| File name: | trigger.ps1 |
| Full analysis: | https://app.any.run/tasks/e19a79d0-76e6-4026-9a7c-040f0b45be83 |
| Verdict: | Malicious activity |
| Analysis date: | November 20, 2024, 23:30:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 136BD5042C063EE3047B2CF91CE3A13E |
| SHA1: | 8EE372EFF6166CEA45B32F40008DCA9A61A75B5A |
| SHA256: | 071BDFF08A6119B3A845F1DD9B10F7B7EAD26E56B845137D4E5A96538BB917D4 |
| SSDEEP: | 3:sR1yLd0R5LRdkeTA/snzTH3x8Jd34yOGAsvAlenhR:w1yLOR5L7kM1zLh8Jd34zTghR |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 376)
SUSPICIOUS
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 376)
Checks for external IP
- svchost.exe (PID: 2192)
- powershell.exe (PID: 376)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2192)
- powershell.exe (PID: 376)
Executable content was dropped or overwritten
- powershell.exe (PID: 376)
INFO
Checks proxy server information
- powershell.exe (PID: 376)
Disables trace logs
- powershell.exe (PID: 376)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 376)
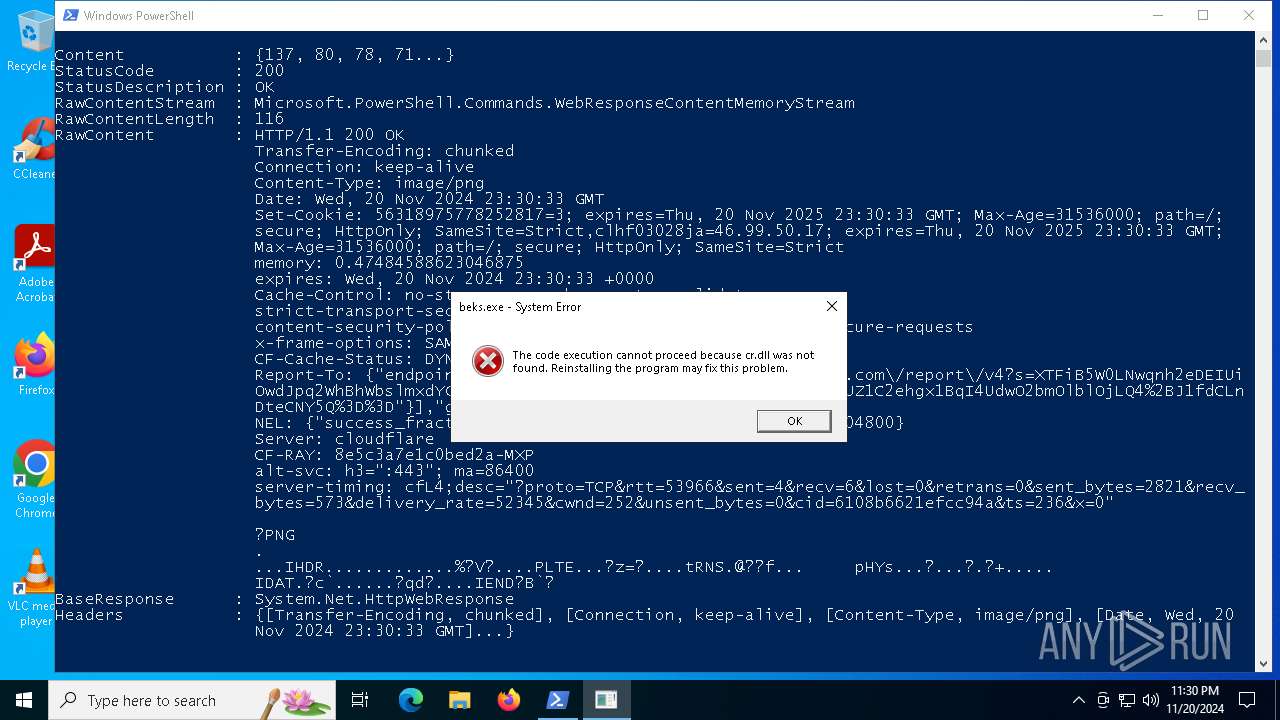
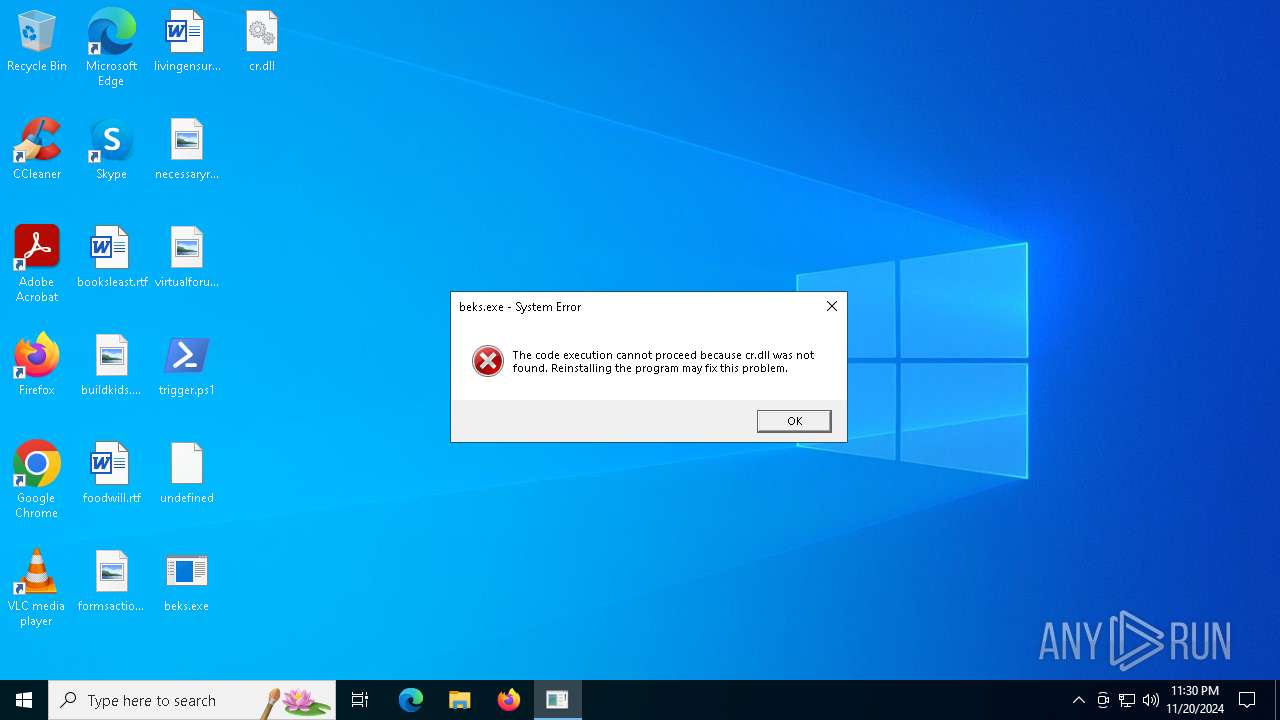
The executable file from the user directory is run by the Powershell process
- beks.exe (PID: 4036)
Manual execution by a user
- beks.exe (PID: 3732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
120
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 376 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\trigger.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | "C:\Users\admin\Desktop\beks.exe" | C:\Users\admin\Desktop\beks.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 4036 | "C:\Users\admin\AppData\Roaming\Hashed\beks.exe" | C:\Users\admin\AppData\Roaming\Hashed\beks.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
8 829
Read events
8 829
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
5
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 376 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\9UGHIWVJIXTFWZ43YYXL.temp | binary | |
MD5:BBEEE8AD126C817E3BA99263486852A6 | SHA256:7EA45684074DCE60361C63AA91CCD79CFF3CA6C9F56C1C0B4C88082CB7B98448 | |||
| 376 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RFea2b4.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 376 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p0q2jvth.nm0.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 376 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:BBEEE8AD126C817E3BA99263486852A6 | SHA256:7EA45684074DCE60361C63AA91CCD79CFF3CA6C9F56C1C0B4C88082CB7B98448 | |||
| 376 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_y315t4wf.vqb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 376 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:DB2608498B3BED14544D19563400D298 | SHA256:AB0ED00D2883AB8312921F32A27E9C8E08B28BE6BD57DB11D8F0C56BB77D8AA1 | |||
| 376 | powershell.exe | C:\Users\admin\AppData\Roaming\Hashed\cr.dll | executable | |
MD5:2A53C7F50B074DB464F7DACFCBAD3BE8 | SHA256:EE5C5DD1AEE927A6BCB8E390A0D2C5ADCDA66DA5EC9E7D41B22014DD3181E793 | |||
| 376 | powershell.exe | C:\Users\admin\AppData\Roaming\pkzd.zip | compressed | |
MD5:5CB3B50E145EBE31F3EFFF1A79E85445 | SHA256:59AEB2712A0D12740366A62CC3C6FAA8A3CE66317FC74DCC4C1A997D95EEF9E9 | |||
| 376 | powershell.exe | C:\Users\admin\AppData\Roaming\Hashed\beks.exe | executable | |
MD5:02A3FF6CF40A59890512E2199C3A3256 | SHA256:A539405F9E4C86CE4ADE7FDFE39ECC2DA493083654F5CD6662BB14B9BBB9CA53 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
26
DNS requests
10
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6024 | RUXIMICS.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6024 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 172.67.167.249:443 | https://iplogger.co/1t0RV4 | unknown | image | 116 b | shared |
— | — | POST | 200 | 172.67.152.241:443 | https://steep-number.cyou/api | unknown | text | 17.1 Kb | unknown |
— | — | GET | 200 | 185.61.154.193:443 | https://fadeaway.supply/krekan.zip | unknown | compressed | 3.49 Mb | unknown |
— | — | GET | 200 | 185.61.154.192:443 | https://benetinc.com/next/zukaz.txt | unknown | text | 498 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6024 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4932 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6024 | RUXIMICS.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4932 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6024 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4932 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
benetinc.com |
| unknown |
fadeaway.supply |
| unknown |
iplogger.co |
| shared |
steep-number.cyou |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
Threats
2 ETPRO signatures available at the full report