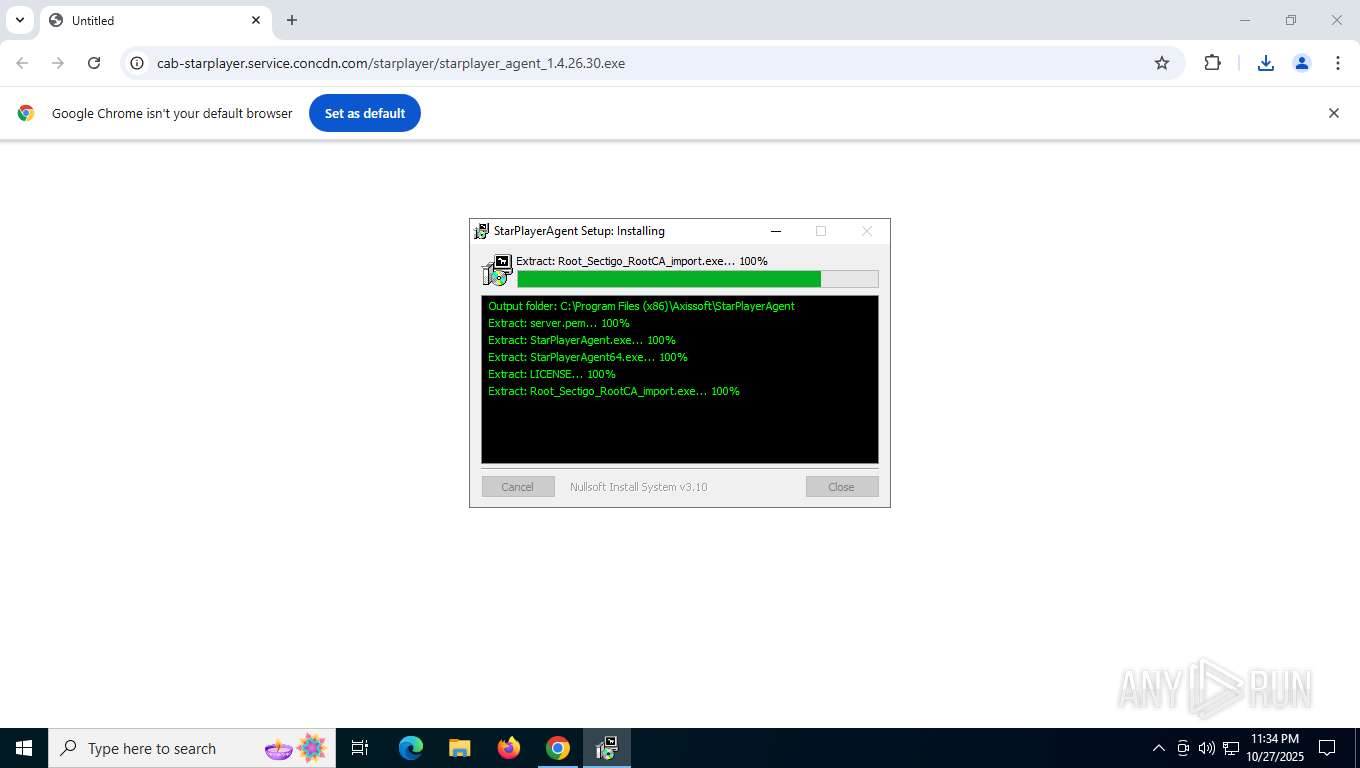
| URL: | https://cab-starplayer.service.concdn.com/starplayer/starplayer_agent_1.4.26.30.exe |
| Full analysis: | https://app.any.run/tasks/8317aff4-3c03-4de0-8aa9-7645cada73d9 |
| Verdict: | Malicious activity |
| Analysis date: | October 27, 2025, 23:34:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | 029B2E193AEB47A2AEBD92799B1B702C |
| SHA1: | 1D00E86484EE0BB80ECF4E47E898D82911C9B450 |
| SHA256: | 0729997123BFF95BD79DA46B71B8A5F3A757F923AD03E62ADED314E422F042D5 |
| SSDEEP: | 3:N8ZH+X4xbwcYNRXxaWZxvjS0Cn:20otBWRXJQJ |
MALICIOUS
Changes settings of System certificates
- Root_Sectigo_RootCA_import.exe (PID: 2316)
SUSPICIOUS
Executable content was dropped or overwritten
- starplayer_agent_1.4.26.30.exe (PID: 7192)
- Root_Sectigo_RootCA_import.exe (PID: 2316)
Uses TASKKILL.EXE to kill process
- starplayer_agent_1.4.26.30.exe (PID: 7192)
The process creates files with name similar to system file names
- starplayer_agent_1.4.26.30.exe (PID: 7192)
- Root_Sectigo_RootCA_import.exe (PID: 2316)
Malware-specific behavior (creating "System.dll" in Temp)
- Root_Sectigo_RootCA_import.exe (PID: 2316)
- starplayer_agent_1.4.26.30.exe (PID: 7192)
Adds/modifies Windows certificates
- Root_Sectigo_RootCA_import.exe (PID: 2316)
- starplayer_agent_1.4.26.30.exe (PID: 7192)
Non windows owned service launched
- StarPlayerAgent64.exe (PID: 3028)
Reads security settings of Internet Explorer
- StarPlayerAgent64.exe (PID: 3028)
- StarPlayerAgent64.exe (PID: 2180)
Executes as Windows Service
- StarPlayerAgent64.exe (PID: 3028)
Application launched itself
- StarPlayerAgent64.exe (PID: 3028)
Changes settings of the software policy
- starplayer_agent_1.4.26.30.exe (PID: 7192)
There is functionality for taking screenshot (YARA)
- StarPlayerAgent64.exe (PID: 3028)
- StarPlayerAgent64.exe (PID: 2180)
Potential Corporate Privacy Violation
- StarPlayerAgent64.exe (PID: 2180)
INFO
Application launched itself
- chrome.exe (PID: 7380)
Executable content was dropped or overwritten
- chrome.exe (PID: 7380)
The sample compiled with english language support
- chrome.exe (PID: 7380)
- starplayer_agent_1.4.26.30.exe (PID: 7192)
Create files in a temporary directory
- starplayer_agent_1.4.26.30.exe (PID: 7192)
- Root_Sectigo_RootCA_import.exe (PID: 2316)
Checks supported languages
- starplayer_agent_1.4.26.30.exe (PID: 7192)
- Root_Sectigo_RootCA_import.exe (PID: 2316)
- StarPlayerAgent64.exe (PID: 6140)
- StarPlayerAgent64.exe (PID: 3028)
- StarPlayerAgent64.exe (PID: 2180)
- StarPlayerAgent64.exe (PID: 6364)
Launching a file from the Downloads directory
- chrome.exe (PID: 7380)
Reads the computer name
- starplayer_agent_1.4.26.30.exe (PID: 7192)
- Root_Sectigo_RootCA_import.exe (PID: 2316)
- StarPlayerAgent64.exe (PID: 6364)
- StarPlayerAgent64.exe (PID: 6140)
- StarPlayerAgent64.exe (PID: 2180)
- StarPlayerAgent64.exe (PID: 3028)
Creates files in the program directory
- Root_Sectigo_RootCA_import.exe (PID: 2316)
- starplayer_agent_1.4.26.30.exe (PID: 7192)
The sample compiled with korean language support
- starplayer_agent_1.4.26.30.exe (PID: 7192)
Reads the machine GUID from the registry
- Root_Sectigo_RootCA_import.exe (PID: 2316)
- StarPlayerAgent64.exe (PID: 2180)
Checks proxy server information
- StarPlayerAgent64.exe (PID: 3028)
- StarPlayerAgent64.exe (PID: 2180)
- slui.exe (PID: 688)
Creates files or folders in the user directory
- StarPlayerAgent64.exe (PID: 2180)
Creates a software uninstall entry
- starplayer_agent_1.4.26.30.exe (PID: 7192)
Reads the software policy settings
- slui.exe (PID: 688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
198
Monitored processes
41
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --string-annotations --gpu-preferences=UAAAAAAAAADoABAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAABCAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=5768,i,1610655386649849226,18260590748169931892,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5664 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 644 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --string-annotations --field-trial-handle=5516,i,1610655386649849226,18260590748169931892,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5668 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 688 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1264 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --field-trial-handle=5640,i,1610655386649849226,18260590748169931892,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5868 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1876 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | StarPlayerAgent64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2180 | "C:\Program Files (x86)\Axissoft\StarPlayerAgent\StarPlayerAgent64.exe" work | C:\Program Files (x86)\Axissoft\StarPlayerAgent\StarPlayerAgent64.exe | StarPlayerAgent64.exe | ||||||||||||
User: admin Company: Axissoft Integrity Level: MEDIUM Description: StarPlayer Agent Version: 1.4.26.30 Modules
| |||||||||||||||
| 2316 | "C:\Program Files (x86)\Axissoft\StarPlayerAgent\Root_Sectigo_RootCA_import.exe" | C:\Program Files (x86)\Axissoft\StarPlayerAgent\Root_Sectigo_RootCA_import.exe | starplayer_agent_1.4.26.30.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2392 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 2792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --field-trial-handle=3556,i,1610655386649849226,18260590748169931892,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5460 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --field-trial-handle=5868,i,1610655386649849226,18260590748169931892,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5852 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
Total events
15 070
Read events
15 043
Write events
20
Delete events
7
Modification events
| (PID) Process: | (2316) Root_Sectigo_RootCA_import.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | 9F744E9F2B4DBAEC0F312C50B6563B8E2D93C311 |
Value: | |||
| (PID) Process: | (2316) Root_Sectigo_RootCA_import.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\9F744E9F2B4DBAEC0F312C50B6563B8E2D93C311 |
| Operation: | write | Name: | Blob |
Value: 0300000001000000140000009F744E9F2B4DBAEC0F312C50B6563B8E2D93C31120000000010000008D020000308202893082020FA00302010202101F47AFAA62007050544C019E9B63992A300A06082A8648CE3D040303308185310B3009060355040613024742311B30190603550408131247726561746572204D616E636865737465723110300E0603550407130753616C666F7264311A3018060355040A1311434F4D4F444F204341204C696D69746564312B302906035504031322434F4D4F444F204543432043657274696669636174696F6E20417574686F72697479301E170D3038303330363030303030305A170D3338303131383233353935395A308185310B3009060355040613024742311B30190603550408131247726561746572204D616E636865737465723110300E0603550407130753616C666F7264311A3018060355040A1311434F4D4F444F204341204C696D69746564312B302906035504031322434F4D4F444F204543432043657274696669636174696F6E20417574686F726974793076301006072A8648CE3D020106052B810400220362000403477B2F75C9821585FB75E49116D4AB6299F53E520B06CE41007F97E10A243C1D0104EE3DD28D09970CE075E4FAFB778A2AF503604B368B162316AD0971F44AF42850B4FE881C6E3F6C2F2F09595BA55B0B3399E2C33D89F96A2CEFB2D306E9A3423040301D0603551D0E041604147571A7194819BC9D9DEA4147DF94C4487799D379300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300A06082A8648CE3D0403030368003065023100EF035B7AACB7780A72B788DFFFB54614090AFAA0E67D08C61A87BD18A873BD26CA600C9DCE999FCF5C0F30E1BE1431EA023014F4933C49A7337A904647B3637D139B4EB76F18378053FEDD20E0359A36D1C701B9E6DCDDF3FF1D2C3A1657D99239D6 | |||
| (PID) Process: | (2316) Root_Sectigo_RootCA_import.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | 2B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E |
Value: | |||
| (PID) Process: | (2316) Root_Sectigo_RootCA_import.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\2B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E |
| Operation: | write | Name: | Blob |
Value: 0300000001000000140000002B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E2000000001000000E2050000308205DE308203C6A003020102021001FD6D30FCA3CA51A81BBC640E35032D300D06092A864886F70D01010C0500308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F72697479301E170D3130303230313030303030305A170D3338303131383233353935395A308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F7269747930820222300D06092A864886F70D01010105000382020F003082020A028202010080126517360EC3DB08B3D0AC570D76EDCD27D34CAD508361E2AA204D092D6409DCCE899FCC3DA9ECF6CFC1DCF1D3B1D67B3728112B47DA39C6BC3A19B45FA6BD7D9DA36342B676F2A93B2B91F8E26FD0EC162090093EE2E874C918B491D46264DB7FA306F188186A90223CBCFE13F087147BF6E41F8ED4E451C61167460851CB8614543FBC33FE7E6C9CFF169D18BD518E35A6A766C87267DB2166B1D49B7803C0503AE8CCF0DCBC9E4CFEAF0596351F575AB7FFCEF93DB72CB6F654DDC8E7123A4DAE4C8AB75C9AB4B7203DCA7F2234AE7E3B68660144E7014E46539B3360F794BE5337907343F332C353EFDBAAFE744E69C76B8C6093DEC4C70CDFE132AECC933B517895678BEE3D56FE0CD0690F1B0FF325266B336DF76E47FA7343E57E0EA566B1297C3284635589C40DC19354301913ACD37D37A7EB5D3A6C355CDB41D712DAA9490BDFD8808A0993628EB566CF2588CD84B8B13FA4390FD9029EEB124C957CF36B05A95E1683CCB867E2E8139DCC5B82D34CB3ED5BFFDEE573AC233B2D00BF3555740949D849581A7F9236E651920EF3267D1C4D17BCC9EC4326D0BF415F40A94444F499E757879E501F5754A83EFD74632FB1506509E658422E431A4CB4F0254759FA041E93D426464A5081B2DEBE78B7FC6715E1C957841E0F63D6E962BAD65F552EEA5CC62808042539B80E2BA9F24C971C073F0D52F5EDEF2F820F0203010001A3423040301D0603551D0E041604145379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300D06092A864886F70D01010C050003820201005CD47C0DCFF7017D4199650C73C5529FCBF8CF99067F1BDA43159F9E0255579614F1523C27879428ED1F3A0137A276FC5350C0849BC66B4EBA8C214FA28E556291F36915D8BC88E3C4AA0BFDEFA8E94B552A06206D55782919EE5F305C4B241155FF249A6E5E2A2BEE0B4D9F7FF70138941495430709FB60A9EE1CAB128CA09A5EA7986A596D8B3F08FBC8D145AF18156490120F73282EC5E2244EFC58ECF0F445FE22B3EB2F8ED2D9456105C1976FA876728F8B8C36AFBF0D05CE718DE6A66F1F6CA67162C5D8D083720CF16711890C9C134C7234DFBCD571DFAA71DDE1B96C8C3C125D65DABD5712B6436BFFE5DE4D661151CF99AEEC17B6E871918CDE49FEDD3571A21527941CCF61E326BB6FA36725215DE6DD1D0B2E681B3B82AFEC836785D4985174B1B9998089FF7F78195C794A602E9240AE4C372A2CC9C762C80E5DF7365BCAE0252501B4DD1A079C77003FD0DCD5EC3DD4FABB3FCC85D66F7FA92DDFB902F7F5979AB535DAC367B0874AA9289E238EFF5C276BE1B04FF307EE002ED45987CB524195EAF447D7EE6441557C8D590295DD629DC2B9EE5A287484A59BB790C70C07DFF589367432D628C1B0B00BE09C4CC31CD6FCE369B54746812FA282ABD3634470C48DFF2D33BAAD8F7BB57088AE3E19CF4028D8FCC890BB5D9922F552E658C51F883143EE881DD7C68E3C436A1DA718DE7D3D16F162F9CA90A8FD | |||
| (PID) Process: | (2316) Root_Sectigo_RootCA_import.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | D1EB23A46D17D68FD92564C2F1F1601764D8E349 |
Value: | |||
| (PID) Process: | (2316) Root_Sectigo_RootCA_import.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\D1EB23A46D17D68FD92564C2F1F1601764D8E349 |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000D1EB23A46D17D68FD92564C2F1F1601764D8E349200000000100000036040000308204323082031AA003020102020101300D06092A864886F70D0101050500307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C18414141204365727469666963617465205365727669636573301E170D3034303130313030303030305A170D3238313233313233353935395A307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C1841414120436572746966696361746520536572766963657330820122300D06092A864886F70D01010105000382010F003082010A0282010100BE409DF46EE1EA76871C4D45448EBE46C883069DC12AFE181F8EE402FAF3AB5D508A16310B9A06D0C57022CD492D5463CCB66E68460B53EACB4C24C0BC724EEAF115AEF4549A120AC37AB23360E2DA8955F32258F3DEDCCFEF8386A28C944F9F68F29890468427C776BFE3CC352C8B5E07646582C048B0A891F9619F762050A891C766B5EB78620356F08A1A13EA31A31EA099FD38F6F62732586F07F56BB8FB142BAFB7AACCD6635F738CDA0599A838A8CB17783651ACE99EF4783A8DCF0FD942E2980CAB2F9F0E01DEEF9F9949F12DDFAC744D1B98B547C5E529D1F99018C7629CBE83C7267B3E8A25C7C0DD9DE6356810209D8FD8DED2C3849C0D5EE82FC90203010001A381C03081BD301D0603551D0E04160414A0110A233E96F107ECE2AF29EF82A57FD030A4B4300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF307B0603551D1F047430723038A036A0348632687474703A2F2F63726C2E636F6D6F646F63612E636F6D2F414141436572746966696361746553657276696365732E63726C3036A034A0328630687474703A2F2F63726C2E636F6D6F646F2E6E65742F414141436572746966696361746553657276696365732E63726C300D06092A864886F70D010105050003820101000856FC02F09BE8FFA4FAD67BC64480CE4FC4C5F60058CCA6B6BC1449680476E8E6EE5DEC020F60D68D50184F264E01E3E6B0A5EEBFBC745441BFFDFC12B8C74F5AF48960057F60B7054AF3F6F1C2BFC4B97486B62D7D6BCCD2F346DD2FC6E06AC3C334032C7D96DD5AC20EA70A99C1058BAB0C2FF35C3ACF6C37550987DE53406C58EFFCB6AB656E04F61BDC3CE05A15C69ED9F15948302165036CECE92173EC9B03A1E037ADA015188FFABA02CEA72CA910132CD4E50826AB229760F8905E74D4A29A53BDF2A968E0A26EC2D76CB1A30F9EBFEB68E756F2AEF2E32B383A0981B56B85D7BE2DED3F1AB7B263E2F5622C82D46A004150F139839F95E93696986E | |||
| (PID) Process: | (2316) Root_Sectigo_RootCA_import.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | 02FAF3E291435468607857694DF5E45B68851868 |
Value: | |||
| (PID) Process: | (2316) Root_Sectigo_RootCA_import.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\02FAF3E291435468607857694DF5E45B68851868 |
| Operation: | write | Name: | Blob |
Value: 03000000010000001400000002FAF3E291435468607857694DF5E45B6885186820000000010000003A040000308204363082031EA003020102020101300D06092A864886F70D0101050500306F310B300906035504061302534531143012060355040A130B416464547275737420414231263024060355040B131D41646454727573742045787465726E616C20545450204E6574776F726B312230200603550403131941646454727573742045787465726E616C20434120526F6F74301E170D3030303533303130343833385A170D3230303533303130343833385A306F310B300906035504061302534531143012060355040A130B416464547275737420414231263024060355040B131D41646454727573742045787465726E616C20545450204E6574776F726B312230200603550403131941646454727573742045787465726E616C20434120526F6F7430820122300D06092A864886F70D01010105000382010F003082010A0282010100B7F71A33E6F200042D39E04E5BED1FBC6C0FCDB5FA23B6CEDE9B113397A4294C7D939FBD4ABC93ED031AE38FCFE56D505AD69729945A80B0497ADB2E95FDB8CABF37382D1E3E9141AD7056C7F04F3FE8329E74CAC89054E9C65F0F789D9A403C0EAC61AA5E148F9E87A16A50DCD79A4EAF05B3A671949C71B350600AC7139D38078602A8E9A869261890AB4CB04F23AB3A4F84D8DFCE9FE1696FBBD742D76B44E4C7ADEE6D415F725A710837B37965A459A09437F7002F0DC29272DAD03872DB14A845C45D2A7DB7B4D6C4EEACCD1344B7C92BDD430025FA61B9696A582311B7A7338F567559F5CD29D746B70A2B65B6D3426F15B2B87BFBEFE95D53D5345A270203010001A381DC3081D9301D0603551D0E04160414ADBD987A34B426F7FAC42654EF03BDE024CB541A300B0603551D0F040403020106300F0603551D130101FF040530030101FF3081990603551D2304819130818E8014ADBD987A34B426F7FAC42654EF03BDE024CB541AA173A471306F310B300906035504061302534531143012060355040A130B416464547275737420414231263024060355040B131D41646454727573742045787465726E616C20545450204E6574776F726B312230200603550403131941646454727573742045787465726E616C20434120526F6F74820101300D06092A864886F70D01010505000382010100B09BE08525C2D623E20F9606929D41989CD9847981D91E5B14072336658FB0D877BBAC416C47608351B0F9323DE7FCF62613C78016A5BF5AFC87CF787989219AE24C070A8635BCF2DE51C4D296B7DC7E4EEE70FD1C39EB0C0251142D8EBD16E0C1DF4675E724ADECF442B48593701067BA9D06354A18D32B7ACC5142A17A63D1E6BBA1C52BC236BE130DE6BD637E797BA7090D40AB6ADD8F8AC3F6F68C1A420551D445F59FA76221681520433C99E77CBD24D8A9911773883F561B313818B4710F9ACDC80E9E8E2E1BE18C9883CB1F31F1444CC604734976600FC7F8BD17806B2EE9CC4C0E5A9A790F200A2ED59E63261E559294D882175A7BD0BCC78F4E8604 | |||
| (PID) Process: | (2316) Root_Sectigo_RootCA_import.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | EE869387FFFD8349AB5AD14322588789A457B012 |
Value: | |||
| (PID) Process: | (2316) Root_Sectigo_RootCA_import.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\EE869387FFFD8349AB5AD14322588789A457B012 |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000EE869387FFFD8349AB5AD14322588789A457B0122000000001000000D4030000308203D0308202B8A003020102021020A4C47FDDDFE1C75363071388776012300D06092A864886F70D0101050500308181310B3009060355040613024742311B30190603550408131247726561746572204D616E636865737465723110300E0603550407130753616C666F7264311A3018060355040A1311434F4D4F444F204341204C696D69746564312730250603550403131E434F4D4F444F2043657274696669636174696F6E20417574686F72697479301E170D3131303130313030303030305A170D3330313233313233353935395A308181310B3009060355040613024742311B30190603550408131247726561746572204D616E636865737465723110300E0603550407130753616C666F7264311A3018060355040A1311434F4D4F444F204341204C696D69746564312730250603550403131E434F4D4F444F2043657274696669636174696F6E20417574686F7269747930820122300D06092A864886F70D01010105000382010F003082010A0282010100D0408B8B72E3911BF751C11B540498D3A9BFC1E68A5D3B87FBBB88CE0DE32F3F0696F0A2295099AEDB3BA157B0745171CDED42914D41FEA9C8D86A867744BB596697505EB4D42C7044CFDA379542693C30C471B352F0214DA1D8BA397C1C9EA3249DF2831698AA167C439B155BB7AE3491FED4622618469A3FEBC1F9F19057EBAC7A0D8BDB72306A66D5E046A370DC68D9FF04488977DEB5E9FB676D41E9BC39BD32D96202F1B1A83D6E379CE22FE2D3A2268BC6B8554388E1233EA5D224396A47AB00D4A1B3A925FE0D3FA71DBAD351C10BA4DAAC38EF55502405654693344F2D8DADC6D42119D28ECA056171077347E58A1912BD044DCE4E9CA548ACBB26F70203010001A3423040301D0603551D0E041604140B58E58BC64C1537A440A930A921BE47365A56FF300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300D06092A864886F70D010105050003820101002FC9C41C073BCF610200B1D9215175720330B0C4161F6C008B10ACAFF147D4AE103C0C1AF8D4936CAC10377CB7A68364ADCDDF0E87339D37B0C67B3872B1F31A0EA3F9557A6D03660317954AF1B17ADF562106428FB1D3A885DEEE971D62EBA7E7311266C30FA64B2E4182F7FDC91BA81BAFEE3CCEE39CAE2807A12C9B24C20F232683328B860F1F2B124625168F7690036BDEBCAA22686B8CA1AC2B1139A6DB70C27D72E933E7FC26F1745A91E69D84ACF8A8061946E6A7E9AA3422A4A19F7AADB7B2A49A338871023C2ED67AB21FA2CAC0DD2F1094FDB38C84207946D505D410E4D2DB644FB85BEE1BC520475B94AB6ED495331DA61571F1F894CA54393EC1 | |||
Executable files
23
Suspicious files
369
Text files
42
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RFfb80c.TMP | — | |
MD5:— | SHA256:— | |||
| 7380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RFfb81b.TMP | — | |
MD5:— | SHA256:— | |||
| 7380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RFfb81b.TMP | — | |
MD5:— | SHA256:— | |||
| 7380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RFfb81b.TMP | — | |
MD5:— | SHA256:— | |||
| 7380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RFfb81b.TMP | — | |
MD5:— | SHA256:— | |||
| 7380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
59
DNS requests
39
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7652 | chrome.exe | GET | 200 | 142.250.186.174:80 | http://clients2.google.com/time/1/current?cup2key=8:6kLVkDyqlYaB5N22kbvUqW1_pFL2MQHgPEttND8_f8o&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
6716 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2180 | StarPlayerAgent64.exe | GET | 200 | 183.111.14.45:80 | http://cab-starplayer.service.concdn.com/starplayer/localhost.axissoft.co.kr.2024.09.pem.txt?date=20251027 | unknown | — | — | unknown |
6180 | SIHClient.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fa5db9388dd1e70b | unknown | — | — | whitelisted |
6928 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
3132 | slui.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?67e70c38f661bf3b | unknown | — | — | whitelisted |
6928 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
6928 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
6928 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
6928 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2392 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5596 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6884 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7652 | chrome.exe | 142.250.186.174:80 | clients2.google.com | GOOGLE | US | whitelisted |
7652 | chrome.exe | 142.250.185.170:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
7652 | chrome.exe | 183.111.14.45:443 | cab-starplayer.service.concdn.com | Korea Telecom | KR | unknown |
7652 | chrome.exe | 64.233.167.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7380 | chrome.exe | 224.0.0.251:5353 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
cab-starplayer.service.concdn.com |
| unknown |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2180 | StarPlayerAgent64.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
2180 | StarPlayerAgent64.exe | Misc activity | ET INFO Observed UA-CPU Header |
Process | Message |
|---|---|
StarPlayerAgent64.exe | Complete installed |
StarPlayerAgent64.exe | Started service |
StarPlayerAgent64.exe | work... |
StarPlayerAgent64.exe | C:\Program Files (x86)\Axissoft\StarPlayerAgent\StarPlayerAgent64.exe work |
StarPlayerAgent64.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\localhost.axissoft.co.kr.2024.09.pem[1].txt |
StarPlayerAgent64.exe | starplayer_monitoring.onopen... |