| File name: | FA09102016AT.msi |
| Full analysis: | https://app.any.run/tasks/1b4107b9-4451-4367-a97b-291ebccd2fd4 |
| Verdict: | Malicious activity |
| Analysis date: | June 16, 2019, 23:02:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Dec 11 11:47:44 2009, Security: 0, Code page: 1252, Revision Number: {D923683E-FF5A-4019-BCF9-906DB2753899}, Number of Words: 10, Subject: Adobe Acrobat Reader, Author: Adobe Acrobat Reader, Name of Creating Application: Advanced Installer 12.2.1 build 64247, Template: ;1033, Comments: This installer database contains the logic and data required to install Adobe Acrobat Reader., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | 024B95D32B9F75F1D13BE644E722D008 |
| SHA1: | 0805684144F8AC6BED77A5C90B2B9B76624306F9 |
| SHA256: | 07440783C3F441D061C698EAF744B1C0FBEED279D5DB2492090F14C6CA265DEE |
| SSDEEP: | 3072:zc97NIA+/WQx5TYD9yOePnMzYMTxHwgz88ereWn/7w05g0d9bY5Alt7k3DxAkQ8B:zbRMN28er1nzT1Y5AlK3DeQ2 |
MALICIOUS
Changes the autorun value in the registry
- reg.exe (PID: 2476)
Application was dropped or rewritten from another process
- lc8FD4.tmp (PID: 2692)
SUSPICIOUS
Executable content was dropped or overwritten
- msiexec.exe (PID: 324)
- MsiExec.exe (PID: 2428)
Creates files in the user directory
- cmd.exe (PID: 3628)
- MsiExec.exe (PID: 2428)
Starts CMD.EXE for commands execution
- MsiExec.exe (PID: 2428)
Starts Internet Explorer
- cmd.exe (PID: 3628)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2236)
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3824)
Reads Internet Cache Settings
- MsiExec.exe (PID: 2428)
INFO
Application launched itself
- msiexec.exe (PID: 324)
- iexplore.exe (PID: 2796)
Changes internet zones settings
- iexplore.exe (PID: 2796)
Reads Internet Cache Settings
- iexplore.exe (PID: 4084)
Creates files in the user directory
- iexplore.exe (PID: 4084)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3824)
Reads settings of System Certificates
- iexplore.exe (PID: 4084)
Reads internet explorer settings
- iexplore.exe (PID: 4084)
Starts application with an unusual extension
- MsiExec.exe (PID: 2428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (88.6) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (10) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2009:12:11 11:47:44 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {D923683E-FF5A-4019-BCF9-906DB2753899} |
| Words: | 10 |
| Subject: | Adobe Acrobat Reader |
| Author: | Adobe Acrobat Reader |
| LastModifiedBy: | - |
| Software: | Advanced Installer 12.2.1 build 64247 |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install Adobe Acrobat Reader. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
55
Monitored processes
14
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 864 | "C:\Windows\System32\cmd.exe" /C shutdown -r -f -t 0 | C:\Windows\System32\cmd.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1652 | shutdown /r /t 1 /f | C:\Windows\system32\shutdown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shutdown and Annotation Tool Exit code: 1115 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
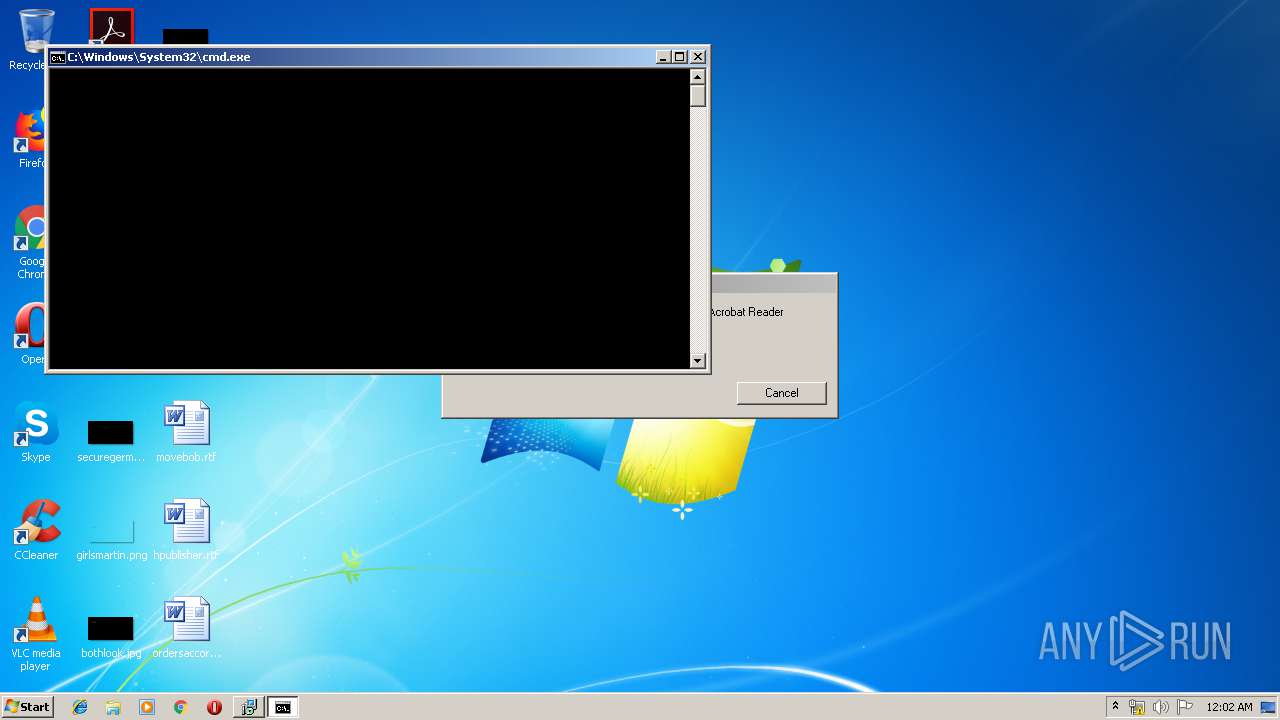
| 2236 | "C:\Windows\System32\cmd.exe" /C start /MIN reg add HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v jMTAlO /t reg_sz /d "C:\jMTAlO\jMTAlO.exe" | C:\Windows\System32\cmd.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2428 | C:\Windows\system32\MsiExec.exe -Embedding E1032938515459BAA3DF15DCAAA727CF | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1073807364 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2476 | reg add HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v jMTAlO /t reg_sz /d "C:\jMTAlO\jMTAlO.exe" | C:\Windows\system32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2572 | "C:\Windows\system32\cmd.exe" /c shutdown /r /t 1 /f | C:\Windows\system32\cmd.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1115 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2616 | shutdown -r -f -t 0 | C:\Windows\system32\shutdown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
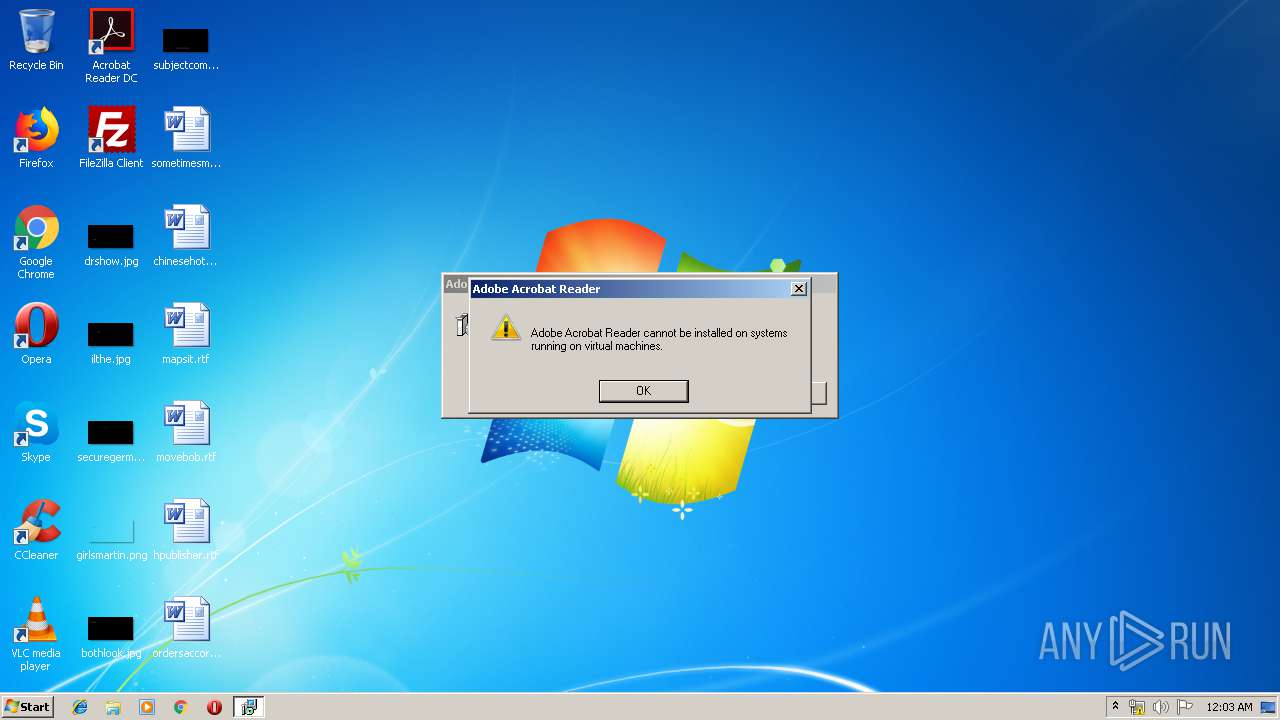
| 2692 | "C:\Users\admin\AppData\Local\Temp\lc8FD4.tmp" | C:\Users\admin\AppData\Local\Temp\lc8FD4.tmp | — | MsiExec.exe | |||||||||||
User: admin Company: Caphyon LTD Integrity Level: MEDIUM Description: Executable that detects if running in a virtual machine Exit code: 1073807364 Version: 12.2.1.0 Modules
| |||||||||||||||
| 2796 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1073807364 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
968
Read events
813
Write events
149
Delete events
6
Modification events
| (PID) Process: | (324) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 44010000EE8E05959724D501 | |||
| (PID) Process: | (324) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 92CDAADC1DBD0A7EC4EB42A56A934C9998E42D7BB2C83E93BE47DBAE9BF031F7 | |||
| (PID) Process: | (324) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2428) MsiExec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2428) MsiExec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2796) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2796) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2796) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2796) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2796) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
9
Suspicious files
4
Text files
112
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2796 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2796 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 324 | msiexec.exe | C:\Windows\Installer\11fae7.msi | executable | |
MD5:— | SHA256:— | |||
| 2428 | MsiExec.exe | C:\Users\admin\AppData\Roaming\user.txt | text | |
MD5:A067F5EC97BA51B576825B69BC855E58 | SHA256:CF3E339D25C3C023C9417FFC5D8E73F1DA828B18FEECAF14FDB9C24D04E49BA0 | |||
| 3628 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\IETldCache\index.dat | dat | |
MD5:D7A950FEFD60DBAA01DF2D85FEFB3862 | SHA256:75D0B1743F61B76A35B1FEDD32378837805DE58D79FA950CB6E8164BFA72073A | |||
| 2796 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Feeds Cache\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 4084 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\J5AIYZAU\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 4084 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 4084 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\J5AIYZAU\scribe_endpoint[1].png | — | |
MD5:— | SHA256:— | |||
| 4084 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\1ZTQDB9Q\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
94
TCP/UDP connections
26
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
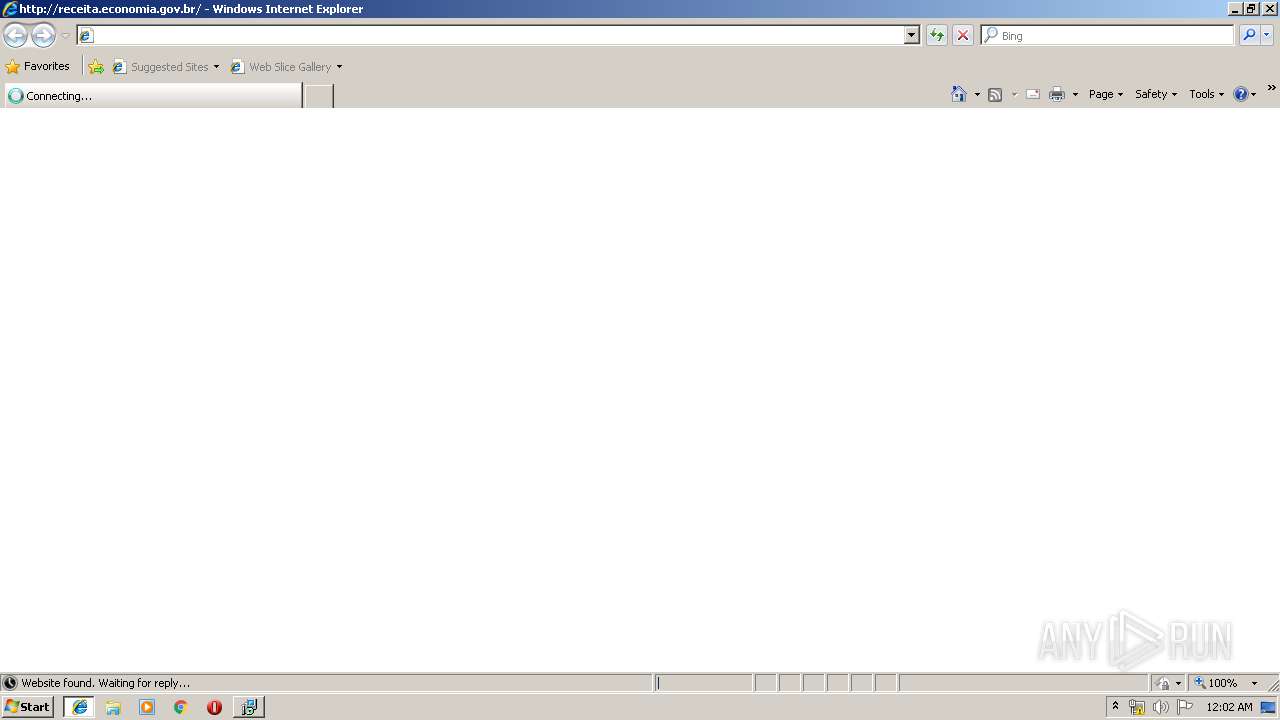
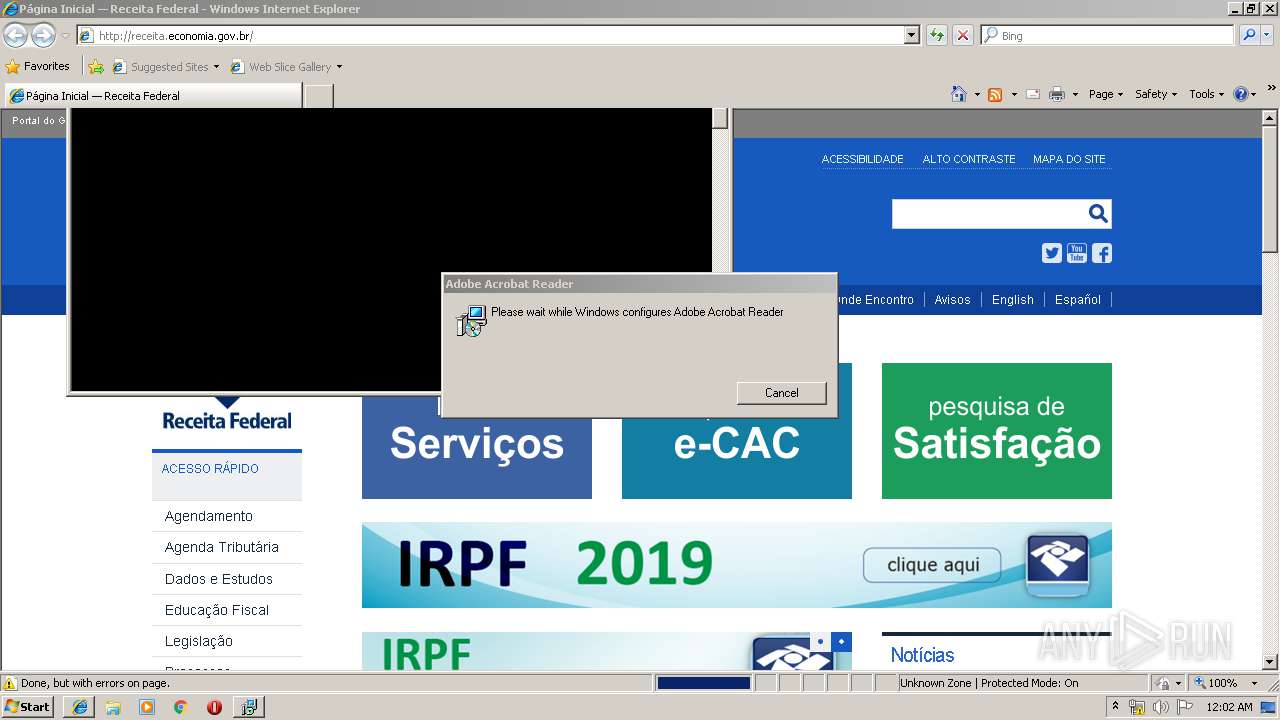
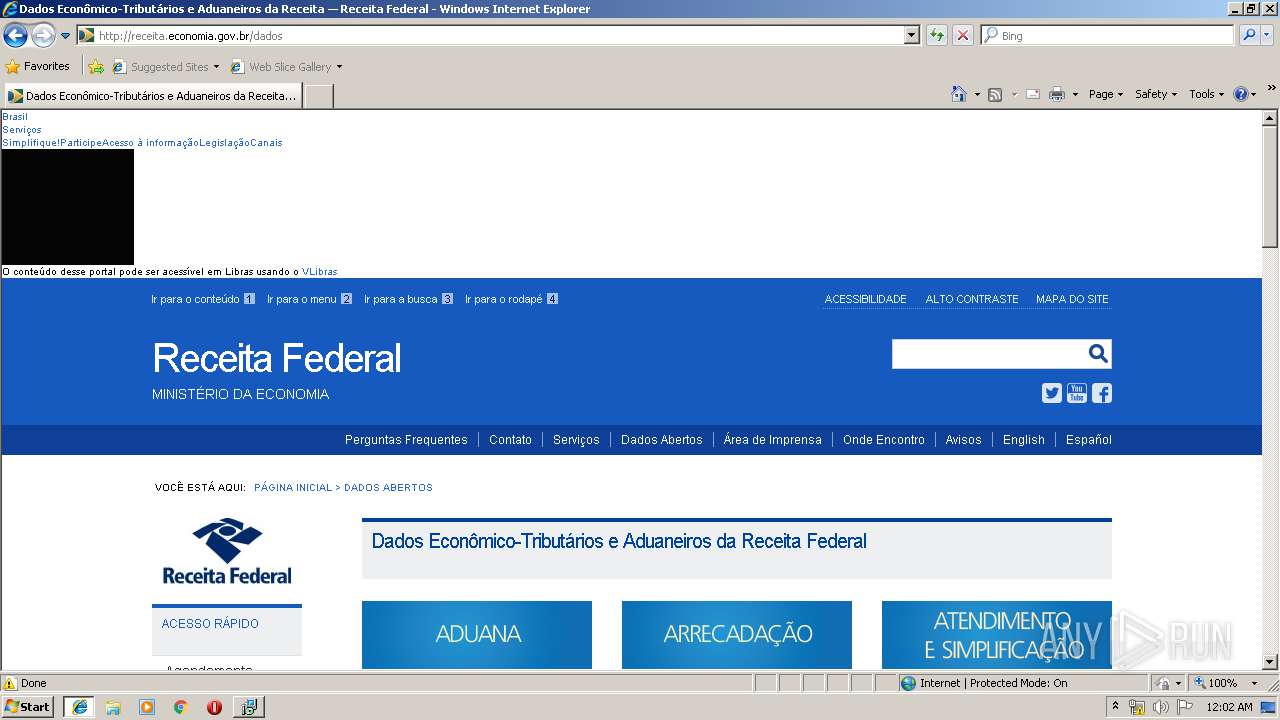
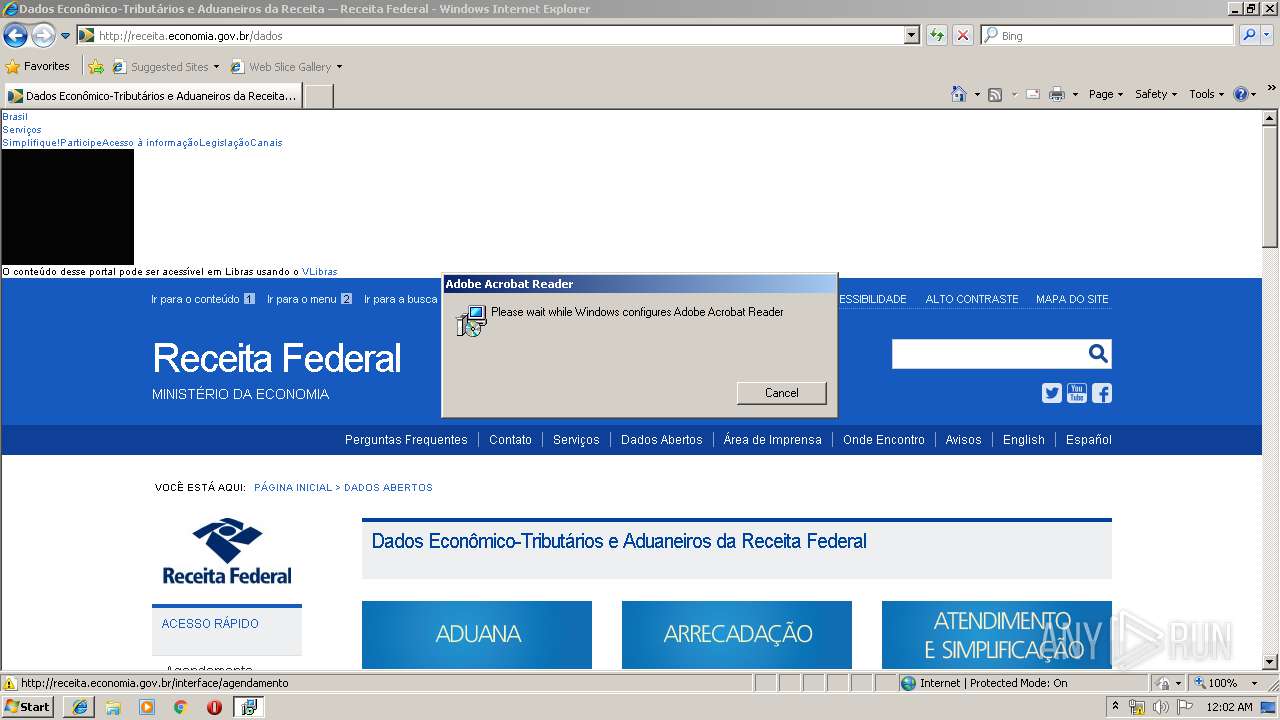
4084 | iexplore.exe | GET | 200 | 161.148.231.170:80 | http://receita.economia.gov.br/ | BR | html | 91.9 Kb | suspicious |
4084 | iexplore.exe | GET | 301 | 67.199.248.10:80 | http://bit.ly/2HJogDw | US | html | 118 b | shared |
4084 | iexplore.exe | GET | 200 | 161.148.231.170:80 | http://receita.economia.gov.br/portal_css/Sunburst%20Theme/resourceplone.formwidget.autocompletejquery.autocomplete-cachekey-69ee8461f3f7222226ebccfd17f0d947.css | BR | text | 2.63 Kb | suspicious |
4084 | iexplore.exe | GET | 200 | 161.148.231.170:80 | http://receita.economia.gov.br/portal_css/Sunburst%20Theme/reset-cachekey-060d597ce52d12b79b1f594f28beab9e.css | BR | text | 477 b | suspicious |
4084 | iexplore.exe | GET | 200 | 31.13.92.14:80 | http://connect.facebook.net/pt_BR/all.js | IE | text | 1.74 Kb | whitelisted |
4084 | iexplore.exe | GET | 200 | 161.148.231.170:80 | http://receita.economia.gov.br/portal_css/Sunburst%20Theme/resourceplone.app.jquerytools.dateinput-cachekey-4f1ddc153a01a2c9f550fd5884d0b33e.css | BR | text | 4.50 Kb | suspicious |
4084 | iexplore.exe | GET | 200 | 161.148.231.170:80 | http://receita.economia.gov.br/portal_css/Sunburst%20Theme/resourcecollection-cachekey-f957030d55ce8f49eb391eeb4da52f58.css | BR | text | 5.24 Kb | suspicious |
4084 | iexplore.exe | GET | 200 | 161.148.231.170:80 | http://receita.economia.gov.br/portal_css/Sunburst%20Theme/resourcecalendar_stylescalendar-cachekey-c147cf23d03b6b93340d24c8ea3f13cc.css | BR | text | 1.34 Kb | suspicious |
4084 | iexplore.exe | GET | 200 | 161.148.231.170:80 | http://receita.economia.gov.br/portal_css/Sunburst%20Theme/resourcebrasil.gov.agendaagenda-cachekey-b6e5462502673583537f3967a00a2797.css | BR | text | 11.3 Kb | suspicious |
4084 | iexplore.exe | GET | 200 | 152.195.34.77:80 | http://barra.brasil.gov.br/barra.js | US | html | 7.62 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2796 | iexplore.exe | 161.148.231.170:80 | receita.economia.gov.br | SERVICO FEDERAL DE PROCESSAMENTO DE DADOS - SERPRO | BR | suspicious |
2796 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
4084 | iexplore.exe | 67.199.248.10:80 | bit.ly | Bitly Inc | US | shared |
4084 | iexplore.exe | 161.148.231.170:80 | receita.economia.gov.br | SERVICO FEDERAL DE PROCESSAMENTO DE DADOS - SERPRO | BR | suspicious |
4084 | iexplore.exe | 31.13.92.14:80 | connect.facebook.net | Facebook, Inc. | IE | whitelisted |
4084 | iexplore.exe | 152.195.34.77:80 | barra.brasil.gov.br | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4084 | iexplore.exe | 192.229.133.150:443 | platform.linkedin.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4084 | iexplore.exe | 185.60.216.35:443 | www.facebook.com | Facebook, Inc. | IE | whitelisted |
4084 | iexplore.exe | 161.148.231.100:80 | www.receita.fazenda.gov.br | SERVICO FEDERAL DE PROCESSAMENTO DE DADOS - SERPRO | BR | suspicious |
4084 | iexplore.exe | 31.13.92.14:443 | connect.facebook.net | Facebook, Inc. | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
s3-eu-west-1.amazonaws.com |
| shared |
www.bing.com |
| whitelisted |
bit.ly |
| shared |
receita.economia.gov.br |
| suspicious |
connect.facebook.net |
| whitelisted |
platform.linkedin.com |
| whitelisted |
barra.brasil.gov.br |
| suspicious |
www.facebook.com |
| whitelisted |
www.receita.fazenda.gov.br |
| suspicious |
www.youtube.com |
| whitelisted |