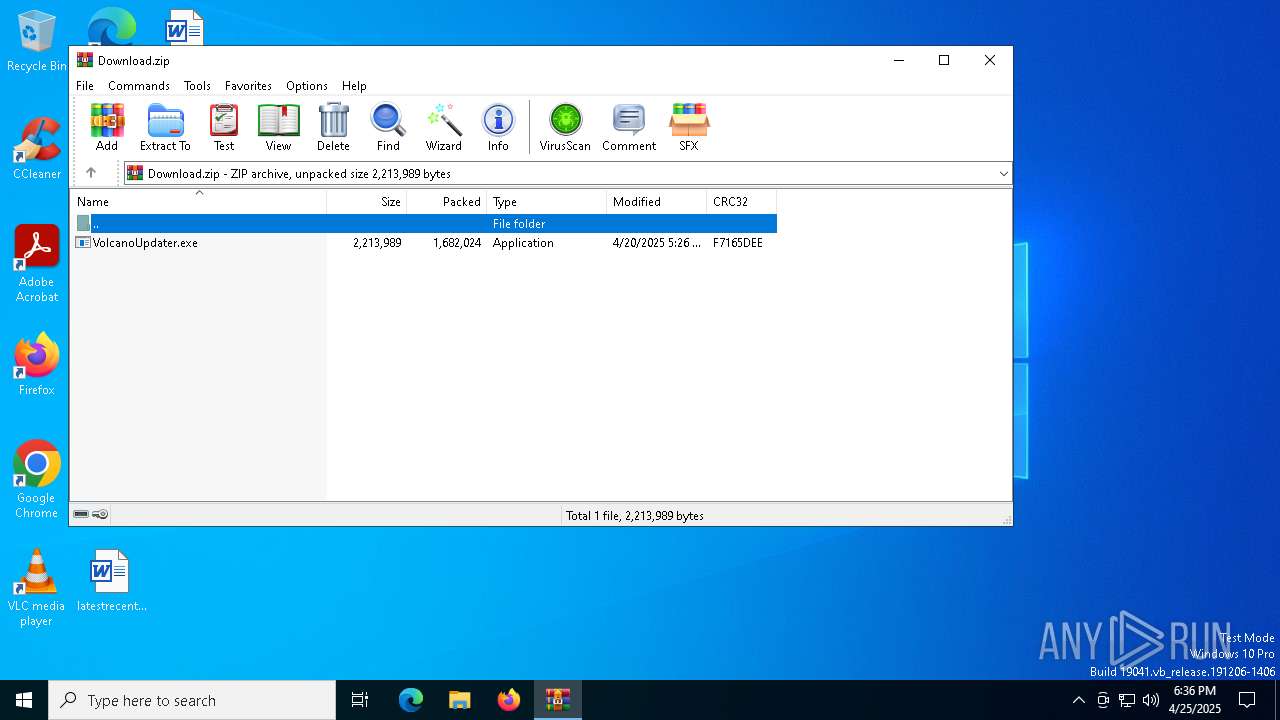
| File name: | Download.zip |
| Full analysis: | https://app.any.run/tasks/3929b3b5-2eaf-4b5d-bc03-b8424f5d8223 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2025, 18:36:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C0BBD72FC000248E9C9E8101B082CE38 |
| SHA1: | 08DC1B634E927CC6038537696D4B0A0590E749D5 |
| SHA256: | 06E877D6B8160900BC2E3BC550AE278BC1CD33BA0263B8B60DB6FAE22A729DF2 |
| SSDEEP: | 49152:ZzRrhdy7aXsaqMtTVOW/QYpNqyAzOAojTgzkf/g/BdUMV2jbgVv1TgTzQXu0Ofhu:ZzRNE4saZ5wW/6XzjojTGkf/g/Bdjwg/ |
MALICIOUS
Generic archive extractor
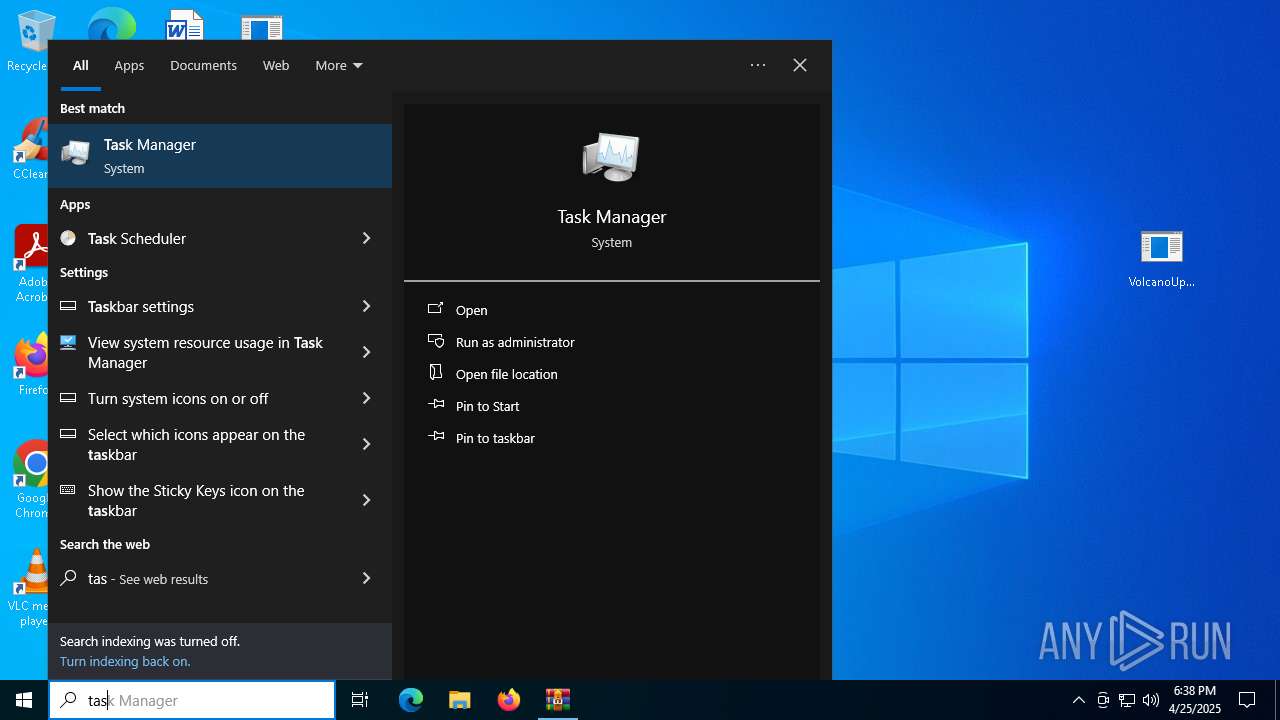
- WinRAR.exe (PID: 1672)
SUSPICIOUS
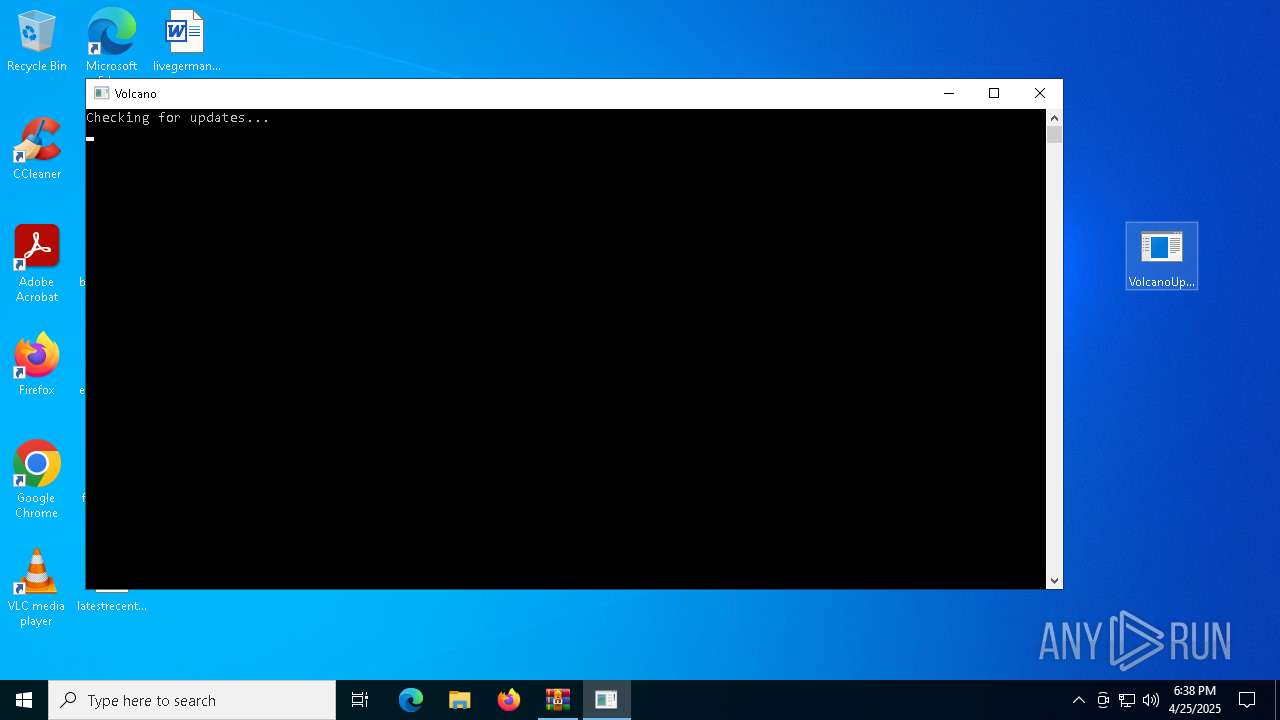
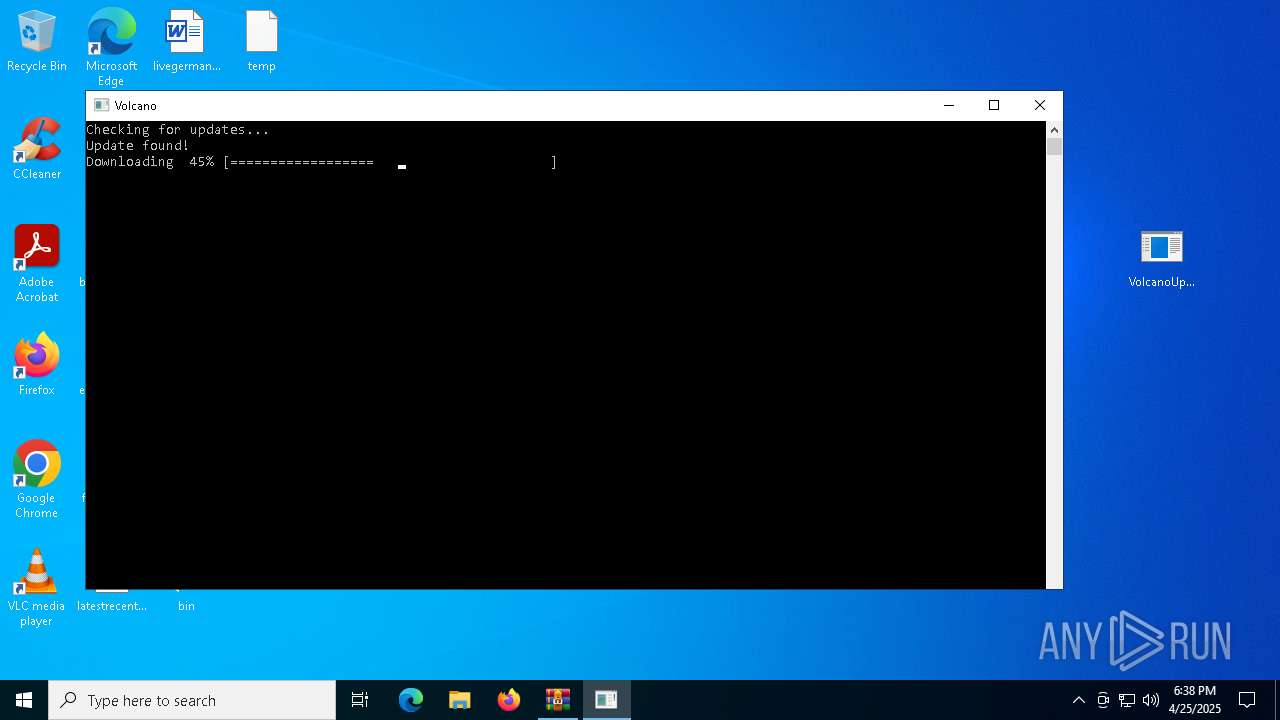
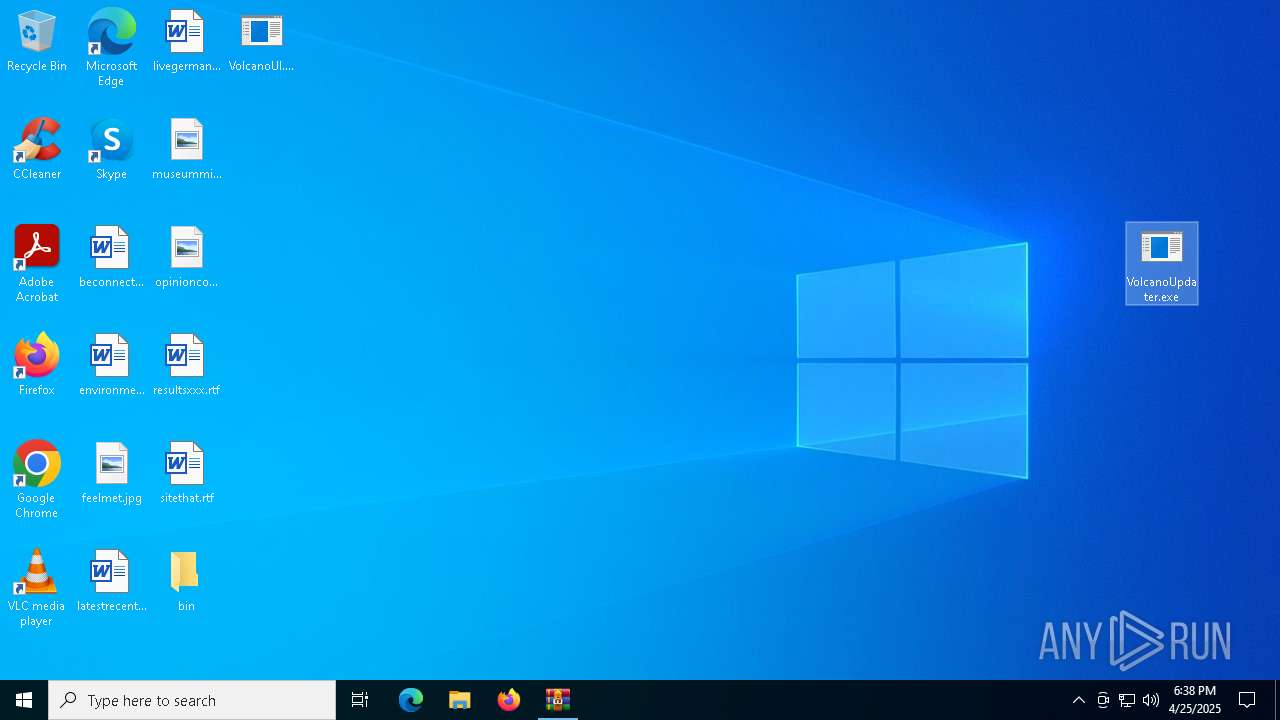
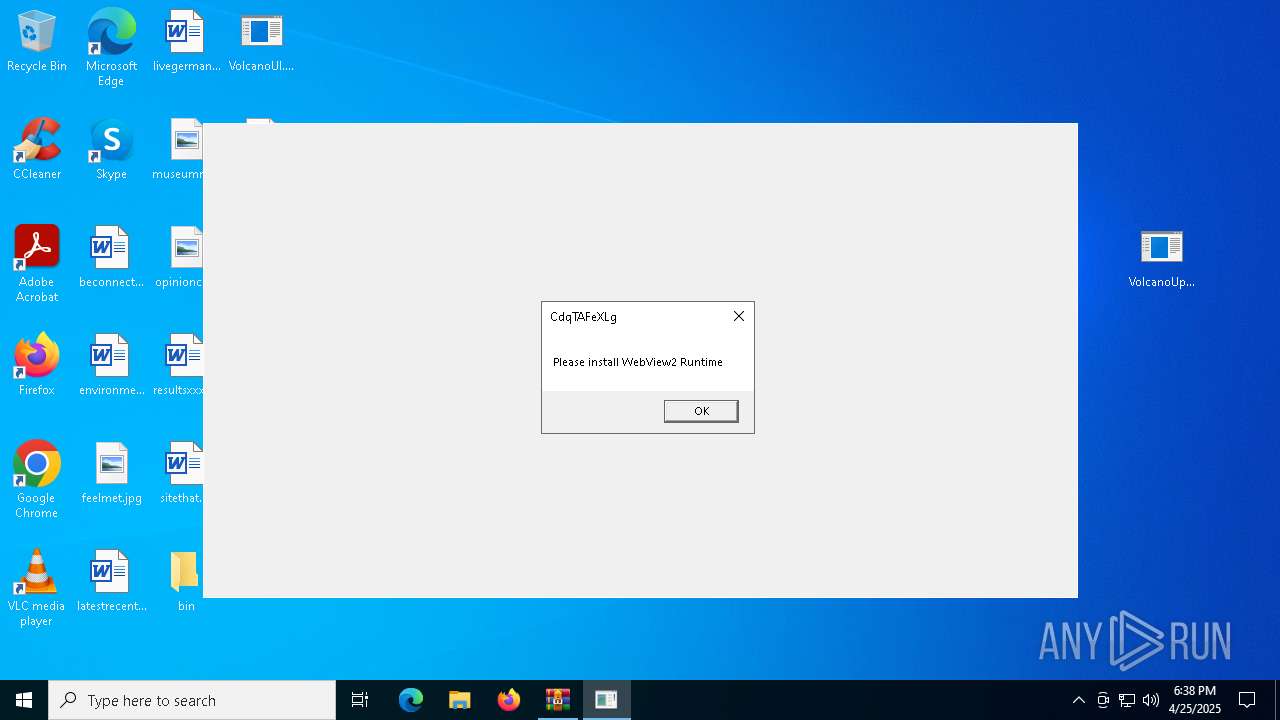
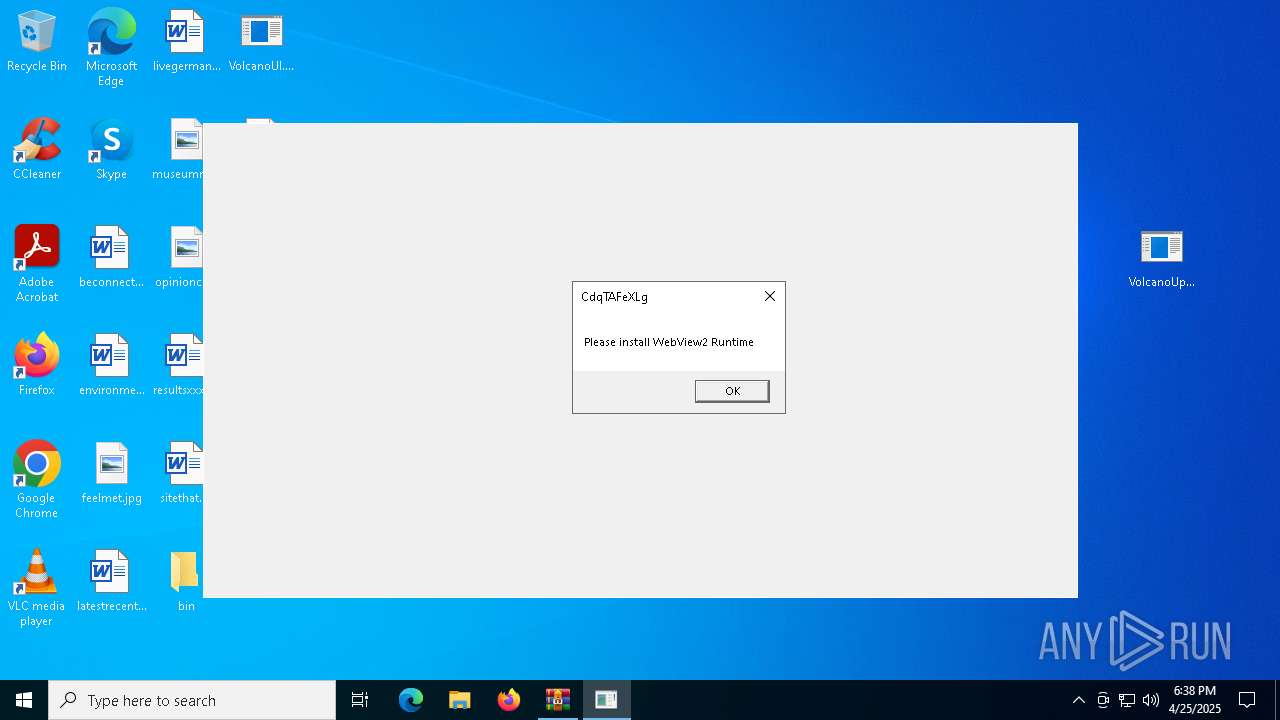
