| File name: | doc |
| Full analysis: | https://app.any.run/tasks/0d7d18e2-005d-4f0e-8c9e-4da92832e9e9 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2025, 08:52:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 3D33AC05D0CA473518C784C37BC887A9 |
| SHA1: | 8071B87AB3307A907052ABCE7092C4F5605E4AE3 |
| SHA256: | 06E4084E2D043F216C0BC7931781CE3E1CEA4ECA1B6092C0E34B01A89E2A6DEA |
| SSDEEP: | 1536:8Wfd3kQFgeD66nH7x1vg1sAsNQhgRLDYBSGRMuchfez7BLe:99kQFfD66bx10s+ICko8 |
MALICIOUS
GENERIC has been found (auto)
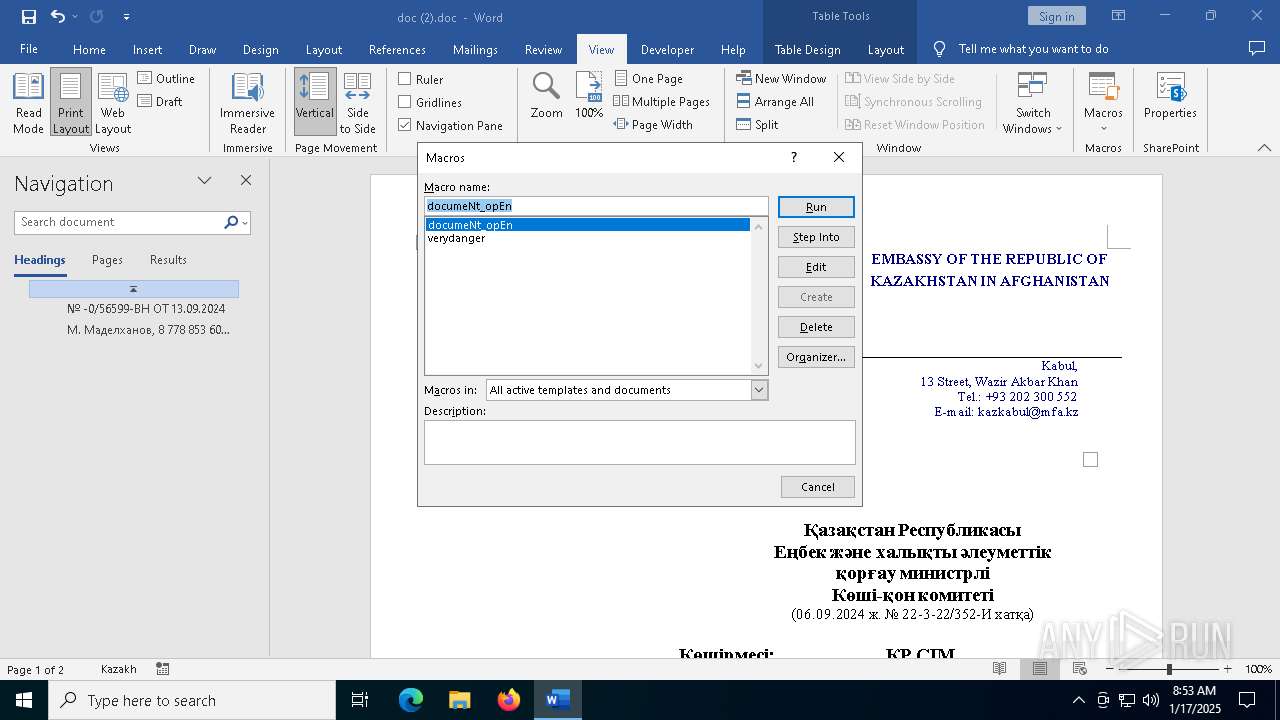
- WINWORD.EXE (PID: 6328)
- WINWORD.EXE (PID: 6704)
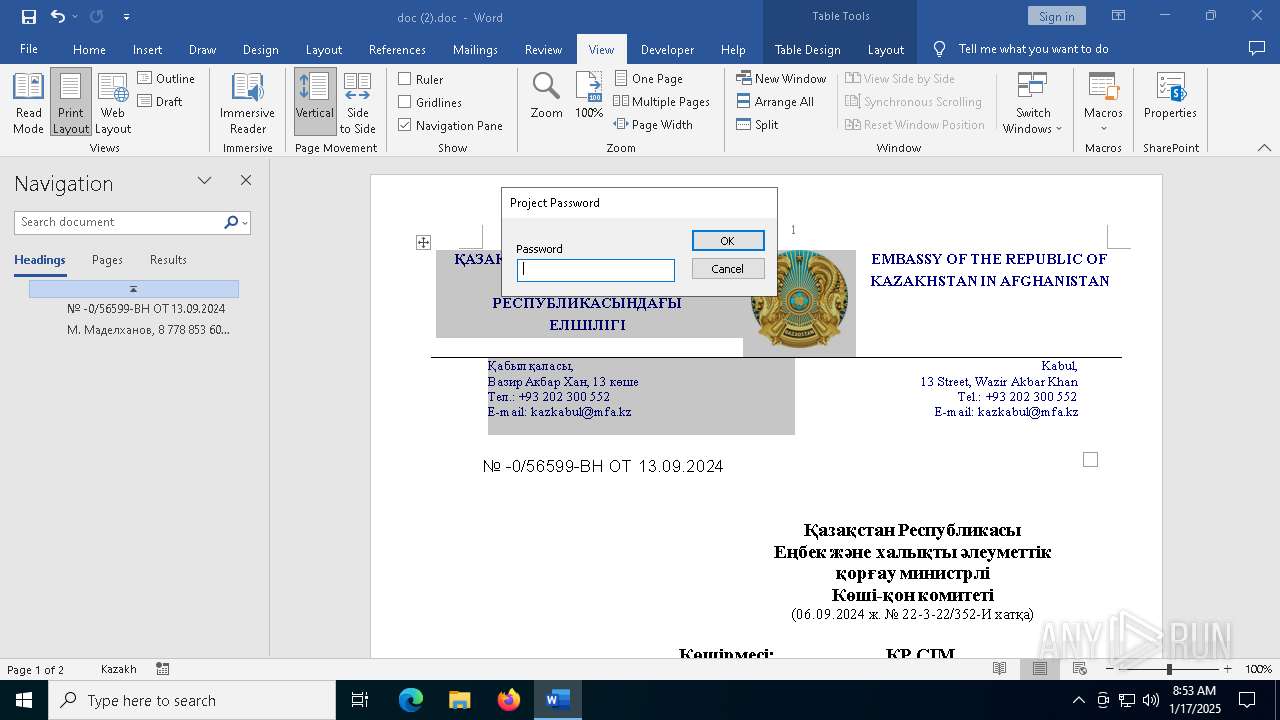
Creates a new registry key or changes the value of an existing one (SCRIPT)
- WINWORD.EXE (PID: 6704)
Access Task Scheduler's settings (SCRIPT)
- WINWORD.EXE (PID: 644)
Gets or sets visibliity for the scheduled task (SCRIPT)
- WINWORD.EXE (PID: 644)
Gets context to execute command-line operations (SCRIPT)
- WINWORD.EXE (PID: 644)
Creates a new scheduled task (SCRIPT)
- WINWORD.EXE (PID: 644)
Accesses environment variables (SCRIPT)
- WINWORD.EXE (PID: 644)
SUSPICIOUS
Accesses Scheduled Task settings (SCRIPT)
- WINWORD.EXE (PID: 644)
Accesses object representing scheduled task trigger (SCRIPT)
- WINWORD.EXE (PID: 644)
Gets context to manipulate triggers of a scheduled task (SCRIPT)
- WINWORD.EXE (PID: 644)
Gets a folder of registered tasks (SCRIPT)
- WINWORD.EXE (PID: 644)
Gets context to manipulate scheduled tasks (SCRIPT)
- WINWORD.EXE (PID: 644)
Gets scheduled task context (SCRIPT)
- WINWORD.EXE (PID: 644)
Writes binary data to a Stream object (SCRIPT)
- WINWORD.EXE (PID: 644)
INFO
Manual execution by a user
- WINWORD.EXE (PID: 6704)
Drops encrypted VBS script (Microsoft Script Encoder)
- WINWORD.EXE (PID: 6704)
Sends debugging messages
- WINWORD.EXE (PID: 6704)
- WINWORD.EXE (PID: 644)
The process uses the downloaded file
- WINWORD.EXE (PID: 6328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:09:13 16:13:56 |
| ZipCRC: | 0x344dd96c |
| ZipCompressedSize: | 449 |
| ZipUncompressedSize: | 2029 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | ЌАЗАЌСТАН РЕСПУБЛИКАСЫНЫЅ |
|---|---|
| Subject: | - |
| Creator: | Consulate |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | Kabul |
| RevisionNumber: | 28 |
| LastPrinted: | 2024:09:12 20:17:00Z |
| CreateDate: | 2024:08:27 14:45:00Z |
| ModifyDate: | 2024:09:12 22:46:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | - |
| Pages: | 2 |
| Words: | 394 |
| Characters: | 2252 |
| Application: | Microsoft Office Word |
| DocSecurity: | Unknown (12) |
| Lines: | 18 |
| Paragraphs: | 5 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: |
|
| Company: | EmbKaz |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 2641 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
137
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /Automation -Embedding | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5888 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "780C3D8E-A8D1-4274-917F-208FCA470DAB" "4975007F-FAB7-4241-98FB-9E676F6852CC" "644" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 6328 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\Desktop\doc.docx /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6704 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\doc (2).doc" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6792 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "044D0C50-2D56-4009-9B00-906365F539E6" "40DF4B6D-B81E-4A41-ACD3-2C88C3D0724C" "6328" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 6852 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "68FDCEEA-7B94-4182-AF91-E4B603DD68DF" "40B918D6-5D0C-4252-8D4E-58C8654363CB" "6704" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
25 223
Read events
23 884
Write events
1 203
Delete events
136
Modification events
| (PID) Process: | (6328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (6328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\6328 |
| Operation: | write | Name: | 0 |
Value: 0B0E10E4E0947CB9CF22478B0124750F3D24712300468ADBB29AD297DAED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B831D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6328) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
34
Suspicious files
168
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6328 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\ED18989C-0D2C-42AC-B9A4-D5C346F93B2A | xml | |
MD5:E296B227D3794B1EEF9F0111E0C1E942 | SHA256:F54039055001A56D48439E7788E046EEB216E32CACEC55BE75256C1C020FFE1E | |||
| 6328 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Word.SurveyEventActivityStats.json | binary | |
MD5:6CA4960355E4951C72AA5F6364E459D5 | SHA256:88301F0B7E96132A2699A8BCE47D120855C7F0A37054540019E3204D6BCBABA3 | |||
| 6328 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\8FD6C58.tmp | binary | |
MD5:05ED2BF9233DBFB833067B1911232DEF | SHA256:846890FAAB846DEDB355DC619C0ED4CEC6ED12F7AE39ACF49EEFD640EDA73ED2 | |||
| 6328 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Diagnostics\WINWORD\App1737103949275381000_7C94E0E4-CFB9-4722-8B01-24750F3D2471.log | — | |
MD5:— | SHA256:— | |||
| 6328 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | binary | |
MD5:518776FF2A8152A85B19E903EE40B377 | SHA256:A5C79E5A4A08AA8B4B579ED249F8DE74C7391D66679D4171FD15BF61750A8056 | |||
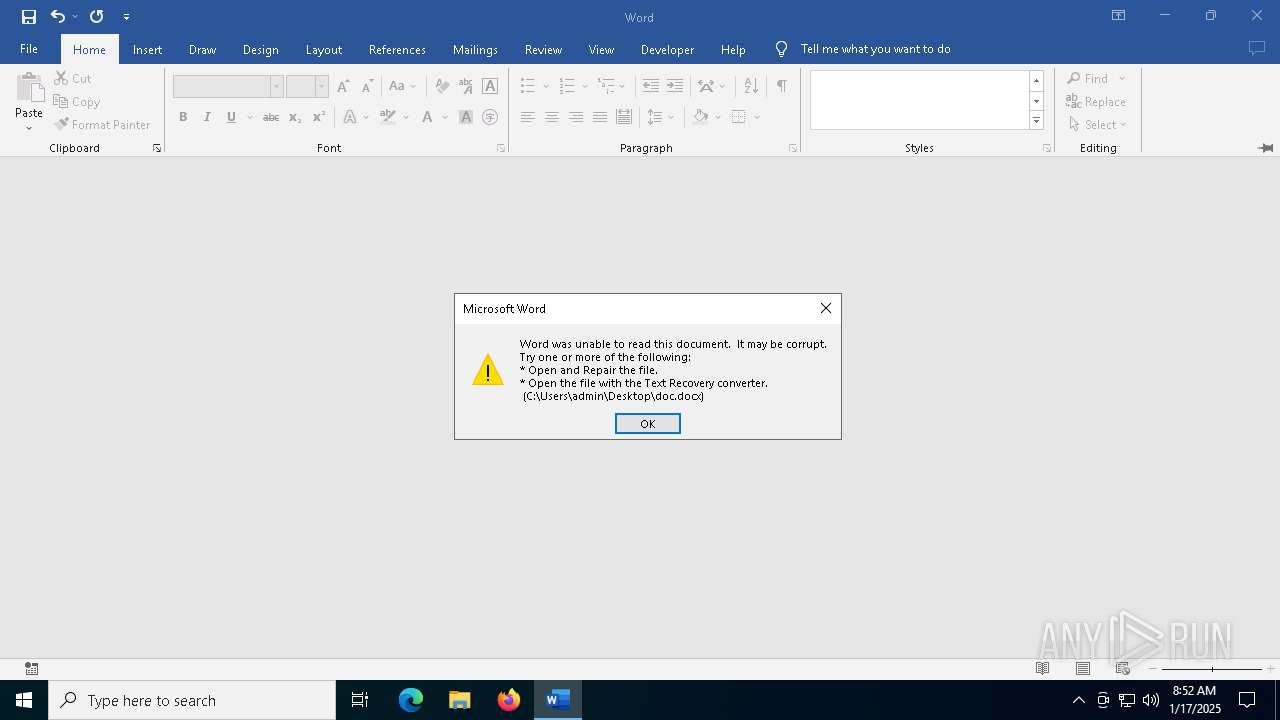
| 6328 | WINWORD.EXE | C:\Users\admin\Desktop\~$doc.docx | binary | |
MD5:EF78C5349716F4C61A516EB02CA1579F | SHA256:C4CB470AAB652BEEA9A520E25082F1AD3F15B381D279ED6639BAB60FDF37E116 | |||
| 6328 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:50D12E78F0091FB442A210926ABBA526 | SHA256:C027AC19CBEA77EE3746D192CEFE7936E22310052231E184169B897BB4C4A534 | |||
| 6328 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:8B50A6BABF4B4067CD231652A8D363CD | SHA256:786E42235D7127569CC778831100D9C9DC61C47CE540684320F6749FFB077984 | |||
| 6328 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json | binary | |
MD5:518776FF2A8152A85B19E903EE40B377 | SHA256:A5C79E5A4A08AA8B4B579ED249F8DE74C7391D66679D4171FD15BF61750A8056 | |||
| 6328 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Word.SurveyHistoryStats.json | binary | |
MD5:6CA4960355E4951C72AA5F6364E459D5 | SHA256:88301F0B7E96132A2699A8BCE47D120855C7F0A37054540019E3204D6BCBABA3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
88
DNS requests
38
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6328 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6328 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6620 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6620 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6704 | WINWORD.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6704 | WINWORD.EXE | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
6056 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | — | Ooredoo Q.S.C. | QA | unknown |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3700 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1176 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|