| File name: | 123.txt |
| Full analysis: | https://app.any.run/tasks/188657d7-e39c-4be8-809d-46a996fc8f2b |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | December 13, 2024, 23:56:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
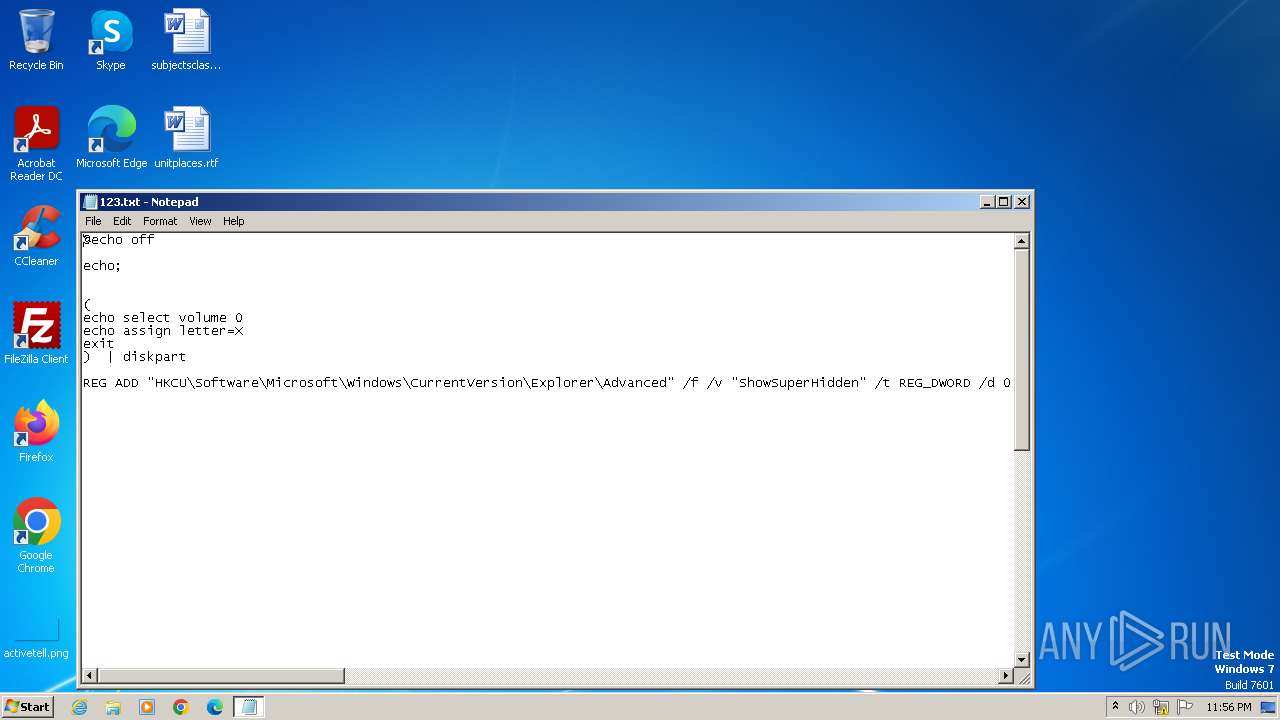
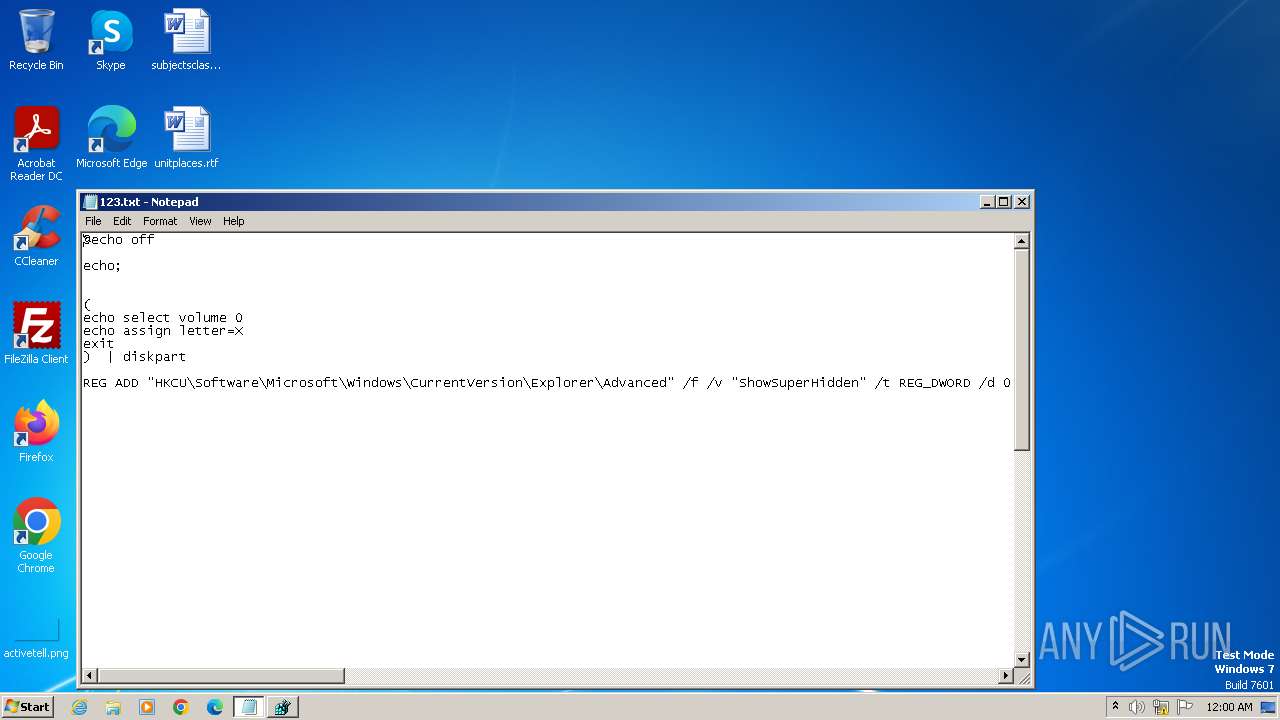
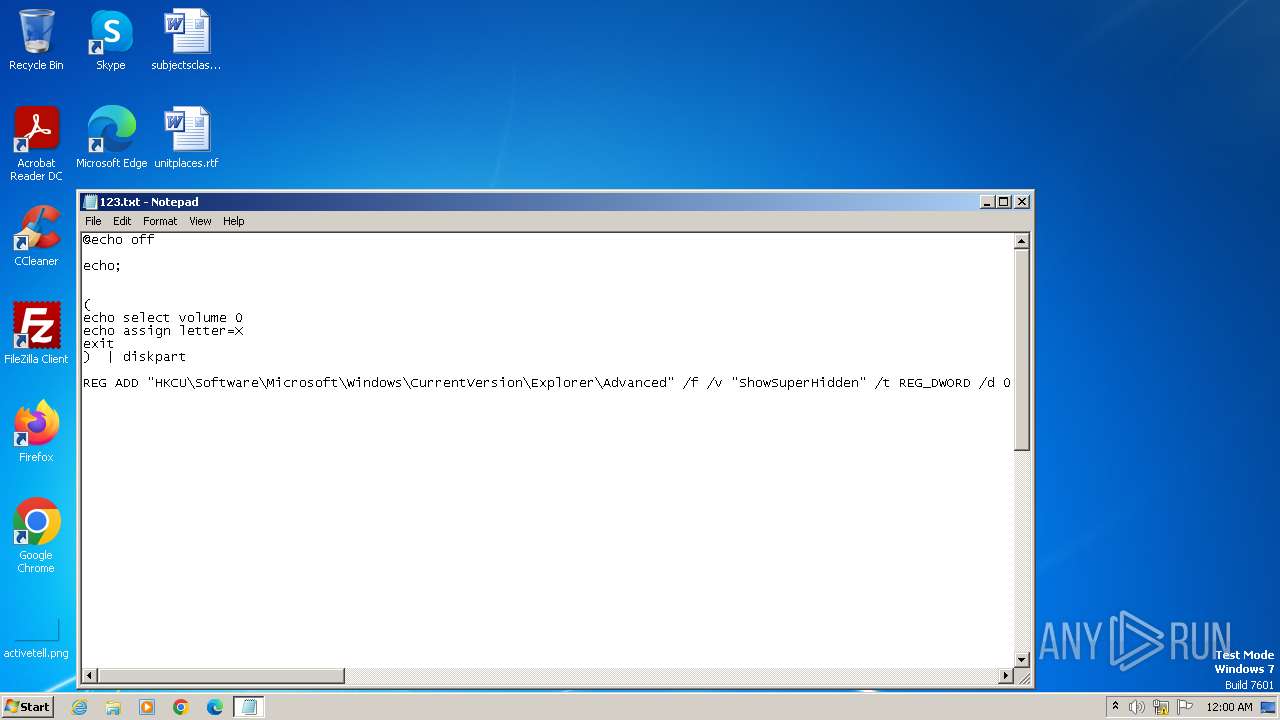
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (424), with CRLF line terminators |
| MD5: | 27D782EACCCB2A76774EB1109C03AF6F |
| SHA1: | C8BF807D0726710911D584225CD5354AE1292CC0 |
| SHA256: | 0700FB8950DE3D3C68D60733D69209AB9EA4EE7ACB1E7D87ED68C080B4416AA9 |
| SSDEEP: | 24:foV7Pl0o+Fn0bt8w4yECKzZ1qBdyV7Pl0o+u3NtvDfyEFd:foRlH+FTTZ1qBdyRlH+Ip |
MALICIOUS
Steals credentials from Web Browsers
- taskhost.exe (PID: 360)
SUSPICIOUS
The process executes via Task Scheduler
- ctfmon.exe (PID: 1048)
- sipnotify.exe (PID: 1300)
Reads the Internet Settings
- taskhost.exe (PID: 360)
- sipnotify.exe (PID: 1300)
Reads settings of System Certificates
- sipnotify.exe (PID: 1300)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 1920)
- IMEDICTUPDATE.EXE (PID: 1484)
- IMEKLMG.EXE (PID: 1688)
- IMEKLMG.EXE (PID: 1928)
- wmpnscfg.exe (PID: 240)
- wmpnscfg.exe (PID: 1940)
Manual execution by a user
- wmpnscfg.exe (PID: 1920)
- regedit.exe (PID: 2840)
- svchost.exe (PID: 1404)
- svchost.exe (PID: 1280)
- IMEDICTUPDATE.EXE (PID: 1484)
- svchost.exe (PID: 1956)
- svchost.exe (PID: 1924)
- IMEKLMG.EXE (PID: 1688)
- IMEKLMG.EXE (PID: 1928)
- taskhost.exe (PID: 360)
- wmpnscfg.exe (PID: 240)
- SearchIndexer.exe (PID: 1024)
- wmpnscfg.exe (PID: 1940)
- EOSNotify.exe (PID: 2160)
- svchost.exe (PID: 1440)
Checks supported languages
- wmpnscfg.exe (PID: 1920)
- wmpnscfg.exe (PID: 240)
- IMEKLMG.EXE (PID: 1928)
- IMEKLMG.EXE (PID: 1688)
- wmpnscfg.exe (PID: 1940)
- IMEDICTUPDATE.EXE (PID: 1484)
Reads the software policy settings
- sipnotify.exe (PID: 1300)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 1688)
- IMEKLMG.EXE (PID: 1928)
- IMEDICTUPDATE.EXE (PID: 1484)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1300)
Creates files in the program directory
- SearchIndexer.exe (PID: 1024)
Reads the time zone
- svchost.exe (PID: 1280)
- svchost.exe (PID: 1404)
Sends debugging messages
- svchost.exe (PID: 1404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
90
Monitored processes
21
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 360 | "taskhost.exe" | C:\Windows\System32\taskhost.exe | services.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Tasks Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1024 | C:\Windows\system32\SearchIndexer.exe /Embedding | C:\Windows\System32\SearchIndexer.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Indexer Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1048 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1252 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\123.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1252 | C:\Windows\System32\spoolsv.exe | C:\Windows\System32\spoolsv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Spooler SubSystem App Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1280 | C:\Windows\system32\svchost.exe -k LocalServiceNoNetwork | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1300 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1404 | C:\Windows\System32\svchost.exe -k utcsvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1440 | C:\Windows\system32\svchost.exe -k LocalServiceAndNoImpersonation | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 703
Read events
9 469
Write events
146
Delete events
88
Modification events
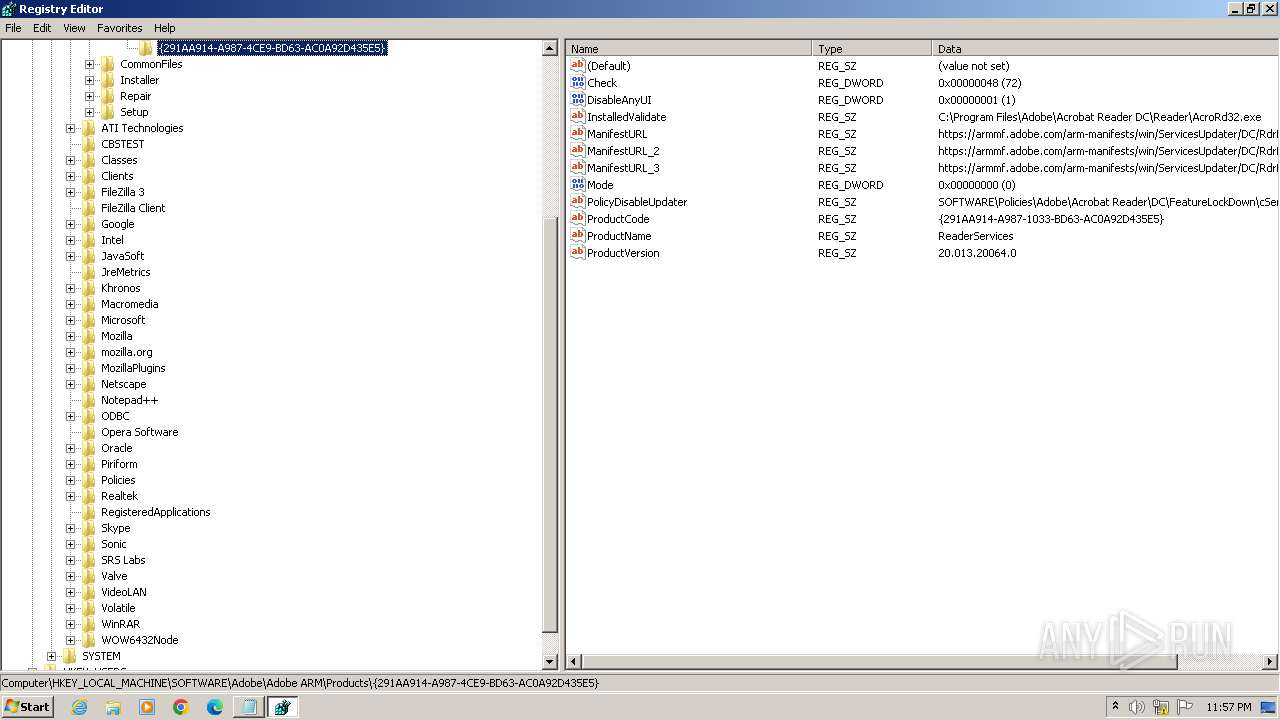
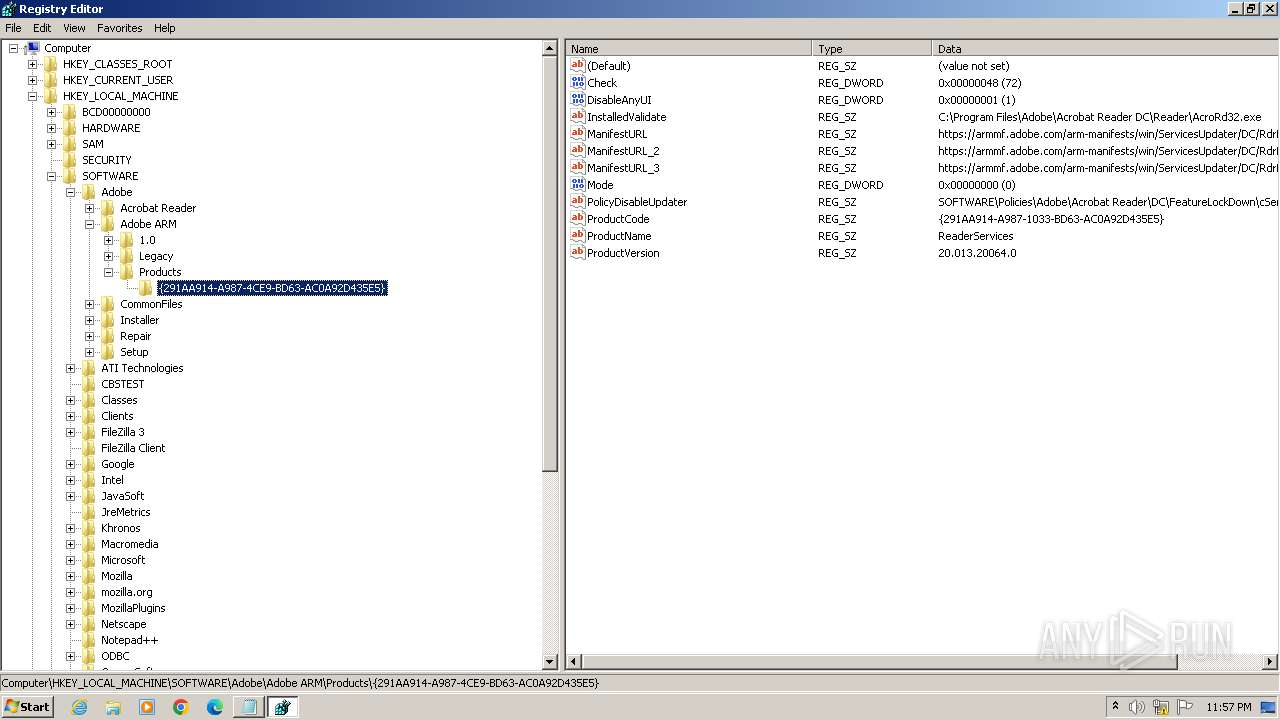
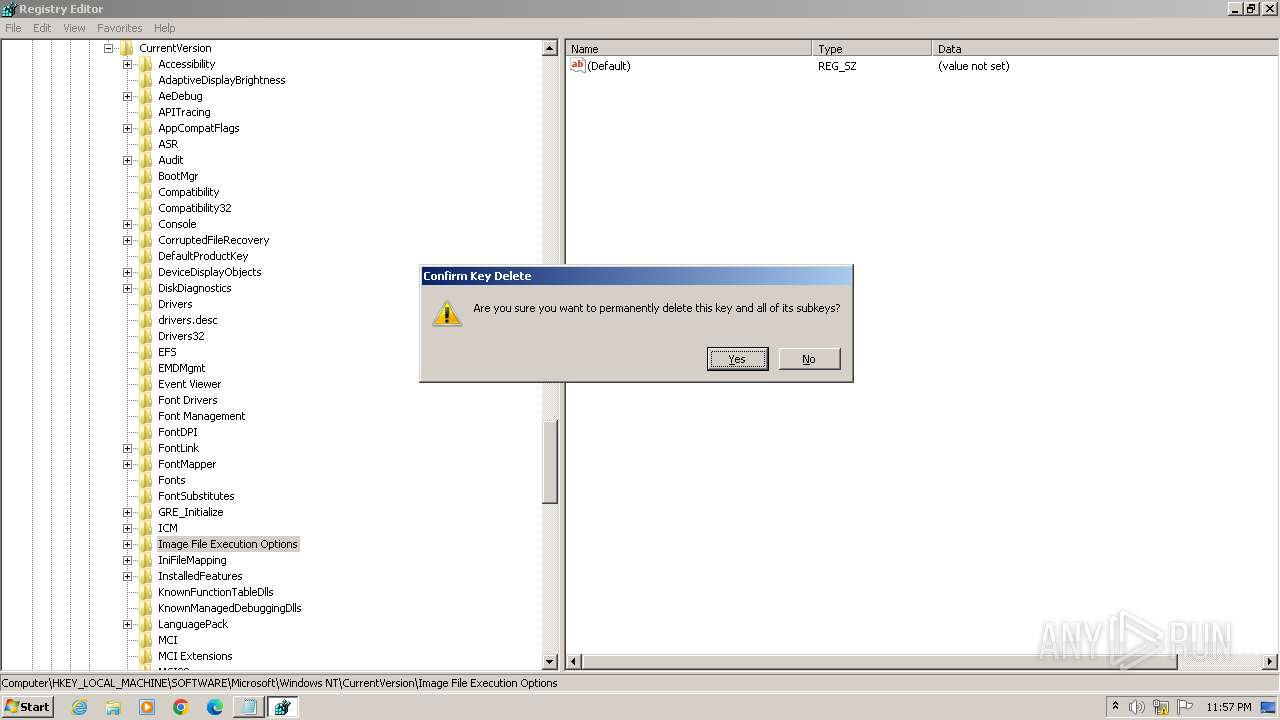
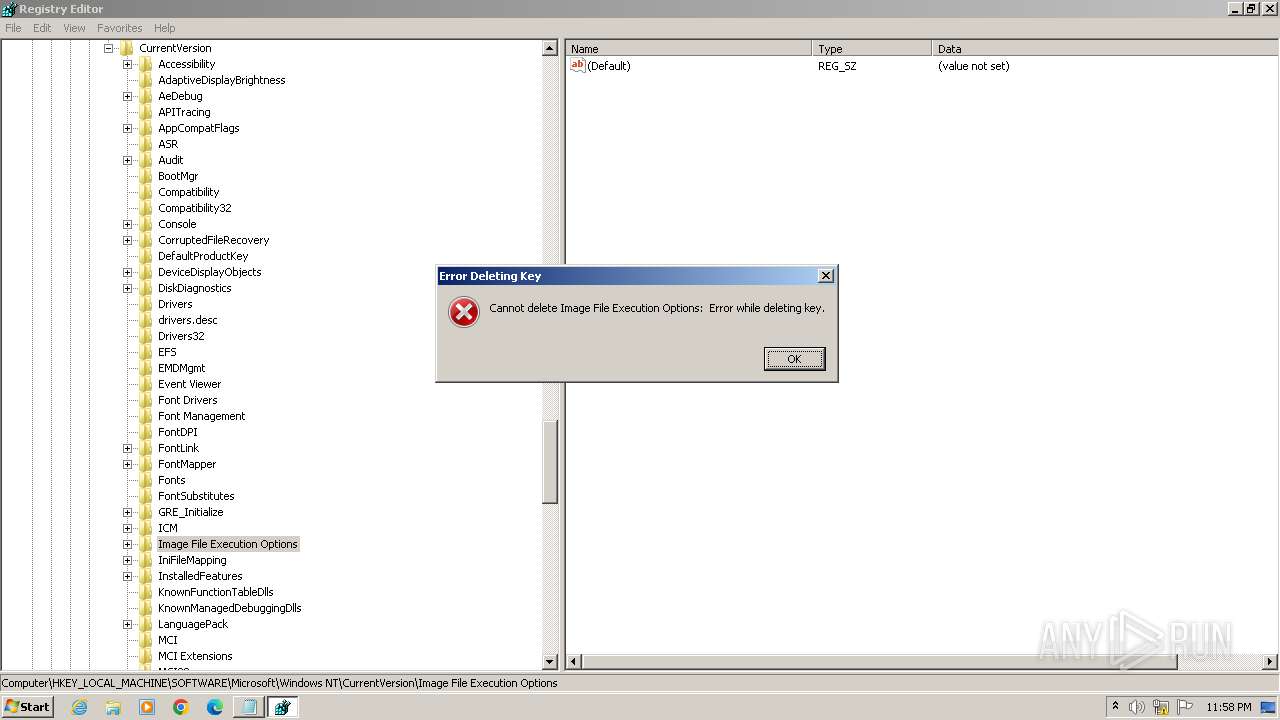
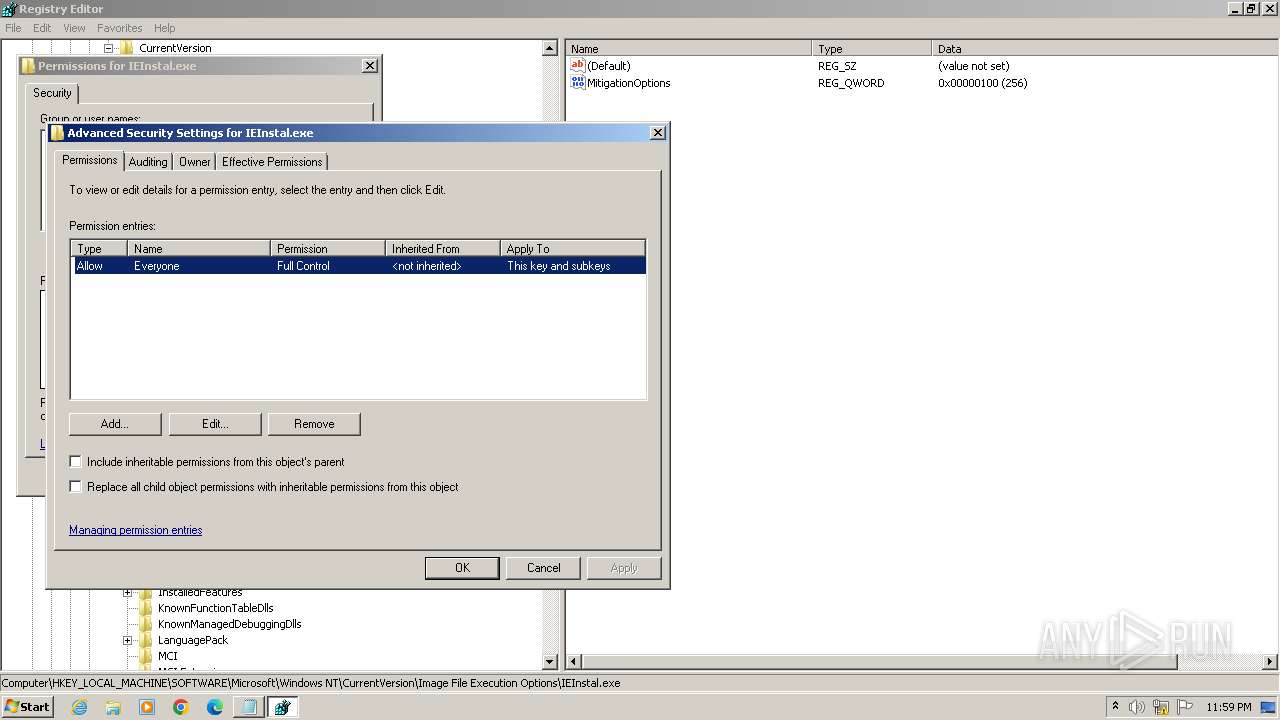
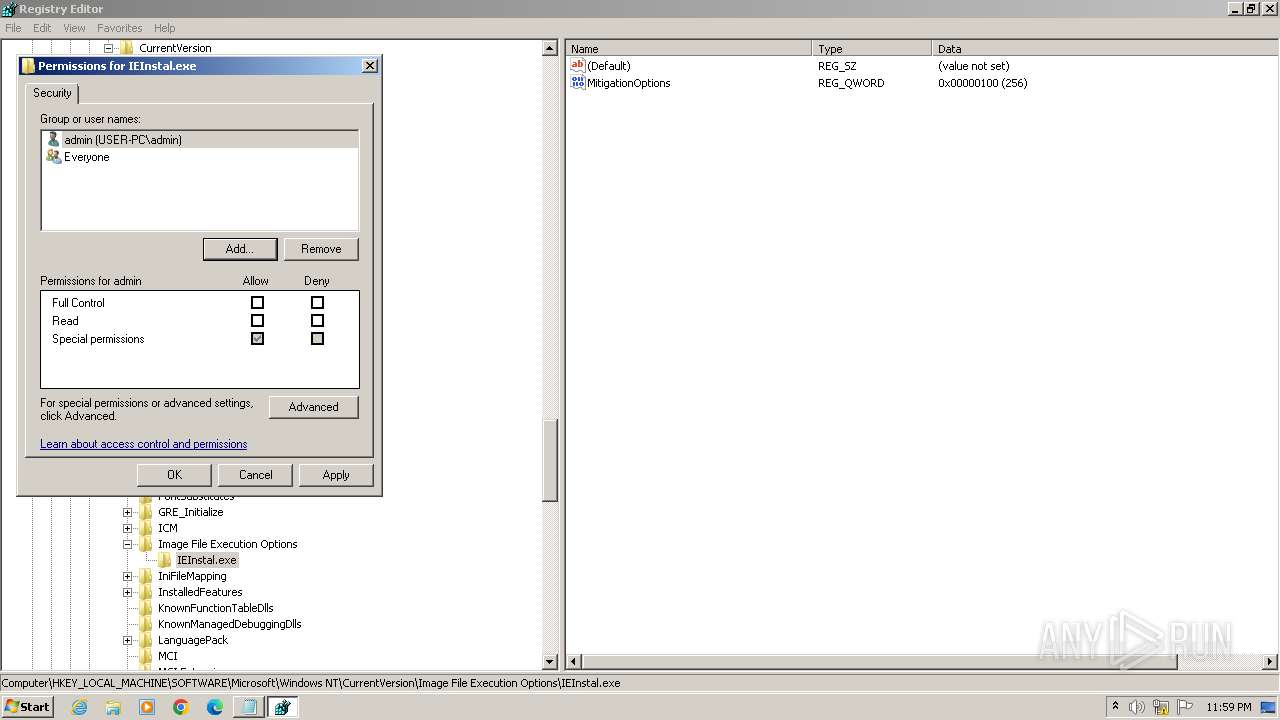
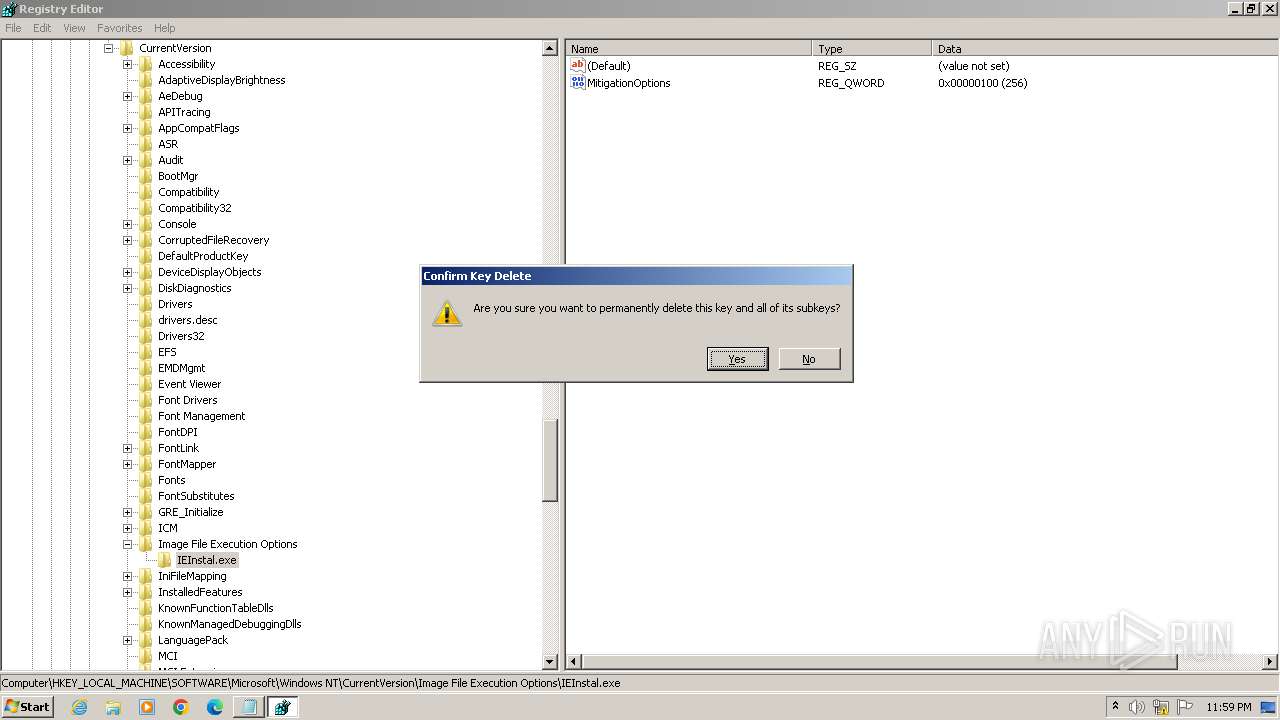
| (PID) Process: | (2840) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\accicons.exe |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2840) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AcroRd32.exe |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2840) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AcroRd32Info.exe |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2840) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\clview.exe |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2840) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cnfnot32.exe |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2840) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\DllNXOptions |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2840) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dw20.exe |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2840) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dwtrig20.exe |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2840) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\excel.exe |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2840) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\excelcnv.exe |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
9
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1404 | svchost.exe | C:\ProgramData\Microsoft\Diagnosis\events00.rbs | — | |
MD5:— | SHA256:— | |||
| 1404 | svchost.exe | C:\ProgramData\Microsoft\Diagnosis\events01.rbs | — | |
MD5:— | SHA256:— | |||
| 1024 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\Windows.edb | — | |
MD5:— | SHA256:— | |||
| 1300 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\script.js | text | |
MD5:A2682382967C351F7ED21762F9E5DE9E | SHA256:36B1D26F1EC69685648C0528C2FCE95A3C2DBECF828CDFA4A8B4239A15B644A2 | |||
| 1404 | svchost.exe | C:\ProgramData\Microsoft\Diagnosis\events11.rbs | binary | |
MD5:317262CEEFBA0C8677B3B35425089E22 | SHA256:2A87919E571701C038F1E3C3311E343BC96D9A805CD3452B5EA6587A9EB35B43 | |||
| 1300 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\main.jpg | image | |
MD5:B342ACE63F77961249A084C61EABC884 | SHA256:E5067BBA2095B5DA7C3171EC116E9A92337E24E471339B0860A160076EFE49B9 | |||
| 1924 | svchost.exe | C:\ProgramData\Microsoft\Windows Defender\Support\MPLog-03192019-130535.log | text | |
MD5:530928790351D761D9CA043F5CEC765C | SHA256:F54D7D265C2AA720DBCB1A75A548C6D09DB65413D27F4683B0C13FFB5B968541 | |||
| 1300 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\metadata.json | binary | |
MD5:E8A970BA6CE386EED9A5E724F26212A6 | SHA256:7E06107D585D8FC7870998F3856DCC3E35800AA97E4406AAB83BC8444B6CBDE3 | |||
| 1300 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\microsoft-logo.png | image | |
MD5:B7C73A0CFBA68CC70C35EF9C63703CE4 | SHA256:1D8B27A0266FF526CF95447F3701592A908848467D37C09A00A2516C1F29A013 | |||
| 1300 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\en-us.html | html | |
MD5:9752942B57692148B9F614CF4C119A36 | SHA256:E31B834DD53FA6815F396FC09C726636ABF98F3367F0CF1590EF5EB3801C75D1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
11
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1300 | sipnotify.exe | HEAD | 200 | 23.212.215.38:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133786080718750000 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1300 | sipnotify.exe | 23.212.215.38:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | AU | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
query.prod.cms.rt.microsoft.com |
| whitelisted |