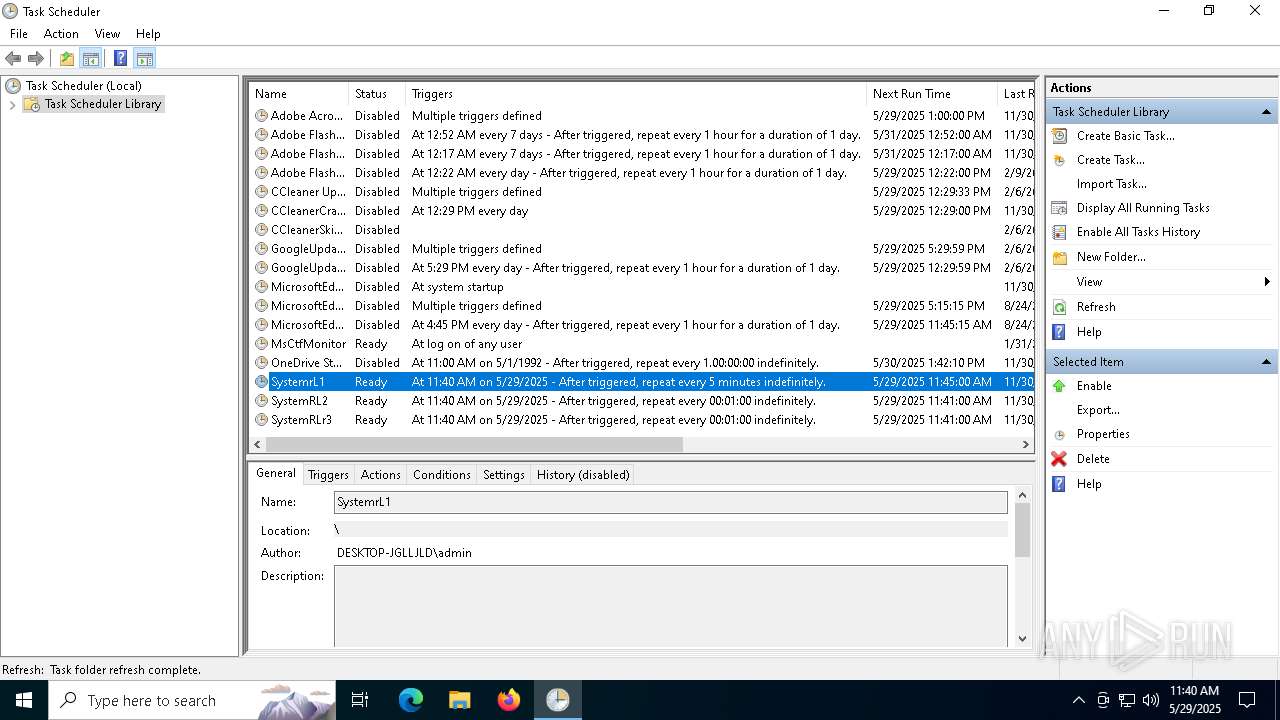
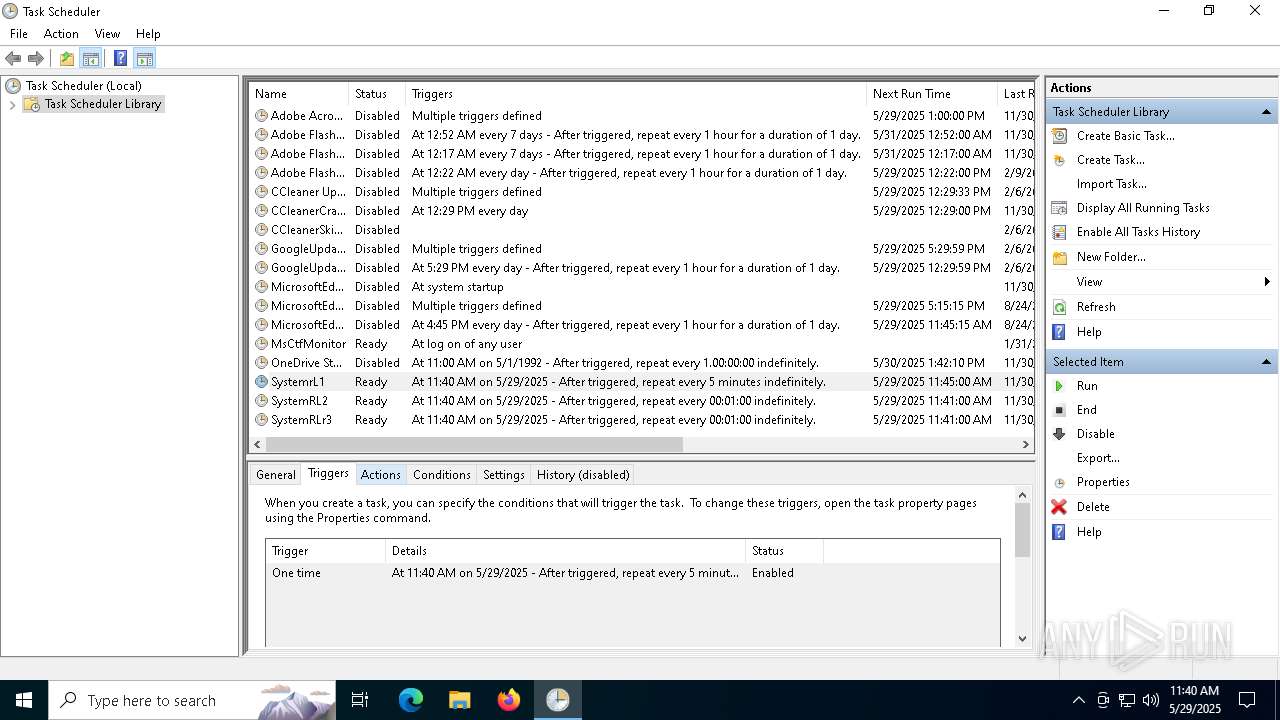
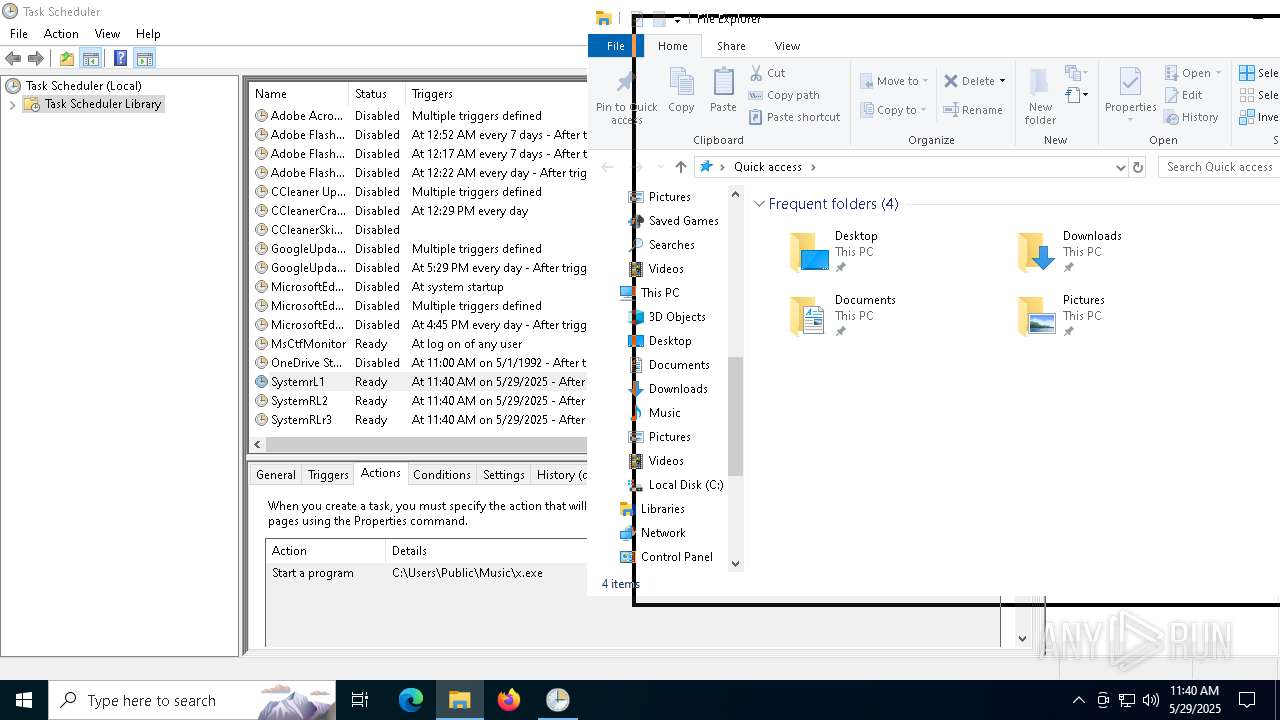
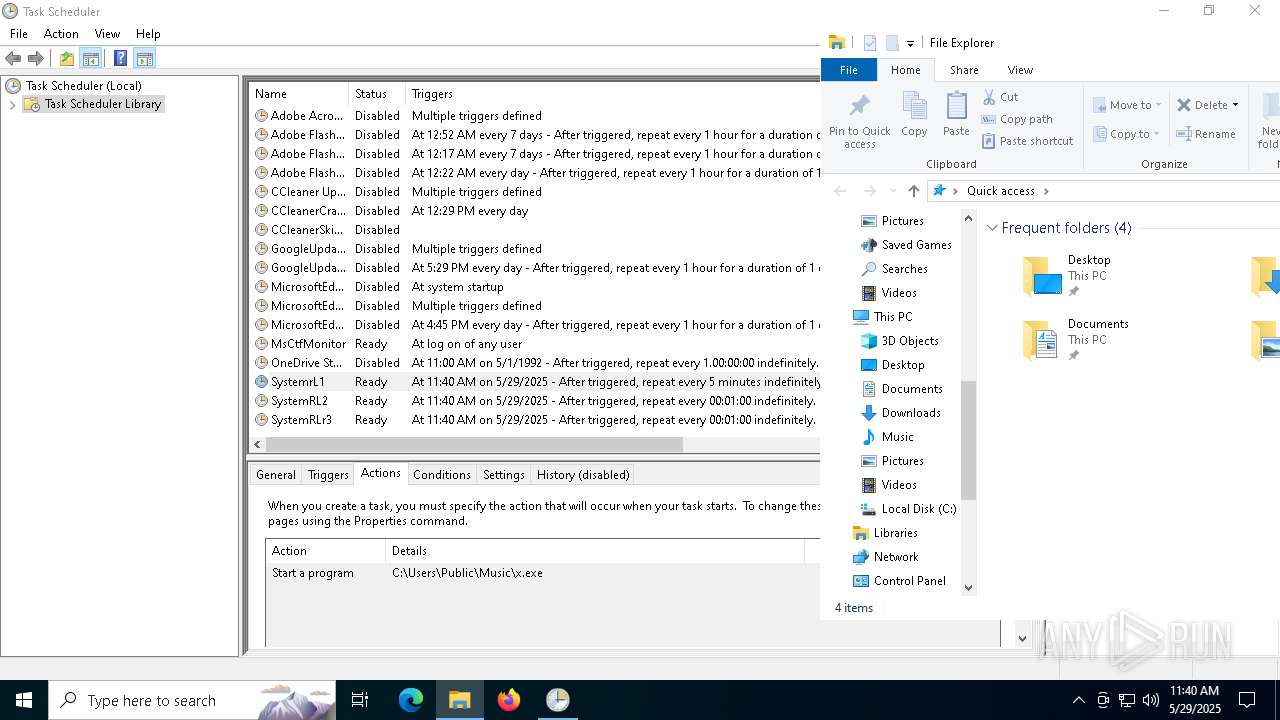
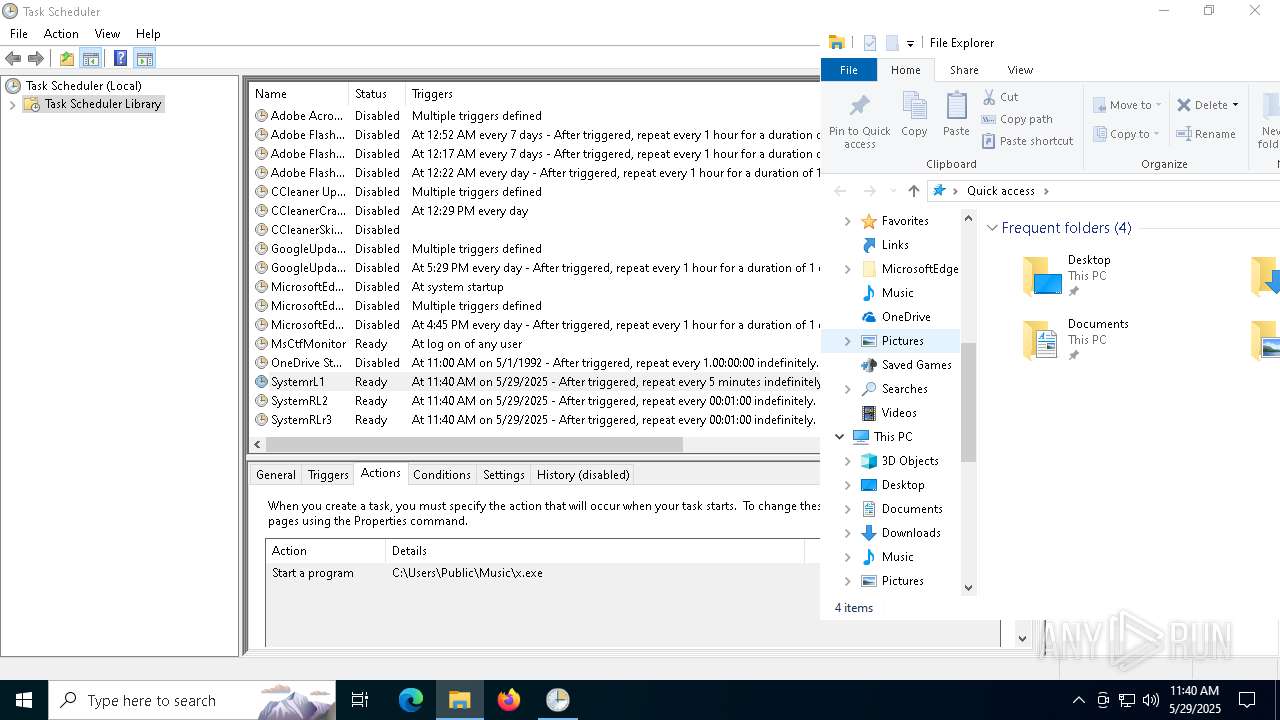
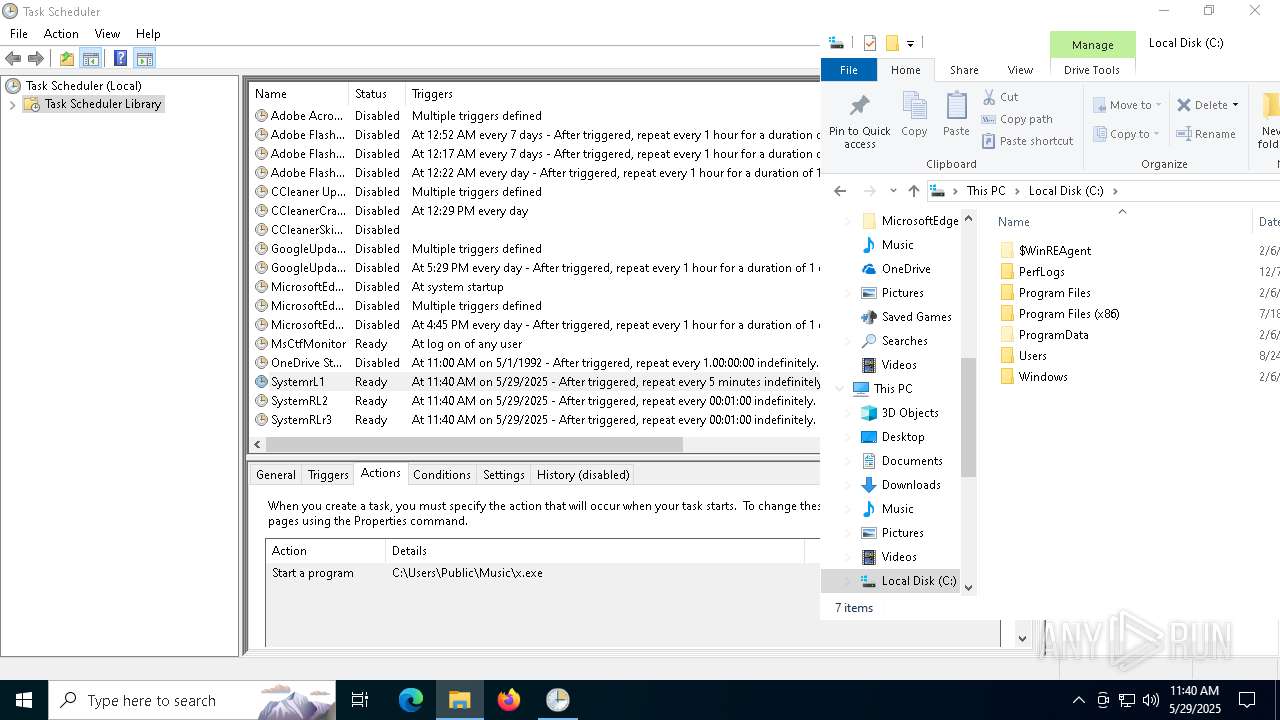
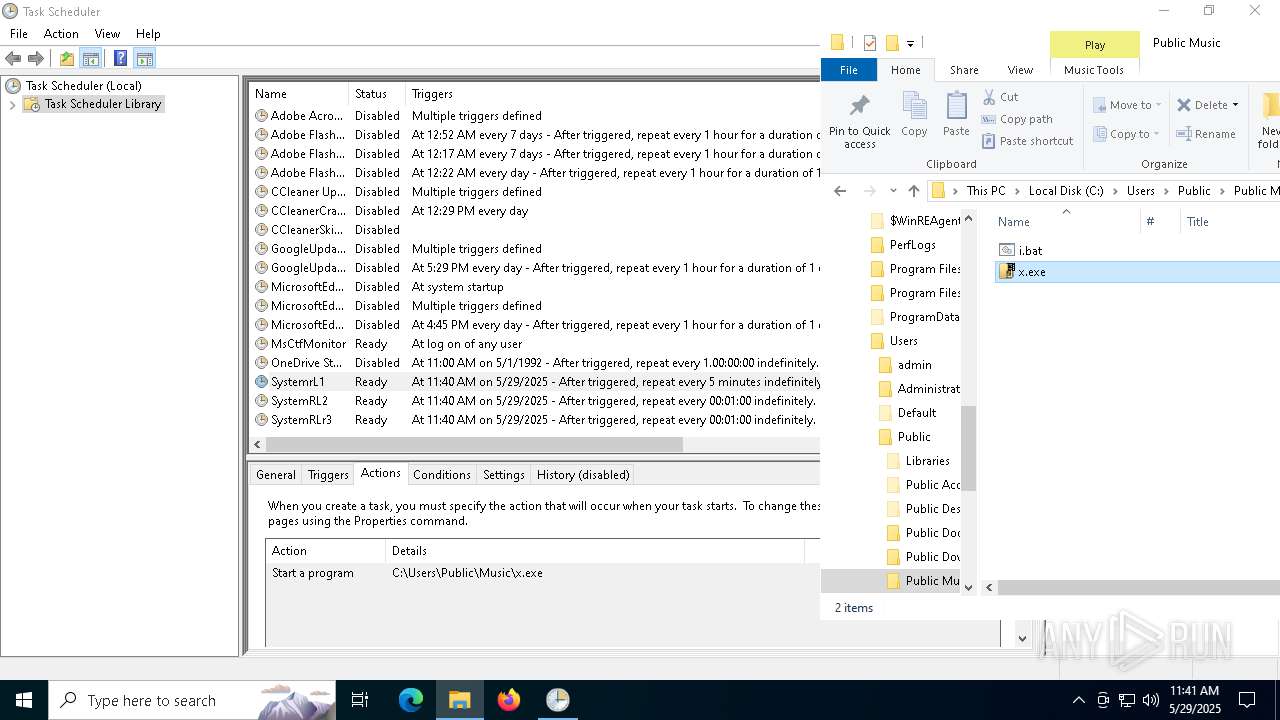
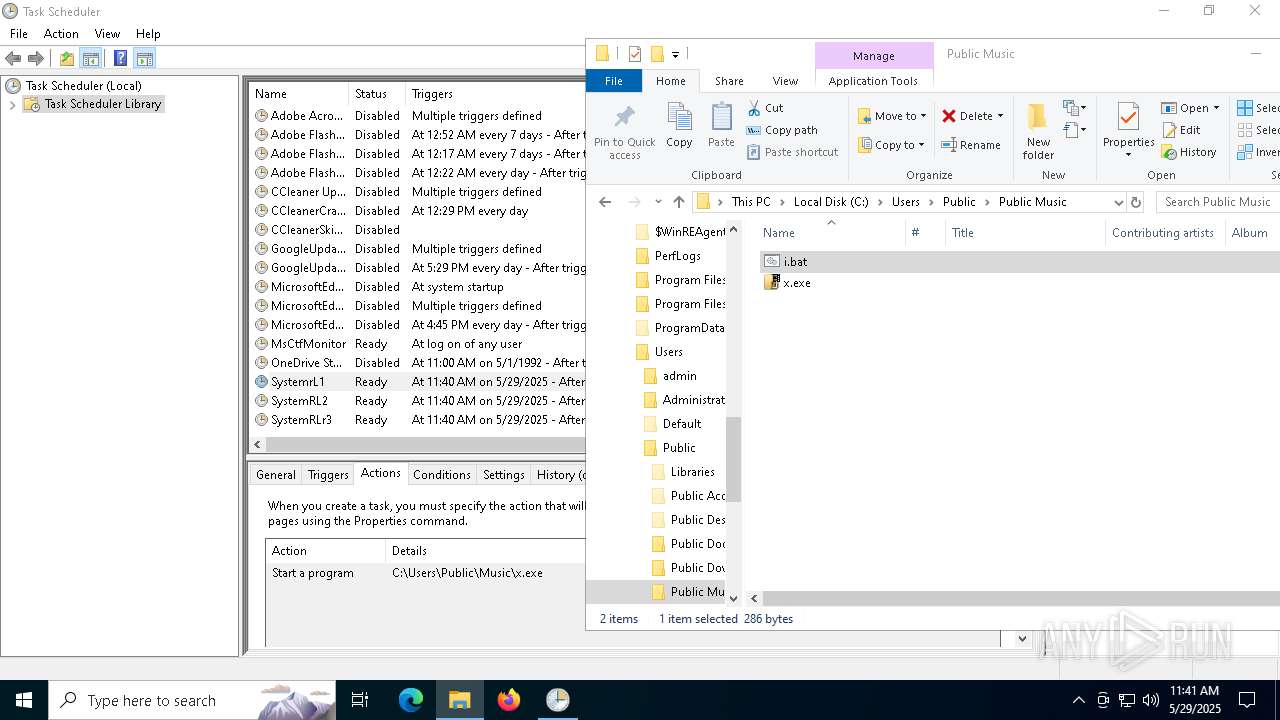
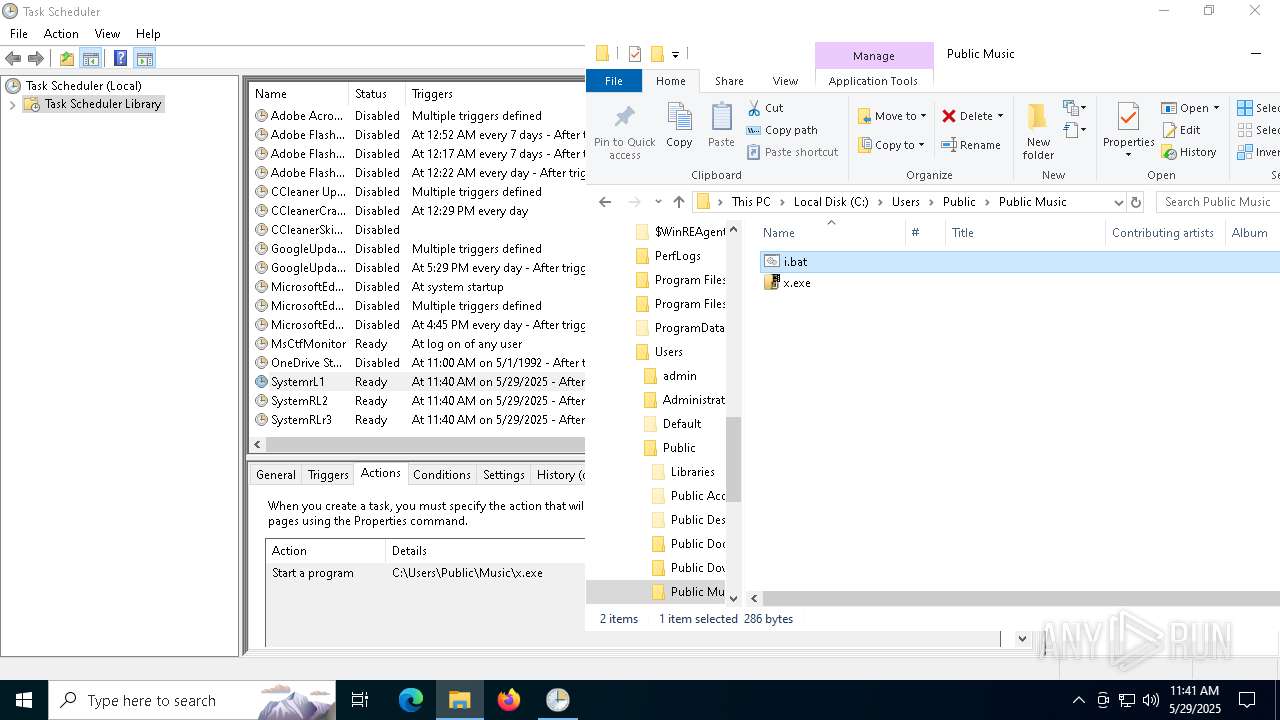
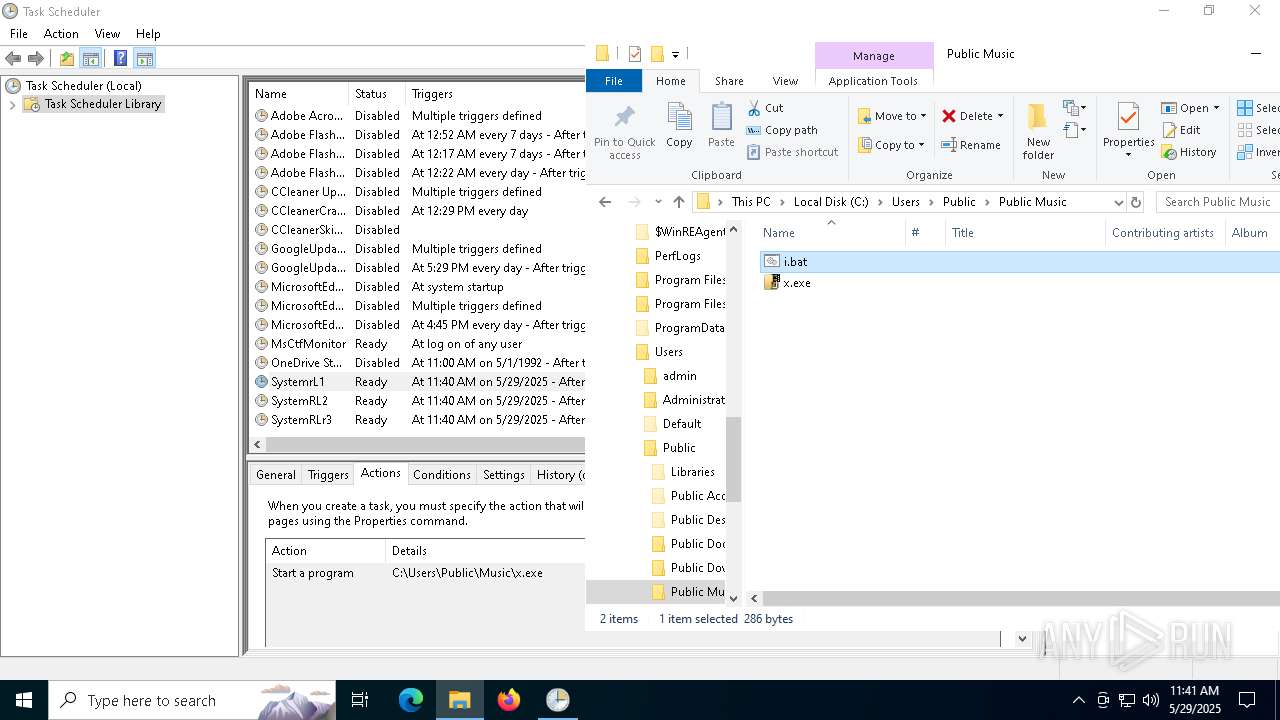
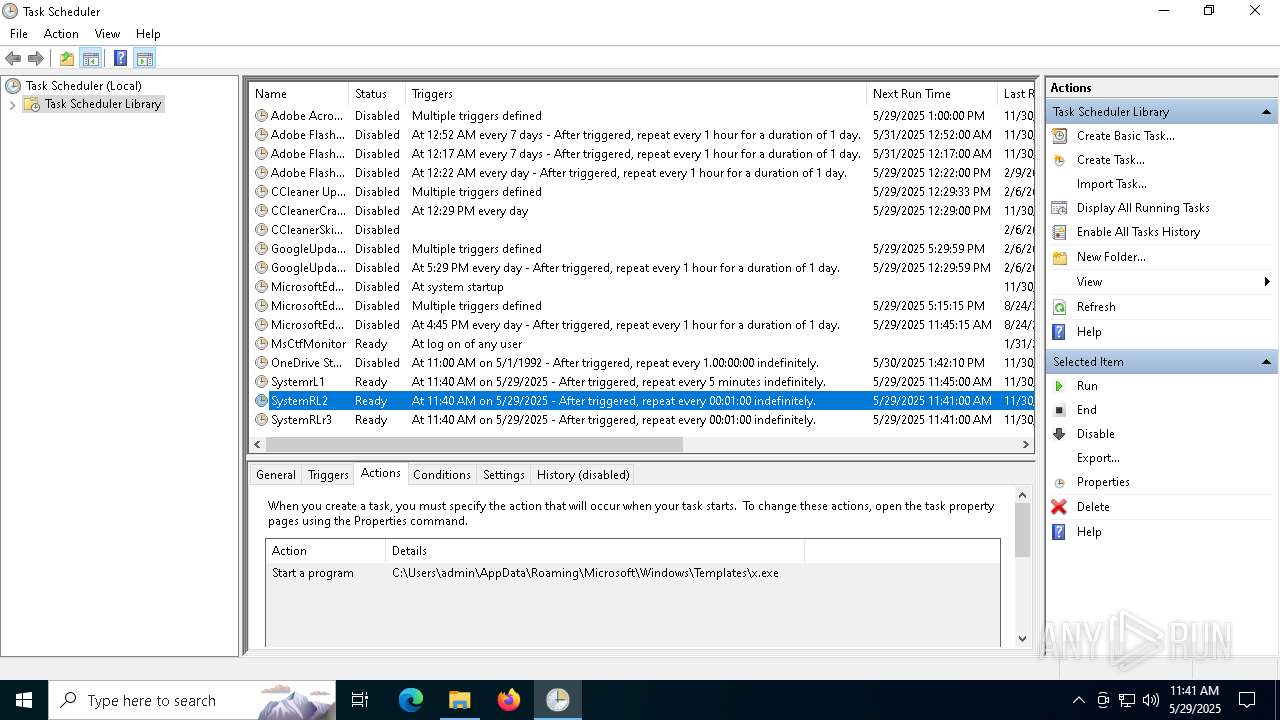
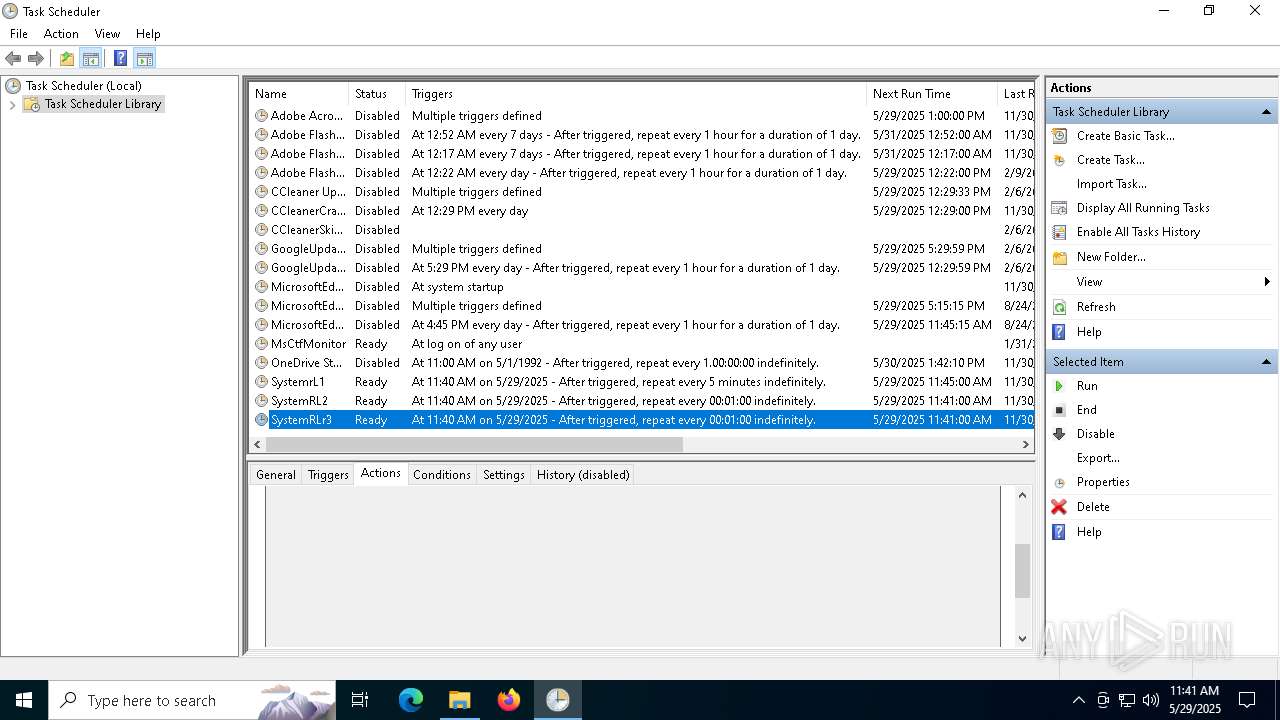
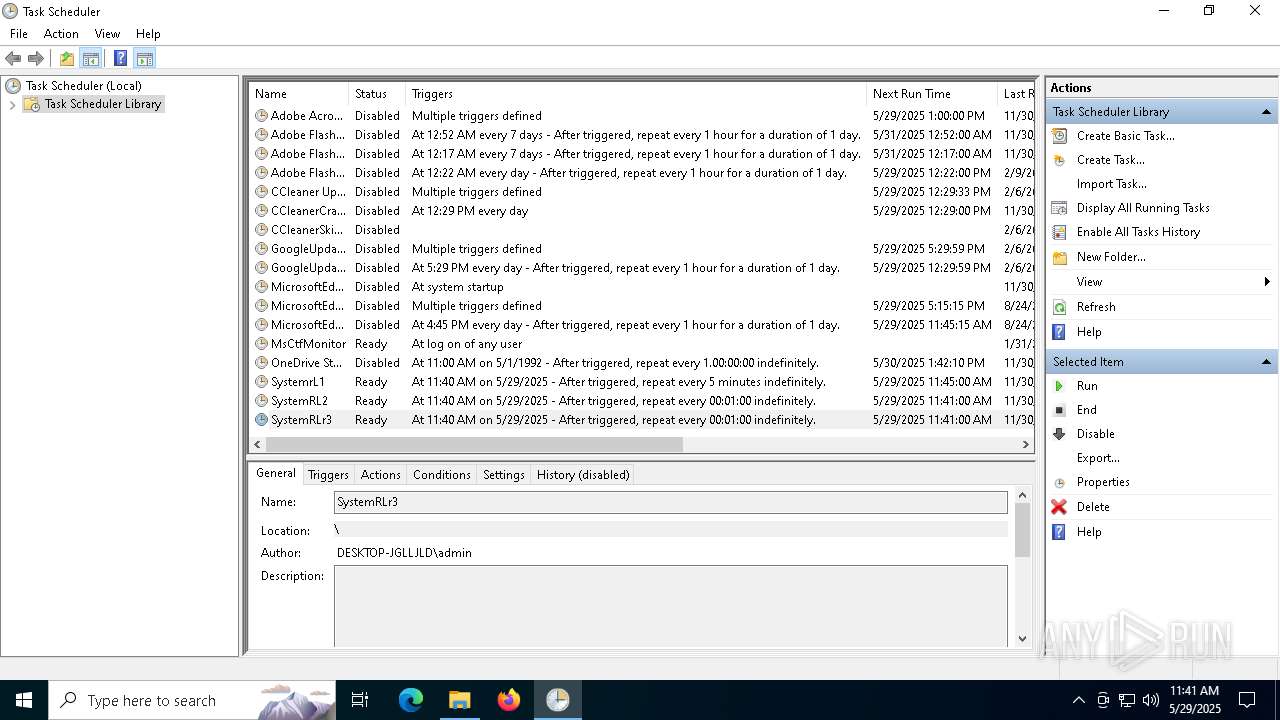
Uses Task Scheduler to run other applications
- cmd.exe (PID: 5124)
SUSPICIOUS
Executable content was dropped or overwritten
- 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe (PID: 5204)
Reads security settings of Internet Explorer
- 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe (PID: 5204)
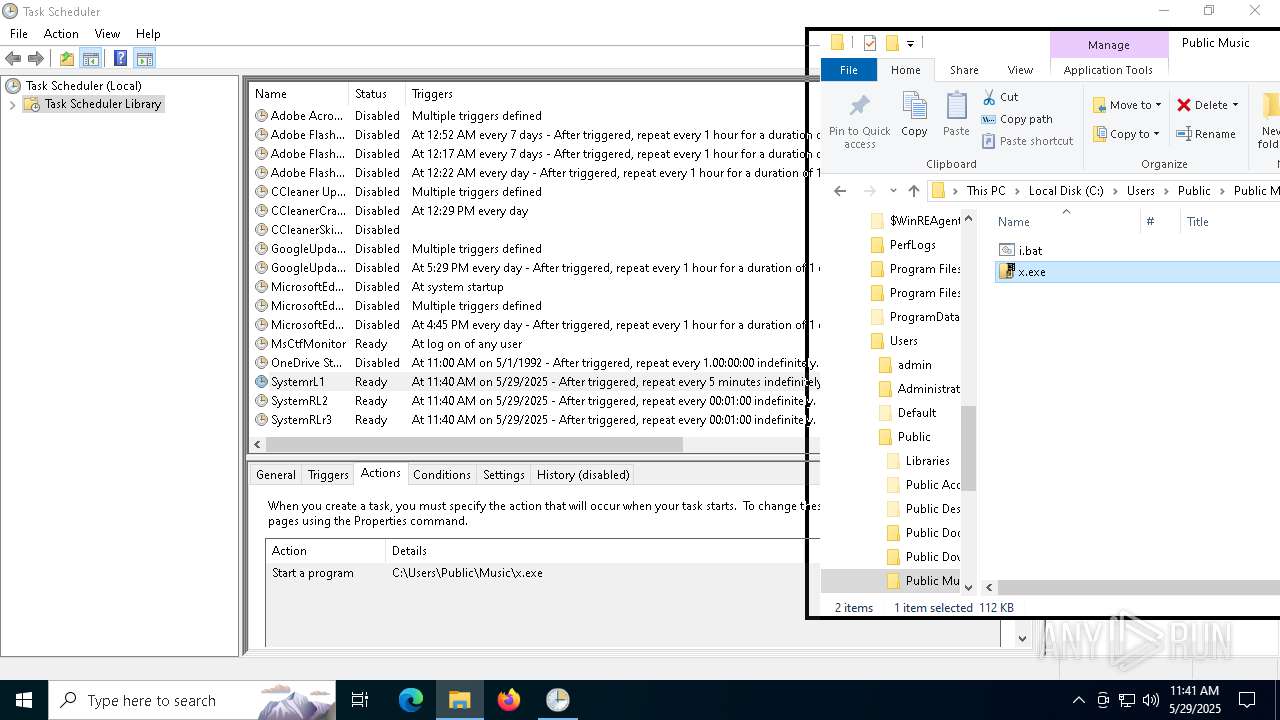
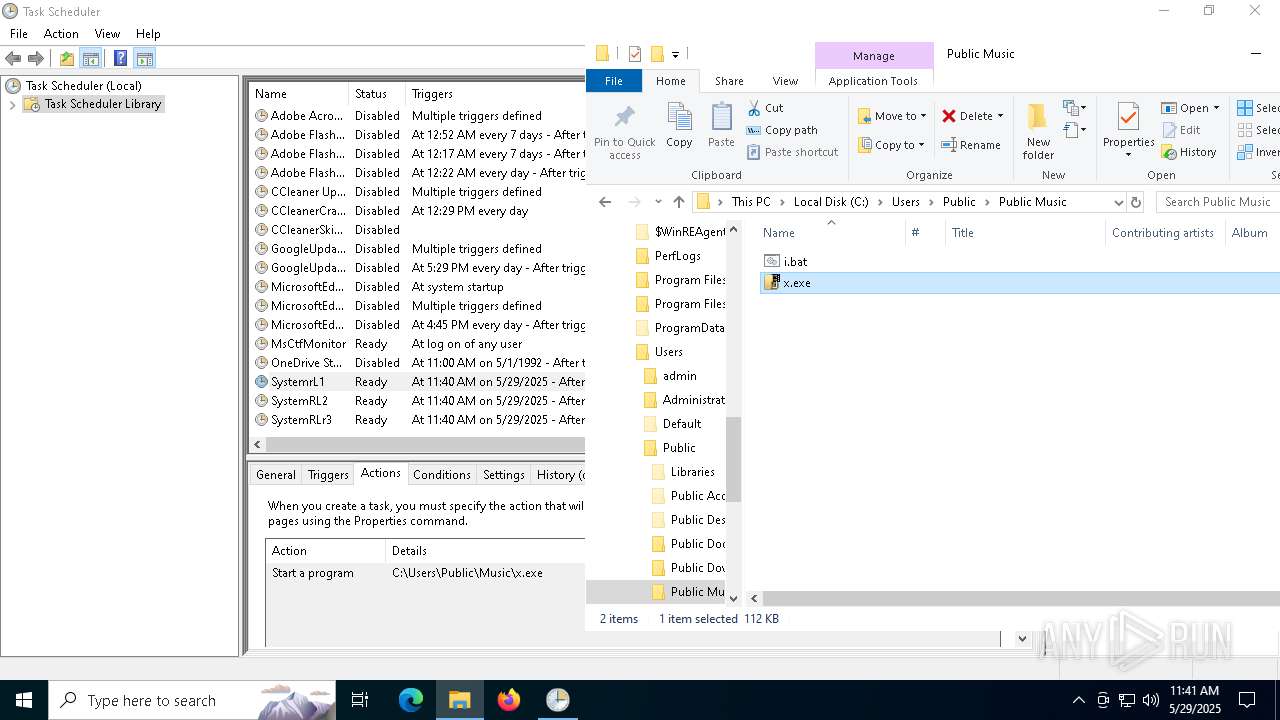
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 5124)
- schtasks.exe (PID: 7276)
- x.exe (PID: 2096)
- notepad++.exe (PID: 2772)
- x.exe (PID: 7384)
- x.exe (PID: 7768)
- schtasks.exe (PID: 7352)
- x.exe (PID: 6136)
Starts CMD.EXE for commands execution
- 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe (PID: 5204)
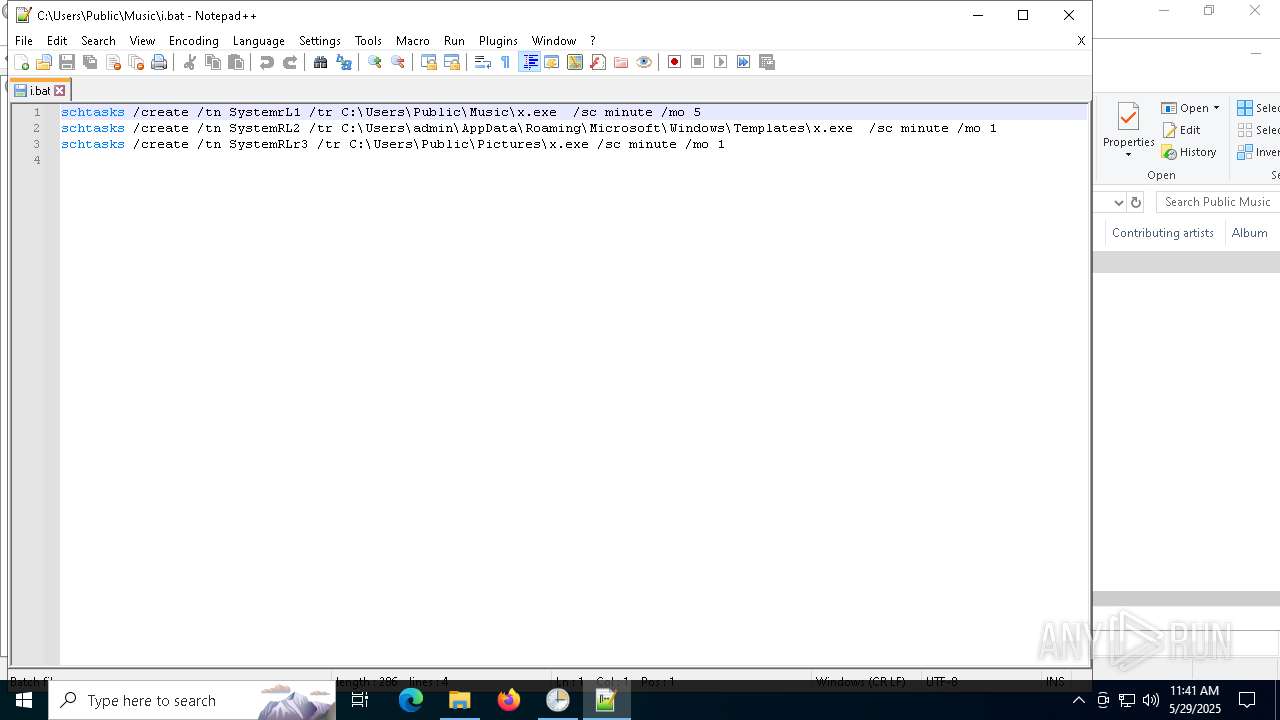
Executing commands from a ".bat" file
- 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe (PID: 5204)
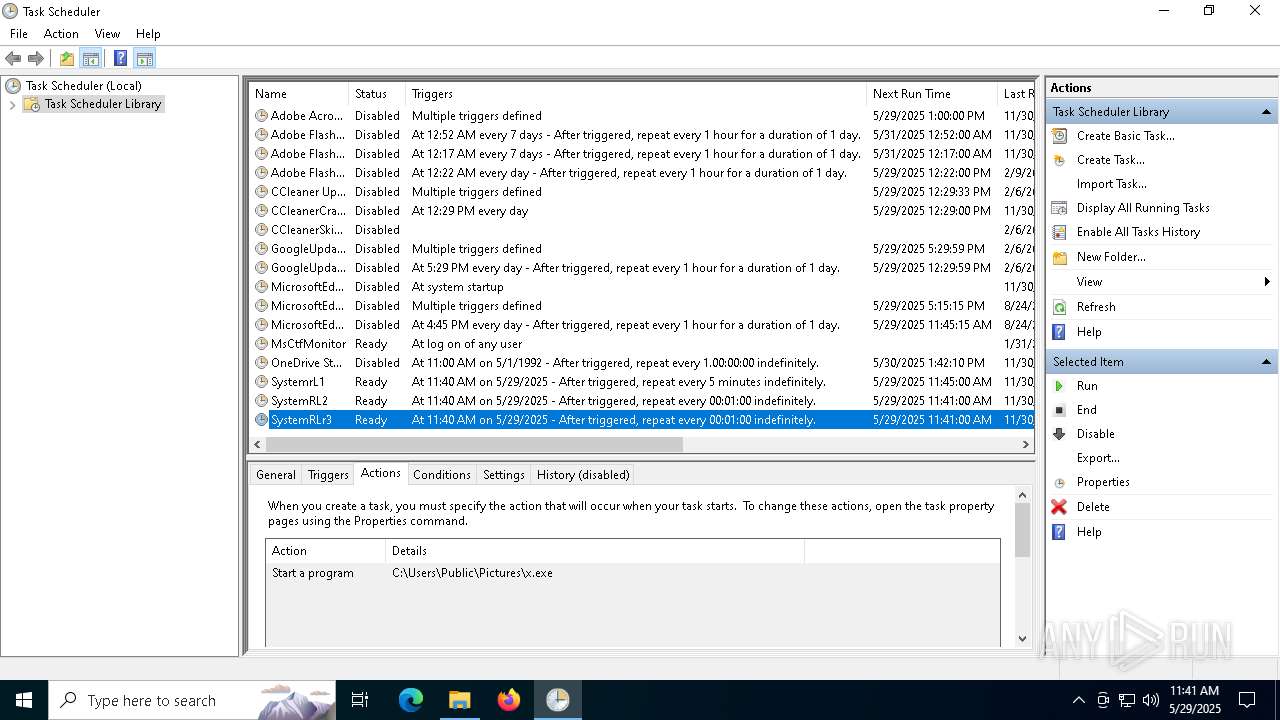
The process executes via Task Scheduler
- x.exe (PID: 7384)
- x.exe (PID: 3268)
- x.exe (PID: 2096)
- x.exe (PID: 7768)
- x.exe (PID: 1764)
- x.exe (PID: 7884)
- x.exe (PID: 6136)
- x.exe (PID: 8128)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6480)
Manual execution by a user
- mmc.exe (PID: 7960)
- mmc.exe (PID: 8032)
- 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe (PID: 5204)
- notepad++.exe (PID: 2772)
Reads security settings of Internet Explorer
- mmc.exe (PID: 8032)
Checks supported languages
- 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe (PID: 5204)
Launch of the file from Startup directory
- 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe (PID: 5204)
Reads the computer name
- 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe (PID: 5204)
Reads the machine GUID from the registry
- 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe (PID: 5204)
Creates files or folders in the user directory
- 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe (PID: 5204)
Process checks computer location settings
- 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe (PID: 5204)
Launch of the file from Task Scheduler
- cmd.exe (PID: 5124)
Reads the software policy settings
- slui.exe (PID: 7208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:05:29 11:37:49+00:00 |
| ArchivedFileName: | 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11 |
Total processes
155
Monitored processes
22
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1764 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\x.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\x.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: System32 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2096 | "C:\Users\Public\Pictures\x.exe" | C:\Users\Public\Pictures\x.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: System32 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2656 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\Public\Music\i.bat" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 3268 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\x.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\x.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: System32 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5124 | C:\WINDOWS\system32\cmd.exe /c ""C:\users\Public\Music\i.bat" " | C:\Windows\SysWOW64\cmd.exe | — | 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5204 | "C:\Users\admin\Desktop\60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe" | C:\Users\admin\Desktop\60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: System32 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5256 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5548 | schtasks /create /tn SystemRL2 /tr C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\x.exe /sc minute /mo 1 | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6136 | "C:\Users\Public\Pictures\x.exe" | C:\Users\Public\Pictures\x.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: System32 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
4 166
Read events
4 145
Write events
21
Delete events
0
Modification events
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.7z | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
5
Suspicious files
0
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5204 | 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Windowns Instaler.exe | executable | |
MD5:3C8130F7C8E72058AB6C35AE91813602 | SHA256:60DDED8C5CBF40B5F5875EDEAECC876939B5E8A3B99D2732D4FA898D48BEBA11 | |||
| 5204 | 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\x.exe | executable | |
MD5:3C8130F7C8E72058AB6C35AE91813602 | SHA256:60DDED8C5CBF40B5F5875EDEAECC876939B5E8A3B99D2732D4FA898D48BEBA11 | |||
| 5204 | 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe | C:\Users\Public\Music\i.bat | text | |
MD5:77E1283EFFC9FF044A49B6CF6A885FD5 | SHA256:F8A4366863AA056A9B950A2A92F2808F642DB90DBC12701A529C316C7BEA3DD7 | |||
| 5204 | 60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11.exe | C:\Users\Public\Pictures\x.exe | executable | |
MD5:3C8130F7C8E72058AB6C35AE91813602 | SHA256:60DDED8C5CBF40B5F5875EDEAECC876939B5E8A3B99D2732D4FA898D48BEBA11 | |||
| 2772 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:FE22EC5755BC98988F9656F73B2E6FB8 | SHA256:F972C425CE176E960F6347F1CA2F64A8CE2B95A375C33A03E57538052BA0624D | |||
| 2772 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:A2ED875AA42589077C4D08F4F8912018 | SHA256:77B0174D655F327C1FC9520B4F8831ECD82E98351B26BB9C2EDD98FF0CD63A2D | |||
| 2772 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:312281C4126FA897EF21A7E8CCB8D495 | SHA256:53B4BE3ED1CFD712E53542B30CFE30C5DB35CC48BE7C57727DFEC26C9E882E90 | |||
| 2772 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:DAFF9C413A1218EA0C3C3C6681FD63FD | SHA256:66C2D6479A1E7011585ABBB1C91439C92C81180B6FD3E9C5019C237C8F2465FE | |||
| 2772 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:F11D96162BC521F5CF49FFE6B6841C9B | SHA256:BE9AEAEAB5A2E4899BA7E582274BA592C1B9BAF688B340A754B8EF32B23CFA9C | |||
| 6480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6480.8599\60dded8c5cbf40b5f5875edeaecc876939b5e8a3b99d2732d4fa898d48beba11 | executable | |
MD5:3C8130F7C8E72058AB6C35AE91813602 | SHA256:60DDED8C5CBF40B5F5875EDEAECC876939B5E8A3B99D2732D4FA898D48BEBA11 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
35
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5728 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5728 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2924 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |