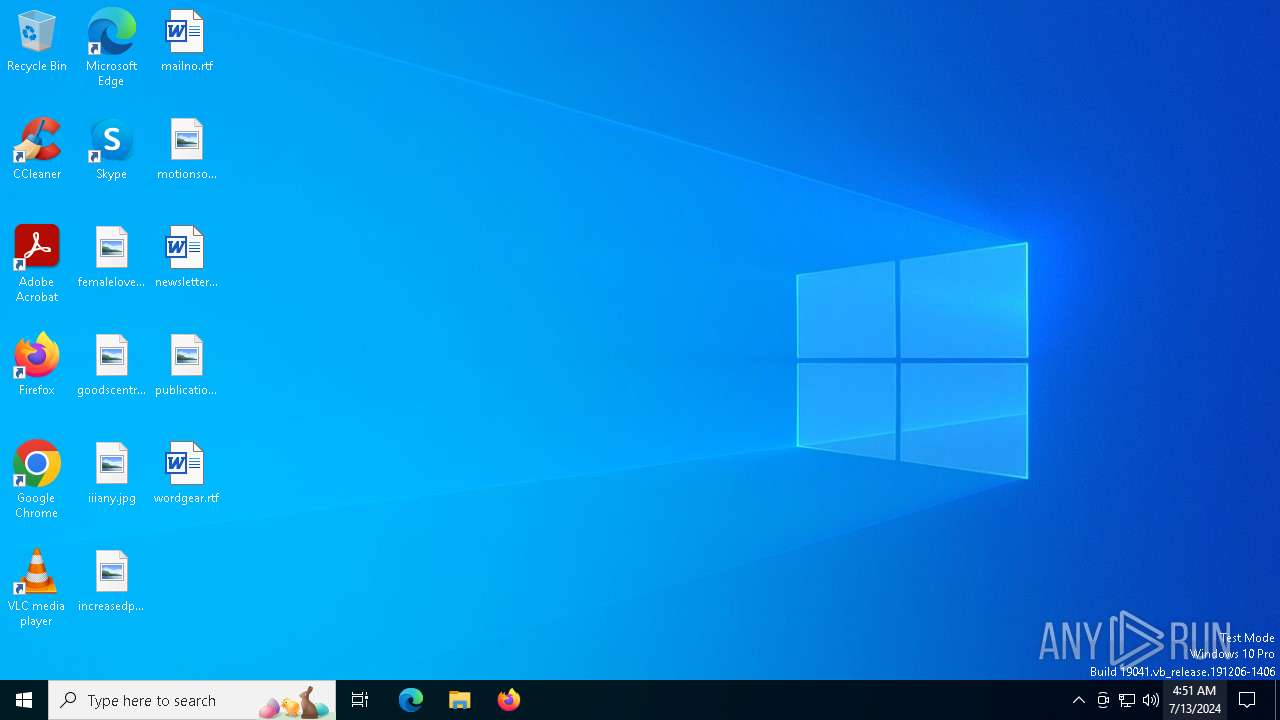
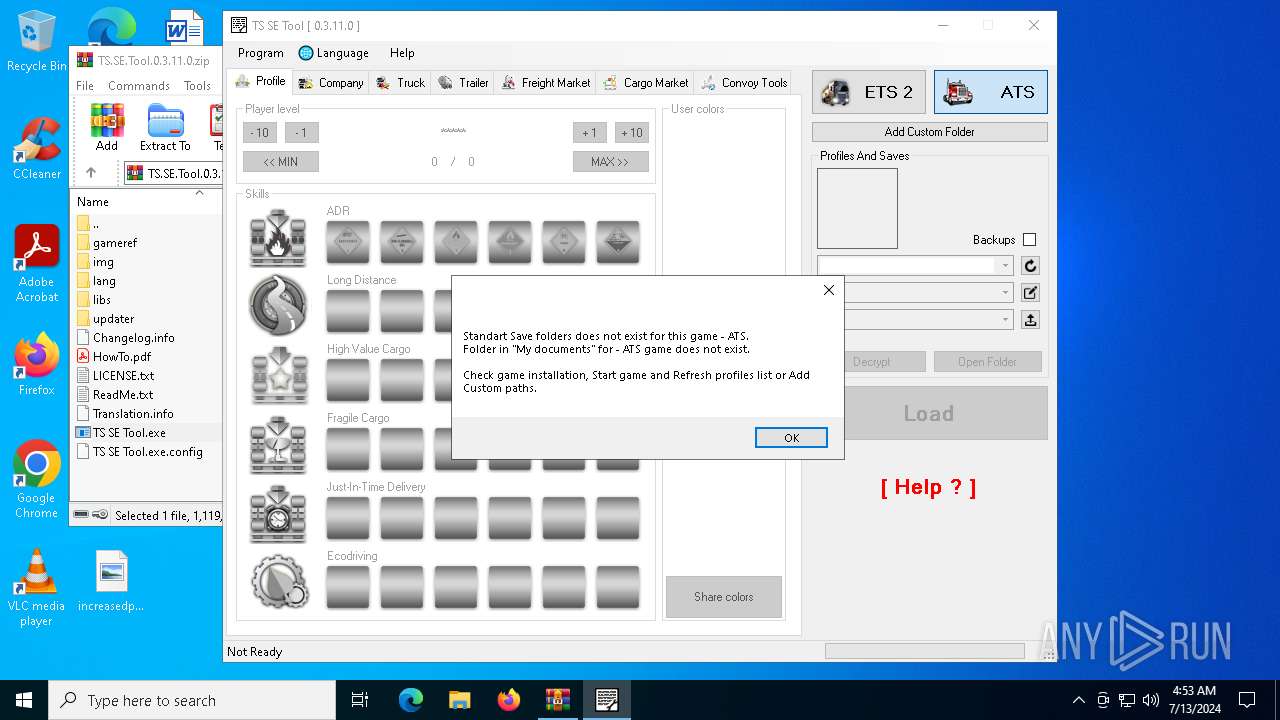
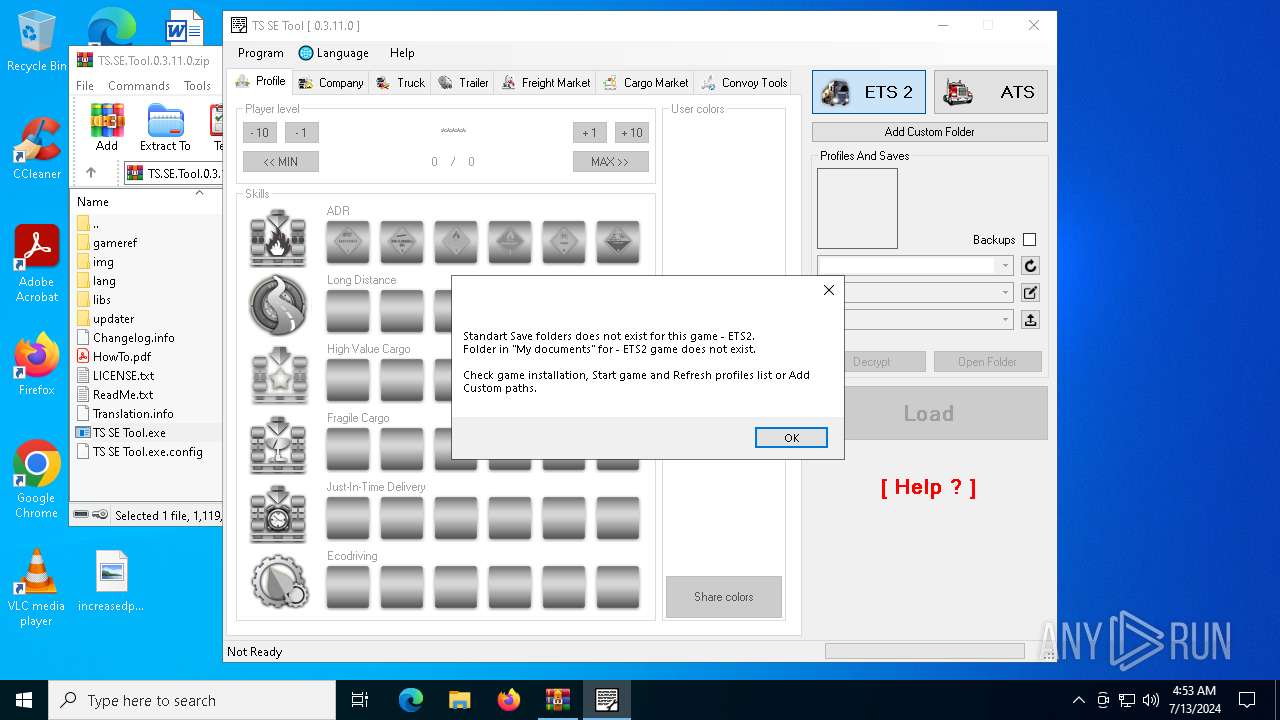
| File name: | TS.SE.Tool.0.3.11.0.zip |
| Full analysis: | https://app.any.run/tasks/da6853f4-444e-4d01-88e7-ff4641e2815b |
| Verdict: | Malicious activity |
| Analysis date: | July 13, 2024, 04:51:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 1E648981466FDE55FB95EBC60CB6A42A |
| SHA1: | D471A45521739A7F3F524920D17D10BC41266BFB |
| SHA256: | 0732CD4D861BD53B1570B90ECF928BC085E8B627C16DB35EDC9A0324D616B0DA |
| SSDEEP: | 98304:4rHVxX6fPsBbFm6MEqtot+YDyvTL+cnCDsTEVDeqgd1lABOe/EW50i1ugt7I+EWd:6jblbt4S5WG |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4320)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4320)
- TS SE Tool.exe (PID: 6224)
Reads Internet Explorer settings
- TS SE Tool.exe (PID: 6224)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4320)
Checks supported languages
- TS SE Tool.exe (PID: 6224)
Reads the computer name
- TS SE Tool.exe (PID: 6224)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4320)
Reads the machine GUID from the registry
- TS SE Tool.exe (PID: 6224)
Create files in a temporary directory
- TS SE Tool.exe (PID: 6224)
Creates files or folders in the user directory
- TS SE Tool.exe (PID: 6224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (33.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:11:27 16:43:58 |
| ZipCRC: | 0x96ac9b9a |
| ZipCompressedSize: | 3122 |
| ZipUncompressedSize: | 9496 |
| ZipFileName: | Changelog.info |
Total processes
132
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4320 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\TS.SE.Tool.0.3.11.0.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6224 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4320.12061\TS SE Tool.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4320.12061\TS SE Tool.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: TS SE Tool Exit code: 0 Version: 0.3.11.0 Modules
| |||||||||||||||
Total events
5 818
Read events
5 783
Write events
35
Delete events
0
Modification events
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\TS.SE.Tool.0.3.11.0.zip | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
27
Suspicious files
473
Text files
570
Unknown types
333
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4320.12061\gameref\cache\ATS\dlc_heavy_cargo.sdf | binary | |
MD5:3B6B7C936534AD61FEFF29FF71EB32E1 | SHA256:BA57CD33070CE955A4299C5EFB6FF8A4D29EEAE01B33CB463E753371BD3E15A4 | |||
| 4320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4320.12061\gameref\cache\ATS\def.sdf | binary | |
MD5:386B0C672C2A9DB45753AE734CD91A2C | SHA256:E6F25B45BB4F76AF5E510CF5E30FA0A4B4EA41F0F554C6E31A8419D763AE0A9A | |||
| 4320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4320.12061\gameref\cache\ATS\dlc_arizona.sdf | binary | |
MD5:5C035197FDB77042C01D4E9CA3F05098 | SHA256:5C785D959ADA21A5B9270BF3631139010AEC6E6EDE8C4C4EE7CA4E4F84C186E6 | |||
| 4320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4320.12061\gameref\cache\ATS\dlc_id.sdf | binary | |
MD5:BA9075DE5D3DE3074B4E8F631D2D1CEE | SHA256:351316C81DE68795FE34F24AF561AE6DB8363D3DD55280A2EAC26A543FF6E1C6 | |||
| 4320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4320.12061\gameref\cache\ATS\dlc_nevada.sdf | binary | |
MD5:AA407D9146228BE77E111E9DF825E750 | SHA256:0CCB272E35904C19A9596F757EA861D9F33DAEDD8DB35FC61DA960799D6E7780 | |||
| 4320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4320.12061\gameref\cache\ATS\dlc_nm.sdf | binary | |
MD5:C9D2454419CC243995FF51F780BB951B | SHA256:8EF02DFE401EBAFFB38E4F5290142902461CCB0681DE54C278A881D54605AA24 | |||
| 4320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4320.12061\gameref\cache\ATS\dlc_or.sdf | binary | |
MD5:EB4A97650CB5F2D5F987A71B3C086CAB | SHA256:81C8F9958728EE034FD52D9C1EA9C28BA7474D94D606926E1D6EC0BA3D8FDE26 | |||
| 4320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4320.12061\gameref\cache\ATS\dlc_forest_harvesting.sdf | binary | |
MD5:E83D3650E08BFEB079C2EEAE4EE7E4D3 | SHA256:B419D9556985916BBB2F6FF46F11E077AA255188D73664DD4BEA8794FA724846 | |||
| 4320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4320.12061\gameref\cache\ETS2\dlc_it.sdf | binary | |
MD5:997B89325F0473DBC5FFD24359593ADA | SHA256:728A5C60AD83B5CA5291C6253EAE74C014425554A14A9E34DB6C564314498880 | |||
| 4320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4320.12061\gameref\cache\ETS2\dlc_east.sdf | binary | |
MD5:7FB387F10771053A525A0561FDCB215A | SHA256:0FE9FC780146FF221475B98E2F58F4C2EB4060D8CB3FD2F24CC9390E2917C965 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
65
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1928 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1928 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4636 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2260 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6728 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6728 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3724 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1888 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1776 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1928 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1928 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4656 | SearchApp.exe | 104.126.37.155:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |