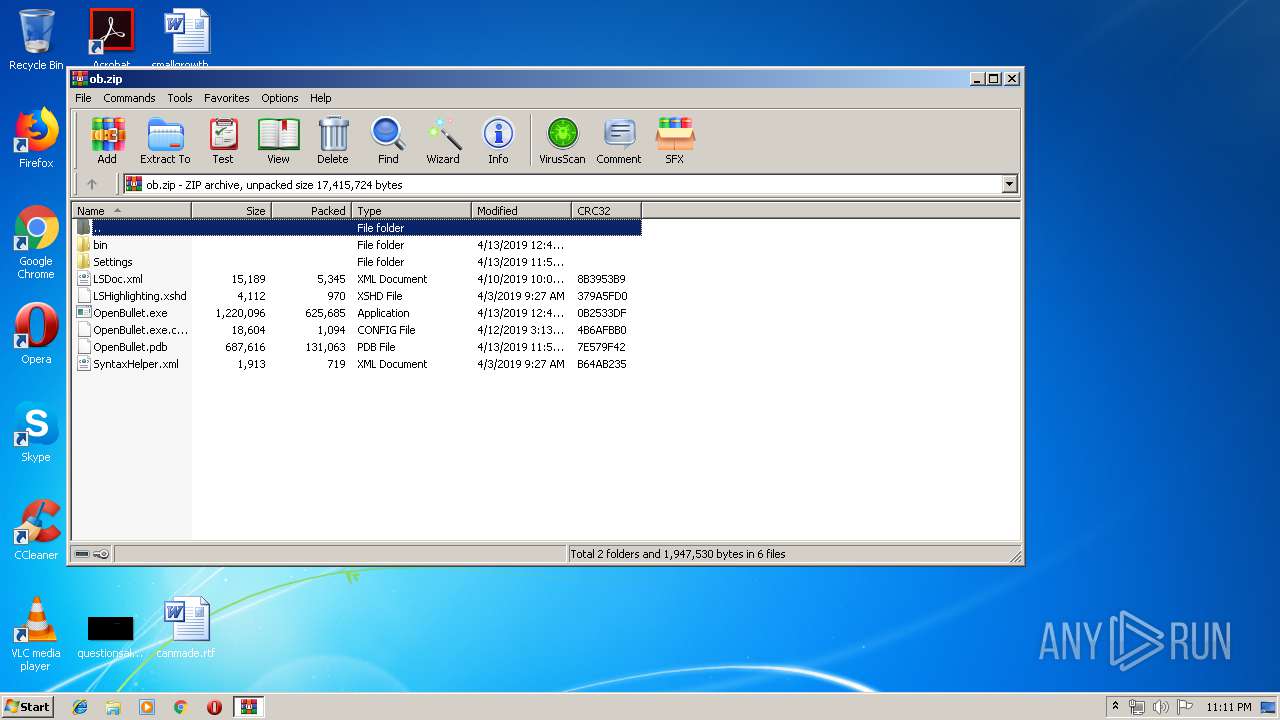
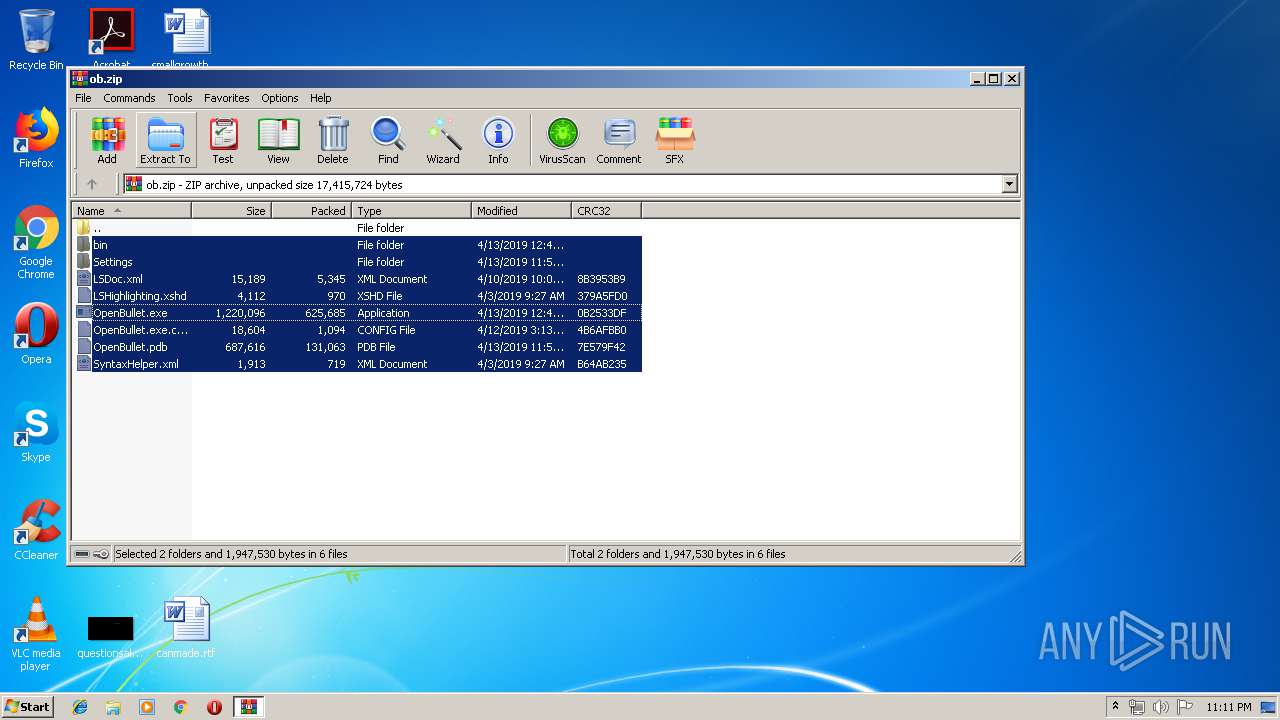
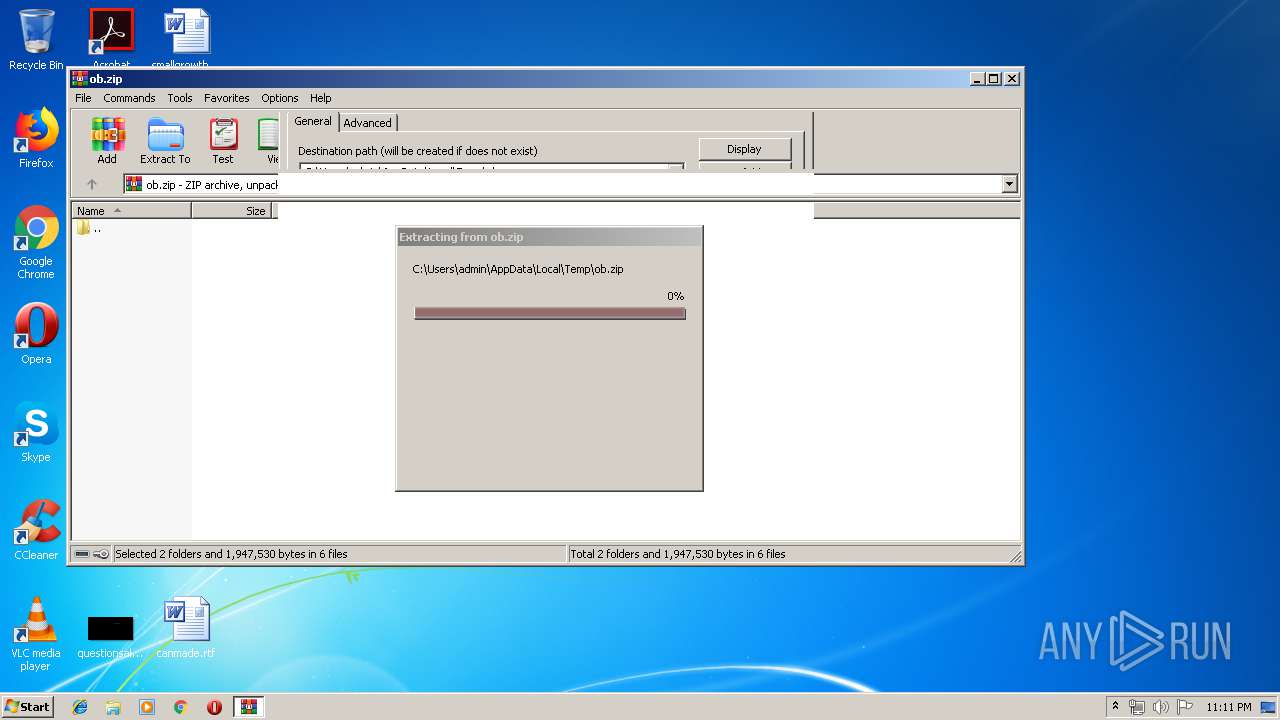
| download: | ob.zip |
| Full analysis: | https://app.any.run/tasks/375e1e89-1bb7-4dc0-97ad-ee9037edfdf9 |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2019, 22:11:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 38650C7F9FF66672F22EEDF991D65FA6 |
| SHA1: | 0C43ADCA7C5C56DFE4970F00F23BC5E387B92320 |
| SHA256: | 071299FD52EE06AD2467997D37D4091026B7C6C1AE40F9C8A495B305D01FB72C |
| SSDEEP: | 196608:G4/RcA7fyxXud7BLlVQ7ZWXRd6KOBZOxmOsjDzP8BW:G4/9LcXuzLQ7ZWXRzOB4szZ |
MALICIOUS
Application was dropped or rewritten from another process
- OpenBullet.exe (PID: 2740)
Loads dropped or rewritten executable
- OpenBullet.exe (PID: 2740)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1512)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:04:13 11:42:05 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
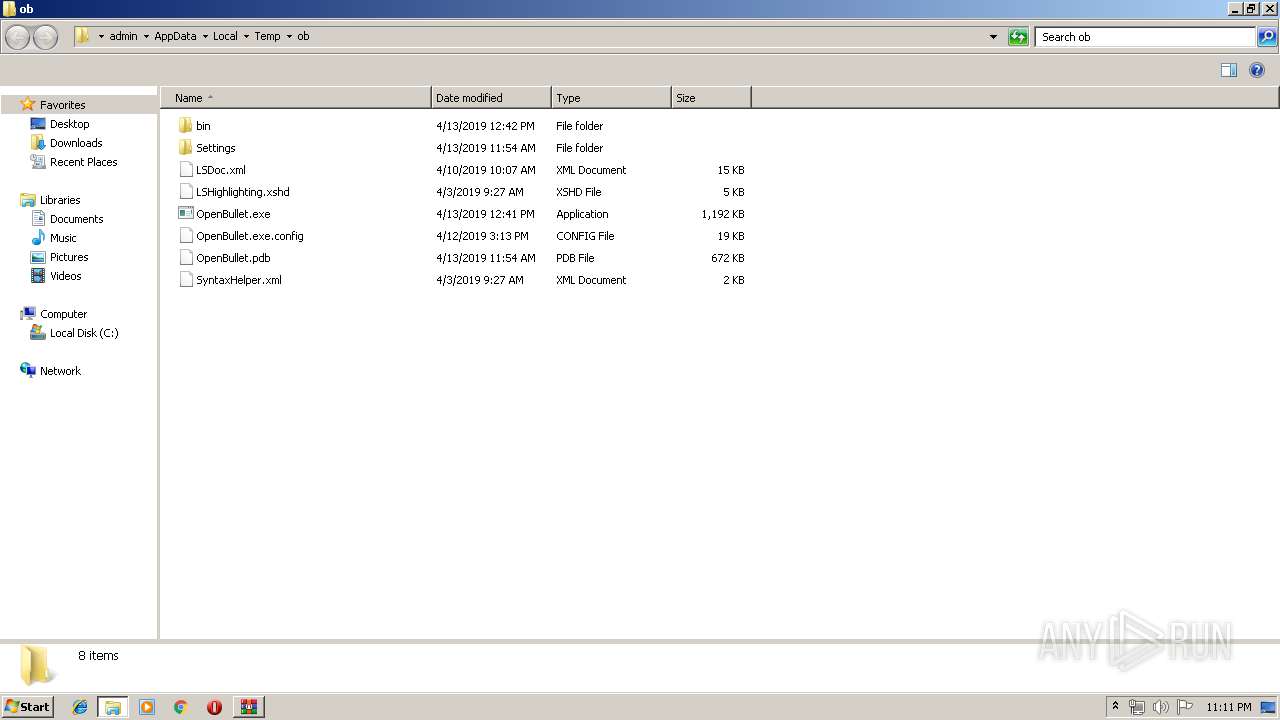
| ZipFileName: | bin/ |
Total processes
33
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1512 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\ob.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
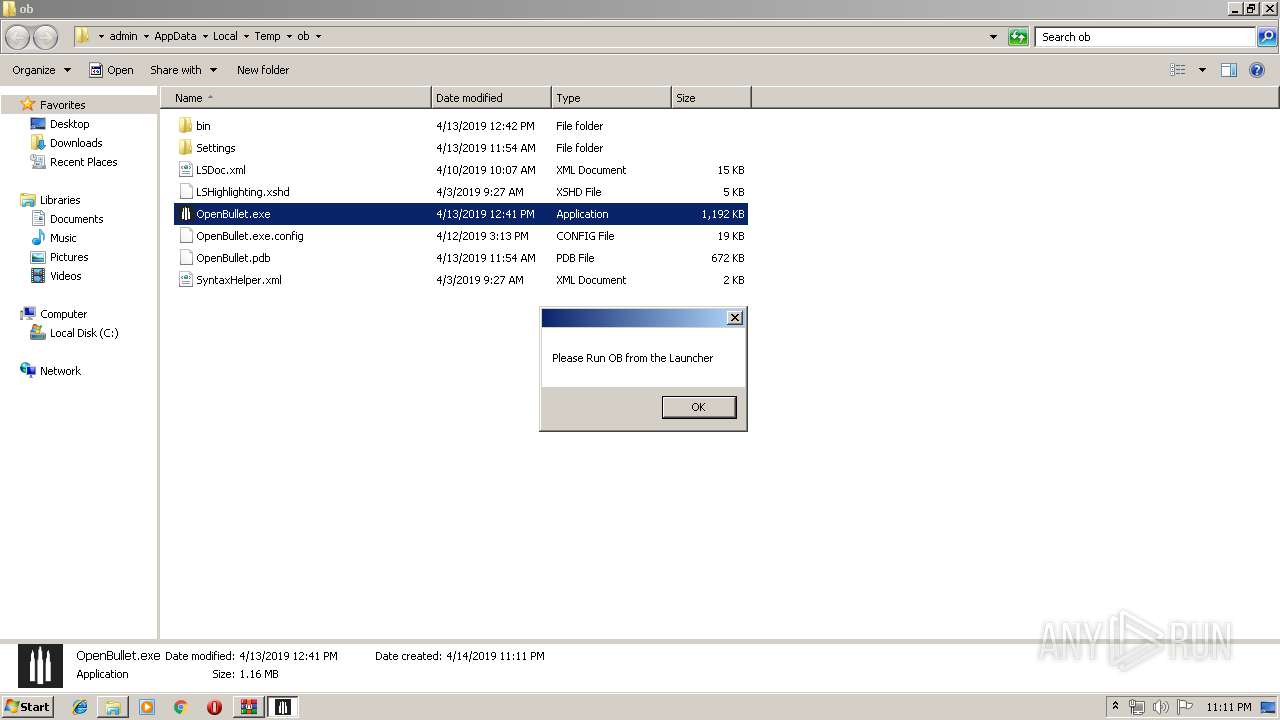
| 2740 | "C:\Users\admin\AppData\Local\Temp\ob\OpenBullet.exe" | C:\Users\admin\AppData\Local\Temp\ob\OpenBullet.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: OpenBullet Exit code: 0 Version: 1.2.1.0 Modules
| |||||||||||||||
Total events
477
Read events
443
Write events
34
Delete events
0
Modification events
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ob.zip | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\msxml3r.dll,-1 |
Value: XML Document | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Extraction\Profile |
| Operation: | write | Name: | Overwrite |
Value: 0 | |||
Executable files
125
Suspicious files
0
Text files
5
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ob\bin\Extreme.Net.dll | executable | |
MD5:— | SHA256:— | |||
| 1512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ob\bin\AngleSharp.dll | executable | |
MD5:BF331AB2E9BB06D900929DE29C659AE8 | SHA256:0B6D37C6113914DECB8AE2142DEE7CF476206036806821AC6DC63D69269F827B | |||
| 1512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ob\bin\Leaf.xNet.dll | executable | |
MD5:3F303B19BFF2A4AD3AEFA94C1A897F34 | SHA256:B762310FBDE4B23D9D353998AC8B11292F715659247674352B9411FAC412D246 | |||
| 1512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ob\bin\BBCX.dll | executable | |
MD5:— | SHA256:— | |||
| 1512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ob\bin\LiteDB.dll | executable | |
MD5:25B242D00C6C32E1F437EB2064EA2E29 | SHA256:E72ACDDF47586BC0999D598E3BD125A254BB6F4AE151C076993304F6E31FBBED | |||
| 1512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ob\bin\ProxySocket.dll | executable | |
MD5:13F842AC397885C4E647EC35F2AB79E5 | SHA256:851E924110BA3FF3DCD8C894D9C264A1AA3715AAED36E5EF4E320A73D3451A16 | |||
| 1512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ob\bin\Microsoft.Win32.Primitives.dll | executable | |
MD5:76B8D417C2F6416FA81EACC45977CEA2 | SHA256:5EAA2E82A26B0B302280D08F54DC9DA25165DD0E286BE52440A271285D63F695 | |||
| 1512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ob\bin\netstandard.dll | executable | |
MD5:0ADF6F32F4D14F9B0BE9AA94F7EFB279 | SHA256:8BE4A2270F8B2BEA40F33F79869FDCCA34E07BB764E63B81DED49D90D2B720DD | |||
| 1512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ob\bin\Microsoft.Scripting.Metadata.dll | executable | |
MD5:1BED5E618B922411CFAE2EAC84AFEF43 | SHA256:A4ACE184DDB98E81CFCC6C838299915D8C33B714594E3836DE7C75B1F70E55EB | |||
| 1512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ob\bin\Microsoft.Scripting.dll | executable | |
MD5:0B75B3835BF11D3163EB0798F7C1A89D | SHA256:D8B3CAB5C0F0E9C308C962FA894BC300C75F93537DAEF0E790069CA8CB1C7170 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report