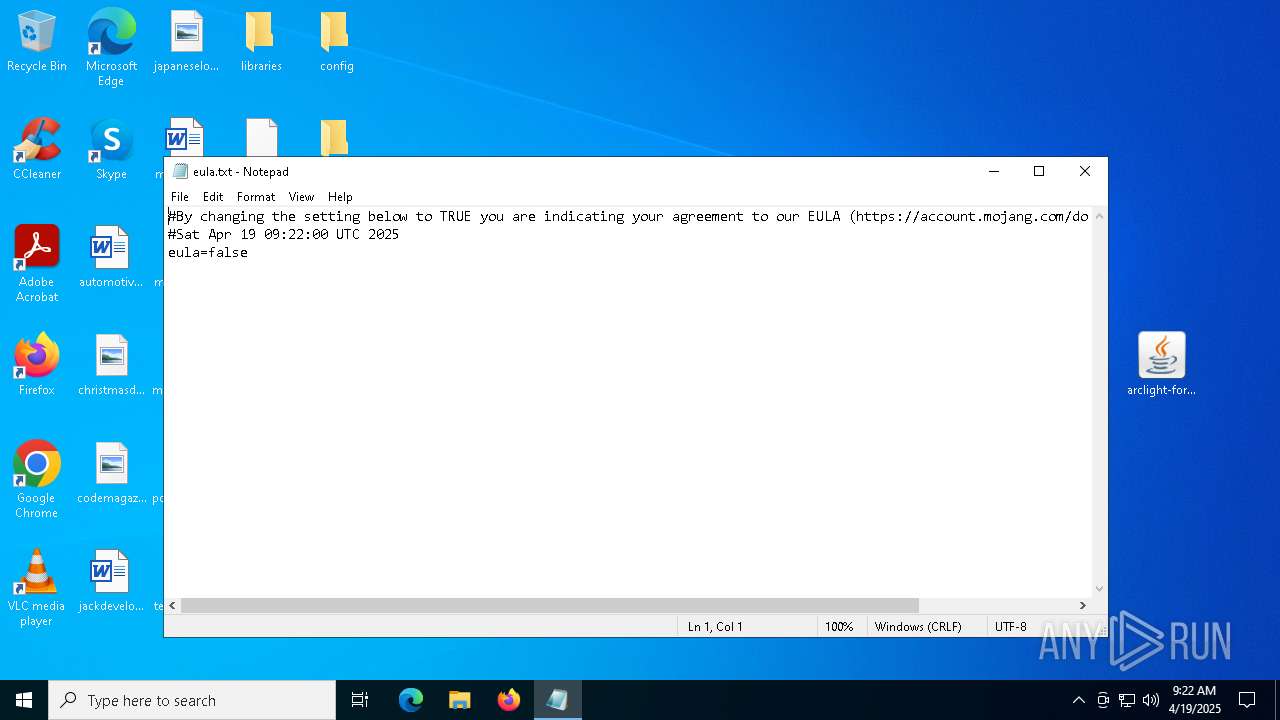
| File name: | arclight-forge-1.16.5-1.0.25-7cf92be3.jar |
| Full analysis: | https://app.any.run/tasks/e1db8ee2-50bf-415c-b197-4a1ae98f6ea2 |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2025, 09:19:13 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/java-archive |
| File info: | Java archive data (JAR) |
| MD5: | D669E51EF65BD717DB8CA5F40BAB8692 |
| SHA1: | EE50053B940DB272747F3EF7570B02274C4AE22A |
| SHA256: | 0711487FB8D624BD89BD74E8BAB271C8BEFB96485282DE5CCC6FD85CF9A40F98 |
| SSDEEP: | 98304:qmOgvIwdc3nFXAJEwNLDbiGr65u4lAFHcd0JwKl/UelHqhbPw7yH9YBZYP8x/gQ1:JmWX6pN4yw5xaw926r |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- javaw.exe (PID: 7020)
INFO
Application based on Java
- javaw.exe (PID: 7020)
- javaw.exe (PID: 5608)
- javaw.exe (PID: 6252)
- javaw.exe (PID: 3900)
Creates files in the program directory
- javaw.exe (PID: 7020)
Reads the computer name
- javaw.exe (PID: 7020)
- java.exe (PID: 6644)
- javaw.exe (PID: 6252)
- java.exe (PID: 3300)
- javaw.exe (PID: 3900)
Reads the machine GUID from the registry
- javaw.exe (PID: 7020)
- java.exe (PID: 6644)
- javaw.exe (PID: 6252)
- java.exe (PID: 3300)
- javaw.exe (PID: 3900)
Checks supported languages
- javaw.exe (PID: 7020)
- java.exe (PID: 6644)
- javaw.exe (PID: 5608)
- javaw.exe (PID: 6252)
- java.exe (PID: 3300)
- javaw.exe (PID: 3900)
Create files in a temporary directory
- javaw.exe (PID: 7020)
- java.exe (PID: 6644)
- javaw.exe (PID: 5608)
- java.exe (PID: 3300)
- javaw.exe (PID: 3900)
- javaw.exe (PID: 6252)
Creates files or folders in the user directory
- javaw.exe (PID: 7020)
Checks proxy server information
- java.exe (PID: 6644)
- java.exe (PID: 3300)
- slui.exe (PID: 6540)
The sample compiled with english language support
- javaw.exe (PID: 7020)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5728)
Reads the software policy settings
- slui.exe (PID: 2316)
- slui.exe (PID: 6540)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 5728)
- notepad.exe (PID: 1760)
Manual execution by a user
- javaw.exe (PID: 6252)
- javaw.exe (PID: 3900)
- notepad.exe (PID: 1760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jar | | | Java Archive (56.8) |
|---|---|---|
| .zip | | | ZIP compressed archive (15.6) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:10:22 03:52:40 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | META-INF/ |
Total processes
144
Monitored processes
17
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1760 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\eula.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2316 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2908 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
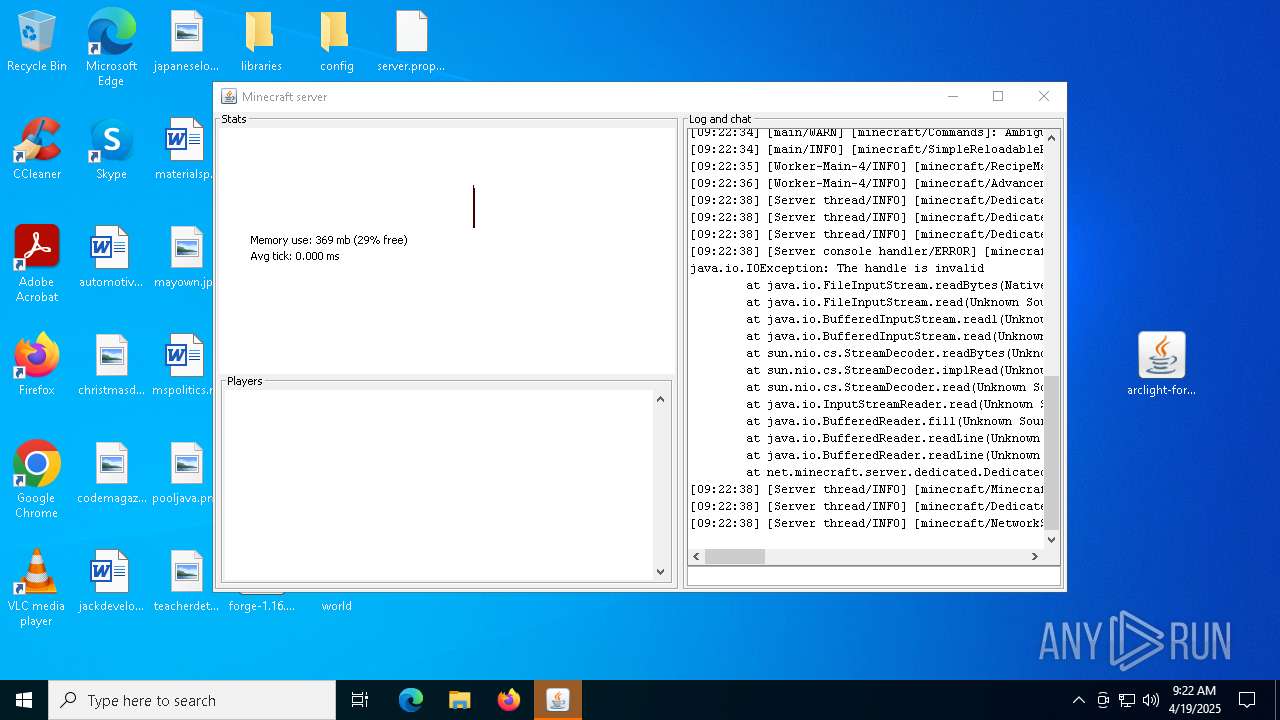
| 3300 | "C:\Program Files\Java\jre1.8.0_271\bin\java" -Djava.net.useSystemProxies=true -jar forge-1.16.5-36.2.39-installer.jar --installServer . | C:\Program Files\Java\jre1.8.0_271\bin\java.exe | javaw.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3900 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\Desktop\arclight-forge-1.16.5-1.0.25-7cf92be3.jar" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Version: 8.0.2710.9 Modules
| |||||||||||||||
| 4056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5608 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
25 046
Read events
25 043
Write events
3
Delete events
0
Modification events
| (PID) Process: | (5728) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.jar\OpenWithProgids |
| Operation: | write | Name: | jarfile |
Value: | |||
Executable files
117
Suspicious files
97
Text files
33
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7020 | javaw.exe | C:\Users\admin\AppData\Local\Temp\libraries\org\apache\maven\maven-model-builder\3.8.1\maven-model-builder-3.8.1.jar | compressed | |
MD5:17F9C840F8AD3E0118142675FA2DF09C | SHA256:B6FF49962516E960E4998C19FF75DC76744595DD72BC91266704D7FB6AB08E99 | |||
| 7020 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:874E574CFB23319051850895685C9470 | SHA256:C1CA5A59CD4ADAFEDBE24EBEA28372B0304AABF38D87AC248A00B8B8FBEC107B | |||
| 7020 | javaw.exe | C:\Users\admin\AppData\Local\Temp\libraries\org\fusesource\jansi\jansi\1.18\jansi-1.18.jar | java | |
MD5:6EE32DE8880DA9F02552474F60AB6FBD | SHA256:109E64FC65767C7A1A3BD654709D76F107B0A3B39DB32CBF11139E13A6F5229B | |||
| 7020 | javaw.exe | C:\Users\admin\AppData\Local\Temp\libraries\org\ow2\asm\asm-analysis\9.0\asm-analysis-9.0.jar | java | |
MD5:DAED5F6BC67AC8F01BEBECA0BB72A369 | SHA256:2D46DE6DF856A4DAAC9AA534459AB7287EB80584E9109850405E5B302DC9C2A6 | |||
| 7020 | javaw.exe | C:\Users\admin\AppData\Local\Temp\arclight.conf | text | |
MD5:1662BC117CF34024EEA46B1BD5D0100F | SHA256:16D28D2AEED8FA0BBCAD21F42DABE8AE4B2EF934CC301D7C33987BDD99DEBC35 | |||
| 7020 | javaw.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\83aa4cc77f591dfc2374580bbd95f6ba_bb926e54-e3ca-40fd-ae90-2764341e7792 | binary | |
MD5:C8366AE350E7019AEFC9D1E6E6A498C6 | SHA256:11E6ACA8E682C046C83B721EEB5C72C5EF03CB5936C60DF6F4993511DDC61238 | |||
| 7020 | javaw.exe | C:\Users\admin\AppData\Local\Temp\1101914240497arclight.conf.tmp | text | |
MD5:1662BC117CF34024EEA46B1BD5D0100F | SHA256:16D28D2AEED8FA0BBCAD21F42DABE8AE4B2EF934CC301D7C33987BDD99DEBC35 | |||
| 7020 | javaw.exe | C:\Users\admin\AppData\Local\Temp\libraries\commons-lang\commons-lang\2.6\commons-lang-2.6.jar | compressed | |
MD5:4D5C1693079575B362EDF41500630BBD | SHA256:50F11B09F877C294D56F24463F47D28F929CF5044F648661C0F0CFBAE9A2F49C | |||
| 7020 | javaw.exe | C:\Users\admin\AppData\Local\Temp\libraries\org\yaml\snakeyaml\1.27\snakeyaml-1.27.jar | java | |
MD5:466FF09DA784F9F21B2E6BF3B486A8CD | SHA256:7E7CCE6740ED705BFDFAAC7B442C1375D2986D2F2935936A5BD40C14E18FD736 | |||
| 7020 | javaw.exe | C:\Users\admin\AppData\Local\Temp\libraries\jline\jline\2.12.1\jline-2.12.1.jar | compressed | |
MD5:96E04A388FFFF0ADEE6C2CE64612A7A1 | SHA256:7A79C9CF47D47537CCF5239E374FA32A6D50B8AFD92C19D193B7BD94DA645D43 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
196
DNS requests
27
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6712 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6712 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7020 | javaw.exe | 119.28.56.73:443 | arclight.mcxk.net | Tencent Building, Kejizhongyi Avenue | HK | unknown |
6544 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arclight.mcxk.net |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arclight.hypertention.cn |
| unknown |
arclight.hypoglycemia.icu |
| unknown |
maven.minecraftforge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
7020 | javaw.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.icu) in TLS SNI |