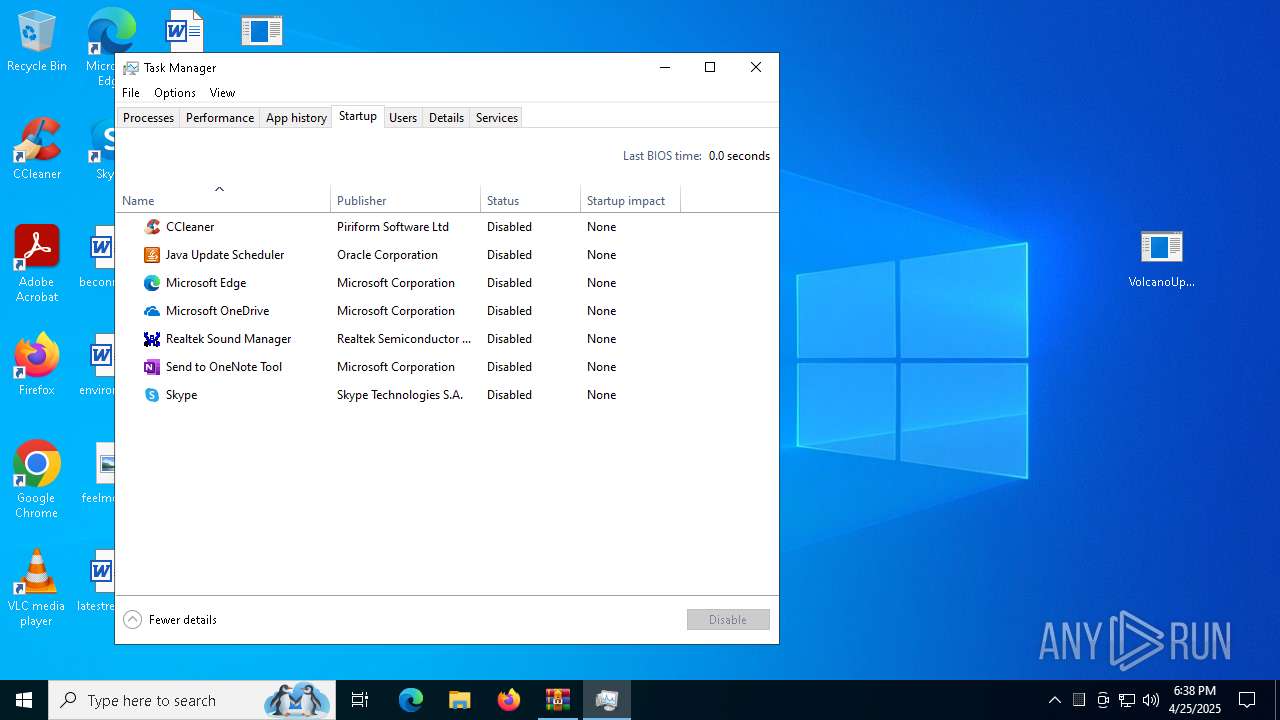
Executable content was dropped or overwritten
- VolcanoUpdater.exe (PID: 6972)
- VolcanoUI.exe (PID: 2240)
Reads the date of Windows installation
- VolcanoUpdater.exe (PID: 6972)
Reads security settings of Internet Explorer
- VolcanoUpdater.exe (PID: 6972)
Reads the BIOS version
- VolcanoUI.exe (PID: 2240)
Process drops legitimate windows executable
- VolcanoUI.exe (PID: 2240)
INFO
Reads the software policy settings
- slui.exe (PID: 4980)
- slui.exe (PID: 6620)
- SearchApp.exe (PID: 2924)
Reads the computer name
- VolcanoUpdater.exe (PID: 6972)
- VolcanoUI.exe (PID: 2240)
Checks supported languages
- VolcanoUI.exe (PID: 2240)
- SearchApp.exe (PID: 2924)
- VolcanoUpdater.exe (PID: 6972)
The sample compiled with english language support
- VolcanoUI.exe (PID: 2240)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1672)
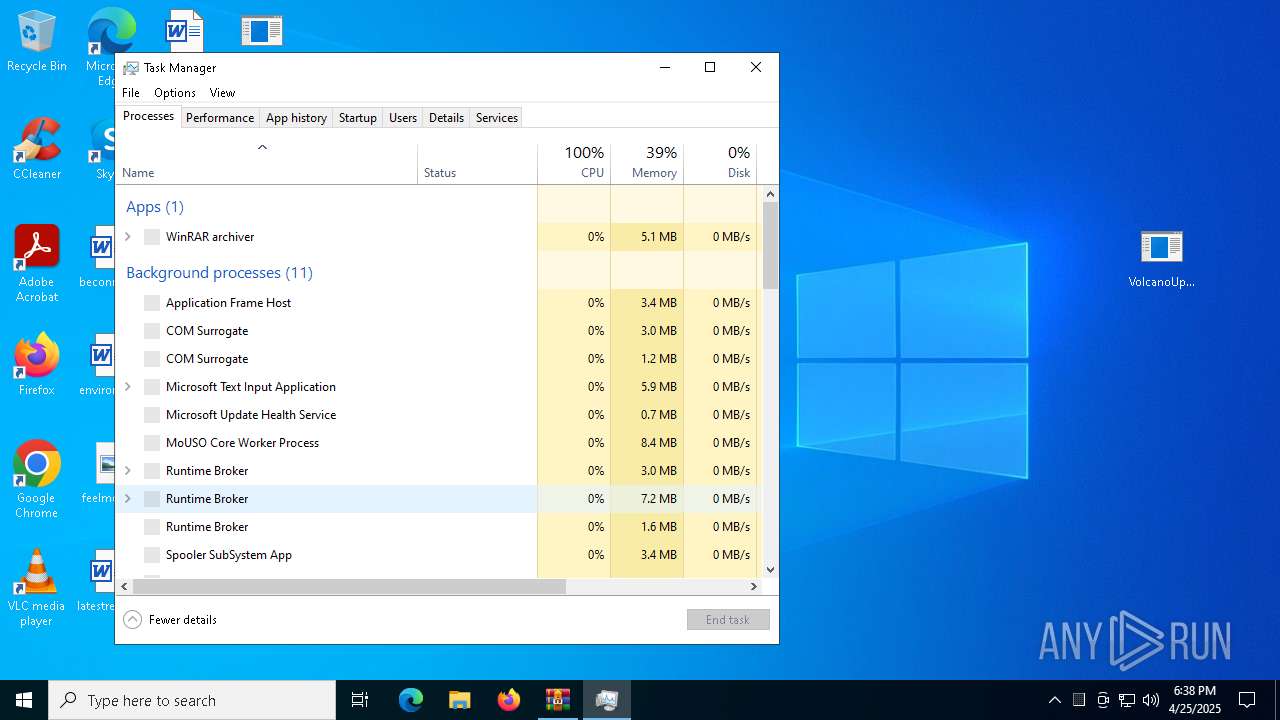
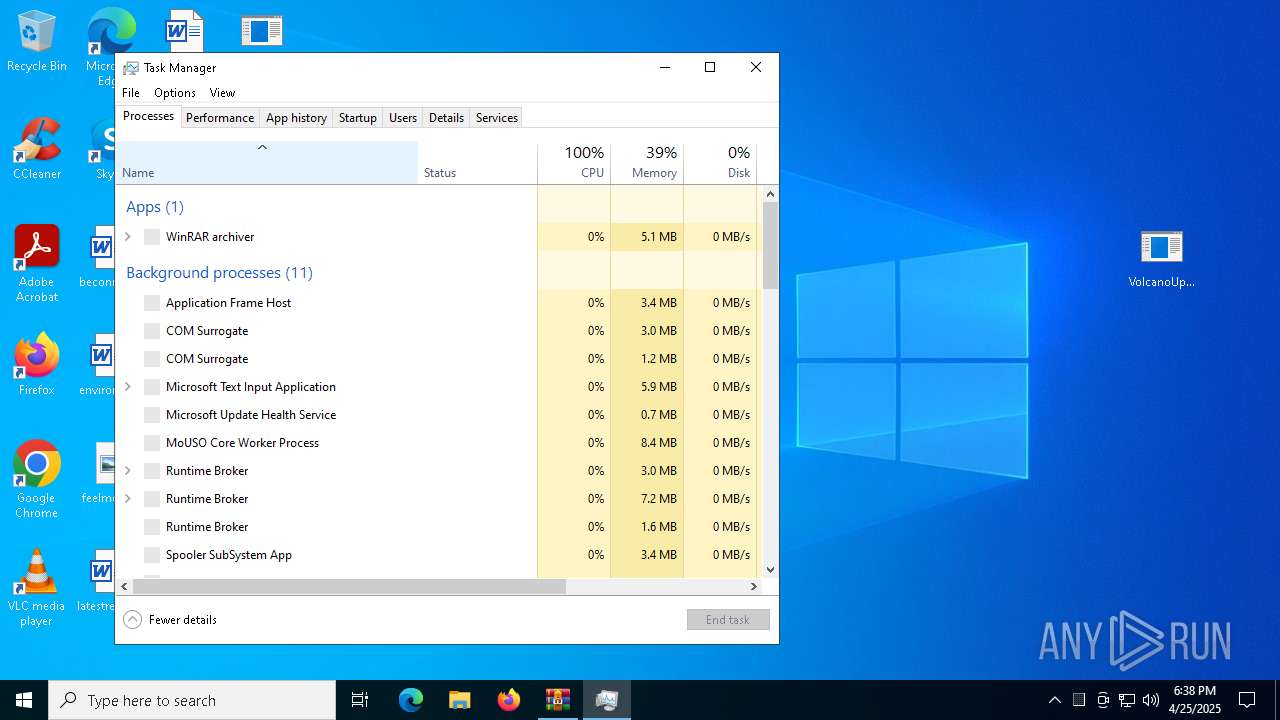
Manual execution by a user
- VolcanoUpdater.exe (PID: 6972)
- Taskmgr.exe (PID: 5164)
- Taskmgr.exe (PID: 2600)
- mmc.exe (PID: 6808)
- mmc.exe (PID: 2800)
- msedge.exe (PID: 3028)
Process checks computer location settings
- VolcanoUpdater.exe (PID: 6972)
- SearchApp.exe (PID: 2924)
Checks proxy server information
- slui.exe (PID: 6620)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 2924)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 2600)
- mmc.exe (PID: 2800)
Application launched itself
- msedge.exe (PID: 3028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:20 12:26:48 |
| ZipCRC: | 0xf7165dee |
| ZipCompressedSize: | 1682024 |
| ZipUncompressedSize: | 2213989 |
| ZipFileName: | VolcanoUpdater.exe |
Total processes
176
Monitored processes
38
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5680 --field-trial-handle=2364,i,2190450321914656984,17424236773232572209,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1328 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=1492 --field-trial-handle=2364,i,2190450321914656984,17424236773232572209,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1584 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6884 --field-trial-handle=2364,i,2190450321914656984,17424236773232572209,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1672 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Download.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1700 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6832 --field-trial-handle=2364,i,2190450321914656984,17424236773232572209,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2136 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | "C:\Users\admin\Desktop\VolcanoUI.exe" | C:\Users\admin\Desktop\VolcanoUI.exe | VolcanoUpdater.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2476 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6944 --field-trial-handle=2364,i,2190450321914656984,17424236773232572209,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2504 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6124 --field-trial-handle=2364,i,2190450321914656984,17424236773232572209,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
17 862
Read events
17 686
Write events
169
Delete events
7
Modification events
| (PID) Process: | (1672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Download.zip | |||
| (PID) Process: | (1672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1672) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | delete value | Name: | JumpListChangedAppIds |
Value: | |||
Executable files
38
Suspicious files
646
Text files
302
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1672.1359\VolcanoUpdater.exe | executable | |
MD5:5E911CA90CD25FB9EAA9AF23DC4B1C9D | SHA256:96AACE7FCC7C313DE9538B47A2DF9581D2AB8F58C91AFA217DDFBD5BF93DE1BC | |||
| 6972 | VolcanoUpdater.exe | C:\Users\admin\Desktop\bin\luau-lifter.exe | executable | |
MD5:F1246A49C8183FCFAC4D7669A6C50881 | SHA256:F5AD37B2293814CE33149CA8D8BF1D673AE0C8F3CB025D7B83954EB0E68E631D | |||
| 6972 | VolcanoUpdater.exe | C:\Users\admin\Desktop\bin\version.txt | text | |
MD5:FB2681E1BFC97DEE1316A0430A5990EE | SHA256:0CE7725FC888E3CD040F747F3A5C0441CB6EECB80C0D006EE6542CDB3ACEEF5D | |||
| 6972 | VolcanoUpdater.exe | C:\Users\admin\Desktop\bin\page\assets\abap-BrgZPUOV.js | text | |
MD5:5E0865606680E6D5AB5FAAE672097932 | SHA256:A3E2A241DA83C7AA80836ACE9FB3B2A242F458FF917DF9F19363F2E6430DD059 | |||
| 6972 | VolcanoUpdater.exe | C:\Users\admin\Desktop\bin\page\assets\bat-CFOPXBzS.js | text | |
MD5:4133D4FC714DDF40B53FB1F2F3B15579 | SHA256:471438AB5BC0B324A6B828AC8FA79CD86214FC4C84F4C2E9AAF55CAF56043D92 | |||
| 6972 | VolcanoUpdater.exe | C:\Users\admin\Desktop\bin\page\assets\bicep-BfEKNvv3.js | text | |
MD5:D57E65CA5EB6CAF649C5393DC167CB6D | SHA256:9DE9B6AD69CBF4B0D3DA56D87E5F33BF0DD5ECBB1DA2B3DEC999F6AEDA197246 | |||
| 6972 | VolcanoUpdater.exe | C:\Users\admin\Desktop\bin\page\assets\clojure-DTECt2xU.js | text | |
MD5:CBE50C2D87AFFE61EE11FAADF2F57252 | SHA256:C897D061A0F39FABC5B9204E0EA8F78FA12C37C4BE45A2749BD1119D2CBCBF68 | |||
| 6972 | VolcanoUpdater.exe | C:\Users\admin\Desktop\bin\page\assets\cssMode-wuhyQlOf.js | binary | |
MD5:B63088DC9449EDE74B283708F401FC0F | SHA256:019BE82D233F42BEE2CFA76DD31E3AA42D73C2F6276C7A576677BC7B005D7A38 | |||
| 6972 | VolcanoUpdater.exe | C:\Users\admin\Desktop\bin\page\assets\cameligo-BFG1Mk7z.js | text | |
MD5:E9D40B956B6BEC8A5BFFD0D94552B2F8 | SHA256:CC50FE6B6738380FDC2D31D1A2FE210EA67CB19A5F6ABBF91E0AD3A08491A1E5 | |||
| 6972 | VolcanoUpdater.exe | C:\Users\admin\Desktop\bin\page\assets\cypher-DrQuvNYM.js | text | |
MD5:EE63F453BC7BA3157DB257900B3C4815 | SHA256:8620DDBCFBCA9DBD8A3D28DF6C60848432DBCEEFBE1EF7C798860F92644FDEC4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
94
DNS requests
92
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.188:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2340 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2340 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.217.18.99:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.217.18.99:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.188:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2340 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |