| File name: | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe |
| Full analysis: | https://app.any.run/tasks/b3ca6f49-e269-4785-9bf5-baf3145395ca |
| Verdict: | Malicious activity |
| Analysis date: | January 26, 2022, 11:59:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | B8924ABBCE3B8AA7D97D75E7667B0915 |
| SHA1: | C393E9BC1C679FBBE471AE148D967E3F22489BF5 |
| SHA256: | 06E6BF15FA7DD2AD205B79B23809C81C5934382C6F05A395FA4519A8ECA40907 |
| SSDEEP: | 12288:ZAwPZW6UQStsYS1WbenKvZke6tzx86qo2En2C+KD:ZANfQcbeWb+KvZkeAzxBqG2AD |
MALICIOUS
Drops executable file immediately after starts
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 1408)
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 3304)
Loads dropped or rewritten executable
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 3304)
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 1408)
Changes settings of System certificates
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 3304)
Application was dropped or rewritten from another process
- sendstat.exe (PID: 2736)
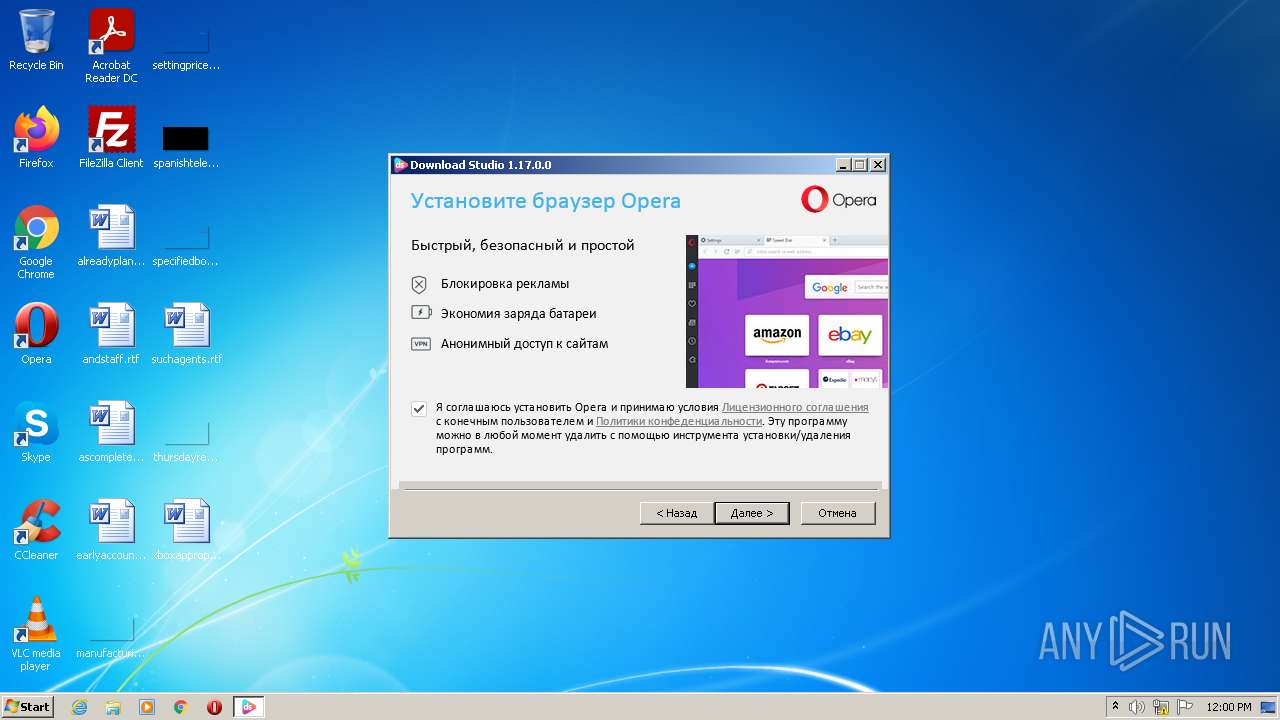
Actions looks like stealing of personal data
- dist_opera.exe (PID: 292)
- dist_opera.exe (PID: 3824)
- dist_opera.exe (PID: 3596)
SUSPICIOUS
Checks supported languages
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 1408)
- dist_opera.exe (PID: 3824)
- dist_opera.exe (PID: 292)
- dist_opera.exe (PID: 3596)
- sendstat.exe (PID: 2736)
- dist_opera.exe (PID: 3544)
- dist_opera.exe (PID: 2728)
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 3304)
Drops a file with too old compile date
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 1408)
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 3304)
Reads the date of Windows installation
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 3304)
Executable content was dropped or overwritten
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 3304)
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 1408)
Adds / modifies Windows certificates
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 3304)
Reads internet explorer settings
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 3304)
Application launched itself
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 1408)
- dist_opera.exe (PID: 3596)
- dist_opera.exe (PID: 3824)
Reads the computer name
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 3304)
- dist_opera.exe (PID: 3824)
- dist_opera.exe (PID: 3596)
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 1408)
Reads Microsoft Outlook installation path
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 3304)
Creates files in the user directory
- dist_opera.exe (PID: 292)
Starts itself from another location
- dist_opera.exe (PID: 3824)
INFO
Reads settings of System Certificates
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 3304)
Checks Windows Trust Settings
- windows-loader-v2.2-password-111.zip[QkSeERyrd].exe (PID: 3304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
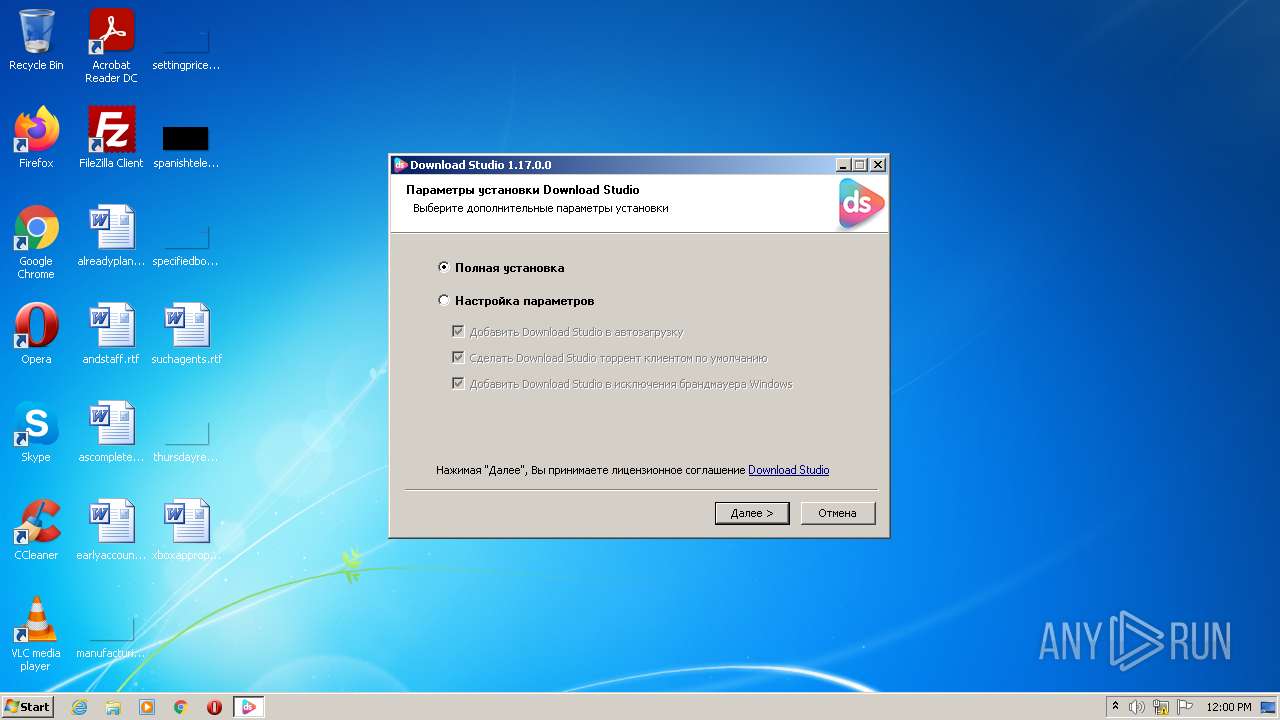
| ProductVersion: | 1.17.0.0 |
|---|---|
| ProductName: | Download Studio |
| LegalCopyright: | 2021 (c) Download Studio Project |
| FileVersion: | 1.17.0.0 |
| FileDescription: | Download Studio Setup |
| CompanyName: | Download Studio Project |
| CharacterSet: | Unicode |
| LanguageCode: | Unknown (04B0) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x0000 |
| ProductVersionNumber: | 1.17.0.0 |
| FileVersionNumber: | 1.17.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | 6 |
| OSVersion: | 4 |
| EntryPoint: | 0x35fd |
| UninitializedDataSize: | 2048 |
| InitializedDataSize: | 186880 |
| CodeSize: | 27136 |
| LinkerVersion: | 6 |
| PEType: | PE32 |
| TimeStamp: | 2021:07:25 00:22:34+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 24-Jul-2021 22:22:34 |
| Detected languages: |
|
| CompanyName: | Download Studio Project |
| FileDescription: | Download Studio Setup |
| FileVersion: | 1.17.0.0 |
| LegalCopyright: | 2021 (c) Download Studio Project |
| ProductName: | Download Studio |
| ProductVersion: | 1.17.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 24-Jul-2021 22:22:34 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000068E3 | 0x00006A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.4799 |
.rdata | 0x00008000 | 0x000014A4 | 0x00001600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.01239 |
.data | 0x0000A000 | 0x0002B058 | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.41827 |
.ndata | 0x00036000 | 0x0002F000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00065000 | 0x0001DCD8 | 0x0001DE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.0464 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.28775 | 1249 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 7.92982 | 18748 | UNKNOWN | English - United States | RT_ICON |
3 | 4.33435 | 16936 | UNKNOWN | English - United States | RT_ICON |
4 | 4.49243 | 9640 | UNKNOWN | English - United States | RT_ICON |
5 | 4.80295 | 4264 | UNKNOWN | English - United States | RT_ICON |
6 | 5.10184 | 1128 | UNKNOWN | English - United States | RT_ICON |
103 | 2.79908 | 90 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.68372 | 512 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.91148 | 248 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.89887 | 238 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
49
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\dist_opera.exe --type=crashpad-handler /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Roaming\Opera Software\Opera Stable\Crash Reports" "--crash-count-file=C:\Users\admin\AppData\Roaming\Opera Software\Opera Stable\crash_count.txt" --url=https://crashstats-collector.opera.com/collector/submit --annotation=channel=Stable --annotation=plat=Win32 --annotation=prod=OperaDesktop --annotation=ver=83.0.4254.19 --initial-client-data=0x174,0x178,0x17c,0x148,0x180,0x6d94a888,0x6d94a898,0x6d94a8a4 | C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\dist_opera.exe | dist_opera.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera Installer Exit code: 0 Version: 83.0.4254.19 Modules
| |||||||||||||||
| 1408 | "C:\Users\admin\AppData\Local\Temp\windows-loader-v2.2-password-111.zip[QkSeERyrd].exe" | C:\Users\admin\AppData\Local\Temp\windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | Explorer.EXE | ||||||||||||
User: admin Company: Download Studio Project Integrity Level: MEDIUM Description: Download Studio Setup Exit code: 0 Version: 1.17.0.0 Modules
| |||||||||||||||
| 2728 | "C:\Users\admin\AppData\Local\Temp\.opera\Opera Installer Temp\dist_opera.exe" --version | C:\Users\admin\AppData\Local\Temp\.opera\Opera Installer Temp\dist_opera.exe | — | dist_opera.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2736 | "C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\sendstat.exe" --silent --partner 9 | C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\sendstat.exe | — | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3304 | "C:\Users\admin\AppData\Local\Temp\windows-loader-v2.2-password-111.zip[QkSeERyrd].exe" /UAC:901A8 /NCRC | C:\Users\admin\AppData\Local\Temp\windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | ||||||||||||
User: admin Company: Download Studio Project Integrity Level: HIGH Description: Download Studio Setup Exit code: 0 Version: 1.17.0.0 Modules
| |||||||||||||||
| 3544 | C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\dist_opera.exe --type=crashpad-handler /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Roaming\Opera Software\Opera Stable\Crash Reports" "--crash-count-file=C:\Users\admin\AppData\Roaming\Opera Software\Opera Stable\crash_count.txt" --url=https://crashstats-collector.opera.com/collector/submit --annotation=channel=Stable --annotation=plat=Win32 --annotation=prod=OperaDesktop --annotation=ver=83.0.4254.19 --initial-client-data=0x180,0x184,0x188,0x148,0x18c,0x6d14a888,0x6d14a898,0x6d14a8a4 | C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\dist_opera.exe | dist_opera.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera Installer Exit code: 0 Version: 83.0.4254.19 Modules
| |||||||||||||||
| 3596 | "C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\dist_opera.exe" --backend --install --import-browser-data=0 --enable-stats=1 --enable-installer-stats=1 --launchopera=1 --installfolder="C:\Users\admin\AppData\Local\Programs\Opera" --profile-folder --language=en --singleprofile=0 --copyonly=0 --allusers=0 --setdefaultbrowser=1 --pintotaskbar=1 --pintostartmenu=1 --pin-additional-shortcuts=1 --server-tracking-data=server_tracking_data --initial-pid=3824 --package-dir-prefix="C:\Users\admin\AppData\Local\Temp\.opera\Opera Installer Temp\opera_package_20220126120042" --session-guid=60bb9b1b-7d13-4860-a073-43e8f3da3edf --server-tracking-blob=YzdkN2E2MDlmM2Y1ODk5NjBiZDBiZjdkYTVmZGExNGI4ZDdkNTRlNjYyMjgxMTIxMTljNTEyZjI2ZTRmNWI4ZTp7ImNvdW50cnkiOiJGSSIsImVkaXRpb24iOiJZeCswMyIsImluc3RhbGxlcl9uYW1lIjoiT3BlcmFTZXR1cC5leGUiLCJwcm9kdWN0Ijoib3BlcmEiLCJxdWVyeSI6Ii9vcGVyYS9zdGFibGUvd2luZG93cy8/dXRtX21lZGl1bT1hcGImZWRpdGlvbj1ZeCUyQjAzJnV0bV9zb3VyY2U9bWt0JnV0bV9jYW1wYWlnbj03MzUiLCJ0aW1lc3RhbXAiOiIxNjQzMTk4NDQwLjA3MTciLCJ1c2VyYWdlbnQiOiJEUy8xLjE3LjAuMCAoK2h0dHBzOi8vZG93bmxvYWQuc3R1ZGlvKSIsInV0bSI6eyJjYW1wYWlnbiI6IjczNSIsIm1lZGl1bSI6ImFwYiIsInNvdXJjZSI6Im1rdCJ9LCJ1dWlkIjoiNDAzYWM4MTEtMzczMS00NGI3LTg0NjAtNDkwODRiY2JlZDJjIn0= --silent --desktopshortcut=1 --wait-for-package --initial-proc-handle=F002000000000000 | C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\dist_opera.exe | dist_opera.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera Installer Exit code: 0 Version: 83.0.4254.19 Modules
| |||||||||||||||
| 3824 | "C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\dist_opera.exe" --silent --allusers=0 | C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\dist_opera.exe | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera Installer Exit code: 0 Version: 83.0.4254.19 Modules
| |||||||||||||||
| 3880 | "C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\dist_avast.exe" --silent=true /silent | C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\dist_avast.exe | — | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | |||||||||||
User: admin Company: AVAST Software Integrity Level: HIGH Description: Avast Installer Exit code: 0 Version: 2.1.67.0 | |||||||||||||||
Total events
8 497
Read events
8 425
Write events
69
Delete events
3
Modification events
| (PID) Process: | (3304) windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3304) windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3304) windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3304) windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3304) windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3304) windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3304) windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3304) windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3304) windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3304) windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{362E934C-743B-4588-8259-D2482DB771A8} |
| Operation: | write | Name: | WpadDecisionReason |
Value: 1 | |||
Executable files
10
Suspicious files
11
Text files
13
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:ACAEDA60C79C6BCAC925EEB3653F45E0 | SHA256:6B0CECCF0103AFD89844761417C1D23ACC41F8AEBF3B7230765209B61EEE5658 | |||
| 3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\nsJSON.dll | executable | |
MD5:F4D89D9A2A3E2F164AEA3E93864905C9 | SHA256:64B3EFDF3DE54E338D4DB96B549A7BDB7237BB88A82A0A63AEF570327A78A6FB | |||
| 3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:54E9306F95F32E50CCD58AF19753D929 | SHA256:45F94DCEB18A8F738A26DA09CE4558995A4FE02B971882E8116FC9B59813BB72 | |||
| 3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | C:\Users\admin\AppData\Local\Temp\Cab28B7.tmp | compressed | |
MD5:ACAEDA60C79C6BCAC925EEB3653F45E0 | SHA256:6B0CECCF0103AFD89844761417C1D23ACC41F8AEBF3B7230765209B61EEE5658 | |||
| 3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | C:\Users\admin\AppData\Local\Temp\Tar28B8.tmp | cat | |
MD5:D99661D0893A52A0700B8AE68457351A | SHA256:BDD5111162A6FA25682E18FA74E37E676D49CAFCB5B7207E98E5256D1EF0D003 | |||
| 3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\opera-mockup.jpg | image | |
MD5:34BC65D661AB1F432ABB5FE4B1991D4D | SHA256:1E4F6573DEC9E8D88BC3ADD573E1042FC9C4AA32B38FF3351A20BE40B0E1ED60 | |||
| 3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | C:\Users\admin\AppData\Local\Temp\nshE90D.tmp\bgopera.jpg | image | |
MD5:F2DD34AE26837260DD8A271F328F0493 | SHA256:BBEA56B4C234560C0C9867BE1BF5C3737434C9B7CF799B10CF07A4519FBB7D3B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
22
DNS requests
20
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | GET | — | 137.74.94.144:80 | http://dl3.dstudio.app/main/1.17.0.0/dstudio-gui.exe | FR | — | — | suspicious |
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAonX%2BcE1u7LI9XNW0saTgQ%3D | US | der | 471 b | whitelisted |
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | GET | 200 | 13.225.84.49:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
3880 | dist_avast.exe | POST | 204 | 5.62.40.203:80 | http://v7event.stats.avast.com/cgi-bin/iavsevents.cgi | DE | — | — | whitelisted |
3824 | dist_opera.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAbOPm2BUJKsC9DUuFz2WXk%3D | US | der | 314 b | whitelisted |
3824 | dist_opera.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | US | der | 471 b | whitelisted |
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | GET | 200 | 13.225.84.145:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | GET | 200 | 95.140.236.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fb4c3d331f22f7d9 | GB | compressed | 4.70 Kb | whitelisted |
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | GET | 200 | 13.225.84.66:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | GET | 200 | 104.89.32.83:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | 18.198.4.253:443 | dsapi.io | Massachusetts Institute of Technology | US | suspicious |
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | 92.122.255.132:443 | bits.avcdn.net | GTT Communications Inc. | — | unknown |
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | 13.225.84.145:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | 13.225.84.49:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | 185.26.182.111:443 | net.geo.opera.com | Opera Software AS | — | whitelisted |
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3824 | dist_opera.exe | 82.145.216.20:443 | autoupdate.geo.opera.com | Opera Software AS | — | unknown |
3824 | dist_opera.exe | 82.145.217.121:443 | desktop-netinstaller-sub.osp.opera.software | Opera Software AS | — | suspicious |
3880 | dist_avast.exe | 5.62.40.203:80 | v7event.stats.avast.com | AVAST Software s.r.o. | DE | unknown |
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | 13.225.84.88:80 | ocsp.sca1b.amazontrust.com | — | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dsapi.io |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
k3net.s3.eu-central-1.amazonaws.com |
| shared |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.sca1b.amazontrust.com |
| whitelisted |
net.geo.opera.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3304 | windows-loader-v2.2-password-111.zip[QkSeERyrd].exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |